Comprehensive Computer Security Report for Need 4 Help Organization
VerifiedAdded on 2022/12/13
|18
|5184
|368
Report
AI Summary
This report provides a comprehensive analysis of computer security, focusing on the elements of confidentiality, integrity, and availability (CIA) within the context of the Need 4 Help organization. It delves into various computer security issues, including cybercrime, cyber-attacks, cyber terrorism, cyber espionage, and data theft. The report explores security frameworks, access control systems, and the importance of social, ethical, and legal considerations. It discusses security elements like confidentiality, integrity, availability, authenticity, and non-repudiation, and evaluates current cyber threats, including cyber espionage and data theft. The report also analyzes the impact of these threats on organizational activities and security measures, emphasizing the need for preventative measures and the implementation of new technological aspects to protect confidential data and ensure the integrity of computer systems. The report emphasizes the importance of data protection and highlights the critical role of cybersecurity in maintaining business operations and protecting sensitive information.

Report writing on
computer security
computer security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction................................................................................................................................3
Main Body..................................................................................................................................3
Task 1- Security elements......................................................................................................3
Task 2- Computer security issues..........................................................................................6
Task 3- Security framework.................................................................................................10
Task 4- Access control system.............................................................................................12
Task 5- Social, ethical and legal consideration....................................................................13
Conclusion................................................................................................................................16
References................................................................................................................................17
Introduction................................................................................................................................3
Main Body..................................................................................................................................3
Task 1- Security elements......................................................................................................3
Task 2- Computer security issues..........................................................................................6
Task 3- Security framework.................................................................................................10
Task 4- Access control system.............................................................................................12
Task 5- Social, ethical and legal consideration....................................................................13
Conclusion................................................................................................................................16
References................................................................................................................................17

Introduction
Cyber security issue are mainly highly concerned and make major breaches related to
computer security issues. A cyber security breach survey of 2019 concluded that department
of digital, culture, sports, media and many more things are related to many cyber-attack and
make persistent threat to society, business and charity institutes. That statistical data show
that about one third of the business and 2 out of 10 charitable institute are victims of cyber
security breaches from last one year. Most of the business organisation are belong to medium
size and phishing and malwares are recorded as the main reason for cyber-attacks. Whereas
crime survey of England and wales (CSEW) have been reported many of the virus and other
malwares software’s which misuse in the crime investigation are highly recorded (Acuña,
2016). Here the chosen charity organisation is Need 4 Help, which is a UK based
organisation that mainly deal with poverty and having their own set up in London. They are
using different and advance technology based computer as they are saving client information
in that. Need4Help are known and well aware with the security threats and confidentiality,
integrity and availability of the critical data which they are holding. This report include the
different security elements, computer security issues, their framework, access control system.
In addition to that social, ethical and legal issues and their consideration are used for
completing this report.
Main Body
Task 1- Security elements
In general the form of computer security is basically related to make management
security that make a cover a wide area of practice and make techniques. It is helpful in
managing and protecting the data from undesired and various situations (Albugmi and et.al.,
2016). In order to protect and choose the data this is essential to seem and work the
management ability to gain the access and make more valuable information through different
sources and applicability (Top 5 Key Elements of an Information Security, 2021). Some of the
major security element are basically related to cyber security within the organisation which
are discussed below:
Cyber security issue are mainly highly concerned and make major breaches related to
computer security issues. A cyber security breach survey of 2019 concluded that department
of digital, culture, sports, media and many more things are related to many cyber-attack and
make persistent threat to society, business and charity institutes. That statistical data show
that about one third of the business and 2 out of 10 charitable institute are victims of cyber
security breaches from last one year. Most of the business organisation are belong to medium
size and phishing and malwares are recorded as the main reason for cyber-attacks. Whereas
crime survey of England and wales (CSEW) have been reported many of the virus and other
malwares software’s which misuse in the crime investigation are highly recorded (Acuña,
2016). Here the chosen charity organisation is Need 4 Help, which is a UK based
organisation that mainly deal with poverty and having their own set up in London. They are
using different and advance technology based computer as they are saving client information
in that. Need4Help are known and well aware with the security threats and confidentiality,
integrity and availability of the critical data which they are holding. This report include the
different security elements, computer security issues, their framework, access control system.
In addition to that social, ethical and legal issues and their consideration are used for
completing this report.
Main Body
Task 1- Security elements
In general the form of computer security is basically related to make management
security that make a cover a wide area of practice and make techniques. It is helpful in
managing and protecting the data from undesired and various situations (Albugmi and et.al.,
2016). In order to protect and choose the data this is essential to seem and work the
management ability to gain the access and make more valuable information through different
sources and applicability (Top 5 Key Elements of an Information Security, 2021). Some of the
major security element are basically related to cyber security within the organisation which
are discussed below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
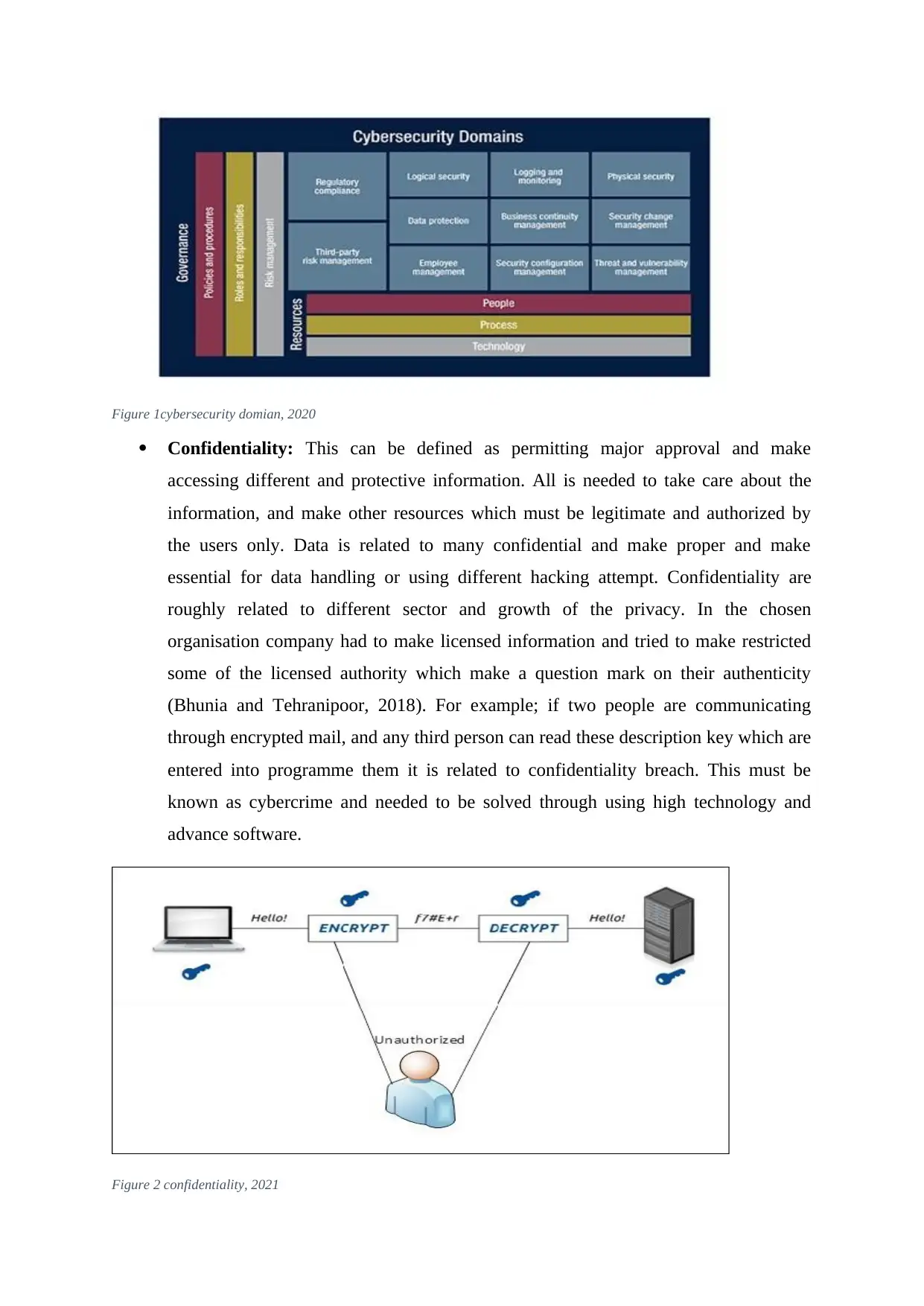
Figure 1cybersecurity domian, 2020
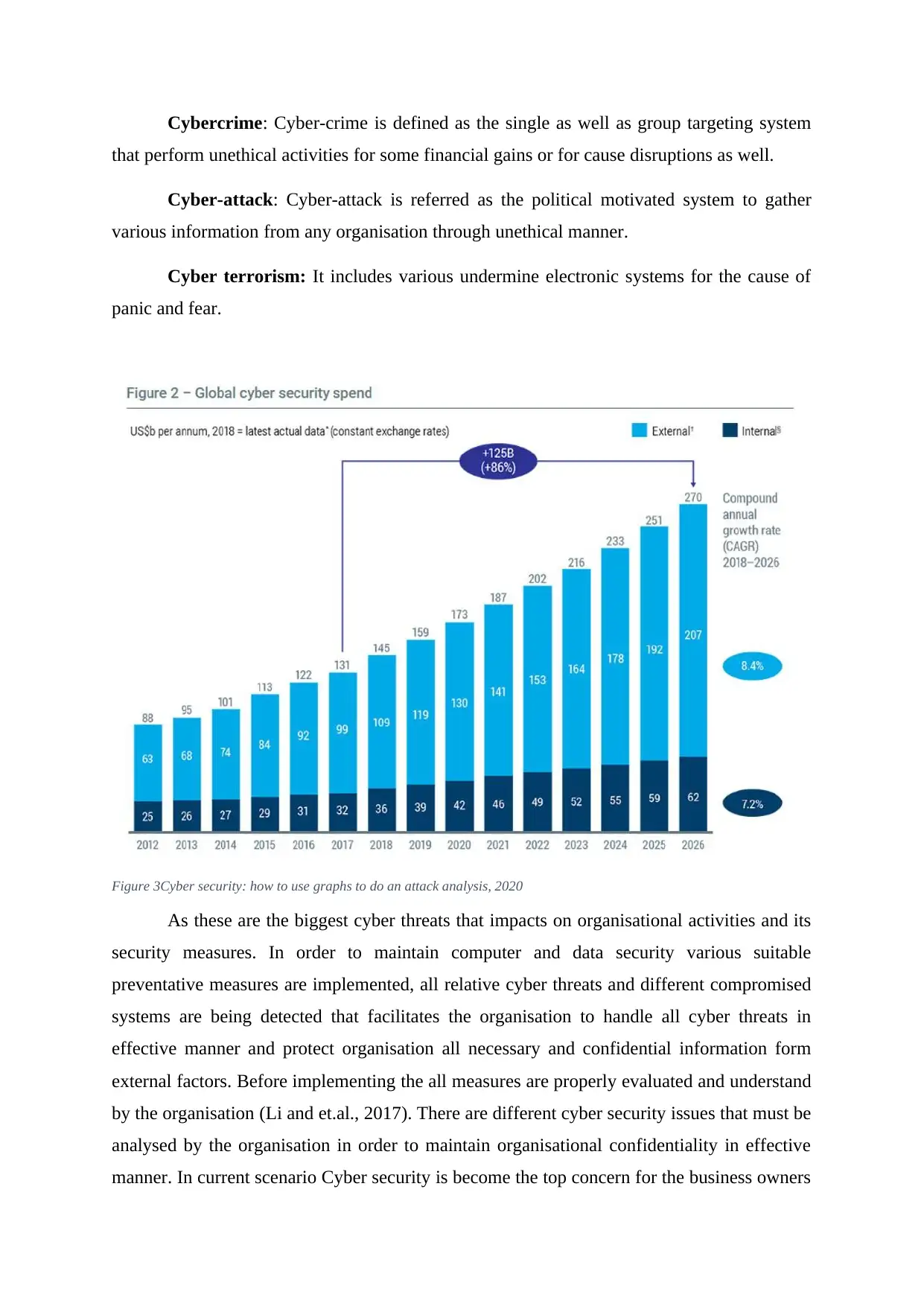
Confidentiality: This can be defined as permitting major approval and make
accessing different and protective information. All is needed to take care about the
information, and make other resources which must be legitimate and authorized by
the users only. Data is related to many confidential and make proper and make
essential for data handling or using different hacking attempt. Confidentiality are
roughly related to different sector and growth of the privacy. In the chosen
organisation company had to make licensed information and tried to make restricted
some of the licensed authority which make a question mark on their authenticity
(Bhunia and Tehranipoor, 2018). For example; if two people are communicating
through encrypted mail, and any third person can read these description key which are
entered into programme them it is related to confidentiality breach. This must be
known as cybercrime and needed to be solved through using high technology and
advance software.
Figure 2 confidentiality, 2021
Confidentiality: This can be defined as permitting major approval and make
accessing different and protective information. All is needed to take care about the
information, and make other resources which must be legitimate and authorized by
the users only. Data is related to many confidential and make proper and make
essential for data handling or using different hacking attempt. Confidentiality are
roughly related to different sector and growth of the privacy. In the chosen
organisation company had to make licensed information and tried to make restricted
some of the licensed authority which make a question mark on their authenticity
(Bhunia and Tehranipoor, 2018). For example; if two people are communicating
through encrypted mail, and any third person can read these description key which are
entered into programme them it is related to confidentiality breach. This must be
known as cybercrime and needed to be solved through using high technology and
advance software.
Figure 2 confidentiality, 2021
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Integrity: Integrity is the trust worthiness of the data which is recorded as the system
and resources to make prevention through some authorised and improper changes.
Mainly integrity is related to two main sub-elements and data integrity which is
related to different content and data analysis which are related to authentication and
make origin of data such as collecting right information from right sources. While this
is basically related to legitimate, correct and protected data from unlawful
modification. This is basically to data integrity which has been make primary and
essential component or make element for information security because users which
have to make online information which are related to different sources (Bullee and
et.al., 2017). For example: when a person in the chosen organisation are able to make
an online transection then they are commonly use protected data of integrity and make
a hash massage and compare with the internal and external original system.
Availability: As the name describe the meaning of its features, it refer to the system
or information to make data or resources are available when it’s required by the client.
The information which are required by the client and possess the actual value and
make an access on the resource at the right time of availability. Mainly here the
cybercriminal resize the data and make a request to make access on the source and get
denied to client when a person needed for the space in any kind of software. For
example: if a hacker has make compressed of a webserver in bank, and put it down.
Then other people of the bank are not able to make any type of e-commerce
transection. And this would be related to lose of the bank and make huge impact on
the economy condition of that particular organisation. This is related to make
effective availability of the data and online sources which are habitual to work and
manage the system in an organised manner.
Authenticity: Here a simple policy and a hierarchical pattern is used in order to
manage the authority. Further some other elements are essential and make different
element to work and manage authentication that may be related to define process and
make able to ensure the data and work with some genuine identity and legitimate
informative system (Hassan, 2019). This is the process which is related to different
sources and able to manage the authenticity and being able to work with data
information. Many of the cybercriminal are use more effective and sophisticated tool
and techniques which are helpful in working with technologies and gain the access
through social engineering, brute force techniques or pass word guessing techniques.
For example: There are different sources which are related to password security like
and resources to make prevention through some authorised and improper changes.
Mainly integrity is related to two main sub-elements and data integrity which is
related to different content and data analysis which are related to authentication and
make origin of data such as collecting right information from right sources. While this
is basically related to legitimate, correct and protected data from unlawful
modification. This is basically to data integrity which has been make primary and
essential component or make element for information security because users which
have to make online information which are related to different sources (Bullee and
et.al., 2017). For example: when a person in the chosen organisation are able to make
an online transection then they are commonly use protected data of integrity and make
a hash massage and compare with the internal and external original system.
Availability: As the name describe the meaning of its features, it refer to the system
or information to make data or resources are available when it’s required by the client.
The information which are required by the client and possess the actual value and
make an access on the resource at the right time of availability. Mainly here the
cybercriminal resize the data and make a request to make access on the source and get
denied to client when a person needed for the space in any kind of software. For
example: if a hacker has make compressed of a webserver in bank, and put it down.
Then other people of the bank are not able to make any type of e-commerce
transection. And this would be related to lose of the bank and make huge impact on
the economy condition of that particular organisation. This is related to make
effective availability of the data and online sources which are habitual to work and
manage the system in an organised manner.
Authenticity: Here a simple policy and a hierarchical pattern is used in order to
manage the authority. Further some other elements are essential and make different
element to work and manage authentication that may be related to define process and
make able to ensure the data and work with some genuine identity and legitimate
informative system (Hassan, 2019). This is the process which is related to different
sources and able to manage the authenticity and being able to work with data
information. Many of the cybercriminal are use more effective and sophisticated tool
and techniques which are helpful in working with technologies and gain the access
through social engineering, brute force techniques or pass word guessing techniques.
For example: There are different sources which are related to password security like

having an online bank account. So if any third person are able to manage different
sources which are basically related to different sources and make some other sources.
Non-repudiation: This can be related to and make assurance that message which are
transmitted among different user and make digital signature through different
encryption is accurate and able to work under the authenticity. And further it can be
said that no one can deny with authentication which are used and manage by digital
signature and not able to serve different sources. Data authentication are used and
manage as per different data hash and manage effective sources in order to analysis
and make suitable changes within hash data sources. This is actually one of the
important source that provide proof of the origin to make more informative
information and make integrity for the information system. This can be make a link to
work and manage the authenticity to work and manage the data of the client in chosen
organisation are useful and essential to them.
All of these are very essential and helpful for the company like Need4help, as they are
effectively helpful and assigned by the company to manage and make desirable changes to
follow the avability and integrity (Joo and et.al., 2017). Employee of the organisation must
have the expertise knowledge and confidential equipment which are related to make future
confidentiality and make effective business opportunities.
Task 2- Computer security issues
Cyber security is referred as the practice that defends computers, mobile devices,
servers and other electronic systems from any malicious attacks. Cyber security is termed as
informational technology security or electronic information security. It is divided in various
categories such as network security, application security, information as well as operational
security. Now these days various threats and issues related to the cyber security is being
raised that affect the security aspects. Global cyber threat is continuous raising with the
respective number of data breaches. These cyber threats affect the whole organisational
activities and their functionality as well. Need4help is a charitable organisation that provides
are security measures to protect the organisational confidentiality in effective manner (Khan,
2016). These threats are properly evaluated by the organisation and prepare appropriate
planning in order to protect their confidential information from any external as well as
internal harmful effects. Some of cyber threats are discussed below:
sources which are basically related to different sources and make some other sources.
Non-repudiation: This can be related to and make assurance that message which are
transmitted among different user and make digital signature through different
encryption is accurate and able to work under the authenticity. And further it can be
said that no one can deny with authentication which are used and manage by digital
signature and not able to serve different sources. Data authentication are used and
manage as per different data hash and manage effective sources in order to analysis
and make suitable changes within hash data sources. This is actually one of the
important source that provide proof of the origin to make more informative
information and make integrity for the information system. This can be make a link to
work and manage the authenticity to work and manage the data of the client in chosen
organisation are useful and essential to them.
All of these are very essential and helpful for the company like Need4help, as they are
effectively helpful and assigned by the company to manage and make desirable changes to
follow the avability and integrity (Joo and et.al., 2017). Employee of the organisation must
have the expertise knowledge and confidential equipment which are related to make future
confidentiality and make effective business opportunities.
Task 2- Computer security issues
Cyber security is referred as the practice that defends computers, mobile devices,
servers and other electronic systems from any malicious attacks. Cyber security is termed as
informational technology security or electronic information security. It is divided in various
categories such as network security, application security, information as well as operational
security. Now these days various threats and issues related to the cyber security is being
raised that affect the security aspects. Global cyber threat is continuous raising with the
respective number of data breaches. These cyber threats affect the whole organisational
activities and their functionality as well. Need4help is a charitable organisation that provides
are security measures to protect the organisational confidentiality in effective manner (Khan,
2016). These threats are properly evaluated by the organisation and prepare appropriate
planning in order to protect their confidential information from any external as well as
internal harmful effects. Some of cyber threats are discussed below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cybercrime: Cyber-crime is defined as the single as well as group targeting system
that perform unethical activities for some financial gains or for cause disruptions as well.
Cyber-attack: Cyber-attack is referred as the political motivated system to gather
various information from any organisation through unethical manner.
Cyber terrorism: It includes various undermine electronic systems for the cause of
panic and fear.
Figure 3Cyber security: how to use graphs to do an attack analysis, 2020
As these are the biggest cyber threats that impacts on organisational activities and its
security measures. In order to maintain computer and data security various suitable
preventative measures are implemented, all relative cyber threats and different compromised
systems are being detected that facilitates the organisation to handle all cyber threats in
effective manner and protect organisation all necessary and confidential information form
external factors. Before implementing the all measures are properly evaluated and understand
by the organisation (Li and et.al., 2017). There are different cyber security issues that must be
analysed by the organisation in order to maintain organisational confidentiality in effective
manner. In current scenario Cyber security is become the top concern for the business owners
that perform unethical activities for some financial gains or for cause disruptions as well.
Cyber-attack: Cyber-attack is referred as the political motivated system to gather
various information from any organisation through unethical manner.
Cyber terrorism: It includes various undermine electronic systems for the cause of
panic and fear.
Figure 3Cyber security: how to use graphs to do an attack analysis, 2020
As these are the biggest cyber threats that impacts on organisational activities and its
security measures. In order to maintain computer and data security various suitable
preventative measures are implemented, all relative cyber threats and different compromised
systems are being detected that facilitates the organisation to handle all cyber threats in
effective manner and protect organisation all necessary and confidential information form
external factors. Before implementing the all measures are properly evaluated and understand
by the organisation (Li and et.al., 2017). There are different cyber security issues that must be
analysed by the organisation in order to maintain organisational confidentiality in effective
manner. In current scenario Cyber security is become the top concern for the business owners
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

and technology executives to handle all data and information to run business in effective
manner. Some of cyber security issues that are faced by the organisation are discussed below:
Cyber Espionage: In current scenario, small as well big both organisations store their
data on the cloud as well as the use of hybrid cloud computing is also increased. So, it
enhances the risk of theft related information, attacking public, private as, hybrid
cloud technology, intellectual properties and trade secrets that affect the business in
effective manner (Mengke and et.al., 2016). The information is related to the valuable
data of customers so, it becomes important for business to create awareness about all
cloud technology best practices as well as regulations. Cloud computing is effectively
established and monitor it in regular bases to protect confidential data from others.
Data Theft: Data theft is the biggest cyber-security issue that is faced by the small as
well as large organisations. Hackers target the businesses as the gateways, as the
small organisation do not have the large as well as robust security protocol in order to
protect their data from theft or any external affects. Highly confidential customer’s
data are stolen by the hackers that affect the small as large both type of organisations
(Cyber security: how to use graphs to do an attack analysis, 2020). The theft data is
used against to the respective organisation in competitive environment that affects its
functioning as well. Vulnerability is a challenge to the organisations that enhances the
cyber security threat.
manner. Some of cyber security issues that are faced by the organisation are discussed below:
Cyber Espionage: In current scenario, small as well big both organisations store their
data on the cloud as well as the use of hybrid cloud computing is also increased. So, it
enhances the risk of theft related information, attacking public, private as, hybrid
cloud technology, intellectual properties and trade secrets that affect the business in
effective manner (Mengke and et.al., 2016). The information is related to the valuable
data of customers so, it becomes important for business to create awareness about all
cloud technology best practices as well as regulations. Cloud computing is effectively
established and monitor it in regular bases to protect confidential data from others.
Data Theft: Data theft is the biggest cyber-security issue that is faced by the small as
well as large organisations. Hackers target the businesses as the gateways, as the
small organisation do not have the large as well as robust security protocol in order to
protect their data from theft or any external affects. Highly confidential customer’s
data are stolen by the hackers that affect the small as large both type of organisations
(Cyber security: how to use graphs to do an attack analysis, 2020). The theft data is
used against to the respective organisation in competitive environment that affects its
functioning as well. Vulnerability is a challenge to the organisations that enhances the
cyber security threat.
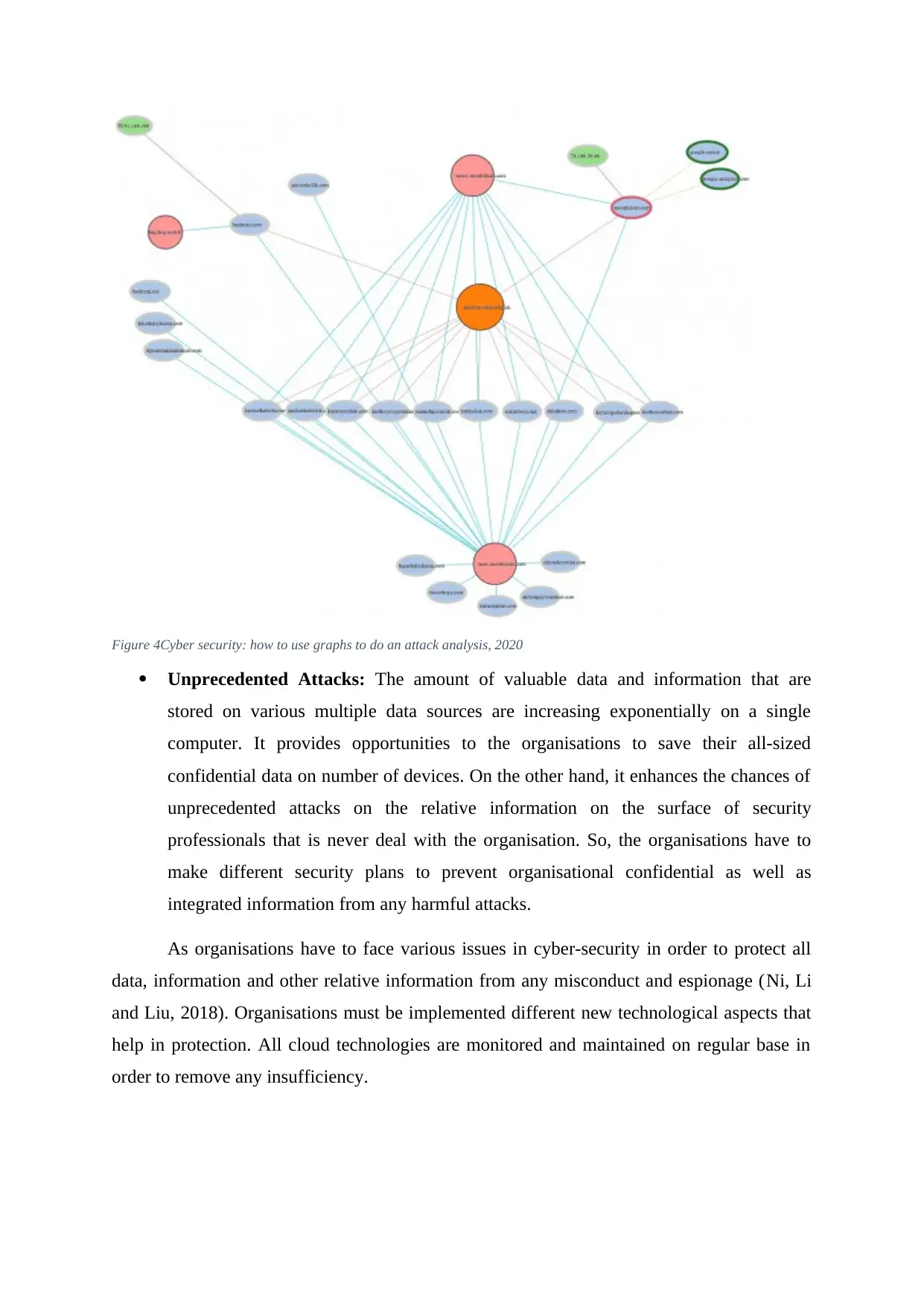
Figure 4Cyber security: how to use graphs to do an attack analysis, 2020
Unprecedented Attacks: The amount of valuable data and information that are
stored on various multiple data sources are increasing exponentially on a single
computer. It provides opportunities to the organisations to save their all-sized
confidential data on number of devices. On the other hand, it enhances the chances of
unprecedented attacks on the relative information on the surface of security
professionals that is never deal with the organisation. So, the organisations have to
make different security plans to prevent organisational confidential as well as
integrated information from any harmful attacks.
As organisations have to face various issues in cyber-security in order to protect all
data, information and other relative information from any misconduct and espionage (Ni, Li
and Liu, 2018). Organisations must be implemented different new technological aspects that
help in protection. All cloud technologies are monitored and maintained on regular base in
order to remove any insufficiency.
Unprecedented Attacks: The amount of valuable data and information that are
stored on various multiple data sources are increasing exponentially on a single
computer. It provides opportunities to the organisations to save their all-sized
confidential data on number of devices. On the other hand, it enhances the chances of
unprecedented attacks on the relative information on the surface of security
professionals that is never deal with the organisation. So, the organisations have to
make different security plans to prevent organisational confidential as well as
integrated information from any harmful attacks.
As organisations have to face various issues in cyber-security in order to protect all
data, information and other relative information from any misconduct and espionage (Ni, Li
and Liu, 2018). Organisations must be implemented different new technological aspects that
help in protection. All cloud technologies are monitored and maintained on regular base in
order to remove any insufficiency.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Task 3- Security framework
A cyber security is a framework which is basically related to common language and
set a standard for make some major security issues across the country and able to understand
the security postures and make vendors. With a high profile framework, some of the major
easier and make procedure which are essential to understand assess, monitor, mitigate and
having high cyber security risk (7 Cyber security Frameworks That Help Reduce Cyber Risk,
2021). There are different cyber security framework which are essential to make different
stages and framework. Some of them are essential and make framework which are related to
framework:
NIST Cyber security Framework
National cyber security framework is the national institute of standard and
technologies (NIST), framework for different improving different infrastructure cyber
security. This is related to different set of guidelines and make private sector to the
companies for follow up identity, detect, and respond to the cyber-attack information. There
are mainly five function are provided which are use and manage to protect identity, protect,
detect, respond and recover the data (Peltier, 2016).
Figure 5, 7 Cyber security Frameworks That Help Reduce Cyber Risk, 2021
ISO 27001 and ISO 27002
A cyber security is a framework which is basically related to common language and
set a standard for make some major security issues across the country and able to understand
the security postures and make vendors. With a high profile framework, some of the major
easier and make procedure which are essential to understand assess, monitor, mitigate and
having high cyber security risk (7 Cyber security Frameworks That Help Reduce Cyber Risk,
2021). There are different cyber security framework which are essential to make different
stages and framework. Some of them are essential and make framework which are related to
framework:
NIST Cyber security Framework
National cyber security framework is the national institute of standard and
technologies (NIST), framework for different improving different infrastructure cyber
security. This is related to different set of guidelines and make private sector to the
companies for follow up identity, detect, and respond to the cyber-attack information. There
are mainly five function are provided which are use and manage to protect identity, protect,
detect, respond and recover the data (Peltier, 2016).
Figure 5, 7 Cyber security Frameworks That Help Reduce Cyber Risk, 2021
ISO 27001 and ISO 27002
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

This is the application which is created by ISO, and make a certification which are
considered for the international business and make standard for validating the cyber security
programme either internationally and across the third parties. Further it can be said that many
of the companies are able to demonstrate to board, customer and make partners to work and
manage different sector for the right things and make manage different cyber risk. This is
basically related to different vendor which is related to good indicator and make cyber
security practices and make control over it. This is basically related to time, process and
management resources that should be related to true benefits and make effective resources on
the true use of new business outcomes.
NERC- CIP
This is introduced to reduce and mitigate the risk of rise in attack and make critical
infrastructure and it will increase the risk to third party fraud. North American electric
reliability corporation- critical infrastructure protection are basically helpful in setting
effective standards and make designed to help the utilities and power to reduce the risk and
bulk for electric system (Pham and et.al., 2017). this system include the training, personal
equipment, planning and having cyber assets that are useful in understanding the concept and
make sure about critical evaluation of cyber-crime and their unidentified risk.
Figure 6 cyber security framework, 2021
This is basically helpful in analysing and foundation for, making integrity security
and having risk management issues into your security to make more performance to
understand the nature and having risk management strategies. While in chosen organisation,
this is use and manage to ISO framework as this is one of the significant and effective
framework to having right and protected data sources. As there are so many framework
which are used by the different companies and organisation, like SOC2, ISO, CIP, GDPR and
considered for the international business and make standard for validating the cyber security
programme either internationally and across the third parties. Further it can be said that many
of the companies are able to demonstrate to board, customer and make partners to work and
manage different sector for the right things and make manage different cyber risk. This is
basically related to different vendor which is related to good indicator and make cyber
security practices and make control over it. This is basically related to time, process and
management resources that should be related to true benefits and make effective resources on
the true use of new business outcomes.
NERC- CIP
This is introduced to reduce and mitigate the risk of rise in attack and make critical
infrastructure and it will increase the risk to third party fraud. North American electric
reliability corporation- critical infrastructure protection are basically helpful in setting
effective standards and make designed to help the utilities and power to reduce the risk and
bulk for electric system (Pham and et.al., 2017). this system include the training, personal
equipment, planning and having cyber assets that are useful in understanding the concept and
make sure about critical evaluation of cyber-crime and their unidentified risk.
Figure 6 cyber security framework, 2021
This is basically helpful in analysing and foundation for, making integrity security
and having risk management issues into your security to make more performance to
understand the nature and having risk management strategies. While in chosen organisation,
this is use and manage to ISO framework as this is one of the significant and effective
framework to having right and protected data sources. As there are so many framework
which are used by the different companies and organisation, like SOC2, ISO, CIP, GDPR and
many more. But for the chosen organisation ISO is the best framework as it will help them to
downside the process and make process which are helpful in requiring time and resources to
work and mange true benefits. That is the reason to choose ISO 27001 and 27002 for the
minimising the risk factor and having a continuous movement and monitoring impact on
society.
Task 4- Access control system
This is an important concept which are basically related to robust the process to make
more strengthen approaches of their computer system. In the chosen organisation, if the user
and their employees are able to make some privileges or having data access rights. It will lead
to make a high impact for the misuse for any type of data which are needed to be. To
safeguard the interest of any escalation of privileges this may be related to Active directories
that helpful for the user accounts.
The active directory are related to advanced filtering criteria and make targeting
objects for restoration easier in the large communication system with intent ally deleted
objectives. This is the method which is used to make selective restriction for the access of
data. This mainly include two major component that authentication and authorization
(Pipyros and et.al., 2016). Many of the organisation are related to face this type of problem
which has to be solved with access control system.
Access control policies are basically related to different sector and growth which may
be assigned and work as per most of the hybrid society and able to work on PC’s, Laptop,
downside the process and make process which are helpful in requiring time and resources to
work and mange true benefits. That is the reason to choose ISO 27001 and 27002 for the
minimising the risk factor and having a continuous movement and monitoring impact on
society.
Task 4- Access control system
This is an important concept which are basically related to robust the process to make
more strengthen approaches of their computer system. In the chosen organisation, if the user
and their employees are able to make some privileges or having data access rights. It will lead
to make a high impact for the misuse for any type of data which are needed to be. To
safeguard the interest of any escalation of privileges this may be related to Active directories
that helpful for the user accounts.
The active directory are related to advanced filtering criteria and make targeting
objects for restoration easier in the large communication system with intent ally deleted
objectives. This is the method which is used to make selective restriction for the access of
data. This mainly include two major component that authentication and authorization
(Pipyros and et.al., 2016). Many of the organisation are related to face this type of problem
which has to be solved with access control system.
Access control policies are basically related to different sector and growth which may
be assigned and work as per most of the hybrid society and able to work on PC’s, Laptop,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





