Computer and Networks Security: Self-Testing Kits and Hospital Data
VerifiedAdded on 2023/06/03
|17
|4086
|432
Report
AI Summary
This report delves into the security vulnerabilities associated with self-testing kits and centralized hospital data systems. It highlights risks such as data breaches, denial-of-service attacks, and unauthorized access to patient information. The report analyzes these threats using the STRIDE methodology and assesses the impact of risks based on factors such as damage potential and exploitability through the DREAD framework. It examines the characteristics of hospital databases, including data flow and critical security measures. The report concludes by suggesting mitigation strategies, including encryption, authentication, and secure design specifications for self-testing kits and the overall system. The student emphasizes the importance of embracing self-testing kits while addressing and mitigating their inherent security risks.

Computer and Networks Security 1
University
Student’s name
Course
Date
1
University
Student’s name
Course
Date
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer and Networks Security 2
Abstract
The following is a report that highlights the threats and risks that arise from using self-testing kits and
a centralized system to manage patient data. The report highlights the vulnerabilities that may arise from
setting up centralized systems in the medical field. Several threats have been identified including; the risk
of leaking patient information to third parties, loss of data and denial of service attacks leading to users of
the system experiencing delays in accessing the system. The impact of these risks are highlighted on a
scale depending on factors such as; the ease at which an attack can occur, the number of people affected
plus the amount of resources needed to recover the loss. The report concludes by suggesting various
alternatives to mitigate the risks such as applying encryption and authentication measures on the kits and
the centralized system. Self-testing kits are an emerging technology that should be embraced and not
discouraged due to the risks that lurk from using them.
2
Abstract
The following is a report that highlights the threats and risks that arise from using self-testing kits and
a centralized system to manage patient data. The report highlights the vulnerabilities that may arise from
setting up centralized systems in the medical field. Several threats have been identified including; the risk
of leaking patient information to third parties, loss of data and denial of service attacks leading to users of
the system experiencing delays in accessing the system. The impact of these risks are highlighted on a
scale depending on factors such as; the ease at which an attack can occur, the number of people affected
plus the amount of resources needed to recover the loss. The report concludes by suggesting various
alternatives to mitigate the risks such as applying encryption and authentication measures on the kits and
the centralized system. Self-testing kits are an emerging technology that should be embraced and not
discouraged due to the risks that lurk from using them.
2

Computer and Networks Security 3
Table of Contents
Introduction...............................................................................................................................................4
Threats and Risks of Self-Testing Kits and the hospital database.....................................................4
Characteristics of the Hospital database and the data flow...............................................................5
Threat analysis of the self-testing systems...........................................................................................7
Criteria used to rate the risks In the DREAD and STRIDE analysis................................................7
The risk analysis of the self-testing kits system.................................................................................13
Secure design specification for self-testing kits.................................................................................14
Conclusion and Recommendation......................................................................................................15
References.................................................................................................................................................17
3
Table of Contents
Introduction...............................................................................................................................................4
Threats and Risks of Self-Testing Kits and the hospital database.....................................................4
Characteristics of the Hospital database and the data flow...............................................................5
Threat analysis of the self-testing systems...........................................................................................7
Criteria used to rate the risks In the DREAD and STRIDE analysis................................................7
The risk analysis of the self-testing kits system.................................................................................13
Secure design specification for self-testing kits.................................................................................14
Conclusion and Recommendation......................................................................................................15
References.................................................................................................................................................17
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Computer and Networks Security 4
Introduction
Self-medical testing kits are becoming common among users these days. The
devices help in diagnosing a patient and provide the status of their medical condition. Not only
are they beneficial to the users but also assist doctors by reducing their workload of conducting a
diagnosis on multiple patients and tracking their patients’ health (Shadbolt, 2015). With the rise
in technology, self-testing kits are also advancing in their design and properties. The gadgets can
now conduct a diagnosis on the patient and provide an output of numerous medical conditions
from just one blood test. The results of the tests can also be shared with health professionals by
the users. However, this advancement also creates a risk on the data that is transmitted through
the kits (Guise, et al, 2018).Red ozone kits are an example of self-testing kits. Hospitals are using
centralized systems to manage their data. Patients can connect to the hospital server remotely
through their user accounts. The results will be known to the user within few minutes once the
results are known by the doctor or when the sample is sent to the laboratory. The user will be
notified via text message in the phone and will also receive a message in the online portal and in
the Red-ozone kit. Red ozone can now conduct a diagnosis on the patient and provide an output
of numerous medical conditions from just one blood test. The results of these tests can also be
shared with health professionals by the users.
The following functionality is expected to be included in the Red ozone kits which are
considered as minimum system requirements:
● The information of the patients can be viewed using apps in different platforms like iOS,
Android and also on the online portal using the login details through the Red ozone
website.
● The sample of the blood test should only be sent from the Red ozone kit which can be
logged in using the fingerprints or the password.
● The health details are obtained from the blood sampling and performing the
measurements, and uploading it to the centralized system securely. The health records
and condition of the patients should be immutable, but reviewable by health professionals
and users.
● Doctors can refer the blood sample to the laboratories for further investigation of the
sample through their online portal and
4
Introduction
Self-medical testing kits are becoming common among users these days. The
devices help in diagnosing a patient and provide the status of their medical condition. Not only
are they beneficial to the users but also assist doctors by reducing their workload of conducting a
diagnosis on multiple patients and tracking their patients’ health (Shadbolt, 2015). With the rise
in technology, self-testing kits are also advancing in their design and properties. The gadgets can
now conduct a diagnosis on the patient and provide an output of numerous medical conditions
from just one blood test. The results of the tests can also be shared with health professionals by
the users. However, this advancement also creates a risk on the data that is transmitted through
the kits (Guise, et al, 2018).Red ozone kits are an example of self-testing kits. Hospitals are using
centralized systems to manage their data. Patients can connect to the hospital server remotely
through their user accounts. The results will be known to the user within few minutes once the
results are known by the doctor or when the sample is sent to the laboratory. The user will be
notified via text message in the phone and will also receive a message in the online portal and in
the Red-ozone kit. Red ozone can now conduct a diagnosis on the patient and provide an output
of numerous medical conditions from just one blood test. The results of these tests can also be
shared with health professionals by the users.
The following functionality is expected to be included in the Red ozone kits which are
considered as minimum system requirements:
● The information of the patients can be viewed using apps in different platforms like iOS,
Android and also on the online portal using the login details through the Red ozone
website.
● The sample of the blood test should only be sent from the Red ozone kit which can be
logged in using the fingerprints or the password.
● The health details are obtained from the blood sampling and performing the
measurements, and uploading it to the centralized system securely. The health records
and condition of the patients should be immutable, but reviewable by health professionals
and users.
● Doctors can refer the blood sample to the laboratories for further investigation of the
sample through their online portal and
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer and Networks Security 5
● The user can also enter various notes, for instance, other health conditions along the
blood sample, allowing to edit or delete the notes only by the user, but doctors and users
can view them.
The different functionality of the Red ozone kits mentioned above means that there are also
threats to the system which the company and user must defend against. Red-ozone have great
benefits but can some time cause distress by false-positive results. However, the
advancement on the kit also creates risk on the data that is transmitted through the kits.
Background Research:
1.Theranos: It has two component one is blood collection vessel “nanotainer” and analysis
machine “Edison” which could be used to test the conditions such as cancer and cholesterol. It
only uses few drops from a finger-prick rather than using a needle to take blood from a vein.
2.Selphi: Selphi allows user to their own blood sample and performs a simple test then reads
their own result. Its test for HIV. Selphi does not give a positive diagnosis, the self-tests with
positive result must be confirmed by a doctor. Therefore, the results from such devices would not
misguide the user as the results has to be confirmed by the doctors.
Threats and Risks of Self-Testing Kits and the hospital database
As more people acquire the kits so does the amount of data that is held and transmitted by the
gadgets and its underlying infrastructure increase. Emerging self-testing kits allow one to share the results
of their diagnosis with their doctors on a real time basis. This means that doctors gain access to the health
records of their patients on a virtual space that stores all the information. The number of tests done by the
users also allows the devices to monitor the well-being of the patient as it records each time a user
conducts a diagnosis and the results from the test.. The hospitals use a centralized database to store data.
A centralized system uses a single resource as the main server to store and retrieve all the information
regarding the operations of an institution (R.King, 2018). This creates certain threats and risks that arise
from implementing one server to run all operations (Chegg Study, 2018) . Information based on facts
such as the number of interactions between the patient and provider and other important information such
as the outcomes of a diagnosis or the health status and the healthy plan to be followed by a patient has to
be updated frequently allowing its timely use and analysis. This will allow the databases and network of
5
● The user can also enter various notes, for instance, other health conditions along the
blood sample, allowing to edit or delete the notes only by the user, but doctors and users
can view them.
The different functionality of the Red ozone kits mentioned above means that there are also
threats to the system which the company and user must defend against. Red-ozone have great
benefits but can some time cause distress by false-positive results. However, the
advancement on the kit also creates risk on the data that is transmitted through the kits.
Background Research:
1.Theranos: It has two component one is blood collection vessel “nanotainer” and analysis
machine “Edison” which could be used to test the conditions such as cancer and cholesterol. It
only uses few drops from a finger-prick rather than using a needle to take blood from a vein.
2.Selphi: Selphi allows user to their own blood sample and performs a simple test then reads
their own result. Its test for HIV. Selphi does not give a positive diagnosis, the self-tests with
positive result must be confirmed by a doctor. Therefore, the results from such devices would not
misguide the user as the results has to be confirmed by the doctors.
Threats and Risks of Self-Testing Kits and the hospital database
As more people acquire the kits so does the amount of data that is held and transmitted by the
gadgets and its underlying infrastructure increase. Emerging self-testing kits allow one to share the results
of their diagnosis with their doctors on a real time basis. This means that doctors gain access to the health
records of their patients on a virtual space that stores all the information. The number of tests done by the
users also allows the devices to monitor the well-being of the patient as it records each time a user
conducts a diagnosis and the results from the test.. The hospitals use a centralized database to store data.
A centralized system uses a single resource as the main server to store and retrieve all the information
regarding the operations of an institution (R.King, 2018). This creates certain threats and risks that arise
from implementing one server to run all operations (Chegg Study, 2018) . Information based on facts
such as the number of interactions between the patient and provider and other important information such
as the outcomes of a diagnosis or the health status and the healthy plan to be followed by a patient has to
be updated frequently allowing its timely use and analysis. This will allow the databases and network of
5

Computer and Networks Security 6
the hospital to assist directly in the patient care. Centralized systems are sometimes incapable of
sustaining real time input and retrieve of data. The servers might be overwhelmed by the number of
transactions occurring if users are many. Users will experience delays in accessing the resources of the
database due to multiple requests being made at the same time. This leads to patients and doctors alike
adding and retrieving relevant information when it is already late. If information is not sufficiently up to
date, care providers cannot fully rely on it while making clinical decisions.
Characteristics of the Hospital database and the data flow
The database needs to have the ability to analyze patterns, the quality and cost of care. This is
very important for the users who will benefit in knowing their progress on matters health over a period of
time. Patients may wish to create a profile highlighting their episodes of care or develop any other
relevant information related to their profile. Important issues such as all the care provided to a certain
patient for a particular disease or injury needs to be available. Data that is used for clinical care needs to
be accurate and complete. The information describing a particular patient needs to only describe the
individual and do so accurately. Out of date data and records that commingle files mixing up data can
lead to harm. The system should also allow one to correct errors identified later.
Unique universal person-identifiers will be part of the hospital database. They apply to only one person
and are not changed overtime. Health insurers, entitlement products and plans assign identifiers, the
health providers also assign identifiers to their patients. This is in the form of a medical record or account
number which are not used beyond the hospital or specific provider.
The hospitals, physicians, pharmacies, public program offices, patients and offices generate input to the
database, connecting them through a network. The databases in the data networks is connected by various
physical arrangements including; local-area networks, public-switched network and wide area networks.
The data network allows for health records to be moved beyond the care setting from which it was
generated plus allows for persons to be identified and person- identifiable data. The health database
organization, which refers to any entity that has access to the hospital database has crucial characteristics.
Some devices have the capacity to control a number of resources on the network. They acquire and hold
information from a wide range of sources in the health field. Sources like; physicians in private practice,
institutions and facilities, providers such as pharmacies plus clinics and agencies. Information that goes
beyond the health sector might also be added to the database network such as the individuals that are
covered by an insurance plan. The health database organization will update information within periods
that range from hourly to weekly or monthly. It should also add data on case-specific basis such as all
patients diagnosed with a certain disease or all the type of providers in the health facility.
6
the hospital to assist directly in the patient care. Centralized systems are sometimes incapable of
sustaining real time input and retrieve of data. The servers might be overwhelmed by the number of
transactions occurring if users are many. Users will experience delays in accessing the resources of the
database due to multiple requests being made at the same time. This leads to patients and doctors alike
adding and retrieving relevant information when it is already late. If information is not sufficiently up to
date, care providers cannot fully rely on it while making clinical decisions.
Characteristics of the Hospital database and the data flow
The database needs to have the ability to analyze patterns, the quality and cost of care. This is
very important for the users who will benefit in knowing their progress on matters health over a period of
time. Patients may wish to create a profile highlighting their episodes of care or develop any other
relevant information related to their profile. Important issues such as all the care provided to a certain
patient for a particular disease or injury needs to be available. Data that is used for clinical care needs to
be accurate and complete. The information describing a particular patient needs to only describe the
individual and do so accurately. Out of date data and records that commingle files mixing up data can
lead to harm. The system should also allow one to correct errors identified later.
Unique universal person-identifiers will be part of the hospital database. They apply to only one person
and are not changed overtime. Health insurers, entitlement products and plans assign identifiers, the
health providers also assign identifiers to their patients. This is in the form of a medical record or account
number which are not used beyond the hospital or specific provider.
The hospitals, physicians, pharmacies, public program offices, patients and offices generate input to the
database, connecting them through a network. The databases in the data networks is connected by various
physical arrangements including; local-area networks, public-switched network and wide area networks.
The data network allows for health records to be moved beyond the care setting from which it was
generated plus allows for persons to be identified and person- identifiable data. The health database
organization, which refers to any entity that has access to the hospital database has crucial characteristics.
Some devices have the capacity to control a number of resources on the network. They acquire and hold
information from a wide range of sources in the health field. Sources like; physicians in private practice,
institutions and facilities, providers such as pharmacies plus clinics and agencies. Information that goes
beyond the health sector might also be added to the database network such as the individuals that are
covered by an insurance plan. The health database organization will update information within periods
that range from hourly to weekly or monthly. It should also add data on case-specific basis such as all
patients diagnosed with a certain disease or all the type of providers in the health facility.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
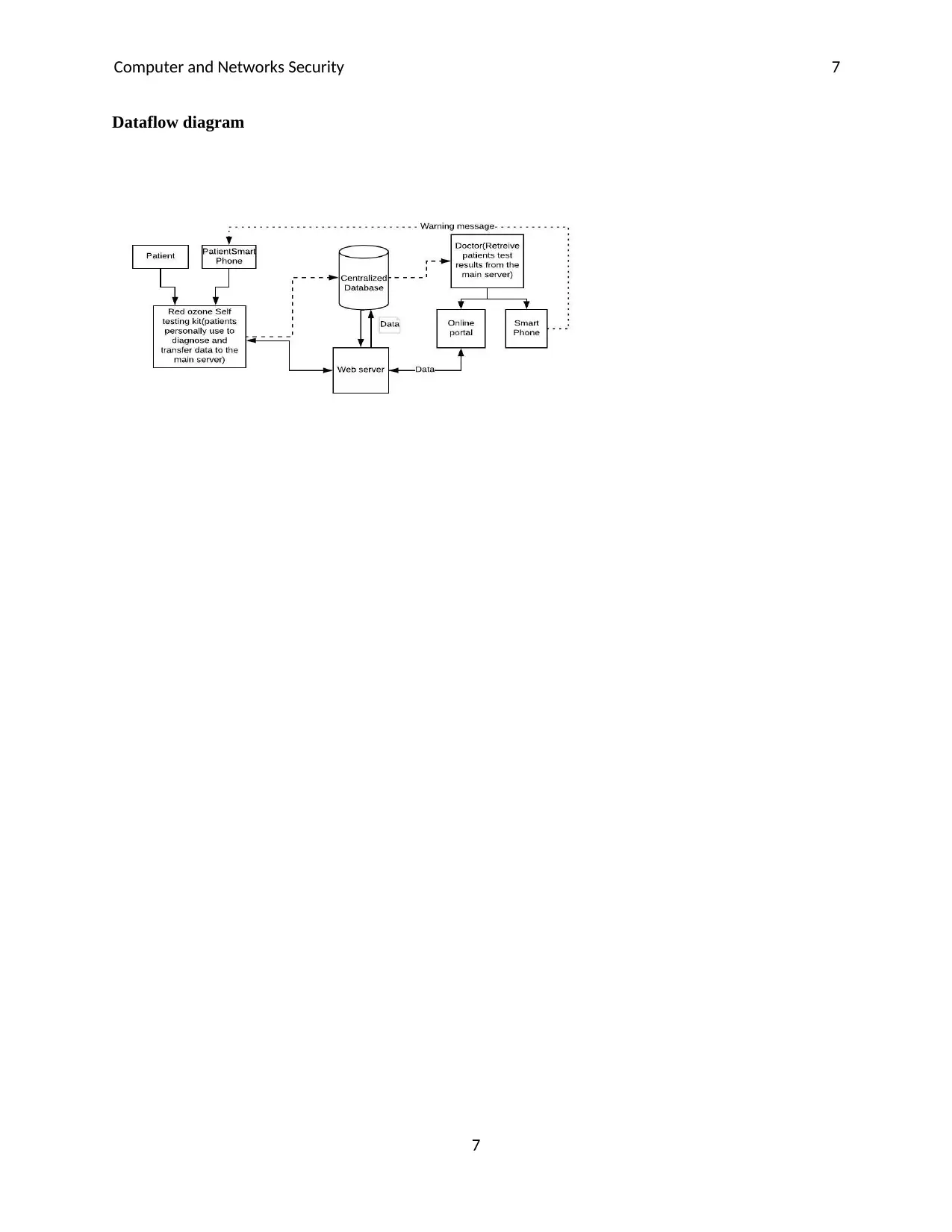
Computer and Networks Security 7
Dataflow diagram
7
Dataflow diagram
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer and Networks Security 8
Threat analysis of the self-testing systems
While conducting a threat analysis of the system, the STRIDE technique is used to identify the threats
that a system poses on users’ information and any data stored within the system. The technique developed
by Microsoft helps in creating a clear picture of the threats that lurk within the system. STRIDE is an
acronym that stands for spoofing, Tampering, Repudiation, Information disclosure and Denial of service
(Moffa, Tyco & Security, 2018).
Criteria used to rate the risks In the DREAD and STRIDE analysis
Damage potential: 0-3 leaking non-health data 4-6 leaking trivial information 7-10 Leaking sensitive
information by bypassing administrative levels
Reproducibility: 0-2-very difficult to reproduce 2-4 requires multiple steps to reproduce 5-7 three step
procedure to reproduce damage 8-10 only a web browser needed
Exploitability 0-3 requires technical skill to implement 4-6 the threat can be automated 7-10 requires a
novice programmer
Affected users: 0-3 few users 4-6 some users 7-10 majority or all users
Discoverability: 0-3 very unlikely to discover 4-6 only few users have access 7-10 it is published
Spoofing refers to an attack whereby the attacker poses as an authorized user of the system and is able to
gain access to the system’s resources by providing false credentials or overriding the login procedure.
This will lead the system to interact with the attacker as it would normally do with authorized individuals
who have access to the system.
Item network
Title Illegal access to the database
Application Operating System
Threat target Data on the server
Threat Type Spoofing
Risk The damage may be patient information is leaked to the public violating their
privacy(10)
8
Threat analysis of the self-testing systems
While conducting a threat analysis of the system, the STRIDE technique is used to identify the threats
that a system poses on users’ information and any data stored within the system. The technique developed
by Microsoft helps in creating a clear picture of the threats that lurk within the system. STRIDE is an
acronym that stands for spoofing, Tampering, Repudiation, Information disclosure and Denial of service
(Moffa, Tyco & Security, 2018).
Criteria used to rate the risks In the DREAD and STRIDE analysis
Damage potential: 0-3 leaking non-health data 4-6 leaking trivial information 7-10 Leaking sensitive
information by bypassing administrative levels
Reproducibility: 0-2-very difficult to reproduce 2-4 requires multiple steps to reproduce 5-7 three step
procedure to reproduce damage 8-10 only a web browser needed
Exploitability 0-3 requires technical skill to implement 4-6 the threat can be automated 7-10 requires a
novice programmer
Affected users: 0-3 few users 4-6 some users 7-10 majority or all users
Discoverability: 0-3 very unlikely to discover 4-6 only few users have access 7-10 it is published
Spoofing refers to an attack whereby the attacker poses as an authorized user of the system and is able to
gain access to the system’s resources by providing false credentials or overriding the login procedure.
This will lead the system to interact with the attacker as it would normally do with authorized individuals
who have access to the system.
Item network
Title Illegal access to the database
Application Operating System
Threat target Data on the server
Threat Type Spoofing
Risk The damage may be patient information is leaked to the public violating their
privacy(10)
8
Computer and Networks Security 9
To reproduce the attack, one would have to acquire multiple provider login
credentials to gain access to many patients’ data(5)
To exploit one would have to be experienced and skilled in programming to be
able to bypass the database account login protocols(4)
The affected users would be the patients and doctors whose data confidentiality
is exposed. (9)
To discover the vulnerability will require strong security measures and skilled
personnel to find out the source of attack.(5)
Risk rating 7
Secure Design
recommendations
Applying strong encryption measures throughout the network and having all
authorized users set up strong passwords that are changed often.
Tampering on the other hand refers to attempts by an attacker to change the data that is transmitted
between applications and approved users.
Item Data
Title Altering patient data
Application Operating System
Threat Target Wireless connections
Threat type Tampering
Risk The damage could be patient data is taken and edited leading to doctors getting
the wrong information which could lead them to administer wrong treatment(5)
To reproduce the attacker requires to gain access to the network so as to get to
the central server(6)
To exploit the attacker needs to have permissions of editing data on the network
plus information on the encryption measures implemented on the self-testing kits
system(4)
The affected users would be the patients health whose test results are altered
also the doctors who get the wrong information(5)
It could be difficult to discover the vulnerability especially in instances where
strong encryption measures are in place(6)
Risk rating 8
Secure design Having end to end encryption of all the messages and data sent among patients
9
To reproduce the attack, one would have to acquire multiple provider login
credentials to gain access to many patients’ data(5)
To exploit one would have to be experienced and skilled in programming to be
able to bypass the database account login protocols(4)
The affected users would be the patients and doctors whose data confidentiality
is exposed. (9)
To discover the vulnerability will require strong security measures and skilled
personnel to find out the source of attack.(5)
Risk rating 7
Secure Design
recommendations
Applying strong encryption measures throughout the network and having all
authorized users set up strong passwords that are changed often.
Tampering on the other hand refers to attempts by an attacker to change the data that is transmitted
between applications and approved users.
Item Data
Title Altering patient data
Application Operating System
Threat Target Wireless connections
Threat type Tampering
Risk The damage could be patient data is taken and edited leading to doctors getting
the wrong information which could lead them to administer wrong treatment(5)
To reproduce the attacker requires to gain access to the network so as to get to
the central server(6)
To exploit the attacker needs to have permissions of editing data on the network
plus information on the encryption measures implemented on the self-testing kits
system(4)
The affected users would be the patients health whose test results are altered
also the doctors who get the wrong information(5)
It could be difficult to discover the vulnerability especially in instances where
strong encryption measures are in place(6)
Risk rating 8
Secure design Having end to end encryption of all the messages and data sent among patients
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Computer and Networks Security
10
recommendations and doctors.
Repudiation means actions being done by users of the system cannot be attributed. If a legitimate user
within the system does a wrong action, the user can deny the truth of their actions.
Item Network
Title Denial of actions conducted within the system by users
Application Operating System
Threat Target Network devices
Threat Type Repudiation
Risk The damage would be high as patient’s health is at risk if a doctor denies
administering wrong treatment to the patient via the network.(7)
The attack would be reproduced if the system has less techniques in storing
and retrieving events conducted on the network(6)
The exploitation of this attack is possible if policies are not set to monitor the
standards of practitioners and providers in their duties on the system.(6)
The affected users would be patients and doctors too(5)
It is easy to discover if the network and servers have techniques of collecting
and storing events.(4)
Risk Rating 6
Secure design
Recommendations
Set up policies and standards that will guide users of the network on their actions
within the system, the policies should include the legal procedures that are
followed if found to be sending wrong data or information.
Information Disclosure can be described as breach of data by an attacker and is able to gain access to
private information.
Item Information
Title Illegal access to data
Application Operating System
Threat Target Patients and Doctors’ data
10
10
recommendations and doctors.
Repudiation means actions being done by users of the system cannot be attributed. If a legitimate user
within the system does a wrong action, the user can deny the truth of their actions.
Item Network
Title Denial of actions conducted within the system by users
Application Operating System
Threat Target Network devices
Threat Type Repudiation
Risk The damage would be high as patient’s health is at risk if a doctor denies
administering wrong treatment to the patient via the network.(7)
The attack would be reproduced if the system has less techniques in storing
and retrieving events conducted on the network(6)
The exploitation of this attack is possible if policies are not set to monitor the
standards of practitioners and providers in their duties on the system.(6)
The affected users would be patients and doctors too(5)
It is easy to discover if the network and servers have techniques of collecting
and storing events.(4)
Risk Rating 6
Secure design
Recommendations
Set up policies and standards that will guide users of the network on their actions
within the system, the policies should include the legal procedures that are
followed if found to be sending wrong data or information.
Information Disclosure can be described as breach of data by an attacker and is able to gain access to
private information.
Item Information
Title Illegal access to data
Application Operating System
Threat Target Patients and Doctors’ data
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Computer and Networks Security
11
Threat Type Information Disclosure
Risk The damage would be high as patient’s data on their diagnosis is at risk of being
altered leading to doctors administering wrong treatment.(7)
To reproduce the attack, the attacker would need to gain access to data
belonging to multiple patients(5)
To exploit the attack one needs to be specialized in coding languages that will
help to bypass the security measures set.(8)
The affected users would be patients and doctors too(5)
It is easy to discover the damage done if patients and doctors discover the
alteration on their data. (7)
Risk Rating 6
Secure design
Recommendations
Develop Strong authentication measures within the system and central server.
Verifying if the information transmitted is from appropriate sources
Denial of service (DOS) refers to interruptions being experienced by users of the system in accessing a
service.
Item Network
Title System crashes and delays
Application Remote connections
Threat Target Network devices
Threat Type Denial of Service
Risk The damage would affect patients and doctors alike from accessing the servers
and other network resources.(7)
To reproduce the attack, the attacker would have to send multiple packets to the
server continuously to keep delaying users from accessing the system.(6)
The attacker needs to be experienced in IT and programming skills to exploit the
attack.(7)
The affected users would be patients and doctors too(5)
It is easy to discover the attack if the source is from a wireless device.(4)
Risk Rating 7
Secure design
Recommendations
Implement multiple servers in running the network operations of the system.
Setting up proper encryption techniques within the network framework will also
11
11
Threat Type Information Disclosure
Risk The damage would be high as patient’s data on their diagnosis is at risk of being
altered leading to doctors administering wrong treatment.(7)
To reproduce the attack, the attacker would need to gain access to data
belonging to multiple patients(5)
To exploit the attack one needs to be specialized in coding languages that will
help to bypass the security measures set.(8)
The affected users would be patients and doctors too(5)
It is easy to discover the damage done if patients and doctors discover the
alteration on their data. (7)
Risk Rating 6
Secure design
Recommendations
Develop Strong authentication measures within the system and central server.
Verifying if the information transmitted is from appropriate sources
Denial of service (DOS) refers to interruptions being experienced by users of the system in accessing a
service.
Item Network
Title System crashes and delays
Application Remote connections
Threat Target Network devices
Threat Type Denial of Service
Risk The damage would affect patients and doctors alike from accessing the servers
and other network resources.(7)
To reproduce the attack, the attacker would have to send multiple packets to the
server continuously to keep delaying users from accessing the system.(6)
The attacker needs to be experienced in IT and programming skills to exploit the
attack.(7)
The affected users would be patients and doctors too(5)
It is easy to discover the attack if the source is from a wireless device.(4)
Risk Rating 7
Secure design
Recommendations
Implement multiple servers in running the network operations of the system.
Setting up proper encryption techniques within the network framework will also
11
Computer and Networks Security
12
minimize unauthorized access to the servers.
Elevation of privilege refers to legitimate users of the system acquiring more rights that are beyond their
authority.
Item Hardware
Title Attackers perform actions they are not allowed to perform
Application Network resources
Threat Target Network devices
Threat Type Elevation of privileges
Risk The damage would occur if a patient can brute force logging in protocols and
pose as a health practitioner within the system, allowing them to view other
patient records.(5)
It is not easy to reproduce the attack as one will need technical skills of
bypassing encryptions(4)
To exploit the attack, one requires to physically access the server for them to
connect to the ports and retrieve data.(3)
The affected users would be patients and doctors too(5)
It is difficult to discover as experience and preparation is required for one to
carry out the attack.(6)
Risk Rating 6
Secure design
Recommendations
Set up policies and standards that will guide users of the network on their actions
within the system the policies should include the legal procedures that are
followed if found to be accessing network resources that one is not authorized to
do so.
12
12
minimize unauthorized access to the servers.
Elevation of privilege refers to legitimate users of the system acquiring more rights that are beyond their
authority.
Item Hardware
Title Attackers perform actions they are not allowed to perform
Application Network resources
Threat Target Network devices
Threat Type Elevation of privileges
Risk The damage would occur if a patient can brute force logging in protocols and
pose as a health practitioner within the system, allowing them to view other
patient records.(5)
It is not easy to reproduce the attack as one will need technical skills of
bypassing encryptions(4)
To exploit the attack, one requires to physically access the server for them to
connect to the ports and retrieve data.(3)
The affected users would be patients and doctors too(5)
It is difficult to discover as experience and preparation is required for one to
carry out the attack.(6)
Risk Rating 6
Secure design
Recommendations
Set up policies and standards that will guide users of the network on their actions
within the system the policies should include the legal procedures that are
followed if found to be accessing network resources that one is not authorized to
do so.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





