A Comprehensive Overview of Computer Networks: Types, and Technologies
VerifiedAdded on 2022/02/07
|24
|8450
|118
Report
AI Summary
This report provides a comprehensive overview of computer networks, covering various types such as Personal Area Networks (PAN), Local Area Networks (LAN), Metropolitan Area Networks (MAN), Wide Area Networks (WAN), and Wireless Local Area Networks (WLAN). It defines computer networks and their importance in sharing data and information. The report delves into the advantages of computer networks, including shared internet connections, resource sharing, and increased storage capacity. It also addresses the limitations, such as security issues, virus spread, and the cost of implementation. Each network type is explained with its characteristics, uses, benefits, and drawbacks, providing a clear understanding of their functionalities and applications. The report utilizes diagrams to illustrate network structures and concludes with a summary of the key concepts, making it a valuable resource for students studying computer networks. This document is available on Desklib, a platform offering AI-based study tools for students.

Introduction
The network can be defined as the set of groups or organizations where different ideas and
information can be shared. In the context of computers, a computer network can be defined as
the set of groups of multiple computers connect to share data, files, hardware, application,
information, and many other purposes. For the communication or sharing of these data,
computers should be connected to a network. For the connection of the computer’s different
types of wire or wireless devices are used. To understand the network among the computers
we need to know networking principles. Those main principles help user to deliver their ideas
and experience about the computer network with others. Along with the principles, a network
must follow some network protocols. Therefore, Network protocols are the set of policies and
plans, which contains some formats and rules for making possible communication between
computers over a network. Similarly, Networking devices are also required, Networking devices
are those physical devices, which are required communication and interaction between
hardware on a computer network. These networking devices connect various networks using
different types of networking protocols. Similarly, the Network topology is the process of
arranging elements present in a communication network that can be depicted physically or
logically.
Fig no.1: computer network
Source: https://1.bp.blogspot.com/-FBc_Q-tj2oA/XoIBk69CkKI/AAAAAAAAAnk/5P7PVJHTc0MQSzhA-dQGNh9gXuROmk6pwCLcBGAsYHQ/w1200-h630-p-k-no-
nu/Pengertian-Komunikasi-Daring.jpg
1 | P a g e
RUBYN-NETWORKING
The network can be defined as the set of groups or organizations where different ideas and
information can be shared. In the context of computers, a computer network can be defined as
the set of groups of multiple computers connect to share data, files, hardware, application,
information, and many other purposes. For the communication or sharing of these data,
computers should be connected to a network. For the connection of the computer’s different
types of wire or wireless devices are used. To understand the network among the computers
we need to know networking principles. Those main principles help user to deliver their ideas
and experience about the computer network with others. Along with the principles, a network
must follow some network protocols. Therefore, Network protocols are the set of policies and
plans, which contains some formats and rules for making possible communication between
computers over a network. Similarly, Networking devices are also required, Networking devices
are those physical devices, which are required communication and interaction between
hardware on a computer network. These networking devices connect various networks using
different types of networking protocols. Similarly, the Network topology is the process of
arranging elements present in a communication network that can be depicted physically or
logically.
Fig no.1: computer network
Source: https://1.bp.blogspot.com/-FBc_Q-tj2oA/XoIBk69CkKI/AAAAAAAAAnk/5P7PVJHTc0MQSzhA-dQGNh9gXuROmk6pwCLcBGAsYHQ/w1200-h630-p-k-no-
nu/Pengertian-Komunikasi-Daring.jpg
1 | P a g e
RUBYN-NETWORKING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Advantage of a computer network:
It helps to share an internet connection. Using a home network or office, multiple devices
can be connected to access the internet without having to pay for an ISP for multiple
accounts.
Devices like network printers, scanners, webcams, and CD burners can be shared.
Files like audio, photos, videos, text can be shared.
Multiple online and popular games can be played with different people from different
places at the same time.
Storage capacity also can be increased.
Having the better advantage of computer networks there is some limitation of computer
networks.
Limitations of computer network
The major drawback of computer networks is security issues. If a computer is on a
network, computer hackers can get unauthorized access by using different tools.
The rapid spread of computer viruses. Viruses get spread on a network easily because of
the interconnection of the workstation. Viruses make our computer slow, can also delete
important files.
Network faults can cause loss of data.
Purchasing the network cabling and file servers can be expensive.
Managing a large network is complicated, requires training and a network manager
usually needs to be employed.
These are the advantages and disadvantages of computer networks. As we know there are
different types of computer networks. So, the different types of computer networks there use,
advantages, and disadvantages are now discussed below.
Types of computer networks are:
i. PAN (Personal Area Network)
ii. LAN (local area network)
iii. MAN (metropolitan area network)
iv. WAN (wide area network)
v. WLAN (wireless local area network)
2 | P a g e
RUBYN-NETWORKING
It helps to share an internet connection. Using a home network or office, multiple devices
can be connected to access the internet without having to pay for an ISP for multiple
accounts.
Devices like network printers, scanners, webcams, and CD burners can be shared.
Files like audio, photos, videos, text can be shared.
Multiple online and popular games can be played with different people from different
places at the same time.
Storage capacity also can be increased.
Having the better advantage of computer networks there is some limitation of computer
networks.
Limitations of computer network
The major drawback of computer networks is security issues. If a computer is on a
network, computer hackers can get unauthorized access by using different tools.
The rapid spread of computer viruses. Viruses get spread on a network easily because of
the interconnection of the workstation. Viruses make our computer slow, can also delete
important files.
Network faults can cause loss of data.
Purchasing the network cabling and file servers can be expensive.
Managing a large network is complicated, requires training and a network manager
usually needs to be employed.
These are the advantages and disadvantages of computer networks. As we know there are
different types of computer networks. So, the different types of computer networks there use,
advantages, and disadvantages are now discussed below.
Types of computer networks are:
i. PAN (Personal Area Network)
ii. LAN (local area network)
iii. MAN (metropolitan area network)
iv. WAN (wide area network)
v. WLAN (wireless local area network)
2 | P a g e
RUBYN-NETWORKING
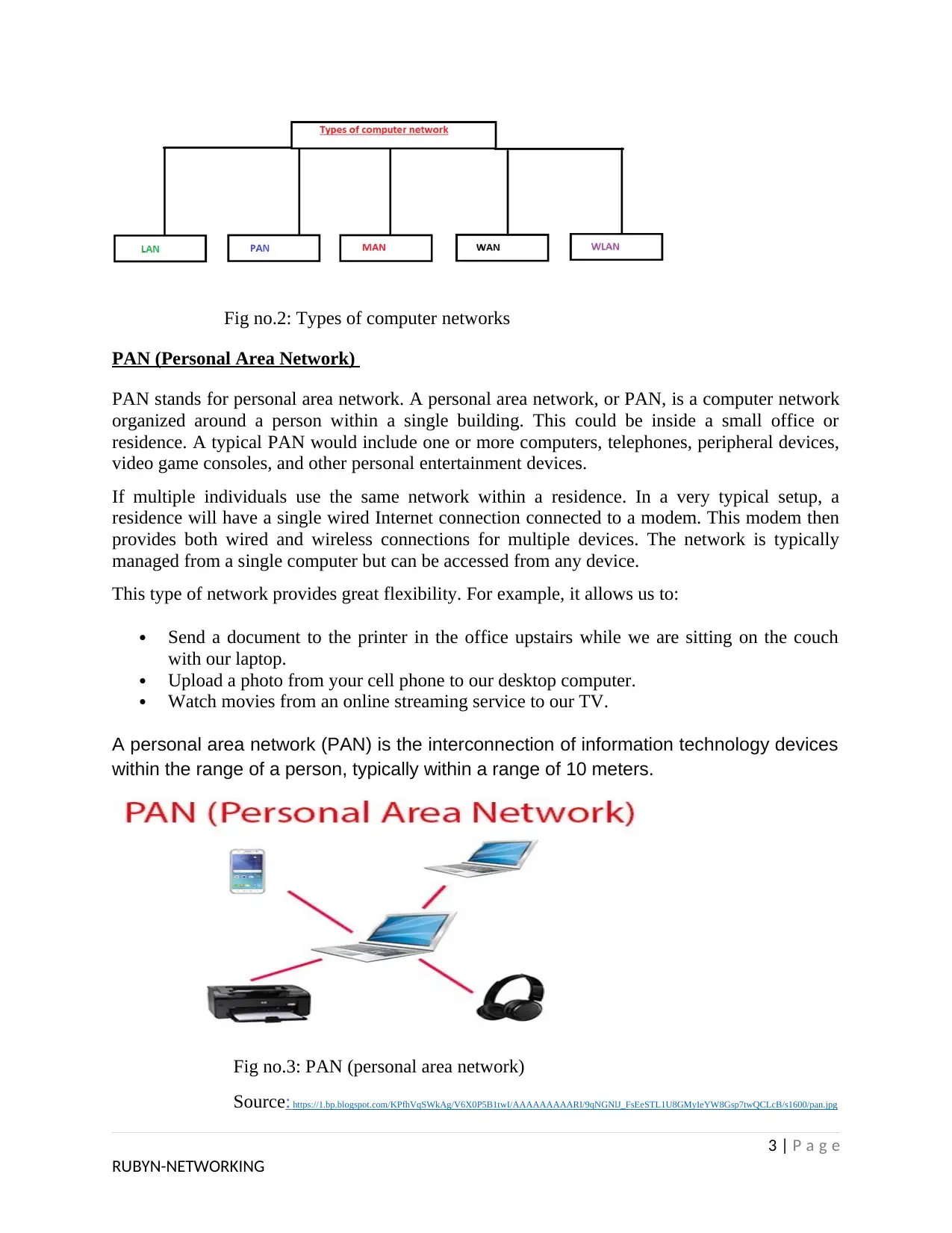
Fig no.2: Types of computer networks
PAN (Personal Area Network)
PAN stands for personal area network. A personal area network, or PAN, is a computer network
organized around a person within a single building. This could be inside a small office or
residence. A typical PAN would include one or more computers, telephones, peripheral devices,
video game consoles, and other personal entertainment devices.
If multiple individuals use the same network within a residence. In a very typical setup, a
residence will have a single wired Internet connection connected to a modem. This modem then
provides both wired and wireless connections for multiple devices. The network is typically
managed from a single computer but can be accessed from any device.
This type of network provides great flexibility. For example, it allows us to:
Send a document to the printer in the office upstairs while we are sitting on the couch
with our laptop.
Upload a photo from your cell phone to our desktop computer.
Watch movies from an online streaming service to our TV.
A personal area network (PAN) is the interconnection of information technology devices
within the range of a person, typically within a range of 10 meters.
Fig no.3: PAN (personal area network)
Source: https://1.bp.blogspot.com/KPfhVqSWkAg/V6X0P5B1twI/AAAAAAAAARI/9qNGNlJ_FsEeSTL1U8GMyIeYW8Gsp7twQCLcB/s1600/pan.jpg
3 | P a g e
RUBYN-NETWORKING
PAN (Personal Area Network)
PAN stands for personal area network. A personal area network, or PAN, is a computer network
organized around a person within a single building. This could be inside a small office or
residence. A typical PAN would include one or more computers, telephones, peripheral devices,
video game consoles, and other personal entertainment devices.
If multiple individuals use the same network within a residence. In a very typical setup, a
residence will have a single wired Internet connection connected to a modem. This modem then
provides both wired and wireless connections for multiple devices. The network is typically
managed from a single computer but can be accessed from any device.
This type of network provides great flexibility. For example, it allows us to:
Send a document to the printer in the office upstairs while we are sitting on the couch
with our laptop.
Upload a photo from your cell phone to our desktop computer.
Watch movies from an online streaming service to our TV.
A personal area network (PAN) is the interconnection of information technology devices
within the range of a person, typically within a range of 10 meters.
Fig no.3: PAN (personal area network)
Source: https://1.bp.blogspot.com/KPfhVqSWkAg/V6X0P5B1twI/AAAAAAAAARI/9qNGNlJ_FsEeSTL1U8GMyIeYW8Gsp7twQCLcB/s1600/pan.jpg
3 | P a g e
RUBYN-NETWORKING
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The main characteristics of PAN:
It is mostly personal devices network equipped within a limited area.
Allows you to handle the interconnection of IT devices in the surrounding of a single
user.
PAN includes mobile devices, tablets, and laptops.
It can be wirelessly connected to the internet called WPAN.
Appliances used for PAN: cordless mice, keyboards, and Bluetooth systems.
Benefits of PAN network:
PAN networks are relatively secure and safe
It offers only short-range solutions up to ten meters
Strictly restricted to a small area
The drawback of using PAN network:
It may establish a bad connection to other networks at the same radio bands.
Distance limits.
LAN (Local Area Network):
• A local area network is a network, which is used in local areas means it is a small
network that covers small areas like an office, school, college, building, etc. In this
network, we can connect computers, printers, servers, and other network devices.
Local area network is a privately owned network that means anyone can create this
network easily we just need some cables like Ethernet cables or central devices like
hub or switch. Local area networks are capable to transfer data at very fast rates so
data transfer speed over a LAN network can reach up to 1000 Mbps. Using Ethernet
cables, data transfer speed can reach up to 10 Mbps and by using FDDI or Gigabit
Ethernet, data transfer speed can reach up to 1 Gbps. The Range of LAN is 1000
meters.
Uses of Local Area Network:
LAN networks are mostly used in businesses where all business data is stored in servers.
This network can be used in factories.
This network can be used in Schools and Colleges where all the students, teachers, and
staff data are stored in servers.
This network can also be used in our homes where all the computers, mobiles, printers
are connected to the switch/router, and these devices can exchange data.
4 | P a g e
RUBYN-NETWORKING
It is mostly personal devices network equipped within a limited area.
Allows you to handle the interconnection of IT devices in the surrounding of a single
user.
PAN includes mobile devices, tablets, and laptops.
It can be wirelessly connected to the internet called WPAN.
Appliances used for PAN: cordless mice, keyboards, and Bluetooth systems.
Benefits of PAN network:
PAN networks are relatively secure and safe
It offers only short-range solutions up to ten meters
Strictly restricted to a small area
The drawback of using PAN network:
It may establish a bad connection to other networks at the same radio bands.
Distance limits.
LAN (Local Area Network):
• A local area network is a network, which is used in local areas means it is a small
network that covers small areas like an office, school, college, building, etc. In this
network, we can connect computers, printers, servers, and other network devices.
Local area network is a privately owned network that means anyone can create this
network easily we just need some cables like Ethernet cables or central devices like
hub or switch. Local area networks are capable to transfer data at very fast rates so
data transfer speed over a LAN network can reach up to 1000 Mbps. Using Ethernet
cables, data transfer speed can reach up to 10 Mbps and by using FDDI or Gigabit
Ethernet, data transfer speed can reach up to 1 Gbps. The Range of LAN is 1000
meters.
Uses of Local Area Network:
LAN networks are mostly used in businesses where all business data is stored in servers.
This network can be used in factories.
This network can be used in Schools and Colleges where all the students, teachers, and
staff data are stored in servers.
This network can also be used in our homes where all the computers, mobiles, printers
are connected to the switch/router, and these devices can exchange data.
4 | P a g e
RUBYN-NETWORKING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Now, here are the important characteristics of a LAN network:
It is a private network, so an outside regulatory body never controls it.
LAN operates at a relatively higher speed compared to other WAN systems.
There are various kinds of media access control methods like token ring and ethernet.
Benefits of LAN:
Computer resources like hard-disks, DVD-ROM, and printers can share local area
networks. This significantly reduces the cost of hardware purchases.
You can use the same software over the network instead of purchasing the licensed
software for each client in the network.
Data of all network users can be stored on a single hard disk of the server computer.
You can easily transfer data and messages over networked computers.
It will be easy to manage data in only one place, which makes data more secure.
Local Area Network offers the facility to share a single internet connection among all the
LAN users.
Drawbacks of LAN:
LAN will indeed save cost because of shared computer resources, but the initial cost of
installing Local Area Networks is quite high.
The LAN admin can check the personal data files of every LAN user, so it does not offer
good privacy.
Unauthorized users can access critical data of an organization in case LAN admin is not
able to secure a centralized data repository.
Local Area Network requires a constant LAN administration as there are issues related to
software setup and hardware failures.
Fig no.4: Local Area Network (LAN)
Sources: http://4.bp.blogspot.com/-xZM7NSPBaBM/T_sO-DTRiAI/AAAAAAAAAAc/WhqTfq2c_Bk/s1600/Local-Area-Network.jpg
MAN (Metropolitan area network)
5 | P a g e
RUBYN-NETWORKING
It is a private network, so an outside regulatory body never controls it.
LAN operates at a relatively higher speed compared to other WAN systems.
There are various kinds of media access control methods like token ring and ethernet.
Benefits of LAN:
Computer resources like hard-disks, DVD-ROM, and printers can share local area
networks. This significantly reduces the cost of hardware purchases.
You can use the same software over the network instead of purchasing the licensed
software for each client in the network.
Data of all network users can be stored on a single hard disk of the server computer.
You can easily transfer data and messages over networked computers.
It will be easy to manage data in only one place, which makes data more secure.
Local Area Network offers the facility to share a single internet connection among all the
LAN users.
Drawbacks of LAN:
LAN will indeed save cost because of shared computer resources, but the initial cost of
installing Local Area Networks is quite high.
The LAN admin can check the personal data files of every LAN user, so it does not offer
good privacy.
Unauthorized users can access critical data of an organization in case LAN admin is not
able to secure a centralized data repository.
Local Area Network requires a constant LAN administration as there are issues related to
software setup and hardware failures.
Fig no.4: Local Area Network (LAN)
Sources: http://4.bp.blogspot.com/-xZM7NSPBaBM/T_sO-DTRiAI/AAAAAAAAAAc/WhqTfq2c_Bk/s1600/Local-Area-Network.jpg
MAN (Metropolitan area network)
5 | P a g e
RUBYN-NETWORKING

MAN stands for metropolitan area network. It is a large computer network that usually spans a
vast geographical area and is used in large companies and university campuses. For example,
MAN is used to link the various buildings such as academic colleges or departments, libraries,
student residence halls, etc. located within a university campus. A Metropolitan Area Network
(MAN) is a large computer network on a large geographical area that includes several buildings
or even the entire city (metropolis). The geographical area of the MAN is larger than LAN but
smaller than WAN. MAN includes many communication devices and provides Internet
connectivity for the LANs in the metropolitan area.
MAN is used to combine into a networking group located in different buildings into a single
network. The diameter of such a network can range from 5 to 50 kilometers. MANs rarely extend
beyond 100 KM and frequently comprise a combination of different hardware and transmission
media.
Now, here are important characteristics of the MAN network:
It mostly covers towns and cities in a maximum 50 km range
Mostly used medium is optical fibers, cables
Data rates adequate for distributed computing applications.
Benefits of MAN network:
It offers fast communication using high-speed carriers,
like fiber optic cable.
It provides excellent support for an extensive size network and
greater access to WANs.
The dual bus in the MAN network provides support to transmit
data in both directions concurrently.
A MAN network mostly includes some areas of a city or an
entire city.
Drawbacks using the MAN network:
You need more cable to establish a MAN connection from one
place to another.
In MAN network it is tough to make the system secure from
hackers.
6 | P a g e
RUBYN-NETWORKING
vast geographical area and is used in large companies and university campuses. For example,
MAN is used to link the various buildings such as academic colleges or departments, libraries,
student residence halls, etc. located within a university campus. A Metropolitan Area Network
(MAN) is a large computer network on a large geographical area that includes several buildings
or even the entire city (metropolis). The geographical area of the MAN is larger than LAN but
smaller than WAN. MAN includes many communication devices and provides Internet
connectivity for the LANs in the metropolitan area.
MAN is used to combine into a networking group located in different buildings into a single
network. The diameter of such a network can range from 5 to 50 kilometers. MANs rarely extend
beyond 100 KM and frequently comprise a combination of different hardware and transmission
media.
Now, here are important characteristics of the MAN network:
It mostly covers towns and cities in a maximum 50 km range
Mostly used medium is optical fibers, cables
Data rates adequate for distributed computing applications.
Benefits of MAN network:
It offers fast communication using high-speed carriers,
like fiber optic cable.
It provides excellent support for an extensive size network and
greater access to WANs.
The dual bus in the MAN network provides support to transmit
data in both directions concurrently.
A MAN network mostly includes some areas of a city or an
entire city.
Drawbacks using the MAN network:
You need more cable to establish a MAN connection from one
place to another.
In MAN network it is tough to make the system secure from
hackers.
6 | P a g e
RUBYN-NETWORKING
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
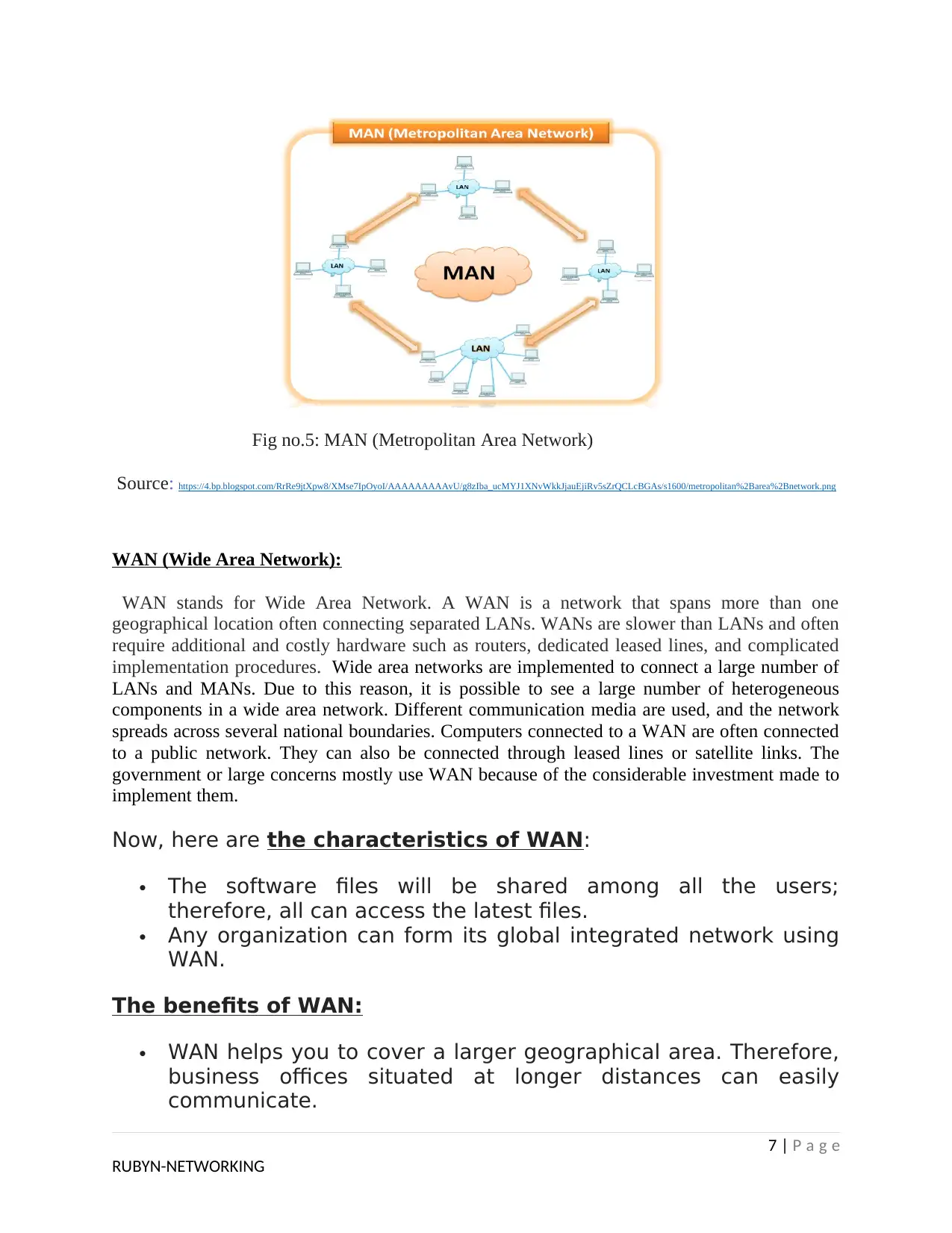
Fig no.5: MAN (Metropolitan Area Network)
Source: https://4.bp.blogspot.com/RrRe9jtXpw8/XMse7IpOyoI/AAAAAAAAAvU/g8zIba_ucMYJ1XNvWkkJjauEjiRv5sZrQCLcBGAs/s1600/metropolitan%2Barea%2Bnetwork.png
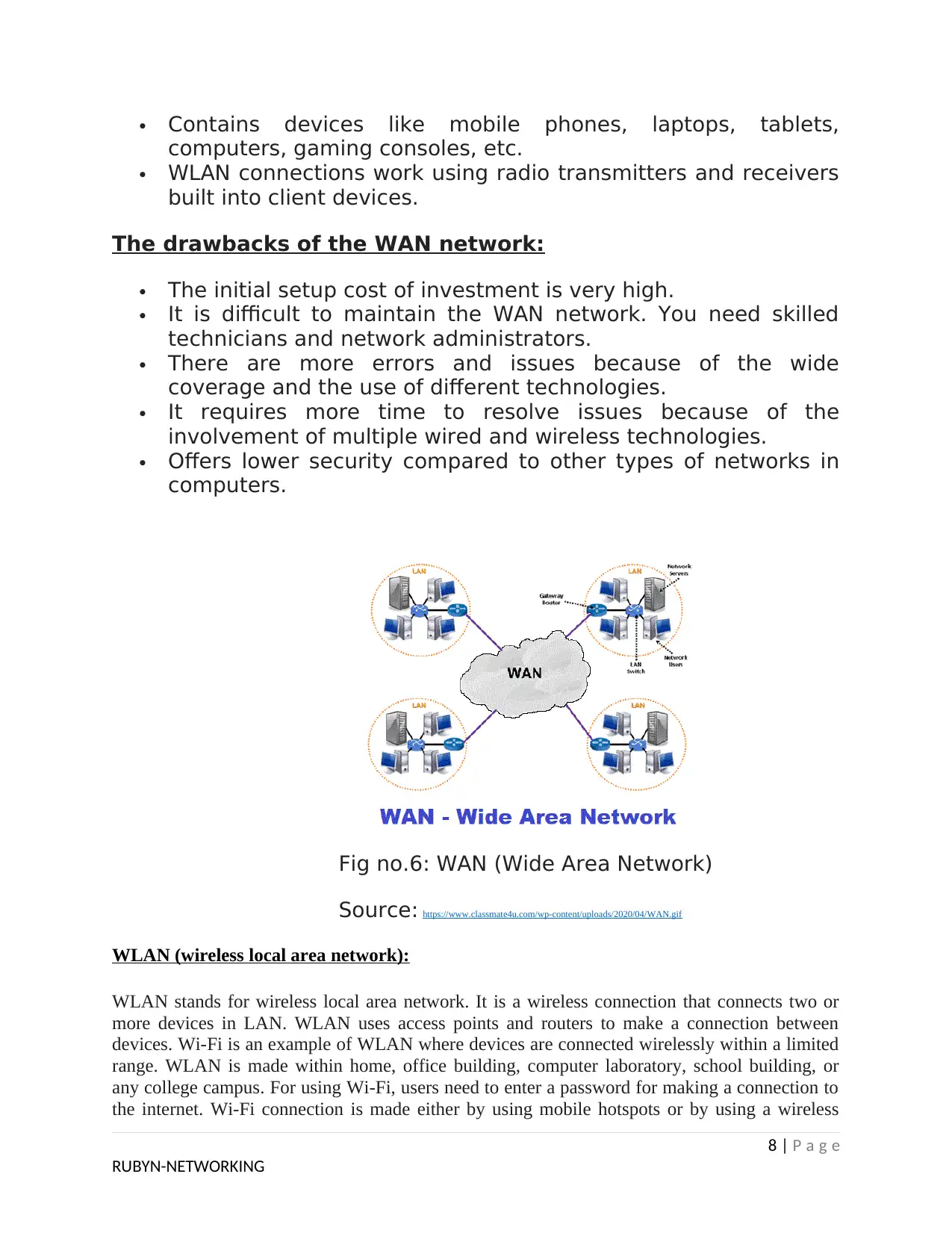
WAN (Wide Area Network):
WAN stands for Wide Area Network. A WAN is a network that spans more than one
geographical location often connecting separated LANs. WANs are slower than LANs and often
require additional and costly hardware such as routers, dedicated leased lines, and complicated
implementation procedures. Wide area networks are implemented to connect a large number of
LANs and MANs. Due to this reason, it is possible to see a large number of heterogeneous
components in a wide area network. Different communication media are used, and the network
spreads across several national boundaries. Computers connected to a WAN are often connected
to a public network. They can also be connected through leased lines or satellite links. The
government or large concerns mostly use WAN because of the considerable investment made to
implement them.
Now, here are the characteristics of WAN:
The software files will be shared among all the users;
therefore, all can access the latest files.
Any organization can form its global integrated network using
WAN.
The benefits of WAN:
WAN helps you to cover a larger geographical area. Therefore,
business offices situated at longer distances can easily
communicate.
7 | P a g e
RUBYN-NETWORKING
Source: https://4.bp.blogspot.com/RrRe9jtXpw8/XMse7IpOyoI/AAAAAAAAAvU/g8zIba_ucMYJ1XNvWkkJjauEjiRv5sZrQCLcBGAs/s1600/metropolitan%2Barea%2Bnetwork.png
WAN (Wide Area Network):
WAN stands for Wide Area Network. A WAN is a network that spans more than one
geographical location often connecting separated LANs. WANs are slower than LANs and often
require additional and costly hardware such as routers, dedicated leased lines, and complicated
implementation procedures. Wide area networks are implemented to connect a large number of
LANs and MANs. Due to this reason, it is possible to see a large number of heterogeneous
components in a wide area network. Different communication media are used, and the network
spreads across several national boundaries. Computers connected to a WAN are often connected
to a public network. They can also be connected through leased lines or satellite links. The
government or large concerns mostly use WAN because of the considerable investment made to
implement them.
Now, here are the characteristics of WAN:
The software files will be shared among all the users;
therefore, all can access the latest files.
Any organization can form its global integrated network using
WAN.
The benefits of WAN:
WAN helps you to cover a larger geographical area. Therefore,
business offices situated at longer distances can easily
communicate.
7 | P a g e
RUBYN-NETWORKING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Contains devices like mobile phones, laptops, tablets,
computers, gaming consoles, etc.
WLAN connections work using radio transmitters and receivers
built into client devices.
The drawbacks of the WAN network:
The initial setup cost of investment is very high.
It is difficult to maintain the WAN network. You need skilled
technicians and network administrators.
There are more errors and issues because of the wide
coverage and the use of different technologies.
It requires more time to resolve issues because of the
involvement of multiple wired and wireless technologies.
Offers lower security compared to other types of networks in
computers.
Fig no.6: WAN (Wide Area Network)
Source: https://www.classmate4u.com/wp-content/uploads/2020/04/WAN.gif
WLAN (wireless local area network):
WLAN stands for wireless local area network. It is a wireless connection that connects two or
more devices in LAN. WLAN uses access points and routers to make a connection between
devices. Wi-Fi is an example of WLAN where devices are connected wirelessly within a limited
range. WLAN is made within home, office building, computer laboratory, school building, or
any college campus. For using Wi-Fi, users need to enter a password for making a connection to
the internet. Wi-Fi connection is made either by using mobile hotspots or by using a wireless
8 | P a g e
RUBYN-NETWORKING
computers, gaming consoles, etc.
WLAN connections work using radio transmitters and receivers
built into client devices.
The drawbacks of the WAN network:
The initial setup cost of investment is very high.
It is difficult to maintain the WAN network. You need skilled
technicians and network administrators.
There are more errors and issues because of the wide
coverage and the use of different technologies.
It requires more time to resolve issues because of the
involvement of multiple wired and wireless technologies.
Offers lower security compared to other types of networks in
computers.
Fig no.6: WAN (Wide Area Network)
Source: https://www.classmate4u.com/wp-content/uploads/2020/04/WAN.gif
WLAN (wireless local area network):
WLAN stands for wireless local area network. It is a wireless connection that connects two or
more devices in LAN. WLAN uses access points and routers to make a connection between
devices. Wi-Fi is an example of WLAN where devices are connected wirelessly within a limited
range. WLAN is made within home, office building, computer laboratory, school building, or
any college campus. For using Wi-Fi, users need to enter a password for making a connection to
the internet. Wi-Fi connection is made either by using mobile hotspots or by using a wireless
8 | P a g e
RUBYN-NETWORKING

modem or wireless router. WLAN includes an access point (AP) which is used to connect to the
internet. AP sends and receives radio frequency signals to the connected devices. In 1990 WLAN
installation was expensive and was only deployed where the wired connection was not possible.
In the late 1990s, cost decreases to implement WLAN because of using IEEE 802.11 standard. It
works with a bandwidth of 2.4 GHZ (802.11b) or 5 GHZ (802.11 a). The devices which WLAN
connects are also called clients.
Advantages of WLAN:
It is a reliable type of communication.
As WLAN reduces physical wires it is a flexible way of communication.
WLAN also reduces the cost of ownership.
It is easier to add remote workstations.
It provides a high data rate due to small area coverage.
You can also move the workstation while maintaining the connectivity.
For propagation, light of sight is not required.
The direction of connectivity can be anywhere i.e., you can connect devices in any
direction unless it is within the range of the access point.
Easy installation and you need don’t need extra cables for installation.
WLAN can be useful in disasters situation e.g., earthquakes and fires. People can still
communicate through the wireless network during a disaster.
It is economical because of the small area access.
If there are any buildings or trees then still wireless connection works.
Disadvantages of WLAN:
WLAN requires a license
It has a limited area to cover
Government agencies can limit the signals of WLAN if required. This can affect data
transfer from connected devices to the internet
If the number of connected devices increases then the data transfer rate decreases
WLAN uses radio frequency which can interfere with other devices which use radio
frequency
If there is rain or thunder then communication may interfere
Attackers can get access to the transmitted data because wireless LAN has low data
security
Signals may be affected by the environment as compared to using fiber optics
The radiation of WLAN can be harmful to the environment
As WLAN uses access points are more expensive than wires and hubs
Access points can get signals of nearest access points
It is required to change the network card and access point when standard changes
LAN cable is still required which acts as the backbone of the WLAN
Low data transfer rate than wired connection because WLAN uses radio frequency
Chances of errors are high
Communication is not secure and can be accessed by unauthorized users
9 | P a g e
RUBYN-NETWORKING
internet. AP sends and receives radio frequency signals to the connected devices. In 1990 WLAN
installation was expensive and was only deployed where the wired connection was not possible.
In the late 1990s, cost decreases to implement WLAN because of using IEEE 802.11 standard. It
works with a bandwidth of 2.4 GHZ (802.11b) or 5 GHZ (802.11 a). The devices which WLAN
connects are also called clients.
Advantages of WLAN:
It is a reliable type of communication.
As WLAN reduces physical wires it is a flexible way of communication.
WLAN also reduces the cost of ownership.
It is easier to add remote workstations.
It provides a high data rate due to small area coverage.
You can also move the workstation while maintaining the connectivity.
For propagation, light of sight is not required.
The direction of connectivity can be anywhere i.e., you can connect devices in any
direction unless it is within the range of the access point.
Easy installation and you need don’t need extra cables for installation.
WLAN can be useful in disasters situation e.g., earthquakes and fires. People can still
communicate through the wireless network during a disaster.
It is economical because of the small area access.
If there are any buildings or trees then still wireless connection works.
Disadvantages of WLAN:
WLAN requires a license
It has a limited area to cover
Government agencies can limit the signals of WLAN if required. This can affect data
transfer from connected devices to the internet
If the number of connected devices increases then the data transfer rate decreases
WLAN uses radio frequency which can interfere with other devices which use radio
frequency
If there is rain or thunder then communication may interfere
Attackers can get access to the transmitted data because wireless LAN has low data
security
Signals may be affected by the environment as compared to using fiber optics
The radiation of WLAN can be harmful to the environment
As WLAN uses access points are more expensive than wires and hubs
Access points can get signals of nearest access points
It is required to change the network card and access point when standard changes
LAN cable is still required which acts as the backbone of the WLAN
Low data transfer rate than wired connection because WLAN uses radio frequency
Chances of errors are high
Communication is not secure and can be accessed by unauthorized users
9 | P a g e
RUBYN-NETWORKING
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Fig no.7: WLAN (Wireless Local Area Network)
Source: http://accoladewireless.com/wp-content/uploads/2015/05/wlan41.jpg
These are the different types of networks, now we are going to discuss the different network
systems, their advantages, and disadvantages. So, the different types of the network system are:
I. Peer-To-Peer Network
II. Client-Server Network
III. Cloud Network
IV. Cluster Network
V. Virtualized Network
VI. Centralized Network
I. Peer-To-Peer Network:
A Peer-to-Peer network is defined as a network of computers, which does not consist server and
is mostly used by small organizations, which allows sharing of certain files and folders to every
user or selected user. Small organizations, having peer-to-peer networks uses a dedicated file
server. In such networks, files and folders can only be configured to allow the users for copying
them. Those files and folders cannot be placed/altered in their original location. This is done for
the safety of files and folders. Characteristics of a Peer-to-peer network are similar to small local
area networks (LAN). Computers involved in a peer-to-peer network use the same set of
networking rules and regulations and the same software. The router provides centralized Internet.
In these types of networks, computers are connected directly. This kind of network is mostly
used in small organizations like schools, colleges, and small government offices where there is
no need for security. It is mostly used for sharing data and information.
10 | P a g e
RUBYN-NETWORKING
Source: http://accoladewireless.com/wp-content/uploads/2015/05/wlan41.jpg
These are the different types of networks, now we are going to discuss the different network
systems, their advantages, and disadvantages. So, the different types of the network system are:
I. Peer-To-Peer Network
II. Client-Server Network
III. Cloud Network
IV. Cluster Network
V. Virtualized Network
VI. Centralized Network
I. Peer-To-Peer Network:
A Peer-to-Peer network is defined as a network of computers, which does not consist server and
is mostly used by small organizations, which allows sharing of certain files and folders to every
user or selected user. Small organizations, having peer-to-peer networks uses a dedicated file
server. In such networks, files and folders can only be configured to allow the users for copying
them. Those files and folders cannot be placed/altered in their original location. This is done for
the safety of files and folders. Characteristics of a Peer-to-peer network are similar to small local
area networks (LAN). Computers involved in a peer-to-peer network use the same set of
networking rules and regulations and the same software. The router provides centralized Internet.
In these types of networks, computers are connected directly. This kind of network is mostly
used in small organizations like schools, colleges, and small government offices where there is
no need for security. It is mostly used for sharing data and information.
10 | P a g e
RUBYN-NETWORKING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
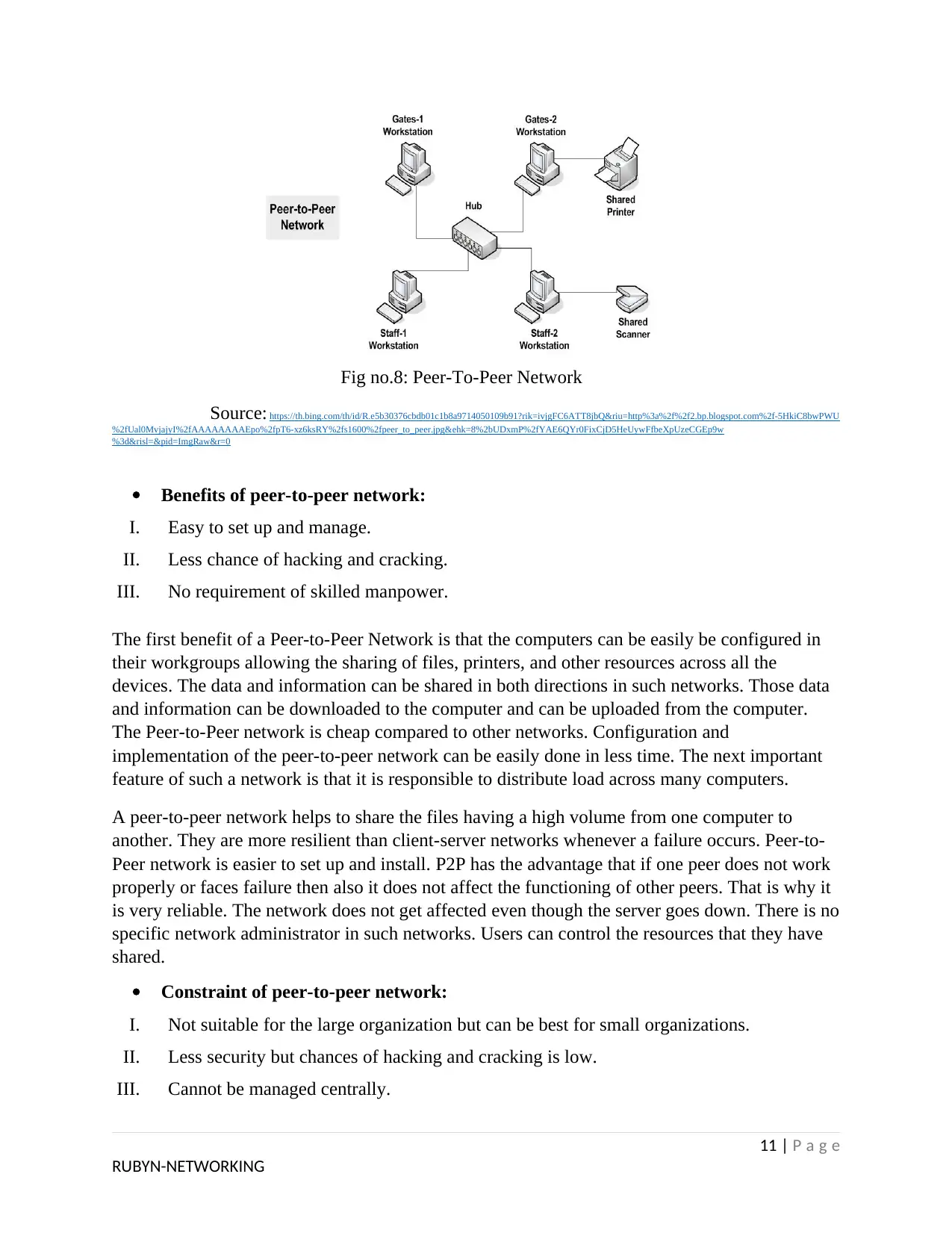
Fig no.8: Peer-To-Peer Network
Source: https://th.bing.com/th/id/R.e5b30376cbdb01c1b8a9714050109b91?rik=ivjgFC6ATT8jbQ&riu=http%3a%2f%2f2.bp.blogspot.com%2f-5HkiC8bwPWU
%2fUal0MvjajyI%2fAAAAAAAAEpo%2fpT6-xz6ksRY%2fs1600%2fpeer_to_peer.jpg&ehk=8%2bUDxmP%2fYAE6QYr0FixCjD5HeUywFfbeXpUzeCGEp9w
%3d&risl=&pid=ImgRaw&r=0
Benefits of peer-to-peer network:
I. Easy to set up and manage.
II. Less chance of hacking and cracking.
III. No requirement of skilled manpower.
The first benefit of a Peer-to-Peer Network is that the computers can be easily be configured in
their workgroups allowing the sharing of files, printers, and other resources across all the
devices. The data and information can be shared in both directions in such networks. Those data
and information can be downloaded to the computer and can be uploaded from the computer.
The Peer-to-Peer network is cheap compared to other networks. Configuration and
implementation of the peer-to-peer network can be easily done in less time. The next important
feature of such a network is that it is responsible to distribute load across many computers.
A peer-to-peer network helps to share the files having a high volume from one computer to
another. They are more resilient than client-server networks whenever a failure occurs. Peer-to-
Peer network is easier to set up and install. P2P has the advantage that if one peer does not work
properly or faces failure then also it does not affect the functioning of other peers. That is why it
is very reliable. The network does not get affected even though the server goes down. There is no
specific network administrator in such networks. Users can control the resources that they have
shared.
Constraint of peer-to-peer network:
I. Not suitable for the large organization but can be best for small organizations.
II. Less security but chances of hacking and cracking is low.
III. Cannot be managed centrally.
11 | P a g e
RUBYN-NETWORKING
Source: https://th.bing.com/th/id/R.e5b30376cbdb01c1b8a9714050109b91?rik=ivjgFC6ATT8jbQ&riu=http%3a%2f%2f2.bp.blogspot.com%2f-5HkiC8bwPWU
%2fUal0MvjajyI%2fAAAAAAAAEpo%2fpT6-xz6ksRY%2fs1600%2fpeer_to_peer.jpg&ehk=8%2bUDxmP%2fYAE6QYr0FixCjD5HeUywFfbeXpUzeCGEp9w
%3d&risl=&pid=ImgRaw&r=0
Benefits of peer-to-peer network:
I. Easy to set up and manage.
II. Less chance of hacking and cracking.
III. No requirement of skilled manpower.
The first benefit of a Peer-to-Peer Network is that the computers can be easily be configured in
their workgroups allowing the sharing of files, printers, and other resources across all the
devices. The data and information can be shared in both directions in such networks. Those data
and information can be downloaded to the computer and can be uploaded from the computer.
The Peer-to-Peer network is cheap compared to other networks. Configuration and
implementation of the peer-to-peer network can be easily done in less time. The next important
feature of such a network is that it is responsible to distribute load across many computers.
A peer-to-peer network helps to share the files having a high volume from one computer to
another. They are more resilient than client-server networks whenever a failure occurs. Peer-to-
Peer network is easier to set up and install. P2P has the advantage that if one peer does not work
properly or faces failure then also it does not affect the functioning of other peers. That is why it
is very reliable. The network does not get affected even though the server goes down. There is no
specific network administrator in such networks. Users can control the resources that they have
shared.
Constraint of peer-to-peer network:
I. Not suitable for the large organization but can be best for small organizations.
II. Less security but chances of hacking and cracking is low.
III. Cannot be managed centrally.
11 | P a g e
RUBYN-NETWORKING
As a peer-to-peer network does not rely on a central server and it does not have a specific
administrator, the whole system is decentralized and it is difficult to control. In such networks, a
specific person cannot have the right to determine the whole accessibility setting of the network
to handle it properly. One of the main drawbacks is that it is not secure. Security is very poor
because of which viruses and malware can easily be transmitted over its architecture. Once the
data gets lost from this type of network, it cannot be recovered, or even if it is recovered, it takes
a lot of time and hard work. A computer in this network must have a backup system. A peer-to-
peer network is a technology, which is mostly used in torrents. In torrents, it is used to transfer a
lot of movies, music, and other copyrighted files. It slows down the performance of users
because others or anyone in this network can access each computer.
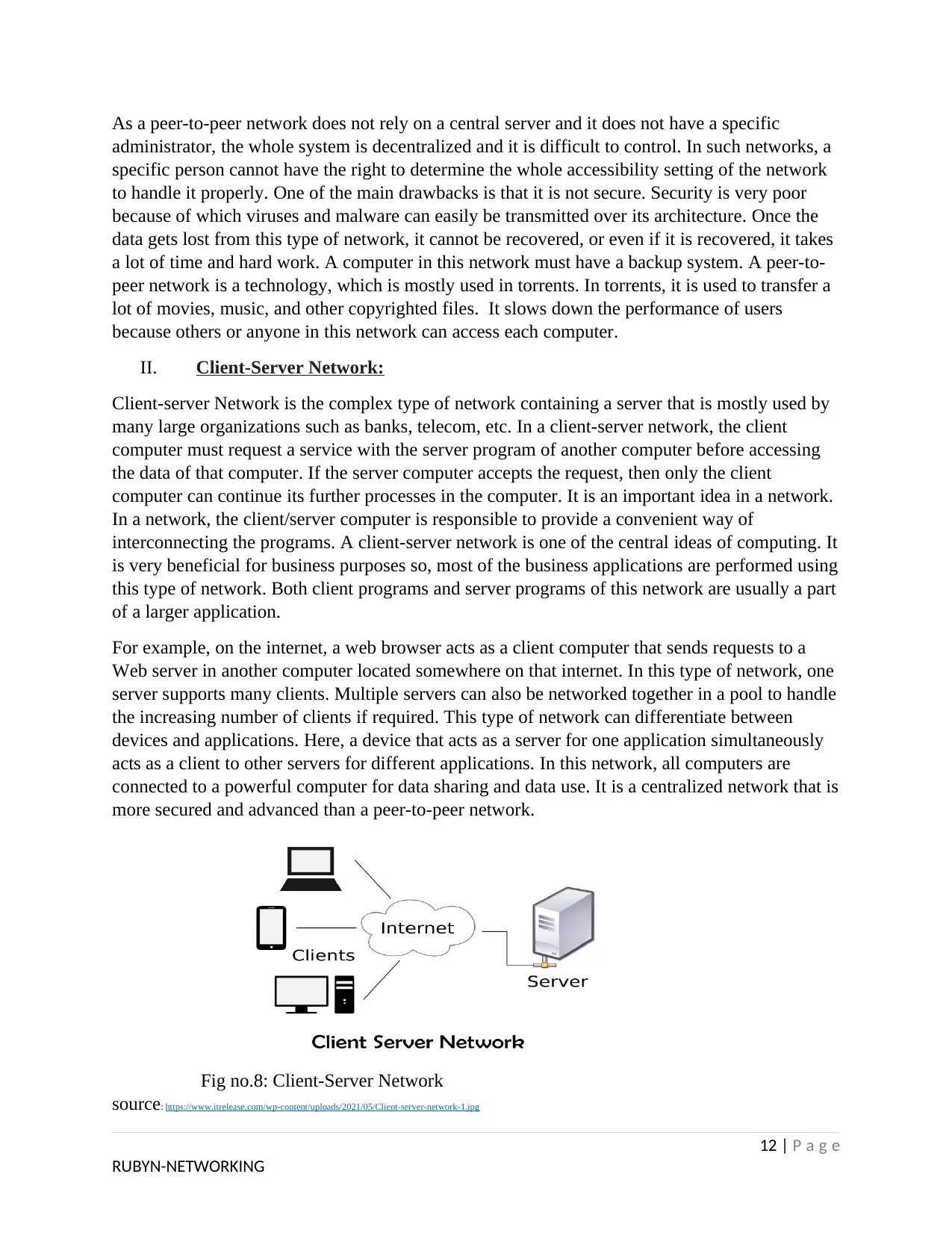
II. Client-Server Network:
Client-server Network is the complex type of network containing a server that is mostly used by
many large organizations such as banks, telecom, etc. In a client-server network, the client
computer must request a service with the server program of another computer before accessing
the data of that computer. If the server computer accepts the request, then only the client
computer can continue its further processes in the computer. It is an important idea in a network.
In a network, the client/server computer is responsible to provide a convenient way of
interconnecting the programs. A client-server network is one of the central ideas of computing. It
is very beneficial for business purposes so, most of the business applications are performed using
this type of network. Both client programs and server programs of this network are usually a part
of a larger application.
For example, on the internet, a web browser acts as a client computer that sends requests to a
Web server in another computer located somewhere on that internet. In this type of network, one
server supports many clients. Multiple servers can also be networked together in a pool to handle
the increasing number of clients if required. This type of network can differentiate between
devices and applications. Here, a device that acts as a server for one application simultaneously
acts as a client to other servers for different applications. In this network, all computers are
connected to a powerful computer for data sharing and data use. It is a centralized network that is
more secured and advanced than a peer-to-peer network.
Fig no.8: Client-Server Network
source: https://www.itrelease.com/wp-content/uploads/2021/05/Client-server-network-1.jpg
12 | P a g e
RUBYN-NETWORKING
administrator, the whole system is decentralized and it is difficult to control. In such networks, a
specific person cannot have the right to determine the whole accessibility setting of the network
to handle it properly. One of the main drawbacks is that it is not secure. Security is very poor
because of which viruses and malware can easily be transmitted over its architecture. Once the
data gets lost from this type of network, it cannot be recovered, or even if it is recovered, it takes
a lot of time and hard work. A computer in this network must have a backup system. A peer-to-
peer network is a technology, which is mostly used in torrents. In torrents, it is used to transfer a
lot of movies, music, and other copyrighted files. It slows down the performance of users
because others or anyone in this network can access each computer.
II. Client-Server Network:
Client-server Network is the complex type of network containing a server that is mostly used by
many large organizations such as banks, telecom, etc. In a client-server network, the client
computer must request a service with the server program of another computer before accessing
the data of that computer. If the server computer accepts the request, then only the client
computer can continue its further processes in the computer. It is an important idea in a network.
In a network, the client/server computer is responsible to provide a convenient way of
interconnecting the programs. A client-server network is one of the central ideas of computing. It
is very beneficial for business purposes so, most of the business applications are performed using
this type of network. Both client programs and server programs of this network are usually a part
of a larger application.
For example, on the internet, a web browser acts as a client computer that sends requests to a
Web server in another computer located somewhere on that internet. In this type of network, one
server supports many clients. Multiple servers can also be networked together in a pool to handle
the increasing number of clients if required. This type of network can differentiate between
devices and applications. Here, a device that acts as a server for one application simultaneously
acts as a client to other servers for different applications. In this network, all computers are
connected to a powerful computer for data sharing and data use. It is a centralized network that is
more secured and advanced than a peer-to-peer network.
Fig no.8: Client-Server Network
source: https://www.itrelease.com/wp-content/uploads/2021/05/Client-server-network-1.jpg
12 | P a g e
RUBYN-NETWORKING
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





