ENGR8762: Computer Networks and Cybersecurity Assignment Solution
VerifiedAdded on 2023/06/04
|8
|1281
|94
Homework Assignment
AI Summary
This document presents a comprehensive solution to a computer networks and cybersecurity assignment, covering key concepts and protocols. The assignment addresses topics such as baud rate, bit rate, and Manchester encoding in physical layer transmission systems. It also explores HDLC protocols, error detection, and the functionality of bridges and switches. The solution further delves into TCP and UDP protocols, their applications, and comparisons. Additionally, the document provides detailed explanations of IP addressing, including network and broadcast addresses, along with an exploration of IPv6 addressing. Finally, the assignment covers forwarding decisions and routing protocols like distance-vector routing. References are also included at the end of the document. The assignment is intended to help students understand the underlying concepts of computer networks and cybersecurity.

Networking 1
Computer Networks and Cybersecurity
By (Name)
Name of the class (course)
Professor
Name of the school (university)
Date
Computer Networks and Cybersecurity
By (Name)
Name of the class (course)
Professor
Name of the school (university)
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Networking 2
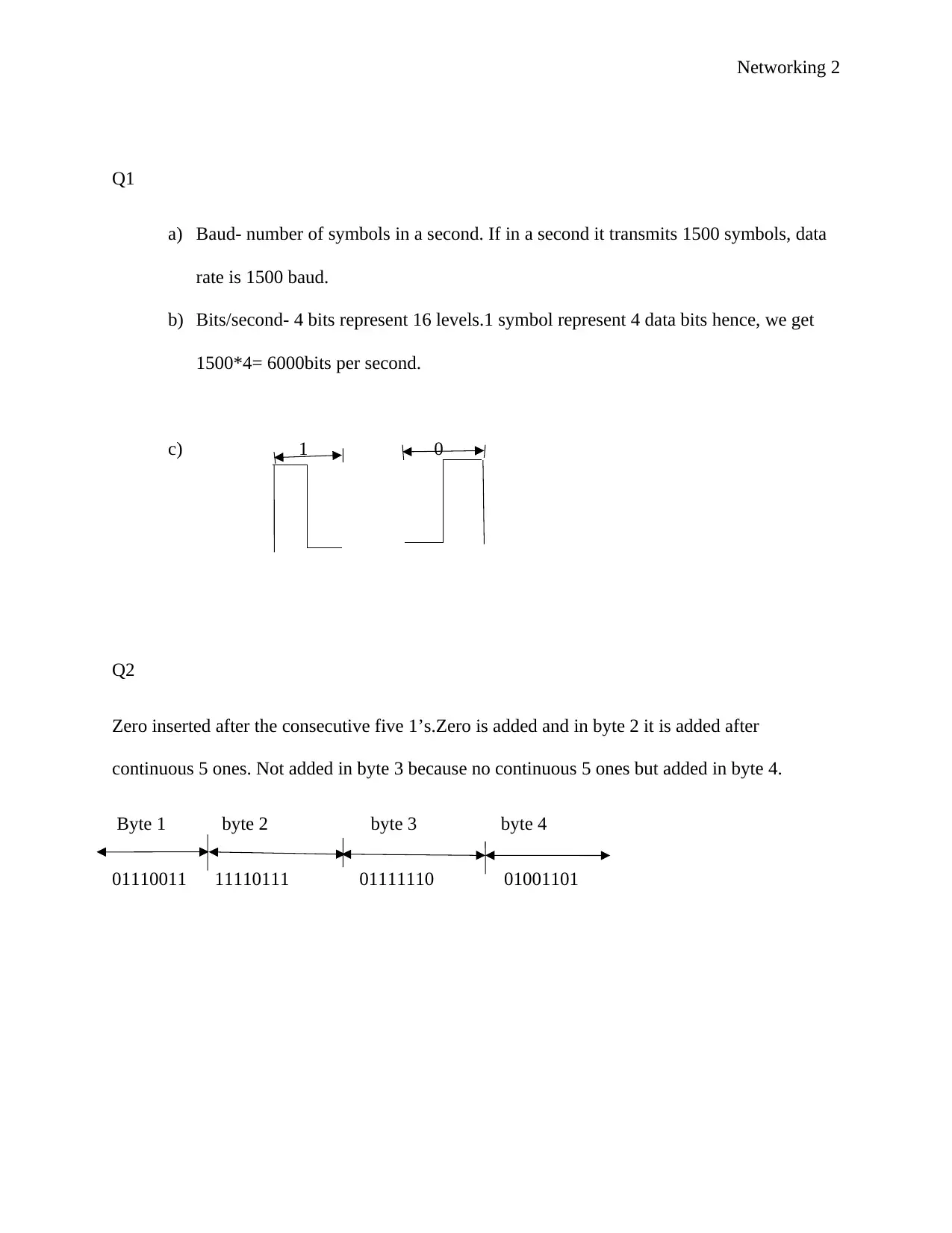
Q1
a) Baud- number of symbols in a second. If in a second it transmits 1500 symbols, data
rate is 1500 baud.
b) Bits/second- 4 bits represent 16 levels.1 symbol represent 4 data bits hence, we get
1500*4= 6000bits per second.
c) 1 0
Q2
Zero inserted after the consecutive five 1’s.Zero is added and in byte 2 it is added after
continuous 5 ones. Not added in byte 3 because no continuous 5 ones but added in byte 4.
Byte 1 byte 2 byte 3 byte 4
01110011 11110111 01111110 01001101
Q1
a) Baud- number of symbols in a second. If in a second it transmits 1500 symbols, data
rate is 1500 baud.
b) Bits/second- 4 bits represent 16 levels.1 symbol represent 4 data bits hence, we get
1500*4= 6000bits per second.
c) 1 0
Q2
Zero inserted after the consecutive five 1’s.Zero is added and in byte 2 it is added after
continuous 5 ones. Not added in byte 3 because no continuous 5 ones but added in byte 4.
Byte 1 byte 2 byte 3 byte 4
01110011 11110111 01111110 01001101

Networking 3
Q3
Reliability- This characteristic is measured by the rate at which failures occur and the time it
takes to recover from those failures. The performance of the network to the users should be great
without any problem (Marina, Das and Subramanian 2010).
Delay- applications can persevere delay at different magnitude. Delayed data is of no use
hence for good performance systems should deliver data in a timely manner (Marina, Das and
Subramanian 2010).
Jitter- It is the variation in delay of packets in the same flow. This can be caused by
congestion in the network or improper queuing of packets. The variation of packets should
remain constant for better performance (Marina, Das and Subramanian 2010).
Bandwidth- Different files need different bandwidths. Some require a lot of speed to
refresh, unlike others.
Q 4
a) A bridge operates in physical and data link layer while switches operate in data link
layer. A bridge has only two ports that connects two LANs and controls the flow of
data between them while a switch contains many ports. It understands which machine
device is connected to its port by using its IP address (Stallings 2017).
b) Switches have many ports like hundreds, unlike bridges which has only sixteen ports.
Switches support full duplex communication while bridges support half duplex.
Q3
Reliability- This characteristic is measured by the rate at which failures occur and the time it
takes to recover from those failures. The performance of the network to the users should be great
without any problem (Marina, Das and Subramanian 2010).
Delay- applications can persevere delay at different magnitude. Delayed data is of no use
hence for good performance systems should deliver data in a timely manner (Marina, Das and
Subramanian 2010).
Jitter- It is the variation in delay of packets in the same flow. This can be caused by
congestion in the network or improper queuing of packets. The variation of packets should
remain constant for better performance (Marina, Das and Subramanian 2010).
Bandwidth- Different files need different bandwidths. Some require a lot of speed to
refresh, unlike others.
Q 4
a) A bridge operates in physical and data link layer while switches operate in data link
layer. A bridge has only two ports that connects two LANs and controls the flow of
data between them while a switch contains many ports. It understands which machine
device is connected to its port by using its IP address (Stallings 2017).
b) Switches have many ports like hundreds, unlike bridges which has only sixteen ports.
Switches support full duplex communication while bridges support half duplex.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Networking 4
Bridges are software based while switches are hardware-based which make filtering
decisions with the help of ASICs chip.
c) A router can use IP address, unlike a switch which uses MAC address. A router
reviews the destination IP address before forwarding a packet (Stallings 2017).
Q5
In single bit error, one bit of data is replaced either by 0 or 1 and vice versa
while in burst error more than two bits in data unit are changed.
The likelihood of single bit error to occur in serial transmission is very low
while that of burst error is high.
Single bit error happens in parallel transmission because all data bits are
transmitted using separate wire medium while burst error the bits need not be
consecutively changed (Yan, Şekercioğlu and Narayanan 2010).
a) If 0.1 ms is equivalent to 0.0001 of a second and are being transmitted at a
rate of 100mbps, within 0.1ms, transmission of 10,000 bits will occur and
burst will affect them.
b) The use of parity bits is appropriate if only single bit errors are being
expected.
Bridges are software based while switches are hardware-based which make filtering
decisions with the help of ASICs chip.
c) A router can use IP address, unlike a switch which uses MAC address. A router
reviews the destination IP address before forwarding a packet (Stallings 2017).
Q5
In single bit error, one bit of data is replaced either by 0 or 1 and vice versa
while in burst error more than two bits in data unit are changed.
The likelihood of single bit error to occur in serial transmission is very low
while that of burst error is high.
Single bit error happens in parallel transmission because all data bits are
transmitted using separate wire medium while burst error the bits need not be
consecutively changed (Yan, Şekercioğlu and Narayanan 2010).
a) If 0.1 ms is equivalent to 0.0001 of a second and are being transmitted at a
rate of 100mbps, within 0.1ms, transmission of 10,000 bits will occur and
burst will affect them.
b) The use of parity bits is appropriate if only single bit errors are being
expected.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking 5
Q6
a) TCP works above IP and offers a connection reliable oriented service where
data is transferred to destination with congestion control and control of flow
while UDP provides connectionless unreliable protocol which does not have
error detection, and control of flow provided by UDP. It is also a service
with great effort (Krutz and Vines 2010).
b)
i. File transfer- TCP, error detection and correction is required because
losing data cannot be allowed.
ii. Watching a real stream video- UDP, the delay may be critical and
there is not enough time to get retransmission of any errors.
iii. Web browsing-TCP, web pages should be uploaded without errors
hence error detection and correction are required.
iv. A voice over IP (VoIP) telephone conversation- UDP, the timing of
telephone conversation requirements for data transfer is strict and if
we seek the retransmission of errors, it may lead to delay
(Halsall,1996).
c) They both provide services to many higher layer protocols which can be
combined into one layer of TCP or UDP. They use port numbers which are
16 bit in size. The port numbers then pinpoint a particular higher level
Q6
a) TCP works above IP and offers a connection reliable oriented service where
data is transferred to destination with congestion control and control of flow
while UDP provides connectionless unreliable protocol which does not have
error detection, and control of flow provided by UDP. It is also a service
with great effort (Krutz and Vines 2010).
b)
i. File transfer- TCP, error detection and correction is required because
losing data cannot be allowed.
ii. Watching a real stream video- UDP, the delay may be critical and
there is not enough time to get retransmission of any errors.
iii. Web browsing-TCP, web pages should be uploaded without errors
hence error detection and correction are required.
iv. A voice over IP (VoIP) telephone conversation- UDP, the timing of
telephone conversation requirements for data transfer is strict and if
we seek the retransmission of errors, it may lead to delay
(Halsall,1996).
c) They both provide services to many higher layer protocols which can be
combined into one layer of TCP or UDP. They use port numbers which are
16 bit in size. The port numbers then pinpoint a particular higher level

Networking 6
protocol for the destination of a certain data stream (Marina, Das and
Subramanian 2010).
Q7
a) Network address- Since network mask is 255.255.255.224, the address
of network is 192.168.3.192
b) Broadcast address- is shown by putting as 1s all the bits belonging to
the host portion and therefore it is 192.168.3.223
c) Hosts- formula 2n-2
Hence 25-2=30 (Taneja and Kush 2010)
Q8
A double colon can replace any single string of one or more hextets
consisting of all 0s. Leading zeros can be omitted.
a) 2001:EB8:0:1470::200
b) F380::123:4568:89AB:CDAF
Q9
a) Forwarding decisions need to be done fast where routers are supposed to make
decisions to use the current information. In this stage, other routers are not
notified about the forwarding decisions by the current router. Packets then
protocol for the destination of a certain data stream (Marina, Das and
Subramanian 2010).
Q7
a) Network address- Since network mask is 255.255.255.224, the address
of network is 192.168.3.192
b) Broadcast address- is shown by putting as 1s all the bits belonging to
the host portion and therefore it is 192.168.3.223
c) Hosts- formula 2n-2
Hence 25-2=30 (Taneja and Kush 2010)
Q8
A double colon can replace any single string of one or more hextets
consisting of all 0s. Leading zeros can be omitted.
a) 2001:EB8:0:1470::200
b) F380::123:4568:89AB:CDAF
Q9
a) Forwarding decisions need to be done fast where routers are supposed to make
decisions to use the current information. In this stage, other routers are not
notified about the forwarding decisions by the current router. Packets then
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Networking 7
leave the current router and may be passed on to another router or delivered to
their destination (Singh, Singh and Singh 2010).
b) This protocols work via routers giving information of links which are directly
connected and they forward routing tables to neighboring routers. They repeat
the process after receiving the information after calculating their own routing
tables. The whole routing table information is send whether updated or not
(Singh, Singh and Singh 2010).
leave the current router and may be passed on to another router or delivered to
their destination (Singh, Singh and Singh 2010).
b) This protocols work via routers giving information of links which are directly
connected and they forward routing tables to neighboring routers. They repeat
the process after receiving the information after calculating their own routing
tables. The whole routing table information is send whether updated or not
(Singh, Singh and Singh 2010).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking 8
References
Halsall, F., 1996. Data communications, computer networks and open systems (Vol. 347).
Harlow: Addison-Wesley.
Krutz, R.L. and Vines, R.D., 2010. Cloud security: A comprehensive guide to secure cloud
computing. New jersey:Wiley Publishing.
Marina, M.K., Das, S.R. and Subramanian, A.P., 2010. A topology control approach for utilizing
multiple channels in multi-radio wireless mesh networks. Computer networks, 54(2), pp.241-
256.
Singh, S.K., Singh, M.P. and Singh, D.K., 2010. Routing protocols in wireless sensor networks–
A survey. International Journal of Computer Science & Engineering Survey (IJCSES), 1(2),
pp.63-83.
Stallings, W., 2017. Cryptography and network security: principles and practice (p. 743). Upper
Saddle River, NJ: Pearson.
Taneja, S. and Kush, A., 2010. A survey of routing protocols in mobile ad hoc
networks. International Journal of innovation, Management and technology, 1(3), p.279.
Yan, X., Şekercioğlu, Y.A. and Narayanan, S., 2010. A survey of vertical handover decision
algorithms in Fourth Generation heterogeneous wireless networks. Computer networks, 54(11),
pp.1848-1863.
References
Halsall, F., 1996. Data communications, computer networks and open systems (Vol. 347).
Harlow: Addison-Wesley.
Krutz, R.L. and Vines, R.D., 2010. Cloud security: A comprehensive guide to secure cloud
computing. New jersey:Wiley Publishing.
Marina, M.K., Das, S.R. and Subramanian, A.P., 2010. A topology control approach for utilizing
multiple channels in multi-radio wireless mesh networks. Computer networks, 54(2), pp.241-
256.
Singh, S.K., Singh, M.P. and Singh, D.K., 2010. Routing protocols in wireless sensor networks–
A survey. International Journal of Computer Science & Engineering Survey (IJCSES), 1(2),
pp.63-83.
Stallings, W., 2017. Cryptography and network security: principles and practice (p. 743). Upper
Saddle River, NJ: Pearson.
Taneja, S. and Kush, A., 2010. A survey of routing protocols in mobile ad hoc
networks. International Journal of innovation, Management and technology, 1(3), p.279.
Yan, X., Şekercioğlu, Y.A. and Narayanan, S., 2010. A survey of vertical handover decision
algorithms in Fourth Generation heterogeneous wireless networks. Computer networks, 54(11),
pp.1848-1863.
1 out of 8
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

