Computer Networks: Internetworking with TCP/IP Assessment, Semester 1
VerifiedAdded on 2021/04/21
|11
|1947
|21
Homework Assignment
AI Summary
This document presents a comprehensive solution to an Internetworking with TCP/IP assignment. It begins with a comparison of the OSI and TCP/IP network models, highlighting their similarities and differences, including the layer-based architecture and functionalities. The solution then delves into practical exercises, including subnet mask calculations for IPv4 addresses and determining host address ranges and broadcast addresses. Furthermore, the assignment addresses the Address Resolution Protocol (ARP), explaining its purpose and function in mapping IP addresses to physical addresses. A significant portion of the document is dedicated to a case study involving the design of a network solution for a company with multiple branches. This includes network diagrams, addressing solutions, subnetting plans, and considerations for network security and scalability, such as the impact of increased hosts per building and recommendations for network configuration. The document also provides a bibliography of the references used in the assignment.

Running head: INTERNETWORKING WITH TCP/IP
Internetworking with TCP/IP
Assessment No
Assessment Title
Student Name & ID
Subject Name and Code
Student Email Address
Internetworking with TCP/IP
Assessment No
Assessment Title
Student Name & ID
Subject Name and Code
Student Email Address
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INTERNETWORKING WITH TCP/IP
Table of Contents
Answer to Question 1: Comparison of the OSI reference model with TCP/IP networking model.2
Answer to Question 2:.....................................................................................................................3
Hands on Project 2.3: Subnet mask calculation for the required IPV4 subnets..........................3
Hands on Project 2.5: Host address range, broadcast address caluclation..................................3
Answer to Question 3: Address Resolution Protocol and its Purpose.............................................4
Answer to Question 4: Case Study Task.........................................................................................5
Bibliography....................................................................................................................................9
INTERNETWORKING WITH TCP/IP
Table of Contents
Answer to Question 1: Comparison of the OSI reference model with TCP/IP networking model.2
Answer to Question 2:.....................................................................................................................3
Hands on Project 2.3: Subnet mask calculation for the required IPV4 subnets..........................3
Hands on Project 2.5: Host address range, broadcast address caluclation..................................3
Answer to Question 3: Address Resolution Protocol and its Purpose.............................................4
Answer to Question 4: Case Study Task.........................................................................................5
Bibliography....................................................................................................................................9

2
INTERNETWORKING WITH TCP/IP
Answer to Question 1: Comparison of the OSI reference model with TCP/IP
networking model
When the TCP/IP network model is compared with the OSI reference model it is found
that the TCP/IP is older and the OSI model have 7 layers while TCP/IP have 4 layers. The
application layer, transport layer and the network layer of the OSI model is similar with the
layers of the TCP/IP model. There are no session and presentation layer present in the TCP/IP
model while the transport layer of the TCP/IP model performs some of the operation of session
layer present in the OSI layer (Grasa et al., 2016). The network layer of the TCP/IP network
model performs the task of the physical and the data link layer of the OSI model. In the TCP/IP
the network layer does not possess the acknowledgement and the sequencing service but it is
present in the OSI model (data link layer). The responsibility of sequencing and
acknowledgement is managed by the transport layer of the TCP/IP model.
The OSI layer does not finds its application in the practical environment and it acts as a
conceptual model. The OSI model is used for understanding the functionality of the network and
describing and discussing the different components of the network. But the TCP/IP model is
designed for troubleshooting different network problems and it does not provide much
description as the OSI model (Bruschi et al., 2017). The TCP/IP model works on the standard
internet protocols while the OSi model is independent of protocol and thus it is more useful for
working with and describing the elements of the network.
INTERNETWORKING WITH TCP/IP
Answer to Question 1: Comparison of the OSI reference model with TCP/IP
networking model
When the TCP/IP network model is compared with the OSI reference model it is found
that the TCP/IP is older and the OSI model have 7 layers while TCP/IP have 4 layers. The
application layer, transport layer and the network layer of the OSI model is similar with the
layers of the TCP/IP model. There are no session and presentation layer present in the TCP/IP
model while the transport layer of the TCP/IP model performs some of the operation of session
layer present in the OSI layer (Grasa et al., 2016). The network layer of the TCP/IP network
model performs the task of the physical and the data link layer of the OSI model. In the TCP/IP
the network layer does not possess the acknowledgement and the sequencing service but it is
present in the OSI model (data link layer). The responsibility of sequencing and
acknowledgement is managed by the transport layer of the TCP/IP model.
The OSI layer does not finds its application in the practical environment and it acts as a
conceptual model. The OSI model is used for understanding the functionality of the network and
describing and discussing the different components of the network. But the TCP/IP model is
designed for troubleshooting different network problems and it does not provide much
description as the OSI model (Bruschi et al., 2017). The TCP/IP model works on the standard
internet protocols while the OSi model is independent of protocol and thus it is more useful for
working with and describing the elements of the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
INTERNETWORKING WITH TCP/IP
Answer to Question 2:
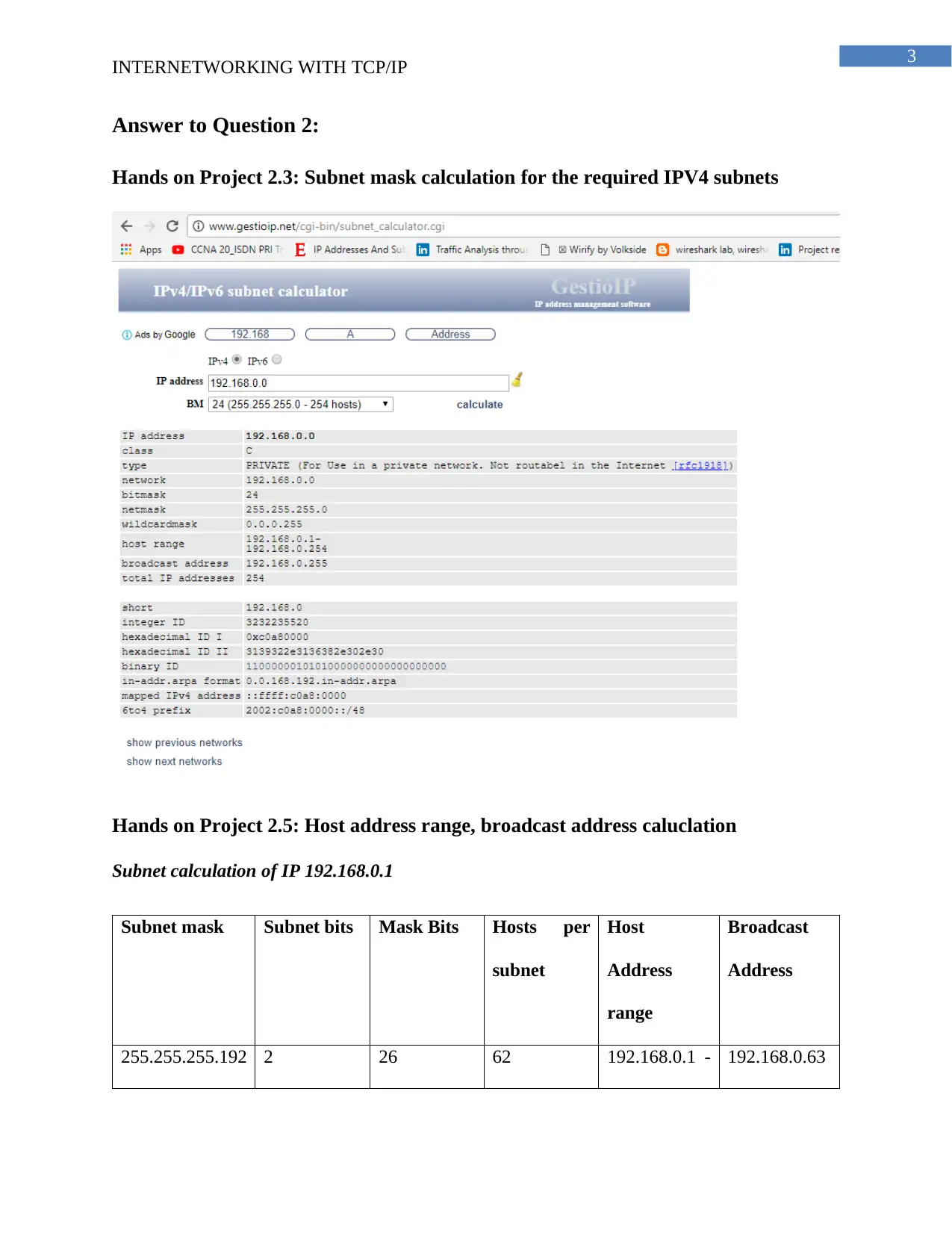
Hands on Project 2.3: Subnet mask calculation for the required IPV4 subnets
Hands on Project 2.5: Host address range, broadcast address caluclation
Subnet calculation of IP 192.168.0.1
Subnet mask Subnet bits Mask Bits Hosts per
subnet
Host
Address
range
Broadcast
Address
255.255.255.192 2 26 62 192.168.0.1 - 192.168.0.63
INTERNETWORKING WITH TCP/IP
Answer to Question 2:
Hands on Project 2.3: Subnet mask calculation for the required IPV4 subnets
Hands on Project 2.5: Host address range, broadcast address caluclation
Subnet calculation of IP 192.168.0.1
Subnet mask Subnet bits Mask Bits Hosts per
subnet
Host
Address
range
Broadcast
Address
255.255.255.192 2 26 62 192.168.0.1 - 192.168.0.63
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
INTERNETWORKING WITH TCP/IP
192.168.0.62
Subnet calculation of IP 10.0.0.1
Subnet bits Maximum
subnets
Mask Bits Hosts per
subnet
Host
Address
range
Broadcast
Address
8 256 16 65534 10.0.0.1 -
10.0.255.254
10.0.255.255
The experiment is continued with selection IP’s of different class and the change in the
mask bits are noted. The range also changes on changing the class of the IP address.
Answer to Question 3: Address Resolution Protocol and its Purpose
Address Resolution protocol (ARP) – It is used for creating a map between the physical
address and the IP address such that the host can be recognized in the network (Rao, Rai &
Narain, 2017). It maintains a table also known as ARP cache for maintaining a correlation
between the MAC (physical address) and the IP address of the hosts.
Purpose of ARP Cache
To maintain correlation between the Mac address and the IP address
Used for communicating with the hosts using the Arp protocol
For handling the traffic to a specific IP address (Ma et al., 2016)
To find the active hosts connected in the network.
INTERNETWORKING WITH TCP/IP
192.168.0.62
Subnet calculation of IP 10.0.0.1
Subnet bits Maximum
subnets
Mask Bits Hosts per
subnet
Host
Address
range
Broadcast
Address
8 256 16 65534 10.0.0.1 -
10.0.255.254
10.0.255.255
The experiment is continued with selection IP’s of different class and the change in the
mask bits are noted. The range also changes on changing the class of the IP address.
Answer to Question 3: Address Resolution Protocol and its Purpose
Address Resolution protocol (ARP) – It is used for creating a map between the physical
address and the IP address such that the host can be recognized in the network (Rao, Rai &
Narain, 2017). It maintains a table also known as ARP cache for maintaining a correlation
between the MAC (physical address) and the IP address of the hosts.
Purpose of ARP Cache
To maintain correlation between the Mac address and the IP address
Used for communicating with the hosts using the Arp protocol
For handling the traffic to a specific IP address (Ma et al., 2016)
To find the active hosts connected in the network.
5
INTERNETWORKING WITH TCP/IP
Answer to Question 4: Case Study Task
Introduction
The ForeShore IT solution have the requirement to connect all of its six branches for
expanding their operations. The network is designed using the private IP address of 10.0.0.0 and
for connecting each of the department a network subnet plan is created and the IP address is
divided into six subnets. The report is prepared including the design prepared for connecting all
the six department and an addressing solution is calculated for the configuration of the interface
of the device required for enabling communication between the departments located in different
areas of Adelaide. The network solution is designed for connecting 1200 workstations across all
the departments of the organization.
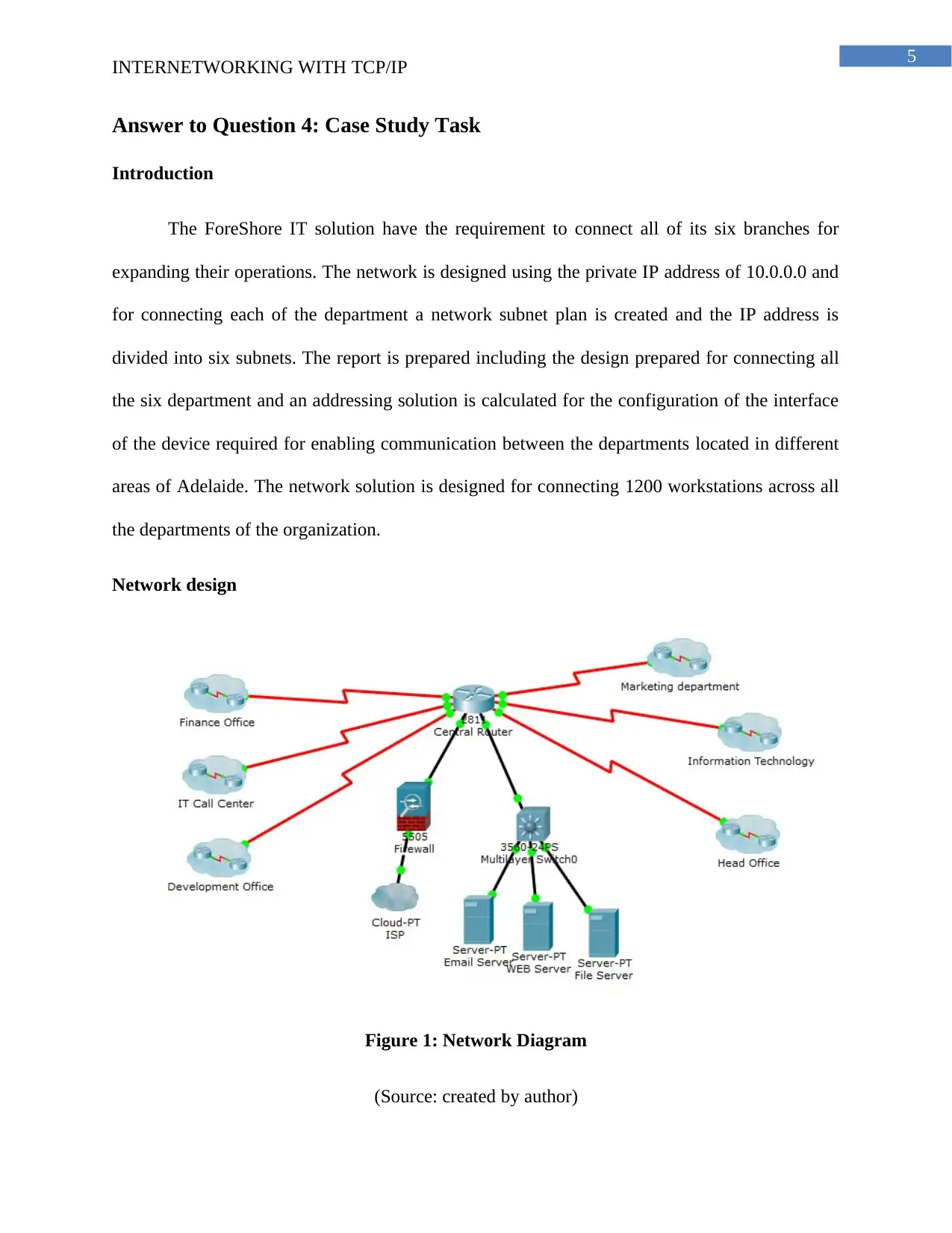
Network design
Figure 1: Network Diagram
(Source: created by author)
INTERNETWORKING WITH TCP/IP
Answer to Question 4: Case Study Task
Introduction
The ForeShore IT solution have the requirement to connect all of its six branches for
expanding their operations. The network is designed using the private IP address of 10.0.0.0 and
for connecting each of the department a network subnet plan is created and the IP address is
divided into six subnets. The report is prepared including the design prepared for connecting all
the six department and an addressing solution is calculated for the configuration of the interface
of the device required for enabling communication between the departments located in different
areas of Adelaide. The network solution is designed for connecting 1200 workstations across all
the departments of the organization.
Network design
Figure 1: Network Diagram
(Source: created by author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
INTERNETWORKING WITH TCP/IP
Justification
A prototype of the network solution for connecting all the six sites are created in cisco
packet tracer 7.1. Six different routers are used for connecting each of the department and the
router is needed to be configured according to the address plan. A central router is used for
connecting the branches and it is required to be configured with access control list protocol for
allowing or blocking the device connected in the network to access the sensitive organization
information stored in the servers. A firewall is used for blocking the unknown request coming
from different sources and increase the security of the network. The router for each of the
department is configured with a username and password for securing the network such that
unauthorized users cannot modify the configuration of the router. A switch is connected with the
router for connecting the hosts of the branch office and allow them to communicate with the
other hosts in the network.
Addressing solution
Network Address: 10.0.0.0/21
Number of IP address available for the network: 2046
Required number of IP address: 1130
Number of IP address available in the subnet: 2036
Subnet Name Neede
d Size
Allocate
d Size
Mas
k
Dec Mask Addre
ss
Assignabl
e Range
Broadcas
t
Head_Office 60 62 /26 255.255.25
5.192
10.0.7.
128
10.0.7.129
-
10.0.7.19
INTERNETWORKING WITH TCP/IP
Justification
A prototype of the network solution for connecting all the six sites are created in cisco
packet tracer 7.1. Six different routers are used for connecting each of the department and the
router is needed to be configured according to the address plan. A central router is used for
connecting the branches and it is required to be configured with access control list protocol for
allowing or blocking the device connected in the network to access the sensitive organization
information stored in the servers. A firewall is used for blocking the unknown request coming
from different sources and increase the security of the network. The router for each of the
department is configured with a username and password for securing the network such that
unauthorized users cannot modify the configuration of the router. A switch is connected with the
router for connecting the hosts of the branch office and allow them to communicate with the
other hosts in the network.
Addressing solution
Network Address: 10.0.0.0/21
Number of IP address available for the network: 2046
Required number of IP address: 1130
Number of IP address available in the subnet: 2036
Subnet Name Neede
d Size
Allocate
d Size
Mas
k
Dec Mask Addre
ss
Assignabl
e Range
Broadcas
t
Head_Office 60 62 /26 255.255.25
5.192
10.0.7.
128
10.0.7.129
-
10.0.7.19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
INTERNETWORKING WITH TCP/IP
10.0.7.190 1
Finance_office 260 510 /23 255.255.25
4.0
10.0.4.
0
10.0.4.1 -
10.0.5.254
10.0.5.25
5
IT_Call
Centre
520 1022 /22 255.255.25
2.0
10.0.0.
0
10.0.0.1 -
10.0.3.254
10.0.3.25
5
Research_and
_Development
_Office
120 126 /25 255.255.25
5.128
10.0.7.
0
10.0.7.1 -
10.0.7.126
10.0.7.12
7
Marketing_De
partment
40 62 /26 255.255.25
5.192
10.0.7.
192
10.0.7.193
-
10.0.7.254
10.0.7.25
5
Information_T
echnology
130 254 /24 255.255.25
5.0
10.0.6.
0
10.0.6.1 -
10.0.6.254
10.0.6.25
5
The router interface needs to be configured following the address table and each of the
router have different subnet, thus a DHCP pool is created with the range of the IP address to
automatically assign the IP address to the hosts connected in the network. The steps for the
calculation of the subnet mask are shown in the above table and some extra number of IP address
are kept in reserve such that if there is a increase the host the network can accommodate the
hosts. The creation of the network subnet plan reduces the wastage of the IP address and
increases the security of the network. The pools created for the DHCP should follow a naming
scheme such that the errors in the network can be easily rectified and the efficiency of the
network can be increased.
INTERNETWORKING WITH TCP/IP
10.0.7.190 1
Finance_office 260 510 /23 255.255.25
4.0
10.0.4.
0
10.0.4.1 -
10.0.5.254
10.0.5.25
5
IT_Call
Centre
520 1022 /22 255.255.25
2.0
10.0.0.
0
10.0.0.1 -
10.0.3.254
10.0.3.25
5
Research_and
_Development
_Office
120 126 /25 255.255.25
5.128
10.0.7.
0
10.0.7.1 -
10.0.7.126
10.0.7.12
7
Marketing_De
partment
40 62 /26 255.255.25
5.192
10.0.7.
192
10.0.7.193
-
10.0.7.254
10.0.7.25
5
Information_T
echnology
130 254 /24 255.255.25
5.0
10.0.6.
0
10.0.6.1 -
10.0.6.254
10.0.6.25
5
The router interface needs to be configured following the address table and each of the
router have different subnet, thus a DHCP pool is created with the range of the IP address to
automatically assign the IP address to the hosts connected in the network. The steps for the
calculation of the subnet mask are shown in the above table and some extra number of IP address
are kept in reserve such that if there is a increase the host the network can accommodate the
hosts. The creation of the network subnet plan reduces the wastage of the IP address and
increases the security of the network. The pools created for the DHCP should follow a naming
scheme such that the errors in the network can be easily rectified and the efficiency of the
network can be increased.

8
INTERNETWORKING WITH TCP/IP
b. Explanation if the number of host per network jumps over 1024 per building
The current number of hosts if suddenly jumps to 1024 the routers could not
automatically assign IP address to some of the hosts in the network. For enabling the network to
communicate the network configuration of the needs to be reconfigured and a new subnet plan.
All the interface of the routers and the configuration should be done from the scratch and the
previous configuration should be deleted such that it does not conflict with the current network
configuration. The errors in the project is required to be eliminated and more switch should be
added with the router for connecting them with the current network of the organization. This is a
cost effective solution and there is no requirement of adding new hardware devices if the hosts
per building jumps to 1024. The traffic would also be increased in the network and the switch
should also be configured with VTP and VLAN for the management of the network.
Conclusion
The network solution designed for Foreshore IT solution is created after analysis of the
requirement of the organization. The current network framework is evaluated for the proposal of
the expansion and connect the branch offices with the central head office of the organization.
The business rules of the organization is needed to be documented for configuring the router
aligning the business rules of the organization. The increase in the host per building would
generate more traffic in the network and it should be managed with the creation of separate vlan
for the management of the network.
INTERNETWORKING WITH TCP/IP
b. Explanation if the number of host per network jumps over 1024 per building
The current number of hosts if suddenly jumps to 1024 the routers could not
automatically assign IP address to some of the hosts in the network. For enabling the network to
communicate the network configuration of the needs to be reconfigured and a new subnet plan.
All the interface of the routers and the configuration should be done from the scratch and the
previous configuration should be deleted such that it does not conflict with the current network
configuration. The errors in the project is required to be eliminated and more switch should be
added with the router for connecting them with the current network of the organization. This is a
cost effective solution and there is no requirement of adding new hardware devices if the hosts
per building jumps to 1024. The traffic would also be increased in the network and the switch
should also be configured with VTP and VLAN for the management of the network.
Conclusion
The network solution designed for Foreshore IT solution is created after analysis of the
requirement of the organization. The current network framework is evaluated for the proposal of
the expansion and connect the branch offices with the central head office of the organization.
The business rules of the organization is needed to be documented for configuring the router
aligning the business rules of the organization. The increase in the host per building would
generate more traffic in the network and it should be managed with the creation of separate vlan
for the management of the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
INTERNETWORKING WITH TCP/IP
Bibliography
Bruschi, D., Di Pasquale, A., Ghilardi, S., Lanzi, A., & Pagani, E. (2017, September). Formal
Verification of ARP (Address Resolution Protocol) Through SMT-Based Model
Checking-A Case Study. In International Conference on Integrated Formal Methods (pp.
391-406). Springer, Cham.
Comer, D. (2014). Fundamentals Of Computer Networking And Internetworking.
Edwards, J., & Bramante, R. (2015). Networking self-teaching guide: OSI, TCP/IP, LANs,
MANs, WANs, implementation, management, and maintenance. John Wiley & Sons.
Grasa, E., Bergesio, L., Tarzan, M., Trouva, E., Gaston, B., Salvestrini, F., ... & Colle, D. (2016).
Recursive InterNetwork Architecture, Investigating RINA as an Alternative to TCP/IP
(IRATI). In Building the Future Internet through FIRE (pp. 491-520).
Hua, Y. (2016, April). Cheetah: An efficient flat addressing scheme for fast query services in
cloud computing. In INFOCOM 2016-The 35th Annual IEEE International Conference
on Computer Communications, IEEE (pp. 1-9). IEEE.
IPv4/IPv6 subnet calculator and addressing planner. (2018). Gestioip.net. Retrieved 24 March
2018, from http://www.gestioip.net/cgi-bin/subnet_calculator.cgi
Kizza, J. M. (2017). Guide to computer network security. Springer.
Ma, C., Xie, Y., Chen, H., Deng, Y., & Yan, W. (2014, May). Simplified addressing scheme for
mixed radix FFT algorithms. In Acoustics, Speech and Signal Processing (ICASSP),
2014 IEEE International Conference on (pp. 8355-8359). IEEE.
INTERNETWORKING WITH TCP/IP
Bibliography
Bruschi, D., Di Pasquale, A., Ghilardi, S., Lanzi, A., & Pagani, E. (2017, September). Formal
Verification of ARP (Address Resolution Protocol) Through SMT-Based Model
Checking-A Case Study. In International Conference on Integrated Formal Methods (pp.
391-406). Springer, Cham.
Comer, D. (2014). Fundamentals Of Computer Networking And Internetworking.
Edwards, J., & Bramante, R. (2015). Networking self-teaching guide: OSI, TCP/IP, LANs,
MANs, WANs, implementation, management, and maintenance. John Wiley & Sons.
Grasa, E., Bergesio, L., Tarzan, M., Trouva, E., Gaston, B., Salvestrini, F., ... & Colle, D. (2016).
Recursive InterNetwork Architecture, Investigating RINA as an Alternative to TCP/IP
(IRATI). In Building the Future Internet through FIRE (pp. 491-520).
Hua, Y. (2016, April). Cheetah: An efficient flat addressing scheme for fast query services in
cloud computing. In INFOCOM 2016-The 35th Annual IEEE International Conference
on Computer Communications, IEEE (pp. 1-9). IEEE.
IPv4/IPv6 subnet calculator and addressing planner. (2018). Gestioip.net. Retrieved 24 March
2018, from http://www.gestioip.net/cgi-bin/subnet_calculator.cgi
Kizza, J. M. (2017). Guide to computer network security. Springer.
Ma, C., Xie, Y., Chen, H., Deng, Y., & Yan, W. (2014, May). Simplified addressing scheme for
mixed radix FFT algorithms. In Acoustics, Speech and Signal Processing (ICASSP),
2014 IEEE International Conference on (pp. 8355-8359). IEEE.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
INTERNETWORKING WITH TCP/IP
Ma, H., Ding, H., Yang, Y., Mi, Z., Yang, J. Y., & Xiong, Z. (2016). Bayes-based ARP attack
detection algorithm for cloud centers. Tsinghua Science and Technology, 21(1), 17-28.
Oppitz, M., & Tomsu, P. (2018). Networks for Sharing and Connecting. In Inventing the Cloud
Century (pp. 97-129). Springer, Cham.
Porter, C. (2018). Online IP Subnet Calculator. Subnet-calculator.com. Retrieved 24 March
2018, from http://www.subnet-calculator.com/
Rao, J. D. P., Rai, S., & Narain, B. (2017). A study of Network Attacks and Features of Secure
Protocols. Research Journal of Engineering and Technology, 8(1), 4.
INTERNETWORKING WITH TCP/IP
Ma, H., Ding, H., Yang, Y., Mi, Z., Yang, J. Y., & Xiong, Z. (2016). Bayes-based ARP attack
detection algorithm for cloud centers. Tsinghua Science and Technology, 21(1), 17-28.
Oppitz, M., & Tomsu, P. (2018). Networks for Sharing and Connecting. In Inventing the Cloud
Century (pp. 97-129). Springer, Cham.
Porter, C. (2018). Online IP Subnet Calculator. Subnet-calculator.com. Retrieved 24 March
2018, from http://www.subnet-calculator.com/
Rao, J. D. P., Rai, S., & Narain, B. (2017). A study of Network Attacks and Features of Secure
Protocols. Research Journal of Engineering and Technology, 8(1), 4.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


