Analysis of Inter-networking: Protocols, Topology, and Design
VerifiedAdded on 2020/11/23
|8
|1946
|91
Report
AI Summary
This report provides a comprehensive overview of inter-networking, encompassing its scope, functional and non-functional requirements, and design considerations. It delves into the design of networking based on human concepts, exploring the use of top-down and bottom-up approaches. The report analyzes the requirements of internet protocols (IP) and presents them in a tabular format, illustrating the application of IP addressing and network connections. Furthermore, it includes a topology diagram of networking, detailing switch, router, and DHCP configurations. The conclusion summarizes the key aspects of inter-networking, emphasizing its role in facilitating communication and data transfer across different devices. The report also includes references to relevant books and journals that support the information provided.

Overviewing of inter-networking
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION..........................................................................................................................1
1.Scope of inter-networking........................................................................................................1
2.functional and non-functional requirements (NFR) of inter-networking.................................1
3. Design of networking based on the human concepts..............................................................2
4. Requirements of internet protocols (IP) and its justification in a tabular form....................2
5. Topology diagram of networking including Switch configuration, Router
configuration,DHCP configuration.............................................................................................3
CONCLUSION................................................................................................................................4
REFERENCES................................................................................................................................5
INTRODUCTION..........................................................................................................................1
1.Scope of inter-networking........................................................................................................1
2.functional and non-functional requirements (NFR) of inter-networking.................................1
3. Design of networking based on the human concepts..............................................................2
4. Requirements of internet protocols (IP) and its justification in a tabular form....................2
5. Topology diagram of networking including Switch configuration, Router
configuration,DHCP configuration.............................................................................................3
CONCLUSION................................................................................................................................4
REFERENCES................................................................................................................................5

INTRODUCTION
A computer network can be determined as inter-connection of data network which shares
data and resources using connected nodes and switches. It may be open system inter-networking
in which systems are ready to interact with each other. The present study will be based on the
inter-connectivity of computer which establish a huge network in order to share data resources. It
will also provide some information about the methods by which computers are connected to each
other. The report will also focus on the topological structure which is minimising the
complexities of inter-networking. It will also provide focus on the requirements used for building
network connections and use of internet protocols in inter-networking.
1.Scope of network requirement analysis
Requirement analysis can be referred as identifying, gathering and understanding the
concept which facilitates resource sharing. Development of networking have widely influenced
the society. Networking have made all those things possible which have earlier faced lot of
difficulties. In this modernised world, peoples are totally dependent on this inter-networking
technology which have provided a lot of ease in communication across the different places of
world (Hamid and et.al., 2015). It has maximised the job opportunities for unemployed people
as well it requires always updated technological skills as lot of technological advancements are
occurring rapidly. There are lot of scope in this networking sector as some of them are
mentioned below:
It had maximised huge job opportunities in the field of Information technology.
Networking is considered to be one of the best job as the technology always changes and
this maintains interest of employees in doing task properly.
Implementation of wide area network in the world have increased the number of data
centres at different places and this require a human resource to control all the activities of
inter-connected networking devices. So it has also increased the demand of workforce
and this will result in minimising unemployed people in country.
Invention of wireless fidelity (Wi-Fi) had made interdependency of the work in order to
share data and information among different systems.
1
A computer network can be determined as inter-connection of data network which shares
data and resources using connected nodes and switches. It may be open system inter-networking
in which systems are ready to interact with each other. The present study will be based on the
inter-connectivity of computer which establish a huge network in order to share data resources. It
will also provide some information about the methods by which computers are connected to each
other. The report will also focus on the topological structure which is minimising the
complexities of inter-networking. It will also provide focus on the requirements used for building
network connections and use of internet protocols in inter-networking.
1.Scope of network requirement analysis
Requirement analysis can be referred as identifying, gathering and understanding the
concept which facilitates resource sharing. Development of networking have widely influenced
the society. Networking have made all those things possible which have earlier faced lot of
difficulties. In this modernised world, peoples are totally dependent on this inter-networking
technology which have provided a lot of ease in communication across the different places of
world (Hamid and et.al., 2015). It has maximised the job opportunities for unemployed people
as well it requires always updated technological skills as lot of technological advancements are
occurring rapidly. There are lot of scope in this networking sector as some of them are
mentioned below:
It had maximised huge job opportunities in the field of Information technology.
Networking is considered to be one of the best job as the technology always changes and
this maintains interest of employees in doing task properly.
Implementation of wide area network in the world have increased the number of data
centres at different places and this require a human resource to control all the activities of
inter-connected networking devices. So it has also increased the demand of workforce
and this will result in minimising unemployed people in country.
Invention of wireless fidelity (Wi-Fi) had made interdependency of the work in order to
share data and information among different systems.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2.functional and non-functional requirements (NFR) of inter-networking
Networking requires huge connectivity to forward the data from source to destination.
These requirements may be functional or non functional (Monckeberg, Bergamini and Pérez,
2015). But apart from these networking requirements there might be technical needs of
establishing a huge network such as use of first hope redundancy protocol ( FHRP), network
security mechanism etc. there are lot of tools and services which supports inter-networking
communication. Types of networking requirements are as follows:
Application or Functional requirements: These can be considered as main foundation which
helps in establishing a large inter-connectivity between different devices. These mainly addresses
the basic needs of system design. These are commonly referred as application requirements
which are priorly needed by designer. It includes environmental, business, and performance wise
needs of organisation.
Technical requirements or non functional requirements: It can be determined as those
requirements which are related to the technical aspects. It can vary according to the type and size
of the business operations. Technical requirements are often called as non-functional
requirements of networking. This includes security, resource availability and integrity concerns.
It helps network designer in selecting the hardware platform which is based on the protocols and
specified features.
3. Design of networking based on the human concepts
Network designs are the main aspect of developing a powerful large networking-
connectivity. Design constraints are required to be identified first in order to decide the basic
needs of business and software (Sathick and Venkat, 2015). Network is designed by estimating
multiple factors which involves Cost, time, location, infrastructure equipments, availability of
technical staff members etc. it is basically a structure of network designing which provides basic
architecture and this is helpful in creating a potential communication Chanel between different
workstations.
1. Top-down approach: This concept mainly focus in splitting the tasks of designing. This
ultimately help network designers in getting the desired concept establishing a large
network. This approach enables the structural flow of data and information which leads to
the effective development of inter-connectivity between different systems.
2
Networking requires huge connectivity to forward the data from source to destination.
These requirements may be functional or non functional (Monckeberg, Bergamini and Pérez,
2015). But apart from these networking requirements there might be technical needs of
establishing a huge network such as use of first hope redundancy protocol ( FHRP), network
security mechanism etc. there are lot of tools and services which supports inter-networking
communication. Types of networking requirements are as follows:
Application or Functional requirements: These can be considered as main foundation which
helps in establishing a large inter-connectivity between different devices. These mainly addresses
the basic needs of system design. These are commonly referred as application requirements
which are priorly needed by designer. It includes environmental, business, and performance wise
needs of organisation.
Technical requirements or non functional requirements: It can be determined as those
requirements which are related to the technical aspects. It can vary according to the type and size
of the business operations. Technical requirements are often called as non-functional
requirements of networking. This includes security, resource availability and integrity concerns.
It helps network designer in selecting the hardware platform which is based on the protocols and
specified features.
3. Design of networking based on the human concepts
Network designs are the main aspect of developing a powerful large networking-
connectivity. Design constraints are required to be identified first in order to decide the basic
needs of business and software (Sathick and Venkat, 2015). Network is designed by estimating
multiple factors which involves Cost, time, location, infrastructure equipments, availability of
technical staff members etc. it is basically a structure of network designing which provides basic
architecture and this is helpful in creating a potential communication Chanel between different
workstations.
1. Top-down approach: This concept mainly focus in splitting the tasks of designing. This
ultimately help network designers in getting the desired concept establishing a large
network. This approach enables the structural flow of data and information which leads to
the effective development of inter-connectivity between different systems.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
2. Bottom-up design: This networking approach helps in selecting the physical
requirements of the designing a network connectivity between systems (Silva, da Silva,
and Araújo, H.C., 2017). It is a commonly approachable idea which focuses in
identifying the technologies used in creating a network inter-connectivity.
4. Requirements of internet protocols (IP) and its justification in a tabular form
Internet protocols can be determined as rules and regulation which are applied when any
internet service is provided to a new user. These service providers can use IP addresses to detect
devices and their existence. It is generally a four bit number which is assigned automatically to
every user. When people request server then server responds the system using multiple
connectivity routers and switches. Internet protocols provides services which allows the client
systems to obtain the required data and information. This is mainly used for providing network
interface and identifying the location of addressing. The Latest version of internet protocol is
Ipv6 which is generally 32 bits of number. The table will provide the correct outcome of
calculating the total number of networks with IP addressing.
Address class Address range Subnet connections Usable IP address
A 24-
150.XXX.XXX
2255.225.2425.186 72
B 115-
165.XXX.XXX
225.225.225.286 48
D 126-
255.XXX.XXX
225.225.225.163 63
Above tabular format have explained the use of internet protocols in identifying the connected
networks to a particular server and this helps in estimating the number of devices which are
using for communication perspective. Above table have four addressing classes and it also
provides the range of internet-connection (Xiong and et.al., 2016). This range will be helpful in
identifying number of subnet connections. Use of classes and fixed range will provide detect the
total number of device are exchanging the data and information in a particular time.
3
requirements of the designing a network connectivity between systems (Silva, da Silva,
and Araújo, H.C., 2017). It is a commonly approachable idea which focuses in
identifying the technologies used in creating a network inter-connectivity.
4. Requirements of internet protocols (IP) and its justification in a tabular form
Internet protocols can be determined as rules and regulation which are applied when any
internet service is provided to a new user. These service providers can use IP addresses to detect
devices and their existence. It is generally a four bit number which is assigned automatically to
every user. When people request server then server responds the system using multiple
connectivity routers and switches. Internet protocols provides services which allows the client
systems to obtain the required data and information. This is mainly used for providing network
interface and identifying the location of addressing. The Latest version of internet protocol is
Ipv6 which is generally 32 bits of number. The table will provide the correct outcome of
calculating the total number of networks with IP addressing.
Address class Address range Subnet connections Usable IP address
A 24-
150.XXX.XXX
2255.225.2425.186 72
B 115-
165.XXX.XXX
225.225.225.286 48
D 126-
255.XXX.XXX
225.225.225.163 63
Above tabular format have explained the use of internet protocols in identifying the connected
networks to a particular server and this helps in estimating the number of devices which are
using for communication perspective. Above table have four addressing classes and it also
provides the range of internet-connection (Xiong and et.al., 2016). This range will be helpful in
identifying number of subnet connections. Use of classes and fixed range will provide detect the
total number of device are exchanging the data and information in a particular time.
3

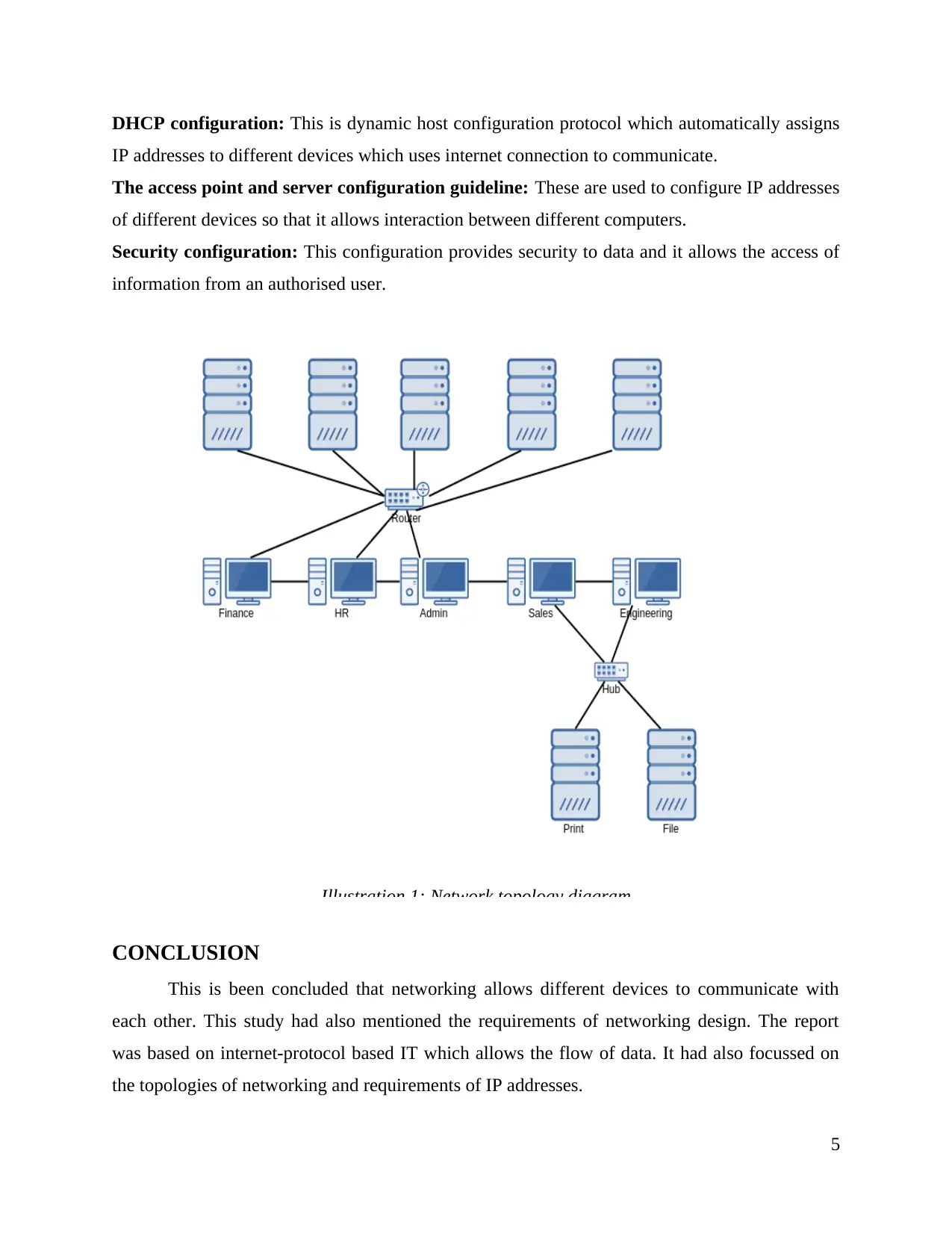
5. Topology diagram of networking including Switch configuration, Router configuration,DHCP
configuration
Topology diagram represents the arrangement of interconnected systems. Networking
topology is a systematic description of different peripheral devices which shares information.
This is referred as an architecture which consists of a common network. The networking
architecture might be connected through physical channels or it may be a virtual connection
which do not require any physical nodes to build a network. There are different kinds of
networking topologies available which are as follows:
1. Point-to-point topology- This type of computer networking allows the direct connection
between different devices. It is considered as the simplest method of networking
topology.
2. Bus topology- it is basically uses a one main node to connect all the systems together.
Among these computers one system can be considered as the server which provides
connectivity and facilitates the powerful communication. But there is also a negative side
in this kind of topology as if breakage in main cable leads to the destruction of all the
connected devices.
3. Star topology- In this networking topology every system is connected to a central device
which provides the functionality to share information (Ziri, Samsudin and Fontaine,
2017). It is most popular architecture which allows the interconnectivity of multiple
systems through a main system which is called as hub.
4. Ring topology- This architecture allows the connection of different systems in a circular
structure. This allows the movement of data in one direction. This structure is easy to
build and install.
5. Hybrid topology- this allows the randomly connected devices which can be combination
of all different kinds of topologies.
Switch configuration: This is used to receive, process and forward the packets of information
to various destination systems. It is generally small packets of information which passes through
different routes
Router configuration: It is mainly a way of taking these data packets from source to
destination. Shortest distance is selected to forward the data packets (Career in networking,
2018).
4
configuration
Topology diagram represents the arrangement of interconnected systems. Networking
topology is a systematic description of different peripheral devices which shares information.
This is referred as an architecture which consists of a common network. The networking
architecture might be connected through physical channels or it may be a virtual connection
which do not require any physical nodes to build a network. There are different kinds of
networking topologies available which are as follows:
1. Point-to-point topology- This type of computer networking allows the direct connection
between different devices. It is considered as the simplest method of networking
topology.
2. Bus topology- it is basically uses a one main node to connect all the systems together.
Among these computers one system can be considered as the server which provides
connectivity and facilitates the powerful communication. But there is also a negative side
in this kind of topology as if breakage in main cable leads to the destruction of all the
connected devices.
3. Star topology- In this networking topology every system is connected to a central device
which provides the functionality to share information (Ziri, Samsudin and Fontaine,
2017). It is most popular architecture which allows the interconnectivity of multiple
systems through a main system which is called as hub.
4. Ring topology- This architecture allows the connection of different systems in a circular
structure. This allows the movement of data in one direction. This structure is easy to
build and install.
5. Hybrid topology- this allows the randomly connected devices which can be combination
of all different kinds of topologies.
Switch configuration: This is used to receive, process and forward the packets of information
to various destination systems. It is generally small packets of information which passes through
different routes
Router configuration: It is mainly a way of taking these data packets from source to
destination. Shortest distance is selected to forward the data packets (Career in networking,
2018).
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
DHCP configuration: This is dynamic host configuration protocol which automatically assigns
IP addresses to different devices which uses internet connection to communicate.
The access point and server configuration guideline: These are used to configure IP addresses
of different devices so that it allows interaction between different computers.
Security configuration: This configuration provides security to data and it allows the access of
information from an authorised user.
CONCLUSION
This is been concluded that networking allows different devices to communicate with
each other. This study had also mentioned the requirements of networking design. The report
was based on internet-protocol based IT which allows the flow of data. It had also focussed on
the topologies of networking and requirements of IP addresses.
5
Illustration 1: Network topology diagram
IP addresses to different devices which uses internet connection to communicate.
The access point and server configuration guideline: These are used to configure IP addresses
of different devices so that it allows interaction between different computers.
Security configuration: This configuration provides security to data and it allows the access of
information from an authorised user.
CONCLUSION
This is been concluded that networking allows different devices to communicate with
each other. This study had also mentioned the requirements of networking design. The report
was based on internet-protocol based IT which allows the flow of data. It had also focussed on
the topologies of networking and requirements of IP addresses.
5
Illustration 1: Network topology diagram
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Books and journals
Hamid, S. and et.al., 2015. Understanding students' perceptions of the benefits of online social
networking use for teaching and learning. The Internet and Higher Education. 26.pp.1-9.
Monckeberg, J. C., Bergamini, K. and Pérez, C., 2015. Environmental enforcement networking
efforts in Chile: Lessons learnt and challenges ahead. M. Faure, P. De Smedt & A. Stas,
Environmental enforcement networks. pp.470-481.
Sathick, J. and Venkat, J., 2015. A generic framework for extraction of knowledge from social
web sources (social networking websites) for an online recommendation system. The
International Review of Research in Open and Distributed Learning. 16(2).
Silva, M., da Silva, S.M. and Araújo, H.C., 2017. Networking in education: From concept to
action–An analytical view on the Educational Territories of Priority Intervention (TEIP) in
Northern Portugal. Improving Schools. 20(1). pp.48-61.
Xiong, H. and et.al., 2016. Upper Limit Analysis of Scalable Parallel Computing on the Premise
of Reliability Requirement. IETE Technical Review. 33(6). pp.573-583.
Ziri, S. R., Samsudin, A. T. and Fontaine, C., 2017, February. Service Chaining Implementation
in Network Function Virtualization with Software Defined Networking. In Proceedings of
the 5th International Conference on Communications and Broadband Networking (pp. 70-
75). ACM.
Online
Career in networking. 2018. [online]. Available through:<http://imedita.com/blog/career-in-
networking-scope-in-networking/>
6
Books and journals
Hamid, S. and et.al., 2015. Understanding students' perceptions of the benefits of online social
networking use for teaching and learning. The Internet and Higher Education. 26.pp.1-9.
Monckeberg, J. C., Bergamini, K. and Pérez, C., 2015. Environmental enforcement networking
efforts in Chile: Lessons learnt and challenges ahead. M. Faure, P. De Smedt & A. Stas,
Environmental enforcement networks. pp.470-481.
Sathick, J. and Venkat, J., 2015. A generic framework for extraction of knowledge from social
web sources (social networking websites) for an online recommendation system. The
International Review of Research in Open and Distributed Learning. 16(2).
Silva, M., da Silva, S.M. and Araújo, H.C., 2017. Networking in education: From concept to
action–An analytical view on the Educational Territories of Priority Intervention (TEIP) in
Northern Portugal. Improving Schools. 20(1). pp.48-61.
Xiong, H. and et.al., 2016. Upper Limit Analysis of Scalable Parallel Computing on the Premise
of Reliability Requirement. IETE Technical Review. 33(6). pp.573-583.
Ziri, S. R., Samsudin, A. T. and Fontaine, C., 2017, February. Service Chaining Implementation
in Network Function Virtualization with Software Defined Networking. In Proceedings of
the 5th International Conference on Communications and Broadband Networking (pp. 70-
75). ACM.
Online
Career in networking. 2018. [online]. Available through:<http://imedita.com/blog/career-in-
networking-scope-in-networking/>
6
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





