Introduction to Computer Hackers: Types, Motives, Access, and Methods
VerifiedAdded on 2019/09/23
|8
|2699
|294
Report
AI Summary
This report provides a detailed analysis of computer hackers, categorizing them into black hat, white hat, and grey hat hackers, and explaining their respective roles and intentions. It explores the various motives behind hacking, including financial gain, reputation enhancement, and aiding companies. The report further examines the methods hackers use to gain access to computer systems, such as phishing emails, malicious website links, social networking pages, and malware. It also delves into password cracking techniques, including dictionary attacks, brute force attacks, rainbow table attacks, phishing, and malware. Finally, the report discusses the legal and illegal aspects of hacking, providing a comprehensive overview of the subject.

Running head: Blog Writing
BLOG WRITING
BLOG WRITING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: Blog Writing
COMPUTER HACKERS
July, 29th 2019
INTRODUCTION TO THE COMPUTER HACKERS
The developments in the information and communication technology have provided ease
of performing business to the organization. However, developments in the given sector have led
to developing different other types of issues. Hence, one of the common issues that is associated
with cybercrime is hacking. In accordance with the given context, it can be said that hacking is
being regarded as the activity of using computers with an aim to perform different types of
crimes. The individual who used to perform such crimes is called by the name of hackers.
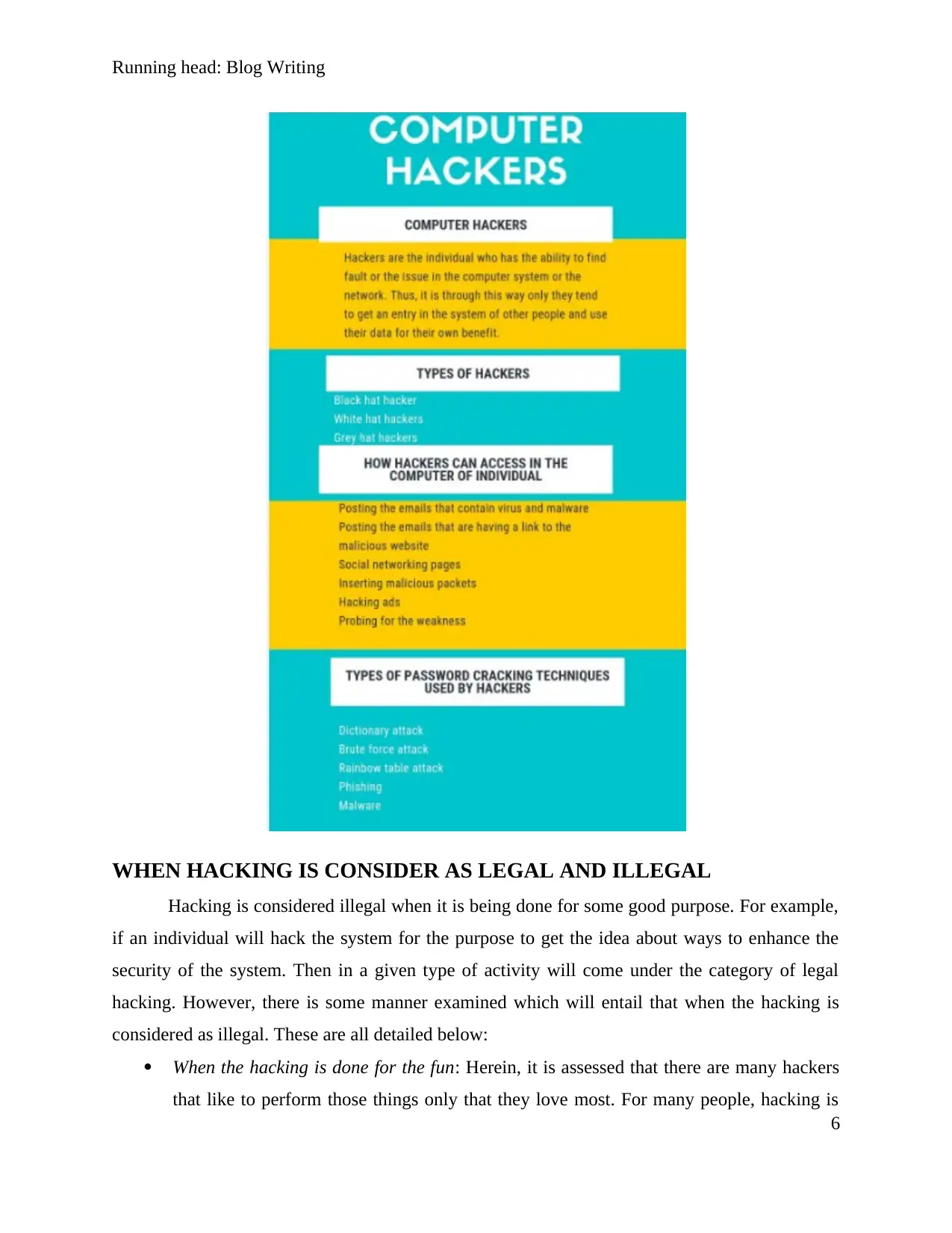
Thus, it can be said that hackers are the individual who has the ability to find fault or the
issue in the computer system or the network. Thus, it is through this way only they tend to get an
entry in the system of other people and use their data for their own benefit. In this study, detail
analysis will be carried out on computer hackers.
TYPES OF HACKERS
At first, the discussion will be carried out on the types of hackers. Herein, it can be
depicted that there are basically three main types of hackers and the details about them are given
below:
Black hat hacker
The very first type of hacker is being called by the name of a black hat hacker. It is being
regarded as the type of hackers who tends to hack the computers for malicious intent. Such types
of individual are being considered as the bad guy. Herein, it can be said that the respective type
of individual uses his hacking skill with an aim to steal the data or the money. On the other hand,
such type of hackers loves their work very much and they like to come in the news because of
their bad habit. For example, black hat hackers sometimes change the font color of the
company’s website. In addition to this, they also try to break the computer system and will try to
get the credit card information of the individual in an effectual manner. Hence, respective
hackers are being considered as very much dangerous for the company. They also carried out
their efforts outside the company’s laws and regulations.
1
COMPUTER HACKERS
July, 29th 2019
INTRODUCTION TO THE COMPUTER HACKERS
The developments in the information and communication technology have provided ease
of performing business to the organization. However, developments in the given sector have led
to developing different other types of issues. Hence, one of the common issues that is associated
with cybercrime is hacking. In accordance with the given context, it can be said that hacking is
being regarded as the activity of using computers with an aim to perform different types of
crimes. The individual who used to perform such crimes is called by the name of hackers.
Thus, it can be said that hackers are the individual who has the ability to find fault or the
issue in the computer system or the network. Thus, it is through this way only they tend to get an
entry in the system of other people and use their data for their own benefit. In this study, detail
analysis will be carried out on computer hackers.
TYPES OF HACKERS
At first, the discussion will be carried out on the types of hackers. Herein, it can be
depicted that there are basically three main types of hackers and the details about them are given
below:
Black hat hacker
The very first type of hacker is being called by the name of a black hat hacker. It is being
regarded as the type of hackers who tends to hack the computers for malicious intent. Such types
of individual are being considered as the bad guy. Herein, it can be said that the respective type
of individual uses his hacking skill with an aim to steal the data or the money. On the other hand,
such type of hackers loves their work very much and they like to come in the news because of
their bad habit. For example, black hat hackers sometimes change the font color of the
company’s website. In addition to this, they also try to break the computer system and will try to
get the credit card information of the individual in an effectual manner. Hence, respective
hackers are being considered as very much dangerous for the company. They also carried out
their efforts outside the company’s laws and regulations.
1

Running head: Blog Writing
White hat hackers
The White hat hackers are basically the computer system specialist who basically breaks
the protected system and the network in order to test the as well as assess their security. They use
their skills with an aim to see improve the security of the system. In accordance with the given
context, they basically get the data regarding different vulnerabilities that could pose harm to the
computer system and could break the security of the network. Hence, it is very right to say that
they are being proved as a very helpful individual for the companies. This is due to the reason
that they basically give a description of the problems that could harm the system of the firm.
Hence, it is through this way only firms can find out some protective measures with an aim to
protect their data from the ineffective individuals or the black hat hackers. Further, it can also be
said that they are also synonyms with the ethical hackers and thus they tend to play a vital role in
introducing different strategies that could help in removing all the malicious attack related
problem of the company in an effectual manner.
Grey hat hackers
The last type of hacker is called by the name of grey hat hackers. It is also referred to as
the computer security expert who sometimes violates the ethical standard as well as law, but it
does not possess any kind of malicious intent just like the black hat hackers does. Additionally, it
can also be said that grey hat hackers will basically engage itself in the type of practices which
seems less than above any kind of board. However, it often performs its function for the common
good in an effectual manner. In other words, it can also be depicted that grey hat hackers
basically represent the middle ground between white and black hat hackers. The grey hat hackers
also play a significant role in the security environment. The grey hat hackers will explore the
vulnerability in the security and thus it will tend to give information about the same to the public
and thus make them aware of the existence of vulnerabilities. Here, it will also give them
guidance about the actions that they can perform with an aim to protect themselves from any
kind of cyber attacks from the side of black hat hackers.
MOTIVE BEHIND HACKING
Till now the major discussion is being carried out about the types of hackers and the
meaning of the same. Now the discussion is being put forward towards the main motives behind
2
White hat hackers
The White hat hackers are basically the computer system specialist who basically breaks
the protected system and the network in order to test the as well as assess their security. They use
their skills with an aim to see improve the security of the system. In accordance with the given
context, they basically get the data regarding different vulnerabilities that could pose harm to the
computer system and could break the security of the network. Hence, it is very right to say that
they are being proved as a very helpful individual for the companies. This is due to the reason
that they basically give a description of the problems that could harm the system of the firm.
Hence, it is through this way only firms can find out some protective measures with an aim to
protect their data from the ineffective individuals or the black hat hackers. Further, it can also be
said that they are also synonyms with the ethical hackers and thus they tend to play a vital role in
introducing different strategies that could help in removing all the malicious attack related
problem of the company in an effectual manner.
Grey hat hackers
The last type of hacker is called by the name of grey hat hackers. It is also referred to as
the computer security expert who sometimes violates the ethical standard as well as law, but it
does not possess any kind of malicious intent just like the black hat hackers does. Additionally, it
can also be said that grey hat hackers will basically engage itself in the type of practices which
seems less than above any kind of board. However, it often performs its function for the common
good in an effectual manner. In other words, it can also be depicted that grey hat hackers
basically represent the middle ground between white and black hat hackers. The grey hat hackers
also play a significant role in the security environment. The grey hat hackers will explore the
vulnerability in the security and thus it will tend to give information about the same to the public
and thus make them aware of the existence of vulnerabilities. Here, it will also give them
guidance about the actions that they can perform with an aim to protect themselves from any
kind of cyber attacks from the side of black hat hackers.
MOTIVE BEHIND HACKING
Till now the major discussion is being carried out about the types of hackers and the
meaning of the same. Now the discussion is being put forward towards the main motives behind
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: Blog Writing
the hacking. In accordance with the given context, there are different motives of hackers behind
hacking is examined. The details of the same are given in the below points:
The primary motive behind hacking is to get financial gains. In this context, the hackers
will lead to crack the computer system with an aim to get the credit details of the specific
person. Thus, it is through this way only they tend to perform different types of financial
fraud in an effectual manner.
The second motive behind hacking is to increase the reputation of the hackers in the
hacking subculture. Here, by performing hacking and individual will tends to prove itself
that it can perform a variety of tasks. Here, it is through this way only it will showcase its
hacking-related skills to other individuals in an effectual manner.
The third motive behind hacking is to give assistance to the companies whose secret
information is being lost. Thus, with the help of hackers companies can track the
individual who has committed a respective type of work.
HOW HACKERS CAN ACCESS IN THE COMPUTER OF INDIVIDUAL
There are different ways examined which are being used by hackers in order to get access
in the computer system of the individual. These are all detailed below;
Posting the emails that contain virus and malware: It is being regarded as one of the most
popular methods for the purpose to spread the malware that is hidden in the attachment of
the email. Once an individual will open the attachment, then in this condition malicious
software automatically execute and will be downloaded in the computer system.
Posting the emails that are having a link to the malicious website: It is also being
considered as second most common ways that are being used by the hackers in order to
the hack the computer system of a company or the individual. In this context, the HTML
link which is being attached with email leads an individual to some fake website. Here,
trial and trick method is being used with an aim to get sensitive information about the
person. The information could be related to a person’s bank details and password etc. On
the other hand, many times these websites also attempt to install different virus and
malware in the recipient of the computer system.
Social networking pages: Yes, this is right hackers can also get access in the computer
system of the individual with the help of different social networking sites like Facebook.
3
the hacking. In accordance with the given context, there are different motives of hackers behind
hacking is examined. The details of the same are given in the below points:
The primary motive behind hacking is to get financial gains. In this context, the hackers
will lead to crack the computer system with an aim to get the credit details of the specific
person. Thus, it is through this way only they tend to perform different types of financial
fraud in an effectual manner.
The second motive behind hacking is to increase the reputation of the hackers in the
hacking subculture. Here, by performing hacking and individual will tends to prove itself
that it can perform a variety of tasks. Here, it is through this way only it will showcase its
hacking-related skills to other individuals in an effectual manner.
The third motive behind hacking is to give assistance to the companies whose secret
information is being lost. Thus, with the help of hackers companies can track the
individual who has committed a respective type of work.
HOW HACKERS CAN ACCESS IN THE COMPUTER OF INDIVIDUAL
There are different ways examined which are being used by hackers in order to get access
in the computer system of the individual. These are all detailed below;
Posting the emails that contain virus and malware: It is being regarded as one of the most
popular methods for the purpose to spread the malware that is hidden in the attachment of
the email. Once an individual will open the attachment, then in this condition malicious
software automatically execute and will be downloaded in the computer system.
Posting the emails that are having a link to the malicious website: It is also being
considered as second most common ways that are being used by the hackers in order to
the hack the computer system of a company or the individual. In this context, the HTML
link which is being attached with email leads an individual to some fake website. Here,
trial and trick method is being used with an aim to get sensitive information about the
person. The information could be related to a person’s bank details and password etc. On
the other hand, many times these websites also attempt to install different virus and
malware in the recipient of the computer system.
Social networking pages: Yes, this is right hackers can also get access in the computer
system of the individual with the help of different social networking sites like Facebook.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: Blog Writing
Twitter and Instagram etc. In this context, hackers will tend to prepare some fake website
and thus it will influence the individual to follow the malicious website and thus it is
through this way only it will get the personal information about the person in an effectual
manner.
Inserting malicious packets: The given thing basically relies on the access to the swathe
of the zombie computers with an aim to send the large quantities of data to many people.
The main aim here to identify the router and the firewall with the specific port to be open
and it is through this way only access to the computers can be gained behind the
firewalls.
Hacking ads: It can also be considered as one of a popular way which is being used by
hackers in order to get access to the computer system in an effectual manner. Herein, it
can be said that such type of things comes under the category of cybercrimes. In this
different ad that tends to possess malicious links are being posted on the legitimate
website. The given thing is performed either by purchasing the ad directing or by hacking
the ad account of some other individual.
Probing for the weakness: There are many situations in which hackers will tend to send
the mass emails in order to compromise the firewall or intrusion the prevention system
for the purpose to gain access to computer system behind the given defenses. It is
basically a type of number game in which millions of email goes out to identify
unpatched equipment.
TYPES OF PASSWORD CRACKING TECHNIQUES USED BY HACKERS
Now we will improve our knowledge about the password cracking techniques that are
being used by hackers. The given techniques will help in the process of fulfilling the aims and
objectives of the hackers in an effectual manner. Hence, significant details in relation to the same
are given below:
Dictionary attack: The given attack basically uses a simple file that contains words that
will be found in the dictionary. Thus, it is a straightforward name. Here, in the respective
attack, the attacker will basically use the kinds of words that are being used by many
individuals in their password. It is through this way only it cleverly groups the different
words together.
4
Twitter and Instagram etc. In this context, hackers will tend to prepare some fake website
and thus it will influence the individual to follow the malicious website and thus it is
through this way only it will get the personal information about the person in an effectual
manner.
Inserting malicious packets: The given thing basically relies on the access to the swathe
of the zombie computers with an aim to send the large quantities of data to many people.
The main aim here to identify the router and the firewall with the specific port to be open
and it is through this way only access to the computers can be gained behind the
firewalls.
Hacking ads: It can also be considered as one of a popular way which is being used by
hackers in order to get access to the computer system in an effectual manner. Herein, it
can be said that such type of things comes under the category of cybercrimes. In this
different ad that tends to possess malicious links are being posted on the legitimate
website. The given thing is performed either by purchasing the ad directing or by hacking
the ad account of some other individual.
Probing for the weakness: There are many situations in which hackers will tend to send
the mass emails in order to compromise the firewall or intrusion the prevention system
for the purpose to gain access to computer system behind the given defenses. It is
basically a type of number game in which millions of email goes out to identify
unpatched equipment.
TYPES OF PASSWORD CRACKING TECHNIQUES USED BY HACKERS
Now we will improve our knowledge about the password cracking techniques that are
being used by hackers. The given techniques will help in the process of fulfilling the aims and
objectives of the hackers in an effectual manner. Hence, significant details in relation to the same
are given below:
Dictionary attack: The given attack basically uses a simple file that contains words that
will be found in the dictionary. Thus, it is a straightforward name. Here, in the respective
attack, the attacker will basically use the kinds of words that are being used by many
individuals in their password. It is through this way only it cleverly groups the different
words together.
4

Running head: Blog Writing
Brute force attack: It is being regarded as another type of password cracking technique.
Just like the dictionary attack, it comes with the added bonus for the hackers. Here,
instead of simply using the words, in the brute force attack non-dictionary words by
being detected by following the alpha-numeric combination. On the other hand, it can
also be shorthand by throwing the additional computer related horsepower.
Rainbow table attack: In the respective type of password cracking technique, a hacker can
boil the rainbow table down in the list of the pre-computed hashes. Here, numerical
values are being used for the purpose to do encryption of the password. The respective
table will tend to possess hashes of all possible combinations of the password. On the
other hand, the rainbow table is very much attractive as it will help in reducing the time
that is being needed for the purpose to crack the password hashes. But, it is to be
evaluated that the rainbow table is huge and it also has the unwieldy things. Further, they
also require serious computing power to run.
Phishing: It is being regarded as another most significant way which is being used by
hackers in order to crack the password of the computer system. In this context, here an
email will lead an individual towards some faked logged in services which are being
formed by a hacker. Thus, it is the kind of trap which is being made by hackers in order
to get the password and other related details of the people. It is through this way only
hackers can perform different crimes such as stealing money from the account of
individuals and molding the data of company etc.
Malware: Another most effective password cracking technique is malware. Here, key
logger and screen scraper is being installed by malware which will make a record of each
and everything that we write and take the screenshot during the login process. The copy
of the same will be forwarded to the hacker central. Here, malware will basically look for
the existence of the web browser client password file. Overall, it can be said that these are
some major password cracking techniques which are being used by hackers to hack the
system.
5
Brute force attack: It is being regarded as another type of password cracking technique.
Just like the dictionary attack, it comes with the added bonus for the hackers. Here,
instead of simply using the words, in the brute force attack non-dictionary words by
being detected by following the alpha-numeric combination. On the other hand, it can
also be shorthand by throwing the additional computer related horsepower.
Rainbow table attack: In the respective type of password cracking technique, a hacker can
boil the rainbow table down in the list of the pre-computed hashes. Here, numerical
values are being used for the purpose to do encryption of the password. The respective
table will tend to possess hashes of all possible combinations of the password. On the
other hand, the rainbow table is very much attractive as it will help in reducing the time
that is being needed for the purpose to crack the password hashes. But, it is to be
evaluated that the rainbow table is huge and it also has the unwieldy things. Further, they
also require serious computing power to run.
Phishing: It is being regarded as another most significant way which is being used by
hackers in order to crack the password of the computer system. In this context, here an
email will lead an individual towards some faked logged in services which are being
formed by a hacker. Thus, it is the kind of trap which is being made by hackers in order
to get the password and other related details of the people. It is through this way only
hackers can perform different crimes such as stealing money from the account of
individuals and molding the data of company etc.
Malware: Another most effective password cracking technique is malware. Here, key
logger and screen scraper is being installed by malware which will make a record of each
and everything that we write and take the screenshot during the login process. The copy
of the same will be forwarded to the hacker central. Here, malware will basically look for
the existence of the web browser client password file. Overall, it can be said that these are
some major password cracking techniques which are being used by hackers to hack the
system.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Running head: Blog Writing
WHEN HACKING IS CONSIDER AS LEGAL AND ILLEGAL
Hacking is considered illegal when it is being done for some good purpose. For example,
if an individual will hack the system for the purpose to get the idea about ways to enhance the
security of the system. Then in a given type of activity will come under the category of legal
hacking. However, there is some manner examined which will entail that when the hacking is
considered as illegal. These are all detailed below:
When the hacking is done for the fun: Herein, it is assessed that there are many hackers
that like to perform those things only that they love most. For many people, hacking is
6
WHEN HACKING IS CONSIDER AS LEGAL AND ILLEGAL
Hacking is considered illegal when it is being done for some good purpose. For example,
if an individual will hack the system for the purpose to get the idea about ways to enhance the
security of the system. Then in a given type of activity will come under the category of legal
hacking. However, there is some manner examined which will entail that when the hacking is
considered as illegal. These are all detailed below:
When the hacking is done for the fun: Herein, it is assessed that there are many hackers
that like to perform those things only that they love most. For many people, hacking is
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: Blog Writing
passion instead of a job. On the other hand, conducting the hacking against the company
without taking their prior permission in relation to the same is considered as an offense
under the Computer Misuse Act 1990. It is being regarded as major legislation that
covers the hacking offenses and it also covers the data protection act.
When hacking is performed for the political purpose: This happens when the political
party will resonate with the hackers. In the respective situation, they always take the law
in their own hands by hacking the personal accounts, emails, and website of the other
political party. The given thing recently happens with Donald Trump in the presidential
election.
When hacking comes under the part of crime: In terms of organized crime, hacking is
being considered as big business. It is also being regarded as very much sophisticated in
nature. On the other hand, hacking for the profit is being considered as very much
lucrative. Further, the technique which is being used by hackers in order to perform
hacking is also considered as the offense in the eyes of law.
When hacking is being done for notoriety: The given type of technique is basically used
by the younger generation of the hackers. Herein, the script kiddies will basically try to
prove their knowledge to the group where they basically belong. Generally, the given
types of attacks are majorly website defacement; however, in some cases, they are very
much larger in scale. The given form of hacking is considered as illegal. Further, there is
no authorization for this individual for the purpose to perform active testing on the
system. The respective activity will also lead to different types of additional offenses.
These individuals are often referred to as the black hat hackers.
CONCLUSION
From the conducted analysis, it can be said that hacking is being regarded as one of the
biggest crime in the field of information technology. However, hackers are the individual who
used to perform a given type of crime. These people have the specialized skill which they tend to
use in order to hack the system of the other individuals in an effectual manner. Further, there are
different passwords hacking techniques which are being used by them in order to get access to
the system of other people in an effectual way.
7
passion instead of a job. On the other hand, conducting the hacking against the company
without taking their prior permission in relation to the same is considered as an offense
under the Computer Misuse Act 1990. It is being regarded as major legislation that
covers the hacking offenses and it also covers the data protection act.
When hacking is performed for the political purpose: This happens when the political
party will resonate with the hackers. In the respective situation, they always take the law
in their own hands by hacking the personal accounts, emails, and website of the other
political party. The given thing recently happens with Donald Trump in the presidential
election.
When hacking comes under the part of crime: In terms of organized crime, hacking is
being considered as big business. It is also being regarded as very much sophisticated in
nature. On the other hand, hacking for the profit is being considered as very much
lucrative. Further, the technique which is being used by hackers in order to perform
hacking is also considered as the offense in the eyes of law.
When hacking is being done for notoriety: The given type of technique is basically used
by the younger generation of the hackers. Herein, the script kiddies will basically try to
prove their knowledge to the group where they basically belong. Generally, the given
types of attacks are majorly website defacement; however, in some cases, they are very
much larger in scale. The given form of hacking is considered as illegal. Further, there is
no authorization for this individual for the purpose to perform active testing on the
system. The respective activity will also lead to different types of additional offenses.
These individuals are often referred to as the black hat hackers.
CONCLUSION
From the conducted analysis, it can be said that hacking is being regarded as one of the
biggest crime in the field of information technology. However, hackers are the individual who
used to perform a given type of crime. These people have the specialized skill which they tend to
use in order to hack the system of the other individuals in an effectual manner. Further, there are
different passwords hacking techniques which are being used by them in order to get access to
the system of other people in an effectual way.
7
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





