Coursework 1: Computer Forensics and Security Fundamentals Analysis
VerifiedAdded on 2023/05/28
|8
|1546
|185
Homework Assignment
AI Summary
This coursework delves into the core concepts of computer forensics and security fundamentals, examining topics such as system audits and the Computer Misuse Act 1990. It explores port scanning techniques and the TCP handshake, providing insights into how these methods are used. The assignment includes a vulnerability assessment of a Metasploitable virtual machine, identifying common vulnerabilities and potential exploits. Furthermore, it discusses mitigation strategies, including the use of firewalls, IP tables, and additional approaches to enhance system security. The coursework aims to provide a comprehensive understanding of these critical aspects of cybersecurity, offering practical solutions and recommendations to safeguard systems against potential threats. It also includes a bibliography of the sources that were used in the document.

Computer Forensics and Security
Fundamentals
Coursework 1
YOUNES AHMED, 18061675
14/12/2018
1
Fundamentals
Coursework 1
YOUNES AHMED, 18061675
14/12/2018
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
System Audit.........................................................................................................................................3
Computer Misuse Act 1990...............................................................................................................3
Port Scanning & the TCP Handshake.................................................................................................3
Vulnerability Assessment of Metasploitable Virtual Machine...........................................................4
Common Vulnerabilities and Exploits Identified................................................................................4
Mitigation..............................................................................................................................................5
Firewalls Background.........................................................................................................................5
IP Tables Background and Deployment.............................................................................................5
Additional Mitigation Approaches.....................................................................................................7
Bibliography.......................................................................................................................................8
2
System Audit.........................................................................................................................................3
Computer Misuse Act 1990...............................................................................................................3
Port Scanning & the TCP Handshake.................................................................................................3
Vulnerability Assessment of Metasploitable Virtual Machine...........................................................4
Common Vulnerabilities and Exploits Identified................................................................................4
Mitigation..............................................................................................................................................5
Firewalls Background.........................................................................................................................5
IP Tables Background and Deployment.............................................................................................5
Additional Mitigation Approaches.....................................................................................................7
Bibliography.......................................................................................................................................8
2
System Audit
Computer Misuse Act 1990
Computer Misuse Act 1990 is a act for protecting the computer material from hacker and virus
writer. Any unauthorized user can not login the system. Therefore, the login screen carry out a
message saying that the access is limited to authorized user only. This thing cannot prevent a hacker
to access the data but the hackers will not be claim ignorance of committing offence (Yan and Yu
2015). The Act says you need permission to use a computer system. Someone performing security
testing on a system that is not theirs needs to obtain the permission of the system’s owner first, or
they risk violating the CMA. This is a fact regardless of whether or not the system to be tested is a
physical server or a virtual server rented from the cloud.
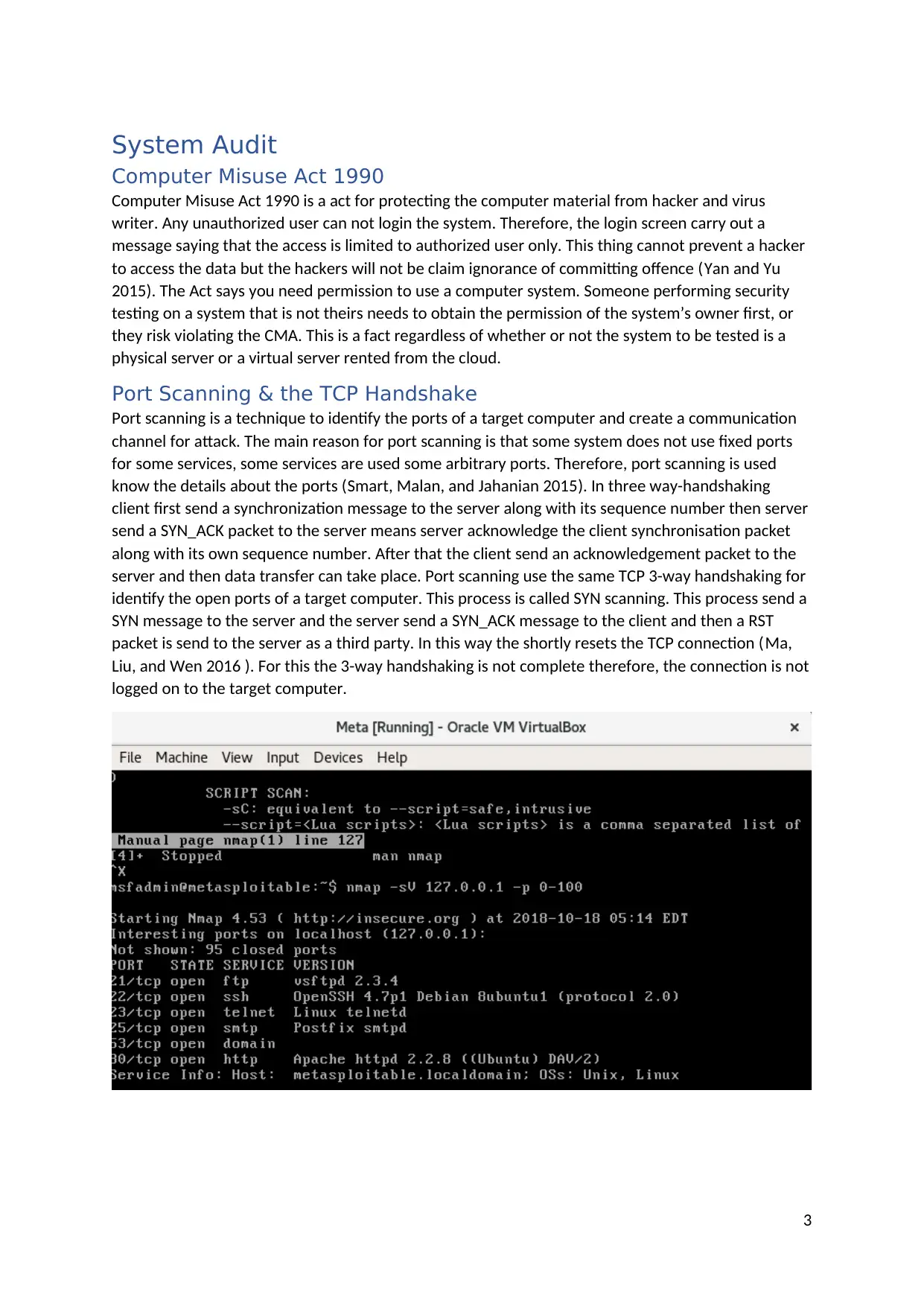
Port Scanning & the TCP Handshake
Port scanning is a technique to identify the ports of a target computer and create a communication
channel for attack. The main reason for port scanning is that some system does not use fixed ports
for some services, some services are used some arbitrary ports. Therefore, port scanning is used
know the details about the ports (Smart, Malan, and Jahanian 2015). In three way-handshaking
client first send a synchronization message to the server along with its sequence number then server
send a SYN_ACK packet to the server means server acknowledge the client synchronisation packet
along with its own sequence number. After that the client send an acknowledgement packet to the
server and then data transfer can take place. Port scanning use the same TCP 3-way handshaking for
identify the open ports of a target computer. This process is called SYN scanning. This process send a
SYN message to the server and the server send a SYN_ACK message to the client and then a RST
packet is send to the server as a third party. In this way the shortly resets the TCP connection (Ma,
Liu, and Wen 2016 ). For this the 3-way handshaking is not complete therefore, the connection is not
logged on to the target computer.
3
Computer Misuse Act 1990
Computer Misuse Act 1990 is a act for protecting the computer material from hacker and virus
writer. Any unauthorized user can not login the system. Therefore, the login screen carry out a
message saying that the access is limited to authorized user only. This thing cannot prevent a hacker
to access the data but the hackers will not be claim ignorance of committing offence (Yan and Yu
2015). The Act says you need permission to use a computer system. Someone performing security
testing on a system that is not theirs needs to obtain the permission of the system’s owner first, or
they risk violating the CMA. This is a fact regardless of whether or not the system to be tested is a
physical server or a virtual server rented from the cloud.
Port Scanning & the TCP Handshake
Port scanning is a technique to identify the ports of a target computer and create a communication
channel for attack. The main reason for port scanning is that some system does not use fixed ports
for some services, some services are used some arbitrary ports. Therefore, port scanning is used
know the details about the ports (Smart, Malan, and Jahanian 2015). In three way-handshaking
client first send a synchronization message to the server along with its sequence number then server
send a SYN_ACK packet to the server means server acknowledge the client synchronisation packet
along with its own sequence number. After that the client send an acknowledgement packet to the
server and then data transfer can take place. Port scanning use the same TCP 3-way handshaking for
identify the open ports of a target computer. This process is called SYN scanning. This process send a
SYN message to the server and the server send a SYN_ACK message to the client and then a RST
packet is send to the server as a third party. In this way the shortly resets the TCP connection (Ma,
Liu, and Wen 2016 ). For this the 3-way handshaking is not complete therefore, the connection is not
logged on to the target computer.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
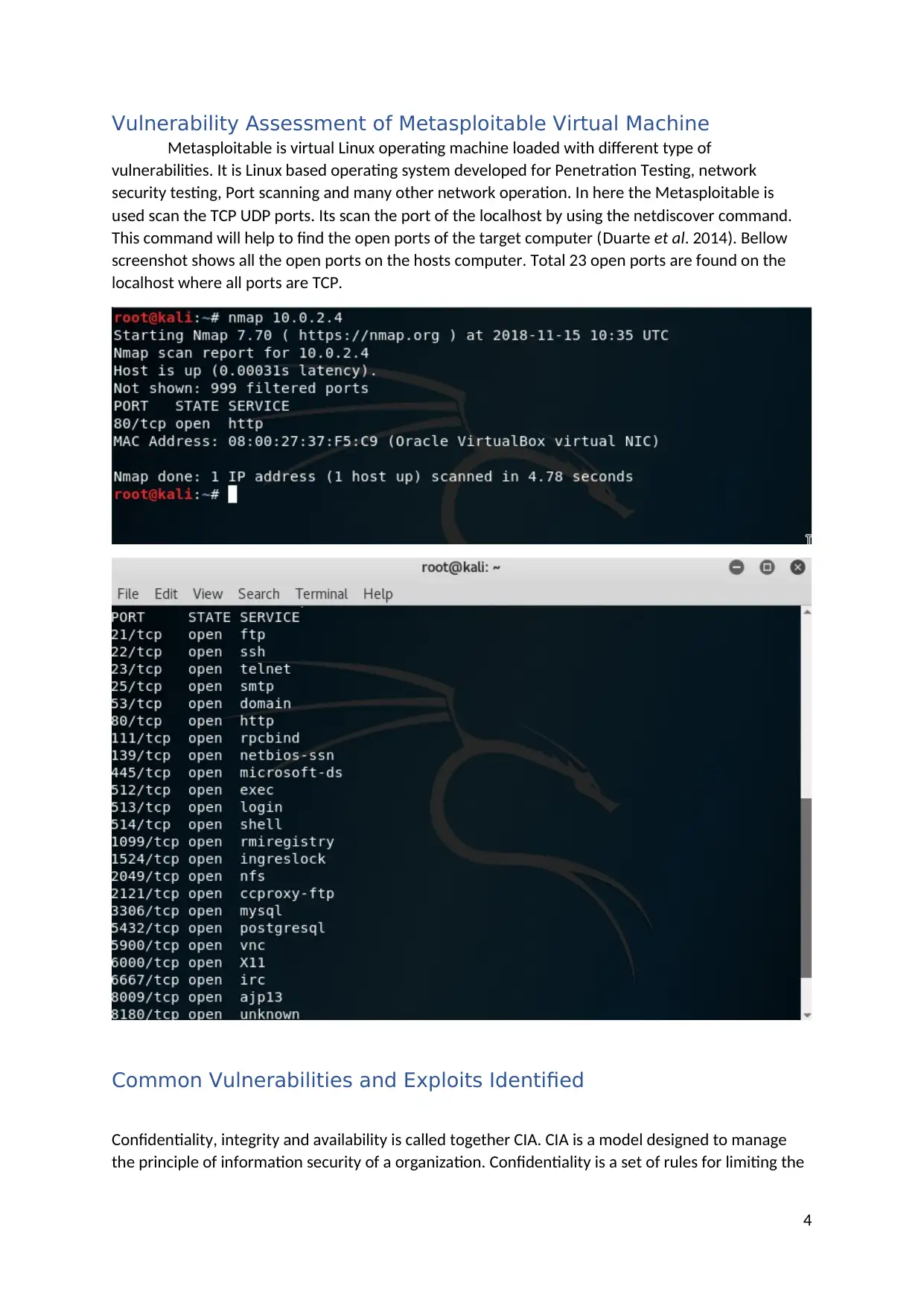
Vulnerability Assessment of Metasploitable Virtual Machine
Metasploitable is virtual Linux operating machine loaded with different type of
vulnerabilities. It is Linux based operating system developed for Penetration Testing, network
security testing, Port scanning and many other network operation. In here the Metasploitable is
used scan the TCP UDP ports. Its scan the port of the localhost by using the netdiscover command.
This command will help to find the open ports of the target computer (Duarte et al. 2014). Bellow
screenshot shows all the open ports on the hosts computer. Total 23 open ports are found on the
localhost where all ports are TCP.
Common Vulnerabilities and Exploits Identified
Confidentiality, integrity and availability is called together CIA. CIA is a model designed to manage
the principle of information security of a organization. Confidentiality is a set of rules for limiting the
4
Metasploitable is virtual Linux operating machine loaded with different type of
vulnerabilities. It is Linux based operating system developed for Penetration Testing, network
security testing, Port scanning and many other network operation. In here the Metasploitable is
used scan the TCP UDP ports. Its scan the port of the localhost by using the netdiscover command.
This command will help to find the open ports of the target computer (Duarte et al. 2014). Bellow
screenshot shows all the open ports on the hosts computer. Total 23 open ports are found on the
localhost where all ports are TCP.
Common Vulnerabilities and Exploits Identified
Confidentiality, integrity and availability is called together CIA. CIA is a model designed to manage
the principle of information security of a organization. Confidentiality is a set of rules for limiting the
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

access. Integrity is use as a assurance of the information that is trustworthy. And the availability is a
reliable access to the information for the authorized person. Vulnerability effect all these CIA model
of a organization. The Different type of vulnerability is present. DOS (denial of service attack) and
Man in the middle attack is the most common vulnerable attack which is perform in most of the
organization. DOS attack destroy all the valuable information of a organization. Which break the
confidentiality and availability. This attack stop access to the information which is a big loss for any
business. Man in the middle attack is another most common attack on the network. This attack will
gain access to any secure information which break the CIA model.
Mitigation
Use the subheadings in this section to structure your work. You may remove this text.
Firewalls Background
Firewall is a network security system which is used to prevent the un-authorized access to the
system. Firewall can be two type one is software and another one is hardware. Firewall is mainly
used on the network for securing and prevent the un-authorized access from the internet user. Two
type of firewall is mainly used on the network one is proxy filter firewall and another one is packet
filter firewall (Nagasundaram and Aissi 2017). In packet filter firewall mainly all packets are filter. In
this type of filtering the mainly ports are used to provide access. A pre-defined rules are set in this
type of firewall. In this rule a access list is pre-defined for gain the access to the system. In proxy
filter firewall, a proxy server is used to bypass the access. Mainly the proxy server check the
incoming packets and its identity then it will grant access to the system otherwise it will drop the
packets.
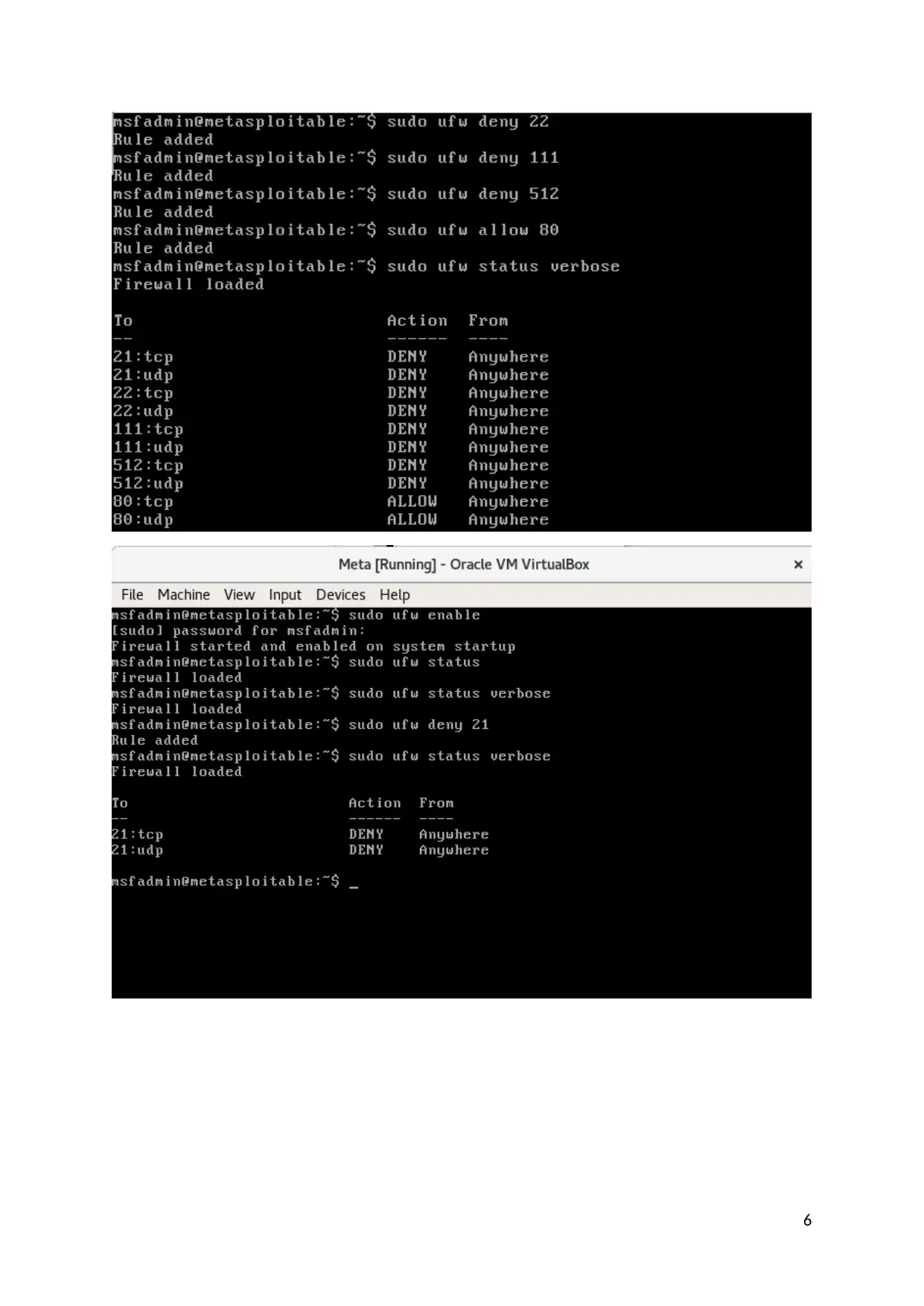
IP Tables Background and Deployment
Ip table is table structure which is use in firewall for defining the firewall rules and command. Mainly
IP table is used to manage packet filtering rules. Ip table is mainly used on Linux operating system. A
Ip table contain multiple table and table contain rules. Mainly, port number, destination address and
permission is given in the rules. In here web server use port 80 for HTTP. Therefore, this port is open.
And other vulnerable port are blocked. Bellow screen capture provide the IP table rules and other
details. In the system UFW command is used for defining the rule.
5
reliable access to the information for the authorized person. Vulnerability effect all these CIA model
of a organization. The Different type of vulnerability is present. DOS (denial of service attack) and
Man in the middle attack is the most common vulnerable attack which is perform in most of the
organization. DOS attack destroy all the valuable information of a organization. Which break the
confidentiality and availability. This attack stop access to the information which is a big loss for any
business. Man in the middle attack is another most common attack on the network. This attack will
gain access to any secure information which break the CIA model.
Mitigation
Use the subheadings in this section to structure your work. You may remove this text.
Firewalls Background
Firewall is a network security system which is used to prevent the un-authorized access to the
system. Firewall can be two type one is software and another one is hardware. Firewall is mainly
used on the network for securing and prevent the un-authorized access from the internet user. Two
type of firewall is mainly used on the network one is proxy filter firewall and another one is packet
filter firewall (Nagasundaram and Aissi 2017). In packet filter firewall mainly all packets are filter. In
this type of filtering the mainly ports are used to provide access. A pre-defined rules are set in this
type of firewall. In this rule a access list is pre-defined for gain the access to the system. In proxy
filter firewall, a proxy server is used to bypass the access. Mainly the proxy server check the
incoming packets and its identity then it will grant access to the system otherwise it will drop the
packets.
IP Tables Background and Deployment
Ip table is table structure which is use in firewall for defining the firewall rules and command. Mainly
IP table is used to manage packet filtering rules. Ip table is mainly used on Linux operating system. A
Ip table contain multiple table and table contain rules. Mainly, port number, destination address and
permission is given in the rules. In here web server use port 80 for HTTP. Therefore, this port is open.
And other vulnerable port are blocked. Bellow screen capture provide the IP table rules and other
details. In the system UFW command is used for defining the rule.
5
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
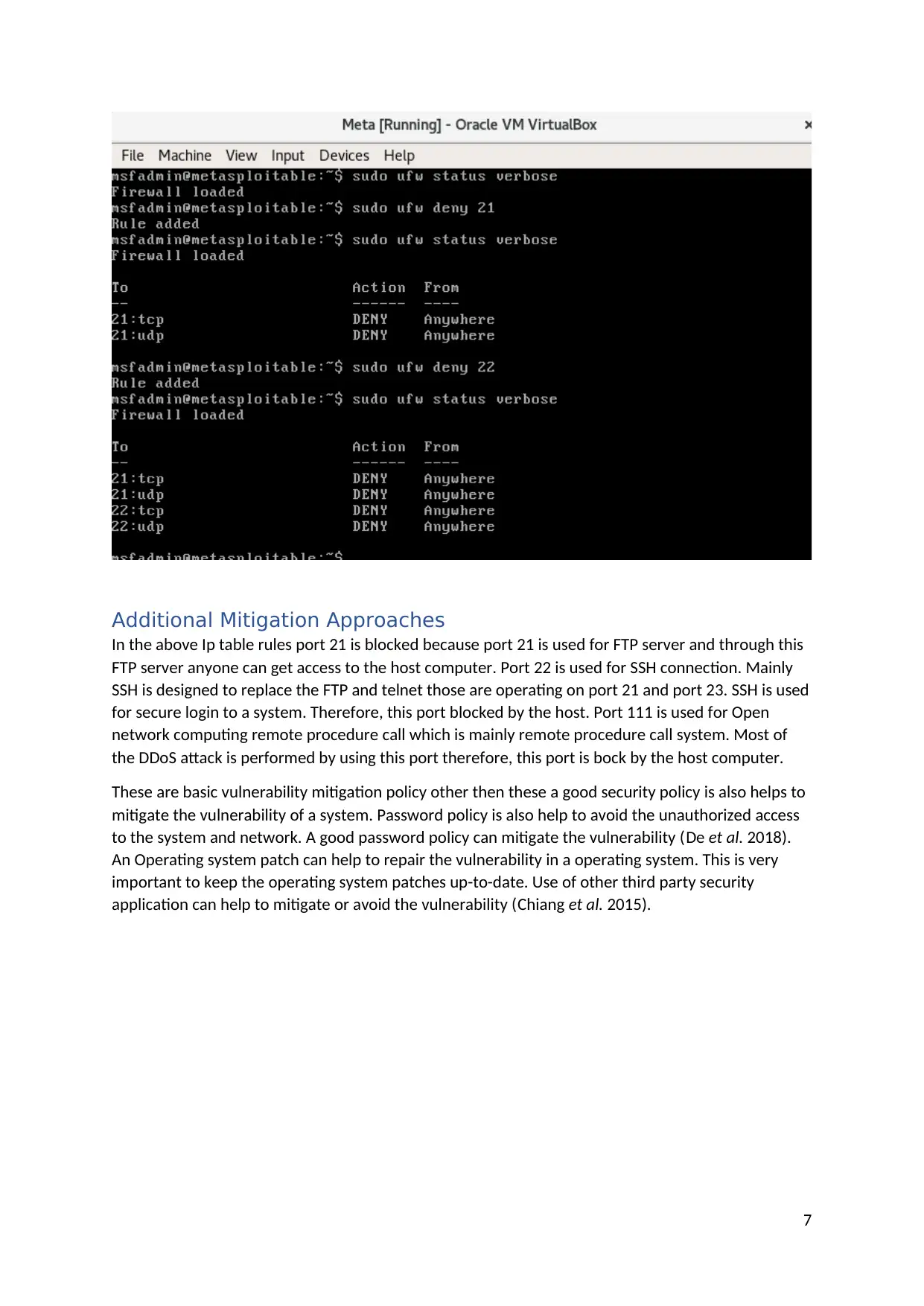
Additional Mitigation Approaches
In the above Ip table rules port 21 is blocked because port 21 is used for FTP server and through this
FTP server anyone can get access to the host computer. Port 22 is used for SSH connection. Mainly
SSH is designed to replace the FTP and telnet those are operating on port 21 and port 23. SSH is used
for secure login to a system. Therefore, this port blocked by the host. Port 111 is used for Open
network computing remote procedure call which is mainly remote procedure call system. Most of
the DDoS attack is performed by using this port therefore, this port is bock by the host computer.
These are basic vulnerability mitigation policy other then these a good security policy is also helps to
mitigate the vulnerability of a system. Password policy is also help to avoid the unauthorized access
to the system and network. A good password policy can mitigate the vulnerability (De et al. 2018).
An Operating system patch can help to repair the vulnerability in a operating system. This is very
important to keep the operating system patches up-to-date. Use of other third party security
application can help to mitigate or avoid the vulnerability (Chiang et al. 2015).
7
In the above Ip table rules port 21 is blocked because port 21 is used for FTP server and through this
FTP server anyone can get access to the host computer. Port 22 is used for SSH connection. Mainly
SSH is designed to replace the FTP and telnet those are operating on port 21 and port 23. SSH is used
for secure login to a system. Therefore, this port blocked by the host. Port 111 is used for Open
network computing remote procedure call which is mainly remote procedure call system. Most of
the DDoS attack is performed by using this port therefore, this port is bock by the host computer.
These are basic vulnerability mitigation policy other then these a good security policy is also helps to
mitigate the vulnerability of a system. Password policy is also help to avoid the unauthorized access
to the system and network. A good password policy can mitigate the vulnerability (De et al. 2018).
An Operating system patch can help to repair the vulnerability in a operating system. This is very
important to keep the operating system patches up-to-date. Use of other third party security
application can help to mitigate or avoid the vulnerability (Chiang et al. 2015).
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Bibliography
Chiang, R.C., Rajasekaran, S., Zhang, N. and Huang, H.H., 2015. Swiper: Exploiting virtual machine
vulnerability in third-party clouds with competition for i/o resources. IEEE Transactions on Parallel
and Distributed Systems, 26(6), pp.1732-1742.
De Vivo, M., Carrasco, E., Isern, G. and de Vivo, G.O., 2018. A review of port scanning
techniques. ACM SIGCOMM Computer Communication Review, 29(2), pp.41-48.
Duarte, F.S., Sikansi, F., Fatore, F.M., Fadel, S.G. and Paulovich, F.V., 2014. Nmap: A novel
neighborhood preservation space-filling algorithm. IEEE Transactions on Visualization & Computer
Graphics, (12), pp.2063-2071.
Ma, Q.M., Liu, S.Y. and Wen, X.J., 2016. TCP Three-Way Handshake Protocol based on Quantum
Entanglement. Journal of Computers, 27(3), pp.33-40.
Nagasundaram, S. and Aissi, S., Visa International Service Association, 2017. Privacy firewall. U.S.
Patent 9,665,722.
Smart, M., Malan, G.R. and Jahanian, F., 2015, August. Defeating TCP/IP Stack Fingerprinting.
In Usenix Security Symposium.
Yan, Q. and Yu, F.R., 2015. Distributed denial of service attacks in software-defined networking with
cloud computing. IEEE Communications Magazine, 53(4), pp.52-59.
8
Chiang, R.C., Rajasekaran, S., Zhang, N. and Huang, H.H., 2015. Swiper: Exploiting virtual machine
vulnerability in third-party clouds with competition for i/o resources. IEEE Transactions on Parallel
and Distributed Systems, 26(6), pp.1732-1742.
De Vivo, M., Carrasco, E., Isern, G. and de Vivo, G.O., 2018. A review of port scanning
techniques. ACM SIGCOMM Computer Communication Review, 29(2), pp.41-48.
Duarte, F.S., Sikansi, F., Fatore, F.M., Fadel, S.G. and Paulovich, F.V., 2014. Nmap: A novel
neighborhood preservation space-filling algorithm. IEEE Transactions on Visualization & Computer
Graphics, (12), pp.2063-2071.
Ma, Q.M., Liu, S.Y. and Wen, X.J., 2016. TCP Three-Way Handshake Protocol based on Quantum
Entanglement. Journal of Computers, 27(3), pp.33-40.
Nagasundaram, S. and Aissi, S., Visa International Service Association, 2017. Privacy firewall. U.S.
Patent 9,665,722.
Smart, M., Malan, G.R. and Jahanian, F., 2015, August. Defeating TCP/IP Stack Fingerprinting.
In Usenix Security Symposium.
Yan, Q. and Yu, F.R., 2015. Distributed denial of service attacks in software-defined networking with
cloud computing. IEEE Communications Magazine, 53(4), pp.52-59.
8
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





