University Computer Networks and Cybersecurity Report, 2018
VerifiedAdded on 2023/06/03
|13
|2163
|176
Report
AI Summary
This report delves into the crucial topic of secure computer networks, focusing on the implementation of various control measures within an organization to mitigate potential threats. The report categorizes these controls into administrative, product, and physical types, further classifying their functions as preventive, detective, corrective, or compensatory. It addresses ten specific threat categories, including accidental information corruption, loss of intellectual property, software piracy, various forms of information theft, website defacement, equipment theft, and threats like viruses, privilege elevation, and fire/flood events. For each threat, the report outlines appropriate control strategies, providing detailed descriptions and classifications. The report emphasizes the importance of a risk-based approach to selecting and implementing these controls, highlighting the need for regular audits and updates to adapt to evolving threats and technologies. The conclusion underscores the necessity of a comprehensive threat protection and control system for organizational survival in the modern marketplace.

Running Head: SECURE COMPUTER NETWORKS 0
Secure Computer Networks
Computer Networks and Cyber security
(Student Details:)
10/12/2018
Secure Computer Networks
Computer Networks and Cyber security
(Student Details:)
10/12/2018
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Secure Computer Networks 1
Contents
Introduction................................................................................................................................2
Controlling threats to computer system security of an organization..........................................2
Type of controls.....................................................................................................................2
Conclusion................................................................................................................................10
Contents
Introduction................................................................................................................................2
Controlling threats to computer system security of an organization..........................................2
Type of controls.....................................................................................................................2
Conclusion................................................................................................................................10

Secure Computer Networks 2
Introduction
This report is describing various types of Control programs which should be used in an
organisation for effective operation. The main challenge for any organization is to define the
correct set of information and personnel security controls, that if get implemented and
defined to be effective in their application, mitigate the impact of each found threat.
Additionally, for each specified security class, a range of controls are essential for a complete
and strong security frame (Legg et al., 2015).
Moreover, the chief factor that will affect the selection of threat controls is a risk-based cost
or profit analysis (The Economic Times, 2018). Another factor includes ease of use,
compatibility with present controls, and transparency to operators. Thus, controls finding
action is an organizational wide exercise, which explains the protection necessities for the
diverse classes of info. However data as well as info owners are eventually accountable
persons for the accurate working of information security controls (Wall, 2018).
Controlling threats to computer system security of an organization
Type of controls
Three main types express the key goals of operative security implementation:
■ Physical Controls Security (PCS): control procedures, devices, and ways to control
physical entree to a definite system structure
■ Technical Controls Technology (TCT): control measures to control analytical access to
sensitive data
■ Administrative Controls: control policies, methods, and business processes to describe and
guide operator actions as well as restrictions while dealing with sensitive data
Moreover, above control actions can be further categorized into following:
■ Preventive controls limit the possibility of a threat by preventing intended or unintended
and unauthorized exposure of sensitive info.
■ Detective controls identify and report tried unauthorized attempts by anyone
Introduction
This report is describing various types of Control programs which should be used in an
organisation for effective operation. The main challenge for any organization is to define the
correct set of information and personnel security controls, that if get implemented and
defined to be effective in their application, mitigate the impact of each found threat.
Additionally, for each specified security class, a range of controls are essential for a complete
and strong security frame (Legg et al., 2015).
Moreover, the chief factor that will affect the selection of threat controls is a risk-based cost
or profit analysis (The Economic Times, 2018). Another factor includes ease of use,
compatibility with present controls, and transparency to operators. Thus, controls finding
action is an organizational wide exercise, which explains the protection necessities for the
diverse classes of info. However data as well as info owners are eventually accountable
persons for the accurate working of information security controls (Wall, 2018).
Controlling threats to computer system security of an organization
Type of controls
Three main types express the key goals of operative security implementation:
■ Physical Controls Security (PCS): control procedures, devices, and ways to control
physical entree to a definite system structure
■ Technical Controls Technology (TCT): control measures to control analytical access to
sensitive data
■ Administrative Controls: control policies, methods, and business processes to describe and
guide operator actions as well as restrictions while dealing with sensitive data
Moreover, above control actions can be further categorized into following:
■ Preventive controls limit the possibility of a threat by preventing intended or unintended
and unauthorized exposure of sensitive info.
■ Detective controls identify and report tried unauthorized attempts by anyone
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
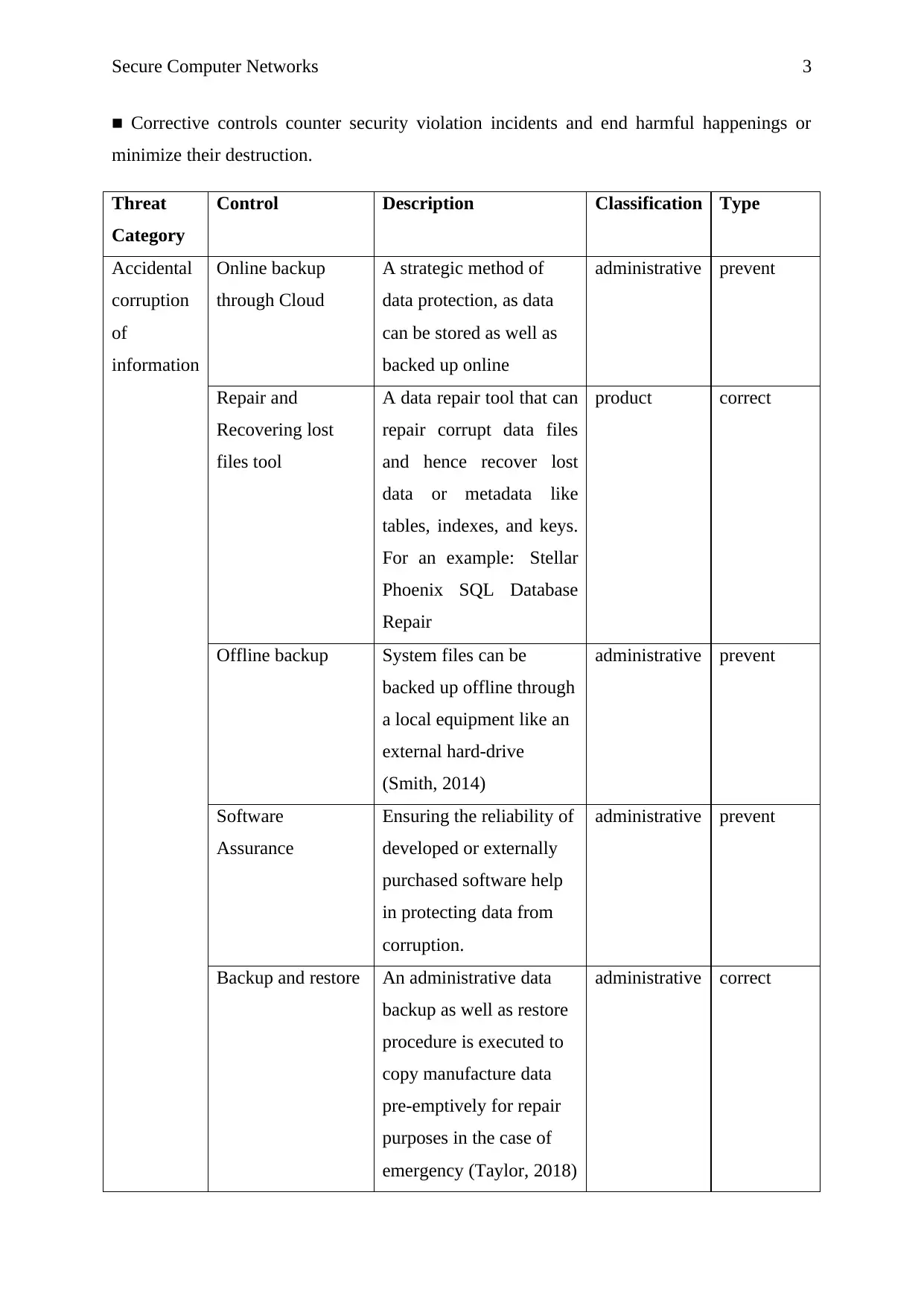
Secure Computer Networks 3
■ Corrective controls counter security violation incidents and end harmful happenings or
minimize their destruction.
Threat
Category
Control Description Classification Type
Accidental
corruption
of
information
Online backup
through Cloud
A strategic method of
data protection, as data
can be stored as well as
backed up online
administrative prevent
Repair and
Recovering lost
files tool
A data repair tool that can
repair corrupt data files
and hence recover lost
data or metadata like
tables, indexes, and keys.
For an example: Stellar
Phoenix SQL Database
Repair
product correct
Offline backup System files can be
backed up offline through
a local equipment like an
external hard-drive
(Smith, 2014)
administrative prevent
Software
Assurance
Ensuring the reliability of
developed or externally
purchased software help
in protecting data from
corruption.
administrative prevent
Backup and restore An administrative data
backup as well as restore
procedure is executed to
copy manufacture data
pre-emptively for repair
purposes in the case of
emergency (Taylor, 2018)
administrative correct
■ Corrective controls counter security violation incidents and end harmful happenings or
minimize their destruction.
Threat
Category
Control Description Classification Type
Accidental
corruption
of
information
Online backup
through Cloud
A strategic method of
data protection, as data
can be stored as well as
backed up online
administrative prevent
Repair and
Recovering lost
files tool
A data repair tool that can
repair corrupt data files
and hence recover lost
data or metadata like
tables, indexes, and keys.
For an example: Stellar
Phoenix SQL Database
Repair
product correct
Offline backup System files can be
backed up offline through
a local equipment like an
external hard-drive
(Smith, 2014)
administrative prevent
Software
Assurance
Ensuring the reliability of
developed or externally
purchased software help
in protecting data from
corruption.
administrative prevent
Backup and restore An administrative data
backup as well as restore
procedure is executed to
copy manufacture data
pre-emptively for repair
purposes in the case of
emergency (Taylor, 2018)
administrative correct
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
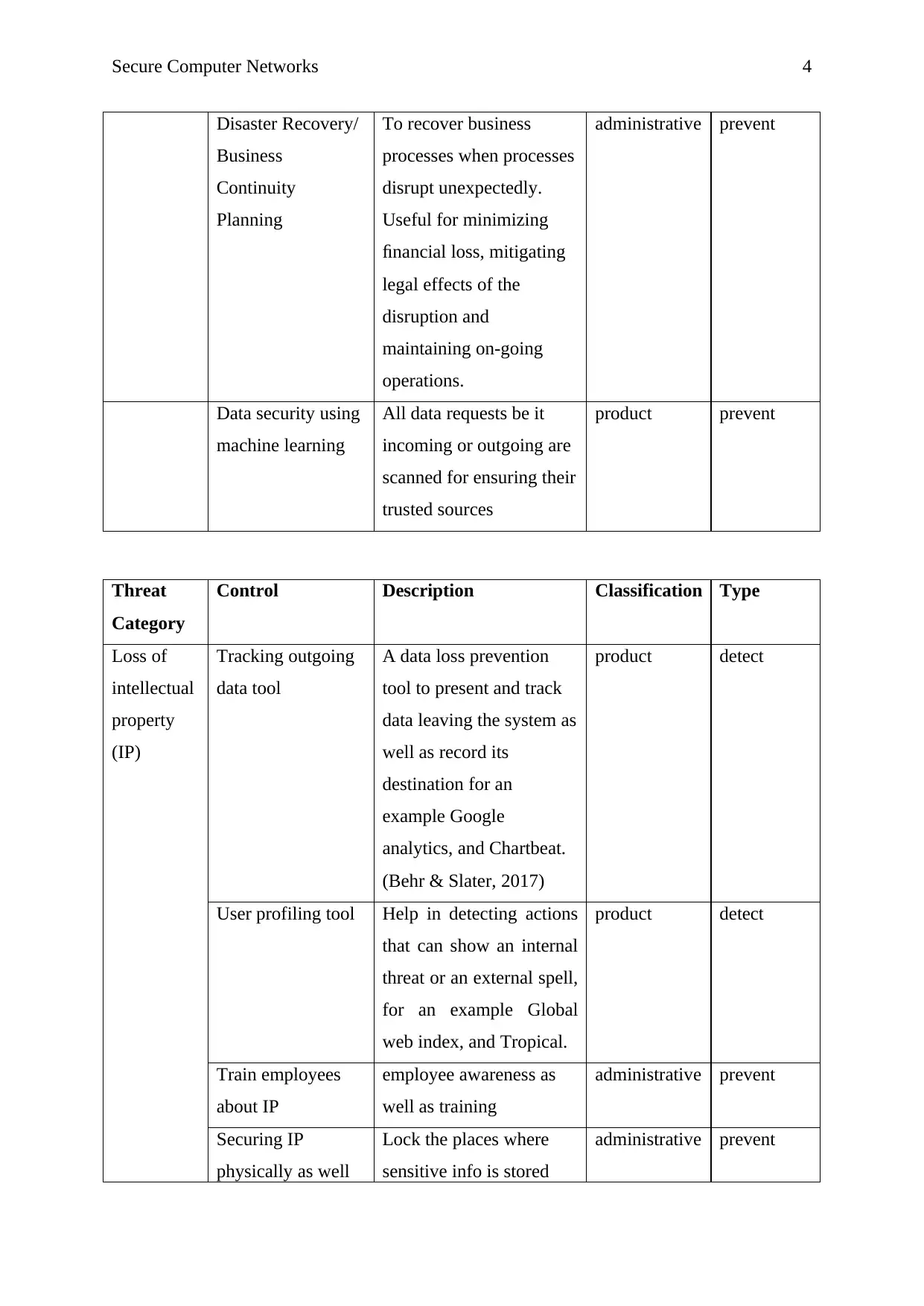
Secure Computer Networks 4
Disaster Recovery/
Business
Continuity
Planning
To recover business
processes when processes
disrupt unexpectedly.
Useful for minimizing
financial loss, mitigating
legal effects of the
disruption and
maintaining on-going
operations.
administrative prevent
Data security using
machine learning
All data requests be it
incoming or outgoing are
scanned for ensuring their
trusted sources
product prevent
Threat
Category
Control Description Classification Type
Loss of
intellectual
property
(IP)
Tracking outgoing
data tool
A data loss prevention
tool to present and track
data leaving the system as
well as record its
destination for an
example Google
analytics, and Chartbeat.
(Behr & Slater, 2017)
product detect
User profiling tool Help in detecting actions
that can show an internal
threat or an external spell,
for an example Global
web index, and Tropical.
product detect
Train employees
about IP
employee awareness as
well as training
administrative prevent
Securing IP
physically as well
Lock the places where
sensitive info is stored
administrative prevent
Disaster Recovery/
Business
Continuity
Planning
To recover business
processes when processes
disrupt unexpectedly.
Useful for minimizing
financial loss, mitigating
legal effects of the
disruption and
maintaining on-going
operations.
administrative prevent
Data security using
machine learning
All data requests be it
incoming or outgoing are
scanned for ensuring their
trusted sources
product prevent
Threat
Category
Control Description Classification Type
Loss of
intellectual
property
(IP)
Tracking outgoing
data tool
A data loss prevention
tool to present and track
data leaving the system as
well as record its
destination for an
example Google
analytics, and Chartbeat.
(Behr & Slater, 2017)
product detect
User profiling tool Help in detecting actions
that can show an internal
threat or an external spell,
for an example Global
web index, and Tropical.
product detect
Train employees
about IP
employee awareness as
well as training
administrative prevent
Securing IP
physically as well
Lock the places where
sensitive info is stored
administrative prevent
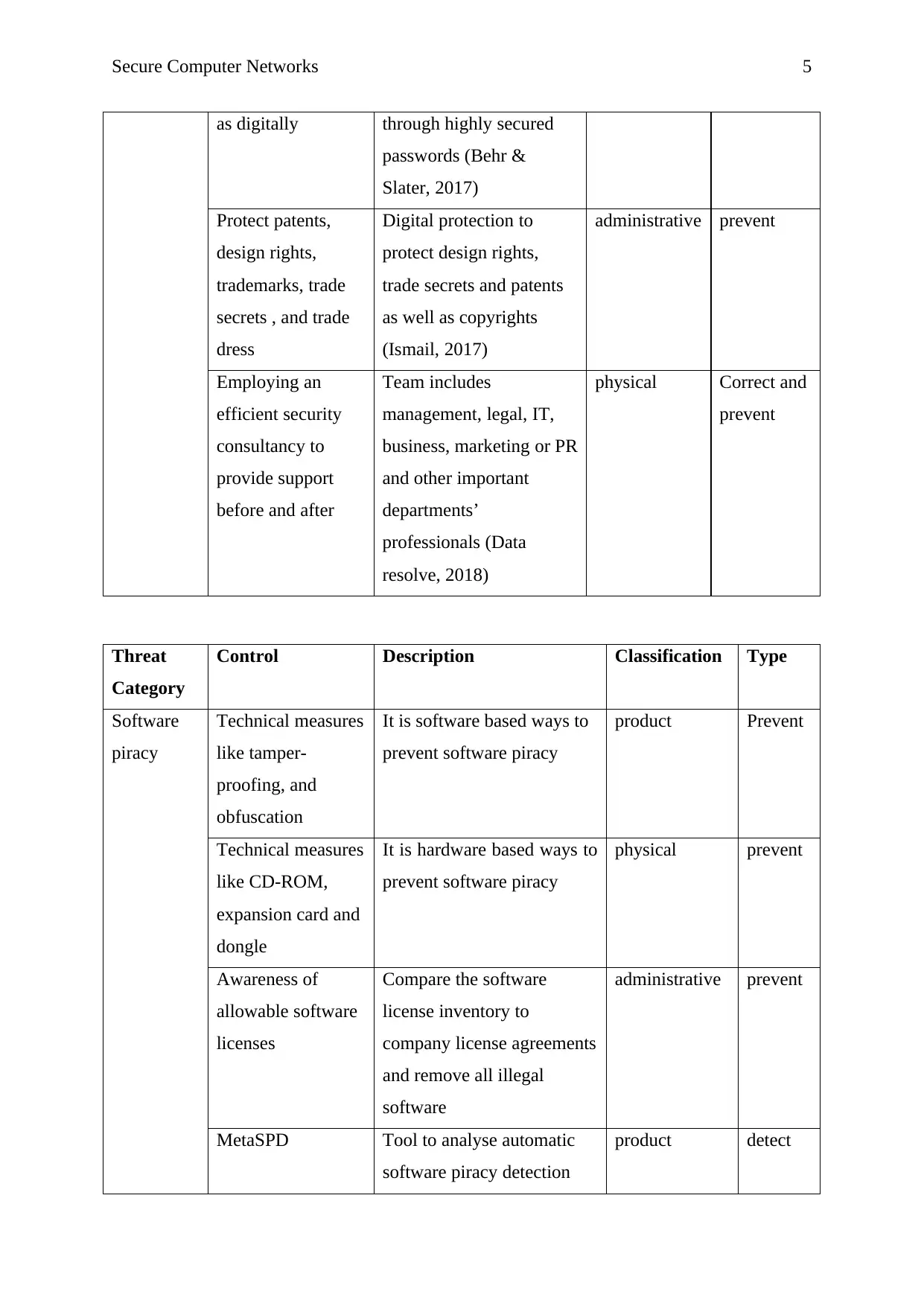
Secure Computer Networks 5
as digitally through highly secured
passwords (Behr &
Slater, 2017)
Protect patents,
design rights,
trademarks, trade
secrets , and trade
dress
Digital protection to
protect design rights,
trade secrets and patents
as well as copyrights
(Ismail, 2017)
administrative prevent
Employing an
efficient security
consultancy to
provide support
before and after
Team includes
management, legal, IT,
business, marketing or PR
and other important
departments’
professionals (Data
resolve, 2018)
physical Correct and
prevent
Threat
Category
Control Description Classification Type
Software
piracy
Technical measures
like tamper-
proofing, and
obfuscation
It is software based ways to
prevent software piracy
product Prevent
Technical measures
like CD-ROM,
expansion card and
dongle
It is hardware based ways to
prevent software piracy
physical prevent
Awareness of
allowable software
licenses
Compare the software
license inventory to
company license agreements
and remove all illegal
software
administrative prevent
MetaSPD Tool to analyse automatic
software piracy detection
product detect
as digitally through highly secured
passwords (Behr &
Slater, 2017)
Protect patents,
design rights,
trademarks, trade
secrets , and trade
dress
Digital protection to
protect design rights,
trade secrets and patents
as well as copyrights
(Ismail, 2017)
administrative prevent
Employing an
efficient security
consultancy to
provide support
before and after
Team includes
management, legal, IT,
business, marketing or PR
and other important
departments’
professionals (Data
resolve, 2018)
physical Correct and
prevent
Threat
Category
Control Description Classification Type
Software
piracy
Technical measures
like tamper-
proofing, and
obfuscation
It is software based ways to
prevent software piracy
product Prevent
Technical measures
like CD-ROM,
expansion card and
dongle
It is hardware based ways to
prevent software piracy
physical prevent
Awareness of
allowable software
licenses
Compare the software
license inventory to
company license agreements
and remove all illegal
software
administrative prevent
MetaSPD Tool to analyse automatic
software piracy detection
product detect
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
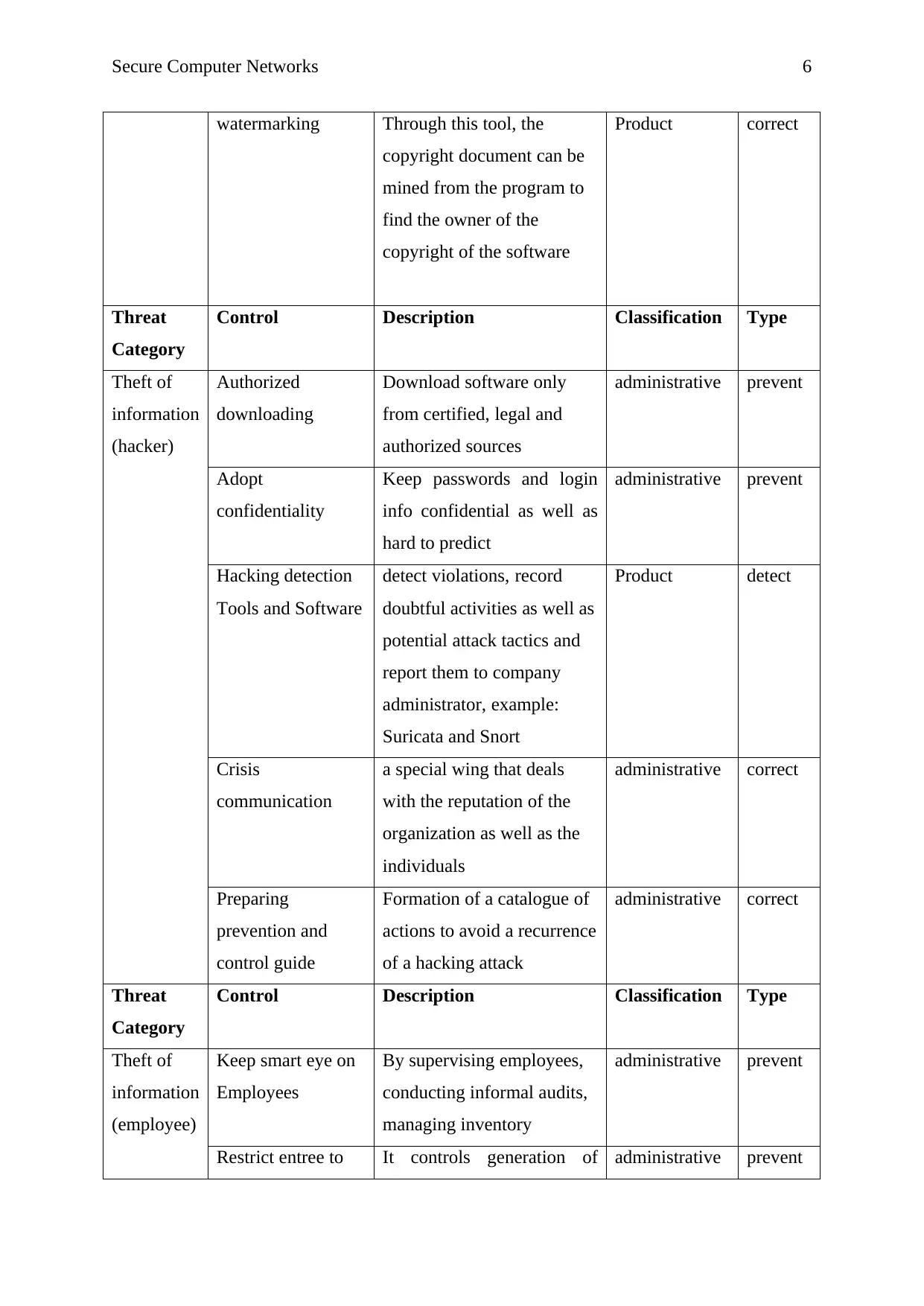
Secure Computer Networks 6
watermarking Through this tool, the
copyright document can be
mined from the program to
find the owner of the
copyright of the software
Product correct
Threat
Category
Control Description Classification Type
Theft of
information
(hacker)
Authorized
downloading
Download software only
from certified, legal and
authorized sources
administrative prevent
Adopt
confidentiality
Keep passwords and login
info confidential as well as
hard to predict
administrative prevent
Hacking detection
Tools and Software
detect violations, record
doubtful activities as well as
potential attack tactics and
report them to company
administrator, example:
Suricata and Snort
Product detect
Crisis
communication
a special wing that deals
with the reputation of the
organization as well as the
individuals
administrative correct
Preparing
prevention and
control guide
Formation of a catalogue of
actions to avoid a recurrence
of a hacking attack
administrative correct
Threat
Category
Control Description Classification Type
Theft of
information
(employee)
Keep smart eye on
Employees
By supervising employees,
conducting informal audits,
managing inventory
administrative prevent
Restrict entree to It controls generation of administrative prevent
watermarking Through this tool, the
copyright document can be
mined from the program to
find the owner of the
copyright of the software
Product correct
Threat
Category
Control Description Classification Type
Theft of
information
(hacker)
Authorized
downloading
Download software only
from certified, legal and
authorized sources
administrative prevent
Adopt
confidentiality
Keep passwords and login
info confidential as well as
hard to predict
administrative prevent
Hacking detection
Tools and Software
detect violations, record
doubtful activities as well as
potential attack tactics and
report them to company
administrator, example:
Suricata and Snort
Product detect
Crisis
communication
a special wing that deals
with the reputation of the
organization as well as the
individuals
administrative correct
Preparing
prevention and
control guide
Formation of a catalogue of
actions to avoid a recurrence
of a hacking attack
administrative correct
Threat
Category
Control Description Classification Type
Theft of
information
(employee)
Keep smart eye on
Employees
By supervising employees,
conducting informal audits,
managing inventory
administrative prevent
Restrict entree to It controls generation of administrative prevent
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Secure Computer Networks 7
computer terminals
as well as records
cash receipts, and installing
computer security measures
is done
Strong post theft
action taken by the
company
Identify the theft responsible
employee, dismiss their
employment and take further
legal action (Webroot
Smarter Cybersecurity,
2016)
administrative correct
forensic
accountants and
investigators
To legally counsel the
employees as well as
company management
physical correct
i-Sight
Investigation
Software
Establishing an Anonymous
reporting system or hotline
to detect employee fraud
Product detect
Threat
Category
Control Description Classification Type
Web site
defacement
web site
defacement
detection tools
To monitor websites
incoming and outgoing data
for its better security,
Example: SUCURI tool
Product detect
Regular security
audits and
penetration testing
evaluating the security of an
IT infrastructure, and better
protecting the system
technical incident
response team
Team include the security
manager, web masters or
web developers as well as
web server team
physical correct
Defender programs Protection against Cross-
Site Scripting (XSS) attacks,
and SQL injection attacks
Product prevent
Threat
Category
Control Description Classification Type
computer terminals
as well as records
cash receipts, and installing
computer security measures
is done
Strong post theft
action taken by the
company
Identify the theft responsible
employee, dismiss their
employment and take further
legal action (Webroot
Smarter Cybersecurity,
2016)
administrative correct
forensic
accountants and
investigators
To legally counsel the
employees as well as
company management
physical correct
i-Sight
Investigation
Software
Establishing an Anonymous
reporting system or hotline
to detect employee fraud
Product detect
Threat
Category
Control Description Classification Type
Web site
defacement
web site
defacement
detection tools
To monitor websites
incoming and outgoing data
for its better security,
Example: SUCURI tool
Product detect
Regular security
audits and
penetration testing
evaluating the security of an
IT infrastructure, and better
protecting the system
technical incident
response team
Team include the security
manager, web masters or
web developers as well as
web server team
physical correct
Defender programs Protection against Cross-
Site Scripting (XSS) attacks,
and SQL injection attacks
Product prevent
Threat
Category
Control Description Classification Type
Secure Computer Networks 8
Theft of
equipment
Identification
markings
Stamping, engraving,
etching, use of acid pens and
sandblasting on company’s
equipment can stop theft.
physical prevent
Physical restraints To lock important machines
or systems, and laptops
through mechanical locking
systems
Physical prevent
immobilisers To prevent unauthorized use
and moving of any
equipment
Physical prevent
Alarm and tracking
systems
To alert the management
regarding theft and
determine the position of the
theft equipment
physical correct
Testing as well as
certification
To certify anti-theft systems
by independent
organizations
Physical detect
Threat
Category
Control Description Classification Type
Viruses,
worms,
Trojan
horses
Antivirus packages running an updated antivirus
or antispyware scan
Product Detect
and
correct
disconnecting
network
Disconnect the network
from the infected machine
administrative correct
surf smart Safely surf and cope with
links, random files, ads, and
other free services on world
wide web
administrative prevent
Technical
safeguards
to manage and control data
flow amid different trusted
networks levels through
permitting, denying data,
product Prevent
and
detect
Theft of
equipment
Identification
markings
Stamping, engraving,
etching, use of acid pens and
sandblasting on company’s
equipment can stop theft.
physical prevent
Physical restraints To lock important machines
or systems, and laptops
through mechanical locking
systems
Physical prevent
immobilisers To prevent unauthorized use
and moving of any
equipment
Physical prevent
Alarm and tracking
systems
To alert the management
regarding theft and
determine the position of the
theft equipment
physical correct
Testing as well as
certification
To certify anti-theft systems
by independent
organizations
Physical detect
Threat
Category
Control Description Classification Type
Viruses,
worms,
Trojan
horses
Antivirus packages running an updated antivirus
or antispyware scan
Product Detect
and
correct
disconnecting
network
Disconnect the network
from the infected machine
administrative correct
surf smart Safely surf and cope with
links, random files, ads, and
other free services on world
wide web
administrative prevent
Technical
safeguards
to manage and control data
flow amid different trusted
networks levels through
permitting, denying data,
product Prevent
and
detect
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Secure Computer Networks 9
example: firewalls (Scitech
Connect Elsevier, 2013)
Backup and restore To restore infected system
so that harmful virus, worms
can be fully eliminated
administrative Prevent
and
correct
Threat
Category
Control Description Classification Type
Elevation
of privilege
thorough family,
education and
professional
screening over all
administrators
In order to confirm that they
are greatly trustworthy
administrative Prevent
and
detect
SID filtering Session identifiers filtering
to determine the present risk
level of the system
administrative prevent
Elevation of
Privilege (EoP)
Card Game
to create easy threat
modelling and accessible for
company developers and
architects
product Prevent
and
correct
Threat
Category
Control Description Classification Type
Fire/Flood Fire detection
alarms
They get automatically
activated during the fire
event
physical Detect
Fire suppression
equipment
To extinguish fire including
example: automatic
sprinklers.
physical correct
Fire exits Creation of escape exits;
with clear of obstructions
physical correct
Using fire resistant
materials
Improving impassive fire
precautions example: fire
resistant doors (Scitech
physical prevent
example: firewalls (Scitech
Connect Elsevier, 2013)
Backup and restore To restore infected system
so that harmful virus, worms
can be fully eliminated
administrative Prevent
and
correct
Threat
Category
Control Description Classification Type
Elevation
of privilege
thorough family,
education and
professional
screening over all
administrators
In order to confirm that they
are greatly trustworthy
administrative Prevent
and
detect
SID filtering Session identifiers filtering
to determine the present risk
level of the system
administrative prevent
Elevation of
Privilege (EoP)
Card Game
to create easy threat
modelling and accessible for
company developers and
architects
product Prevent
and
correct
Threat
Category
Control Description Classification Type
Fire/Flood Fire detection
alarms
They get automatically
activated during the fire
event
physical Detect
Fire suppression
equipment
To extinguish fire including
example: automatic
sprinklers.
physical correct
Fire exits Creation of escape exits;
with clear of obstructions
physical correct
Using fire resistant
materials
Improving impassive fire
precautions example: fire
resistant doors (Scitech
physical prevent
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Secure Computer Networks 10
Connect Elsevier, 2013)
Designated
personnel
to control emigration and to
co-ordinate with the
emergency actions
Physical correct
Designation of a
safe place
To evacuate company’s
people safely (Yeh &
Chang, 2007)
physical prevent
Conclusion
In conclusion, without having threats protection and control system no company can survive
in the marketplace. Additionally, the execution of effective controls as well as safeguards is
an on-going process, while the efficacy of controls at a particular point of time is the meter of
the overall secure information system. In order to react effectually on changing
vulnerabilities, business processes and conditions and new technologies, threats controlling
schemes are mandatory. Hence, above prevention, detection and compensation programs help
to audit, review, and update safeguards and controls on a routine basis for an organization.
Information system security controls are the product, technical, administrative, and physical
and policy defence tools designed to guard sensitive information. Thus, all organizations
should review and re-evaluate its information security controlling programs on a regular basis
to define any essential adjustments to any of its modules.
Connect Elsevier, 2013)
Designated
personnel
to control emigration and to
co-ordinate with the
emergency actions
Physical correct
Designation of a
safe place
To evacuate company’s
people safely (Yeh &
Chang, 2007)
physical prevent
Conclusion
In conclusion, without having threats protection and control system no company can survive
in the marketplace. Additionally, the execution of effective controls as well as safeguards is
an on-going process, while the efficacy of controls at a particular point of time is the meter of
the overall secure information system. In order to react effectually on changing
vulnerabilities, business processes and conditions and new technologies, threats controlling
schemes are mandatory. Hence, above prevention, detection and compensation programs help
to audit, review, and update safeguards and controls on a routine basis for an organization.
Information system security controls are the product, technical, administrative, and physical
and policy defence tools designed to guard sensitive information. Thus, all organizations
should review and re-evaluate its information security controlling programs on a regular basis
to define any essential adjustments to any of its modules.

Secure Computer Networks 11
References
Behr, & Slater, , 2017. How to protect intellectual property? 10 tips to keep IP safe. [Online]
Available at: https://www.csoonline.com/article/2138380/loss-prevention/how-to-protect-
intellectual-property-10-tips-to-keep-ip-safe.html [Accessed 12 October 2018].
Data resolve, 2018. Intellectual Property Theft Solutions. [Online] Available at:
https://www.dataresolve.com/intellectual-property-theft.php [Accessed 13 October 2018].
Ismail, N., 2017. 7 nightmare cyber security threats to SMEs and how to secure against them.
[Online] Available at: https://www.information-age.com/7-nightmare-cyber-security-threats-
smes-secure-123466495/ [Accessed 12 October 2018].
Legg, S.J., Olsen, K.B., Laird, I.S. & Hasle, P., 2015. Managing safety in small and medium
enterprises. Safety Science, 71(Part C), pp.189-96.
Scitech Connect Elsevier, 2013. Controls and Safeguards. [Online] Available at:
http://scitechconnect.elsevier.com/wp-content/uploads/2013/09/Controls-and-Safeguards.pdf
[Accessed 12 October 2018].
Smith, , 2014. What is Data corruption and how to prevent it. [Online] Available at:
https://www.makeuseof.com/tag/data-corruption-prevent/ [Accessed 12 October 2018].
Taylor, T., 2018. ALL IS NOT LOST: DEALING WITH DATA CORRUPTION AT YOUR
ORGANIZATION. [Online] Available at: http://techgenix.com/dealing-with-data-corruption/
[Accessed 12 October 2018].
The Economic Times, 2018. 5 simple tips to keep your business secure from cyberattacks.
[Online] Available at:
https://economictimes.indiatimes.com/small-biz/security-tech/security/5-simple-tips-to-keep-
your-business-secure-from-cyberattacks/articleshow/64568063.cms [Accessed 12 October
2018].
Wall, E., 2018. Cyber security threats and provisions for SMEs. [Online] Available at:
https://www.itproportal.com/features/cyber-security-threats-and-provisions-for-smes/
[Accessed 12 October 2018].
References
Behr, & Slater, , 2017. How to protect intellectual property? 10 tips to keep IP safe. [Online]
Available at: https://www.csoonline.com/article/2138380/loss-prevention/how-to-protect-
intellectual-property-10-tips-to-keep-ip-safe.html [Accessed 12 October 2018].
Data resolve, 2018. Intellectual Property Theft Solutions. [Online] Available at:
https://www.dataresolve.com/intellectual-property-theft.php [Accessed 13 October 2018].
Ismail, N., 2017. 7 nightmare cyber security threats to SMEs and how to secure against them.
[Online] Available at: https://www.information-age.com/7-nightmare-cyber-security-threats-
smes-secure-123466495/ [Accessed 12 October 2018].
Legg, S.J., Olsen, K.B., Laird, I.S. & Hasle, P., 2015. Managing safety in small and medium
enterprises. Safety Science, 71(Part C), pp.189-96.
Scitech Connect Elsevier, 2013. Controls and Safeguards. [Online] Available at:
http://scitechconnect.elsevier.com/wp-content/uploads/2013/09/Controls-and-Safeguards.pdf
[Accessed 12 October 2018].
Smith, , 2014. What is Data corruption and how to prevent it. [Online] Available at:
https://www.makeuseof.com/tag/data-corruption-prevent/ [Accessed 12 October 2018].
Taylor, T., 2018. ALL IS NOT LOST: DEALING WITH DATA CORRUPTION AT YOUR
ORGANIZATION. [Online] Available at: http://techgenix.com/dealing-with-data-corruption/
[Accessed 12 October 2018].
The Economic Times, 2018. 5 simple tips to keep your business secure from cyberattacks.
[Online] Available at:
https://economictimes.indiatimes.com/small-biz/security-tech/security/5-simple-tips-to-keep-
your-business-secure-from-cyberattacks/articleshow/64568063.cms [Accessed 12 October
2018].
Wall, E., 2018. Cyber security threats and provisions for SMEs. [Online] Available at:
https://www.itproportal.com/features/cyber-security-threats-and-provisions-for-smes/
[Accessed 12 October 2018].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





