Computer Networks Assignment - Deakin University, Semester 1
VerifiedAdded on 2021/04/22
|9
|1879
|87
Homework Assignment
AI Summary
This assignment solution delves into the intricacies of computer networks, focusing on the mechanisms of cookies and TCP connections. The document begins by explaining the cookie mechanism, illustrating its role in e-commerce and web user behavior through detailed diagrams. It outlines the process of cookie creation, storage, and retrieval, highlighting the differences between session and persistent cookies. The assignment further analyzes a scenario where an advertising company uses cookies on the Deakin University website, explaining the steps involved in tracking user behavior. Additionally, the solution presents a diagram demonstrating the flow of messages between a client and server using TCP connections, detailing TCP segments and header information. A comprehensive bibliography of relevant research papers supports the analysis.

Running head: COMPUTER NETWORKS
Computer Networks
Name of the Student
Name of the University
Author Note
Computer Networks
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1
COMPUTER NETWORKS
Ans 1 (A) :
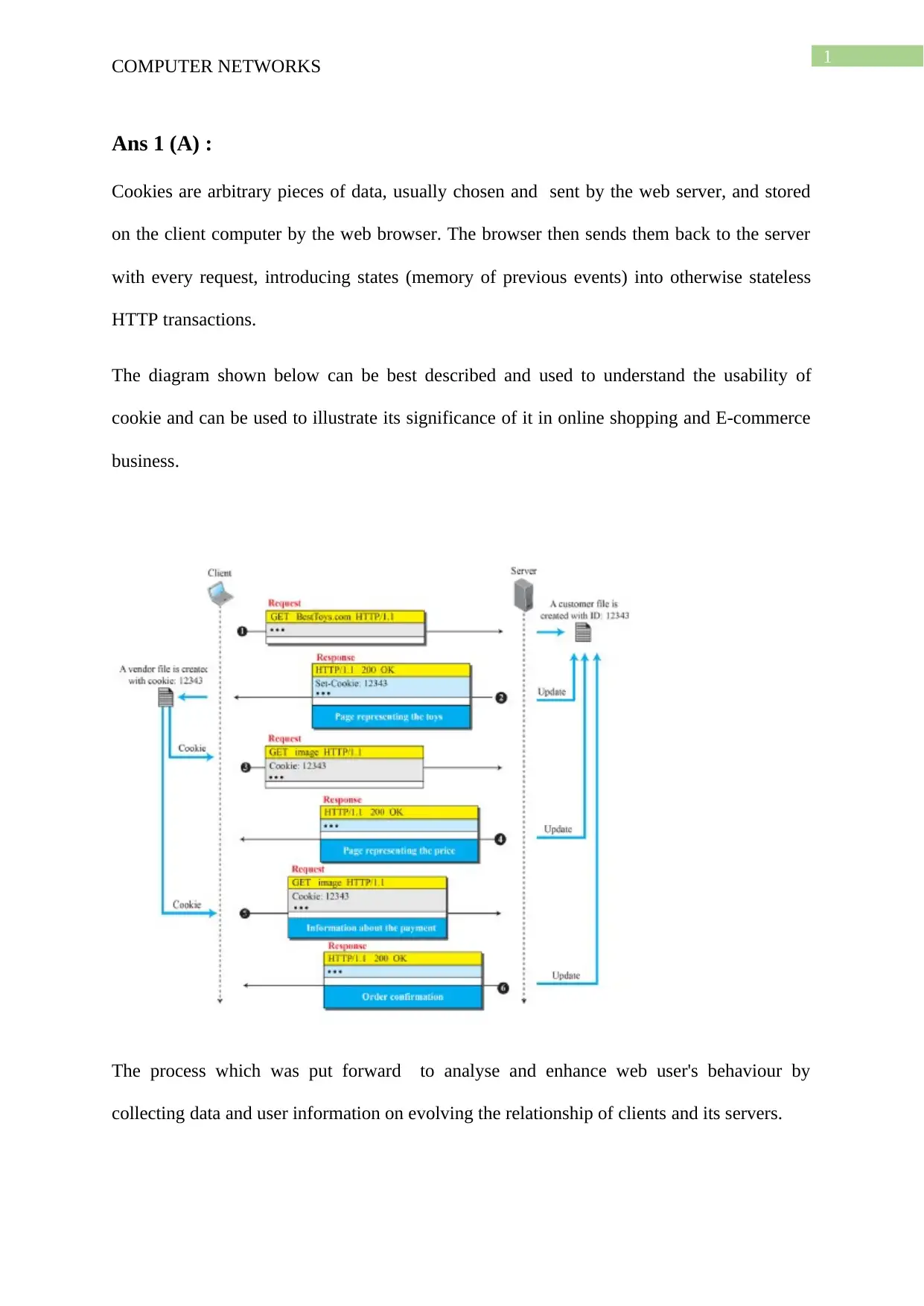
Cookies are arbitrary pieces of data, usually chosen and sent by the web server, and stored
on the client computer by the web browser. The browser then sends them back to the server
with every request, introducing states (memory of previous events) into otherwise stateless
HTTP transactions.
The diagram shown below can be best described and used to understand the usability of
cookie and can be used to illustrate its significance of it in online shopping and E-commerce
business.
The process which was put forward to analyse and enhance web user's behaviour by
collecting data and user information on evolving the relationship of clients and its servers.
COMPUTER NETWORKS
Ans 1 (A) :
Cookies are arbitrary pieces of data, usually chosen and sent by the web server, and stored
on the client computer by the web browser. The browser then sends them back to the server
with every request, introducing states (memory of previous events) into otherwise stateless
HTTP transactions.
The diagram shown below can be best described and used to understand the usability of
cookie and can be used to illustrate its significance of it in online shopping and E-commerce
business.
The process which was put forward to analyse and enhance web user's behaviour by
collecting data and user information on evolving the relationship of clients and its servers.

2
COMPUTER NETWORKS
The files that are created as cookie file is one on the side of the client and other on the side of
the user which store data respectively. A cookie with ID 12343 is created on the client side
in the vendor file and another file gets created on the server side with the exact cookie ID i.e
12343 which is used to store data on either side for their respective uses.
The client side deals with the request made while the server side with responses generated .
The data on the client side gets automatically gets stored in its vendor file and the customer
file when a response and a request is made respectively. Now, because of the request made by
the client, the server is obliged to respond which result in update of the server generated by
the user through its file which then updates its own ID. Now the last response that is made
using this mechanism is the detail of the order's confirmation received for that particular
order.
The above stated mechanism is very successfully used in dealing with placing orders in an E-
commerce. The desired page that is to be used by the user for shopping is requested through
the browser to the server for viewing and using of the E-commerce page from where the user
wants to shop from the web server then give its response which then initiates cookies to be
set using set-cookies, which is used to direct the browser to store the cookie and its data ,
which can also be used in the by the server if the client request through the browser of same
history without removal of any cookie . The client then makes another request through the
cookie to the browser to open the site that has the required item in there catalogue to shop
from the online website. The user, then makes another request to the server to fetch the
required details needed from the server.
Then the website through the browser returns the request of the user by providing pages
with the details of the items needed.
COMPUTER NETWORKS
The files that are created as cookie file is one on the side of the client and other on the side of
the user which store data respectively. A cookie with ID 12343 is created on the client side
in the vendor file and another file gets created on the server side with the exact cookie ID i.e
12343 which is used to store data on either side for their respective uses.
The client side deals with the request made while the server side with responses generated .
The data on the client side gets automatically gets stored in its vendor file and the customer
file when a response and a request is made respectively. Now, because of the request made by
the client, the server is obliged to respond which result in update of the server generated by
the user through its file which then updates its own ID. Now the last response that is made
using this mechanism is the detail of the order's confirmation received for that particular
order.
The above stated mechanism is very successfully used in dealing with placing orders in an E-
commerce. The desired page that is to be used by the user for shopping is requested through
the browser to the server for viewing and using of the E-commerce page from where the user
wants to shop from the web server then give its response which then initiates cookies to be
set using set-cookies, which is used to direct the browser to store the cookie and its data ,
which can also be used in the by the server if the client request through the browser of same
history without removal of any cookie . The client then makes another request through the
cookie to the browser to open the site that has the required item in there catalogue to shop
from the online website. The user, then makes another request to the server to fetch the
required details needed from the server.
Then the website through the browser returns the request of the user by providing pages
with the details of the items needed.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
COMPUTER NETWORKS
The given page will often contain all the details and the responses by the server along with
the content of the websites with their descriptive details as needed by the user. Two cookies
are generated along with the later process. Among the two cookie, the name of the first
cookie is the session cookie which is deleted as soon as the page is aborted because there is
no constraint of time and date with the session cookie. The session cookie can be made to last
for more than a session and even for a large duration of time if the previous session of the
cookie is being restored and can be used accordingly. The session token which is the second
type of cookie and also more persistent cookie as it contain a maximum age attribute which
help the website with the help of the browser to eliminate it at a notified time unlike the
previous type of cookie which does not need any instruction for any time bound operation.
The successful execution of the desired step result in the browser again sending request to
the server for the webpage. The request sent to the browser has a previous cookie that was
used with HTTP Header, which is easily recognised by the server as a previous request. The
server responds according to the request by the browser which was given through the
concerned user and send cookie to the page as instructed which includes cookie header also
which will help in proceeding further to the item the user wants to purchase.
After this, the browser request the servers to get the requested image of items available or
which the user wants to purchase. The user can anytime modify the Set-cookie by adding
another similar cookie which is set in nature, while the browser does also change the value of
old cookies with the value with that of a new one.
The last stage of online shopping which perhaps is the crucial stage as it deals with the
financial aspect of user is proceeded when the user request the server for payment. A final
cookie is automatically generated which knows that the server is proceeding to know about
the details of the amount required to facilitate the online transaction of the item. This is
COMPUTER NETWORKS
The given page will often contain all the details and the responses by the server along with
the content of the websites with their descriptive details as needed by the user. Two cookies
are generated along with the later process. Among the two cookie, the name of the first
cookie is the session cookie which is deleted as soon as the page is aborted because there is
no constraint of time and date with the session cookie. The session cookie can be made to last
for more than a session and even for a large duration of time if the previous session of the
cookie is being restored and can be used accordingly. The session token which is the second
type of cookie and also more persistent cookie as it contain a maximum age attribute which
help the website with the help of the browser to eliminate it at a notified time unlike the
previous type of cookie which does not need any instruction for any time bound operation.
The successful execution of the desired step result in the browser again sending request to
the server for the webpage. The request sent to the browser has a previous cookie that was
used with HTTP Header, which is easily recognised by the server as a previous request. The
server responds according to the request by the browser which was given through the
concerned user and send cookie to the page as instructed which includes cookie header also
which will help in proceeding further to the item the user wants to purchase.
After this, the browser request the servers to get the requested image of items available or
which the user wants to purchase. The user can anytime modify the Set-cookie by adding
another similar cookie which is set in nature, while the browser does also change the value of
old cookies with the value with that of a new one.
The last stage of online shopping which perhaps is the crucial stage as it deals with the
financial aspect of user is proceeded when the user request the server for payment. A final
cookie is automatically generated which knows that the server is proceeding to know about
the details of the amount required to facilitate the online transaction of the item. This is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
COMPUTER NETWORKS
proceeded by setting the cookie and response accordingly to again facilitate the transaction.
The final response is the amount needed by the server of the webpage to finish the transaction
procedure for the purchase of the item through the chosen website of the E-commerce.
The above statements can give us a detailed step by step of the procedure that is depicted in
the diagram.
Ans 1 (B) :
For the condition when an advertising company pays fees to the Deakin university for
showing banner ads in the university website an image is used as a hyperlink when the user
clicks on the image the user is redirected to the advertising web page and it fetches request
from the university web server.
The above diagrams are analysed for explaining the four steps for the use of a cookie.
COMPUTER NETWORKS
proceeded by setting the cookie and response accordingly to again facilitate the transaction.
The final response is the amount needed by the server of the webpage to finish the transaction
procedure for the purchase of the item through the chosen website of the E-commerce.
The above statements can give us a detailed step by step of the procedure that is depicted in
the diagram.
Ans 1 (B) :
For the condition when an advertising company pays fees to the Deakin university for
showing banner ads in the university website an image is used as a hyperlink when the user
clicks on the image the user is redirected to the advertising web page and it fetches request
from the university web server.
The above diagrams are analysed for explaining the four steps for the use of a cookie.

5
COMPUTER NETWORKS
The cookie mechanism, allows the server to store information its own information about a
user in the user's own computer. This mechanism will be demonstrated with the help of the
following diagrams.
In cookie mechanism , two types of file gets generated, client and server side respectively. In
the client side, vendor file gets generated whereas in the server side a customer file is
generated.
The first diagram shows the user as client , Deakin university website and the advertising site
as the server side. The mechanism involved in the working of the cookie is at first user
requests by using the GET method to direct to a particular site which in this case is Deakin
University website. The server which is Deakin University serves the request by sending the
required HTML page. In the next step the client side requests the server(advertising site) to
get to the particular banner ad , with the cookie value "none". The server serves the request
by sending the required HTML page and sets the cookie value by the Set-Cookie method.
The Set-Cookie HTTP response Header enables the server to send cookies to the user agent.
In this case , cookie name:_uld and cookie value:abc1.
In the second diagram, the user is the client, the manufacturing and the advertising sites are
the servers. The mechanism involved in the working of the cookie is at first user requests by
using the GET method to direct to a particular site which in this case is the manufacturing
site. The server which is manufacturing serves the request by sending the required HTML
page.
In the next step the client side requests the server(advertising site) to get to the particular
HTML page , with the cookie value "abc1". The server serves the request by sending the
required HTML page.
COMPUTER NETWORKS
The cookie mechanism, allows the server to store information its own information about a
user in the user's own computer. This mechanism will be demonstrated with the help of the
following diagrams.
In cookie mechanism , two types of file gets generated, client and server side respectively. In
the client side, vendor file gets generated whereas in the server side a customer file is
generated.
The first diagram shows the user as client , Deakin university website and the advertising site
as the server side. The mechanism involved in the working of the cookie is at first user
requests by using the GET method to direct to a particular site which in this case is Deakin
University website. The server which is Deakin University serves the request by sending the
required HTML page. In the next step the client side requests the server(advertising site) to
get to the particular banner ad , with the cookie value "none". The server serves the request
by sending the required HTML page and sets the cookie value by the Set-Cookie method.
The Set-Cookie HTTP response Header enables the server to send cookies to the user agent.
In this case , cookie name:_uld and cookie value:abc1.
In the second diagram, the user is the client, the manufacturing and the advertising sites are
the servers. The mechanism involved in the working of the cookie is at first user requests by
using the GET method to direct to a particular site which in this case is the manufacturing
site. The server which is manufacturing serves the request by sending the required HTML
page.
In the next step the client side requests the server(advertising site) to get to the particular
HTML page , with the cookie value "abc1". The server serves the request by sending the
required HTML page.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
COMPUTER NETWORKS
Thus this is the procedure by which the cookie is used when retrieving a Deakin web page
containing an advertisement and then tracking the users of Deakin's website visiting the
manufacturing's website when the user clicks on an advertisement.
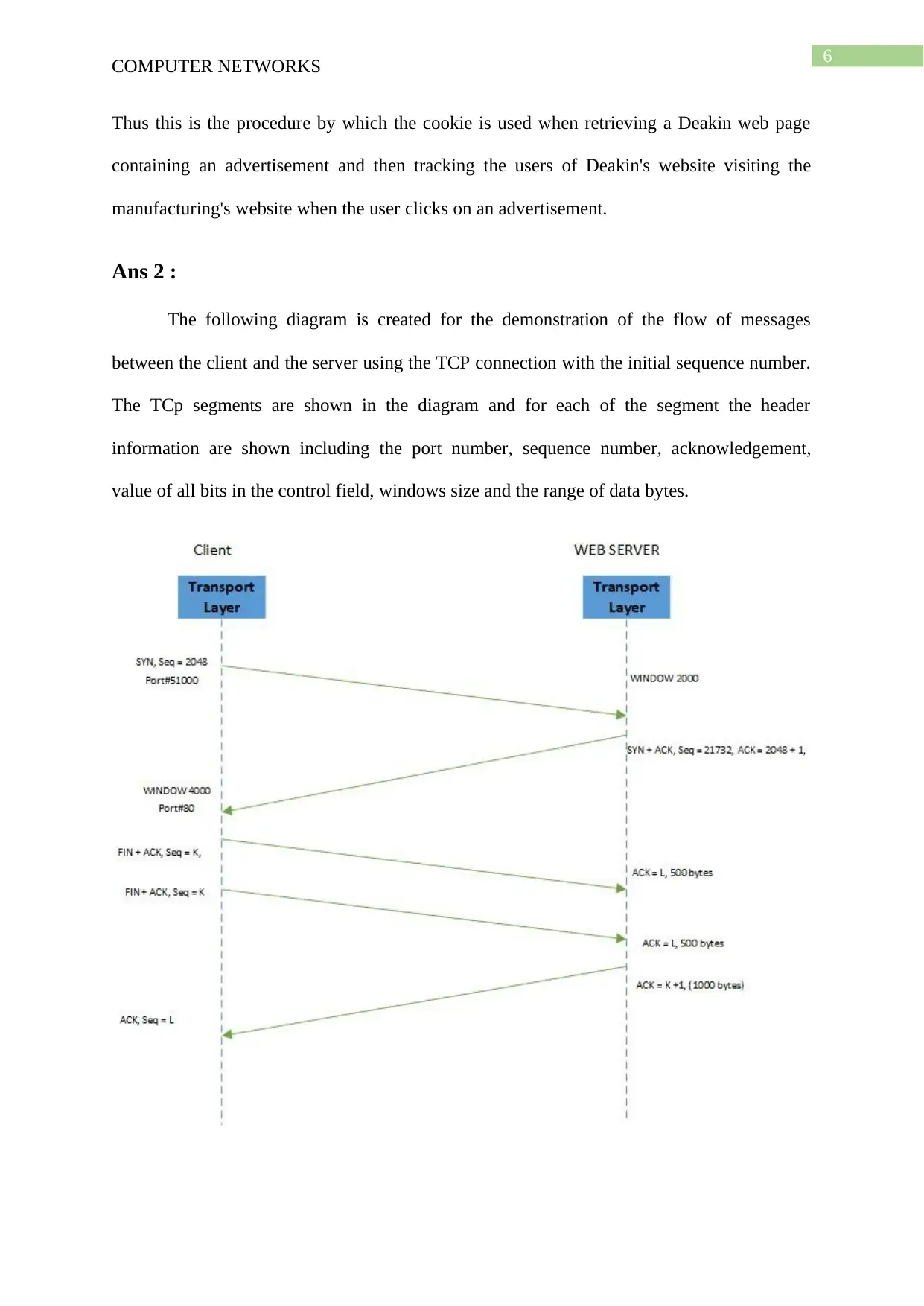
Ans 2 :
The following diagram is created for the demonstration of the flow of messages
between the client and the server using the TCP connection with the initial sequence number.
The TCp segments are shown in the diagram and for each of the segment the header
information are shown including the port number, sequence number, acknowledgement,
value of all bits in the control field, windows size and the range of data bytes.
COMPUTER NETWORKS
Thus this is the procedure by which the cookie is used when retrieving a Deakin web page
containing an advertisement and then tracking the users of Deakin's website visiting the
manufacturing's website when the user clicks on an advertisement.
Ans 2 :
The following diagram is created for the demonstration of the flow of messages
between the client and the server using the TCP connection with the initial sequence number.
The TCp segments are shown in the diagram and for each of the segment the header
information are shown including the port number, sequence number, acknowledgement,
value of all bits in the control field, windows size and the range of data bytes.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
COMPUTER NETWORKS
Bibliography
Asadi, A., Wang, Q. and Mancuso, V., 2014. A survey on device-to-device communication in
cellular networks. IEEE Communications Surveys & Tutorials, 16(4), pp.1801-1819.
Chen, P., Nikiforakis, N., Huygens, C. and Desmet, L., 2015. A Dangerous Mix: Large-scale
analysis of mixed-content websites. In Information Security (pp. 354-363). Springer, Cham.
Cunha, F., Villas, L., Boukerche, A., Maia, G., Viana, A., Mini, R.A. and Loureiro, A.A.,
2016. Data communication in VANETs: Protocols, applications and challenges. Ad Hoc
Networks, 44, pp.90-103.
Da Cunha, F.D., Boukerche, A., Villas, L., Viana, A.C. and Loureiro, A.A., 2014. Data
communication in VANETs: a survey, challenges and applications (Doctoral dissertation,
INRIA Saclay; INRIA).
Jussila, J., 2018. HTTP cookie weaknesses, attack methods and defense mechanisms: a
systematic literature review.
Liu, J., Kato, N., Ma, J. and Kadowaki, N., 2015. Device-to-device communication in LTE-
advanced networks: A survey. IEEE Communications Surveys & Tutorials, 17(4), pp.1923-
1940.
McMahan, H.B., Moore, E., Ramage, D. and Hampson, S., 2016. Communication-efficient
learning of deep networks from decentralized data. arXiv preprint arXiv:1602.05629.
Milgrom, J. and Gemmill, A.W., 2015. Introduction.
Rao, R.K., Ram, S., Kumar, M.A., Supritha, R. and Reza, S.A., 2017. Cross site scripting
attacks and preventive measures. International Research Journal of Engineering and
Technology, 4(2), pp.2016-2019.
COMPUTER NETWORKS
Bibliography
Asadi, A., Wang, Q. and Mancuso, V., 2014. A survey on device-to-device communication in
cellular networks. IEEE Communications Surveys & Tutorials, 16(4), pp.1801-1819.
Chen, P., Nikiforakis, N., Huygens, C. and Desmet, L., 2015. A Dangerous Mix: Large-scale
analysis of mixed-content websites. In Information Security (pp. 354-363). Springer, Cham.
Cunha, F., Villas, L., Boukerche, A., Maia, G., Viana, A., Mini, R.A. and Loureiro, A.A.,
2016. Data communication in VANETs: Protocols, applications and challenges. Ad Hoc
Networks, 44, pp.90-103.
Da Cunha, F.D., Boukerche, A., Villas, L., Viana, A.C. and Loureiro, A.A., 2014. Data
communication in VANETs: a survey, challenges and applications (Doctoral dissertation,
INRIA Saclay; INRIA).
Jussila, J., 2018. HTTP cookie weaknesses, attack methods and defense mechanisms: a
systematic literature review.
Liu, J., Kato, N., Ma, J. and Kadowaki, N., 2015. Device-to-device communication in LTE-
advanced networks: A survey. IEEE Communications Surveys & Tutorials, 17(4), pp.1923-
1940.
McMahan, H.B., Moore, E., Ramage, D. and Hampson, S., 2016. Communication-efficient
learning of deep networks from decentralized data. arXiv preprint arXiv:1602.05629.
Milgrom, J. and Gemmill, A.W., 2015. Introduction.
Rao, R.K., Ram, S., Kumar, M.A., Supritha, R. and Reza, S.A., 2017. Cross site scripting
attacks and preventive measures. International Research Journal of Engineering and
Technology, 4(2), pp.2016-2019.

8
COMPUTER NETWORKS
Zheng, X., Jiang, J., Liang, J., Duan, H.X., Chen, S., Wan, T. and Weaver, N., 2015, August.
Cookies Lack Integrity: Real-World Implications. In USENIX Security Symposium (pp. 707-
721).
COMPUTER NETWORKS
Zheng, X., Jiang, J., Liang, J., Duan, H.X., Chen, S., Wan, T. and Weaver, N., 2015, August.
Cookies Lack Integrity: Real-World Implications. In USENIX Security Symposium (pp. 707-
721).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





