Info 2411 - Information Security Policy for Gold Star Company Project
VerifiedAdded on 2022/08/27
|9
|2007
|18
Project
AI Summary
This assignment presents a comprehensive information security policy (ISP) developed for the Gold Star Company, a small to medium-sized enterprise specializing in software development and networking solutions. The ISP addresses the company's need to safeguard against both external and internal threats, moving beyond a generic acceptable use policy to define clear guidelines for employee conduct and data protection. The policy's scope encompasses all Gold Star employees, developers, consultants, and stakeholders who handle company information, covering the use of company-owned devices, networks, and equipment. The assignment details the objectives of the ISP, which include defining requirements for network access, reducing risks associated with unauthorized resource use, and mitigating potential damages such as data loss, intellectual property theft, and financial liabilities. It outlines relevant legislation like the Data Protection Act and Computer Misuse Act, as well as other related laws such as the Freedom of Information Act and Defamation Act. The assignment further elaborates on the application of the policy, acceptable use guidelines, password policies, privilege policies, and policies regarding computer software and hardware, internet use, email use, and network usage. It also includes a backup policy and an easy access matrix to clarify resource roles and responsibilities.

Running head: FOUNDATION OF COMPUTER SECURITY
FOUNDATION OF COMPUTER SECURITY
Name of the Student
Name of the University
Author Note
FOUNDATION OF COMPUTER SECURITY
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1FOUNDATION OF COMPUTER SECURITY
Discussions
The policy of information security is a sequence of regulations and rules those are enacted
by any organization in order to ensure that all the end users or the networks of the structure of
IT within the domain of the company abide by the prescriptions relating to the data security
digitally within the borders that the company maps its authority.
1. Scope
The scope of the policy of information security concerns to all the members of the Gold
Star Company and the others that handle the information of the company including the
employees, developers, consultants and the stakeholders of the company (Peltier, 2016). The
policy associates to the information those are managed or associated in the Gold Star
company whether is stored or processed utilising the facilities of the company including the
devices, computers, networks and the equipments owned by the company
2. Objectives
The purpose of this policy of information security is to define the requirements and the
rules in order to connect to the network of the Gold Star Company and systems from any
host. The regulations and rules are devised in order to reduce the exposure to employees,
developers, consultants, vendors and the other members of the Company as well as the
company itself from any kind of damages and that can result from the unauthorized
utilization of the resources of the Gold Star Company (Muller and Lind, 2020). The critical
damages consists of but they are not restricted to the loss of confidential or important data,
intellectual property, harm to the internal systems of the company and other liabilities those
are financial that could be acquired due to these damages.
Discussions
The policy of information security is a sequence of regulations and rules those are enacted
by any organization in order to ensure that all the end users or the networks of the structure of
IT within the domain of the company abide by the prescriptions relating to the data security
digitally within the borders that the company maps its authority.
1. Scope
The scope of the policy of information security concerns to all the members of the Gold
Star Company and the others that handle the information of the company including the
employees, developers, consultants and the stakeholders of the company (Peltier, 2016). The
policy associates to the information those are managed or associated in the Gold Star
company whether is stored or processed utilising the facilities of the company including the
devices, computers, networks and the equipments owned by the company
2. Objectives
The purpose of this policy of information security is to define the requirements and the
rules in order to connect to the network of the Gold Star Company and systems from any
host. The regulations and rules are devised in order to reduce the exposure to employees,
developers, consultants, vendors and the other members of the Company as well as the
company itself from any kind of damages and that can result from the unauthorized
utilization of the resources of the Gold Star Company (Muller and Lind, 2020). The critical
damages consists of but they are not restricted to the loss of confidential or important data,
intellectual property, harm to the internal systems of the company and other liabilities those
are financial that could be acquired due to these damages.

2FOUNDATION OF COMPUTER SECURITY
3. Legislation and Other Policy
The legislation that is associated to the policy of information security of the Gold Star
Company is the Data Protection Act and Computer Misuse Act.
The Data Protection is an act of United Kingdom that was passed in the year 1988. The
Act was devised to control the way various information of the customers is used by various
companies and the government (Manton, 2019). It safeguards people and puts down
regulations about the way the data of people can be utilised.
The eight principles of the Data Protection Act include:
Fair and lawful
Particular for its objectives
Be adequate and only for what is required
Accurate and up to date
Not kept longer than required
Take into account the right of people
Kept secure and safe
Not to be transmitted outside EEA
The Computer Misuse Act was devised in the year 1990. The Computer Misuse Act
safeguards the personal data that is held by companies from modification and unauthorized
admittance (Karagiannopoulos, 2016). This refers to accessing a system of computer without
permission and unauthorized access to systems of computer with the purpose in order to
execute a crime.
The three principles of Computer Misuse Act include:
Unauthorized admittance to computer material
3. Legislation and Other Policy
The legislation that is associated to the policy of information security of the Gold Star
Company is the Data Protection Act and Computer Misuse Act.
The Data Protection is an act of United Kingdom that was passed in the year 1988. The
Act was devised to control the way various information of the customers is used by various
companies and the government (Manton, 2019). It safeguards people and puts down
regulations about the way the data of people can be utilised.
The eight principles of the Data Protection Act include:
Fair and lawful
Particular for its objectives
Be adequate and only for what is required
Accurate and up to date
Not kept longer than required
Take into account the right of people
Kept secure and safe
Not to be transmitted outside EEA
The Computer Misuse Act was devised in the year 1990. The Computer Misuse Act
safeguards the personal data that is held by companies from modification and unauthorized
admittance (Karagiannopoulos, 2016). This refers to accessing a system of computer without
permission and unauthorized access to systems of computer with the purpose in order to
execute a crime.
The three principles of Computer Misuse Act include:
Unauthorized admittance to computer material
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3FOUNDATION OF COMPUTER SECURITY
Unauthorized admittance with the intention to execute or assist commission of offences
Acts those are unauthorized with the intention to impair or with some recklessness as to
impairing the operations of computer.
There are various types of legislation that can be associated to the information security
policy. These include Freedom of Information Act 2000, regulation of Investigatory Powers
Act 2000 and Defamation Act 1996 and many more laws.
The Freedom of Information Act 2000: The Freedom of Information Act 2000 is a general
right of public admittance to all kinds of information those are recorded held by authorities of
public to promote a culture of accountability and openness
Defamation Act 1996: Defamation is false allegation of an offence of words or action of
someone. The defamation laws exist to safeguard a person or reputation of an organization
from damage
Regulation of Investigatory Powers Act 2000: The Regulation of Investigatory Powers Act
2000 controls the powers of the bodies those are public in order to execute investigation and
surveillance. It envelops the interception and the utilisation of data of communication and can
appeal to in cases of security of nation for the aim of detection of crime and many more.
4. Application of the Policy
The director or the administration of the Gold Star Company must enforce the policy of
information security of the company. The employees of the Gold Star organization must
follow the policy of information security and should be enforced. The policy must be
followed in case of any data breach in company (Safa, Von Solms and Furnell, 2016). A data
breach takes place when there is a security breach that leads to loss of personal and sensitive
data. If the data breach tales place in the Gold Star organization holding the sensitive and the
personal data must notify the supervisory authority without any kind of delay.
Unauthorized admittance with the intention to execute or assist commission of offences
Acts those are unauthorized with the intention to impair or with some recklessness as to
impairing the operations of computer.
There are various types of legislation that can be associated to the information security
policy. These include Freedom of Information Act 2000, regulation of Investigatory Powers
Act 2000 and Defamation Act 1996 and many more laws.
The Freedom of Information Act 2000: The Freedom of Information Act 2000 is a general
right of public admittance to all kinds of information those are recorded held by authorities of
public to promote a culture of accountability and openness
Defamation Act 1996: Defamation is false allegation of an offence of words or action of
someone. The defamation laws exist to safeguard a person or reputation of an organization
from damage
Regulation of Investigatory Powers Act 2000: The Regulation of Investigatory Powers Act
2000 controls the powers of the bodies those are public in order to execute investigation and
surveillance. It envelops the interception and the utilisation of data of communication and can
appeal to in cases of security of nation for the aim of detection of crime and many more.
4. Application of the Policy
The director or the administration of the Gold Star Company must enforce the policy of
information security of the company. The employees of the Gold Star organization must
follow the policy of information security and should be enforced. The policy must be
followed in case of any data breach in company (Safa, Von Solms and Furnell, 2016). A data
breach takes place when there is a security breach that leads to loss of personal and sensitive
data. If the data breach tales place in the Gold Star organization holding the sensitive and the
personal data must notify the supervisory authority without any kind of delay.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4FOUNDATION OF COMPUTER SECURITY
5. Acceptable Use Policy
The Acceptable Use Policy of the Gold Star Company is as follows:
Every member of the company is given a ID and password that provides access to the
internet, email and the computer network of the company (Policy, 2020).
All admittance is denied unless it is granted by the information technology
The aces to the network of the company is a privilege and not a right and it must be
treated as such by the employees of the company
It is the responsibility of the employees of the company to protect the company against
any abuses of the network
The resources of computing of the company must not be utilised for any unlawful
activities
The employees of the company should not copy, modify or destroy nah data or software
belonging to the company
a. Password Policy
The employees should have different passwords for the online accounts’
Use of strong passwords using a combination of numbers and letters (Siponen,
Puhakainen and Vance, 2020).
The name of pet, school or any other should not be used that someone can guess the
password easily
The security questions on the accounts must be made something unique
b. Privileges Policy
The allocation of the privilege rights must be limited and controlled and not be offered by
default
Authorization for the utilisation of the resources should be provided explicitly and from a
written request from the manager of the company
5. Acceptable Use Policy
The Acceptable Use Policy of the Gold Star Company is as follows:
Every member of the company is given a ID and password that provides access to the
internet, email and the computer network of the company (Policy, 2020).
All admittance is denied unless it is granted by the information technology
The aces to the network of the company is a privilege and not a right and it must be
treated as such by the employees of the company
It is the responsibility of the employees of the company to protect the company against
any abuses of the network
The resources of computing of the company must not be utilised for any unlawful
activities
The employees of the company should not copy, modify or destroy nah data or software
belonging to the company
a. Password Policy
The employees should have different passwords for the online accounts’
Use of strong passwords using a combination of numbers and letters (Siponen,
Puhakainen and Vance, 2020).
The name of pet, school or any other should not be used that someone can guess the
password easily
The security questions on the accounts must be made something unique
b. Privileges Policy
The allocation of the privilege rights must be limited and controlled and not be offered by
default
Authorization for the utilisation of the resources should be provided explicitly and from a
written request from the manager of the company

5FOUNDATION OF COMPUTER SECURITY
The technical teams of the company should safeguard against issuing the rights of
privilege in order to prevent loss off integrity or confidentiality
The privilege to the employees of the company will be provided by the senior manager of
the company
c. Computer Software Policies
The company must take by the terms of the Software license agreement
Must be conscious that all the software is confined by a copyright (Chen et al.,2019)
Must not duplicate or copy software for any objective outside those permitted in that
specific licence agreement of software
Must not accept software those are not licensed from any third party
Must not install illegal copies of the software in the computer system operated by the
company
d. Computer Hardware Policies
All the devices of hardware those are purchased on behalf of the company shall be
deemed as the property of company (Otterness et al.,2017).
The current standards of hardware are available in the standards document of hardware.
Any change from these standards must be approved before the purchase
All the computer must be replaced on a cycle of four years
No outside devices should be plugged in the network of the company
All the hardwares and the equipments of the company are a responsibility of the
employees and they are responsible for maintaining and any kind of damage of the
equipments
e. Internet Use Policy
The access of the internet is for job-related activities and should be used for personal use
The technical teams of the company should safeguard against issuing the rights of
privilege in order to prevent loss off integrity or confidentiality
The privilege to the employees of the company will be provided by the senior manager of
the company
c. Computer Software Policies
The company must take by the terms of the Software license agreement
Must be conscious that all the software is confined by a copyright (Chen et al.,2019)
Must not duplicate or copy software for any objective outside those permitted in that
specific licence agreement of software
Must not accept software those are not licensed from any third party
Must not install illegal copies of the software in the computer system operated by the
company
d. Computer Hardware Policies
All the devices of hardware those are purchased on behalf of the company shall be
deemed as the property of company (Otterness et al.,2017).
The current standards of hardware are available in the standards document of hardware.
Any change from these standards must be approved before the purchase
All the computer must be replaced on a cycle of four years
No outside devices should be plugged in the network of the company
All the hardwares and the equipments of the company are a responsibility of the
employees and they are responsible for maintaining and any kind of damage of the
equipments
e. Internet Use Policy
The access of the internet is for job-related activities and should be used for personal use
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6FOUNDATION OF COMPUTER SECURITY
The employees may not utilise the internet to send, receive or store any kind of unlawful
content
The employees of the company are prohibited from downloading any kind of software
using the internet of the company without the permission from the IT department
The employees are prohibited to play any internet games or watch online videos using the
internet of the company
The internet usage and the access of the employees should be monitored by the company
and take strict action if any unlawful activities are seen
f. Email Use Policy
The employees should use email systems of the company for business
The company must limit personal use of email
The company must set out when email should not and should not be used
The company must set out what devices the employees may use in order to send or
receive emails
g. Network Use Policy
The company must provide an ID and password for each employee in order to access the
company’s network.
The employees are prohibited to modify or install any kind of devices in the network
The employees should not install mail servers without the permission of the IT
department
The employees must access the network in an authorized manner
h. Backup Policy
The employees must backup important data and information from their systems
The backups must be kept in a pen drive or a external hard drive
The backup of the information and data must be done every 1 week
The employees may not utilise the internet to send, receive or store any kind of unlawful
content
The employees of the company are prohibited from downloading any kind of software
using the internet of the company without the permission from the IT department
The employees are prohibited to play any internet games or watch online videos using the
internet of the company
The internet usage and the access of the employees should be monitored by the company
and take strict action if any unlawful activities are seen
f. Email Use Policy
The employees should use email systems of the company for business
The company must limit personal use of email
The company must set out when email should not and should not be used
The company must set out what devices the employees may use in order to send or
receive emails
g. Network Use Policy
The company must provide an ID and password for each employee in order to access the
company’s network.
The employees are prohibited to modify or install any kind of devices in the network
The employees should not install mail servers without the permission of the IT
department
The employees must access the network in an authorized manner
h. Backup Policy
The employees must backup important data and information from their systems
The backups must be kept in a pen drive or a external hard drive
The backup of the information and data must be done every 1 week
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7FOUNDATION OF COMPUTER SECURITY
It is the responsibility of the employees to see that the backup of the sensitive data and
information is done properly
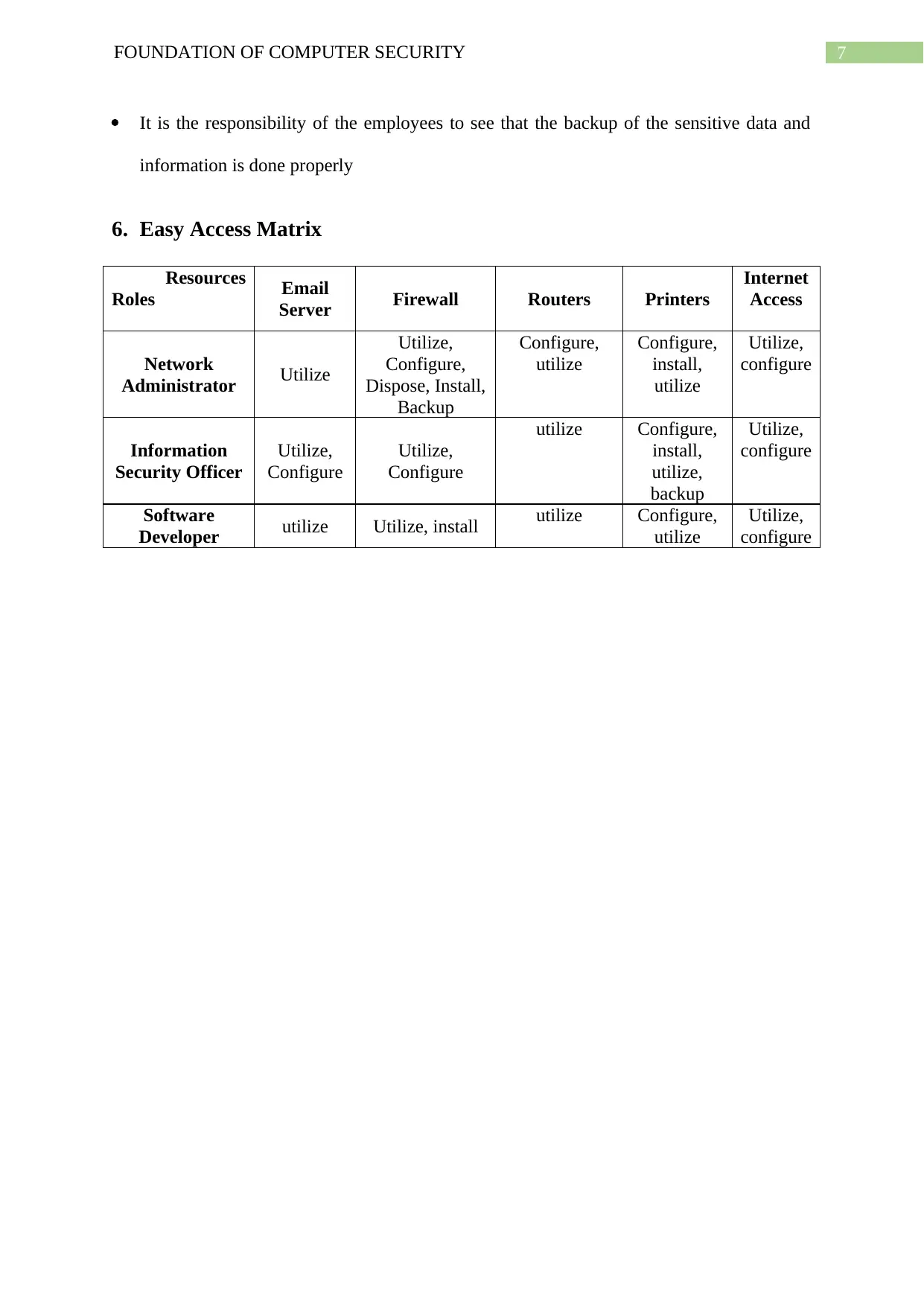
6. Easy Access Matrix
Resources
Roles Email
Server Firewall Routers Printers
Internet
Access
Network
Administrator Utilize
Utilize,
Configure,
Dispose, Install,
Backup
Configure,
utilize
Configure,
install,
utilize
Utilize,
configure
Information
Security Officer
Utilize,
Configure
Utilize,
Configure
utilize Configure,
install,
utilize,
backup
Utilize,
configure
Software
Developer utilize Utilize, install utilize Configure,
utilize
Utilize,
configure
It is the responsibility of the employees to see that the backup of the sensitive data and
information is done properly
6. Easy Access Matrix
Resources
Roles Email
Server Firewall Routers Printers
Internet
Access
Network
Administrator Utilize
Utilize,
Configure,
Dispose, Install,
Backup
Configure,
utilize
Configure,
install,
utilize
Utilize,
configure
Information
Security Officer
Utilize,
Configure
Utilize,
Configure
utilize Configure,
install,
utilize,
backup
Utilize,
configure
Software
Developer utilize Utilize, install utilize Configure,
utilize
Utilize,
configure

8FOUNDATION OF COMPUTER SECURITY
References
Chen, K., Deng, Q., Hou, Y., Jin, Y. and Guo, X., 2019, December. Hardware and Software
Co-Verification from Security Perspective. In 2019 20th International Workshop on
Microprocessor/SoC Test, Security and Verification (MTV) (pp. 50-55). IEEE.
Karagiannopoulos, V., 2016. Insider unauthorised use of authorised access: What are the
alternatives to the Computer Misuse Act 1990?. International Journal of Law, Crime
and Justice, 47, pp.85-96.
Manton, K., 2019. The 1984 Data Protection Act. In Population Registers and Privacy in
Britain, 1936—1984 (pp. 193-216). Palgrave Macmillan, Cham.
Muller, S.R. and Lind, M.L., 2020. Factors in Information Assurance Professionals'
Intentions to Adhere to Information Security Policies. International Journal of
Systems and Software Security and Protection (IJSSSP), 11(1), pp.17-32.
Otterness, N., Yang, M., Amert, T., Anderson, J. and Smith, F.D., 2017. Inferring the
scheduling policies of an embedded CUDA GPU. OSPERT’17.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Policy, A.U., 2020. Acceptable Use Policy.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance
model in organizations. computers & security, 56, pp.70-82.
Siponen, M., Puhakainen, P. and Vance, A., 2020. Can individuals’ neutralization techniques
be overcome? A field experiment on password policy. Computers & Security, 88,
p.101617.
References
Chen, K., Deng, Q., Hou, Y., Jin, Y. and Guo, X., 2019, December. Hardware and Software
Co-Verification from Security Perspective. In 2019 20th International Workshop on
Microprocessor/SoC Test, Security and Verification (MTV) (pp. 50-55). IEEE.
Karagiannopoulos, V., 2016. Insider unauthorised use of authorised access: What are the
alternatives to the Computer Misuse Act 1990?. International Journal of Law, Crime
and Justice, 47, pp.85-96.
Manton, K., 2019. The 1984 Data Protection Act. In Population Registers and Privacy in
Britain, 1936—1984 (pp. 193-216). Palgrave Macmillan, Cham.
Muller, S.R. and Lind, M.L., 2020. Factors in Information Assurance Professionals'
Intentions to Adhere to Information Security Policies. International Journal of
Systems and Software Security and Protection (IJSSSP), 11(1), pp.17-32.
Otterness, N., Yang, M., Amert, T., Anderson, J. and Smith, F.D., 2017. Inferring the
scheduling policies of an embedded CUDA GPU. OSPERT’17.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Policy, A.U., 2020. Acceptable Use Policy.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance
model in organizations. computers & security, 56, pp.70-82.
Siponen, M., Puhakainen, P. and Vance, A., 2020. Can individuals’ neutralization techniques
be overcome? A field experiment on password policy. Computers & Security, 88,
p.101617.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





