Exploring VPN Replacement Technologies for Enhanced Network Security
VerifiedAdded on 2020/03/04
|14
|4340
|48
Report
AI Summary
This report delves into VPN replacement technologies, examining their evolution and the issues they address. It begins with an abstract and introduction to VPNs, followed by a historical overview and a literature review of existing VPN technologies. The report then analyzes the VPN security model, explaining concepts like congestion, latency, fragmentation, and packet loss, and how these factors impact network performance. It explores the handling of missing packets and the difficulties associated with compliance and troubleshooting VPNs. The report also touches upon the limitations of VPNs, such as repeating patterns and bandwidth consumption. Furthermore, it looks at connectivity requirements, challenges, and potential future developments in this field. The document provides an in-depth analysis of various aspects of VPNs and their alternatives, offering valuable insights into the field of computer and network security. The paper also discusses the impact of latency and packet loss on the throughput of the virtual private network. It also covers the difficulties associated with troubleshooting common VPN issues, including configuration problems and connection failures.
Computer and network security
2017
2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
VPN replacement technologies..................................................................................................2
Abstract:.....................................................................................................................................2
Introduction:...............................................................................................................................2
History and background:............................................................................................................2
Literature Review:......................................................................................................................2
VPN security model:..................................................................................................................3
Explanation:...............................................................................................................................3
Congestion, latency, fragmentation, and packet loss:............................................................3
Handling of the missing packet:.............................................................................................4
Difficulties with compliance and troubleshooting:................................................................5
Lacks in Repeating patterns:..................................................................................................6
More bandwidth-intensive than clear text transmission.........................................................7
Connectivity requires high availability:.................................................................................7
Challenges and drawbacks:........................................................................................................7
Future work:...............................................................................................................................7
Conclusion..................................................................................................................................7
References:.................................................................................................................................7
VPN replacement technologies..................................................................................................2
Abstract:.....................................................................................................................................2
Introduction:...............................................................................................................................2
History and background:............................................................................................................2
Literature Review:......................................................................................................................2
VPN security model:..................................................................................................................3
Explanation:...............................................................................................................................3
Congestion, latency, fragmentation, and packet loss:............................................................3
Handling of the missing packet:.............................................................................................4
Difficulties with compliance and troubleshooting:................................................................5
Lacks in Repeating patterns:..................................................................................................6
More bandwidth-intensive than clear text transmission.........................................................7
Connectivity requires high availability:.................................................................................7
Challenges and drawbacks:........................................................................................................7
Future work:...............................................................................................................................7
Conclusion..................................................................................................................................7
References:.................................................................................................................................7

VPN replacement technologies
Abstract:
In this paper, we are looking on the issues
related on the virtual private network and
the replacement technologies for providing
alternative solution to the VPN. The
virtual tunnelling protocol are used for
deploying virtual point to point connection
in creating traffic encryption in creating
virtual private network. The problem of
latency and packet loss can be resolved
with the multiple accessing. The MPLS
VPN network helps in reducing the cost
and increasing the productivity of the
system because it does not require any
additional security system for securing the
premises. The application can be
developed by using the SSL VPN on any
web browser. The communication cost can
be reduced by deploying the concept of
VPN. The VPN solution provides the
security for managing encrypted
connection to permit security.
I. Introduction:
The virtual private network is the
extension of the private network up to the
deployment of public network. It is used of
sending, receiving, and sharing data on the
public network which are directly
connected to the private network. It is
capable of providing functionality,
management, and security to the
application running on the private network.
The corporate intranet is securely access
by the employees with the help of VPN.
“The geographically separated offices can
be securely connected with the use of
cohesive network”[1]. The proxy server is
used for putting geo-restriction for
securing the wireless transaction which
helps in protecting the identity of the
location and the person. The virtual
tunnelling protocol are used for deploying
virtual point to point connection in
creating traffic encryption in creating
virtual private network. “The classification
of the virtual private network are depends
on protocols used for tunnelling the traffic,
location of the termination point in the
tunnel, topologies used for connection,
security level protection, layer 2 and layer
3 are used for providing network
connectivity” [6]. VPN is the complete
solution which is capable of providing
security to the internet connection,
securing the connection of the Wi-Fi
hotspots, protection from the data sniffers,
avoiding surveillance to the third party,
inspection of the ISP packet, protecting the
identity of the person, preventing geo-
Abstract:
In this paper, we are looking on the issues
related on the virtual private network and
the replacement technologies for providing
alternative solution to the VPN. The
virtual tunnelling protocol are used for
deploying virtual point to point connection
in creating traffic encryption in creating
virtual private network. The problem of
latency and packet loss can be resolved
with the multiple accessing. The MPLS
VPN network helps in reducing the cost
and increasing the productivity of the
system because it does not require any
additional security system for securing the
premises. The application can be
developed by using the SSL VPN on any
web browser. The communication cost can
be reduced by deploying the concept of
VPN. The VPN solution provides the
security for managing encrypted
connection to permit security.
I. Introduction:
The virtual private network is the
extension of the private network up to the
deployment of public network. It is used of
sending, receiving, and sharing data on the
public network which are directly
connected to the private network. It is
capable of providing functionality,
management, and security to the
application running on the private network.
The corporate intranet is securely access
by the employees with the help of VPN.
“The geographically separated offices can
be securely connected with the use of
cohesive network”[1]. The proxy server is
used for putting geo-restriction for
securing the wireless transaction which
helps in protecting the identity of the
location and the person. The virtual
tunnelling protocol are used for deploying
virtual point to point connection in
creating traffic encryption in creating
virtual private network. “The classification
of the virtual private network are depends
on protocols used for tunnelling the traffic,
location of the termination point in the
tunnel, topologies used for connection,
security level protection, layer 2 and layer
3 are used for providing network
connectivity” [6]. VPN is the complete
solution which is capable of providing
security to the internet connection,
securing the connection of the Wi-Fi
hotspots, protection from the data sniffers,
avoiding surveillance to the third party,
inspection of the ISP packet, protecting the
identity of the person, preventing geo-
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

targeting, easy internet surfing, providing
the services of the VoIP, overcoming the
throttling ISP speed, experiencing the fast
and ultra-streaming.
II. History and background:
The virtual private network is the standard
solution which is capable of providing
access control of the network. The
encryption methodologies and security
mechanisms are used for ensuring the
authorisation of the user for accessing the
network. “The encryption tunnel is used
for transferring the information between
two location which helps in preventing the
confidentiality of the data” [4]. Encryption
and decryption methodologies are used for
sending and receiving information securely
over the network. The protocols which are
used for deploying the virtual private
network are IPSec, PPTP, and L2TP.
“IPSec protocol is the set of protocols
which are used for securing the packet
exchange in the IP layer”[2]. The transport
and the tunnel mode are the encryption
mode which is used for deploying the
virtual private network. The Point to point
tunnelling protocol is used for deploying
the virtual private network across remote
accessible vendor companies.”L2TP stands
for Layer2 tunnelling protocol which is
used for carrying over operation between
ISP and the VPN”[16].
III. Literature Review:
The virtual private network is used for
providing secure connection for the
management of multi-office location. “The
secure connection can be managed
between remote employees and internal
system”[3]. The cloud computing
technologies are used for managing the
encrypted connection with the remote
devices. The communication issues are the
major concern area for managing the
connection of the client with the contact
centre. The VPN solution provides the
security for managing encrypted
connection to permit security. “The cloud
based solution can be leveraged with the
remote accessing and site to site VPN
connection”[7]. It helps in lowering the
cost and providing robust functionality to
provide cloud based communication. The
secure connection can be managed
between multiple users, transfer of data
between remote offices, flexibility, and
scalability. The characteristics of the VPN
are categorised as data confidentiality,
integrity of data, non-repudiation of the
sender, and authentication of the messages.
The restriction of un-authorization of data
helps in managing the confidentiality of
the data. The VPN tunnels are used for
sending the data packets over the network.
The high amount of bandwidth is wasted
in the transmission of data. The
encapsulation of the packet helps in
the services of the VoIP, overcoming the
throttling ISP speed, experiencing the fast
and ultra-streaming.
II. History and background:
The virtual private network is the standard
solution which is capable of providing
access control of the network. The
encryption methodologies and security
mechanisms are used for ensuring the
authorisation of the user for accessing the
network. “The encryption tunnel is used
for transferring the information between
two location which helps in preventing the
confidentiality of the data” [4]. Encryption
and decryption methodologies are used for
sending and receiving information securely
over the network. The protocols which are
used for deploying the virtual private
network are IPSec, PPTP, and L2TP.
“IPSec protocol is the set of protocols
which are used for securing the packet
exchange in the IP layer”[2]. The transport
and the tunnel mode are the encryption
mode which is used for deploying the
virtual private network. The Point to point
tunnelling protocol is used for deploying
the virtual private network across remote
accessible vendor companies.”L2TP stands
for Layer2 tunnelling protocol which is
used for carrying over operation between
ISP and the VPN”[16].
III. Literature Review:
The virtual private network is used for
providing secure connection for the
management of multi-office location. “The
secure connection can be managed
between remote employees and internal
system”[3]. The cloud computing
technologies are used for managing the
encrypted connection with the remote
devices. The communication issues are the
major concern area for managing the
connection of the client with the contact
centre. The VPN solution provides the
security for managing encrypted
connection to permit security. “The cloud
based solution can be leveraged with the
remote accessing and site to site VPN
connection”[7]. It helps in lowering the
cost and providing robust functionality to
provide cloud based communication. The
secure connection can be managed
between multiple users, transfer of data
between remote offices, flexibility, and
scalability. The characteristics of the VPN
are categorised as data confidentiality,
integrity of data, non-repudiation of the
sender, and authentication of the messages.
The restriction of un-authorization of data
helps in managing the confidentiality of
the data. The VPN tunnels are used for
sending the data packets over the network.
The high amount of bandwidth is wasted
in the transmission of data. The
encapsulation of the packet helps in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

creating the dynamic tunnels for the
transfer of packet. The L2TP and PPTP
protocols are used for managing the
tunnels of the packet. The tunnels are
created for initiating the action taken by
the user. The voluntary tunnels are
developed for managing the data integrity.
IV. VPN security model:
The security model of the virtual private
network provides the confidentiality to the
exchange of data which takes place on
managing the traffic on network at packet
level. The encrypted data is not easy for
the attacker to track it. The unauthorized
accessing of virtual private network can be
done by using the sender authentication.
“The message integrity is used for
detecting tampering instances within the
transmitted messages. The security of the
VPN can be done by using the VPN
protocols”[15]. Internet protocol security
is used for providing authentication,
confidentiality, and integrity of the
transmitted data. “The IPsec protocol is
used for providing encryption and
encapsulation of IPSec packet”[5]. At the
end of the tunnel, the de-encapsulation
process is performed which decrypts the
message and forward it to transmit the
message at desired location. Transport
layer security protocol is used for
providing the individual connections are
secured by using the tunnel deployed on
the entire network traffic management
system. The secure socket layer is used for
providing remote access capabilities of the
virtual private network. The network
address translation and firewall rules are
incorporated in SSL VPN. SSL and TLS
issues can be resolved by using the
datagram transport layer protocol. The
point to point tunnelling protocols are used
for implementing the VPN on different
platform. “The secure shell VPN is used
for providing security to the remote
connection deployed on the network
links”[12].
V. Explanation:
The VPN solution provides the security for
managing encrypted connection to permit
security. The remote accessing of the
server helps in managing the integrity of
the traffic. The L2TP and PPTP protocols
are used for managing the flow of
protocols between the participating units.
Congestion, latency, fragmentation, and
packet loss:
The virtual private network performance
can be measured in terms of congestion,
latency, fragmentation, throughput, and
packet loss.
transfer of packet. The L2TP and PPTP
protocols are used for managing the
tunnels of the packet. The tunnels are
created for initiating the action taken by
the user. The voluntary tunnels are
developed for managing the data integrity.
IV. VPN security model:
The security model of the virtual private
network provides the confidentiality to the
exchange of data which takes place on
managing the traffic on network at packet
level. The encrypted data is not easy for
the attacker to track it. The unauthorized
accessing of virtual private network can be
done by using the sender authentication.
“The message integrity is used for
detecting tampering instances within the
transmitted messages. The security of the
VPN can be done by using the VPN
protocols”[15]. Internet protocol security
is used for providing authentication,
confidentiality, and integrity of the
transmitted data. “The IPsec protocol is
used for providing encryption and
encapsulation of IPSec packet”[5]. At the
end of the tunnel, the de-encapsulation
process is performed which decrypts the
message and forward it to transmit the
message at desired location. Transport
layer security protocol is used for
providing the individual connections are
secured by using the tunnel deployed on
the entire network traffic management
system. The secure socket layer is used for
providing remote access capabilities of the
virtual private network. The network
address translation and firewall rules are
incorporated in SSL VPN. SSL and TLS
issues can be resolved by using the
datagram transport layer protocol. The
point to point tunnelling protocols are used
for implementing the VPN on different
platform. “The secure shell VPN is used
for providing security to the remote
connection deployed on the network
links”[12].
V. Explanation:
The VPN solution provides the security for
managing encrypted connection to permit
security. The remote accessing of the
server helps in managing the integrity of
the traffic. The L2TP and PPTP protocols
are used for managing the flow of
protocols between the participating units.
Congestion, latency, fragmentation, and
packet loss:
The virtual private network performance
can be measured in terms of congestion,
latency, fragmentation, throughput, and
packet loss.
Congestion: The sender sends the
packet without waiting for the
acknowledged sent by the receiver.
TCP congestion window is used for
managing the flow of packets
between the workstation. “The
receiving of the packet before the
acknowledgement of the packet
will increase the effectiveness of
the congestion window” [10].
Latency: Latency is the
measurement of time required to
transfer the packet over the
network. One way and round trip
are the different ways for
measuring the latency. The impact
of the latency is on the chain of
element to transfer data to the
desired location of workstation.
The transfer of data takes place
between WAN links, workstation,
local area network, router, and
server. The increase in latency time
will decrease the throughput of the
virtual private network and vice-
versa.
Fragmentation:
Throughput: Throughput is the
measurement of quantity of data
transferred in the unit of time. The
throughput of the network can be
increased by sending more packets
over the network for the period of
time. The increase in throughput
will decrease in the throughput of
the virtual private network and vice
versa.
Packet Loss: It is the count of
packet loss in the transfer of data
with respect 100 packet.
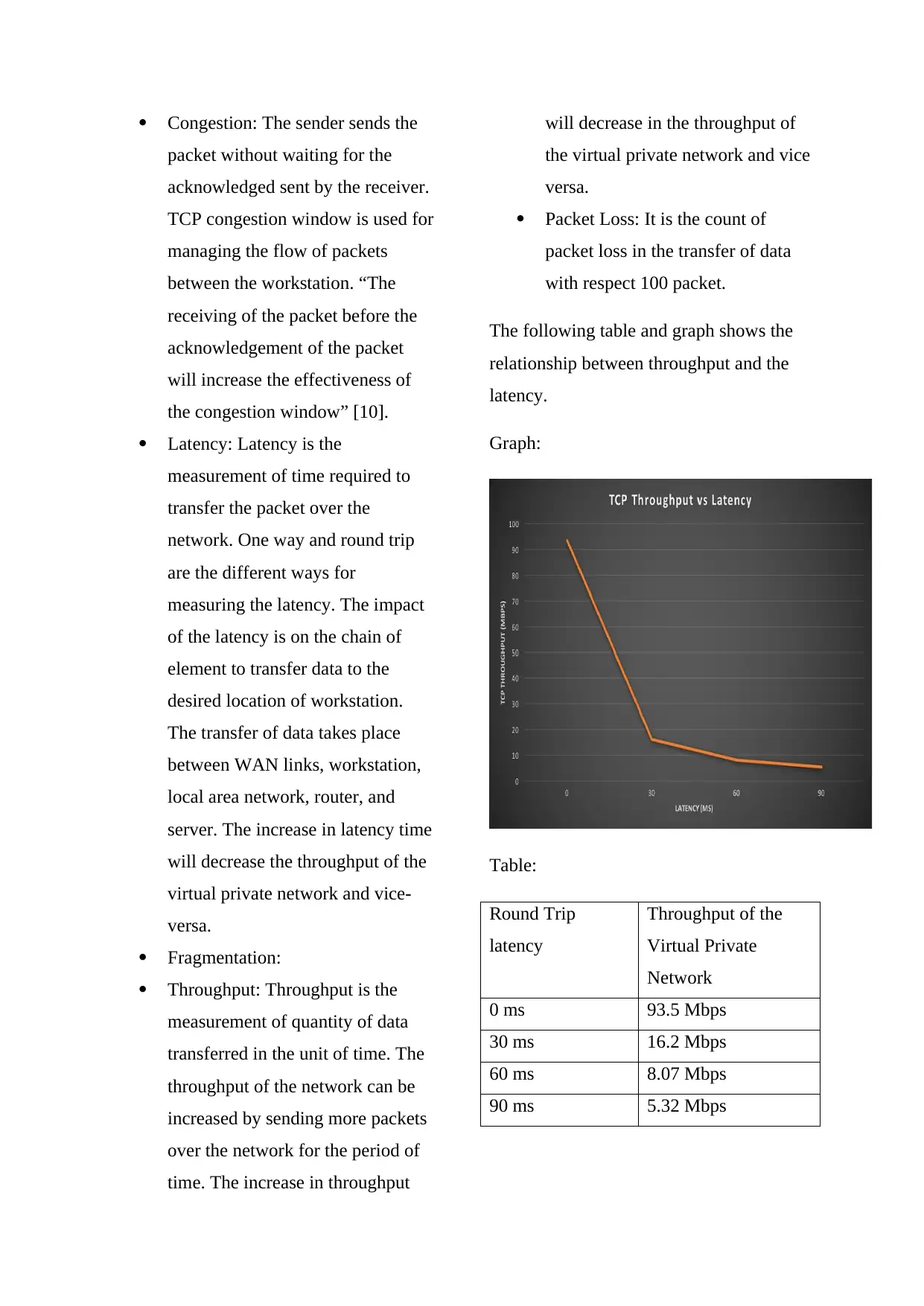
The following table and graph shows the
relationship between throughput and the
latency.
Graph:
Table:
Round Trip
latency
Throughput of the
Virtual Private
Network
0 ms 93.5 Mbps
30 ms 16.2 Mbps
60 ms 8.07 Mbps
90 ms 5.32 Mbps
packet without waiting for the
acknowledged sent by the receiver.
TCP congestion window is used for
managing the flow of packets
between the workstation. “The
receiving of the packet before the
acknowledgement of the packet
will increase the effectiveness of
the congestion window” [10].
Latency: Latency is the
measurement of time required to
transfer the packet over the
network. One way and round trip
are the different ways for
measuring the latency. The impact
of the latency is on the chain of
element to transfer data to the
desired location of workstation.
The transfer of data takes place
between WAN links, workstation,
local area network, router, and
server. The increase in latency time
will decrease the throughput of the
virtual private network and vice-
versa.
Fragmentation:
Throughput: Throughput is the
measurement of quantity of data
transferred in the unit of time. The
throughput of the network can be
increased by sending more packets
over the network for the period of
time. The increase in throughput
will decrease in the throughput of
the virtual private network and vice
versa.
Packet Loss: It is the count of
packet loss in the transfer of data
with respect 100 packet.
The following table and graph shows the
relationship between throughput and the
latency.
Graph:
Table:
Round Trip
latency
Throughput of the
Virtual Private
Network
0 ms 93.5 Mbps
30 ms 16.2 Mbps
60 ms 8.07 Mbps
90 ms 5.32 Mbps
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Handling of the missing packet:
The TCP congestion window plays an
active role in handling the
acknowledgement of the missing packets
which are sent but not received by the
workstation. “If the acknowledgement of
the packet is not received than that packet
come under the category of packet lost
which result into the decrement in the
throughput”[13]. The congestion window
size will increase if the packet are received
by the workstation with their associated
acknowledgement. The transmission speed
of data is effected in two manners such as:
Retransmission of the packet
The optimal throughput is not
allowed by the TCP congestion
window.
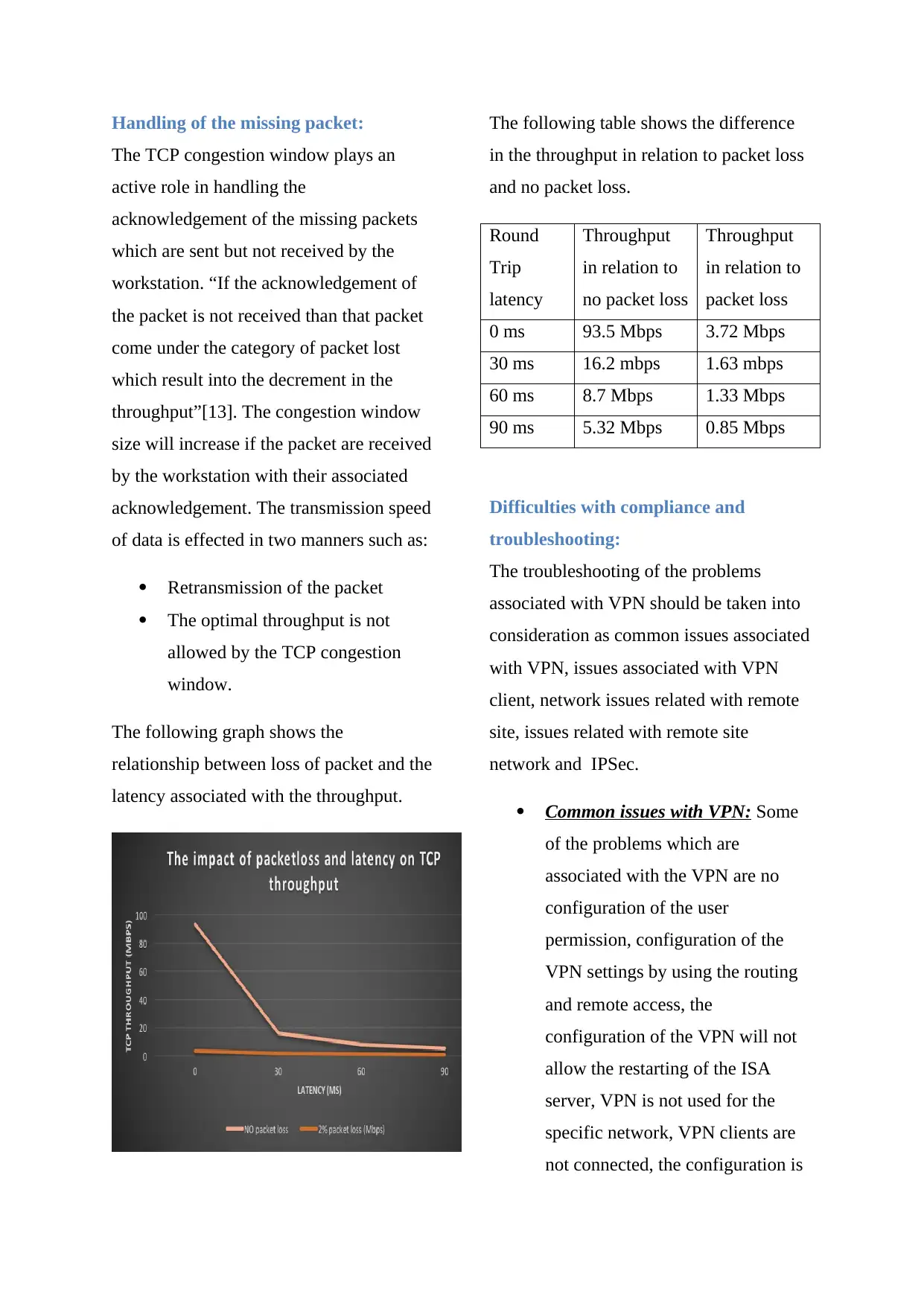
The following graph shows the
relationship between loss of packet and the
latency associated with the throughput.
The following table shows the difference
in the throughput in relation to packet loss
and no packet loss.
Round
Trip
latency
Throughput
in relation to
no packet loss
Throughput
in relation to
packet loss
0 ms 93.5 Mbps 3.72 Mbps
30 ms 16.2 mbps 1.63 mbps
60 ms 8.7 Mbps 1.33 Mbps
90 ms 5.32 Mbps 0.85 Mbps
Difficulties with compliance and
troubleshooting:
The troubleshooting of the problems
associated with VPN should be taken into
consideration as common issues associated
with VPN, issues associated with VPN
client, network issues related with remote
site, issues related with remote site
network and IPSec.
Common issues with VPN: Some
of the problems which are
associated with the VPN are no
configuration of the user
permission, configuration of the
VPN settings by using the routing
and remote access, the
configuration of the VPN will not
allow the restarting of the ISA
server, VPN is not used for the
specific network, VPN clients are
not connected, the configuration is
The TCP congestion window plays an
active role in handling the
acknowledgement of the missing packets
which are sent but not received by the
workstation. “If the acknowledgement of
the packet is not received than that packet
come under the category of packet lost
which result into the decrement in the
throughput”[13]. The congestion window
size will increase if the packet are received
by the workstation with their associated
acknowledgement. The transmission speed
of data is effected in two manners such as:
Retransmission of the packet
The optimal throughput is not
allowed by the TCP congestion
window.
The following graph shows the
relationship between loss of packet and the
latency associated with the throughput.
The following table shows the difference
in the throughput in relation to packet loss
and no packet loss.
Round
Trip
latency
Throughput
in relation to
no packet loss
Throughput
in relation to
packet loss
0 ms 93.5 Mbps 3.72 Mbps
30 ms 16.2 mbps 1.63 mbps
60 ms 8.7 Mbps 1.33 Mbps
90 ms 5.32 Mbps 0.85 Mbps
Difficulties with compliance and
troubleshooting:
The troubleshooting of the problems
associated with VPN should be taken into
consideration as common issues associated
with VPN, issues associated with VPN
client, network issues related with remote
site, issues related with remote site
network and IPSec.
Common issues with VPN: Some
of the problems which are
associated with the VPN are no
configuration of the user
permission, configuration of the
VPN settings by using the routing
and remote access, the
configuration of the VPN will not
allow the restarting of the ISA
server, VPN is not used for the
specific network, VPN clients are
not connected, the configuration is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

not properly done by using the
dynamic host configuration
protocol, and other. The
connections are not properly
managed between VPN client due
to the no proper configuration of
user permission.
Solution: The server domain
controller should be specified of
the user. “The authentication of the
domain controller should be used
for validating the user” [8]. The
validity of the user credentials
should be checked. Remote access
permission should be granted for
accessing the network.
Configuration of the VPN settings
by making remote access and
routing protocol: The connection
between the VPN client does not
take place due to the configuration
of the VPN settings by making
remote access and routing protocol.
Solution: The organization of the
global configuration by using
authentication method, address
assignment by using the DHCP
protocol, domain name system, and
the configuration of windows
internet name service, pre-shared
keys should be used for the
implementation of layer 2
tunnelling protocols, providers of
authentication and accounting
principles, and presentation of the
radius server list. The configuration
of the VPN client involves
configuration of the tunnelling
protocol and the connection
between the VPN client with the
use of point to point tunnelling
protocol and Layer 2 tunnelling
protocol.
Failure of the L2TP connection:
The failure of the L2TP connection
is occur due to not proper
configuration of pre-sharing keys,
not proper configuration of
certificates, and the not proper
connection of connection settings.
Solution: The configuration of the
root certificate should be properly
checked. The trusted certificate
should be generated for the ISA
server computer and VPN client
computer. The authentication
methods should be performed by
matching the VPN client
authentication credentials with the
ISA server configuration.
No start-up of the remote access
and routing: The initialization of
the configuration change not allows
the start-up of the remote accessing
and routing.
Solution: The configuration of the
radius authentication should be
accompanied with the verification
dynamic host configuration
protocol, and other. The
connections are not properly
managed between VPN client due
to the no proper configuration of
user permission.
Solution: The server domain
controller should be specified of
the user. “The authentication of the
domain controller should be used
for validating the user” [8]. The
validity of the user credentials
should be checked. Remote access
permission should be granted for
accessing the network.
Configuration of the VPN settings
by making remote access and
routing protocol: The connection
between the VPN client does not
take place due to the configuration
of the VPN settings by making
remote access and routing protocol.
Solution: The organization of the
global configuration by using
authentication method, address
assignment by using the DHCP
protocol, domain name system, and
the configuration of windows
internet name service, pre-shared
keys should be used for the
implementation of layer 2
tunnelling protocols, providers of
authentication and accounting
principles, and presentation of the
radius server list. The configuration
of the VPN client involves
configuration of the tunnelling
protocol and the connection
between the VPN client with the
use of point to point tunnelling
protocol and Layer 2 tunnelling
protocol.
Failure of the L2TP connection:
The failure of the L2TP connection
is occur due to not proper
configuration of pre-sharing keys,
not proper configuration of
certificates, and the not proper
connection of connection settings.
Solution: The configuration of the
root certificate should be properly
checked. The trusted certificate
should be generated for the ISA
server computer and VPN client
computer. The authentication
methods should be performed by
matching the VPN client
authentication credentials with the
ISA server configuration.
No start-up of the remote access
and routing: The initialization of
the configuration change not allows
the start-up of the remote accessing
and routing.
Solution: The configuration of the
radius authentication should be
accompanied with the verification

of routing and remote accessing.
The configuration of the radius
server should be checked for
providing relevant server.
Lacks in Repeating patterns:
The VPN is established between clouds by
using firewalls. The certificates can be
exchanged by using the asymmetric
encryption. There are three architectures
can be used for deploying the VPN are
gateway to gateway architecture, host to
gateway architecture, and host to host
architecture.
There is a lack in the following patterns:
Automatically defined parameters:
Management of the dynamic and
scaling of the multiple clouds is the
major challenge.
Solution: “The establishing of the
proper communication between the
providers and the consumers can
allow the acceptance and rejection
of the communication with the
automatic working of the perimeter
controller”[14]. The automatic
defined perimeter is used for
authenticating the cloud consumer.
Cloud Authentication Gateway: “It
is compelled for supporting the
multiple authentication by making
use of communication and session
protocols for the management of
components and application” [9].
Solution: The implementation of
authentication service helps in
providing standard authentication
and the establishment of the
session. An authentication gateway
service is used for establishing
front for reverse proxy between the
cloud consumer and the resource.
Secure External cloud connection:
The secure external cloud
connection requires the execution
of the partial cloud for scaling the
requirement and compliance
regulation.
Solution: The border gateway
protocol is used for establishing the
VPN between the cloud providers
and the cloud consumer gateway.
The encrypted connections are
established between the cloud
consumer and the cloud service
providers.
Secure on-premise internet access:
It is a challenge in managing
network segments for assets and
internal clouds.
Solution: The internet access
segment is established between
internal and external entities for
handling controlled sharing
segment. It helps in mitigating
from the occurrence of the current
The configuration of the radius
server should be checked for
providing relevant server.
Lacks in Repeating patterns:
The VPN is established between clouds by
using firewalls. The certificates can be
exchanged by using the asymmetric
encryption. There are three architectures
can be used for deploying the VPN are
gateway to gateway architecture, host to
gateway architecture, and host to host
architecture.
There is a lack in the following patterns:
Automatically defined parameters:
Management of the dynamic and
scaling of the multiple clouds is the
major challenge.
Solution: “The establishing of the
proper communication between the
providers and the consumers can
allow the acceptance and rejection
of the communication with the
automatic working of the perimeter
controller”[14]. The automatic
defined perimeter is used for
authenticating the cloud consumer.
Cloud Authentication Gateway: “It
is compelled for supporting the
multiple authentication by making
use of communication and session
protocols for the management of
components and application” [9].
Solution: The implementation of
authentication service helps in
providing standard authentication
and the establishment of the
session. An authentication gateway
service is used for establishing
front for reverse proxy between the
cloud consumer and the resource.
Secure External cloud connection:
The secure external cloud
connection requires the execution
of the partial cloud for scaling the
requirement and compliance
regulation.
Solution: The border gateway
protocol is used for establishing the
VPN between the cloud providers
and the cloud consumer gateway.
The encrypted connections are
established between the cloud
consumer and the cloud service
providers.
Secure on-premise internet access:
It is a challenge in managing
network segments for assets and
internal clouds.
Solution: The internet access
segment is established between
internal and external entities for
handling controlled sharing
segment. It helps in mitigating
from the occurrence of the current
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

attacks. The cryptography
procedures can be used for
managing the connection between
cloud resources.
More bandwidth-intensive than clear
text transmission:
The allocated bandwidth is difficult to
examine. The simple testing procedures
are used for analysing the connection
speed of the network. The bit-rate and the
resolution of the device can be measured
in pixel aspect ratio. The simulation of the
limited bandwidth results into the
decreasing amount of bandwidth
availability. The traffic management is
difficult in managing the switching
between different ISP.
Solution: The management of the service
level agreement can resolve the issue of
bandwidth and the clear text transmission.
Connectivity requires high availability:
Amazon web services are used for
managing connection in the virtual private
cloud and the on-premises infrastructure.
The reliability and scalability of the
resources can be extended. The redundant
network connection with the AWS can be
managed with the following practices
Solution: “Dynamically routing the
multiple leveraging. The automatic
connection should be made with the
remote devices”[11] . The feasibility of the
private network can be ensured by the
AWS direct connect network service
providers. The dual vendor approach is
used for ensuring the diversity in private
network. The border gateway protocols
can be used for sending the traffic to the
remote data centres. The redundant
connection can be degraded by ensuring
the network capacity.
VI. Findings:
The issues which are associated with the
deployment of the VPN as discussed above
can be resolved with the deployment of
secure private network using MPLS. The
problem of latency and packet loss can be
resolved with the multiple accessing. It
helps in improving the quality of service
and reducing costs. The MPLS helps in
securing trusted devices, interface,
authentication of the routing protocol, link
separation, and authentication. The MPLS
VPN network helps in managing the
mapping between VPN and the user,
sharing of the server location, and
managing the security connection for
managing the remote access server with
the MPLS cloud. The following diagram
shows the multiple accessing using MPLS
VPN.
procedures can be used for
managing the connection between
cloud resources.
More bandwidth-intensive than clear
text transmission:
The allocated bandwidth is difficult to
examine. The simple testing procedures
are used for analysing the connection
speed of the network. The bit-rate and the
resolution of the device can be measured
in pixel aspect ratio. The simulation of the
limited bandwidth results into the
decreasing amount of bandwidth
availability. The traffic management is
difficult in managing the switching
between different ISP.
Solution: The management of the service
level agreement can resolve the issue of
bandwidth and the clear text transmission.
Connectivity requires high availability:
Amazon web services are used for
managing connection in the virtual private
cloud and the on-premises infrastructure.
The reliability and scalability of the
resources can be extended. The redundant
network connection with the AWS can be
managed with the following practices
Solution: “Dynamically routing the
multiple leveraging. The automatic
connection should be made with the
remote devices”[11] . The feasibility of the
private network can be ensured by the
AWS direct connect network service
providers. The dual vendor approach is
used for ensuring the diversity in private
network. The border gateway protocols
can be used for sending the traffic to the
remote data centres. The redundant
connection can be degraded by ensuring
the network capacity.
VI. Findings:
The issues which are associated with the
deployment of the VPN as discussed above
can be resolved with the deployment of
secure private network using MPLS. The
problem of latency and packet loss can be
resolved with the multiple accessing. It
helps in improving the quality of service
and reducing costs. The MPLS helps in
securing trusted devices, interface,
authentication of the routing protocol, link
separation, and authentication. The MPLS
VPN network helps in managing the
mapping between VPN and the user,
sharing of the server location, and
managing the security connection for
managing the remote access server with
the MPLS cloud. The following diagram
shows the multiple accessing using MPLS
VPN.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
The Service Level agreement should be
used to resolve the issues related to the
availability of the service and improving
the performance of the business according
to the changing requirement. The services
provided by the service level agreement
are availability of service, delay in the
round trip, loss of packet and jitter, mean
time repairing and delivery of service, and
improving the quality of service. The
MPLS VPN network helps in reducing the
cost and increasing the productivity of the
system because it does not require any
additional security system for securing the
premises. The MPLS VPN network is
capable of performing proactive network
monitoring. It works well as a logistic
service provider for managing delivery of
products on time, tracking of the products,
and others. The services provided by the
MPLS VPN are summarised in the table
below:
Services Descriptions
Mobility It helps in providing
mobile network
which helps in
retrieving relat status
of the information
Scalability Thousands of host
outlets can be
managed by the
MPLS VPN for
improving the
performance of the
system
Speedy It is successful in
minimizing the
latency period of the
network which helps
in increasing the
operational
efficiency of the
system.
Security The high security
procedures are
enabled in the MPLS
VPN which make
use of data
encryption
methodology,
isolation, tunnelling,
and etc.
Traffic engineering Optimizing the
distribution of the
traffic will result into
enhancing utilization
used to resolve the issues related to the
availability of the service and improving
the performance of the business according
to the changing requirement. The services
provided by the service level agreement
are availability of service, delay in the
round trip, loss of packet and jitter, mean
time repairing and delivery of service, and
improving the quality of service. The
MPLS VPN network helps in reducing the
cost and increasing the productivity of the
system because it does not require any
additional security system for securing the
premises. The MPLS VPN network is
capable of performing proactive network
monitoring. It works well as a logistic
service provider for managing delivery of
products on time, tracking of the products,
and others. The services provided by the
MPLS VPN are summarised in the table
below:
Services Descriptions
Mobility It helps in providing
mobile network
which helps in
retrieving relat status
of the information
Scalability Thousands of host
outlets can be
managed by the
MPLS VPN for
improving the
performance of the
system
Speedy It is successful in
minimizing the
latency period of the
network which helps
in increasing the
operational
efficiency of the
system.
Security The high security
procedures are
enabled in the MPLS
VPN which make
use of data
encryption
methodology,
isolation, tunnelling,
and etc.
Traffic engineering Optimizing the
distribution of the
traffic will result into
enhancing utilization

of the network.
Easy deployment The virtual IP
network make use of
IPSec in the
network
infrastructure.
Service level
agreement
The service level
agreement helps in
providing
availability, packet
loss, delivery of the
service, and jitter.
VII. Challenges and drawbacks:
In the deployment of the virtual private
network, there is some limitation which
should be looked. The security,
complexity, and performance are the issues
with the virtual private network. The
performance of the virtual private network
gets degraded and results into the failure of
network. The connectivity of the network
may results into the hacking attack. Man in
the middle attack is mainly associated with
the hijacking of the VPN. The remote
clients are used for managing connection
with the VPN which may result into the
man-in the middle attack. The authenticity
of the user should be established with the
management of the VPN otherwise the
third party can retrieve the confidential
information. The risks associated on the
client machine are broadband connection,
split tunnelling, and management of the
private network. The attack of malware
and viruses can affect the working of the
VPN. The interoperability between the
different units can be affected due to the
access right.
Solution:
The VPN can be secured by using the
secure authentication protocols which
makes use of strong passwords. The 256
bit encryption methodologies should be
used for allowing high internet speed. The
concept of direct access resolve the issues
related to the remote accessing of
information. The development of the
infrastructure cost can be reduced which is
capable of supporting remote user
population. It is the cost saving program
which reduces the administrative burden of
the VPN. Secure access appliances are
used for supporting the direct access of the
application. The problem of reliability and
availability of data can be resolved with
the deployment of secure private network.
The secure private network or MPLS
resolve the issues related to the external
and the online threats associated with the
traffic management. The secure private
network improves the performance of the
business critical operations. MPLS
resolves the issues of quality of service
Easy deployment The virtual IP
network make use of
IPSec in the
network
infrastructure.
Service level
agreement
The service level
agreement helps in
providing
availability, packet
loss, delivery of the
service, and jitter.
VII. Challenges and drawbacks:
In the deployment of the virtual private
network, there is some limitation which
should be looked. The security,
complexity, and performance are the issues
with the virtual private network. The
performance of the virtual private network
gets degraded and results into the failure of
network. The connectivity of the network
may results into the hacking attack. Man in
the middle attack is mainly associated with
the hijacking of the VPN. The remote
clients are used for managing connection
with the VPN which may result into the
man-in the middle attack. The authenticity
of the user should be established with the
management of the VPN otherwise the
third party can retrieve the confidential
information. The risks associated on the
client machine are broadband connection,
split tunnelling, and management of the
private network. The attack of malware
and viruses can affect the working of the
VPN. The interoperability between the
different units can be affected due to the
access right.
Solution:
The VPN can be secured by using the
secure authentication protocols which
makes use of strong passwords. The 256
bit encryption methodologies should be
used for allowing high internet speed. The
concept of direct access resolve the issues
related to the remote accessing of
information. The development of the
infrastructure cost can be reduced which is
capable of supporting remote user
population. It is the cost saving program
which reduces the administrative burden of
the VPN. Secure access appliances are
used for supporting the direct access of the
application. The problem of reliability and
availability of data can be resolved with
the deployment of secure private network.
The secure private network or MPLS
resolve the issues related to the external
and the online threats associated with the
traffic management. The secure private
network improves the performance of the
business critical operations. MPLS
resolves the issues of quality of service
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




