Analysis of Cookie Mechanism in Computer Networks: SIT202 Report
VerifiedAdded on 2023/06/04
|5
|767
|281
Report
AI Summary
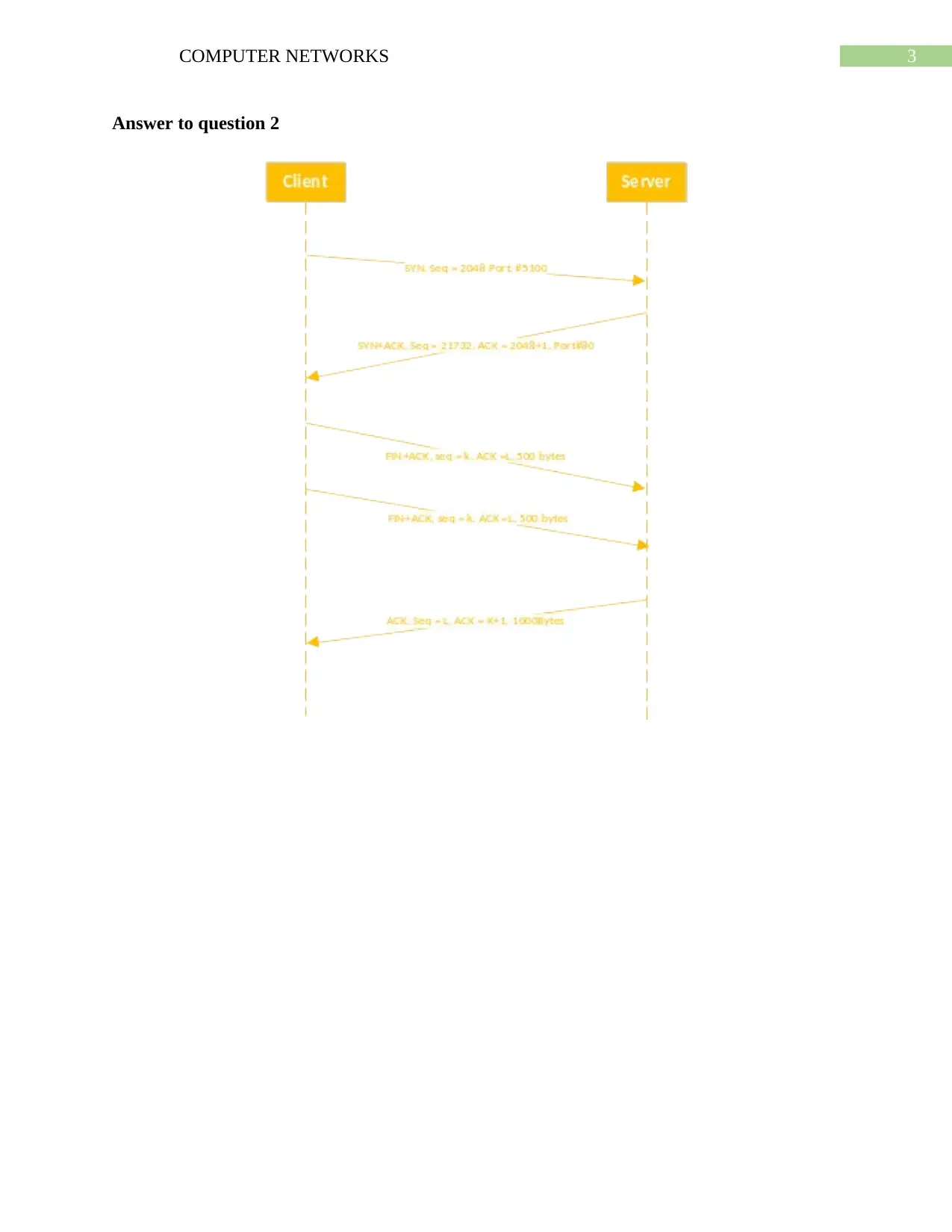
This report analyzes the cookie mechanism within the context of computer networks, focusing on its role in online shopping and web interactions. The assignment addresses the evolution of cookies from a stateless web design, highlighting how they enable stateful relationships between web clients and servers. The report explains the six steps involved in using cookies, including server and client activities, cookie contents, and request/response components. It discusses session cookies, persistent cookies, and the mechanisms by which browsers and servers exchange information to facilitate user tracking and personalized experiences. The report also includes references to relevant research papers and studies on cookies and related technologies.
1 out of 5











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)