Computer Networking Assignment
VerifiedAdded on 2020/02/24
|9
|1911
|469
Homework Assignment
AI Summary
This assignment covers various aspects of computer networking, including Ethernet switches, network topology, congestion control mechanisms, distance vector and link state algorithms, and DHCPv6 protocol. It provides detailed explanations and solutions to common networking problems, making it a valuable resource for students studying theoretical computer science.
computer networking assignment
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Question – 1..........................................................................................................................................2
a) Ethernet Switch........................................................................................................................2
b) Network Topology...................................................................................................................3
Question – 2..........................................................................................................................................3
a) Mechanisms Implementations................................................................................................3
Question – 3..........................................................................................................................................5
a) Distance Vector and Link state Algorithms...........................................................................5
b) DHCPv6 Protocol.....................................................................................................................6
Question – 4..........................................................................................................................................6
a) Network Topology...................................................................................................................6
b) IP addressing............................................................................................................................7
c) RIP configuration....................................................................................................................7
References............................................................................................................................................7
1
Question – 1..........................................................................................................................................2
a) Ethernet Switch........................................................................................................................2
b) Network Topology...................................................................................................................3
Question – 2..........................................................................................................................................3
a) Mechanisms Implementations................................................................................................3
Question – 3..........................................................................................................................................5
a) Distance Vector and Link state Algorithms...........................................................................5
b) DHCPv6 Protocol.....................................................................................................................6
Question – 4..........................................................................................................................................6
a) Network Topology...................................................................................................................6
b) IP addressing............................................................................................................................7
c) RIP configuration....................................................................................................................7
References............................................................................................................................................7
1

Question – 1
a) Ethernet Switch
In network, Ethernet switches are continuously running out of frames and buffers.
Reason for this issues is a queue overrun because the switch kernel assign the queue length
limit but some cases the queue fills the faster higher than queue length. So frames are
dropped. So resolving this issues by using the two different ways such ad queue length and
input traffic. The Input traffic is prevent queue overruns by slowing the down the input
traffic. Another ways is queue length to increase the queue length (Etutorials.org, 2017). The
queue length involves to increasing the buffers in a specified queue. To reduce the running
out of buffers to increasing the number of buffers in the network.
In network, congestion happens in Ethernet switch and it was running out of dropping
frames and buffers. The congestion involves the more the one types of dropping frames.
When congestion happens the frames are potentially delayed. So the frames should be
buffered until transmitted. Reason for this issues includes,
Mismatch of speed between the egress and ingress port
Half duplex collisions
Multiple input ports feeding the single output port
So resolving this issues to using the two basic memory management are used in Ethernet
Switch such as Port buffered memory and shared memory. The Ethernet switches are
utilizing the port buffered memory. To maximizing the buffer running out to use the flexible
buffer sizes that is catalyst 5000 Ethernet line card port buffer memory is flexible. It create
the buffers for any frame size. So it reduce the Ethernet switch running out of buffer and
dropping frames.
The junior team member suggest to resolving this issues by using the half duplex
semantics on the switch port. But the imposing the half duplex does not reducing the running
out of buffer and dropping frames. Because the half duplex cannot transmit and receive at the
same time. Reason is to every computer has the point to point connection with the switch port
so it does not half duplex a device cannot send and receive at the same time (The Data Center
Overlords, 2017).
b) Network Topology
2
a) Ethernet Switch
In network, Ethernet switches are continuously running out of frames and buffers.
Reason for this issues is a queue overrun because the switch kernel assign the queue length
limit but some cases the queue fills the faster higher than queue length. So frames are
dropped. So resolving this issues by using the two different ways such ad queue length and
input traffic. The Input traffic is prevent queue overruns by slowing the down the input
traffic. Another ways is queue length to increase the queue length (Etutorials.org, 2017). The
queue length involves to increasing the buffers in a specified queue. To reduce the running
out of buffers to increasing the number of buffers in the network.
In network, congestion happens in Ethernet switch and it was running out of dropping
frames and buffers. The congestion involves the more the one types of dropping frames.
When congestion happens the frames are potentially delayed. So the frames should be
buffered until transmitted. Reason for this issues includes,
Mismatch of speed between the egress and ingress port
Half duplex collisions
Multiple input ports feeding the single output port
So resolving this issues to using the two basic memory management are used in Ethernet
Switch such as Port buffered memory and shared memory. The Ethernet switches are
utilizing the port buffered memory. To maximizing the buffer running out to use the flexible
buffer sizes that is catalyst 5000 Ethernet line card port buffer memory is flexible. It create
the buffers for any frame size. So it reduce the Ethernet switch running out of buffer and
dropping frames.
The junior team member suggest to resolving this issues by using the half duplex
semantics on the switch port. But the imposing the half duplex does not reducing the running
out of buffer and dropping frames. Because the half duplex cannot transmit and receive at the
same time. Reason is to every computer has the point to point connection with the switch port
so it does not half duplex a device cannot send and receive at the same time (The Data Center
Overlords, 2017).
b) Network Topology
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The above network topology operate at 1000 Mbps with the hub and bridges. The Each
Hub connecting the 40 posts. If the network operate at 10 Mbps port the hub and bridges are
replaced by 4 hosts per hub totally 8 hosts in the network topology. The 10mbps switch using
the single 96 port (UKEssays, 2017). The intermediate devices are provides the security
hosts. It connecting to the modem pool and it authenticated by the RAS server. It provides the
extra layer of security in the network.
To upgrade and downgrade the network topology by improving the network performance
based on performance characteristics. The above network topology is selected facilitate the
network reconfiguration including adding and removing the nodes. It provides the
communications and inter connection between the nodes. It also provides the advanced
functionality such as high availability, enhanced security, advanced quality of service and
effective management (Cisco.com, 2017).
Question – 2
a) Mechanisms Implementations
Identified the policies is used to implemented by higher layer protocols and it provides
the reliable delivery. The Identified the congestion policies are listed below.
Retransmission Policy
When the packers are lost and corrupted, retransmits the packets. The retransmission
increase the network congestion. To prevent the congestion by implement the good
retransmission. The retransmission timers and policy are requires to optimize the network
efficiency at the times of prevent the congestion (policies., 2017).
Acknowledgement Policy
3
Hub connecting the 40 posts. If the network operate at 10 Mbps port the hub and bridges are
replaced by 4 hosts per hub totally 8 hosts in the network topology. The 10mbps switch using
the single 96 port (UKEssays, 2017). The intermediate devices are provides the security
hosts. It connecting to the modem pool and it authenticated by the RAS server. It provides the
extra layer of security in the network.
To upgrade and downgrade the network topology by improving the network performance
based on performance characteristics. The above network topology is selected facilitate the
network reconfiguration including adding and removing the nodes. It provides the
communications and inter connection between the nodes. It also provides the advanced
functionality such as high availability, enhanced security, advanced quality of service and
effective management (Cisco.com, 2017).
Question – 2
a) Mechanisms Implementations
Identified the policies is used to implemented by higher layer protocols and it provides
the reliable delivery. The Identified the congestion policies are listed below.
Retransmission Policy
When the packers are lost and corrupted, retransmits the packets. The retransmission
increase the network congestion. To prevent the congestion by implement the good
retransmission. The retransmission timers and policy are requires to optimize the network
efficiency at the times of prevent the congestion (policies., 2017).
Acknowledgement Policy
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
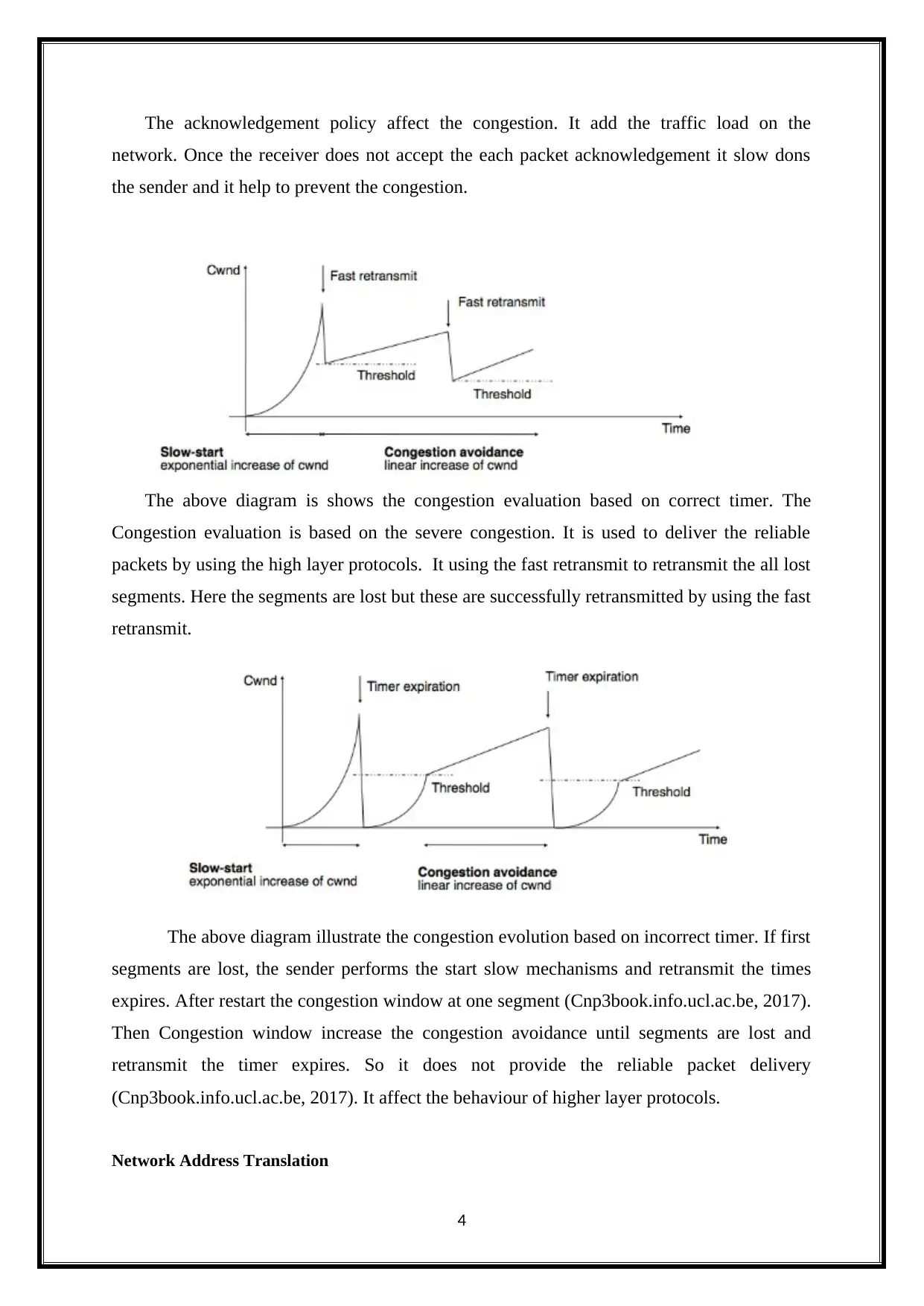
The acknowledgement policy affect the congestion. It add the traffic load on the
network. Once the receiver does not accept the each packet acknowledgement it slow dons
the sender and it help to prevent the congestion.
The above diagram is shows the congestion evaluation based on correct timer. The
Congestion evaluation is based on the severe congestion. It is used to deliver the reliable
packets by using the high layer protocols. It using the fast retransmit to retransmit the all lost
segments. Here the segments are lost but these are successfully retransmitted by using the fast
retransmit.
The above diagram illustrate the congestion evolution based on incorrect timer. If first
segments are lost, the sender performs the start slow mechanisms and retransmit the times
expires. After restart the congestion window at one segment (Cnp3book.info.ucl.ac.be, 2017).
Then Congestion window increase the congestion avoidance until segments are lost and
retransmit the timer expires. So it does not provide the reliable packet delivery
(Cnp3book.info.ucl.ac.be, 2017). It affect the behaviour of higher layer protocols.
Network Address Translation
4
network. Once the receiver does not accept the each packet acknowledgement it slow dons
the sender and it help to prevent the congestion.
The above diagram is shows the congestion evaluation based on correct timer. The
Congestion evaluation is based on the severe congestion. It is used to deliver the reliable
packets by using the high layer protocols. It using the fast retransmit to retransmit the all lost
segments. Here the segments are lost but these are successfully retransmitted by using the fast
retransmit.
The above diagram illustrate the congestion evolution based on incorrect timer. If first
segments are lost, the sender performs the start slow mechanisms and retransmit the times
expires. After restart the congestion window at one segment (Cnp3book.info.ucl.ac.be, 2017).
Then Congestion window increase the congestion avoidance until segments are lost and
retransmit the timer expires. So it does not provide the reliable packet delivery
(Cnp3book.info.ucl.ac.be, 2017). It affect the behaviour of higher layer protocols.
Network Address Translation
4

The IP addresses are classified into two types like Private IP address and public IP
address. The Private address are predefined pool and it re-used by the various organizations.
The public IP addresses are globally unique and Public IP address are common for server and
it needs to require the internet accessing. It has the some disadvantages. These are listed
below.
Security
The public IP address requires the security strategy implementation. Because the
single IP addresses are directly assigned the computer so attackers are take computer
controls.
Expense
The public IP address simplify the server administration so it has increased the
addresses price. For example, organization needs a separate the public IP address to pay the
significant fees to Internet service provider.
Question – 3
a) Distance Vector and Link state Algorithms
The distance vector and link state algorithms are used to solve the link continuously
going up and down in a network. The network link going up and down problems is reduced
and managed by using the dynamic routing protocols (Pluralsight.com, 2017). Because it
using the advanced IP addressing and it investigate the network bandwidth, convergence
speed and reliability. It measures the distance metrics to show the direction to that specific
network. The Link state protocol provides the complete network topology to provide the
protocol information. It provides the link continuous problem informations and resolve the
problem to investigate the network performance.
Distance vector algorithms Link state algorithms
Computation High computation compared
to link state algorithms.
Less Computation.
Communication It helps the router decide
which paths to send traffic
It sends the traffic between the
devices running at layer 3.
Convergence Slow convergence Fast convergence
5
address. The Private address are predefined pool and it re-used by the various organizations.
The public IP addresses are globally unique and Public IP address are common for server and
it needs to require the internet accessing. It has the some disadvantages. These are listed
below.
Security
The public IP address requires the security strategy implementation. Because the
single IP addresses are directly assigned the computer so attackers are take computer
controls.
Expense
The public IP address simplify the server administration so it has increased the
addresses price. For example, organization needs a separate the public IP address to pay the
significant fees to Internet service provider.
Question – 3
a) Distance Vector and Link state Algorithms
The distance vector and link state algorithms are used to solve the link continuously
going up and down in a network. The network link going up and down problems is reduced
and managed by using the dynamic routing protocols (Pluralsight.com, 2017). Because it
using the advanced IP addressing and it investigate the network bandwidth, convergence
speed and reliability. It measures the distance metrics to show the direction to that specific
network. The Link state protocol provides the complete network topology to provide the
protocol information. It provides the link continuous problem informations and resolve the
problem to investigate the network performance.
Distance vector algorithms Link state algorithms
Computation High computation compared
to link state algorithms.
Less Computation.
Communication It helps the router decide
which paths to send traffic
It sends the traffic between the
devices running at layer 3.
Convergence Slow convergence Fast convergence
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
b) DHCPv6 Protocol
DHCP auto configuration features is allow you to apply to current network and already
configured DHCP configuration file. It is used to manage the correct and unique IP address in
distributed manner. It performs the synchronization to detect the network changes. It produce
null overhead in network traffics (Guttman, 2017).
DHCPv6 server is useful to detect the network performance and changes by using the
DHCP auto configuration. It providing the configuration parameters to hosts over the
network. It dynamically allocate the IP address. It remove the DHCP restriction on the
network. It provides the high security and reliability.
Question – 4
a) Network Topology
The Above network topology diagram PC-A and PB-B connected with S1 switch and R1
router. The ARP cache is first occur in PC-B but it does have values. The PC-B contains the
empty ARP cache. After the ARP pinged by PC-A and S1. The Address resolution protocol is
a most important part of the IP networking (Petri, 2017). It communicate the devices on
network. It should be contains the MAC address for the devices. It the ARP cache is start in
empty it using the static ARP entries. The static ARP entries are manually entering the link
between the IP address and MAC address. When network management has the lack of
significant negatives, the static ARP entries are occurred. So the switch tracking the MAC
address and clear the empty ARP entries.
6
DHCP auto configuration features is allow you to apply to current network and already
configured DHCP configuration file. It is used to manage the correct and unique IP address in
distributed manner. It performs the synchronization to detect the network changes. It produce
null overhead in network traffics (Guttman, 2017).
DHCPv6 server is useful to detect the network performance and changes by using the
DHCP auto configuration. It providing the configuration parameters to hosts over the
network. It dynamically allocate the IP address. It remove the DHCP restriction on the
network. It provides the high security and reliability.
Question – 4
a) Network Topology
The Above network topology diagram PC-A and PB-B connected with S1 switch and R1
router. The ARP cache is first occur in PC-B but it does have values. The PC-B contains the
empty ARP cache. After the ARP pinged by PC-A and S1. The Address resolution protocol is
a most important part of the IP networking (Petri, 2017). It communicate the devices on
network. It should be contains the MAC address for the devices. It the ARP cache is start in
empty it using the static ARP entries. The static ARP entries are manually entering the link
between the IP address and MAC address. When network management has the lack of
significant negatives, the static ARP entries are occurred. So the switch tracking the MAC
address and clear the empty ARP entries.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

b) IP addressing
IP addressing Informations are shown below.
The above PCs are connected with single network. The Above network topology does
not need a default gateway because both PC's are connected with same subnet. To ping the
PC-A and PC-B, the PC-B send the MAC address to PC-A. The PC-A receive the PC-B
MAC address on the frame and send the reply the PC-A. Then get the addresses from the
ARP tables.
c) RIP configuration
Answer: R3 pinging 172.16.1.1
References
Cisco.com. (2017). Update Your LAN [Networking Fundamentals] - Cisco Systems. [online]
Available at:
https://www.cisco.com/en/US/netsol/ns339/ns392/ns399/ns400/networking_solutions_white_
paper0900aecd802d5493.shtml [Accessed 27 Aug. 2017].
Cnp3book.info.ucl.ac.be. (2017). Congestion control — Computer Networking : Principles,
Protocols and Practice. [online] Available at:
http://cnp3book.info.ucl.ac.be/2nd/html/protocols/congestion.html [Accessed 27 Aug. 2017].
Etutorials.org. (2017). Buffering Data :: Chapter 2. LAN Switch Architecture :: Lan
switching fundamentals :: Networking :: eTutorials.org. [online] Available at:
http://etutorials.org/Networking/Lan+switching+fundamentals/Chapter+2.+LAN+Switch+Ar
chitecture/Buffering+Data/ [Accessed 27 Aug. 2017].
Guttman, E. (2017). Auto configuration for IP Networking: Enabling Local Communication.
[online] Available at: http://www.zeroconf.org/w3onwire-zeroconf.pdf [Accessed 27 Aug.
2017].
Petri. (2017). ARP cache: What is it and how can it help you? - Petri. [online] Available at:
https://www.petri.com/csc_arp_cache [Accessed 27 Aug. 2017].
7
IP addressing Informations are shown below.
The above PCs are connected with single network. The Above network topology does
not need a default gateway because both PC's are connected with same subnet. To ping the
PC-A and PC-B, the PC-B send the MAC address to PC-A. The PC-A receive the PC-B
MAC address on the frame and send the reply the PC-A. Then get the addresses from the
ARP tables.
c) RIP configuration
Answer: R3 pinging 172.16.1.1
References
Cisco.com. (2017). Update Your LAN [Networking Fundamentals] - Cisco Systems. [online]
Available at:
https://www.cisco.com/en/US/netsol/ns339/ns392/ns399/ns400/networking_solutions_white_
paper0900aecd802d5493.shtml [Accessed 27 Aug. 2017].
Cnp3book.info.ucl.ac.be. (2017). Congestion control — Computer Networking : Principles,
Protocols and Practice. [online] Available at:
http://cnp3book.info.ucl.ac.be/2nd/html/protocols/congestion.html [Accessed 27 Aug. 2017].
Etutorials.org. (2017). Buffering Data :: Chapter 2. LAN Switch Architecture :: Lan
switching fundamentals :: Networking :: eTutorials.org. [online] Available at:
http://etutorials.org/Networking/Lan+switching+fundamentals/Chapter+2.+LAN+Switch+Ar
chitecture/Buffering+Data/ [Accessed 27 Aug. 2017].
Guttman, E. (2017). Auto configuration for IP Networking: Enabling Local Communication.
[online] Available at: http://www.zeroconf.org/w3onwire-zeroconf.pdf [Accessed 27 Aug.
2017].
Petri. (2017). ARP cache: What is it and how can it help you? - Petri. [online] Available at:
https://www.petri.com/csc_arp_cache [Accessed 27 Aug. 2017].
7

Pluralsight.com. (2017). Dynamic Routing Protocols: Distance Vector and Link State
Protocols. [online] Available at: https://www.pluralsight.com/blog/it-ops/dynamic-routing-
protocol [Accessed 27 Aug. 2017].
policies., w. (2017). what is congestion control? Explain various congestion prevention
policies.. [online] Ques10.com. Available at: http://www.ques10.com/p/8635/what-is-
congestion-control-explain-various-congest/ [Accessed 27 Aug. 2017].
Smallbusiness.chron.com. (2017). What Are the Disadvantages of Using Public IP
Addresses?. [online] Available at: http://smallbusiness.chron.com/disadvantages-using-
public-ip-addresses-69877.html [Accessed 27 Aug. 2017].
The Data Center Overlords. (2017). Ethernet Congestion: Drop It or Pause It. [online]
Available at: https://datacenteroverlords.com/2013/02/02/ethernet-congestion-drop-it-or-
pause-it/ [Accessed 27 Aug. 2017].
UKEssays. (2017). The Role Of Intermediary Devices In Networks Information Technology
Essay. [online] Available at: https://www.ukessays.com/essays/information-technology/the-
role-of-intermediary-devices-in-networks-information-technology-essay.php [Accessed 27
Aug. 2017].
8
Protocols. [online] Available at: https://www.pluralsight.com/blog/it-ops/dynamic-routing-
protocol [Accessed 27 Aug. 2017].
policies., w. (2017). what is congestion control? Explain various congestion prevention
policies.. [online] Ques10.com. Available at: http://www.ques10.com/p/8635/what-is-
congestion-control-explain-various-congest/ [Accessed 27 Aug. 2017].
Smallbusiness.chron.com. (2017). What Are the Disadvantages of Using Public IP
Addresses?. [online] Available at: http://smallbusiness.chron.com/disadvantages-using-
public-ip-addresses-69877.html [Accessed 27 Aug. 2017].
The Data Center Overlords. (2017). Ethernet Congestion: Drop It or Pause It. [online]
Available at: https://datacenteroverlords.com/2013/02/02/ethernet-congestion-drop-it-or-
pause-it/ [Accessed 27 Aug. 2017].
UKEssays. (2017). The Role Of Intermediary Devices In Networks Information Technology
Essay. [online] Available at: https://www.ukessays.com/essays/information-technology/the-
role-of-intermediary-devices-in-networks-information-technology-essay.php [Accessed 27
Aug. 2017].
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





