Networks Assignment: Protocols, Security, Services, and Setup
VerifiedAdded on 2023/01/17
|26
|6691
|99
Homework Assignment
AI Summary
This assignment delves into the intricacies of computer networks, encompassing a wide range of topics. It begins with defining a computer network and exploring common media and protocols. The assignment investigates the ownership of the Internet infrastructure, the advantages of fiber-optic cables, and the classification of ISPs. It then examines the roles of Ethernet switches and IP routers, including the protocols and addresses they use. Detailed explanations of IP addresses, MAC addresses, ARP, NAT, RIP, and DHCP are provided. The assignment also covers the OSI model layers for networking components, the concept of 'The Last Mile,' and various communication services with their bandwidth and costs. WiFi security issues and solutions, system logs, firewall functionalities, and packet sniffers are discussed. The assignment also touches upon system monitoring tools, WiFi analyzers, and the setup of a LAMP stack, including the roles of domain registrars and DNS managers. Finally, the assignment covers the steps involved in setting up and securing a virtual server, the purpose of the 'yum' command, and network security tools like ARGUS. It also provides an overview of managed switches, ping, and tracert commands. The assignment encompasses a thorough understanding of network components, protocols, security measures, and practical configurations.

Running head: NETWORKS
Networks
Name of the student:
Name of the university:
Author note:
Networks
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORKS
Networks
1. Define 'computer network' using the definition in class or a better one.
A computer network can be defined as a group of computer systems and some other
computing hardware devices that are linked together via communication channels using
data link communication process to facilitate the share of resources and communication
among a wide range of users. This digital form of telecommunication networks allows the
nodes to share the resources (Gaddala, Satish).
2. What are the most common media and protocols in today's computer networks?
There are generally three types of media in computer networks that includes coaxial
cable, twisted pair cable and fiber optic cable. The most current media type that is being
used is the radio wave media or wireless media which contains two layers namely the
physical layer and data link layer according to the OSI Model. This is used in LAN
technology known as Ethernet.
3. Who owns The Internet infrastructure aka The Internet Backbone? Describe it.
What are the most common media?
According to the Internet Corporation for Assigned Names and Numbers (ICANN), there
is no individual or business or any organization or management that owns the internet
infrastructure. It is a computer web that is distributed all over the world that has
interconnected networks (Wählisch, Matthias, et al.).
The most common media is the twisted pair cable, coaxial cable and fibre optic
chain used as the media for internet propagation.
4. How are fiber-optic cables better than copper for short and long-line
communications cables?
The fiber optical cables are faster than coaxial cables as the optical cables are thinner and
has greater bandwidth capacity as it carries data in the form of light, than the cooper
cables. The fiber optic cables are proved to be more eco friendly than the cooper and
coaxial cables. The fiber optical cable creates less attenuation, and is not easily breakable.
Networks
1. Define 'computer network' using the definition in class or a better one.
A computer network can be defined as a group of computer systems and some other
computing hardware devices that are linked together via communication channels using
data link communication process to facilitate the share of resources and communication
among a wide range of users. This digital form of telecommunication networks allows the
nodes to share the resources (Gaddala, Satish).
2. What are the most common media and protocols in today's computer networks?
There are generally three types of media in computer networks that includes coaxial
cable, twisted pair cable and fiber optic cable. The most current media type that is being
used is the radio wave media or wireless media which contains two layers namely the
physical layer and data link layer according to the OSI Model. This is used in LAN
technology known as Ethernet.
3. Who owns The Internet infrastructure aka The Internet Backbone? Describe it.
What are the most common media?
According to the Internet Corporation for Assigned Names and Numbers (ICANN), there
is no individual or business or any organization or management that owns the internet
infrastructure. It is a computer web that is distributed all over the world that has
interconnected networks (Wählisch, Matthias, et al.).
The most common media is the twisted pair cable, coaxial cable and fibre optic
chain used as the media for internet propagation.
4. How are fiber-optic cables better than copper for short and long-line
communications cables?
The fiber optical cables are faster than coaxial cables as the optical cables are thinner and
has greater bandwidth capacity as it carries data in the form of light, than the cooper
cables. The fiber optic cables are proved to be more eco friendly than the cooper and
coaxial cables. The fiber optical cable creates less attenuation, and is not easily breakable.

2NETWORKS
5. Explain the 4 Tier system for classifying ISPs.
An Internet Service Provider is a group that delivers services for consuming and
accessing the internet. The ISP is divided in 4 tiers. The tier 1 has vast network and they
do not need to purchase a connection from the internet backbone. The Tier 2 are the
providers that have some interconnected agreements and has to purchase some the
connections. Tier 3 only purchases the connection for their internet which is distributed
broadly in the 4th Tier (Wichtlhuber, et al.).
6. What are the roles of the Ethernet Switch and IP Router in a SOHO or SMB
computer network? What protocols and addresses are used by each to carry their
traffic? What OSI layers do they work on?
The switch allows to connect many devices and maintain the traffic between two devices
from getting interrupted on the same network. Switches allow controlling various parts of
networks and monitoring the usage. It provides communication that is faster than internet
in SOHO and SMB computer network (Alani, Mohammed M).
Point to point protocol over Ethernet is used by each to carry their traffic.
The 4th layer of OSI model is the transport coat and works on the traffic protocols.
7. Name and describe each of these addresses and protocols: IP Address, MAC
Address, ARP, NAT, RIP, DHCP.
An IP Address is a numerical label assigned to each device connected to the computer
network using the internet protocol. An IP Address serves two main functions, it host
network interface identification and location addressing.
A media access control address or MAC address is a hardware identity number that
identifies each device on a network (Christopher, et al.).
The address resolution protocol (ARP) is a communication protocol that is used for
exploring the link layer address.
Network address translation is a process of remapping the IP address space of one
to another by modifying the information of network address.
RIT is the Routing Information Protocol that ensures that the information is shared in
routers during the traffic among interconnected LANS.
DHCP is the Dynamic Host Configuration Protocol is management protocol used on
UDP/IP
5. Explain the 4 Tier system for classifying ISPs.
An Internet Service Provider is a group that delivers services for consuming and
accessing the internet. The ISP is divided in 4 tiers. The tier 1 has vast network and they
do not need to purchase a connection from the internet backbone. The Tier 2 are the
providers that have some interconnected agreements and has to purchase some the
connections. Tier 3 only purchases the connection for their internet which is distributed
broadly in the 4th Tier (Wichtlhuber, et al.).
6. What are the roles of the Ethernet Switch and IP Router in a SOHO or SMB
computer network? What protocols and addresses are used by each to carry their
traffic? What OSI layers do they work on?
The switch allows to connect many devices and maintain the traffic between two devices
from getting interrupted on the same network. Switches allow controlling various parts of
networks and monitoring the usage. It provides communication that is faster than internet
in SOHO and SMB computer network (Alani, Mohammed M).
Point to point protocol over Ethernet is used by each to carry their traffic.
The 4th layer of OSI model is the transport coat and works on the traffic protocols.
7. Name and describe each of these addresses and protocols: IP Address, MAC
Address, ARP, NAT, RIP, DHCP.
An IP Address is a numerical label assigned to each device connected to the computer
network using the internet protocol. An IP Address serves two main functions, it host
network interface identification and location addressing.
A media access control address or MAC address is a hardware identity number that
identifies each device on a network (Christopher, et al.).
The address resolution protocol (ARP) is a communication protocol that is used for
exploring the link layer address.
Network address translation is a process of remapping the IP address space of one
to another by modifying the information of network address.
RIT is the Routing Information Protocol that ensures that the information is shared in
routers during the traffic among interconnected LANS.
DHCP is the Dynamic Host Configuration Protocol is management protocol used on
UDP/IP
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORKS
8. On which OSI layer does each of these networking components operate? Ethernet
Switch, IP Router, Cable/RF.
At the 7th layer or the application coating of the OSI model the Ethernet switch is
operated.
IP Router is operated in the system layer that is sheet 3 and also on the second layer
that is the Data Layer (Frank, E. H., & Martin, R).
Cable or RF is operated in the last layer of the OSI Model which is the physical sheet.
9. What is 'The Last Mile' for network or telephone connections? What services are
offered over copper wire? What services are offered over fiber optic cables?
The last mile refers to the portion of the network telecommunications chain that reaches t
he end user's premises physically (Gómez-Cuba, et al).
Cable and DSL internet uses cables made from cooper for transmitting signals. Copper
broadband internet refers to T-carrier lines of T1, T3 and EoC.
Optical fiber wires are used in the broadcasting companies.
10. Characterize each of these common communications services and give it's
bandwidth and approximate cost: POTS, ISDN, T-1, T-3, OC-3, OC-12, FIOS, DSL,
Cable.
The plain old service from the standard telephone which had slow speed communication
and bandwidth is known as the POTS services.
ISDN, integrated services digital network is a set of communication standard for digital
transmissions. It has 128 kbit/s duplex bandwidth. It can cost $60.00 monthly and is
costly (Bocker, Peter.)
T1 carrier is a digital transmission line has 1.544 Mbps speed which is less costly than
ISDN.
T-3 line is a physical circuit that has high speed, media with 44.736 Mbps speed. It costs
$3,000 per month.
Oc-3 carries data on a third level of a synchronous optical network with 155.52 Mbps.
OC-12 is the optical carrier transmission that speeds up to 622.08 Mbit/s.
FIOS speeds up to 940 Mbps and costs $69.99 per month.
DSL’s speed ranges from 128 kbps to 3 Mbps. It costs $20 - $60 per month.
Cable has a bandwidth of 1000 Mbps and costs $80 per month.
8. On which OSI layer does each of these networking components operate? Ethernet
Switch, IP Router, Cable/RF.
At the 7th layer or the application coating of the OSI model the Ethernet switch is
operated.
IP Router is operated in the system layer that is sheet 3 and also on the second layer
that is the Data Layer (Frank, E. H., & Martin, R).
Cable or RF is operated in the last layer of the OSI Model which is the physical sheet.
9. What is 'The Last Mile' for network or telephone connections? What services are
offered over copper wire? What services are offered over fiber optic cables?
The last mile refers to the portion of the network telecommunications chain that reaches t
he end user's premises physically (Gómez-Cuba, et al).
Cable and DSL internet uses cables made from cooper for transmitting signals. Copper
broadband internet refers to T-carrier lines of T1, T3 and EoC.
Optical fiber wires are used in the broadcasting companies.
10. Characterize each of these common communications services and give it's
bandwidth and approximate cost: POTS, ISDN, T-1, T-3, OC-3, OC-12, FIOS, DSL,
Cable.
The plain old service from the standard telephone which had slow speed communication
and bandwidth is known as the POTS services.
ISDN, integrated services digital network is a set of communication standard for digital
transmissions. It has 128 kbit/s duplex bandwidth. It can cost $60.00 monthly and is
costly (Bocker, Peter.)
T1 carrier is a digital transmission line has 1.544 Mbps speed which is less costly than
ISDN.
T-3 line is a physical circuit that has high speed, media with 44.736 Mbps speed. It costs
$3,000 per month.
Oc-3 carries data on a third level of a synchronous optical network with 155.52 Mbps.
OC-12 is the optical carrier transmission that speeds up to 622.08 Mbit/s.
FIOS speeds up to 940 Mbps and costs $69.99 per month.
DSL’s speed ranges from 128 kbps to 3 Mbps. It costs $20 - $60 per month.
Cable has a bandwidth of 1000 Mbps and costs $80 per month.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4NETWORKS
11. What's the problem with WiFi and security? What steps are needed to secure WiFi?
The security protocol that is used to protect the Wi-Fi connections is easy to break and
exposes wireless internet traffic. To secure the Wi-Fi connection the most important step
is to encrypt the Wi-Fi network (Shen, Wenlong, et al.). WPA is the strongest encryption
available for the Wi-Fi network.
12. What's found in the system logs /var/log/secure and /var/log/messages?
The system log file contains events logged by the components of the operating system. T
he operating system itself often predetermines these events. System log files may contain
device changes information, device drivers, system changes, events, operations, and more
.
13. In general, what does a firewall do? What features of Linux were demonstrated for
firewalling a server?
Software firewalls are installed in the devices like a software program which can be
customized and gives control over the function and protection area. It prevents
unauthorized access to the network and works as a barrier which controls incoming and
outgoing network traffic (Suh, Michelle, et al). Features like proxy servers, circuit
level gateway, packet filter, application gateway were verified in order to firewall a
server.
14. What does a 'packet sniffer' do? Name a common packet sniffer.
A packet sniffer is a tool that captures data packet all over the computer network. It is
similar as the process of wire tapping of a telephone network. A packet sniffer can be
either in the form of hardware or software which may allow the unauthorized access of
sensitive data (Verma, Atul, Ankita Singh)
The most common packet sniffer is tcpdump.
11. What's the problem with WiFi and security? What steps are needed to secure WiFi?
The security protocol that is used to protect the Wi-Fi connections is easy to break and
exposes wireless internet traffic. To secure the Wi-Fi connection the most important step
is to encrypt the Wi-Fi network (Shen, Wenlong, et al.). WPA is the strongest encryption
available for the Wi-Fi network.
12. What's found in the system logs /var/log/secure and /var/log/messages?
The system log file contains events logged by the components of the operating system. T
he operating system itself often predetermines these events. System log files may contain
device changes information, device drivers, system changes, events, operations, and more
.
13. In general, what does a firewall do? What features of Linux were demonstrated for
firewalling a server?
Software firewalls are installed in the devices like a software program which can be
customized and gives control over the function and protection area. It prevents
unauthorized access to the network and works as a barrier which controls incoming and
outgoing network traffic (Suh, Michelle, et al). Features like proxy servers, circuit
level gateway, packet filter, application gateway were verified in order to firewall a
server.
14. What does a 'packet sniffer' do? Name a common packet sniffer.
A packet sniffer is a tool that captures data packet all over the computer network. It is
similar as the process of wire tapping of a telephone network. A packet sniffer can be
either in the form of hardware or software which may allow the unauthorized access of
sensitive data (Verma, Atul, Ankita Singh)
The most common packet sniffer is tcpdump.

5NETWORKS
15. What does a system monitor like Nagios do?
A system monitor like Nagios helps the organizations to identify and provide solution to
issues regarding IT infrastructure. The open source network monitoring solution can be
difficult to integrate into automatic processes of provisioning (Enterprises, Nagios).
16. Name two softwares for monitoring or probing network security.
Solarwinds Network Performance Monitor and Nagios XI are the two software for
monitoring or probing network security (Hernantes, et al)
17. What are 'WiFi Analyzers' and 'WiFi Spectrum Analyzers'? What does each show?
Why is a spectrum analyzer important for a network technician's toolkit?
Wi-Fi analyzers help to recognize Wi-Fi glitches and find the best network or the best
area for the router admittance point by revolving the device into an analyzer in wireless
network mode. Whereas the Wi-Fi spectrum analyzer measures the signal strength of the
Wi-Fi in a certain area or region.
Spectrum analyzer identifies the amount of the noise in the RF band. They assist
in configuration of a Wi-Fi network.
18. In the demo of setting up a LAMP stack: What does 'LAMP' stand for? What are
the roles of RackSpace and GoDaddy in the setup? What is 'reverse DNS' and why
is it important? How were dig and nslookup used to check the setup?
LAMP is the model for web service stacks. It is the abbreviation of its four unique open
basis components namely Linux Server, MySql, , Apache HTTP, RDBMS and the PHP
software design language.
Reverse DNS is a domain name mapping IP address which is opposite to the
forward DNS mapping domain. Reverse DNS is used for tracking website visitor.
Nslookup is used for troubleshooting DNS connected difficulties. It can be
castoff in collaborating and no cooperating mode where we have to type nslookup on the
command line of the nslookup command prompt.
15. What does a system monitor like Nagios do?
A system monitor like Nagios helps the organizations to identify and provide solution to
issues regarding IT infrastructure. The open source network monitoring solution can be
difficult to integrate into automatic processes of provisioning (Enterprises, Nagios).
16. Name two softwares for monitoring or probing network security.
Solarwinds Network Performance Monitor and Nagios XI are the two software for
monitoring or probing network security (Hernantes, et al)
17. What are 'WiFi Analyzers' and 'WiFi Spectrum Analyzers'? What does each show?
Why is a spectrum analyzer important for a network technician's toolkit?
Wi-Fi analyzers help to recognize Wi-Fi glitches and find the best network or the best
area for the router admittance point by revolving the device into an analyzer in wireless
network mode. Whereas the Wi-Fi spectrum analyzer measures the signal strength of the
Wi-Fi in a certain area or region.
Spectrum analyzer identifies the amount of the noise in the RF band. They assist
in configuration of a Wi-Fi network.
18. In the demo of setting up a LAMP stack: What does 'LAMP' stand for? What are
the roles of RackSpace and GoDaddy in the setup? What is 'reverse DNS' and why
is it important? How were dig and nslookup used to check the setup?
LAMP is the model for web service stacks. It is the abbreviation of its four unique open
basis components namely Linux Server, MySql, , Apache HTTP, RDBMS and the PHP
software design language.
Reverse DNS is a domain name mapping IP address which is opposite to the
forward DNS mapping domain. Reverse DNS is used for tracking website visitor.
Nslookup is used for troubleshooting DNS connected difficulties. It can be
castoff in collaborating and no cooperating mode where we have to type nslookup on the
command line of the nslookup command prompt.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORKS
19. What does a domain registrar provide for a web server? What's the DNS manager
used for?
Domain registrar manages the reservation of internet domain names. DNS management
software controls the domain name system server clusters. This reduces the human error
during editing complex DNS data.
20. What were the few major steps in the class demo of setting up and securing a virtual
server? Include the two that required a credit card to complete...
The major steps of setting up a virtual server are user formation, network, package
management, , configuration, updating installation, , Firewalls and iptables, NTP
Configuration, Daemon Configuration, Securing SSH, Further Hardening and logging
and SE Linux. The daemon formation and securing SSH requires payment before
configuration.
21. As the server was set up, this command was run:
22. yum install gcc make automake autoconf libtool bind-utils openssl openssl-devel
mod_ssl sendmail sendmail-cf mailx dovecot
What it 'yum' and what does it do? What is the purpose of each component
installed?
YUM or Yellowdog Updater Modified is both an open basis knowledge line and a
graphical bundle tool for the Linux systems based on RPM (Red Hat Packet Manager). It also
enables users and system administrators that easily installs, updates and removes or search a
system for software packages.
23. What's 'ping' used for? What does 'tracert' show?
Ping is used to ensure that the user is actually using the computer as the host. Ping works
by sending ICMP request to specified location.
The tracert command shows several details of the path that isbtaken by a packet
from the computer to the specific destination.
19. What does a domain registrar provide for a web server? What's the DNS manager
used for?
Domain registrar manages the reservation of internet domain names. DNS management
software controls the domain name system server clusters. This reduces the human error
during editing complex DNS data.
20. What were the few major steps in the class demo of setting up and securing a virtual
server? Include the two that required a credit card to complete...
The major steps of setting up a virtual server are user formation, network, package
management, , configuration, updating installation, , Firewalls and iptables, NTP
Configuration, Daemon Configuration, Securing SSH, Further Hardening and logging
and SE Linux. The daemon formation and securing SSH requires payment before
configuration.
21. As the server was set up, this command was run:
22. yum install gcc make automake autoconf libtool bind-utils openssl openssl-devel
mod_ssl sendmail sendmail-cf mailx dovecot
What it 'yum' and what does it do? What is the purpose of each component
installed?
YUM or Yellowdog Updater Modified is both an open basis knowledge line and a
graphical bundle tool for the Linux systems based on RPM (Red Hat Packet Manager). It also
enables users and system administrators that easily installs, updates and removes or search a
system for software packages.
23. What's 'ping' used for? What does 'tracert' show?
Ping is used to ensure that the user is actually using the computer as the host. Ping works
by sending ICMP request to specified location.
The tracert command shows several details of the path that isbtaken by a packet
from the computer to the specific destination.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORKS
24. What functions does a 'managed switch' provide that a cheap switch doesn't.
Security risk, higher downtime due to no resiliency are the main reason to chose managed
switch over the cheap switch. The managed switch does not provide higher downtime and
hence prioritizes the traffic.
25. Which of the network security tools mentioned in class did you install? What do they
show?
I installed ARGUS as the network security tool. Argus is free and open source tool that is
available for analyzing traffic in network. It shows efficiency in depth analysis of network
data. Argus stands for Audit record Generation and Utilization. The comprehensive
reports are received through big chunks (Bhuyan, et al.)
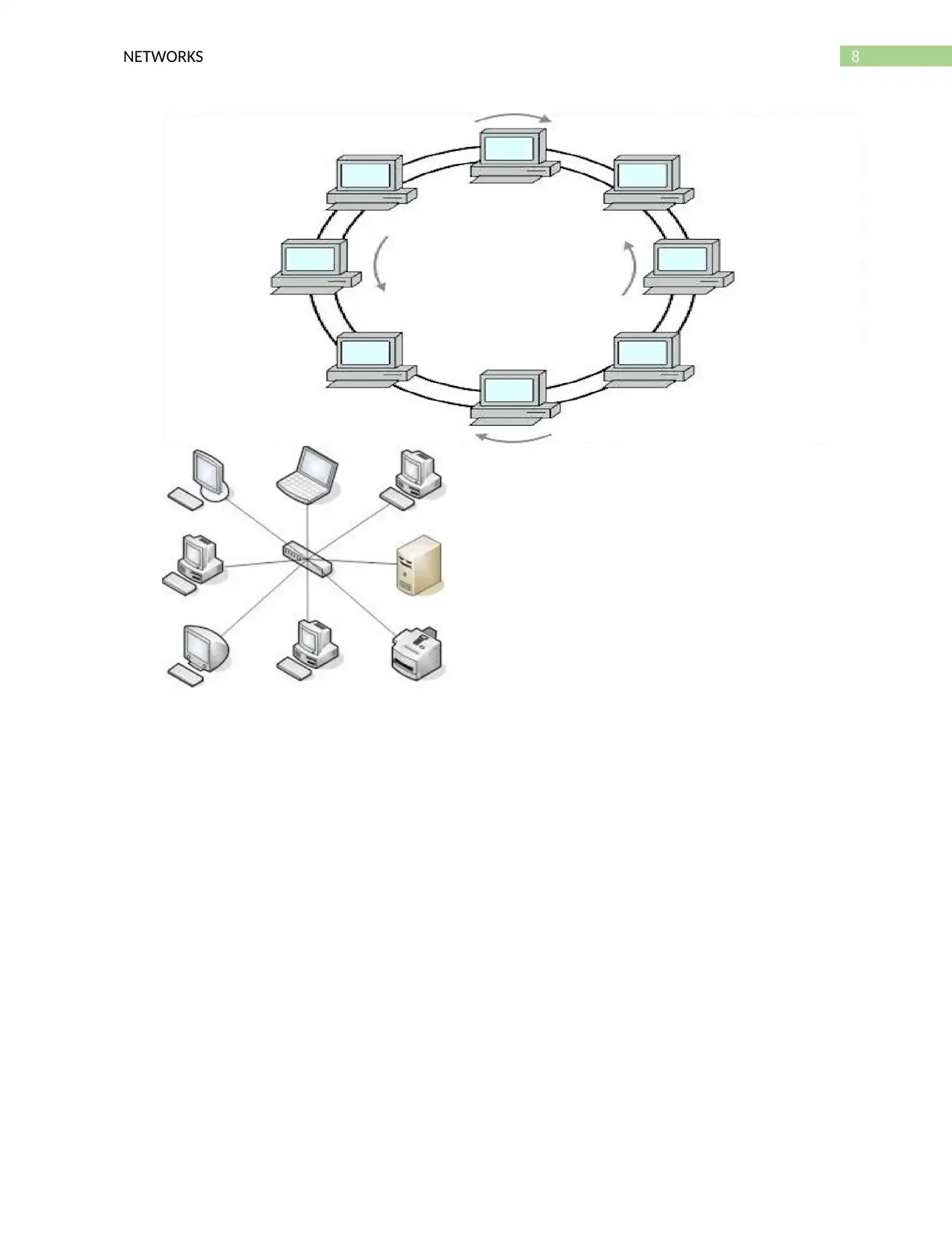
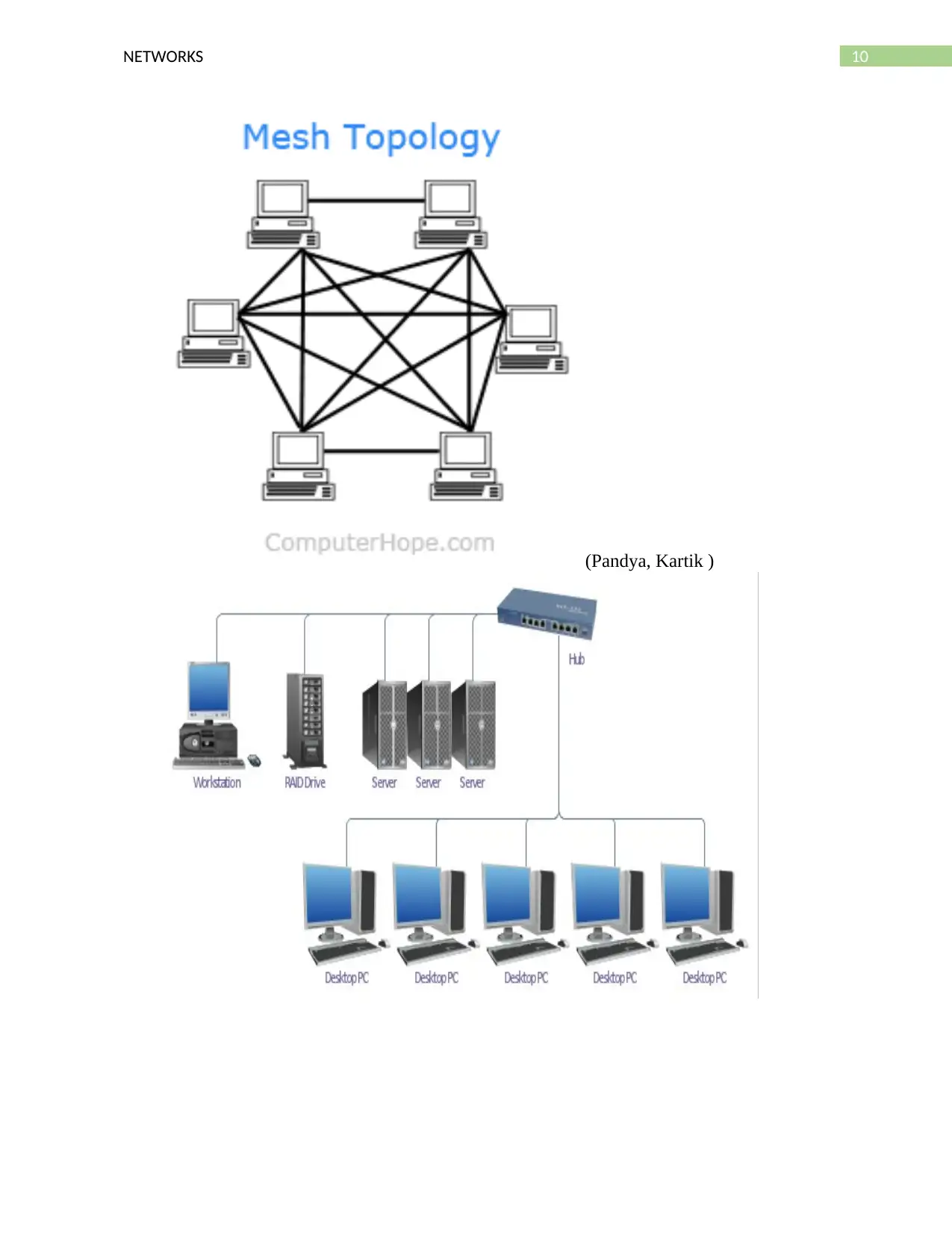
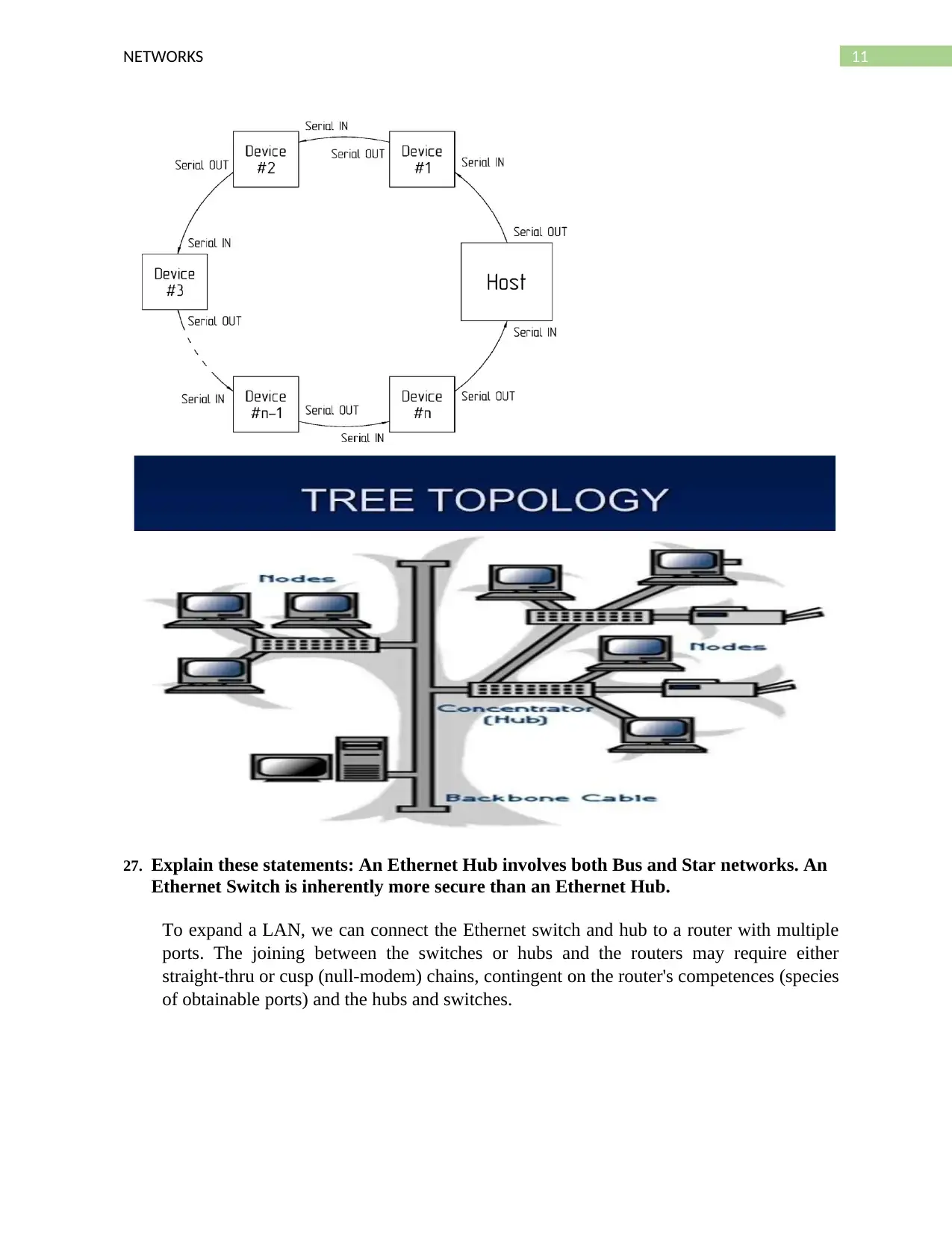
26. Sketch and give a practical application for each of the network topologies sketched
and discussed in class: Serial, Bus, Star, Tree, Ring, and Mesh.
24. What functions does a 'managed switch' provide that a cheap switch doesn't.
Security risk, higher downtime due to no resiliency are the main reason to chose managed
switch over the cheap switch. The managed switch does not provide higher downtime and
hence prioritizes the traffic.
25. Which of the network security tools mentioned in class did you install? What do they
show?
I installed ARGUS as the network security tool. Argus is free and open source tool that is
available for analyzing traffic in network. It shows efficiency in depth analysis of network
data. Argus stands for Audit record Generation and Utilization. The comprehensive
reports are received through big chunks (Bhuyan, et al.)
26. Sketch and give a practical application for each of the network topologies sketched
and discussed in class: Serial, Bus, Star, Tree, Ring, and Mesh.
8NETWORKS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9NETWORKS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10NETWORKS
(Pandya, Kartik )
(Pandya, Kartik )
11NETWORKS
27. Explain these statements: An Ethernet Hub involves both Bus and Star networks. An
Ethernet Switch is inherently more secure than an Ethernet Hub.
To expand a LAN, we can connect the Ethernet switch and hub to a router with multiple
ports. The joining between the switches or hubs and the routers may require either
straight-thru or cusp (null-modem) chains, contingent on the router's competences (species
of obtainable ports) and the hubs and switches.
27. Explain these statements: An Ethernet Hub involves both Bus and Star networks. An
Ethernet Switch is inherently more secure than an Ethernet Hub.
To expand a LAN, we can connect the Ethernet switch and hub to a router with multiple
ports. The joining between the switches or hubs and the routers may require either
straight-thru or cusp (null-modem) chains, contingent on the router's competences (species
of obtainable ports) and the hubs and switches.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 26
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




