SIT202 Computer Networks: Analyzing Cookie Mechanism & TCP Flow
VerifiedAdded on 2023/06/03
|8
|1287
|291
Report
AI Summary
This report provides a detailed analysis of the cookie mechanism used in e-commerce and the TCP message flow in computer networks. It explains the six steps of using cookies in online shopping, including client-server interaction, cookie creation, and data exchange for tracking user behavior. The report also discusses the use of cookies in advertising, detailing how user tracking is maintained between university and advertising servers. Furthermore, it includes a TCP message flow diagram illustrating port numbers, acknowledgment values, and sequence numbers, highlighting the control fields and window size for analyzing response time and connection order. This document is available on Desklib, a platform offering a wide array of study resources and solved assignments for students.

Running head: NETWORKS AND COMMUNICATIONS
Computer Networks
Name of the Student
Name of the University
Author Note
Computer Networks
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1
NETWORKS AND COMMUNICATIONS
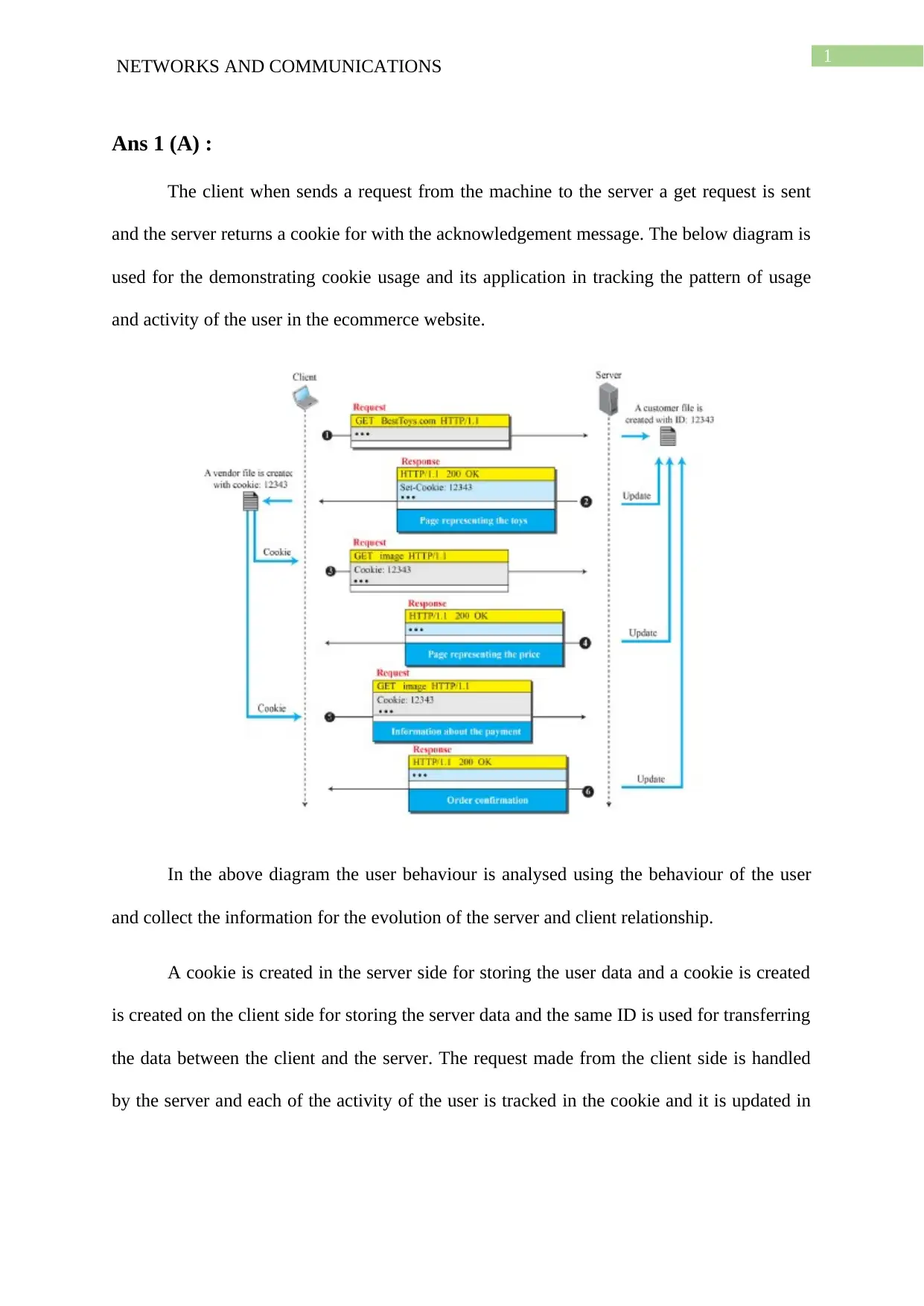
Ans 1 (A) :
The client when sends a request from the machine to the server a get request is sent
and the server returns a cookie for with the acknowledgement message. The below diagram is
used for the demonstrating cookie usage and its application in tracking the pattern of usage
and activity of the user in the ecommerce website.
In the above diagram the user behaviour is analysed using the behaviour of the user
and collect the information for the evolution of the server and client relationship.
A cookie is created in the server side for storing the user data and a cookie is created
is created on the client side for storing the server data and the same ID is used for transferring
the data between the client and the server. The request made from the client side is handled
by the server and each of the activity of the user is tracked in the cookie and it is updated in
NETWORKS AND COMMUNICATIONS
Ans 1 (A) :
The client when sends a request from the machine to the server a get request is sent
and the server returns a cookie for with the acknowledgement message. The below diagram is
used for the demonstrating cookie usage and its application in tracking the pattern of usage
and activity of the user in the ecommerce website.
In the above diagram the user behaviour is analysed using the behaviour of the user
and collect the information for the evolution of the server and client relationship.
A cookie is created in the server side for storing the user data and a cookie is created
is created on the client side for storing the server data and the same ID is used for transferring
the data between the client and the server. The request made from the client side is handled
by the server and each of the activity of the user is tracked in the cookie and it is updated in

2
NETWORKS AND COMMUNICATIONS
the server and saved. The cookie also have an expiration date and time the search pattern of
the user is stored for suggesting the user similar type of items.
The cookie mechanism is applied in the ecommerce website for increasing the
usability and dealing with the placement of orders. The cookie helps to user to redirect to the
desired page by using the data from the cookie and updating the cookie to get the history and
the current item selected. Another request is made by the client that for opening the catalogue
of the shopping website and fetch the files and information from the server.
The web server return the requested page from the cookie and the needed page that is
searched by the user. The details are contained in the searched page and two different types
of cookies are generated for the different process and the first cookie is the session cookie
that is temporary and gets deleted automatically after closing the webpage and the browser.
There are no constraint that have date and time mentioned for limiting the expiration and
configuration can be made such that it can be lasted for a longer time period and restored
when the browser fetched the url again. There is another cookie type i.e. session token that is
applied for the management of the maximum time and eliminate the time boundary of the
cookies.
The desired step is successfully executed and a HTTP header is used for analysing the
request from the user and a response is received form the server depending on the request.
The server responses according to the user request and the cookie header is sent to the user
for sending and receiving the data from the user. The cookie header manages the files and
information from the client for the analysis of the user pattern.
The cookie is used for getting the item requested after checking the availability and
the set of cookie can be modified with the implementation of another cookie and the old
value is changed with the new one for setting the nature. The last procedure of online
NETWORKS AND COMMUNICATIONS
the server and saved. The cookie also have an expiration date and time the search pattern of
the user is stored for suggesting the user similar type of items.
The cookie mechanism is applied in the ecommerce website for increasing the
usability and dealing with the placement of orders. The cookie helps to user to redirect to the
desired page by using the data from the cookie and updating the cookie to get the history and
the current item selected. Another request is made by the client that for opening the catalogue
of the shopping website and fetch the files and information from the server.
The web server return the requested page from the cookie and the needed page that is
searched by the user. The details are contained in the searched page and two different types
of cookies are generated for the different process and the first cookie is the session cookie
that is temporary and gets deleted automatically after closing the webpage and the browser.
There are no constraint that have date and time mentioned for limiting the expiration and
configuration can be made such that it can be lasted for a longer time period and restored
when the browser fetched the url again. There is another cookie type i.e. session token that is
applied for the management of the maximum time and eliminate the time boundary of the
cookies.
The desired step is successfully executed and a HTTP header is used for analysing the
request from the user and a response is received form the server depending on the request.
The server responses according to the user request and the cookie header is sent to the user
for sending and receiving the data from the user. The cookie header manages the files and
information from the client for the analysis of the user pattern.
The cookie is used for getting the item requested after checking the availability and
the set of cookie can be modified with the implementation of another cookie and the old
value is changed with the new one for setting the nature. The last procedure of online
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORKS AND COMMUNICATIONS
shopping is making payment and here a cookie is generated and reducing the time of
transaction. The transaction procedure is used for enabling exchange of information between
the client and the ecommerce website.
Ans 1 (B) :
For redirecting the user and management of the track on the advertising website the
cookie is used and the hyperlink is used where on clicking the banner ad the user is redirected
to the advertising website. The request from the university server is used and the following
diagram shows the flow of the information between the two sited and the servers.
The cookie is transferred from the university server to the advertising server for maintaining a
track on the user. The Get methodology is sued for the retrieving the requested HTML page
and a cookie header is sent from the university server and is updated by storing the values for
the request mage by the user.
In cookie mechanism , two types of file gets generated, client and server side respectively. In
the client side, vendor file gets generated whereas in the server side a customer file is
generated.
NETWORKS AND COMMUNICATIONS
shopping is making payment and here a cookie is generated and reducing the time of
transaction. The transaction procedure is used for enabling exchange of information between
the client and the ecommerce website.
Ans 1 (B) :
For redirecting the user and management of the track on the advertising website the
cookie is used and the hyperlink is used where on clicking the banner ad the user is redirected
to the advertising website. The request from the university server is used and the following
diagram shows the flow of the information between the two sited and the servers.
The cookie is transferred from the university server to the advertising server for maintaining a
track on the user. The Get methodology is sued for the retrieving the requested HTML page
and a cookie header is sent from the university server and is updated by storing the values for
the request mage by the user.
In cookie mechanism , two types of file gets generated, client and server side respectively. In
the client side, vendor file gets generated whereas in the server side a customer file is
generated.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORKS AND COMMUNICATIONS
A request is made from the client end to open the HTML page and set cookie is used for
getting the information. The university and the advertising servers exchanges the cookie
information for tracking the user visiting the website of the manufactured if the user clicks
the banner add to reach the advertising website.
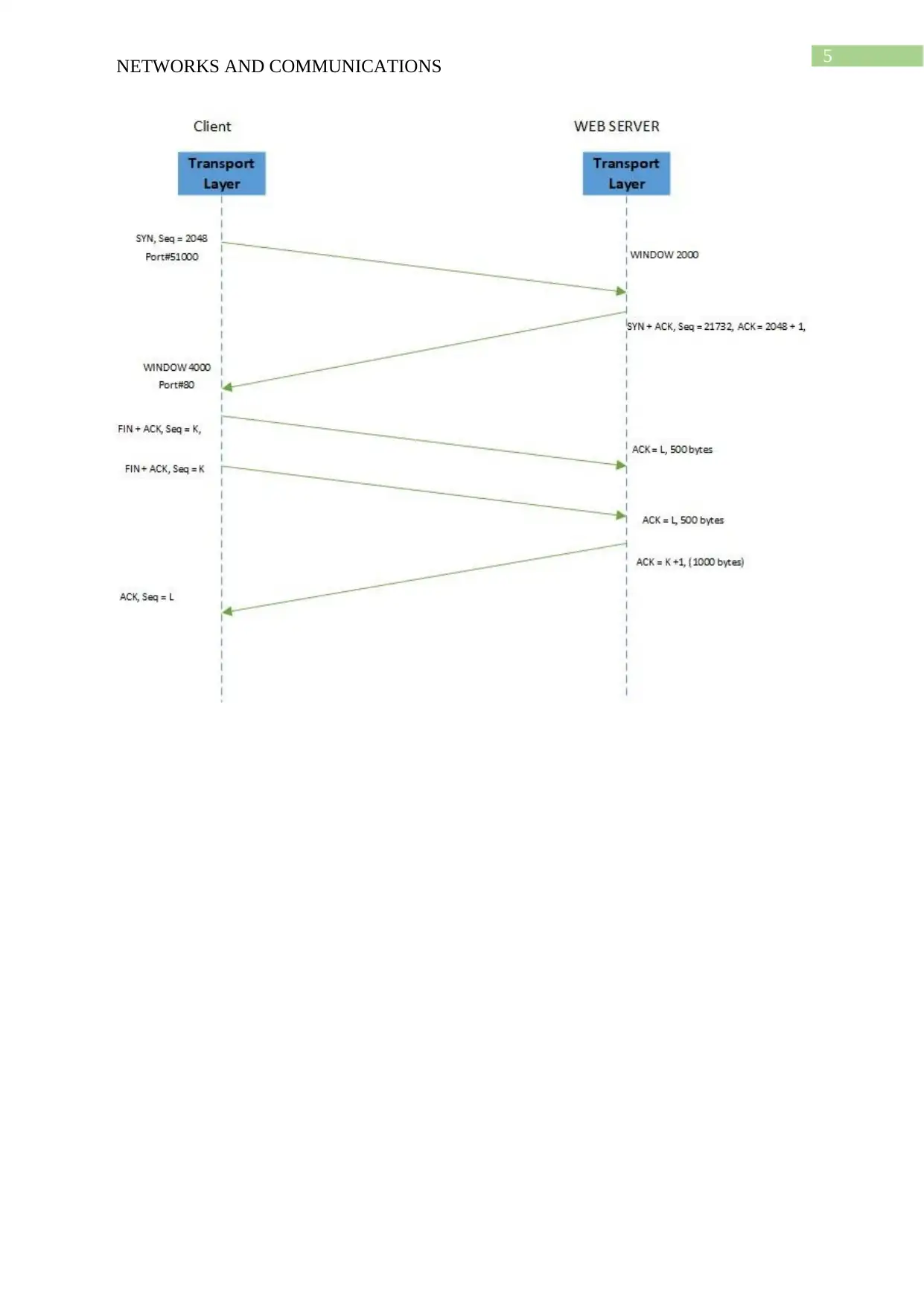
Ans 2 :
The tcp message flow diagram is created for the management of the flow of
information between the client and the server and an initial sequence number and windows
frame is used for management of the sequence header. The following diagram is used for the
demonstration of the port, acknowledgment, value, and sequence number. The control fields
and the window size helps in analysing the response time and demonstration of the order of
connection.
NETWORKS AND COMMUNICATIONS
A request is made from the client end to open the HTML page and set cookie is used for
getting the information. The university and the advertising servers exchanges the cookie
information for tracking the user visiting the website of the manufactured if the user clicks
the banner add to reach the advertising website.
Ans 2 :
The tcp message flow diagram is created for the management of the flow of
information between the client and the server and an initial sequence number and windows
frame is used for management of the sequence header. The following diagram is used for the
demonstration of the port, acknowledgment, value, and sequence number. The control fields
and the window size helps in analysing the response time and demonstration of the order of
connection.
5
NETWORKS AND COMMUNICATIONS
NETWORKS AND COMMUNICATIONS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORKS AND COMMUNICATIONS
Bibliography
Asadi, A., Wang, Q. and Mancuso, V., 2014. A survey on device-to-device communication in
cellular networks. IEEE Communications Surveys & Tutorials, 16(4), pp.1801-1819.
Chen, P., Nikiforakis, N., Huygens, C. and Desmet, L., 2015. A Dangerous Mix: Large-scale
analysis of mixed-content websites. In Information Security (pp. 354-363). Springer, Cham.
Cunha, F., Villas, L., Boukerche, A., Maia, G., Viana, A., Mini, R.A. and Loureiro, A.A.,
2016. Data communication in VANETs: Protocols, applications and challenges. Ad Hoc
Networks, 44, pp.90-103.
Da Cunha, F.D., Boukerche, A., Villas, L., Viana, A.C. and Loureiro, A.A., 2014. Data
communication in VANETs: a survey, challenges and applications (Doctoral dissertation,
INRIA Saclay; INRIA).
Jussila, J., 2018. HTTP cookie weaknesses, attack methods and defense mechanisms: a
systematic literature review.
Liu, J., Kato, N., Ma, J. and Kadowaki, N., 2015. Device-to-device communication in LTE-
advanced networks: A survey. IEEE Communications Surveys & Tutorials, 17(4), pp.1923-
1940.
McMahan, H.B., Moore, E., Ramage, D. and Hampson, S., 2016. Communication-efficient
learning of deep networks from decentralized data. arXiv preprint arXiv:1602.05629.
Milgrom, J. and Gemmill, A.W., 2015. Introduction.
Rao, R.K., Ram, S., Kumar, M.A., Supritha, R. and Reza, S.A., 2017. Cross site scripting
attacks and preventive measures. International Research Journal of Engineering and
Technology, 4(2), pp.2016-2019.
NETWORKS AND COMMUNICATIONS
Bibliography
Asadi, A., Wang, Q. and Mancuso, V., 2014. A survey on device-to-device communication in
cellular networks. IEEE Communications Surveys & Tutorials, 16(4), pp.1801-1819.
Chen, P., Nikiforakis, N., Huygens, C. and Desmet, L., 2015. A Dangerous Mix: Large-scale
analysis of mixed-content websites. In Information Security (pp. 354-363). Springer, Cham.
Cunha, F., Villas, L., Boukerche, A., Maia, G., Viana, A., Mini, R.A. and Loureiro, A.A.,
2016. Data communication in VANETs: Protocols, applications and challenges. Ad Hoc
Networks, 44, pp.90-103.
Da Cunha, F.D., Boukerche, A., Villas, L., Viana, A.C. and Loureiro, A.A., 2014. Data
communication in VANETs: a survey, challenges and applications (Doctoral dissertation,
INRIA Saclay; INRIA).
Jussila, J., 2018. HTTP cookie weaknesses, attack methods and defense mechanisms: a
systematic literature review.
Liu, J., Kato, N., Ma, J. and Kadowaki, N., 2015. Device-to-device communication in LTE-
advanced networks: A survey. IEEE Communications Surveys & Tutorials, 17(4), pp.1923-
1940.
McMahan, H.B., Moore, E., Ramage, D. and Hampson, S., 2016. Communication-efficient
learning of deep networks from decentralized data. arXiv preprint arXiv:1602.05629.
Milgrom, J. and Gemmill, A.W., 2015. Introduction.
Rao, R.K., Ram, S., Kumar, M.A., Supritha, R. and Reza, S.A., 2017. Cross site scripting
attacks and preventive measures. International Research Journal of Engineering and
Technology, 4(2), pp.2016-2019.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
NETWORKS AND COMMUNICATIONS
Zheng, X., Jiang, J., Liang, J., Duan, H.X., Chen, S., Wan, T. and Weaver, N., 2015, August.
Cookies Lack Integrity: Real-World Implications. In USENIX Security Symposium (pp. 707-
721).
NETWORKS AND COMMUNICATIONS
Zheng, X., Jiang, J., Liang, J., Duan, H.X., Chen, S., Wan, T. and Weaver, N., 2015, August.
Cookies Lack Integrity: Real-World Implications. In USENIX Security Symposium (pp. 707-
721).
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





