Computer Forensics: Cybercrime, Social, and Legal Aspects
VerifiedAdded on 2021/07/07
|12
|4209
|154
Report
AI Summary
This report delves into the multifaceted field of computer forensics, examining its critical role in addressing the escalating challenges of cybercrime. It begins with an introduction to the current trends in computer forensics, highlighting the increasing reliance on digital evidence in legal proceedings. The report covers various aspects of computer forensics, including the different types of cybercrimes, social, legal, economic, ethical, political, and environmental impacts. It also explores the legal frameworks and challenges faced by computer forensics professionals, with a specific focus on the situation in Sri Lanka. The report discusses cryptography, steganography, and footprinting, as well as the economic and social impact of cybercrime. Furthermore, it addresses the future challenges in computer forensics, emphasizing the need for continuous development in skills and technology to combat evolving cyber threats. The report concludes by underscoring the importance of computer forensics in ensuring a secure digital environment and the need for proactive measures to address future challenges.

Word count: 3059
Comphute
r Forensics
Name
ID
Programme name
University name
Comphute
r Forensics
Name
ID
Programme name
University name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
A. INTRODUCTION: TRENDING TODAY................................................................................................................................1
B. COMPUTER FORENSICS.................................................................................................................................................1
C. CYBER CRIMES............................................................................................................................................................2
D. SOCIAL IMPACT...........................................................................................................................................................3
E. LEGAL ASPECT............................................................................................................................................................4
F. ECONOMIC ASPECT......................................................................................................................................................5
G. ETHICAL ASPECT..........................................................................................................................................................6
H. POLITICAL ASPECT.......................................................................................................................................................7
I. ENVIRONMENTAL ASPECT.............................................................................................................................................7
J. FUTURE CHALLENGES IN COMPUTER FORENSICS................................................................................................................7
K. CONCLUSION..............................................................................................................................................................8
REFERENCE........................................................................................................................................................................ 8
a
A. INTRODUCTION: TRENDING TODAY................................................................................................................................1
B. COMPUTER FORENSICS.................................................................................................................................................1
C. CYBER CRIMES............................................................................................................................................................2
D. SOCIAL IMPACT...........................................................................................................................................................3
E. LEGAL ASPECT............................................................................................................................................................4
F. ECONOMIC ASPECT......................................................................................................................................................5
G. ETHICAL ASPECT..........................................................................................................................................................6
H. POLITICAL ASPECT.......................................................................................................................................................7
I. ENVIRONMENTAL ASPECT.............................................................................................................................................7
J. FUTURE CHALLENGES IN COMPUTER FORENSICS................................................................................................................7
K. CONCLUSION..............................................................................................................................................................8
REFERENCE........................................................................................................................................................................ 8
a

Computer Forensics
Keywords— computer forencis, challenges, computer forensics
A. INTRODUCTION: TRENDING TODAY
With the rapid development of technology, law
prosecution and the legal formation face number
of new challenges every day. Most countries have
committed several forms of criminal acts to record
the crime related evidence in form of digital.
Furthermore, crimes have now stepped up to the
cyberspace today and therefore, digital based
crime related evidence recording is quite practical
and efficient in law enforcement. Thus, computer
security professionals must be well aware of legal
system requirements related to digital evidence
recording of crimes in field of computer forensics.
Forensic technologies involve various tools and
methods to recover data from a seized computer
system in an evidence form.
B. COMPUTER FORENSICS
Garfinkel [1] states that in digital forensics, the
retrieving data can be from any data source such
as computer memory, hard drive or a printed hard
copy taken from any computer related system.
Further, Popescu et al [2] highlight that this
abstraction must be done in such a way that fulfils
the needs of the event or crime to verify as a solid
evidence. Usually, it can be expected to delete or
alter the system stored data to protect the
convicting facts during a crime [1][2][3]. Thus, by
agreeing to author reviews, the core functionality
of computer forensics can be argued as the
retrieval of such deleted or altered data mainly.
Digital forensics can be divided in to several sub-
disciplines such as computer Forensics, Network
Forensics, Mobile Devices Forensics, Digital
Image Forensics, Digital Video/Audio Forensics
and Memory forensics [4]. this report mainly
focus on the sub-discipline of computer forensics
which indicates the identification, protection,
assembly, investigation and reporting on evidence
gathered in digital storage media, computers and
laptops which increases the efficiency of crime
investigations and legal proceedings.
The cyber security professionals have advised the
requirement to seizure the trend early given the
fact that Sri Lanka is dignified to unveil its
striving programme to turn out to be a regional
commercial hub. The overall yearly expenditure
of all security breaches is estimated as nearly $
2.1 trillion globally by 2019 and it is exactly 4
times bigger than the overall yearly expenditure in
2015. Digital and IT literacy of people in Sri
Lankan is reported as 38.7% and 28.3%
respectively. Further, it is reported that nearly
57% mobiles and 38% computers are connected to
internet in Sri Lanka generally. However, as per
the records of Sri Lanka Police, cyber security is
recognised as a very susceptible problem among
1
Keywords— computer forencis, challenges, computer forensics
A. INTRODUCTION: TRENDING TODAY
With the rapid development of technology, law
prosecution and the legal formation face number
of new challenges every day. Most countries have
committed several forms of criminal acts to record
the crime related evidence in form of digital.
Furthermore, crimes have now stepped up to the
cyberspace today and therefore, digital based
crime related evidence recording is quite practical
and efficient in law enforcement. Thus, computer
security professionals must be well aware of legal
system requirements related to digital evidence
recording of crimes in field of computer forensics.
Forensic technologies involve various tools and
methods to recover data from a seized computer
system in an evidence form.
B. COMPUTER FORENSICS
Garfinkel [1] states that in digital forensics, the
retrieving data can be from any data source such
as computer memory, hard drive or a printed hard
copy taken from any computer related system.
Further, Popescu et al [2] highlight that this
abstraction must be done in such a way that fulfils
the needs of the event or crime to verify as a solid
evidence. Usually, it can be expected to delete or
alter the system stored data to protect the
convicting facts during a crime [1][2][3]. Thus, by
agreeing to author reviews, the core functionality
of computer forensics can be argued as the
retrieval of such deleted or altered data mainly.
Digital forensics can be divided in to several sub-
disciplines such as computer Forensics, Network
Forensics, Mobile Devices Forensics, Digital
Image Forensics, Digital Video/Audio Forensics
and Memory forensics [4]. this report mainly
focus on the sub-discipline of computer forensics
which indicates the identification, protection,
assembly, investigation and reporting on evidence
gathered in digital storage media, computers and
laptops which increases the efficiency of crime
investigations and legal proceedings.
The cyber security professionals have advised the
requirement to seizure the trend early given the
fact that Sri Lanka is dignified to unveil its
striving programme to turn out to be a regional
commercial hub. The overall yearly expenditure
of all security breaches is estimated as nearly $
2.1 trillion globally by 2019 and it is exactly 4
times bigger than the overall yearly expenditure in
2015. Digital and IT literacy of people in Sri
Lankan is reported as 38.7% and 28.3%
respectively. Further, it is reported that nearly
57% mobiles and 38% computers are connected to
internet in Sri Lanka generally. However, as per
the records of Sri Lanka Police, cyber security is
recognised as a very susceptible problem among
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

local society due to the lack of knowledge and
awareness among public in surfing the internet
securely [5]. Country aims for an aspiration with 5
years strategy from 2018 to 2023 to develop a
cyber-crime safe nation. Thus, it can be argued
that if the country can adopt to the new strategy, it
will create a trusted and resilient cyber security
environment in Sri Lanka to allow the people to
gain advantages of digital technology and enable
development [5].
C. CYBER CRIMES
Computer aided crimes
Computer aided crimes include the all the crimes
that can be done with the assistance of computers
although they also can be done without computers
such as theft and fraud, cyber-stalking and cyber-
bullying, corporate and government intelligence,
illegal pornography and paedophilia (e.g. child
abuse, sexual exploitation).
Computer based crimes / computer integrity
crimes
Computer based crimes include the all the crimes
that are performed using computers technology
and these crimes cannot be performed without
computers such as malware (viruses, trojans and
worms), dos attacks, website defacement, hacking
and system trespassing (packet sniffing, port
scanning, key loggers, password cracking),
spamming and adware.
Evidence provision non-computer and computer
based crimes
As stated by Britz [6], computer criminals are
inspired by revenge, greed, other emotions and
anger, sexual impulses, political motives and
psychiatric illnesses. Research up to the present
time specifies that there are no substantial
sociodemographic variances among traditional
criminals and computer criminals. In contrast to
general myths, Nelson et al [7] state that computer
criminals are not more introverted, intelligent, or
socially incompetent than the other criminals or
general public. Even though most computer
criminals are younger and male, compared to
traditional criminals, that demographic profile
describes the majority of persons involved in
dangerous and criminal activities and, similar to
traditional criminals, computer criminals are
inclined to age out of these actions [8].
Particular computer criminal actions for example
those focused at companies (for instance, fraud,
intellectual property theft, data misuse) are
interrelated with specific types of offenders [1][6]
[7]. In such case, the highest risk comes mainly
from inside workers than external parties of
organization. Therefore, it can be argued that it is
dependable on white collar crime in general. In
the insider type of offenders, dissatisfied workers
are responsible for the highest financial effect to
businesses. According to Nelson et al [7], these
workers frequently function behind computer
2
awareness among public in surfing the internet
securely [5]. Country aims for an aspiration with 5
years strategy from 2018 to 2023 to develop a
cyber-crime safe nation. Thus, it can be argued
that if the country can adopt to the new strategy, it
will create a trusted and resilient cyber security
environment in Sri Lanka to allow the people to
gain advantages of digital technology and enable
development [5].
C. CYBER CRIMES
Computer aided crimes
Computer aided crimes include the all the crimes
that can be done with the assistance of computers
although they also can be done without computers
such as theft and fraud, cyber-stalking and cyber-
bullying, corporate and government intelligence,
illegal pornography and paedophilia (e.g. child
abuse, sexual exploitation).
Computer based crimes / computer integrity
crimes
Computer based crimes include the all the crimes
that are performed using computers technology
and these crimes cannot be performed without
computers such as malware (viruses, trojans and
worms), dos attacks, website defacement, hacking
and system trespassing (packet sniffing, port
scanning, key loggers, password cracking),
spamming and adware.
Evidence provision non-computer and computer
based crimes
As stated by Britz [6], computer criminals are
inspired by revenge, greed, other emotions and
anger, sexual impulses, political motives and
psychiatric illnesses. Research up to the present
time specifies that there are no substantial
sociodemographic variances among traditional
criminals and computer criminals. In contrast to
general myths, Nelson et al [7] state that computer
criminals are not more introverted, intelligent, or
socially incompetent than the other criminals or
general public. Even though most computer
criminals are younger and male, compared to
traditional criminals, that demographic profile
describes the majority of persons involved in
dangerous and criminal activities and, similar to
traditional criminals, computer criminals are
inclined to age out of these actions [8].
Particular computer criminal actions for example
those focused at companies (for instance, fraud,
intellectual property theft, data misuse) are
interrelated with specific types of offenders [1][6]
[7]. In such case, the highest risk comes mainly
from inside workers than external parties of
organization. Therefore, it can be argued that it is
dependable on white collar crime in general. In
the insider type of offenders, dissatisfied workers
are responsible for the highest financial effect to
businesses. According to Nelson et al [7], these
workers frequently function behind computer
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
security panels and have intimate knowledge and
intellectual property whose harm would harshly
harm the business either publicly and financially
be uncomfortable to the business.
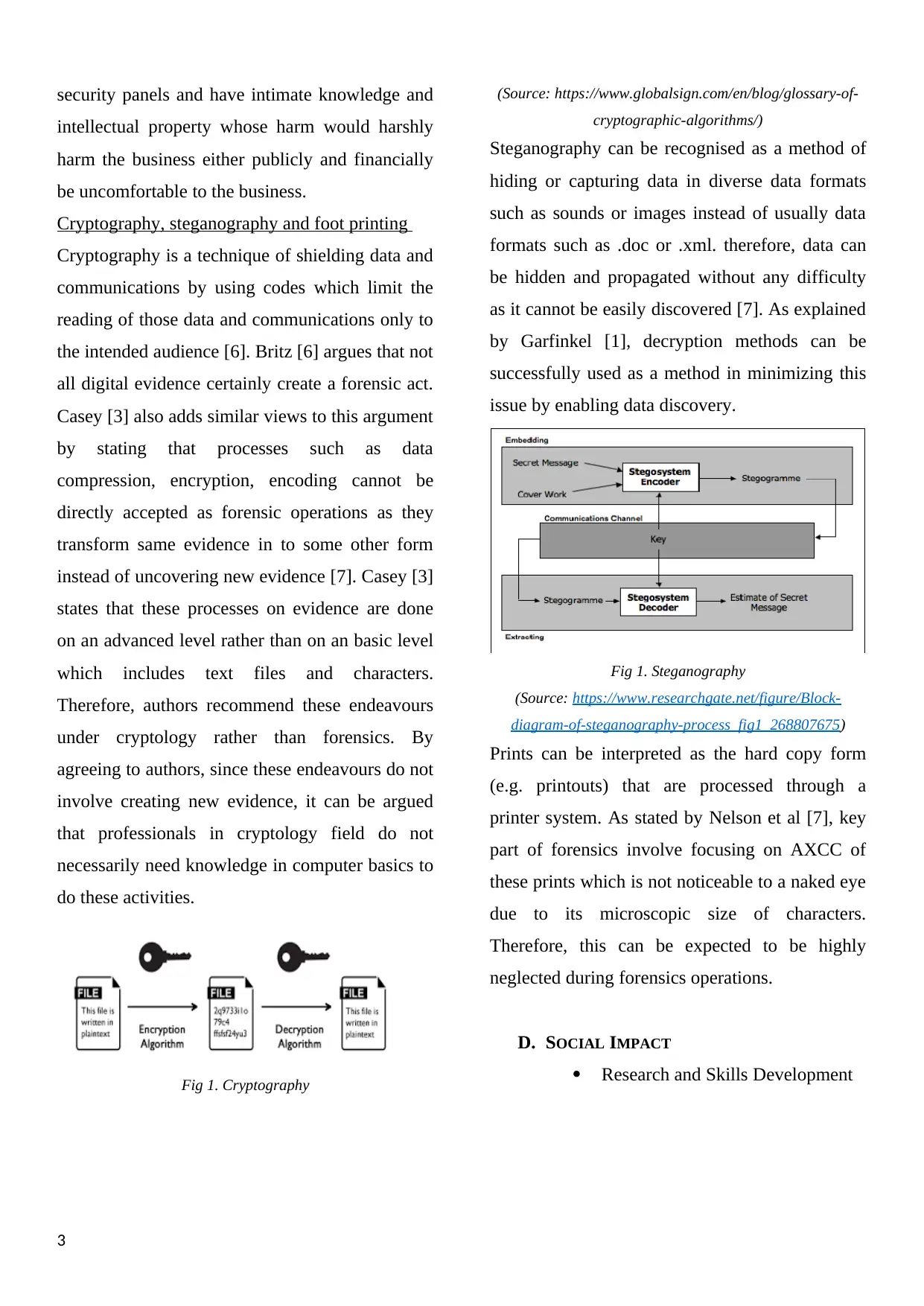
Cryptography, steganography and foot printing
Cryptography is a technique of shielding data and
communications by using codes which limit the
reading of those data and communications only to
the intended audience [6]. Britz [6] argues that not
all digital evidence certainly create a forensic act.
Casey [3] also adds similar views to this argument
by stating that processes such as data
compression, encryption, encoding cannot be
directly accepted as forensic operations as they
transform same evidence in to some other form
instead of uncovering new evidence [7]. Casey [3]
states that these processes on evidence are done
on an advanced level rather than on an basic level
which includes text files and characters.
Therefore, authors recommend these endeavours
under cryptology rather than forensics. By
agreeing to authors, since these endeavours do not
involve creating new evidence, it can be argued
that professionals in cryptology field do not
necessarily need knowledge in computer basics to
do these activities.
Fig 1. Cryptography
(Source: https://www.globalsign.com/en/blog/glossary-of-
cryptographic-algorithms/)
Steganography can be recognised as a method of
hiding or capturing data in diverse data formats
such as sounds or images instead of usually data
formats such as .doc or .xml. therefore, data can
be hidden and propagated without any difficulty
as it cannot be easily discovered [7]. As explained
by Garfinkel [1], decryption methods can be
successfully used as a method in minimizing this
issue by enabling data discovery.
Fig 1. Steganography
(Source: https://www.researchgate.net/figure/Block-
diagram-of-steganography-process_fig1_268807675)
Prints can be interpreted as the hard copy form
(e.g. printouts) that are processed through a
printer system. As stated by Nelson et al [7], key
part of forensics involve focusing on AXCC of
these prints which is not noticeable to a naked eye
due to its microscopic size of characters.
Therefore, this can be expected to be highly
neglected during forensics operations.
D. SOCIAL IMPACT
Research and Skills Development
3
intellectual property whose harm would harshly
harm the business either publicly and financially
be uncomfortable to the business.
Cryptography, steganography and foot printing
Cryptography is a technique of shielding data and
communications by using codes which limit the
reading of those data and communications only to
the intended audience [6]. Britz [6] argues that not
all digital evidence certainly create a forensic act.
Casey [3] also adds similar views to this argument
by stating that processes such as data
compression, encryption, encoding cannot be
directly accepted as forensic operations as they
transform same evidence in to some other form
instead of uncovering new evidence [7]. Casey [3]
states that these processes on evidence are done
on an advanced level rather than on an basic level
which includes text files and characters.
Therefore, authors recommend these endeavours
under cryptology rather than forensics. By
agreeing to authors, since these endeavours do not
involve creating new evidence, it can be argued
that professionals in cryptology field do not
necessarily need knowledge in computer basics to
do these activities.
Fig 1. Cryptography
(Source: https://www.globalsign.com/en/blog/glossary-of-
cryptographic-algorithms/)
Steganography can be recognised as a method of
hiding or capturing data in diverse data formats
such as sounds or images instead of usually data
formats such as .doc or .xml. therefore, data can
be hidden and propagated without any difficulty
as it cannot be easily discovered [7]. As explained
by Garfinkel [1], decryption methods can be
successfully used as a method in minimizing this
issue by enabling data discovery.
Fig 1. Steganography
(Source: https://www.researchgate.net/figure/Block-
diagram-of-steganography-process_fig1_268807675)
Prints can be interpreted as the hard copy form
(e.g. printouts) that are processed through a
printer system. As stated by Nelson et al [7], key
part of forensics involve focusing on AXCC of
these prints which is not noticeable to a naked eye
due to its microscopic size of characters.
Therefore, this can be expected to be highly
neglected during forensics operations.
D. SOCIAL IMPACT
Research and Skills Development
3

However, when Sri Lanka is concerned, the
Digital Forensics Centre (DFC) of University of
Colombo School of Computing (UCSC) was the
first establishment related to computer forensics
in Sri Lanka, which was established in 2011 as a
result of continued request for 15 years by the
local authorities [9]. Further, DFC highlights that
their tools have been built by UCSC academic and
academic support staffs mostly [9]. Therefore, it
can be argued that the computer forensic
processes in Sri Lanka require further expansion
in skills development as it needs a better
combination of more skilled computer forensic
experts and the most suitable and advanced
computer forensic tools, which was not common
in practice in last few decades.
Empowering Police Force
In Sri Lanka, police administration plays a vital
role in public administration and law prosecution.
Sri Lanka is a small country with 401 Police
stations to support nearly 21 million population..
Sri Lankan constitution had offered police force
the duty for law maintenance among several
territories, routine policing such as controlling
anxiety of criminals [10]. However, there is a
noticeable growth in cybercrimes in Sri Lanka
from 71 cases in 2010 to 222 in 2017 [5].
Therefore, it can be argued that while the crime
control functionality of police force remains
constant from the perspective of government, the
country critically requires more developments of
computer forensics technology, further and
further.
E. LEGAL ASPECT
There are many strong cyber laws across countries
to safe guard customers from online fraud such as
identity theft, financial crimes, credit card thefts
and so on. Therefore, an individual who commits
identity theft can face state or federal criminal
fines. Copyright violation is a very common threat
in internet as it can be done simply by clicking
one button in file sharing websites [11]. Thus,
Surfaro [12] argues that strong copyright
infringement is required to impose copyright
protections which protects the rights of persons
and businesses to profit from their creativity.
Defamation laws are mostly considered as civil
laws which are required in cyber space to defend
persons from false public declarations that can
offend somebody’s personal reputation or a
business reputation [11]. Although this is a well-
developed cyber law among many European
nations, it can be argued that noticeable
developments are required in defamation laws in
Sri Lanka today. Usage of social media such as
Facebook by individuals to make personal
statements in public had made critical changes in
local government authority in Sri Lanka in recent
history [11]. Further, personal statements in
Facebook that violate several civil laws lead to
several fights and conflicts among local
community groups, within past three years.
4
Digital Forensics Centre (DFC) of University of
Colombo School of Computing (UCSC) was the
first establishment related to computer forensics
in Sri Lanka, which was established in 2011 as a
result of continued request for 15 years by the
local authorities [9]. Further, DFC highlights that
their tools have been built by UCSC academic and
academic support staffs mostly [9]. Therefore, it
can be argued that the computer forensic
processes in Sri Lanka require further expansion
in skills development as it needs a better
combination of more skilled computer forensic
experts and the most suitable and advanced
computer forensic tools, which was not common
in practice in last few decades.
Empowering Police Force
In Sri Lanka, police administration plays a vital
role in public administration and law prosecution.
Sri Lanka is a small country with 401 Police
stations to support nearly 21 million population..
Sri Lankan constitution had offered police force
the duty for law maintenance among several
territories, routine policing such as controlling
anxiety of criminals [10]. However, there is a
noticeable growth in cybercrimes in Sri Lanka
from 71 cases in 2010 to 222 in 2017 [5].
Therefore, it can be argued that while the crime
control functionality of police force remains
constant from the perspective of government, the
country critically requires more developments of
computer forensics technology, further and
further.
E. LEGAL ASPECT
There are many strong cyber laws across countries
to safe guard customers from online fraud such as
identity theft, financial crimes, credit card thefts
and so on. Therefore, an individual who commits
identity theft can face state or federal criminal
fines. Copyright violation is a very common threat
in internet as it can be done simply by clicking
one button in file sharing websites [11]. Thus,
Surfaro [12] argues that strong copyright
infringement is required to impose copyright
protections which protects the rights of persons
and businesses to profit from their creativity.
Defamation laws are mostly considered as civil
laws which are required in cyber space to defend
persons from false public declarations that can
offend somebody’s personal reputation or a
business reputation [11]. Although this is a well-
developed cyber law among many European
nations, it can be argued that noticeable
developments are required in defamation laws in
Sri Lanka today. Usage of social media such as
Facebook by individuals to make personal
statements in public had made critical changes in
local government authority in Sri Lanka in recent
history [11]. Further, personal statements in
Facebook that violate several civil laws lead to
several fights and conflicts among local
community groups, within past three years.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Occasionally online declarations can interrupt
criminal laws that exclude harassment and
stalking [11]. Therefore, if an individual keeps
sending threatening declarations, it usually
damages both criminal civil and laws. Online
businesses mostly depend on cyber law when
guard their business secrets. For example, search
engine such as Goggle use several unique features
such as maps, flight search services that are
unique to Google. Thus, cyber laws must
essentially protect these business secrets as well.
When a user clicks a button to agree on terms and
conditions, user by default adherers to cyber law
[11]. Contracts can be used to guard persons and
businesses when they use technology during
online dealings.
The General Data Protection Regulation (GDPR)
ensures better transparency in online businesses to
give users more control over their personal data
through data policies [11]. This act is widely
applicable among European countries. However,
privacy activists have been influencing social
media such as Facebook to extend and apply their
changes to other countries as well.
Government of Sri Lanka indorsed the Electronic
Transactions Act No 19 of 2006 primarily to find
and enable for electronic commerce and to boost
both private and public sectors to encourage
digital transactions evading disputes over the
acceptability of e-documents (e.g. emails, SMS)
and electronic transactions [14].
In Sri Lanka, several legislation including
Computer Crimes Act No 24 of 2007 aim to
support police by minimising the crimes and
cover intellectual property rights, digital
transactions and payment devices frauds.
However in Sri Lanka, it is evident that there is no
particular law to cover the sophisticated recent
cybercrimes although the Budapest Convention on
Cyber Crime was ratified in 2015 [9]. Further,
that Data Protection Act must be able to strictly
control the personal data collection of people,
usage and disclosure of them by the organisations
(including government) and violators must
essentially be liable for a noticeable penalty. The
Cyber Security Act must be able to save the
people from sophisticated cyber security threats
specifically.
F. ECONOMIC ASPECT
The Norton Cybercrime revealed that more than
74 million persons became victims of cybercrime
in only 2010 in the United States which resulted
nearly $32 billion financial loses [14]. Further,
Lewis and Baker [15] state that nearly 69% (1
million) of adults who are online become
cybercrime victims daily. Most people believe
that cybercrime happen during online dealings
only [15]. This argument can be accepted as
modern customers have gradually become highly
dependent on internet, computers and other
networks that store and reserve information that
has high threat from cyber-crimes [15]. Further,
Insua et al [16] state that nearly 80% of businesses
5
criminal laws that exclude harassment and
stalking [11]. Therefore, if an individual keeps
sending threatening declarations, it usually
damages both criminal civil and laws. Online
businesses mostly depend on cyber law when
guard their business secrets. For example, search
engine such as Goggle use several unique features
such as maps, flight search services that are
unique to Google. Thus, cyber laws must
essentially protect these business secrets as well.
When a user clicks a button to agree on terms and
conditions, user by default adherers to cyber law
[11]. Contracts can be used to guard persons and
businesses when they use technology during
online dealings.
The General Data Protection Regulation (GDPR)
ensures better transparency in online businesses to
give users more control over their personal data
through data policies [11]. This act is widely
applicable among European countries. However,
privacy activists have been influencing social
media such as Facebook to extend and apply their
changes to other countries as well.
Government of Sri Lanka indorsed the Electronic
Transactions Act No 19 of 2006 primarily to find
and enable for electronic commerce and to boost
both private and public sectors to encourage
digital transactions evading disputes over the
acceptability of e-documents (e.g. emails, SMS)
and electronic transactions [14].
In Sri Lanka, several legislation including
Computer Crimes Act No 24 of 2007 aim to
support police by minimising the crimes and
cover intellectual property rights, digital
transactions and payment devices frauds.
However in Sri Lanka, it is evident that there is no
particular law to cover the sophisticated recent
cybercrimes although the Budapest Convention on
Cyber Crime was ratified in 2015 [9]. Further,
that Data Protection Act must be able to strictly
control the personal data collection of people,
usage and disclosure of them by the organisations
(including government) and violators must
essentially be liable for a noticeable penalty. The
Cyber Security Act must be able to save the
people from sophisticated cyber security threats
specifically.
F. ECONOMIC ASPECT
The Norton Cybercrime revealed that more than
74 million persons became victims of cybercrime
in only 2010 in the United States which resulted
nearly $32 billion financial loses [14]. Further,
Lewis and Baker [15] state that nearly 69% (1
million) of adults who are online become
cybercrime victims daily. Most people believe
that cybercrime happen during online dealings
only [15]. This argument can be accepted as
modern customers have gradually become highly
dependent on internet, computers and other
networks that store and reserve information that
has high threat from cyber-crimes [15]. Further,
Insua et al [16] state that nearly 80% of businesses
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

usually face financial losses due to computer
breaches worldwide which can be nearly $450
million while 10% of that represents financial
fraud.
On the other hand, the risk of losing
confidentiality, integrity, and availability of
computer systems is increasing due to theft of
personal recognition data to denial of service
attacks. However, modern economy of most
businesses highly depend on internet
communication which has direct threat from
cyber-criminals [14]. Stock markets, online
banking and credit card transactions can be listed
as best examples to prove this fact. The modern
global economy connects countries and regions
together. Thus, the interruption of global
financial markets can be argued as a larger
impact and a serious concern of cyber-criminals
[14]. On the other hand, cyber-attack to one
country or one region can directly make negative
impacts on other countries and regions as well. On
the other hand, the economic and productivity
shocks of one industry due to a cybercrime may
carry waves to other industries and markets as
well [14]. Cyber-attacks such as worms and
viruses can make direct negative impacts on user
productivity (e.g. slowing down servers and
machines, jammed networks). Such productivity
impact can negatively impact on customer
services which is linked to organizational
financial aspects. For example, if the customer
service is malfunctioning, this can reduce the
online shopper transactions.
G. ETHICAL ASPECT
Customer trust and satisfaction
As cyber-attackers impose into space of others
and attempt to disrupt the logic of that page (e.g.
web page). if the shopper visits that particular
page, shopper can be unsatisfied and dispirited to
stay in that page for a long time. All though the
root cause of the fault is with the criminal who
attacks hiddenly, only the particular page will be
recognised by shoppers as fraudulent and
punishable [15]. Therefore, confidence of
customers on strengths of such pages and also on
internet will be dropped. As found in survey by
Insua et al [16], more than 80% of online
shoppers mentioned their security as a main
concern when performing online transactions and
over 75% of them stop their transactions if the
credit card information is asked. Thus, it can be
argued that, threat of credit card fraud and
security hazards have made critical impact on e-
commerce. On the other hand, Insua et al [16]
stress that customer sensitivities of fraud
complicates the situation to be worse than the
reality. While consumer experiences and ideas are
powerful in business development, it can also be
damaging in front of cyber-attackers. Thus, it can
be argued that even the smallest observation of
cyber security risk or unprofessional commerce
6
breaches worldwide which can be nearly $450
million while 10% of that represents financial
fraud.
On the other hand, the risk of losing
confidentiality, integrity, and availability of
computer systems is increasing due to theft of
personal recognition data to denial of service
attacks. However, modern economy of most
businesses highly depend on internet
communication which has direct threat from
cyber-criminals [14]. Stock markets, online
banking and credit card transactions can be listed
as best examples to prove this fact. The modern
global economy connects countries and regions
together. Thus, the interruption of global
financial markets can be argued as a larger
impact and a serious concern of cyber-criminals
[14]. On the other hand, cyber-attack to one
country or one region can directly make negative
impacts on other countries and regions as well. On
the other hand, the economic and productivity
shocks of one industry due to a cybercrime may
carry waves to other industries and markets as
well [14]. Cyber-attacks such as worms and
viruses can make direct negative impacts on user
productivity (e.g. slowing down servers and
machines, jammed networks). Such productivity
impact can negatively impact on customer
services which is linked to organizational
financial aspects. For example, if the customer
service is malfunctioning, this can reduce the
online shopper transactions.
G. ETHICAL ASPECT
Customer trust and satisfaction
As cyber-attackers impose into space of others
and attempt to disrupt the logic of that page (e.g.
web page). if the shopper visits that particular
page, shopper can be unsatisfied and dispirited to
stay in that page for a long time. All though the
root cause of the fault is with the criminal who
attacks hiddenly, only the particular page will be
recognised by shoppers as fraudulent and
punishable [15]. Therefore, confidence of
customers on strengths of such pages and also on
internet will be dropped. As found in survey by
Insua et al [16], more than 80% of online
shoppers mentioned their security as a main
concern when performing online transactions and
over 75% of them stop their transactions if the
credit card information is asked. Thus, it can be
argued that, threat of credit card fraud and
security hazards have made critical impact on e-
commerce. On the other hand, Insua et al [16]
stress that customer sensitivities of fraud
complicates the situation to be worse than the
reality. While consumer experiences and ideas are
powerful in business development, it can also be
damaging in front of cyber-attackers. Thus, it can
be argued that even the smallest observation of
cyber security risk or unprofessional commerce
6

extremely endangers prospective business
opportunities.
H. POLITICAL ASPECT
When the policy making and strategic planning
processes in Sri Lanka are concerned, it is obvious
to state that they highly depend on the governing
or ruling party and thus, these strategies usually
changes when the government is changed. By
highlighting the research content of a legal
researcher, Lewis [17] states that a noticeable
decrement in cyber-piracy in film and music
industry as a result of computer forensic
technology enhancements in corporations and
government sector. Today, most crime groups
use the Internet as a common media in most
frauds and thefts today with the involvement of
white-collar crime. Therefore, globally, internet
based crimes are most prevalent in cybercrimes
(e.g. Internet-based stock fraud). As highlighted
by Lewis [17], this success had been achieved by
a strong inter-government cooperative efforts
mainly. When Sri Lanka is concerned, it is
essential to maintain more rigid strategic plan in
empowering the computer forensics activities,
irrespective of the impact by governing or ruling
party.
I. ENVIRONMENTAL ASPECT
With the increment of environmental changes and
challenges, information management and
distribution can become a critical issue in terms of
time efficiency which are essential in meaningful
crime analysis for a sophisticated investigation
[10]. In most of the industries especially in
developed countries, a network of sensors are
used together to monitor data around machinery
productivity and material processing flow. These
data are then sent to servers for interpretation and
create instructions for several hardware devices
such as pumps and motors [18]. However, such
automation can be in a high risk when they are
attacked by cyber criminals as entire process can
be controlled centrally. For example, due to a
hacker attack in 2000, 800,000 liters of
unprocessed sewage to flood the water channels
of Maroochy Shire, Australia. Further, an IT
contractor dissatisfied as he was not employed as
a full-timer and thus, he managed to disable leak
detection alarm systems on three off-shore oil rigs
near Long Beach, Calif in 2009 [18].
J. FUTURE CHALLENGES IN COMPUTER
FORENSICS
Complexity Explosion
it is evident that with the development of
computer forensics, evidence is not limited to on
location but distributed across multiple virtual and
physical locations such as social media and cloud
storages. Thus, professionals may require more
advanced and complex tools in computer
forensics analysis process to adopt to new cyber
threat trends [19].
Privacy-preserving investigations
7
opportunities.
H. POLITICAL ASPECT
When the policy making and strategic planning
processes in Sri Lanka are concerned, it is obvious
to state that they highly depend on the governing
or ruling party and thus, these strategies usually
changes when the government is changed. By
highlighting the research content of a legal
researcher, Lewis [17] states that a noticeable
decrement in cyber-piracy in film and music
industry as a result of computer forensic
technology enhancements in corporations and
government sector. Today, most crime groups
use the Internet as a common media in most
frauds and thefts today with the involvement of
white-collar crime. Therefore, globally, internet
based crimes are most prevalent in cybercrimes
(e.g. Internet-based stock fraud). As highlighted
by Lewis [17], this success had been achieved by
a strong inter-government cooperative efforts
mainly. When Sri Lanka is concerned, it is
essential to maintain more rigid strategic plan in
empowering the computer forensics activities,
irrespective of the impact by governing or ruling
party.
I. ENVIRONMENTAL ASPECT
With the increment of environmental changes and
challenges, information management and
distribution can become a critical issue in terms of
time efficiency which are essential in meaningful
crime analysis for a sophisticated investigation
[10]. In most of the industries especially in
developed countries, a network of sensors are
used together to monitor data around machinery
productivity and material processing flow. These
data are then sent to servers for interpretation and
create instructions for several hardware devices
such as pumps and motors [18]. However, such
automation can be in a high risk when they are
attacked by cyber criminals as entire process can
be controlled centrally. For example, due to a
hacker attack in 2000, 800,000 liters of
unprocessed sewage to flood the water channels
of Maroochy Shire, Australia. Further, an IT
contractor dissatisfied as he was not employed as
a full-timer and thus, he managed to disable leak
detection alarm systems on three off-shore oil rigs
near Long Beach, Calif in 2009 [18].
J. FUTURE CHALLENGES IN COMPUTER
FORENSICS
Complexity Explosion
it is evident that with the development of
computer forensics, evidence is not limited to on
location but distributed across multiple virtual and
physical locations such as social media and cloud
storages. Thus, professionals may require more
advanced and complex tools in computer
forensics analysis process to adopt to new cyber
threat trends [19].
Privacy-preserving investigations
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Today, individuals bring into Internet several
features of their lives, mainly over online social
media sites and social networks. Regrettably,
gathering data to rebuild and locate an attack can
seriously interrupt privacy of the users [19].
K. CONCLUSION
Computer forensics can be recognized as one of
the dedicated method of computer media
investigation to discover and evaluate existing,
erased, unseen or hidden facts or evidence that
can be useful during a legal procedure. Since
digital technologies have turned out to be a
mainstream in modern society, the necessity for a
knowledge that can lead with the advanced
technology has raised a concern for the judicial as
well as for the legal system. The effort of this
report found the formation of a governance
agenda to develop a strategy, performing and
designing of a strong legislation, protocols,
policies and standards for a better regulatory
environment, expand the skilled cyber security
workforce and professionalism, strong association
among public and private sector, increasing
awareness and allowing people against computer
threats and lastly to improve partnerships to form
a strong cyber security environment. The report
can be concluded by stating that although the
methods are innovative and benefit in dealing
with computer crimes, nonetheless with the fast
development of technology, the computer
forensics still require much research and
development in adopting to new tools and
mechanisms.
REFERENCE
1. S.L. Garfinkel, “Digital forensics research:
The next 10 years”, digital
investigation, vol. 7, 2010, pp.S64-S73.
2. A.C. Popescu and H. Farid, “Statistical
tools for digital forensics” in international
workshop on information hiding, Springer,
Berlin, Heidelberg, 2004, pp. 128-147.
3. E. Casey, Digital evidence and computer
crime: Forensic science, computers, and
the internet. Academic press, 2011.
4. The Open University, Digital forensics,
2019. [Online].
Available: https://www.open.edu/openlear
n/science-maths-technology/digital-
forensics/content-section-4.3 [Accessed:
December. 30, 2018].
5. M. Fernando, Alarming increase in SL
Cyber Crime, 2019. [Online].
Available: www.sundayobserver.lk/2018/0
7/22/news-features/alarming-increase-sl-
cyber-crime [Accessed: December. 29,
2018].
6. M.T. Britz, Computer Forensics and Cyber
Crime: An Introduction, 2nd ed, Pearson
Education India, 2009.
8
features of their lives, mainly over online social
media sites and social networks. Regrettably,
gathering data to rebuild and locate an attack can
seriously interrupt privacy of the users [19].
K. CONCLUSION
Computer forensics can be recognized as one of
the dedicated method of computer media
investigation to discover and evaluate existing,
erased, unseen or hidden facts or evidence that
can be useful during a legal procedure. Since
digital technologies have turned out to be a
mainstream in modern society, the necessity for a
knowledge that can lead with the advanced
technology has raised a concern for the judicial as
well as for the legal system. The effort of this
report found the formation of a governance
agenda to develop a strategy, performing and
designing of a strong legislation, protocols,
policies and standards for a better regulatory
environment, expand the skilled cyber security
workforce and professionalism, strong association
among public and private sector, increasing
awareness and allowing people against computer
threats and lastly to improve partnerships to form
a strong cyber security environment. The report
can be concluded by stating that although the
methods are innovative and benefit in dealing
with computer crimes, nonetheless with the fast
development of technology, the computer
forensics still require much research and
development in adopting to new tools and
mechanisms.
REFERENCE
1. S.L. Garfinkel, “Digital forensics research:
The next 10 years”, digital
investigation, vol. 7, 2010, pp.S64-S73.
2. A.C. Popescu and H. Farid, “Statistical
tools for digital forensics” in international
workshop on information hiding, Springer,
Berlin, Heidelberg, 2004, pp. 128-147.
3. E. Casey, Digital evidence and computer
crime: Forensic science, computers, and
the internet. Academic press, 2011.
4. The Open University, Digital forensics,
2019. [Online].
Available: https://www.open.edu/openlear
n/science-maths-technology/digital-
forensics/content-section-4.3 [Accessed:
December. 30, 2018].
5. M. Fernando, Alarming increase in SL
Cyber Crime, 2019. [Online].
Available: www.sundayobserver.lk/2018/0
7/22/news-features/alarming-increase-sl-
cyber-crime [Accessed: December. 29,
2018].
6. M.T. Britz, Computer Forensics and Cyber
Crime: An Introduction, 2nd ed, Pearson
Education India, 2009.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7. B. Nelson, A. Phillips and C. Steuart,
Guide to computer forensics and
investigations. Cengage Learning, 2014.
8. D. Bennett, “The challenges facing
computer forensics investigators in
obtaining information from mobile devices
for use in criminal
investigations”, Information Security
Journal: A Global Perspective, vol. 21(3),
2012, pp.159-168.
9. UCSC, Centre for Digital Forensics, 2019.
[Online].
Available: https://ucsc.cmb.ac.lk/cdf/
[Accessed: December. 31, 2018].
10. R. A. Gandhi, A. Sharma, W. Mahoney, P.
A. Laplante, Dimensions of Cyber-
Attacks: Cultural, Social, Economic, and
Political, 2011. [Online]. Available:
https://www.researchgate.net/publication/2
24223630_Dimensions_of_Cyber-
Attacks_Cultural_Social_Economic_and_
Political [Accessed: December. 30, 2018]
11. D. G. Rajesh and M. Punithavalli, “A
Study on the Existing Computer Aided
Crime Analysis Tools to Handle Indian
State of Affairs”, IJCSI International
Journal of Computer Science Issues, Vol.
9, Issue 2, No 3, 2012. [Online].
Available:
https://www.researchgate.net/publication/2
67427460_A_Study_on_the_Existing_Co
mputer_Aided_Crime_Analysis_Tools_to
_Handle_Indian_State_of_Affairs
[Accessed: January 1, 2019].
12. Legalcareerpath, What is Cyber law?,
2019 http://legalcareerpath.com/what-is-
cyber-law/
13. S. Surfaro, Cyber Laws and Trends: How
the Internet Just Became a Crime Scene,
2018
https://www.securityindustry.org/2018/04/
30/cyber-laws-trends-internet-just-
became-crime-scene/
14. S. D. B. Abeyaratne, Legal recognition of
electronic transactions 2011. [Online].
Available: http://archives.dailynews.lk/20
11/03/22/bus24.asp
15. J. Lewis and S. Baker, “The economic
impact of cybercrime and cyber
espionage”, McAfee, 2013.
16. D.R. Insua, A.C. Vieira and K. Musaraj,
“Some Risk Analysis Problems in Cyber
Insurance Economics”, Estudios de
economía aplicada, vol. 36(1), 2018,
pp.181-194
17. J. Lewis, Economic Impact of
Cybercrime-No Slowing Down. Santa
Clara: McAfee, 2018.
9
Guide to computer forensics and
investigations. Cengage Learning, 2014.
8. D. Bennett, “The challenges facing
computer forensics investigators in
obtaining information from mobile devices
for use in criminal
investigations”, Information Security
Journal: A Global Perspective, vol. 21(3),
2012, pp.159-168.
9. UCSC, Centre for Digital Forensics, 2019.
[Online].
Available: https://ucsc.cmb.ac.lk/cdf/
[Accessed: December. 31, 2018].
10. R. A. Gandhi, A. Sharma, W. Mahoney, P.
A. Laplante, Dimensions of Cyber-
Attacks: Cultural, Social, Economic, and
Political, 2011. [Online]. Available:
https://www.researchgate.net/publication/2
24223630_Dimensions_of_Cyber-
Attacks_Cultural_Social_Economic_and_
Political [Accessed: December. 30, 2018]
11. D. G. Rajesh and M. Punithavalli, “A
Study on the Existing Computer Aided
Crime Analysis Tools to Handle Indian
State of Affairs”, IJCSI International
Journal of Computer Science Issues, Vol.
9, Issue 2, No 3, 2012. [Online].
Available:
https://www.researchgate.net/publication/2
67427460_A_Study_on_the_Existing_Co
mputer_Aided_Crime_Analysis_Tools_to
_Handle_Indian_State_of_Affairs
[Accessed: January 1, 2019].
12. Legalcareerpath, What is Cyber law?,
2019 http://legalcareerpath.com/what-is-
cyber-law/
13. S. Surfaro, Cyber Laws and Trends: How
the Internet Just Became a Crime Scene,
2018
https://www.securityindustry.org/2018/04/
30/cyber-laws-trends-internet-just-
became-crime-scene/
14. S. D. B. Abeyaratne, Legal recognition of
electronic transactions 2011. [Online].
Available: http://archives.dailynews.lk/20
11/03/22/bus24.asp
15. J. Lewis and S. Baker, “The economic
impact of cybercrime and cyber
espionage”, McAfee, 2013.
16. D.R. Insua, A.C. Vieira and K. Musaraj,
“Some Risk Analysis Problems in Cyber
Insurance Economics”, Estudios de
economía aplicada, vol. 36(1), 2018,
pp.181-194
17. J. Lewis, Economic Impact of
Cybercrime-No Slowing Down. Santa
Clara: McAfee, 2018.
9
18. Liberty International Underwriters, Cyber:
The Overlooked Environmental Threat,
2016. [Online]. Available:
http://riskandinsurance.com/cyber-
overlooked-environmental-threat/
[Accessed: December. 31, 2018].
19. S. Burgess, The Future of Computer
Forensics, 2015. [Online].
Available: https://burgessforensics.com/th
e-future-of-computer-forensics/
[Accessed: December. 31, 2018].
10
The Overlooked Environmental Threat,
2016. [Online]. Available:
http://riskandinsurance.com/cyber-
overlooked-environmental-threat/
[Accessed: December. 31, 2018].
19. S. Burgess, The Future of Computer
Forensics, 2015. [Online].
Available: https://burgessforensics.com/th
e-future-of-computer-forensics/
[Accessed: December. 31, 2018].
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

