Computer Security System Investigation Project: VM Image Analysis
VerifiedAdded on 2022/12/15
|18
|3850
|114
Project
AI Summary
This project focuses on computer security, specifically investigating the vulnerabilities of a Virtual Machine (VM) image. The project begins with the installation of the VM, using VMware and Ubuntu. It then delves into the process of inspecting the security system, including the use of Kali Linux to identify and exploit potential weaknesses like cracking passwords. The project explores various security threats, such as network service issues, malware, and password vulnerabilities. It emphasizes the importance of system hardening, strong passwords, and encryption to mitigate risks. The investigation utilizes tools like Lynis for security audits and discusses key management (public and private keys) and disk encryption. The project concludes with suggestions for enhancing the security of the VM image and associated systems, providing a comprehensive analysis of security practices and potential improvements.

University
Semester
COMPUTER SECURITY-SYSTEM
INVESTIGATION
Student ID
Student Name
Submission Date
1
Semester
COMPUTER SECURITY-SYSTEM
INVESTIGATION
Student ID
Student Name
Submission Date
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Project Goal...................................................................................................................................3
2. Virtual Machine (VM) Image File Installation Procedure.............................................................3
3. Inspection of the Security System..................................................................................................7
4. Inspection Report and Details of the Security System.................................................................15
5. Additional Security System Suggestions.....................................................................................17
References...........................................................................................................................................20
2
1. Project Goal...................................................................................................................................3
2. Virtual Machine (VM) Image File Installation Procedure.............................................................3
3. Inspection of the Security System..................................................................................................7
4. Inspection Report and Details of the Security System.................................................................15
5. Additional Security System Suggestions.....................................................................................17
References...........................................................................................................................................20
2

Project Goal
Hacking! Security! Safety! Threat! Malware! These are few words that every user and
every operator is scared of. In today’s world of High end Systems and tons of Data/
Information movie around, it becomes apparent to all that Security is a prime concern. Our
project addresses this major issue and tries tis best to solve it. Our project will study, analyze
and understand the problems related to Security and Threats to a System. Our main
participant in this project is a Virtual Machine (VM). A VM is an operating system (OS) or
application environment that is installed on software, which imitates dedicated hardware and
gives the end user, the same experience on a virtual machine as they would have on a
dedicated hardware. VM image is provided by a computer Firm, “Widgets Inc” to another
firm called “Benny Vandergast Inc” for testing out as same will be used in their new web
based store. By using VMware, Benny Vandergast will use them on the VM’s and ask the
users to evaluate it Security Features. So, in this project, those users are we. Here is where,
we start our work on this Project from. We shall understand the whole Security status of the
VM images provided by Benny Vandergast, inspect them, run tests on them, analyze , locate
the weak security areas and finally prepare a thorough report on all the findings and short
comings. We shall be using “Special Security Tools” (Iron Wasp, Grabber, etc) to
understand and study this project and the security concerns related to it. We shall be testing
the “Virtual Machine Image” files for security threats and attacks and these shall be based on
the following criteria,
Process and Plan for Inspection of the security system.
Various Tools/ Methods to be used for the security system investigation.
Result and Outcome once the investigation is completed.
Analyzing possible outside threats and safe guarding against them.
Additional measures related to security problems.
Thus, now we shall explain and understand all the above points and how it will be
used in our Project related to the Security of VM image files and associated system.
Task 2 - Virtual Machine (VM) Image File Installation Procedure
We shall now install the “Virtual Machine work station” on our system (Ali, 2014).
3
Hacking! Security! Safety! Threat! Malware! These are few words that every user and
every operator is scared of. In today’s world of High end Systems and tons of Data/
Information movie around, it becomes apparent to all that Security is a prime concern. Our
project addresses this major issue and tries tis best to solve it. Our project will study, analyze
and understand the problems related to Security and Threats to a System. Our main
participant in this project is a Virtual Machine (VM). A VM is an operating system (OS) or
application environment that is installed on software, which imitates dedicated hardware and
gives the end user, the same experience on a virtual machine as they would have on a
dedicated hardware. VM image is provided by a computer Firm, “Widgets Inc” to another
firm called “Benny Vandergast Inc” for testing out as same will be used in their new web
based store. By using VMware, Benny Vandergast will use them on the VM’s and ask the
users to evaluate it Security Features. So, in this project, those users are we. Here is where,
we start our work on this Project from. We shall understand the whole Security status of the
VM images provided by Benny Vandergast, inspect them, run tests on them, analyze , locate
the weak security areas and finally prepare a thorough report on all the findings and short
comings. We shall be using “Special Security Tools” (Iron Wasp, Grabber, etc) to
understand and study this project and the security concerns related to it. We shall be testing
the “Virtual Machine Image” files for security threats and attacks and these shall be based on
the following criteria,
Process and Plan for Inspection of the security system.
Various Tools/ Methods to be used for the security system investigation.
Result and Outcome once the investigation is completed.
Analyzing possible outside threats and safe guarding against them.
Additional measures related to security problems.
Thus, now we shall explain and understand all the above points and how it will be
used in our Project related to the Security of VM image files and associated system.
Task 2 - Virtual Machine (VM) Image File Installation Procedure
We shall now install the “Virtual Machine work station” on our system (Ali, 2014).
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Select the Portal where the VM file has to be downloaded
When the process of downloading has been completed, after that install the VM work
station.
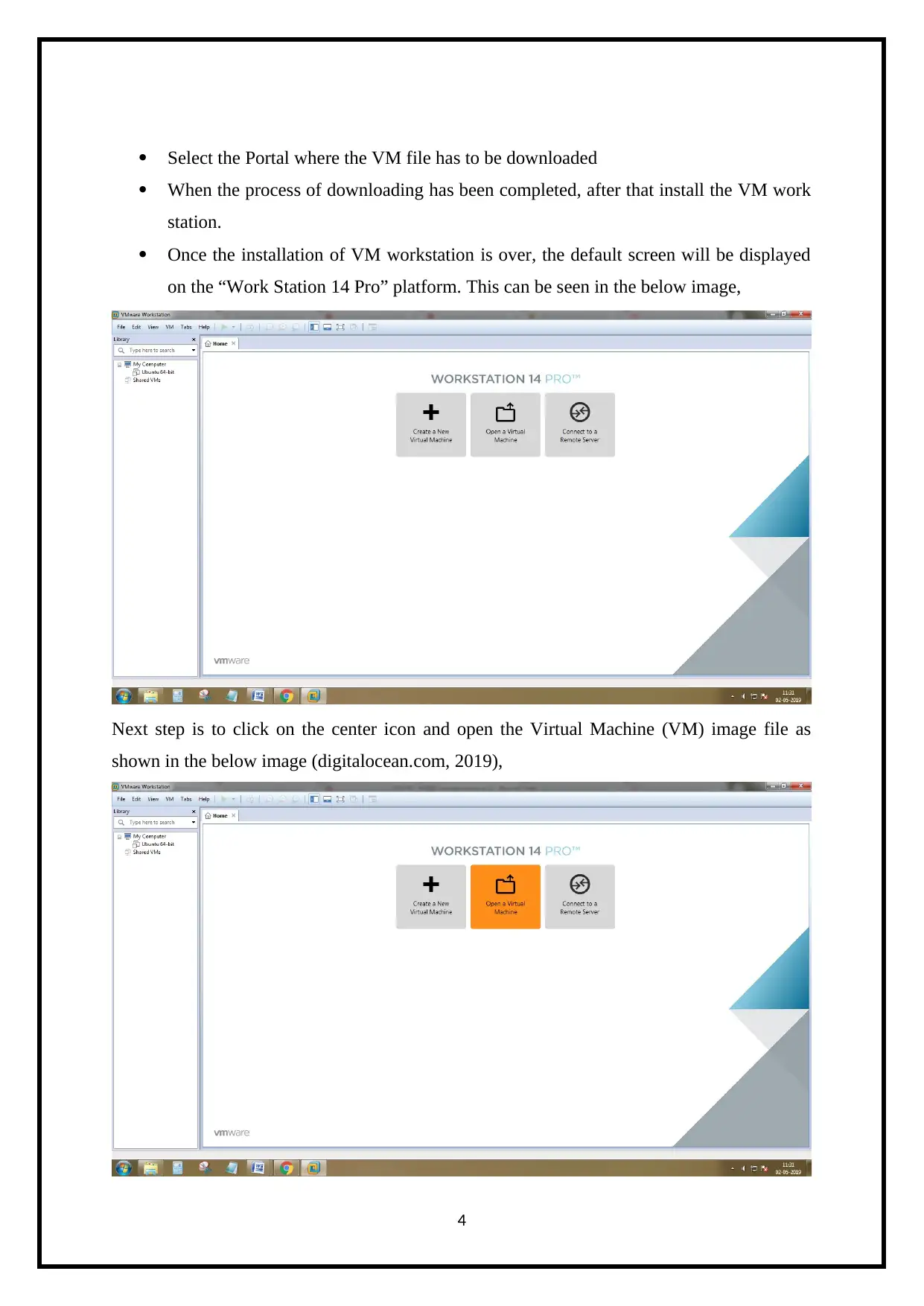
Once the installation of VM workstation is over, the default screen will be displayed
on the “Work Station 14 Pro” platform. This can be seen in the below image,
Next step is to click on the center icon and open the Virtual Machine (VM) image file as
shown in the below image (digitalocean.com, 2019),
4
When the process of downloading has been completed, after that install the VM work
station.
Once the installation of VM workstation is over, the default screen will be displayed
on the “Work Station 14 Pro” platform. This can be seen in the below image,
Next step is to click on the center icon and open the Virtual Machine (VM) image file as
shown in the below image (digitalocean.com, 2019),
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
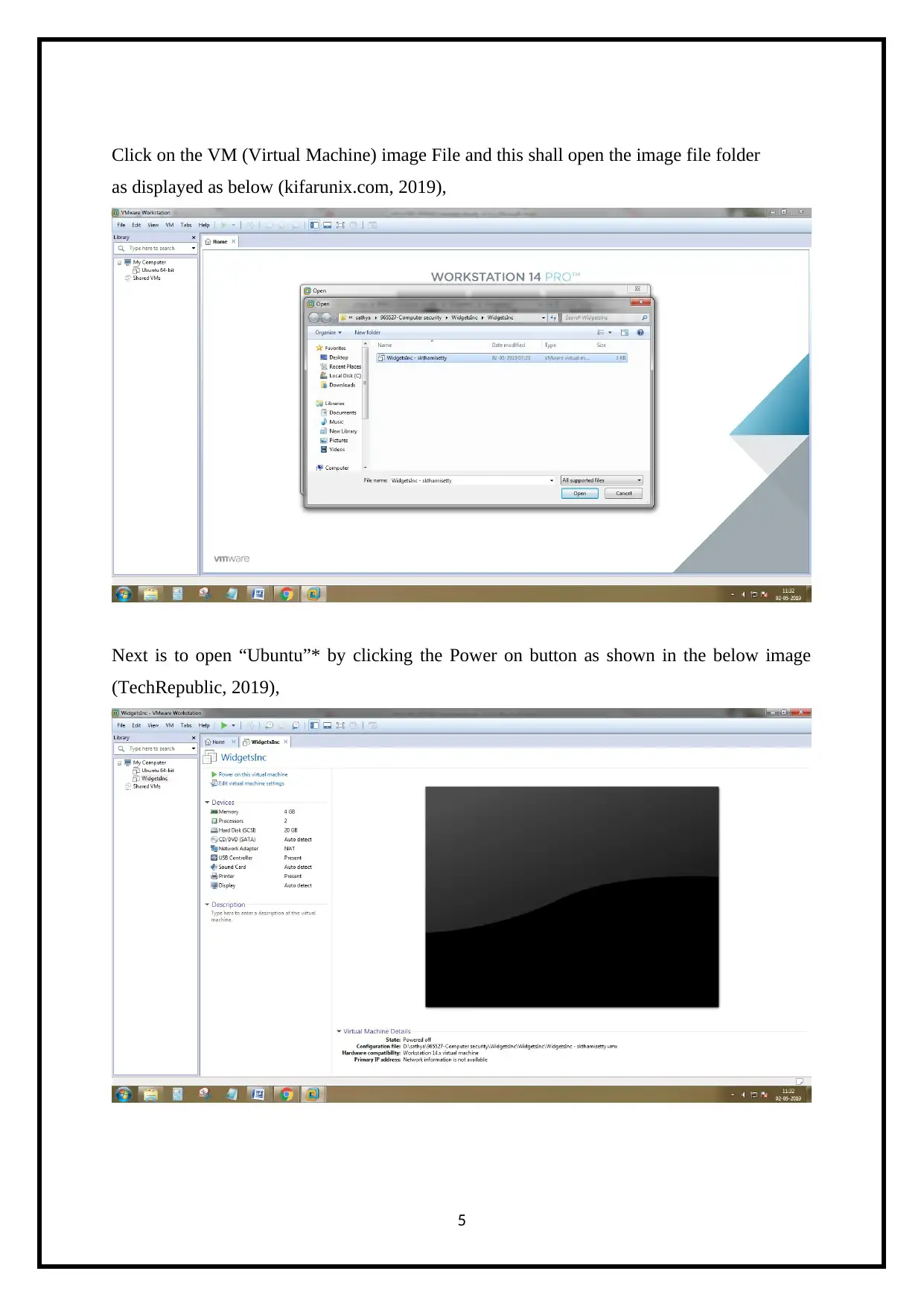
Click on the VM (Virtual Machine) image File and this shall open the image file folder
as displayed as below (kifarunix.com, 2019),
Next is to open “Ubuntu”* by clicking the Power on button as shown in the below image
(TechRepublic, 2019),
5
as displayed as below (kifarunix.com, 2019),
Next is to open “Ubuntu”* by clicking the Power on button as shown in the below image
(TechRepublic, 2019),
5
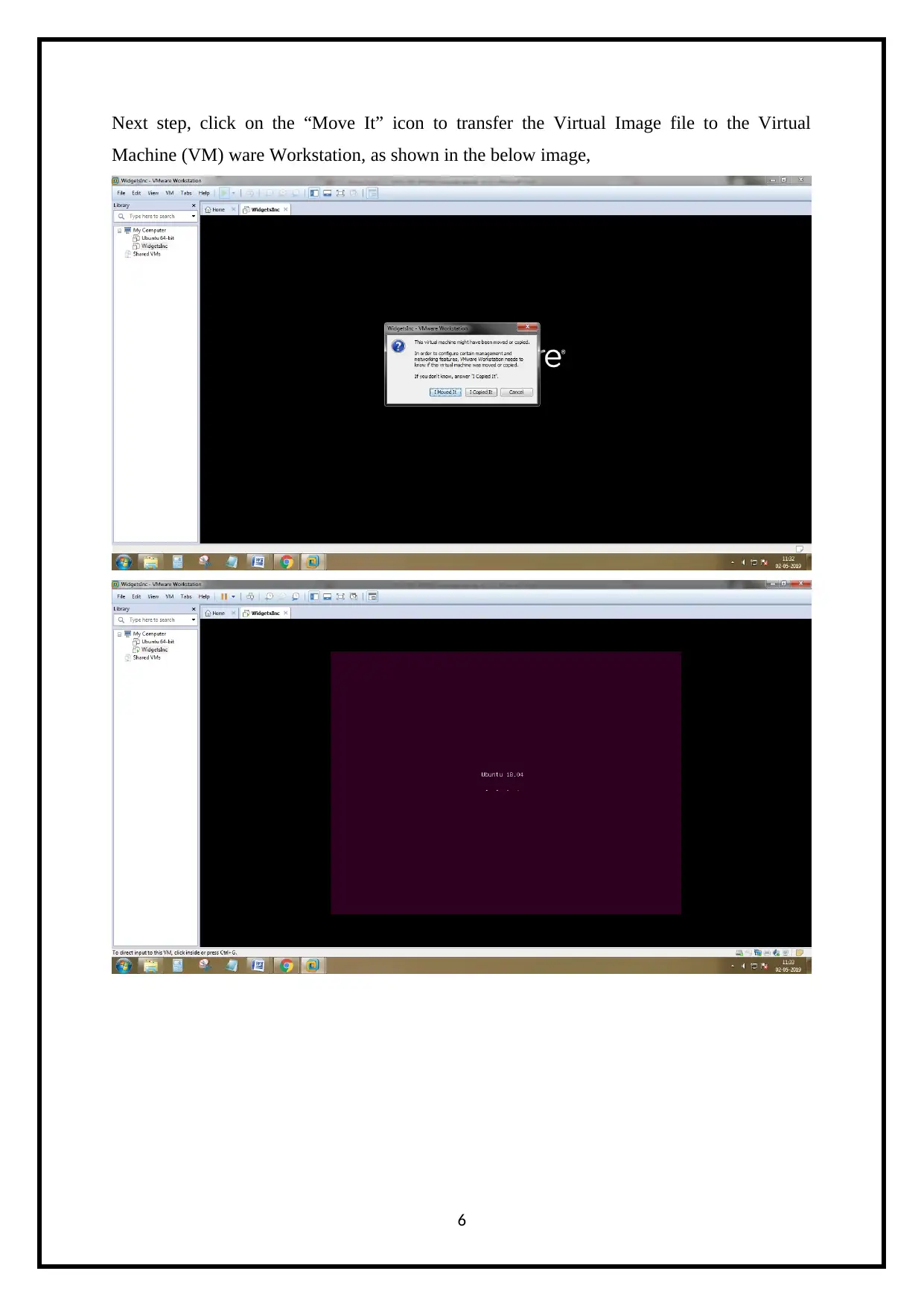
Next step, click on the “Move It” icon to transfer the Virtual Image file to the Virtual
Machine (VM) ware Workstation, as shown in the below image,
6
Machine (VM) ware Workstation, as shown in the below image,
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
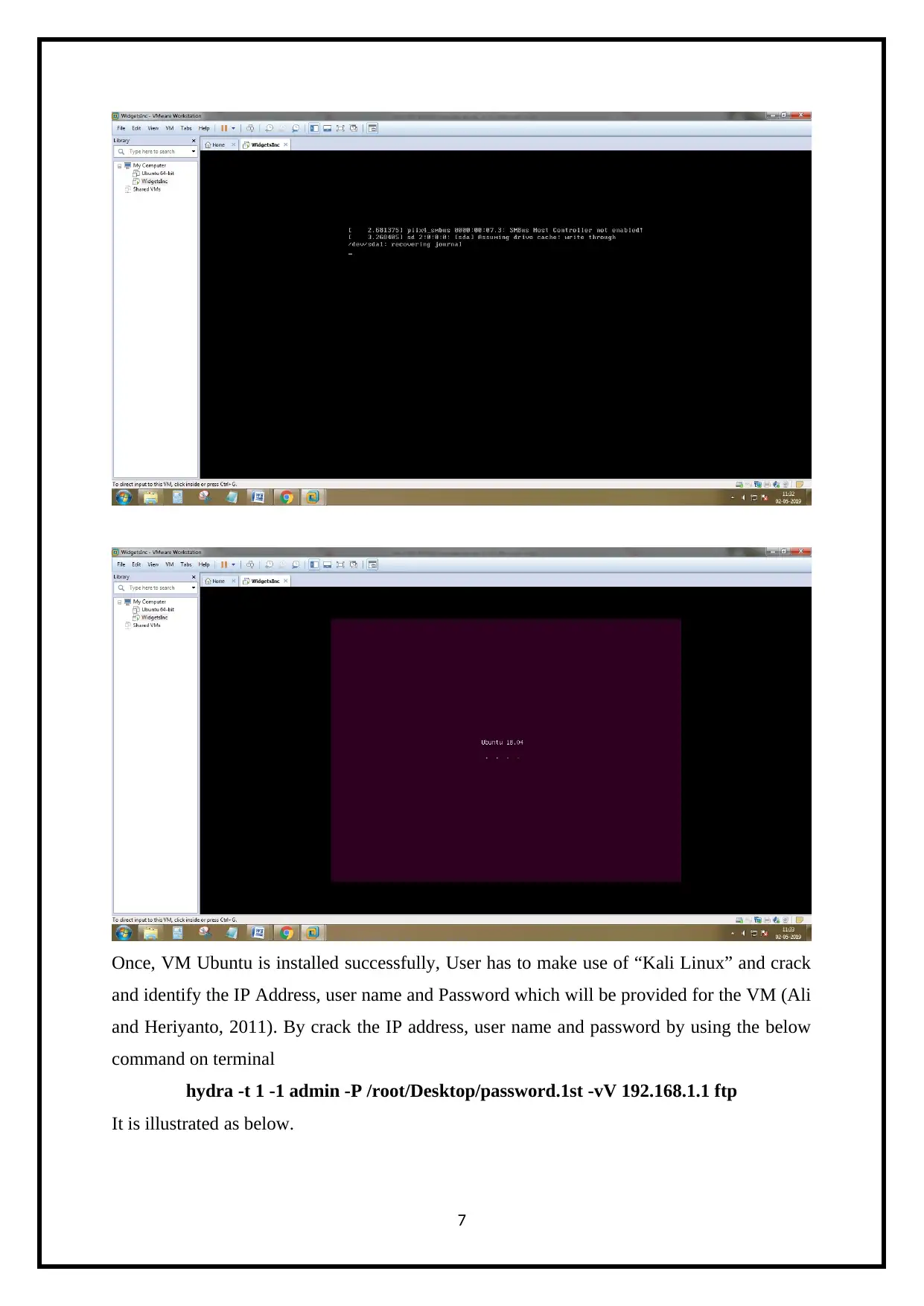
Once, VM Ubuntu is installed successfully, User has to make use of “Kali Linux” and crack
and identify the IP Address, user name and Password which will be provided for the VM (Ali
and Heriyanto, 2011). By crack the IP address, user name and password by using the below
command on terminal
hydra -t 1 -1 admin -P /root/Desktop/password.1st -vV 192.168.1.1 ftp
It is illustrated as below.
7
and identify the IP Address, user name and Password which will be provided for the VM (Ali
and Heriyanto, 2011). By crack the IP address, user name and password by using the below
command on terminal
hydra -t 1 -1 admin -P /root/Desktop/password.1st -vV 192.168.1.1 ftp
It is illustrated as below.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

After, enter the user name as admin and password as password. The user name and
password is hacked because this project is to hack the credentials of Virtual Machine. After,
enter the Ubuntu VM to do the credentials of Virtual Machine by use the below steps
(Bosworth, Kabay and Whyne, n.d.),
1. Boot into the recovery mode
2. Drop to root shell prompt
3. Using the write access prompt, remount the root.
4. Reset the username and password
5. On entering the new password you will be see the “Authentication manipulation
error” as shown below,
passwd username
Enter new UNIX password:
Retype new UNIX password:
passwd: Authentication token manipulation error
passwd: password unchanged
This error is given as the File was only Read access. Thus we have the option of changing /
remounting the File System on the platform. Reset the user name/ password to complete the
procedure. Now the Ubuntu VM in our project faces certain types of Security threats and
problems like (Buchanan, 2014),
Issues related to Network Services.
Backup problems in the system
8
password is hacked because this project is to hack the credentials of Virtual Machine. After,
enter the Ubuntu VM to do the credentials of Virtual Machine by use the below steps
(Bosworth, Kabay and Whyne, n.d.),
1. Boot into the recovery mode
2. Drop to root shell prompt
3. Using the write access prompt, remount the root.
4. Reset the username and password
5. On entering the new password you will be see the “Authentication manipulation
error” as shown below,
passwd username
Enter new UNIX password:
Retype new UNIX password:
passwd: Authentication token manipulation error
passwd: password unchanged
This error is given as the File was only Read access. Thus we have the option of changing /
remounting the File System on the platform. Reset the user name/ password to complete the
procedure. Now the Ubuntu VM in our project faces certain types of Security threats and
problems like (Buchanan, 2014),
Issues related to Network Services.
Backup problems in the system
8

Issues related to Open SSL
Malware/ Virus / Bugs threats
Setting up/ updating of Passwords in the system
Security Patches
Hardening issues for Web Server
Encrypted Data and problems faced during communication.
Task 3 – Investigation on System Security
The Security system inspection and investigation has to be carried out on the Virtual
Machine image File. This has to be a well-planned procedure which follows all the protocols
required (Eliot, 2016). System security policies and procedure are high-level statements or
rules for the concerned systems. Thus they have to be taken seriously as the stakes of Threats
and damages to the system are high. Security of the VM image Files is challenging as the
security certificate so obtained will be checked for standards related to security, legitimacy
and authenticity of the files as confirmed. We shall be using Ubuntu 18.04 as our Virtual
Machine (VM) Image file and all the test procedures will be carried out on this. There will
be a continuous monitoring process as the Tests/ Inspections are going on the system. The aid
of a pre-defined checklist related to security procedures will be used as a reference point.
This will keep updating about the necessary modifications and changes required for updating
the security standards. One of the most common and highly effective tools for security and
safety of data is using “Encryption” (Gollmann, 2011). This technology is used to enables the
files to be encrypted transparently which are used to protect the data confidentiality from the
attackers with physical access to the system. While carrying out the Security inspection, the
Operating system and its operation on the platform will also be checked. Basically, the data
encryption is used to protect the digital confidentiality of the data which is stored on the
computer system and transmitted by using the computer networks or internet connectivity.
Protection will be at different levels which will include connected devices; software’s
working on the platform, storage devices, disks in use etc. One of the most neglected but
important task is to always keep the system/ Files updated. Timely and scheduled updates
help to keep the system at the latest version and thus minimize the threats of possible attacks
(Halton and Weaver, 2016). The hardening is used to secures the system with basic security
procedure by reducing the system surface vulnerability and it is larger process when the
system performs various functions but, if system use single function which is sued to provide
9
Malware/ Virus / Bugs threats
Setting up/ updating of Passwords in the system
Security Patches
Hardening issues for Web Server
Encrypted Data and problems faced during communication.
Task 3 – Investigation on System Security
The Security system inspection and investigation has to be carried out on the Virtual
Machine image File. This has to be a well-planned procedure which follows all the protocols
required (Eliot, 2016). System security policies and procedure are high-level statements or
rules for the concerned systems. Thus they have to be taken seriously as the stakes of Threats
and damages to the system are high. Security of the VM image Files is challenging as the
security certificate so obtained will be checked for standards related to security, legitimacy
and authenticity of the files as confirmed. We shall be using Ubuntu 18.04 as our Virtual
Machine (VM) Image file and all the test procedures will be carried out on this. There will
be a continuous monitoring process as the Tests/ Inspections are going on the system. The aid
of a pre-defined checklist related to security procedures will be used as a reference point.
This will keep updating about the necessary modifications and changes required for updating
the security standards. One of the most common and highly effective tools for security and
safety of data is using “Encryption” (Gollmann, 2011). This technology is used to enables the
files to be encrypted transparently which are used to protect the data confidentiality from the
attackers with physical access to the system. While carrying out the Security inspection, the
Operating system and its operation on the platform will also be checked. Basically, the data
encryption is used to protect the digital confidentiality of the data which is stored on the
computer system and transmitted by using the computer networks or internet connectivity.
Protection will be at different levels which will include connected devices; software’s
working on the platform, storage devices, disks in use etc. One of the most neglected but
important task is to always keep the system/ Files updated. Timely and scheduled updates
help to keep the system at the latest version and thus minimize the threats of possible attacks
(Halton and Weaver, 2016). The hardening is used to secures the system with basic security
procedure by reducing the system surface vulnerability and it is larger process when the
system performs various functions but, if system use single function which is sued to provide
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the more secure than a multipurpose one. Hardening has to be performed both, during and
after the System installation process. Although Linux users are must less prone to viruses
than some other major operating systems, there are still many security issues facing Linux
users and administrators. Linux as such requires passwords to access root files and also for
software installation/ updates. Ubuntu and Linux are very safe software’s and they support
Unified Extensible Firmware Interface (UEFI) Secure Boot. Understanding the Safety,
Security, Functionality and Performance of the system and maintaining a balance is very
important. With Securing a System the above factors are also important. This also is an
important point considered in our Project.
System Hardening
Hardening can be best and optimally used when the “Linux” programing software is
being installed and same process has to be repeated when the installation is completed. Weak
Sectors, Soft targets, vulnerable portions etc will be the first to be identified and security
corrections applied to them. Securing the Access and Authentication helps considerably in
reducing the threat on the system (Halton et al., 2017).
Use strong passwords
After the entire process of Hardening of the Linux System is completed, the next
important and vital step will be the Password. This forms the primary Security cover for the
system. A user account thus created after hardening should thus be allocated a very strong
Password. It should be unique and a combination so that it becomes impossible to be cracked
by any hacker. If the user account is being on a group or a common platform, more reason to
have a secured strong password.
Open SSH security and Hardening
Linux systems have been using this tool for a long time. For reducing considerably
threats and attacks on the system, proceed to carry out Hardening process on the system.
Carry out configuration test on SSH before deploying it on the system. Check how it is
working on the platform and a well-planned approach helps in quickly and effectively finish
the procedure (Henry, 2012). Encrypting is a very powerful tool and widely used everywhere.
It gives the edge in security on all the platforms where it is deployed and eliminates potential
threats. Identifying the Functioning and Non-functioning areas of the system will aid in
removing unwanted sectors from the system.
SSH port forwarding is a mechanism in SSH for tunneling application ports from
the client machine to the server machine, or vice versa. This function can be used for added
10
after the System installation process. Although Linux users are must less prone to viruses
than some other major operating systems, there are still many security issues facing Linux
users and administrators. Linux as such requires passwords to access root files and also for
software installation/ updates. Ubuntu and Linux are very safe software’s and they support
Unified Extensible Firmware Interface (UEFI) Secure Boot. Understanding the Safety,
Security, Functionality and Performance of the system and maintaining a balance is very
important. With Securing a System the above factors are also important. This also is an
important point considered in our Project.
System Hardening
Hardening can be best and optimally used when the “Linux” programing software is
being installed and same process has to be repeated when the installation is completed. Weak
Sectors, Soft targets, vulnerable portions etc will be the first to be identified and security
corrections applied to them. Securing the Access and Authentication helps considerably in
reducing the threat on the system (Halton et al., 2017).
Use strong passwords
After the entire process of Hardening of the Linux System is completed, the next
important and vital step will be the Password. This forms the primary Security cover for the
system. A user account thus created after hardening should thus be allocated a very strong
Password. It should be unique and a combination so that it becomes impossible to be cracked
by any hacker. If the user account is being on a group or a common platform, more reason to
have a secured strong password.
Open SSH security and Hardening
Linux systems have been using this tool for a long time. For reducing considerably
threats and attacks on the system, proceed to carry out Hardening process on the system.
Carry out configuration test on SSH before deploying it on the system. Check how it is
working on the platform and a well-planned approach helps in quickly and effectively finish
the procedure (Henry, 2012). Encrypting is a very powerful tool and widely used everywhere.
It gives the edge in security on all the platforms where it is deployed and eliminates potential
threats. Identifying the Functioning and Non-functioning areas of the system will aid in
removing unwanted sectors from the system.
SSH port forwarding is a mechanism in SSH for tunneling application ports from
the client machine to the server machine, or vice versa. This function can be used for added
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

security covering. It creates an encrypted connection between the different sectors of the
platform, through which it relays the traffic. SSH can be used in Server authentication. By
fine tuning and few modifications, it can become a very strong secured Ubuntu platform
(Lehtinen and Sr, 2011).
As we had discussed in the previous topics, Hardening of Ubuntu system goes a long
way in securing the system. Planned updates and progressive planning for keeping the entire
system up-to-date to the latest version will be the right direction to the security of the System.
The Audit tool of Lynis is a very supportive to identify the security deficiencies in the system
and it passes all this data to the Security center. User can access this report and get an overall
picture of the security status of the system.
Ubuntu Software Center is a utility for installing, purchasing, and removing software
in Ubuntu. This can be used for installing the Lynis Software for Security Audits. Key used
by the Administrator, is one of the primary ways to keep the system safe. Now there are 2
type os keys that are used for safety of the system/ software. Public key and Private key. The
Private Key is accessed by a select few while the public key is configured for the system.
Never mix up the keys or misplace them, as in the wrong hands they will create lot of
problems. The users who manage central system, or running Linux (or UNIX based system)
may utilize ssh-keygen. If you wish to help the new versions of the OS, it is recommended to
utilize the new key format Ed25519. If not, the key called as RSA can be used.
Use disk encryption
The encryption of disk is a technology which is used to protects the information by
converting it into the unreadable format which cannot be dicephered easily by authorised
people. So, use the encryption hardware or software to encrypt the bit of data on the computer
system. Understanding the dynamics of Threats and Attacks gives us a better understanding
of the systems vulnerabilities. Now at start up, Ubuntu cannot be accessed with a Decryption
key. It is coded key which only the admin and a few can be accessed. Hence it helps to
protect the data cause even if someone is able to enter the stored files/ data location; it won’t
be possible to access the information without the decryption key.
Automatic Security Updates
Every software release up-dates and patches for their software’s. Keeping this in
mind, user should keep their software’s relevant by keeping the updating it on regular basis.
Linux like other OS keeps sending up-dates and same has to be implicated in the system.
Ubuntu too has its share of updates and same can be used in the system. Now to avoid
11
platform, through which it relays the traffic. SSH can be used in Server authentication. By
fine tuning and few modifications, it can become a very strong secured Ubuntu platform
(Lehtinen and Sr, 2011).
As we had discussed in the previous topics, Hardening of Ubuntu system goes a long
way in securing the system. Planned updates and progressive planning for keeping the entire
system up-to-date to the latest version will be the right direction to the security of the System.
The Audit tool of Lynis is a very supportive to identify the security deficiencies in the system
and it passes all this data to the Security center. User can access this report and get an overall
picture of the security status of the system.
Ubuntu Software Center is a utility for installing, purchasing, and removing software
in Ubuntu. This can be used for installing the Lynis Software for Security Audits. Key used
by the Administrator, is one of the primary ways to keep the system safe. Now there are 2
type os keys that are used for safety of the system/ software. Public key and Private key. The
Private Key is accessed by a select few while the public key is configured for the system.
Never mix up the keys or misplace them, as in the wrong hands they will create lot of
problems. The users who manage central system, or running Linux (or UNIX based system)
may utilize ssh-keygen. If you wish to help the new versions of the OS, it is recommended to
utilize the new key format Ed25519. If not, the key called as RSA can be used.
Use disk encryption
The encryption of disk is a technology which is used to protects the information by
converting it into the unreadable format which cannot be dicephered easily by authorised
people. So, use the encryption hardware or software to encrypt the bit of data on the computer
system. Understanding the dynamics of Threats and Attacks gives us a better understanding
of the systems vulnerabilities. Now at start up, Ubuntu cannot be accessed with a Decryption
key. It is coded key which only the admin and a few can be accessed. Hence it helps to
protect the data cause even if someone is able to enter the stored files/ data location; it won’t
be possible to access the information without the decryption key.
Automatic Security Updates
Every software release up-dates and patches for their software’s. Keeping this in
mind, user should keep their software’s relevant by keeping the updating it on regular basis.
Linux like other OS keeps sending up-dates and same has to be implicated in the system.
Ubuntu too has its share of updates and same can be used in the system. Now to avoid
11

failures in updateion of software, there is an option of auto update. This facility i.e. “Install
security updates automatically” should be used in all the software’s so that even if we
forget to update, the system will itself update on its own (Najera-Gutierrez, 2018).
While the update of the system is in progress including the configuration, during this
period and the entire process the system remains unprotected. Hence this is a potentially a
dangerous period and when the security will be most vulnerable and exposed to potential
threats. The Admin and the user have to keep this thing in mind while performing the
procedure (Raggi, Thomas and Vugt, 2011).
Enabling the Persistent Connections
A persistent connection (HTTP persistent connection) is a network communication
channel that remains open for further HTTP requests and responses rather than closing after a
single exchange. Now this can be used by SSL connections might be required if one wants to
visit a secure site more than one times in just few minutes
Task 4 – Investigation Report and Details of the Security System
We discussed about that special auditing tool called Lynis. Now Lynis is an extensible
security audit tool for computer systems running Linux. It is widely used by system
managers and also by users for their systems (Linux) for scanning, auditing, analyzing and
taking the appropriate actions as required. The aim is to Harden the system and the platform
so as to reduce the outside threats (Sak and Ram, 2016).
Installation of Lynis
Lynis is freely available software and can be downloaded from various platforms.
Download the package and install the file and thus the software.
Another option is by using the package manager. It’s a very straight forward way to install
“Lynis”.
Enter the below mentioned command to install Lynis on Ubuntu 18.04, enter the below
command,
Sudo apt-get installs Lynis
12
security updates automatically” should be used in all the software’s so that even if we
forget to update, the system will itself update on its own (Najera-Gutierrez, 2018).
While the update of the system is in progress including the configuration, during this
period and the entire process the system remains unprotected. Hence this is a potentially a
dangerous period and when the security will be most vulnerable and exposed to potential
threats. The Admin and the user have to keep this thing in mind while performing the
procedure (Raggi, Thomas and Vugt, 2011).
Enabling the Persistent Connections
A persistent connection (HTTP persistent connection) is a network communication
channel that remains open for further HTTP requests and responses rather than closing after a
single exchange. Now this can be used by SSL connections might be required if one wants to
visit a secure site more than one times in just few minutes
Task 4 – Investigation Report and Details of the Security System
We discussed about that special auditing tool called Lynis. Now Lynis is an extensible
security audit tool for computer systems running Linux. It is widely used by system
managers and also by users for their systems (Linux) for scanning, auditing, analyzing and
taking the appropriate actions as required. The aim is to Harden the system and the platform
so as to reduce the outside threats (Sak and Ram, 2016).
Installation of Lynis
Lynis is freely available software and can be downloaded from various platforms.
Download the package and install the file and thus the software.
Another option is by using the package manager. It’s a very straight forward way to install
“Lynis”.
Enter the below mentioned command to install Lynis on Ubuntu 18.04, enter the below
command,
Sudo apt-get installs Lynis
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





