ITC 212: Detailed Solution for Computer Networking Assignment
VerifiedAdded on 2020/05/28
|10
|1390
|65
Homework Assignment
AI Summary
This document presents a comprehensive solution to an ITC 212 computer networking assignment. It addresses various aspects of networking, including the TCP/IP protocol model, data encapsulation, and the roles of different layers like application, transport, network, data-link, and physical layers. The solution also covers the application of Shannon's and Nyquist's theorems to calculate system capacity and signal levels. Furthermore, it explains IPv6 addressing, including link-local, unique local unicast, and global unicast addresses, alongside IPv4 public and private addresses. The assignment delves into DNS resolution methods (recursive and iterative), persistent and non-persistent HTTP connections, and the workings of trackless BitTorrent, including the role of Distributed Hash Tables. The solution provides detailed explanations and references to support the concepts discussed.

1
ITC 212
ITC 212
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Contents
ITC 212......................................................................................................................................1
Question 1:.................................................................................................................................3
Layer 1:..................................................................................................................................3
Layer 2:..................................................................................................................................4
Layer 3:..................................................................................................................................4
Layer 4:..................................................................................................................................4
Layer 5:..................................................................................................................................4
Receiver’s end:...........................................................................................................................5
Question 2:.................................................................................................................................5
Question 3:.................................................................................................................................6
Link Local addresses..............................................................................................................6
Unique Local Unicast addresses............................................................................................6
Global Unicast addresses.......................................................................................................6
Public IPv4 address................................................................................................................7
Private IPv4 address...............................................................................................................7
Question 4:.................................................................................................................................7
Recursive resolution...............................................................................................................8
Iterative resolution.................................................................................................................8
Question 5:.................................................................................................................................8
Persistent HTTP connections.................................................................................................8
Non-persistent HTTP connections.........................................................................................8
Question 6:.................................................................................................................................9
References................................................................................................................................10
Figure 1:Transfer of file.............................................................................................................3
Figure 2:TCP/IP Protocol Architecture......................................................................................3
Figure 3: Format of link local address.......................................................................................6
Figure 4: Format of Unique Local Unicast address...................................................................6
Figure 5: Format of Global Unicast Address.............................................................................6
Contents
ITC 212......................................................................................................................................1
Question 1:.................................................................................................................................3
Layer 1:..................................................................................................................................3
Layer 2:..................................................................................................................................4
Layer 3:..................................................................................................................................4
Layer 4:..................................................................................................................................4
Layer 5:..................................................................................................................................4
Receiver’s end:...........................................................................................................................5
Question 2:.................................................................................................................................5
Question 3:.................................................................................................................................6
Link Local addresses..............................................................................................................6
Unique Local Unicast addresses............................................................................................6
Global Unicast addresses.......................................................................................................6
Public IPv4 address................................................................................................................7
Private IPv4 address...............................................................................................................7
Question 4:.................................................................................................................................7
Recursive resolution...............................................................................................................8
Iterative resolution.................................................................................................................8
Question 5:.................................................................................................................................8
Persistent HTTP connections.................................................................................................8
Non-persistent HTTP connections.........................................................................................8
Question 6:.................................................................................................................................9
References................................................................................................................................10
Figure 1:Transfer of file.............................................................................................................3
Figure 2:TCP/IP Protocol Architecture......................................................................................3
Figure 3: Format of link local address.......................................................................................6
Figure 4: Format of Unique Local Unicast address...................................................................6
Figure 5: Format of Global Unicast Address.............................................................................6

3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
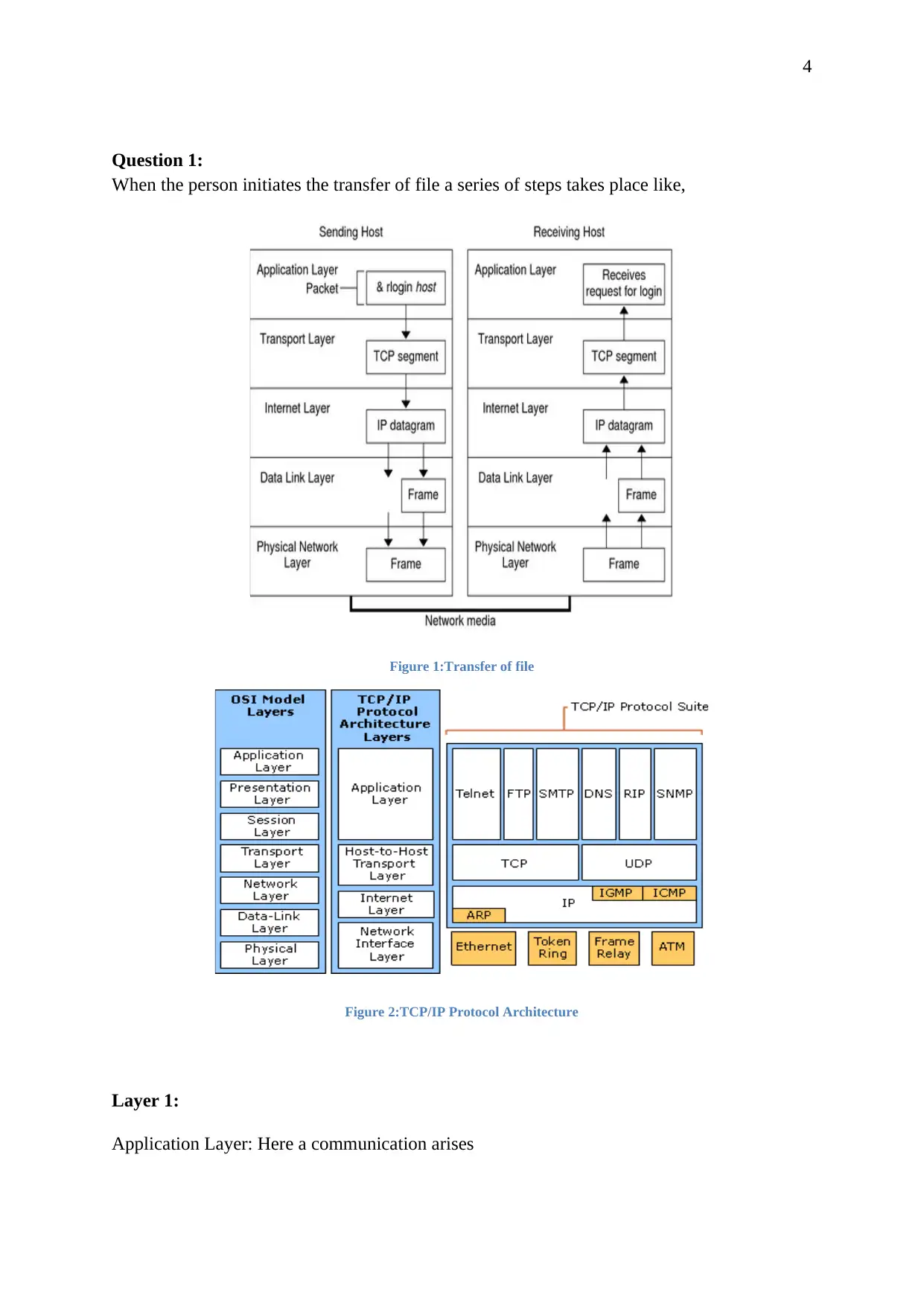
Question 1:
When the person initiates the transfer of file a series of steps takes place like,
Figure 1:Transfer of file
Figure 2:TCP/IP Protocol Architecture
Layer 1:
Application Layer: Here a communication arises
Question 1:
When the person initiates the transfer of file a series of steps takes place like,
Figure 1:Transfer of file
Figure 2:TCP/IP Protocol Architecture
Layer 1:
Application Layer: Here a communication arises
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
The basic work of the application layer is that the protocols of this layer format the file in a
way that it can be easily used by the transport layer protocols. The File Transfer Protocol
(FTP) is used for this file transfer.
Layer 2:
Transport Layer: Here data encapsulation begins
When the file enters the transport layer, the protocols i.e. TCP and UDP initiate the data
encapsulation process. These protocols build a virtual flow of data between the sending and
the receiving application and gives port number to the file.
Layer 3:
Network Interface Layer: The file is prepared for delivery
The file from transport layer protocols is now sending to the internet layer which consists of
the IP protocol. IP protocol formats the file into units known as IP datagrams and then their
IP address is determined to make the delivery easy.
Layer 4:
Data-Link Layer: The file is framed here
The protocols of Data-link layer arranges the IP datagram into frame along with the
attachment of a header and a footer into that frame and checks the errors of the file.
Layer 5:
Physical Network Layer: Here the frames are sent and received
This layer receives the frames from the data link layer and changes the IP addresses into the
hardware addresses according to the network media and then send them (Forouzan, 2007).
Receiver’s end:
When the file reaches the receivers end, the file navigates through the TCP/IP protocol model
in the reverse order.
The basic work of the application layer is that the protocols of this layer format the file in a
way that it can be easily used by the transport layer protocols. The File Transfer Protocol
(FTP) is used for this file transfer.
Layer 2:
Transport Layer: Here data encapsulation begins
When the file enters the transport layer, the protocols i.e. TCP and UDP initiate the data
encapsulation process. These protocols build a virtual flow of data between the sending and
the receiving application and gives port number to the file.
Layer 3:
Network Interface Layer: The file is prepared for delivery
The file from transport layer protocols is now sending to the internet layer which consists of
the IP protocol. IP protocol formats the file into units known as IP datagrams and then their
IP address is determined to make the delivery easy.
Layer 4:
Data-Link Layer: The file is framed here
The protocols of Data-link layer arranges the IP datagram into frame along with the
attachment of a header and a footer into that frame and checks the errors of the file.
Layer 5:
Physical Network Layer: Here the frames are sent and received
This layer receives the frames from the data link layer and changes the IP addresses into the
hardware addresses according to the network media and then send them (Forouzan, 2007).
Receiver’s end:
When the file reaches the receivers end, the file navigates through the TCP/IP protocol model
in the reverse order.

6
Question 2:
This can be solved by Shannon’s theorem which is used to calculate the capacity of the
system in presence of noise.
C = B log2 (1 + SNR)
Here, C= capacity
B= bandwidth
SNR= signal to noise ratio
C= 20 log2 (1+1040)
C=20 log21041
C= 20*10.023
C=200.46mbps
Hence, the highest bit rate of this system is 200.46 mbps.
Nyquist Theorem calculates the number of signals levels.
C=2Blog2M
Here, C= capacity calculated
B= bandwidth
M= no of signal levels
Therefore,
200.46=2*20log2M
Log2M=5.0115
M=32.25(approx.)
Hence, 32 signal levels will be required.
Question 2:
This can be solved by Shannon’s theorem which is used to calculate the capacity of the
system in presence of noise.
C = B log2 (1 + SNR)
Here, C= capacity
B= bandwidth
SNR= signal to noise ratio
C= 20 log2 (1+1040)
C=20 log21041
C= 20*10.023
C=200.46mbps
Hence, the highest bit rate of this system is 200.46 mbps.
Nyquist Theorem calculates the number of signals levels.
C=2Blog2M
Here, C= capacity calculated
B= bandwidth
M= no of signal levels
Therefore,
200.46=2*20log2M
Log2M=5.0115
M=32.25(approx.)
Hence, 32 signal levels will be required.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7
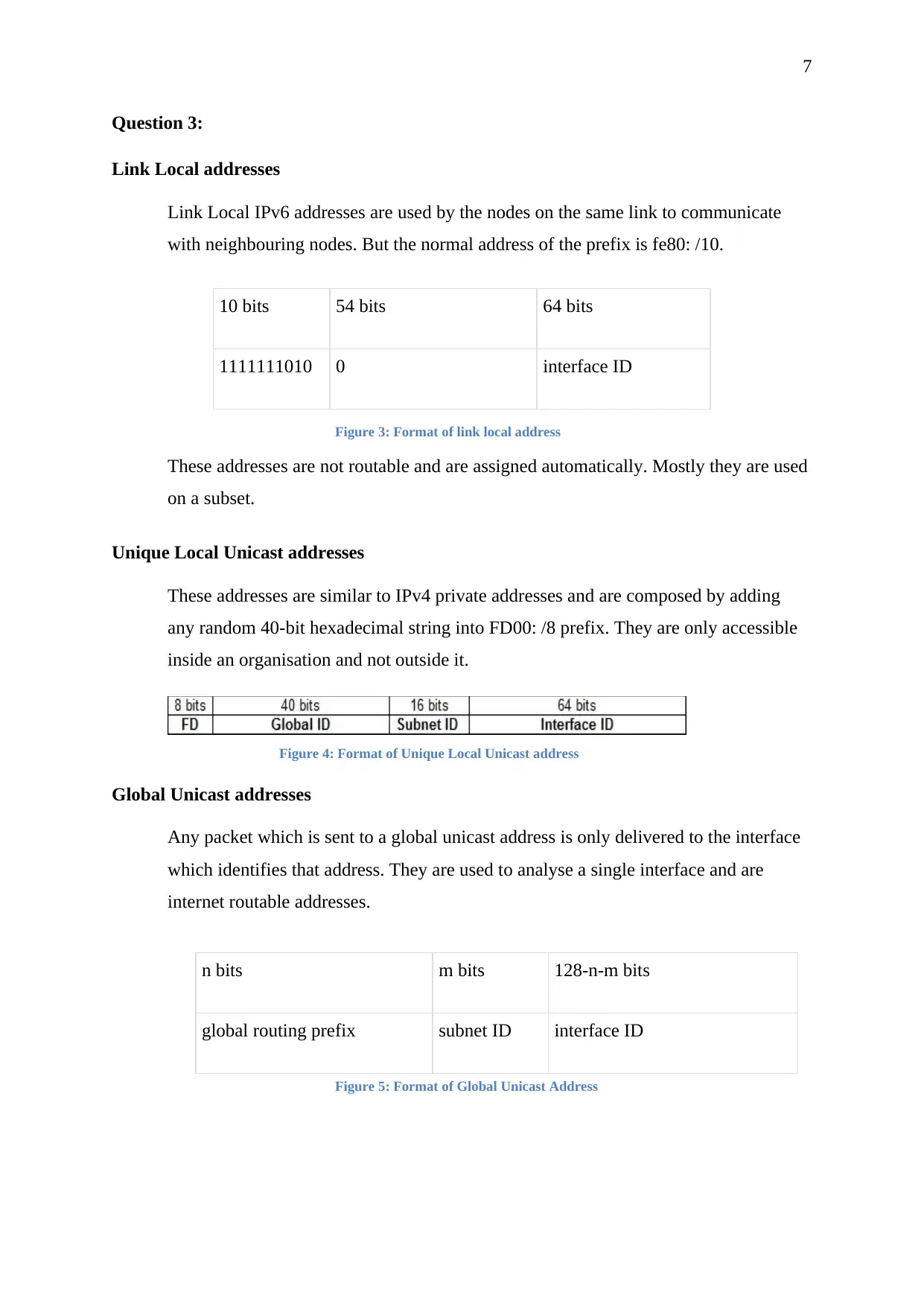
Question 3:
Link Local addresses
Link Local IPv6 addresses are used by the nodes on the same link to communicate
with neighbouring nodes. But the normal address of the prefix is fe80: /10.
Figure 3: Format of link local address
These addresses are not routable and are assigned automatically. Mostly they are used
on a subset.
Unique Local Unicast addresses
These addresses are similar to IPv4 private addresses and are composed by adding
any random 40-bit hexadecimal string into FD00: /8 prefix. They are only accessible
inside an organisation and not outside it.
Figure 4: Format of Unique Local Unicast address
Global Unicast addresses
Any packet which is sent to a global unicast address is only delivered to the interface
which identifies that address. They are used to analyse a single interface and are
internet routable addresses.
Figure 5: Format of Global Unicast Address
10 bits 54 bits 64 bits
1111111010 0 interface ID
n bits m bits 128-n-m bits
global routing prefix subnet ID interface ID
Question 3:
Link Local addresses
Link Local IPv6 addresses are used by the nodes on the same link to communicate
with neighbouring nodes. But the normal address of the prefix is fe80: /10.
Figure 3: Format of link local address
These addresses are not routable and are assigned automatically. Mostly they are used
on a subset.
Unique Local Unicast addresses
These addresses are similar to IPv4 private addresses and are composed by adding
any random 40-bit hexadecimal string into FD00: /8 prefix. They are only accessible
inside an organisation and not outside it.
Figure 4: Format of Unique Local Unicast address
Global Unicast addresses
Any packet which is sent to a global unicast address is only delivered to the interface
which identifies that address. They are used to analyse a single interface and are
internet routable addresses.
Figure 5: Format of Global Unicast Address
10 bits 54 bits 64 bits
1111111010 0 interface ID
n bits m bits 128-n-m bits
global routing prefix subnet ID interface ID
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
IPv4 have only two types of addressing which are public IP address and private IP address.
Public IPv4 address
This address is allocated by InterNIC to any device so that it can directly access the
internet. They are in a form of blocks of CIDR-based addresses and also exist as a
route in the routers of the Internet.
Private IPv4 address
These addresses are assigned to the organisations to develop their own private
network by InterNIC. The private addresses are reserved for class A, class B and class
C. The private address cannot be connected to the internet.
Question 4:
Domain Name System resolves a fully qualified domain name (FQDN) to an IP address. The
two ways by which DNS resolves a domain name are,
Recursive resolution
The client sends a query to the server and expects that the server will solve it
efficiently. The server then searches for resolution in its own database and after that in
its local cache. If the resolution is not found in the database and the cache then the
server goes through the DNS tree until an answer is received by it.
Iterative resolution
Here, when the client sends a query to the server it returns the client IP address of the
server not the complete answer. After receiving this information the clients makes
query to another server and this process goes on till an authoritative answer is not
received. The DNS server only tries to find the query in the local cache (Forouzan,
2007).
Question 5:
Persistent HTTP connections
IPv4 have only two types of addressing which are public IP address and private IP address.
Public IPv4 address
This address is allocated by InterNIC to any device so that it can directly access the
internet. They are in a form of blocks of CIDR-based addresses and also exist as a
route in the routers of the Internet.
Private IPv4 address
These addresses are assigned to the organisations to develop their own private
network by InterNIC. The private addresses are reserved for class A, class B and class
C. The private address cannot be connected to the internet.
Question 4:
Domain Name System resolves a fully qualified domain name (FQDN) to an IP address. The
two ways by which DNS resolves a domain name are,
Recursive resolution
The client sends a query to the server and expects that the server will solve it
efficiently. The server then searches for resolution in its own database and after that in
its local cache. If the resolution is not found in the database and the cache then the
server goes through the DNS tree until an answer is received by it.
Iterative resolution
Here, when the client sends a query to the server it returns the client IP address of the
server not the complete answer. After receiving this information the clients makes
query to another server and this process goes on till an authoritative answer is not
received. The DNS server only tries to find the query in the local cache (Forouzan,
2007).
Question 5:
Persistent HTTP connections

9
When the server sends the response message, it leaves the TCP connection open hence, the
client and the server are allowed to send requests and responses. These connections are the
default mode for HTTP/1.1.
Non-persistent HTTP connections
In this type of connection, the server closes the connection once it sends a response message
to the client. This connection is used only for one request and on response. The default mode
of these connections is HTTP/1.0.
The persistent HTTP connections are more efficient because in these connections the
performance is increased as the CPU’s time is saved in router and hosts. The client do not
have to wait for one response and can send multiple requests simultaneously along with this
the network congestion is also reduced (Irwin, 2016).
Question 6:
In trackless Bit Torrent, the list of people who are downloading the same torrent does not
hold a particular central tracker, and is inside the network of peer downloaders. As a result,
the user should know only one node on the network and not all of them.
Distributed Hash Table is the technology which is used in trackless Bit Torrent to download a
file. The steps to download a file are,
1. To get the tracker URL inside a file the client looks for that .torrent file.
2. The client will now contact this tracker and with the help of this tracker he will get a
list of peers.
3. From that list of peers the file can be downloaded.
4. After downloading the .torrent file, the client figures out the key from this file,
5. This key is now used to get the node from the Distributed Hash Table lookup
6. From this table a peer list is again received and the client downloads the file.
When the server sends the response message, it leaves the TCP connection open hence, the
client and the server are allowed to send requests and responses. These connections are the
default mode for HTTP/1.1.
Non-persistent HTTP connections
In this type of connection, the server closes the connection once it sends a response message
to the client. This connection is used only for one request and on response. The default mode
of these connections is HTTP/1.0.
The persistent HTTP connections are more efficient because in these connections the
performance is increased as the CPU’s time is saved in router and hosts. The client do not
have to wait for one response and can send multiple requests simultaneously along with this
the network congestion is also reduced (Irwin, 2016).
Question 6:
In trackless Bit Torrent, the list of people who are downloading the same torrent does not
hold a particular central tracker, and is inside the network of peer downloaders. As a result,
the user should know only one node on the network and not all of them.
Distributed Hash Table is the technology which is used in trackless Bit Torrent to download a
file. The steps to download a file are,
1. To get the tracker URL inside a file the client looks for that .torrent file.
2. The client will now contact this tracker and with the help of this tracker he will get a
list of peers.
3. From that list of peers the file can be downloaded.
4. After downloading the .torrent file, the client figures out the key from this file,
5. This key is now used to get the node from the Distributed Hash Table lookup
6. From this table a peer list is again received and the client downloads the file.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
References
Forouzan, B., & Fegan, S. (2007). Data communications and networking. New York: McGraw-
Hill Higher Education.
Irwin, J., & Wu, C. (2016). Introduction to Computer Networks and Cybersecurity. Florida: CRC
Press.
References
Forouzan, B., & Fegan, S. (2007). Data communications and networking. New York: McGraw-
Hill Higher Education.
Irwin, J., & Wu, C. (2016). Introduction to Computer Networks and Cybersecurity. Florida: CRC
Press.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





