Computer Science Report: Network Protocols, Subnetting, and Handshakes
VerifiedAdded on 2019/10/31
|8
|1008
|334
Report
AI Summary
This report provides a comprehensive overview of essential computer network concepts. It begins with a discussion on the advantages and disadvantages of TCP and UDP protocols, highlighting their roles in network communication. The report then explains the functionality of DHCP (Dynamic Host Configuration Protocol) in IP address management. Following this, three common network topologies—star, ring, and bus—are described with illustrative figures. The process of the three-way handshake for initiating TCP connections is detailed, explaining how connections are established between clients and servers. Finally, the report addresses the concept of subnetting, illustrating how IP addresses are divided and managed within a network, with an example using a subnet mask. The report concludes with a list of references to support the information presented.

Computer Science
Network Protocols
Page 1 of 8
Network Protocols
Page 1 of 8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer Science
Table of Contents
Introduction......................................................................................................................................2
Discussion........................................................................................................................................2
Advantages and Disadvantages of TCP and UDP Protocols......................................................2
How DHCP Works.......................................................................................................................3
Three Types of Network Topologies.............................................................................................3
Three-Way Handshake Process for Initiating TCP Connections................................................4
How Sub-Netting Works...............................................................................................................5
References........................................................................................................................................7
Page 2 of 8
Table of Contents
Introduction......................................................................................................................................2
Discussion........................................................................................................................................2
Advantages and Disadvantages of TCP and UDP Protocols......................................................2
How DHCP Works.......................................................................................................................3
Three Types of Network Topologies.............................................................................................3
Three-Way Handshake Process for Initiating TCP Connections................................................4
How Sub-Netting Works...............................................................................................................5
References........................................................................................................................................7
Page 2 of 8
Computer Science
Introduction
In my organization, a developer is developing a new network application to get much better
communication and content sharing service. Now developer is asking that communication should
be TCP based or UDP and at management level, the working of DHCP is also necessary to
discuss. Moreover, in this report I will also emphasize on network topologies and connections of
TCP.
Discussion
In this segment of report, I will discuss in detail above mentioned essential points.
Advantages and Disadvantages of TCP and UDP Protocols
TCP Protocol
Advantages Disadvantages
TCP gives guarantee that data will send at
required destination on time and without any
redundancy (Nasrat, 2017).
Operating system performs almost everything
in TCP. But if operating system will have bugs
in it then problems regarding surfing and
downloading content from internet can occur.
In TCP whole process is done by an operating
system. Even the debugging is also done by
TCP.
For broadcast and multicast connections TCP is
not recommended.
Page 3 of 8
Introduction
In my organization, a developer is developing a new network application to get much better
communication and content sharing service. Now developer is asking that communication should
be TCP based or UDP and at management level, the working of DHCP is also necessary to
discuss. Moreover, in this report I will also emphasize on network topologies and connections of
TCP.
Discussion
In this segment of report, I will discuss in detail above mentioned essential points.
Advantages and Disadvantages of TCP and UDP Protocols
TCP Protocol
Advantages Disadvantages
TCP gives guarantee that data will send at
required destination on time and without any
redundancy (Nasrat, 2017).
Operating system performs almost everything
in TCP. But if operating system will have bugs
in it then problems regarding surfing and
downloading content from internet can occur.
In TCP whole process is done by an operating
system. Even the debugging is also done by
TCP.
For broadcast and multicast connections TCP is
not recommended.
Page 3 of 8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Computer Science
UDP Protocol
Advantages Disadvantages
It is considered best for handling multicast
and broadcast connections.
Unlike TCP, UDP does not provide surety for
packet delivery on time and without any
duplication.
There is no restriction regarding connection
based communication model (Conklin, 2016).
In UDP, data breaking is done manually.
How DHCP Works
DHCP stands for Dynamic Host Configuration Protocol. It is basically used to provide fast,
automatic and overall management of distribution of IP addresses within a network. Here DHCP
server provides information regarding IP addresses to DHCP client by exchanging a series of
messages. It is known as DHCP conversation. If the location of DHCP server and DHCP client is
on different subnets then relay agent can be used for facilitate whole transaction or conversation.
DHCP can be used for both server and PC environments successfully (Technet.microsoft.com,
2017).
Three Types of Network Topologies
Star Topology: In this topology, all devices and computers are connected with central hub that
has responsibility to distributes flow of data within the network.
Figure: Star Topology
Page 4 of 8
UDP Protocol
Advantages Disadvantages
It is considered best for handling multicast
and broadcast connections.
Unlike TCP, UDP does not provide surety for
packet delivery on time and without any
duplication.
There is no restriction regarding connection
based communication model (Conklin, 2016).
In UDP, data breaking is done manually.
How DHCP Works
DHCP stands for Dynamic Host Configuration Protocol. It is basically used to provide fast,
automatic and overall management of distribution of IP addresses within a network. Here DHCP
server provides information regarding IP addresses to DHCP client by exchanging a series of
messages. It is known as DHCP conversation. If the location of DHCP server and DHCP client is
on different subnets then relay agent can be used for facilitate whole transaction or conversation.
DHCP can be used for both server and PC environments successfully (Technet.microsoft.com,
2017).
Three Types of Network Topologies
Star Topology: In this topology, all devices and computers are connected with central hub that
has responsibility to distributes flow of data within the network.
Figure: Star Topology
Page 4 of 8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Computer Science
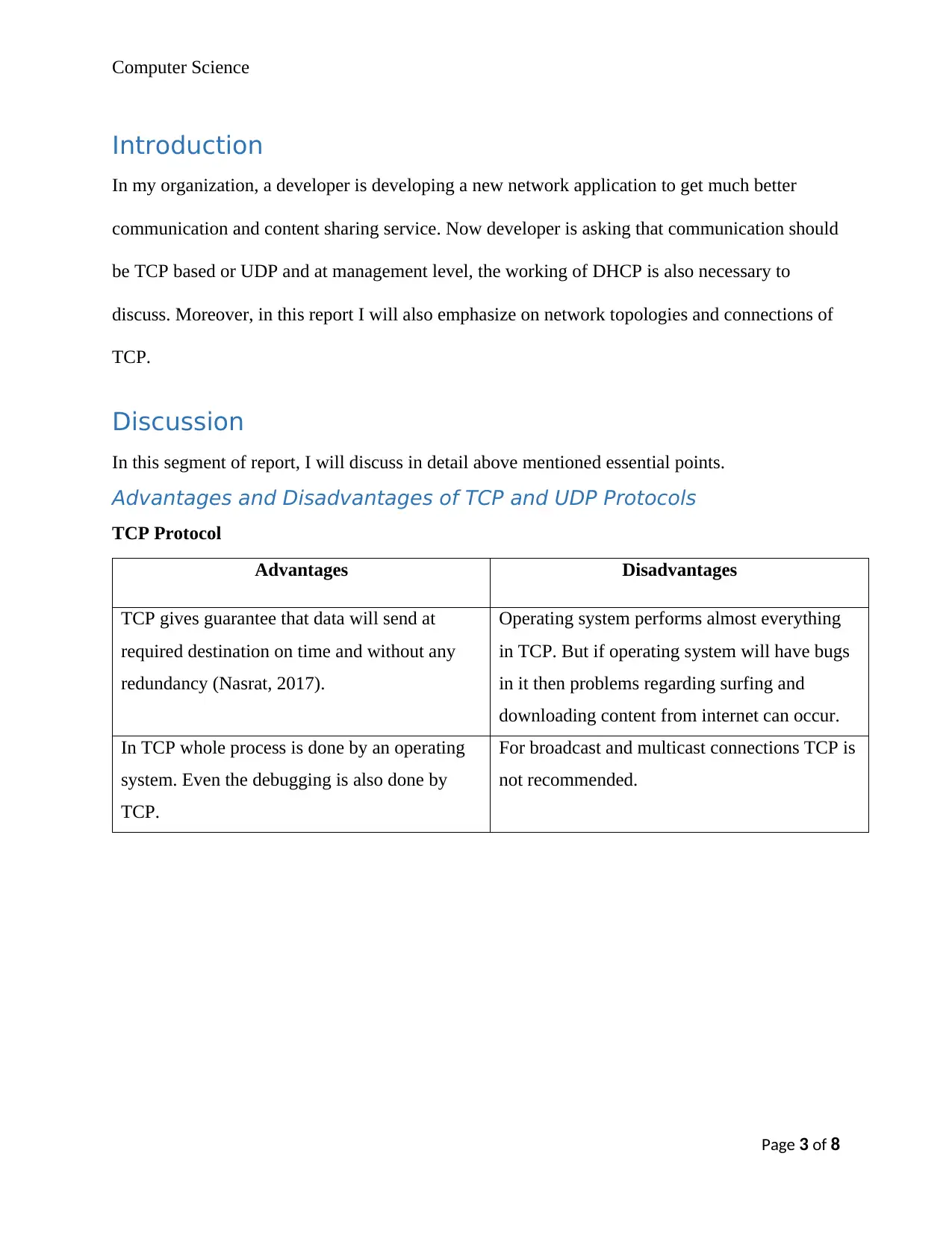
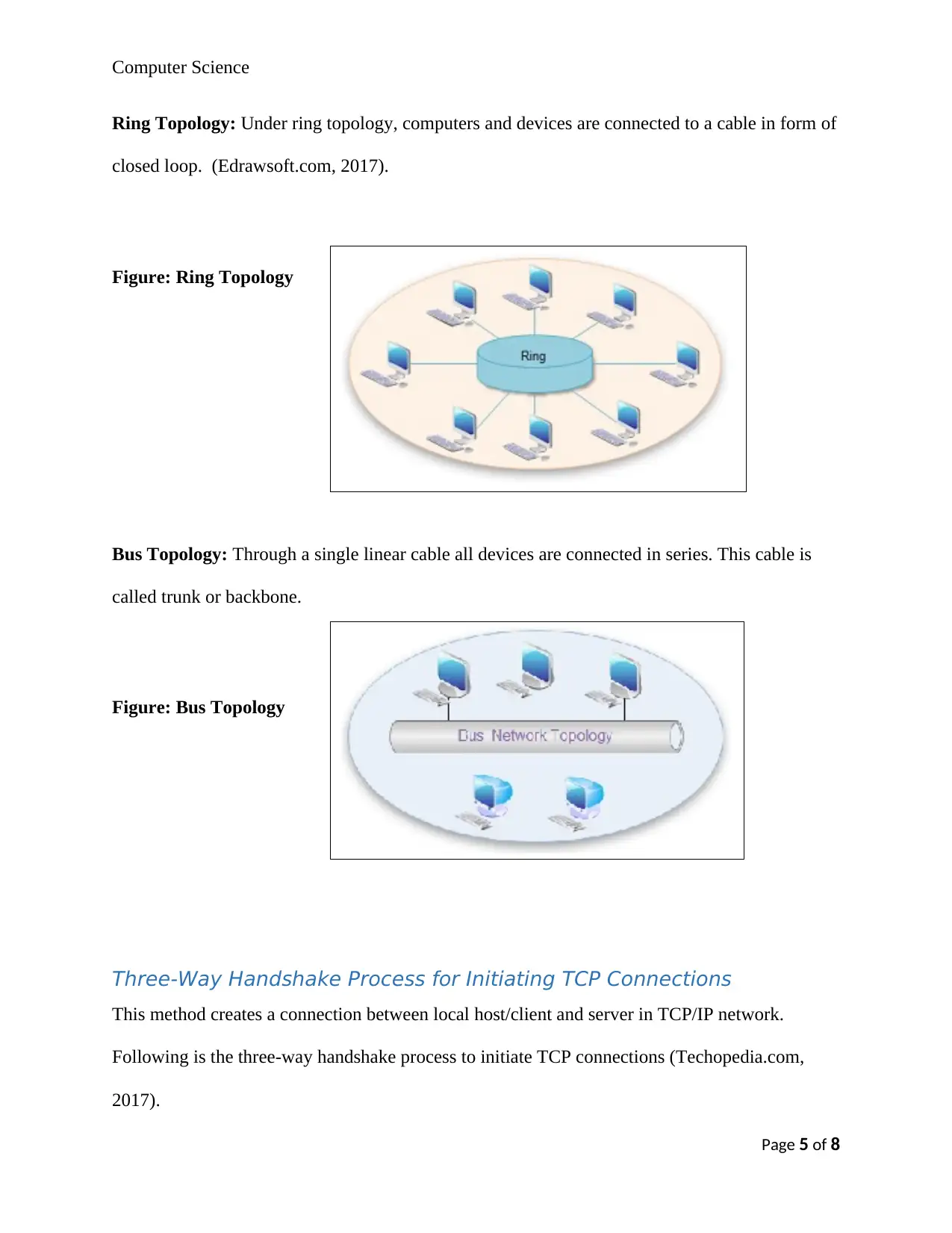
Ring Topology: Under ring topology, computers and devices are connected to a cable in form of
closed loop. (Edrawsoft.com, 2017).
Figure: Ring Topology
Bus Topology: Through a single linear cable all devices are connected in series. This cable is
called trunk or backbone.
Figure: Bus Topology
Three-Way Handshake Process for Initiating TCP Connections
This method creates a connection between local host/client and server in TCP/IP network.
Following is the three-way handshake process to initiate TCP connections (Techopedia.com,
2017).
Page 5 of 8
Ring Topology: Under ring topology, computers and devices are connected to a cable in form of
closed loop. (Edrawsoft.com, 2017).
Figure: Ring Topology
Bus Topology: Through a single linear cable all devices are connected in series. This cable is
called trunk or backbone.
Figure: Bus Topology
Three-Way Handshake Process for Initiating TCP Connections
This method creates a connection between local host/client and server in TCP/IP network.
Following is the three-way handshake process to initiate TCP connections (Techopedia.com,
2017).
Page 5 of 8
Computer Science
1. SYN data packet is sent by client node over an IP network to server. This can be done by
using same network or any external network.
2. On server side, there are some open ports that accept and pledge new connections. A
confirmation receipt is returned to client node by server after receiving SYN packet.
3. After receiving confirmation node from server, client also sends responds to server
through ACK receipt.
After completion of three steps, creation of connection is done and communication between
client and server will be started.
How Sub-Netting Works
The IP sub-netting is fundamental process which is critical for network engineers. IP stands for
Internet Protocol and it works in following ways.
1. In first step, identification of host bits is required that must be used for sub-netting.
2. In next step, inventory of new network IDs is maintained.
3. In this step, recording of IP addresses for every new sub-netted network ID is done.
Here I would like to give example of subnet of IP addresses by using mask 255.255.255.0. It is
using two octets of host from a Class A Network. Through following example 65,536 subnets
and 254 hosts can be created per network (Paul Stewart, 2017).
Example:
Subnet 1: 10.0.0.x (10.0.0.1 - 10.0.0.254)
---------------------------------------------------
Subnet 256: 10.0.255.x (10.0.255.1 - 10.0.255.254)
Page 6 of 8
1. SYN data packet is sent by client node over an IP network to server. This can be done by
using same network or any external network.
2. On server side, there are some open ports that accept and pledge new connections. A
confirmation receipt is returned to client node by server after receiving SYN packet.
3. After receiving confirmation node from server, client also sends responds to server
through ACK receipt.
After completion of three steps, creation of connection is done and communication between
client and server will be started.
How Sub-Netting Works
The IP sub-netting is fundamental process which is critical for network engineers. IP stands for
Internet Protocol and it works in following ways.
1. In first step, identification of host bits is required that must be used for sub-netting.
2. In next step, inventory of new network IDs is maintained.
3. In this step, recording of IP addresses for every new sub-netted network ID is done.
Here I would like to give example of subnet of IP addresses by using mask 255.255.255.0. It is
using two octets of host from a Class A Network. Through following example 65,536 subnets
and 254 hosts can be created per network (Paul Stewart, 2017).
Example:
Subnet 1: 10.0.0.x (10.0.0.1 - 10.0.0.254)
---------------------------------------------------
Subnet 256: 10.0.255.x (10.0.255.1 - 10.0.255.254)
Page 6 of 8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Computer Science
----------------------------------------------------------
Subnet 65536: 10.255.255.x (10.255.255.1 - 10.255.255.254)
Page 7 of 8
----------------------------------------------------------
Subnet 65536: 10.255.255.x (10.255.255.1 - 10.255.255.254)
Page 7 of 8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer Science
References
Conklin, W. (2016). Principles of computer security. New York [etc.]: McGraw-Hill Education.
Technet.microsoft.com. (2017). How DHCP Technology Works: Dynamic Host Configuration
Protocol (DHCP). Retrieved 12 September 2017, from https://technet.microsoft.com/en-
us/library/cc780760(v=ws.10).aspx
sharma, p. (2017). ADVANTAGES AND DISADVANTAGES OF TCP AND UDP.
Smblog.iiitd.com. Retrieved 12 September 2017, from
http://smblog.iiitd.com/2010/09/advantages-and-disadvantages-of-tcp-and.html
Edrawsoft.com. (2017). Network Topology Diagrams, Free Examples, Templates, Software
download. Retrieved 12 September 2017, from https://www.edrawsoft.com/Network-
Topologies.php
Paul Stewart, C. (2017). IP Subnetting Part 2: Simple Subnetting Examples - The Packet
University. The Packet University. Retrieved 12 September 2017, from
http://www.packetu.com/2014/06/27/ip-subnetting-part-2-simple-subnetting-examples/
Techopedia.com. (2017). What is a Three-Way Handshake? - Definition from Techopedia.
Retrieved 12 September 2017, from https://www.techopedia.com/definition/10339/three-
way-handshake
Nasrat. (2017). Tcp and udp. Slideshare.net. Retrieved 12 September 2017, from
https://www.slideshare.net/ahdkhalid/tcp-and-udp
Page 8 of 8
References
Conklin, W. (2016). Principles of computer security. New York [etc.]: McGraw-Hill Education.
Technet.microsoft.com. (2017). How DHCP Technology Works: Dynamic Host Configuration
Protocol (DHCP). Retrieved 12 September 2017, from https://technet.microsoft.com/en-
us/library/cc780760(v=ws.10).aspx
sharma, p. (2017). ADVANTAGES AND DISADVANTAGES OF TCP AND UDP.
Smblog.iiitd.com. Retrieved 12 September 2017, from
http://smblog.iiitd.com/2010/09/advantages-and-disadvantages-of-tcp-and.html
Edrawsoft.com. (2017). Network Topology Diagrams, Free Examples, Templates, Software
download. Retrieved 12 September 2017, from https://www.edrawsoft.com/Network-
Topologies.php
Paul Stewart, C. (2017). IP Subnetting Part 2: Simple Subnetting Examples - The Packet
University. The Packet University. Retrieved 12 September 2017, from
http://www.packetu.com/2014/06/27/ip-subnetting-part-2-simple-subnetting-examples/
Techopedia.com. (2017). What is a Three-Way Handshake? - Definition from Techopedia.
Retrieved 12 September 2017, from https://www.techopedia.com/definition/10339/three-
way-handshake
Nasrat. (2017). Tcp and udp. Slideshare.net. Retrieved 12 September 2017, from
https://www.slideshare.net/ahdkhalid/tcp-and-udp
Page 8 of 8
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




