Computer Networking Assignment: Binary, Hexadecimal, and IP Addresses
VerifiedAdded on 2023/06/04
|11
|2756
|354
Homework Assignment
AI Summary
This assignment solution covers key concepts in computer networking, including number representation and conversion between binary, hexadecimal, and dotted decimal formats. The solution demonstrates the conversion of MAC addresses from binary to hexadecimal and vice versa, along with the conversion of IP addresses. The assignment also includes calculations related to image storage, compression, and network transmission, involving packet sizes, transmission times, and aspect ratios. Furthermore, the solution analyzes a cybersecurity article using the WWW criteria, summarizing the article and providing an assessment of the information presented. The assignment covers topics like data representation, network fundamentals, and cybersecurity analysis, providing a comprehensive understanding of core networking principles.
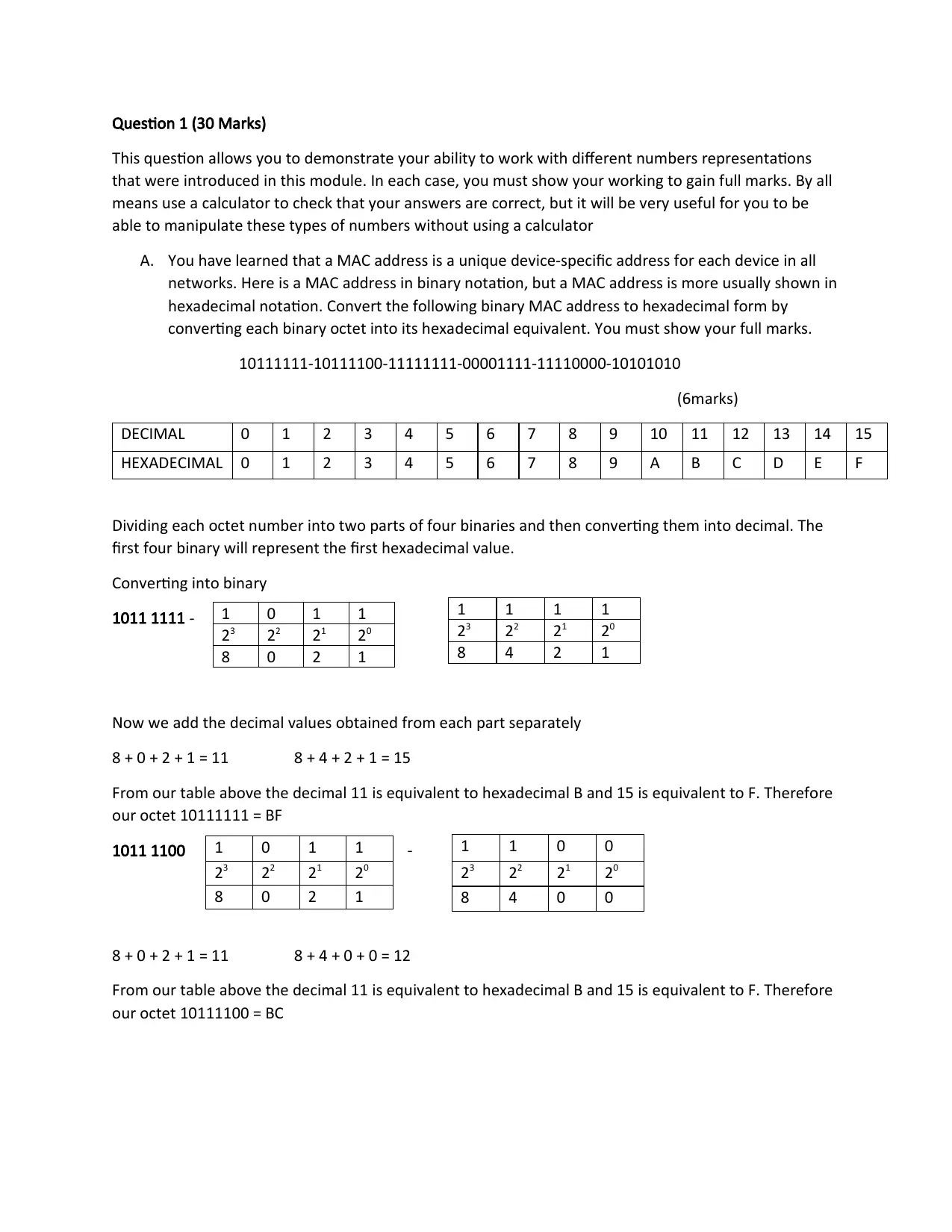
Question 1 (30 Marks)
This question allows you to demonstrate your ability to work with different numbers representations
that were introduced in this module. In each case, you must show your working to gain full marks. By all
means use a calculator to check that your answers are correct, but it will be very useful for you to be
able to manipulate these types of numbers without using a calculator
A. You have learned that a MAC address is a unique device-specific address for each device in all
networks. Here is a MAC address in binary notation, but a MAC address is more usually shown in
hexadecimal notation. Convert the following binary MAC address to hexadecimal form by
converting each binary octet into its hexadecimal equivalent. You must show your full marks.
10111111-10111100-11111111-00001111-11110000-10101010
(6marks)
DECIMAL 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
HEXADECIMAL 0 1 2 3 4 5 6 7 8 9 A B C D E F
Dividing each octet number into two parts of four binaries and then converting them into decimal. The
first four binary will represent the first hexadecimal value.
Converting into binary
1011 1111 -
Now we add the decimal values obtained from each part separately
8 + 0 + 2 + 1 = 11 8 + 4 + 2 + 1 = 15
From our table above the decimal 11 is equivalent to hexadecimal B and 15 is equivalent to F. Therefore
our octet 10111111 = BF
1011 1100 -
8 + 0 + 2 + 1 = 11 8 + 4 + 0 + 0 = 12
From our table above the decimal 11 is equivalent to hexadecimal B and 15 is equivalent to F. Therefore
our octet 10111100 = BC
1 1 1 1
23 22 21 20
8 4 2 1
1 0 1 1
23 22 21 20
8 0 2 1
1 1 0 0
23 22 21 20
8 4 0 0
1 0 1 1
23 22 21 20
8 0 2 1
This question allows you to demonstrate your ability to work with different numbers representations
that were introduced in this module. In each case, you must show your working to gain full marks. By all
means use a calculator to check that your answers are correct, but it will be very useful for you to be
able to manipulate these types of numbers without using a calculator
A. You have learned that a MAC address is a unique device-specific address for each device in all
networks. Here is a MAC address in binary notation, but a MAC address is more usually shown in
hexadecimal notation. Convert the following binary MAC address to hexadecimal form by
converting each binary octet into its hexadecimal equivalent. You must show your full marks.
10111111-10111100-11111111-00001111-11110000-10101010
(6marks)
DECIMAL 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
HEXADECIMAL 0 1 2 3 4 5 6 7 8 9 A B C D E F
Dividing each octet number into two parts of four binaries and then converting them into decimal. The
first four binary will represent the first hexadecimal value.
Converting into binary
1011 1111 -
Now we add the decimal values obtained from each part separately
8 + 0 + 2 + 1 = 11 8 + 4 + 2 + 1 = 15
From our table above the decimal 11 is equivalent to hexadecimal B and 15 is equivalent to F. Therefore
our octet 10111111 = BF
1011 1100 -
8 + 0 + 2 + 1 = 11 8 + 4 + 0 + 0 = 12
From our table above the decimal 11 is equivalent to hexadecimal B and 15 is equivalent to F. Therefore
our octet 10111100 = BC
1 1 1 1
23 22 21 20
8 4 2 1
1 0 1 1
23 22 21 20
8 0 2 1
1 1 0 0
23 22 21 20
8 4 0 0
1 0 1 1
23 22 21 20
8 0 2 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1111 1111 -
8 + 4 + 2 + 1 = 15 8 + 4 + 2 + 1 = 15
From our table above the decimal 15 is equivalent to hexadecimal F and 15 is equivalent to F. Therefore
our octet 11111111 = FF
0000 1111 -
0 + 0 + 0 + 0 = 0 8 + 4 + 2 + 1 = 15
From our table above the decimal 0 is equivalent to hexadecimal 0 and 15 is equivalent to F. Therefore
our octet 11111111 = 0F
1111 0000 -
8 + 4 + 2 + 1 = 15 0 + 0 + 0 + 0 = 0
From our table above the decimal 15 is equivalent to hexadecimal F and 0 is equivalent to 0. Therefore
our octet 11110000 = F0
1010 1010 -
8 + 0 + 2 + 0 = 10 8 + 0 + 2 + 0 = 10
From our table above the decimal 10 is equivalent to hexadecimal A and 10 is equivalent to A. Therefore
our octet 10101010 = AA
Therefore the binary 10111111-10111100-11111111-00001111-11110000-10101010 in hexadecimal is
BF – BC – FF – 0F – F0 – AA
1 1 1 1
23 22 21 20
8 4 2 1
1 1 1 1
23 22 21 20
8 4 2 1
0 0 0 0
23 22 21 20
0 0 0 0
1 1 1 1
23 22 21 20
8 4 2 1
0 0 0 0
23 22 21 20
0 0 0 0
1 1 1 1
23 22 21 20
8 4 2 1
1 0 1 0
23 22 21 20
8 0 2 0
1 0 1 0
23 22 21 20
8 0 2 0
8 + 4 + 2 + 1 = 15 8 + 4 + 2 + 1 = 15
From our table above the decimal 15 is equivalent to hexadecimal F and 15 is equivalent to F. Therefore
our octet 11111111 = FF
0000 1111 -
0 + 0 + 0 + 0 = 0 8 + 4 + 2 + 1 = 15
From our table above the decimal 0 is equivalent to hexadecimal 0 and 15 is equivalent to F. Therefore
our octet 11111111 = 0F
1111 0000 -
8 + 4 + 2 + 1 = 15 0 + 0 + 0 + 0 = 0
From our table above the decimal 15 is equivalent to hexadecimal F and 0 is equivalent to 0. Therefore
our octet 11110000 = F0
1010 1010 -
8 + 0 + 2 + 0 = 10 8 + 0 + 2 + 0 = 10
From our table above the decimal 10 is equivalent to hexadecimal A and 10 is equivalent to A. Therefore
our octet 10101010 = AA
Therefore the binary 10111111-10111100-11111111-00001111-11110000-10101010 in hexadecimal is
BF – BC – FF – 0F – F0 – AA
1 1 1 1
23 22 21 20
8 4 2 1
1 1 1 1
23 22 21 20
8 4 2 1
0 0 0 0
23 22 21 20
0 0 0 0
1 1 1 1
23 22 21 20
8 4 2 1
0 0 0 0
23 22 21 20
0 0 0 0
1 1 1 1
23 22 21 20
8 4 2 1
1 0 1 0
23 22 21 20
8 0 2 0
1 0 1 0
23 22 21 20
8 0 2 0
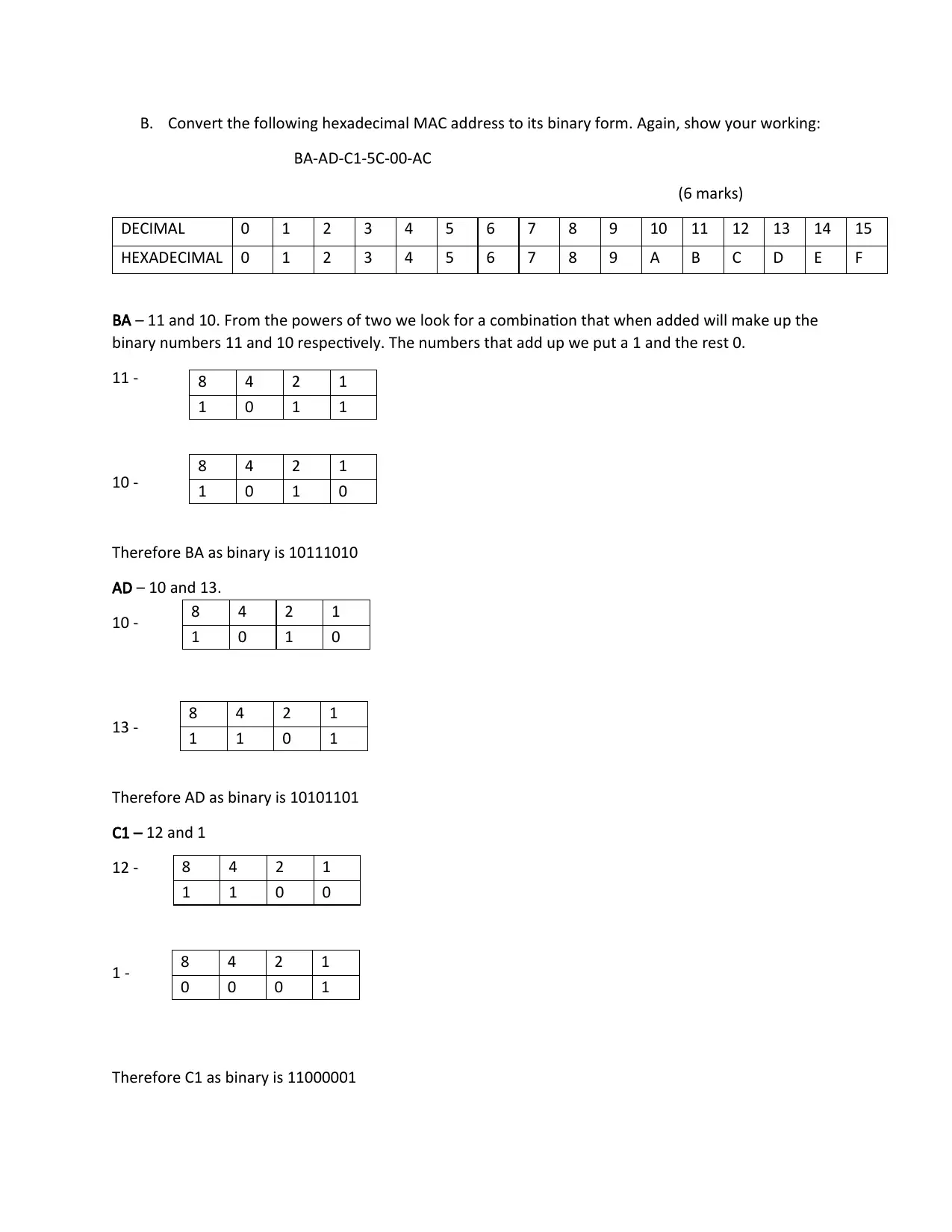
B. Convert the following hexadecimal MAC address to its binary form. Again, show your working:
BA-AD-C1-5C-00-AC
(6 marks)
DECIMAL 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
HEXADECIMAL 0 1 2 3 4 5 6 7 8 9 A B C D E F
BA – 11 and 10. From the powers of two we look for a combination that when added will make up the
binary numbers 11 and 10 respectively. The numbers that add up we put a 1 and the rest 0.
11 -
10 -
Therefore BA as binary is 10111010
AD – 10 and 13.
10 -
13 -
Therefore AD as binary is 10101101
C1 – 12 and 1
12 -
1 -
Therefore C1 as binary is 11000001
8 4 2 1
1 0 1 1
8 4 2 1
1 0 1 0
8 4 2 1
1 0 1 0
8 4 2 1
1 1 0 1
8 4 2 1
1 1 0 0
8 4 2 1
0 0 0 1
BA-AD-C1-5C-00-AC
(6 marks)
DECIMAL 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
HEXADECIMAL 0 1 2 3 4 5 6 7 8 9 A B C D E F
BA – 11 and 10. From the powers of two we look for a combination that when added will make up the
binary numbers 11 and 10 respectively. The numbers that add up we put a 1 and the rest 0.
11 -
10 -
Therefore BA as binary is 10111010
AD – 10 and 13.
10 -
13 -
Therefore AD as binary is 10101101
C1 – 12 and 1
12 -
1 -
Therefore C1 as binary is 11000001
8 4 2 1
1 0 1 1
8 4 2 1
1 0 1 0
8 4 2 1
1 0 1 0
8 4 2 1
1 1 0 1
8 4 2 1
1 1 0 0
8 4 2 1
0 0 0 1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
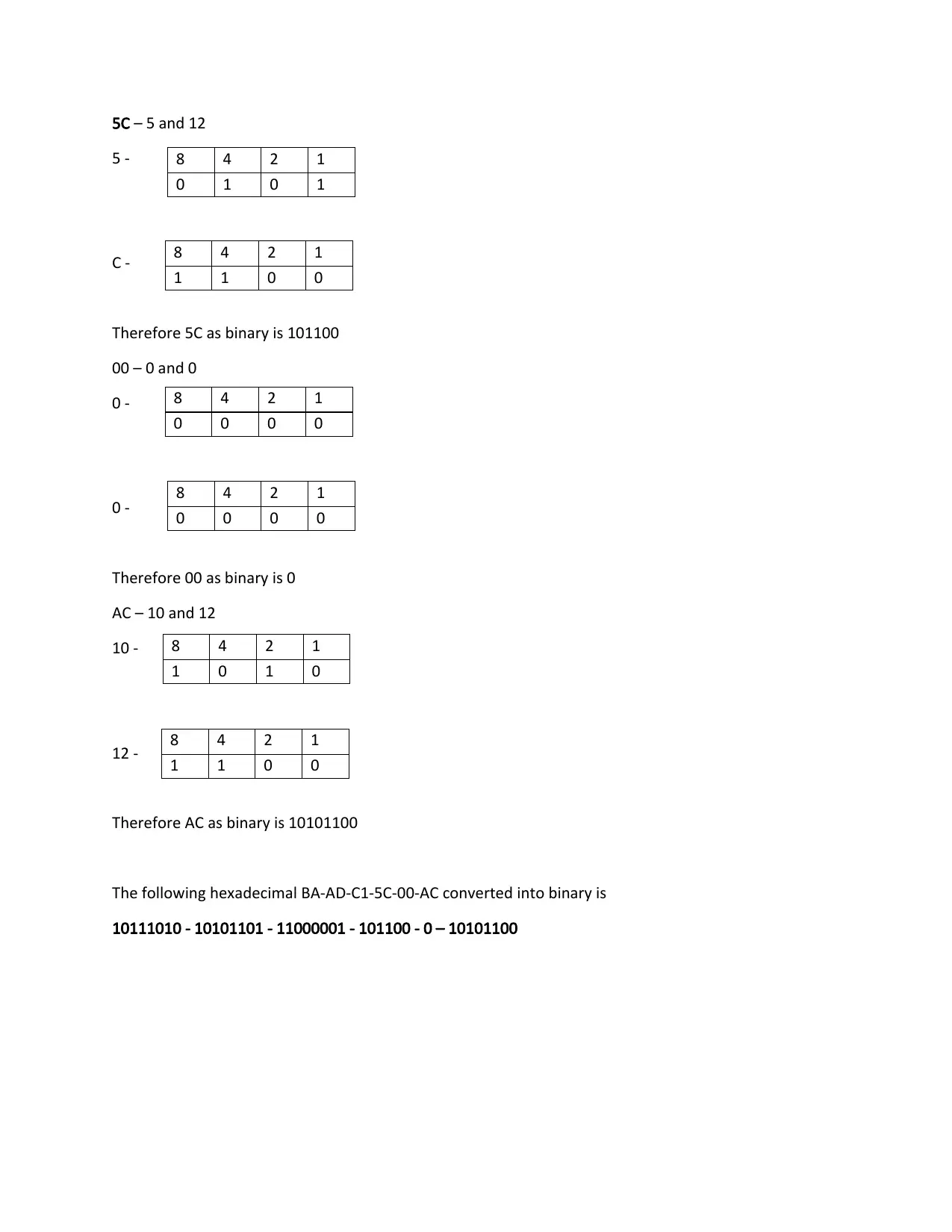
5C – 5 and 12
5 -
C -
Therefore 5C as binary is 101100
00 – 0 and 0
0 -
0 -
Therefore 00 as binary is 0
AC – 10 and 12
10 -
12 -
Therefore AC as binary is 10101100
The following hexadecimal BA-AD-C1-5C-00-AC converted into binary is
10111010 - 10101101 - 11000001 - 101100 - 0 – 10101100
8 4 2 1
0 1 0 1
8 4 2 1
1 1 0 0
8 4 2 1
0 0 0 0
8 4 2 1
0 0 0 0
8 4 2 1
1 0 1 0
8 4 2 1
1 1 0 0
5 -
C -
Therefore 5C as binary is 101100
00 – 0 and 0
0 -
0 -
Therefore 00 as binary is 0
AC – 10 and 12
10 -
12 -
Therefore AC as binary is 10101100
The following hexadecimal BA-AD-C1-5C-00-AC converted into binary is
10111010 - 10101101 - 11000001 - 101100 - 0 – 10101100
8 4 2 1
0 1 0 1
8 4 2 1
1 1 0 0
8 4 2 1
0 0 0 0
8 4 2 1
0 0 0 0
8 4 2 1
1 0 1 0
8 4 2 1
1 1 0 0
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
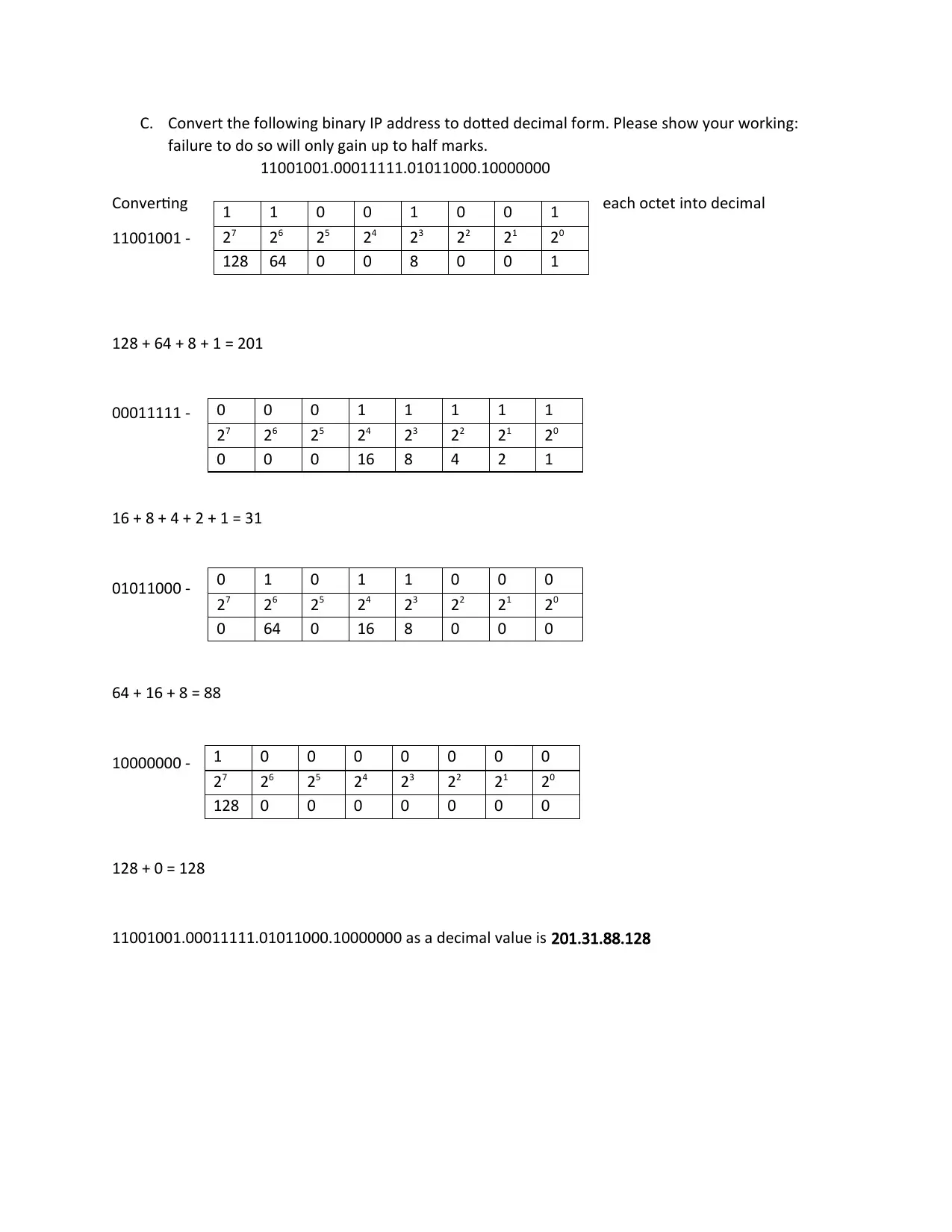
C. Convert the following binary IP address to dotted decimal form. Please show your working:
failure to do so will only gain up to half marks.
11001001.00011111.01011000.10000000
Converting each octet into decimal
11001001 -
128 + 64 + 8 + 1 = 201
00011111 -
16 + 8 + 4 + 2 + 1 = 31
01011000 -
64 + 16 + 8 = 88
10000000 -
128 + 0 = 128
11001001.00011111.01011000.10000000 as a decimal value is 201.31.88.128
1 1 0 0 1 0 0 1
27 26 25 24 23 22 21 20
128 64 0 0 8 0 0 1
0 0 0 1 1 1 1 1
27 26 25 24 23 22 21 20
0 0 0 16 8 4 2 1
0 1 0 1 1 0 0 0
27 26 25 24 23 22 21 20
0 64 0 16 8 0 0 0
1 0 0 0 0 0 0 0
27 26 25 24 23 22 21 20
128 0 0 0 0 0 0 0
failure to do so will only gain up to half marks.
11001001.00011111.01011000.10000000
Converting each octet into decimal
11001001 -
128 + 64 + 8 + 1 = 201
00011111 -
16 + 8 + 4 + 2 + 1 = 31
01011000 -
64 + 16 + 8 = 88
10000000 -
128 + 0 = 128
11001001.00011111.01011000.10000000 as a decimal value is 201.31.88.128
1 1 0 0 1 0 0 1
27 26 25 24 23 22 21 20
128 64 0 0 8 0 0 1
0 0 0 1 1 1 1 1
27 26 25 24 23 22 21 20
0 0 0 16 8 4 2 1
0 1 0 1 1 0 0 0
27 26 25 24 23 22 21 20
0 64 0 16 8 0 0 0
1 0 0 0 0 0 0 0
27 26 25 24 23 22 21 20
128 0 0 0 0 0 0 0
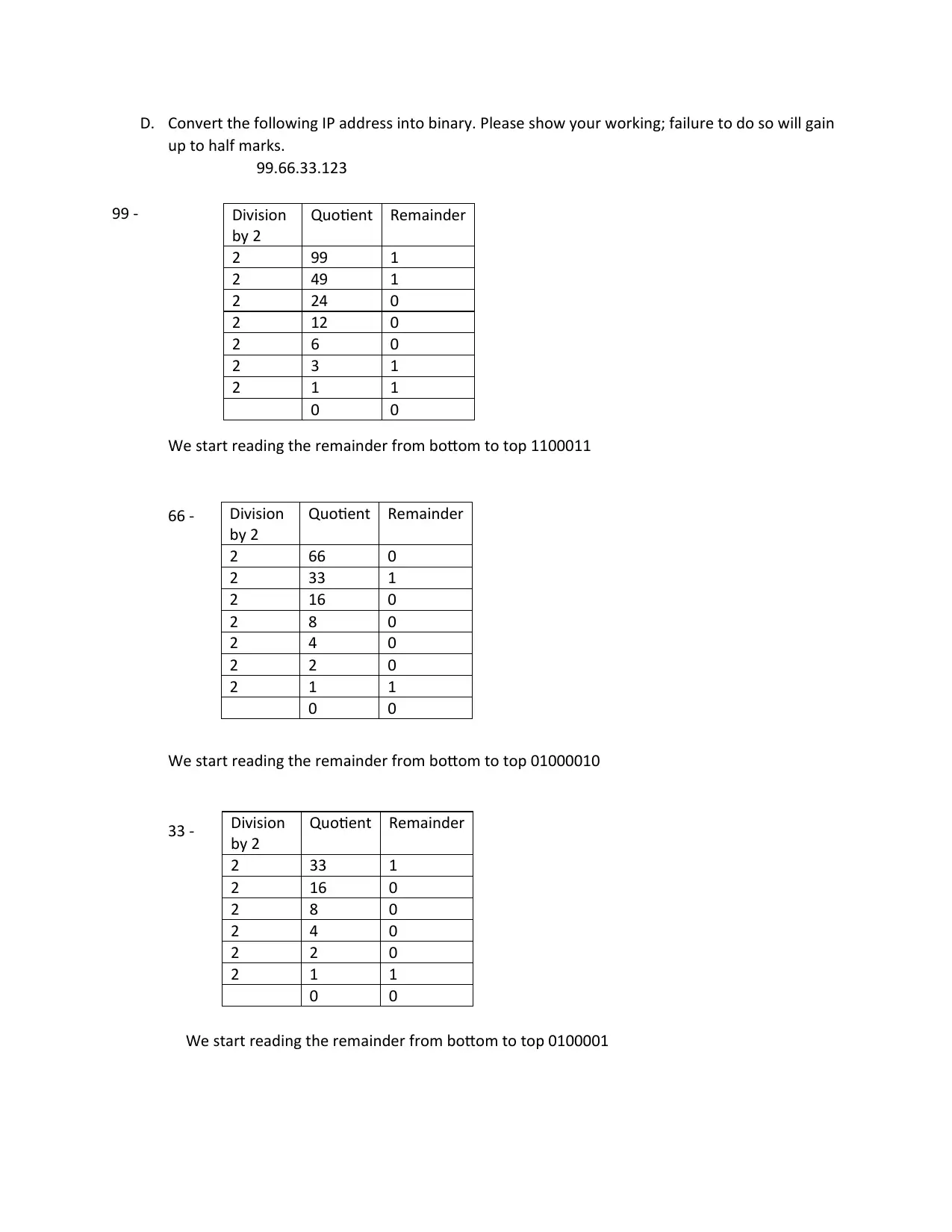
D. Convert the following IP address into binary. Please show your working; failure to do so will gain
up to half marks.
99.66.33.123
99 -
We start reading the remainder from bottom to top 1100011
66 -
We start reading the remainder from bottom to top 01000010
33 -
We start reading the remainder from bottom to top 0100001
Division
by 2
Quotient Remainder
2 99 1
2 49 1
2 24 0
2 12 0
2 6 0
2 3 1
2 1 1
0 0
Division
by 2
Quotient Remainder
2 66 0
2 33 1
2 16 0
2 8 0
2 4 0
2 2 0
2 1 1
0 0
Division
by 2
Quotient Remainder
2 33 1
2 16 0
2 8 0
2 4 0
2 2 0
2 1 1
0 0
up to half marks.
99.66.33.123
99 -
We start reading the remainder from bottom to top 1100011
66 -
We start reading the remainder from bottom to top 01000010
33 -
We start reading the remainder from bottom to top 0100001
Division
by 2
Quotient Remainder
2 99 1
2 49 1
2 24 0
2 12 0
2 6 0
2 3 1
2 1 1
0 0
Division
by 2
Quotient Remainder
2 66 0
2 33 1
2 16 0
2 8 0
2 4 0
2 2 0
2 1 1
0 0
Division
by 2
Quotient Remainder
2 33 1
2 16 0
2 8 0
2 4 0
2 2 0
2 1 1
0 0
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
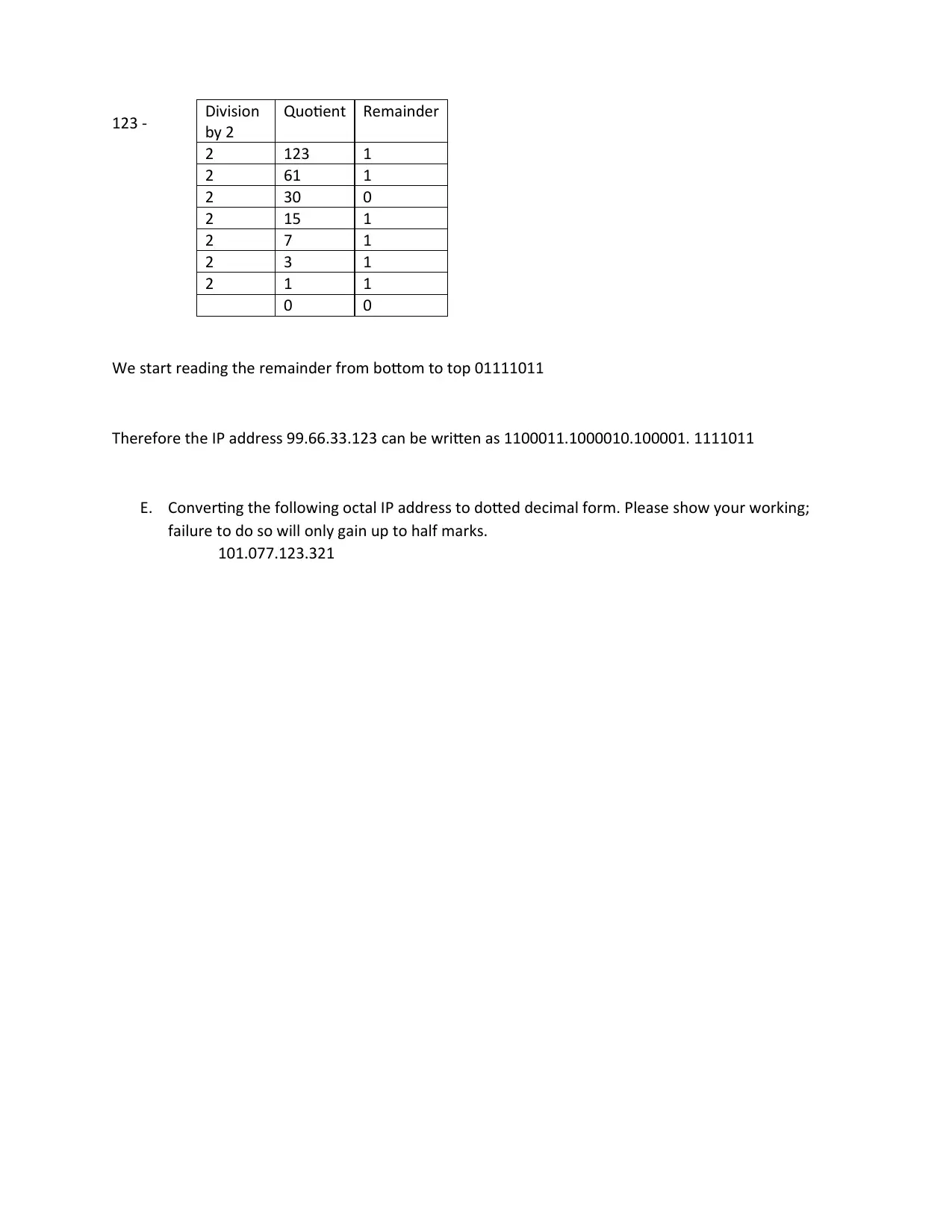
123 -
We start reading the remainder from bottom to top 01111011
Therefore the IP address 99.66.33.123 can be written as 1100011.1000010.100001. 1111011
E. Converting the following octal IP address to dotted decimal form. Please show your working;
failure to do so will only gain up to half marks.
101.077.123.321
Division
by 2
Quotient Remainder
2 123 1
2 61 1
2 30 0
2 15 1
2 7 1
2 3 1
2 1 1
0 0
We start reading the remainder from bottom to top 01111011
Therefore the IP address 99.66.33.123 can be written as 1100011.1000010.100001. 1111011
E. Converting the following octal IP address to dotted decimal form. Please show your working;
failure to do so will only gain up to half marks.
101.077.123.321
Division
by 2
Quotient Remainder
2 123 1
2 61 1
2 30 0
2 15 1
2 7 1
2 3 1
2 1 1
0 0
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

a. An image with an aspect ratio of 16:9 has 2700 pixels along the shorter edge
i. How many pixels does it have along its longer edge?
Ratio 16:9 therefore 9 is the shortest edge.
9 represents 2700 pixels
To calculate the pixels for the longest edge we multiply 16 by 2700 and divide by p
16 * 2700 = 43200
43000/9 = 4800
Therefore pixels on the longer edge are 4800
ii. How many megapixels (to the nearest megapixel) does the image contain?
Megapixel = horizontal pixels * vertical pixels
4800 * 2700 = 12, 960, 000
Nearest megapixel is 13 MP
iii. Each pixel requires 3 bytes of storage. How many bits of storage are required to store
this image? Use your rounded (a)(ii) and write your result in scientific notation to two
significant figures.
1 pixel requires 3 bytes therefore 13MP requires 13MP * 3 = 39,000,000 bytes
1 bytes = 8 bits therefore 39,000,000 bytes =
39,000,000 * 8 = 312,000,000 bits
3.1 * 108 bits
iv. By compressing the image its size can be reduced to 20% of the original size. Find the
number of megabits that is now needed to store the file. Round to the nearest 10
megabits.
To get the new size we multiply 13MP by 20 and divide by 100
20 * 13,000,000 /100 = 2,600,000 pixels
Number of bytes 2,600,000 * 3 = 7,800,000
Number of bits 7,800,000 * 8 = 62,400,000
62.4 Megabits
To the nearest 10 is 60 Megabits
(15 marks)
i. How many pixels does it have along its longer edge?
Ratio 16:9 therefore 9 is the shortest edge.
9 represents 2700 pixels
To calculate the pixels for the longest edge we multiply 16 by 2700 and divide by p
16 * 2700 = 43200
43000/9 = 4800
Therefore pixels on the longer edge are 4800
ii. How many megapixels (to the nearest megapixel) does the image contain?
Megapixel = horizontal pixels * vertical pixels
4800 * 2700 = 12, 960, 000
Nearest megapixel is 13 MP
iii. Each pixel requires 3 bytes of storage. How many bits of storage are required to store
this image? Use your rounded (a)(ii) and write your result in scientific notation to two
significant figures.
1 pixel requires 3 bytes therefore 13MP requires 13MP * 3 = 39,000,000 bytes
1 bytes = 8 bits therefore 39,000,000 bytes =
39,000,000 * 8 = 312,000,000 bits
3.1 * 108 bits
iv. By compressing the image its size can be reduced to 20% of the original size. Find the
number of megabits that is now needed to store the file. Round to the nearest 10
megabits.
To get the new size we multiply 13MP by 20 and divide by 100
20 * 13,000,000 /100 = 2,600,000 pixels
Number of bytes 2,600,000 * 3 = 7,800,000
Number of bits 7,800,000 * 8 = 62,400,000
62.4 Megabits
To the nearest 10 is 60 Megabits
(15 marks)

b. The compresses image is now going to be divided into packets to be transmitted across a
network.
i. If the packet size is 1500 bytes, how many packets will the file be divided into?
Number of bytes of the compressed image divided by the packet size
Number of packets is 7,800,000/1500 = 5,200 packets
ii. If the network can transmit 10 Gbps, how long will it take to transmit a single packet?
Write your answer in milliseconds using scientific notation to two significant figures.
It takes 1 sec to transmit 10,000,000 bits
In bytes it takes 1 sec to transmit 10,000,000/8 = 1,250,000 bytes
In packets it takes 1 sec to transit 1,250,000/1500 = 833 packets
833 packets are transmitted in 1 second. The number of packets are 5200 therefore to
find the time we divide 5200 / 833 = 6.242 seconds
In milliseconds 6.242 * 1000 = 6242 milliseconds or 6.242*103 milliseconds
(5marks)
c. The image is now going to be displayed on a rectangle that has a width of 16 inches and a height
of 6 inches, with pillarbox bars on each side.
(5 marks)
i. What percent of the area of the screen is taken up with pillarbox bars? Round your answers
percent.
Aspect ratio 16:6 = 2.67
Original image aspect ratio 16:9 = 1.78
1.78 * 100% = 178
178 / 2.67 = 66.67%
ii. It is decided that the image needs to be enlarged, keeping its aspect ratio the same. What
are the dimensions of the largest image that meets a resolution of 600 ppi?
Original aspect ratio 16:9 and height 2700 and width 4800
600 pixels per inch
1 inch = 600 pixels.
Calculating for 2700 pixels we get 2700/600 = 4.5
Calculating for 4800 pixels we get 4800 / 600 = 8
Therefore the largest image can be 8 inches width and 4.5 inches height
(10 marks)
network.
i. If the packet size is 1500 bytes, how many packets will the file be divided into?
Number of bytes of the compressed image divided by the packet size
Number of packets is 7,800,000/1500 = 5,200 packets
ii. If the network can transmit 10 Gbps, how long will it take to transmit a single packet?
Write your answer in milliseconds using scientific notation to two significant figures.
It takes 1 sec to transmit 10,000,000 bits
In bytes it takes 1 sec to transmit 10,000,000/8 = 1,250,000 bytes
In packets it takes 1 sec to transit 1,250,000/1500 = 833 packets
833 packets are transmitted in 1 second. The number of packets are 5200 therefore to
find the time we divide 5200 / 833 = 6.242 seconds
In milliseconds 6.242 * 1000 = 6242 milliseconds or 6.242*103 milliseconds
(5marks)
c. The image is now going to be displayed on a rectangle that has a width of 16 inches and a height
of 6 inches, with pillarbox bars on each side.
(5 marks)
i. What percent of the area of the screen is taken up with pillarbox bars? Round your answers
percent.
Aspect ratio 16:6 = 2.67
Original image aspect ratio 16:9 = 1.78
1.78 * 100% = 178
178 / 2.67 = 66.67%
ii. It is decided that the image needs to be enlarged, keeping its aspect ratio the same. What
are the dimensions of the largest image that meets a resolution of 600 ppi?
Original aspect ratio 16:9 and height 2700 and width 4800
600 pixels per inch
1 inch = 600 pixels.
Calculating for 2700 pixels we get 2700/600 = 4.5
Calculating for 4800 pixels we get 4800 / 600 = 8
Therefore the largest image can be 8 inches width and 4.5 inches height
(10 marks)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Question 3 (20 Marks)
Read the following article that describes some features of a cybersecurity attack and answer the
questions that follow:
Gallagher, S. (2018) ‘Russia accused of “false flag” attack on Olympic openning’, Ars Technica, 26
Febuary [Online], Available at http;//arstechnica.com/information-technology/2018/02/Russia-
accused-of-false-flag-attack-on-olympic-opening/(Accessed 13 April 2018)
a. Describe the WWW criteria for assessing information using the above article to illustrate
each element of the criteria. (Hint: the WW criteria were introduced in the Skills
development unit)
(6 marks)
b. Using the WWW criteria, write a short report that summarises the article and presents your
assessment of the information presented in it. Your report should be no longer than 500
words
(14 marks)
Private organizations and governments all over the world know that in order for them to prosper and
also to protect their national security they need to promote Cybersecurity. This indicates that a country
is willing to promote and protect the data and information of their people. The governments need to
come up with ways to deter people from engaging in cybercrime and also in techniques that will prevent
and stop cyber-attacks.
A cyber-attack this year on the Winter Olympics interfered with some of the servers and networks that
had been set up. This in turn affected the selling of tickets, public WI-FI networks and also the press
centers network. This attack was well planned and orchestrated in such a way that determining the
source of the attack was almost impossible. Various clues that had been found seemed to conflict with
each other. The attack used various tools that have been used before by various threat groups
connected to North Korea, China, and Russia.
An investigation carried out by the US intelligence and other investigators determined that the attack
was a false flag operation. This meant that the attackers intentionally left evidence so as to frustrate the
investigators and mislead them to false attribution flags. The malware itself showed that there were
three different potential attackers who could have executed the attack. To prevent forensic analysts to
know the origin of the attack, it was routed through several IP addresses in North Korea. Other
investigators from various security firms did their investigations and they all found that the malware had
similarities to another malware that had been linked to the Russians known as NotPetya.
One puzzle is how the attackers were able to get into the network. Some reports say that South Korea
had been compromised before the event happened. The routers may have been tampered with which
allowed the attackers to re-route network traffic hence making it easier for them to perform man in the
middle attacks including inserting malicious code into the network. Routers have mostly been used by
state intelligence agencies due to the many exploitation tools associated with them.
The main culprits of the Olympic destroyer were not known but investigators continue linking the
Russians to the attack. They also had the motive to perform the attacks. They may have wanted payback
Read the following article that describes some features of a cybersecurity attack and answer the
questions that follow:
Gallagher, S. (2018) ‘Russia accused of “false flag” attack on Olympic openning’, Ars Technica, 26
Febuary [Online], Available at http;//arstechnica.com/information-technology/2018/02/Russia-
accused-of-false-flag-attack-on-olympic-opening/(Accessed 13 April 2018)
a. Describe the WWW criteria for assessing information using the above article to illustrate
each element of the criteria. (Hint: the WW criteria were introduced in the Skills
development unit)
(6 marks)
b. Using the WWW criteria, write a short report that summarises the article and presents your
assessment of the information presented in it. Your report should be no longer than 500
words
(14 marks)
Private organizations and governments all over the world know that in order for them to prosper and
also to protect their national security they need to promote Cybersecurity. This indicates that a country
is willing to promote and protect the data and information of their people. The governments need to
come up with ways to deter people from engaging in cybercrime and also in techniques that will prevent
and stop cyber-attacks.
A cyber-attack this year on the Winter Olympics interfered with some of the servers and networks that
had been set up. This in turn affected the selling of tickets, public WI-FI networks and also the press
centers network. This attack was well planned and orchestrated in such a way that determining the
source of the attack was almost impossible. Various clues that had been found seemed to conflict with
each other. The attack used various tools that have been used before by various threat groups
connected to North Korea, China, and Russia.
An investigation carried out by the US intelligence and other investigators determined that the attack
was a false flag operation. This meant that the attackers intentionally left evidence so as to frustrate the
investigators and mislead them to false attribution flags. The malware itself showed that there were
three different potential attackers who could have executed the attack. To prevent forensic analysts to
know the origin of the attack, it was routed through several IP addresses in North Korea. Other
investigators from various security firms did their investigations and they all found that the malware had
similarities to another malware that had been linked to the Russians known as NotPetya.
One puzzle is how the attackers were able to get into the network. Some reports say that South Korea
had been compromised before the event happened. The routers may have been tampered with which
allowed the attackers to re-route network traffic hence making it easier for them to perform man in the
middle attacks including inserting malicious code into the network. Routers have mostly been used by
state intelligence agencies due to the many exploitation tools associated with them.
The main culprits of the Olympic destroyer were not known but investigators continue linking the
Russians to the attack. They also had the motive to perform the attacks. They may have wanted payback
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

from the International Olympics committee for banning many athletes from Russia and also denying
them to act as representatives of Russia. Also Russia has a previous record of attacking World Anti-
Doping agency and Olympic officials at the 2016 Summer Olympic Games in Brazil have been attributed
to Russian intelligence.
Cybercrimes are growing and nations need to come up with strict laws on combating cybercrimes. As
digitization accelerates its critical for organizations to shore up their defense to ensure information and
system are protected which is a multifaceted response plan in this digital arena. Nations can set up a
cyber-attack center which can be used to monitor and also deal with the cyber-attacks that occur
REFERENCESBinary to Decimal convertion n.d., Electronic Tutorials, viewed 20 Oct 2018. < https://www.electronics-
tutorials.ws/binary/bin_2.html >
Eugene, B. 2018,
How to Convert Decimal to Binary and Binary to Decimal, Owlcation, viewed 20 Oct
2018. <https://owlcation.com/stem/How-to-Convert-Decimal-to-Binary-and-Binary-to-Decimal>
Gallagher, S. 2018,
Russia accused of “false flag” attack on Olympic opening, Ars Technica, viewed 20 Oct
2018. <https://arstechnica.com/information-technology/2018/02/russia-accused-of-false-flag-attack-on-
olympic-opening/>Hex to Binary converter n.d.
, Rapidtables, viewed 20 Oct 2018,
https://www.rapidtables.com/convert/number/hex-to-binary.htmlThe simple math behind decimal-binary conversion algorithms n.d.
, Angular In Depth, viewed 25 Oct
2018, < https://blog.angularindepth.com/the-simple-math-behind-decimal-binary-conversion-
algorithms-d30c967c9724>
them to act as representatives of Russia. Also Russia has a previous record of attacking World Anti-
Doping agency and Olympic officials at the 2016 Summer Olympic Games in Brazil have been attributed
to Russian intelligence.
Cybercrimes are growing and nations need to come up with strict laws on combating cybercrimes. As
digitization accelerates its critical for organizations to shore up their defense to ensure information and
system are protected which is a multifaceted response plan in this digital arena. Nations can set up a
cyber-attack center which can be used to monitor and also deal with the cyber-attacks that occur
REFERENCESBinary to Decimal convertion n.d., Electronic Tutorials, viewed 20 Oct 2018. < https://www.electronics-
tutorials.ws/binary/bin_2.html >
Eugene, B. 2018,
How to Convert Decimal to Binary and Binary to Decimal, Owlcation, viewed 20 Oct
2018. <https://owlcation.com/stem/How-to-Convert-Decimal-to-Binary-and-Binary-to-Decimal>
Gallagher, S. 2018,
Russia accused of “false flag” attack on Olympic opening, Ars Technica, viewed 20 Oct
2018. <https://arstechnica.com/information-technology/2018/02/russia-accused-of-false-flag-attack-on-
olympic-opening/>Hex to Binary converter n.d.
, Rapidtables, viewed 20 Oct 2018,
https://www.rapidtables.com/convert/number/hex-to-binary.htmlThe simple math behind decimal-binary conversion algorithms n.d.
, Angular In Depth, viewed 25 Oct
2018, < https://blog.angularindepth.com/the-simple-math-behind-decimal-binary-conversion-
algorithms-d30c967c9724>
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





