SIT202 Computer Networks: TCP/IP, Encapsulation and Network Loops
VerifiedAdded on 2023/06/08
|14
|1888
|349
Report
AI Summary
This report provides a comprehensive analysis of computer networks, focusing on the TCP/IP protocol suite, data encapsulation, and network loop scenarios. It explains the TCP/IP four-layer architecture, detailing the encapsulation and decapsulation processes with illustrative diagrams. The report addresses the issue of network loops, specifically broadcast storms caused by hubs and switches, and proposes solutions. Furthermore, it discusses data transmission between devices, including the role of routers and the Point-to-Point protocol, covering LCP, PAP, CHAP, and IPCP. Modulation techniques in digital signals and broadband transmission methods like ASK, FSK, and PSK are also examined. Finally, the report identifies collision domains in a network setup, distinguishing between collisions caused by switches and hubs, while also highlighting the collision avoidance capabilities of bridges. Desklib offers this and many other solved assignments to aid students in their studies.

1
SIT202 Computer Networks
Student's Name
Institutional Affiliation
SIT202 Computer Networks
Student's Name
Institutional Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SIT202 COMPUTER NETWORKS 2
Question 1(1)
Transport Communication protocol/ Internet protocol (TCP/IP) is a suite or a set of
communications protocols that allow two or more devices to communicate on the internet; by
providing end-to-end communication that comprises how it should be broken into packets,
addressing, its transmission and the how it will be received at the destination (Wang et al.,2016).
The TCP/IP has four layers namely application, transport, network and internet layer,
that aid in its functionalities.
Question 1(1)
Transport Communication protocol/ Internet protocol (TCP/IP) is a suite or a set of
communications protocols that allow two or more devices to communicate on the internet; by
providing end-to-end communication that comprises how it should be broken into packets,
addressing, its transmission and the how it will be received at the destination (Wang et al.,2016).
The TCP/IP has four layers namely application, transport, network and internet layer,
that aid in its functionalities.

SIT202 COMPUTER NETWORKS 3
The packets transmitted comprise headers with the host’s addresses for sending and
receiving. During encapsulation, as the packets travel across the TCP/IP protocol stack, the
protocols at every layer are added from the basic headers. The figure below shows the life cycle
of a packet from origin to destination.
In order for the data to travel from source to destination, every OSI layer must
communicate with its peer layer at the destination. In this process, all the protocol interchanges,
between the layers, the information is known as the Protocol Data Units (PDU).
The packets transmitted comprise headers with the host’s addresses for sending and
receiving. During encapsulation, as the packets travel across the TCP/IP protocol stack, the
protocols at every layer are added from the basic headers. The figure below shows the life cycle
of a packet from origin to destination.
In order for the data to travel from source to destination, every OSI layer must
communicate with its peer layer at the destination. In this process, all the protocol interchanges,
between the layers, the information is known as the Protocol Data Units (PDU).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SIT202 COMPUTER NETWORKS 4
Every layer relays on the functional services of the layers beneath it, by use of
encapsulation to convey the PDU into its data field from its upper layer. The relevant headers
that will be required for the layer to perform are added. The headers contain all the information
such as the source and destination addresses. The network layer will offer services to the
transport layer which will eventually present its data to the internetwork subsystem. This
involves encapsulation of the PDU to relay data up to the internetwork subsystem layer while
attaching the required headers to create a datagram.
Every layer relays on the functional services of the layers beneath it, by use of
encapsulation to convey the PDU into its data field from its upper layer. The relevant headers
that will be required for the layer to perform are added. The headers contain all the information
such as the source and destination addresses. The network layer will offer services to the
transport layer which will eventually present its data to the internetwork subsystem. This
involves encapsulation of the PDU to relay data up to the internetwork subsystem layer while
attaching the required headers to create a datagram.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SIT202 COMPUTER NETWORKS 5
Question 1(2)
Decapsulation involves the process of reversing encapsulation by opening wrapped
packets that were sent over the network. Using our diagram above, the reverse will occur when
the packets reach the destination computer. Data is transmitted back to the lower layers of the
TCP/IP protocol stack and the corresponding headers are unpacked/unwrapped and the
information in the headers are used to convey the packets to the exact network that they were
intended to reach(Lin et al., 2016). The process of decapsulation can be summarized as in the
diagram below
Question 2
A network loop involves a configuration where there are several paths between devices
which ensure packets are constantly repeated. Network flooding will occur in the diagram since
the hub will transmit everything that it receives blindly to all the connections in the networks as
shown in the diagram below.
Question 1(2)
Decapsulation involves the process of reversing encapsulation by opening wrapped
packets that were sent over the network. Using our diagram above, the reverse will occur when
the packets reach the destination computer. Data is transmitted back to the lower layers of the
TCP/IP protocol stack and the corresponding headers are unpacked/unwrapped and the
information in the headers are used to convey the packets to the exact network that they were
intended to reach(Lin et al., 2016). The process of decapsulation can be summarized as in the
diagram below
Question 2
A network loop involves a configuration where there are several paths between devices
which ensure packets are constantly repeated. Network flooding will occur in the diagram since
the hub will transmit everything that it receives blindly to all the connections in the networks as
shown in the diagram below.
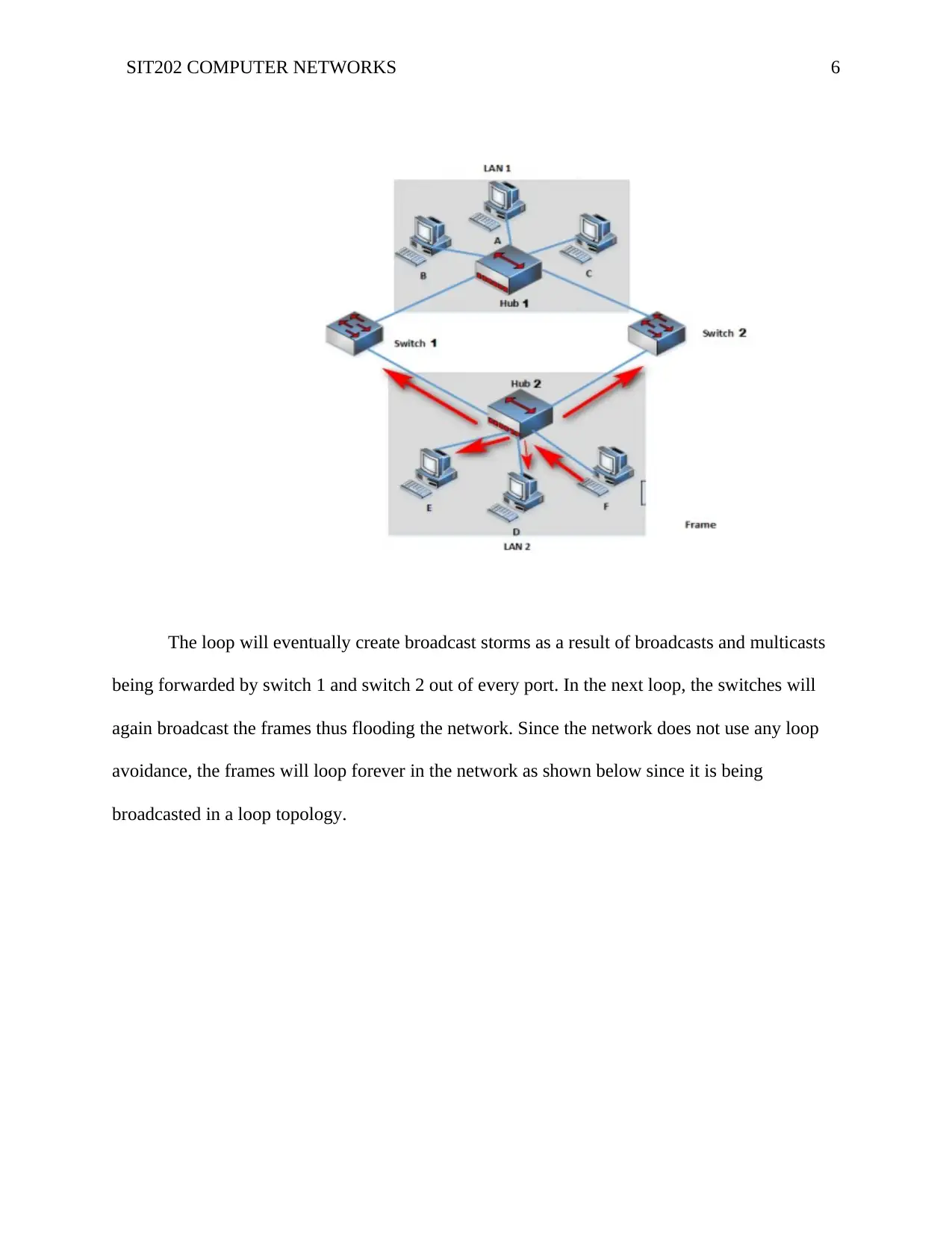
SIT202 COMPUTER NETWORKS 6
The loop will eventually create broadcast storms as a result of broadcasts and multicasts
being forwarded by switch 1 and switch 2 out of every port. In the next loop, the switches will
again broadcast the frames thus flooding the network. Since the network does not use any loop
avoidance, the frames will loop forever in the network as shown below since it is being
broadcasted in a loop topology.
The loop will eventually create broadcast storms as a result of broadcasts and multicasts
being forwarded by switch 1 and switch 2 out of every port. In the next loop, the switches will
again broadcast the frames thus flooding the network. Since the network does not use any loop
avoidance, the frames will loop forever in the network as shown below since it is being
broadcasted in a loop topology.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
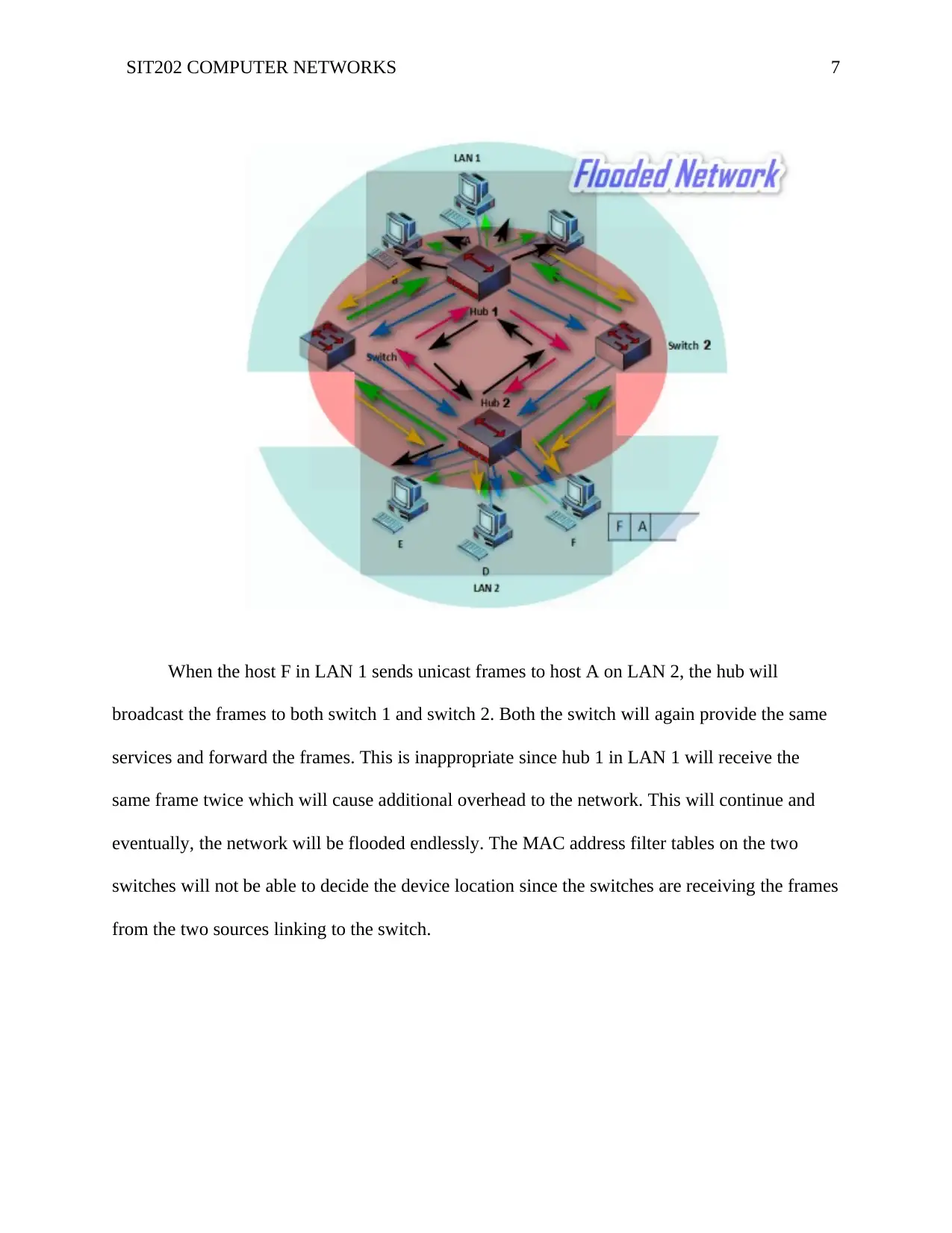
SIT202 COMPUTER NETWORKS 7
When the host F in LAN 1 sends unicast frames to host A on LAN 2, the hub will
broadcast the frames to both switch 1 and switch 2. Both the switch will again provide the same
services and forward the frames. This is inappropriate since hub 1 in LAN 1 will receive the
same frame twice which will cause additional overhead to the network. This will continue and
eventually, the network will be flooded endlessly. The MAC address filter tables on the two
switches will not be able to decide the device location since the switches are receiving the frames
from the two sources linking to the switch.
When the host F in LAN 1 sends unicast frames to host A on LAN 2, the hub will
broadcast the frames to both switch 1 and switch 2. Both the switch will again provide the same
services and forward the frames. This is inappropriate since hub 1 in LAN 1 will receive the
same frame twice which will cause additional overhead to the network. This will continue and
eventually, the network will be flooded endlessly. The MAC address filter tables on the two
switches will not be able to decide the device location since the switches are receiving the frames
from the two sources linking to the switch.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SIT202 COMPUTER NETWORKS 8
Question 3
In the end, data encapsulation will occur at the TCP/IP layers in the transport layer
protocol. The data is transformed to TCP/UDP messages with their headers. It is then
encapsulated inside the body containing the IP address of the data, usually referred to as IP
datagram. After the encapsulation, the data is passed to the data-link layer for transmission
across the network to Bob.
Question 3
In the end, data encapsulation will occur at the TCP/IP layers in the transport layer
protocol. The data is transformed to TCP/UDP messages with their headers. It is then
encapsulated inside the body containing the IP address of the data, usually referred to as IP
datagram. After the encapsulation, the data is passed to the data-link layer for transmission
across the network to Bob.

SIT202 COMPUTER NETWORKS 9
Routers are used to find the shortest or the fastest of the route path between two devices
that are connected to it. Each interface of the router R1 connects to the IP network which links to
router R2 since they have the same subnetwork. When the router receives the datagram from
Alice PC, the network layer adds the network adds the source and destination IP address in the
packet. The data-link layer adds the header to form the frame which is forwarded to the physical
layer.
The frames will be converted into binary and forwarded to the destination MAC address
of the other router in Bob’s end, Router R2. The router will receive the frame and remove the
headers in the decapsulation process. Then, find the destination IP address in the packet. It will
then match the destination IP address to Bob’s Computer IP address in its routing table and
forward the packet through the router’s interface to that network. This procedure will be repeated
until all the packets are received by Bob.
Routers are used to find the shortest or the fastest of the route path between two devices
that are connected to it. Each interface of the router R1 connects to the IP network which links to
router R2 since they have the same subnetwork. When the router receives the datagram from
Alice PC, the network layer adds the network adds the source and destination IP address in the
packet. The data-link layer adds the header to form the frame which is forwarded to the physical
layer.
The frames will be converted into binary and forwarded to the destination MAC address
of the other router in Bob’s end, Router R2. The router will receive the frame and remove the
headers in the decapsulation process. Then, find the destination IP address in the packet. It will
then match the destination IP address to Bob’s Computer IP address in its routing table and
forward the packet through the router’s interface to that network. This procedure will be repeated
until all the packets are received by Bob.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SIT202 COMPUTER NETWORKS 10
Question 4(1)
Point to point comprises of methods for encapsulating multi-protocol datagrams, the link
control protocol for establishing configuration and verify data-link connections which aid in
transporting secured multi-protocol data across the point-to-point links in a Wide Area Network
(Li et al., 2015).
Question 4(2)
The Link Control Protocol (LCP) is used in creation, configuration and establishment of
logical connections/link between the source IP address and the destination IP address. It also
eliminates any error that might be detected in the link. The Password Authentication Protocol
(PAP) is primarily used in granting access rights or authentications between the two ends without
encrypting the passwords. The Challenge Handshake Control Program (CHAP) is used in an
encrypted authentication in point to point network and provide protection against playback
attacks that might arises It is often considered very secure as compared to PAP. The Network
Control Program is used in the provision of configuration and management of facilities that are
applied in the point to point network configuration. It makes it possible for devices to
communicate and access resources from one another remotely through point to point network.
The Internet Protocol Control Protocol (IPCP) is used in the provision of configuration IP
addresses and management of end to end devices connected in a point to point network. It
enables and disables the relevant modules of the IP on both ends
Question 4(1)
Point to point comprises of methods for encapsulating multi-protocol datagrams, the link
control protocol for establishing configuration and verify data-link connections which aid in
transporting secured multi-protocol data across the point-to-point links in a Wide Area Network
(Li et al., 2015).
Question 4(2)
The Link Control Protocol (LCP) is used in creation, configuration and establishment of
logical connections/link between the source IP address and the destination IP address. It also
eliminates any error that might be detected in the link. The Password Authentication Protocol
(PAP) is primarily used in granting access rights or authentications between the two ends without
encrypting the passwords. The Challenge Handshake Control Program (CHAP) is used in an
encrypted authentication in point to point network and provide protection against playback
attacks that might arises It is often considered very secure as compared to PAP. The Network
Control Program is used in the provision of configuration and management of facilities that are
applied in the point to point network configuration. It makes it possible for devices to
communicate and access resources from one another remotely through point to point network.
The Internet Protocol Control Protocol (IPCP) is used in the provision of configuration IP
addresses and management of end to end devices connected in a point to point network. It
enables and disables the relevant modules of the IP on both ends
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SIT202 COMPUTER NETWORKS 11
Question 5(1)
Modulation involves the process of impressing of the data so that it can be transmitted on
the radio carries. The main reason why digital signals are modulated is to squeeze the most data
possible into the least possible amount of spectrum. It ensures data is transmitted as fast as
possible in an assigned bandwidth. Through the process of digital modulation, the noises are
eliminated and robustness to the signals is improved.
Question 5(2)
The broadband transmission involves the transmission of digital signals through a band-
pass channel after modulating the signals; converting the signals from digital to analog signals.
The bandpass channel is a type of a channel whose bandwidth does not start from zero as shown
below (Chung et al., 2015).
The broadband transmission comprises three techniques which are the Amplitude Shift
Keying (ASK), Frequency Shift Keying (FSK) and Phase Shift Keying (PSK). In ASK, the
amplitude of the carrier is modulated according to the message signals, in PSK it conveys data
by modulating the carrier wave and in the FSK, deals with the conversion of signals into binary
states; 0 and 1.
Question 5(1)
Modulation involves the process of impressing of the data so that it can be transmitted on
the radio carries. The main reason why digital signals are modulated is to squeeze the most data
possible into the least possible amount of spectrum. It ensures data is transmitted as fast as
possible in an assigned bandwidth. Through the process of digital modulation, the noises are
eliminated and robustness to the signals is improved.
Question 5(2)
The broadband transmission involves the transmission of digital signals through a band-
pass channel after modulating the signals; converting the signals from digital to analog signals.
The bandpass channel is a type of a channel whose bandwidth does not start from zero as shown
below (Chung et al., 2015).
The broadband transmission comprises three techniques which are the Amplitude Shift
Keying (ASK), Frequency Shift Keying (FSK) and Phase Shift Keying (PSK). In ASK, the
amplitude of the carrier is modulated according to the message signals, in PSK it conveys data
by modulating the carrier wave and in the FSK, deals with the conversion of signals into binary
states; 0 and 1.

SIT202 COMPUTER NETWORKS 12
Question 6
The network set up will have a total of Eight (8) collisions.
Five collisions are experienced in the connection where the switches are. This is because
the switch causes the collision in every device that is connected to its port. Therefore, there will
be a collision between Switch 1 and PC-5, between Switch 2 and PC-6, between Switch 1 and
Switch 2, between Switch 2 and Switch 3, between Router and Switch 3 summing up to a total of
5 collisions as shown in the red spots marked in the diagram below
A hub forwards the collisions, thus all the devices connected on a hub will experience a
resultant of one collision. The network will experience three collisions as a result of hubs; there
will be one resultant collision as a result of PC-4 and Hub 1, the second collision will be as a
Question 6
The network set up will have a total of Eight (8) collisions.
Five collisions are experienced in the connection where the switches are. This is because
the switch causes the collision in every device that is connected to its port. Therefore, there will
be a collision between Switch 1 and PC-5, between Switch 2 and PC-6, between Switch 1 and
Switch 2, between Switch 2 and Switch 3, between Router and Switch 3 summing up to a total of
5 collisions as shown in the red spots marked in the diagram below
A hub forwards the collisions, thus all the devices connected on a hub will experience a
resultant of one collision. The network will experience three collisions as a result of hubs; there
will be one resultant collision as a result of PC-4 and Hub 1, the second collision will be as a
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





