CO4509 Computer Security Assignment 1: CPDoS Exploit Analysis Report
VerifiedAdded on 2022/08/18
|11
|2731
|18
Report
AI Summary
This report provides a comprehensive analysis of the Cache Poisoned Denial of Service (CPDoS) exploit within the context of Content Distribution Networks (CDNs). It begins by explaining the fundamental principles of CDNs, including their architecture and function in delivering web content efficiently, with an example of their use. The report then delves into the specifics of the CPDoS exploit, detailing its mechanics and impact on web servers. It identifies the various attack vectors, such as HTTP header manipulation, used by attackers to compromise CDNs. Furthermore, the report explores and critically discusses two potential solutions to mitigate CPDoS attacks, including the implementation of appropriate HTTP status codes and the configuration of CDNs to prevent caching of error pages. Finally, it offers a forward-looking analysis of the likely future importance and effectiveness of CPDoS, considering evolving cyber threats and technological advancements. The report concludes with a summary of findings and provides a list of references.

TNE WORKING 0
Co uter e uritmp S c y
Co uter e uritmp S c y
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TNE WORKING 1
Table of Contents
ntrodu tionI c .................................................................................................................................................2
rin i les of CP c p DN.........................................................................................................................................2
C o e loitPD S xp ..............................................................................................................................................3
olutions to t e C o attaS h PD S ck.....................................................................................................................6
se t e a ro riate status odeU h pp p c .............................................................................................................6
Configure C ser i es to not a e TT agesDN v c c ch H P p ...................................................................................6
Future i ortan e and effe ti eness of C omp c c v PD S..........................................................................................7
Con lusionc ...................................................................................................................................................7
eferen esR c ...................................................................................................................................................9
Table of Contents
ntrodu tionI c .................................................................................................................................................2
rin i les of CP c p DN.........................................................................................................................................2
C o e loitPD S xp ..............................................................................................................................................3
olutions to t e C o attaS h PD S ck.....................................................................................................................6
se t e a ro riate status odeU h pp p c .............................................................................................................6
Configure C ser i es to not a e TT agesDN v c c ch H P p ...................................................................................6
Future i ortan e and effe ti eness of C omp c c v PD S..........................................................................................7
Con lusionc ...................................................................................................................................................7
eferen esR c ...................................................................................................................................................9

TNE WORKING 2
Introduction
The term CDN is defined as a content distribution network that is capable to deliver larger
performance and availability by distributing the service spatially related to the data
centers. A content distribution network enables consumers to transfer assets required for
loading internet content involve pictures, data files, HTML pages, and videos. It is
determined that CDN has the potential to manage malicious codes and fraud signals
transferred by the criminals and help companies to address DDOS related cyber-attacks
(Ataullah, and Chauhan, 2012). CPDoS refers to the cache-poisoned denial of services which
is an advanced cache poisoning threat that has the capability to disable web sources and
websites effectively. The purpose of the investigation is to evaluate the principles of CDN
and review the concept behind the CPDoS attack. This report will include numerous
sections including principles of CDN, description of the CPDoS exploit, solutions to the
CPDoS exploit and future importance of CPDoS.
Principles of CDN
CDN is a kind of distributed server that provides pages and other web content to the
consumers based on geographic locations. This type of distributed network is significant in
speeding the delivery of information of web servers with larger traffic signals. Brown and
Willink, (2018) reported that CDN has the capability to provide a way where companies
can protect web servers from the traffic signals. Web servers nearest to the website
respond to the requests and transmitted signals. The CDN copies the pages of a webserver
to the computing networks which are dispersed at geographical locations, caching the
information of the web pages (Herzberg, and Shulman, 2013). When a consumer request a
web server, the content distribution network will redirect the request from the originating
server to the main network which is nearest to the user and provide the obtained
information. It is found that the procedure of bouncing through a content distribution
network is nearly transparent to the consumers.
The major way a consumer would know if a content distribution network has been
accessed is if the provided web server is alternate as compared with the requested URL.
Introduction
The term CDN is defined as a content distribution network that is capable to deliver larger
performance and availability by distributing the service spatially related to the data
centers. A content distribution network enables consumers to transfer assets required for
loading internet content involve pictures, data files, HTML pages, and videos. It is
determined that CDN has the potential to manage malicious codes and fraud signals
transferred by the criminals and help companies to address DDOS related cyber-attacks
(Ataullah, and Chauhan, 2012). CPDoS refers to the cache-poisoned denial of services which
is an advanced cache poisoning threat that has the capability to disable web sources and
websites effectively. The purpose of the investigation is to evaluate the principles of CDN
and review the concept behind the CPDoS attack. This report will include numerous
sections including principles of CDN, description of the CPDoS exploit, solutions to the
CPDoS exploit and future importance of CPDoS.
Principles of CDN
CDN is a kind of distributed server that provides pages and other web content to the
consumers based on geographic locations. This type of distributed network is significant in
speeding the delivery of information of web servers with larger traffic signals. Brown and
Willink, (2018) reported that CDN has the capability to provide a way where companies
can protect web servers from the traffic signals. Web servers nearest to the website
respond to the requests and transmitted signals. The CDN copies the pages of a webserver
to the computing networks which are dispersed at geographical locations, caching the
information of the web pages (Herzberg, and Shulman, 2013). When a consumer request a
web server, the content distribution network will redirect the request from the originating
server to the main network which is nearest to the user and provide the obtained
information. It is found that the procedure of bouncing through a content distribution
network is nearly transparent to the consumers.
The major way a consumer would know if a content distribution network has been
accessed is if the provided web server is alternate as compared with the requested URL.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

TNE WORKING 3
Kumar, (2016) highlighted that when providing larger scale webserver to a global
audience, the content distribution network may decrease latency, decrease bandwidth
consumption accelerate site load times and block traffic signals that occurred in the
systems. For example, many companies like Amazon, eBay, and others use CDN based
networks in the webservers that help to address unwanted signals and traffics transmitted
by the criminals. Moreover, using CDN in the webservers can help to address the problem
of DDoS attacks in the companies and protect data from the attackers effectively. In this
modern generation, CDN based systems are utilized for B2B communication and in serving
information to the users through web servers.
All these are major examples of the CDN technique where the companies are taking
advantage of CDN and manage web servers and webpages effectively. Nowadays, numbers
of the aspects are dependent on internet connectivity, companies use CDN based networks
for accelerating dynamic content, static content, e-commerce transactions, and many more.
Levy, Corrigan-Gibbs, and Boneh, (2016) determined that the world’s largest CDN, owned
and operated by Akamai, spans more than 216,000 servers in around 120 countries and
within more than 1500 computing networks in the worldwide. It is determined that an
edge caching is a primary technique which is used in the CDN technique in order to
increase the speed of the delivery of webserver to end consumer. For accelerating the
delivery of dynamically generated web information which is difficult, and effective CDN
network can be used to manage such problems and optimize the TCP connections and
routers effectively (Mangut, et al., 2015). It is found that consumers of web servers
provided through a CDN experience can effectively perform transactions and manage
issues easily. It is true that the utilization of CDN networks can help companies to enhance
web security and mitigate DoS related cyber-attacks in a reliable manner.
CPDoS exploit
It is defined as the cache poisoned DoS attack that has the capability to block
communication channels and webservers of the companies by transferring the larger
traffic signals to the servers. Most of the criminals use botnet and malicious codes for
generating traffic signals and produce data breach problems in the companies. Mokhtarian
Kumar, (2016) highlighted that when providing larger scale webserver to a global
audience, the content distribution network may decrease latency, decrease bandwidth
consumption accelerate site load times and block traffic signals that occurred in the
systems. For example, many companies like Amazon, eBay, and others use CDN based
networks in the webservers that help to address unwanted signals and traffics transmitted
by the criminals. Moreover, using CDN in the webservers can help to address the problem
of DDoS attacks in the companies and protect data from the attackers effectively. In this
modern generation, CDN based systems are utilized for B2B communication and in serving
information to the users through web servers.
All these are major examples of the CDN technique where the companies are taking
advantage of CDN and manage web servers and webpages effectively. Nowadays, numbers
of the aspects are dependent on internet connectivity, companies use CDN based networks
for accelerating dynamic content, static content, e-commerce transactions, and many more.
Levy, Corrigan-Gibbs, and Boneh, (2016) determined that the world’s largest CDN, owned
and operated by Akamai, spans more than 216,000 servers in around 120 countries and
within more than 1500 computing networks in the worldwide. It is determined that an
edge caching is a primary technique which is used in the CDN technique in order to
increase the speed of the delivery of webserver to end consumer. For accelerating the
delivery of dynamically generated web information which is difficult, and effective CDN
network can be used to manage such problems and optimize the TCP connections and
routers effectively (Mangut, et al., 2015). It is found that consumers of web servers
provided through a CDN experience can effectively perform transactions and manage
issues easily. It is true that the utilization of CDN networks can help companies to enhance
web security and mitigate DoS related cyber-attacks in a reliable manner.
CPDoS exploit
It is defined as the cache poisoned DoS attack that has the capability to block
communication channels and webservers of the companies by transferring the larger
traffic signals to the servers. Most of the criminals use botnet and malicious codes for
generating traffic signals and produce data breach problems in the companies. Mokhtarian
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TNE WORKING 4
and Jacobsen, (2016) provided their views and determined that hackers transfer a simple
HTTP request including malicious signals that helps to target main servers of the
companies and reduce the privacy of web servers and networks easily. Moreover, the cache
forwards the request to the main servers because it does not store fresh information from
the targeted sources. At the main servers, request processing provokes an error because of
the presence of the malicious signals into the servers.
The criminals are capable to obtain the login credentials of the computing devices and
CPDoS attack on the webservers and websites used by the companies for obtaining
sensitive data. From recent literature, conducted by Neves, Ochi, and Albuquerque, (2015)
examined that CPDoS is the advanced class of web cache attack that has the potential to
disable web sources and networks easily. In the last four years, the rate of CPDoS attacks
has enhanced by 45% and many companies are suffering from such attacks due to the
presence of traffic signals in the webservers and resources.
There are major three reasons due to which companies are suffering from such attacks
including lack of privacy, fraud or traffic signals occurred in the webservers and utilization
of less secured networks and resources in the webservers. In the context of CPDoS cyber-
crime, the hackers interconnect to a web server until their request is generated to a new
CDN network. The transmitted request of the hackers includes a malformed HTPP header
and CDN enables criminals to transfer such requests to the main server by which cache
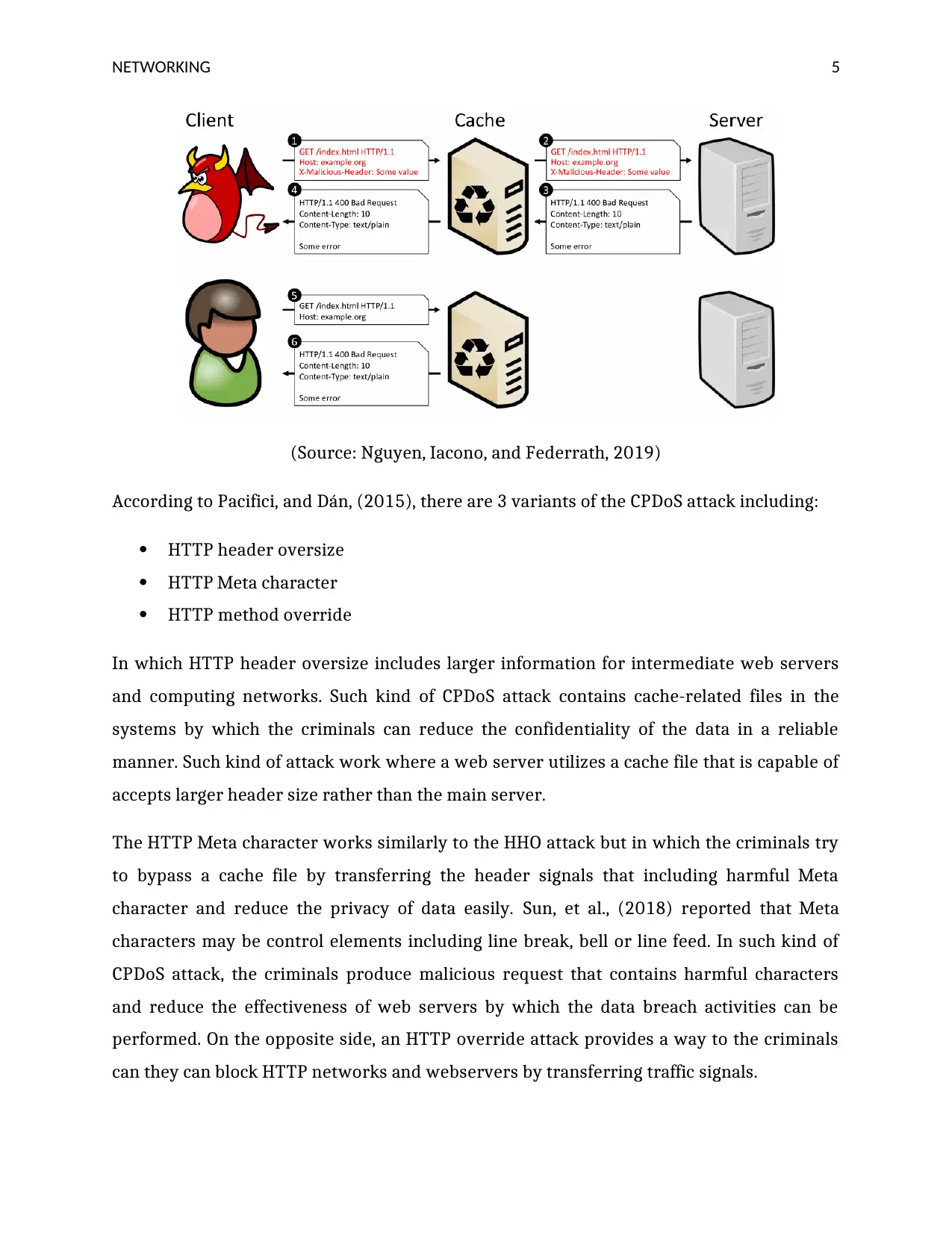
files can be generated in the computing devices and data breach activities can be
performed. The below figure shows the working operations of CPDoS attack in which the
criminals produce cache files and transfer to the main servers for reducing the security of
networks and accessing webservers:
Figure: CPDoS attack
and Jacobsen, (2016) provided their views and determined that hackers transfer a simple
HTTP request including malicious signals that helps to target main servers of the
companies and reduce the privacy of web servers and networks easily. Moreover, the cache
forwards the request to the main servers because it does not store fresh information from
the targeted sources. At the main servers, request processing provokes an error because of
the presence of the malicious signals into the servers.
The criminals are capable to obtain the login credentials of the computing devices and
CPDoS attack on the webservers and websites used by the companies for obtaining
sensitive data. From recent literature, conducted by Neves, Ochi, and Albuquerque, (2015)
examined that CPDoS is the advanced class of web cache attack that has the potential to
disable web sources and networks easily. In the last four years, the rate of CPDoS attacks
has enhanced by 45% and many companies are suffering from such attacks due to the
presence of traffic signals in the webservers and resources.
There are major three reasons due to which companies are suffering from such attacks
including lack of privacy, fraud or traffic signals occurred in the webservers and utilization
of less secured networks and resources in the webservers. In the context of CPDoS cyber-
crime, the hackers interconnect to a web server until their request is generated to a new
CDN network. The transmitted request of the hackers includes a malformed HTPP header
and CDN enables criminals to transfer such requests to the main server by which cache
files can be generated in the computing devices and data breach activities can be
performed. The below figure shows the working operations of CPDoS attack in which the
criminals produce cache files and transfer to the main servers for reducing the security of
networks and accessing webservers:
Figure: CPDoS attack
TNE WORKING 5
(Source: Nguyen, Iacono, and Federrath, 2019)
According to Pacifici, and Dán, (2015), there are 3 variants of the CPDoS attack including:
HTTP header oversize
HTTP Meta character
HTTP method override
In which HTTP header oversize includes larger information for intermediate web servers
and computing networks. Such kind of CPDoS attack contains cache-related files in the
systems by which the criminals can reduce the confidentiality of the data in a reliable
manner. Such kind of attack work where a web server utilizes a cache file that is capable of
accepts larger header size rather than the main server.
The HTTP Meta character works similarly to the HHO attack but in which the criminals try
to bypass a cache file by transferring the header signals that including harmful Meta
character and reduce the privacy of data easily. Sun, et al., (2018) reported that Meta
characters may be control elements including line break, bell or line feed. In such kind of
CPDoS attack, the criminals produce malicious request that contains harmful characters
and reduce the effectiveness of web servers by which the data breach activities can be
performed. On the opposite side, an HTTP override attack provides a way to the criminals
can they can block HTTP networks and webservers by transferring traffic signals.
(Source: Nguyen, Iacono, and Federrath, 2019)
According to Pacifici, and Dán, (2015), there are 3 variants of the CPDoS attack including:
HTTP header oversize
HTTP Meta character
HTTP method override
In which HTTP header oversize includes larger information for intermediate web servers
and computing networks. Such kind of CPDoS attack contains cache-related files in the
systems by which the criminals can reduce the confidentiality of the data in a reliable
manner. Such kind of attack work where a web server utilizes a cache file that is capable of
accepts larger header size rather than the main server.
The HTTP Meta character works similarly to the HHO attack but in which the criminals try
to bypass a cache file by transferring the header signals that including harmful Meta
character and reduce the privacy of data easily. Sun, et al., (2018) reported that Meta
characters may be control elements including line break, bell or line feed. In such kind of
CPDoS attack, the criminals produce malicious request that contains harmful characters
and reduce the effectiveness of web servers by which the data breach activities can be
performed. On the opposite side, an HTTP override attack provides a way to the criminals
can they can block HTTP networks and webservers by transferring traffic signals.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

TNE WORKING 6
It is reported that the presence of traffic signals and cache files in the webservers can lead
security-related problems for the companies and CPDoS is capable to produce the hacking
and data handling issues by reducing the security of web servers and resources. It is
significant for the companies to identify and reduce traffic signals occurred in the main
servers and provide reliable servers by which such kinds of cyber-attacks can be resolved
easily.
Solutions to the CPDoS attack
It is determined that CPDoS is a serious attack for the companies by which data breach and
hacking-related concerns can occur in the workplace and the performance of webservers
can be reduced. There are various mitigation tools that can be used by the companies for
protecting data from criminals and addressing the problem of CPDoS attack:
Use the appropriate status code
It is found that many companies use less secured codes in the webservers that can be
hacked by the criminals for which it is suggested that content providers should utilize the
effective status codes for managing errors. For example, 400 bad requests which are
utilized by numerous HTTP implementations for declaring an oversized is not an
appropriate status code (Trabelsi, 2016). It is found that IIS also utilizes “404 not found”
when a particular header code is exceeded. The perfect and effective error code for an
oversized header is “431 Request header file is large”. As per the analysis, it is reported that
such kinds of signals cannot be cached by any web caching network and companies can
enhance the privacy of data by addressing CPDoS attacks.
Configure CDN services to not cache HTTP pages
It is suggested that companies should configure their content distribution network to not
cache HTTP error pages in order to manage traffic and cache files transferred by the
criminals and address CPDoS attacks. If managers do not have control in the CDN networks,
they can disable the cashing of error pages from the configuration files by including “cache-
control: no-store" to each error page that can help to manage cache files and traffic signals
effectively.
It is reported that the presence of traffic signals and cache files in the webservers can lead
security-related problems for the companies and CPDoS is capable to produce the hacking
and data handling issues by reducing the security of web servers and resources. It is
significant for the companies to identify and reduce traffic signals occurred in the main
servers and provide reliable servers by which such kinds of cyber-attacks can be resolved
easily.
Solutions to the CPDoS attack
It is determined that CPDoS is a serious attack for the companies by which data breach and
hacking-related concerns can occur in the workplace and the performance of webservers
can be reduced. There are various mitigation tools that can be used by the companies for
protecting data from criminals and addressing the problem of CPDoS attack:
Use the appropriate status code
It is found that many companies use less secured codes in the webservers that can be
hacked by the criminals for which it is suggested that content providers should utilize the
effective status codes for managing errors. For example, 400 bad requests which are
utilized by numerous HTTP implementations for declaring an oversized is not an
appropriate status code (Trabelsi, 2016). It is found that IIS also utilizes “404 not found”
when a particular header code is exceeded. The perfect and effective error code for an
oversized header is “431 Request header file is large”. As per the analysis, it is reported that
such kinds of signals cannot be cached by any web caching network and companies can
enhance the privacy of data by addressing CPDoS attacks.
Configure CDN services to not cache HTTP pages
It is suggested that companies should configure their content distribution network to not
cache HTTP error pages in order to manage traffic and cache files transferred by the
criminals and address CPDoS attacks. If managers do not have control in the CDN networks,
they can disable the cashing of error pages from the configuration files by including “cache-
control: no-store" to each error page that can help to manage cache files and traffic signals
effectively.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TNE WORKING 7
Vassilakis, et al., (2015) reported that effective countermeasure against CPDoS attack is to
avoid error pages from caching and include effective codes in the webservers. A web
application firewall can be used by the companies can handle the fraud and unwanted
signals from the computing devices and mitigate CPDoS attacks in an effective way.
However, the firewall should be placed in front of the cache for blocking malicious signals
occurred in the computing devices before they reach to the main servers. It is reported that
using such methods and techniques the rate of CPDoS attack can be reduced effectively and
business communities can protect data and webservers from hackers.
Future importance and effectiveness of CPDoS
It is found that CPDoS is a major security attack that occurs in computing devices and
networks. In the future generation, the companies will be suffered from cyber-crimes as
the uses of ICT technologies and computing networks can produce security and privacy
concerns. It is significant for the companies to focus on security threats and CPDoS attacks
in order to protect data from the cyber-attacks (Vassilakis, et al., 2015). The future
generation will require advanced network security tools and techniques for addressing
CPDoS kinds of attacks and business communities will aware employees about such cyber-
attacks by providing complete training and educational programs. Therefore, it is reported
that in the future, companies will focus on the CPDoS attack and manage such attacks in a
reliable way.
Conclusion
From the above evaluation, it may be concluded that CDN is an effective technique that
provides a way to manage traffic signals and cache files from the webservers and help
companies to protect data against CPDoS attacks. This research identified the key features
of the content distribution networks and evaluated the impact of CPDoS attack on the
webservers. It is found that CPDoS is a serious attack where the criminals transfer
malicious codes and cache files to the webservers and access the computing devices for
gathering sensitive information. It is significant for the companies to focus on the
webservers and reduce cache files and errors from the webservers and websites for
Vassilakis, et al., (2015) reported that effective countermeasure against CPDoS attack is to
avoid error pages from caching and include effective codes in the webservers. A web
application firewall can be used by the companies can handle the fraud and unwanted
signals from the computing devices and mitigate CPDoS attacks in an effective way.
However, the firewall should be placed in front of the cache for blocking malicious signals
occurred in the computing devices before they reach to the main servers. It is reported that
using such methods and techniques the rate of CPDoS attack can be reduced effectively and
business communities can protect data and webservers from hackers.
Future importance and effectiveness of CPDoS
It is found that CPDoS is a major security attack that occurs in computing devices and
networks. In the future generation, the companies will be suffered from cyber-crimes as
the uses of ICT technologies and computing networks can produce security and privacy
concerns. It is significant for the companies to focus on security threats and CPDoS attacks
in order to protect data from the cyber-attacks (Vassilakis, et al., 2015). The future
generation will require advanced network security tools and techniques for addressing
CPDoS kinds of attacks and business communities will aware employees about such cyber-
attacks by providing complete training and educational programs. Therefore, it is reported
that in the future, companies will focus on the CPDoS attack and manage such attacks in a
reliable way.
Conclusion
From the above evaluation, it may be concluded that CDN is an effective technique that
provides a way to manage traffic signals and cache files from the webservers and help
companies to protect data against CPDoS attacks. This research identified the key features
of the content distribution networks and evaluated the impact of CPDoS attack on the
webservers. It is found that CPDoS is a serious attack where the criminals transfer
malicious codes and cache files to the webservers and access the computing devices for
gathering sensitive information. It is significant for the companies to focus on the
webservers and reduce cache files and errors from the webservers and websites for

TNE WORKING 8
protecting data and networks from the CPDoS attack. This paper provided a way to
enhance the experience in the field of CDN and CPDoS attacks and provide effective
solutions for addressing CPDoS related attacks.
protecting data and networks from the CPDoS attack. This paper provided a way to
enhance the experience in the field of CDN and CPDoS attacks and provide effective
solutions for addressing CPDoS related attacks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

TNE WORKING 9
References
Ataullah, M. and Chauhan, N., (2012) An efficient and secure solution for the problems of
arp cache poisoning attacks. International Journal of Computer, Electrical, Automation,
Control and Information Engineering, 6(8), pp.989-996.
Brown, J.D., and Willink, T.J., (2018) ARP cache poisoning and routing loops in ad hoc
networks. Mobile Networks and Applications, 23(5), pp.1306-1317.
Herzberg, A. and Shulman, H., (2013) Socket overloading for fun and cache-poisoning.
In Proceedings of the 29th Annual Computer Security Applications Conference, 12(6), pp.
189-198.
Kumar, G., (2016) Denial of service attacks–an updated perspective. Systems science &
control engineering, 4(1), pp.285-294.
Levy, A., Corrigan-Gibbs, H. and Boneh, D., (2016) Stickler: Defending against malicious
content distribution networks in an unmodified browser. IEEE Security & Privacy, 14(2),
pp.22-28.
Mangut, H.A., Al-Nemrat, A., Benzaïd, C. and Tawil, A.R.H., (2015) ARP cache poisoning
mitigation and forensics investigation. In 2015 IEEE Trustcom/BigDataSE/ISPA, 1(1), pp.
1392-1397.
Mokhtarian, K. and Jacobsen, H.A., (2016) Flexible caching algorithms for video content
distribution networks. IEEE/ACM Transactions on Networking, 25(2), pp.1062-1075.
Neves, T., Ochi, L.S. and Albuquerque, C., (2015) A new hybrid heuristic for replica
placement and request distribution in content distribution networks. Optimization
Letters, 9(4), pp.677-692.
Nguyen, H.V., Iacono, L.L. and Federrath, H., (2019) Your Cache Has Fallen: Cache-Poisoned
Denial-of-Service Attack. In Proceedings of the 2019 ACM SIGSAC Conference on Computer
and Communications Security, 12(6), pp. 1915-1936.
References
Ataullah, M. and Chauhan, N., (2012) An efficient and secure solution for the problems of
arp cache poisoning attacks. International Journal of Computer, Electrical, Automation,
Control and Information Engineering, 6(8), pp.989-996.
Brown, J.D., and Willink, T.J., (2018) ARP cache poisoning and routing loops in ad hoc
networks. Mobile Networks and Applications, 23(5), pp.1306-1317.
Herzberg, A. and Shulman, H., (2013) Socket overloading for fun and cache-poisoning.
In Proceedings of the 29th Annual Computer Security Applications Conference, 12(6), pp.
189-198.
Kumar, G., (2016) Denial of service attacks–an updated perspective. Systems science &
control engineering, 4(1), pp.285-294.
Levy, A., Corrigan-Gibbs, H. and Boneh, D., (2016) Stickler: Defending against malicious
content distribution networks in an unmodified browser. IEEE Security & Privacy, 14(2),
pp.22-28.
Mangut, H.A., Al-Nemrat, A., Benzaïd, C. and Tawil, A.R.H., (2015) ARP cache poisoning
mitigation and forensics investigation. In 2015 IEEE Trustcom/BigDataSE/ISPA, 1(1), pp.
1392-1397.
Mokhtarian, K. and Jacobsen, H.A., (2016) Flexible caching algorithms for video content
distribution networks. IEEE/ACM Transactions on Networking, 25(2), pp.1062-1075.
Neves, T., Ochi, L.S. and Albuquerque, C., (2015) A new hybrid heuristic for replica
placement and request distribution in content distribution networks. Optimization
Letters, 9(4), pp.677-692.
Nguyen, H.V., Iacono, L.L. and Federrath, H., (2019) Your Cache Has Fallen: Cache-Poisoned
Denial-of-Service Attack. In Proceedings of the 2019 ACM SIGSAC Conference on Computer
and Communications Security, 12(6), pp. 1915-1936.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TNE WORKING 10
Pacifici, V. and Dán, G., (2015) Distributed algorithms for content allocation in
interconnected content distribution networks. In 2015 IEEE Conference on Computer
Communications (INFOCOM), 12(6), pp. 2362-2370.
Sun, G., Chang, V., Yang, G. and Liao, D., (2018) The cost-efficient deployment of replica
servers in virtual content distribution networks for data fusion. Information
Sciences, 432(6), pp.495-515.
Trabelsi, Z., (2016) The robustness of microsoft windows and apple mac OS X against ARP
cache poisoning based network attacks. In 2016 13th IEEE Annual Consumer
Communications & Networking Conference (CCNC), 12(6), pp. 1074-1079.
Vassilakis, V.G., Alohali, B.A., Moscholios, I. and Logothetis, M.D., (2015) Mitigating
distributed denial-of-service attacks in named data networking. In Proceedings of the 11th
Advanced International Conference on Telecommunications (AICT), Brussels, Belgium, 12(6),
pp. 18-23.
Pacifici, V. and Dán, G., (2015) Distributed algorithms for content allocation in
interconnected content distribution networks. In 2015 IEEE Conference on Computer
Communications (INFOCOM), 12(6), pp. 2362-2370.
Sun, G., Chang, V., Yang, G. and Liao, D., (2018) The cost-efficient deployment of replica
servers in virtual content distribution networks for data fusion. Information
Sciences, 432(6), pp.495-515.
Trabelsi, Z., (2016) The robustness of microsoft windows and apple mac OS X against ARP
cache poisoning based network attacks. In 2016 13th IEEE Annual Consumer
Communications & Networking Conference (CCNC), 12(6), pp. 1074-1079.
Vassilakis, V.G., Alohali, B.A., Moscholios, I. and Logothetis, M.D., (2015) Mitigating
distributed denial-of-service attacks in named data networking. In Proceedings of the 11th
Advanced International Conference on Telecommunications (AICT), Brussels, Belgium, 12(6),
pp. 18-23.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





