University Computer Security: System Investigation Report and Analysis
VerifiedAdded on 2023/01/20
|18
|2613
|81
Report
AI Summary
This report details a computer security system investigation conducted on a VMware virtual machine image provided by Benny Vandergast Inc. The investigation, undertaken for Widgets Inc., involved identifying the IP address, username, and password of the system using Kali Linux. The report outlines the process of accessing the system, identifying security issues such as encryption, web server hardening, and network service vulnerabilities. The investigation employed the Lynis auditing tool to scan for vulnerabilities, and the results, including identified issues and potential improvements, are presented. Finally, the report proposes steps to secure the system, including system updates, SSH access hardening, removal of unnecessary network services, and firewall configuration. The report is a comprehensive analysis of system security, offering valuable insights into vulnerability assessment and mitigation strategies.

University
Semester
COMPUTER SECURITY-SYSTEM
INVESTIGATION
Student ID
Student Name
Submission Date
Semester
COMPUTER SECURITY-SYSTEM
INVESTIGATION
Student ID
Student Name
Submission Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Project Description........................................................................................................................1
2. VMware Installation......................................................................................................................1
3. Description of how investigate the System Security......................................................................6
4. Description of Result.....................................................................................................................8
5. Proposal on how to Secure the System........................................................................................13
References...........................................................................................................................................16
1. Project Description........................................................................................................................1
2. VMware Installation......................................................................................................................1
3. Description of how investigate the System Security......................................................................6
4. Description of Result.....................................................................................................................8
5. Proposal on how to Secure the System........................................................................................13
References...........................................................................................................................................16
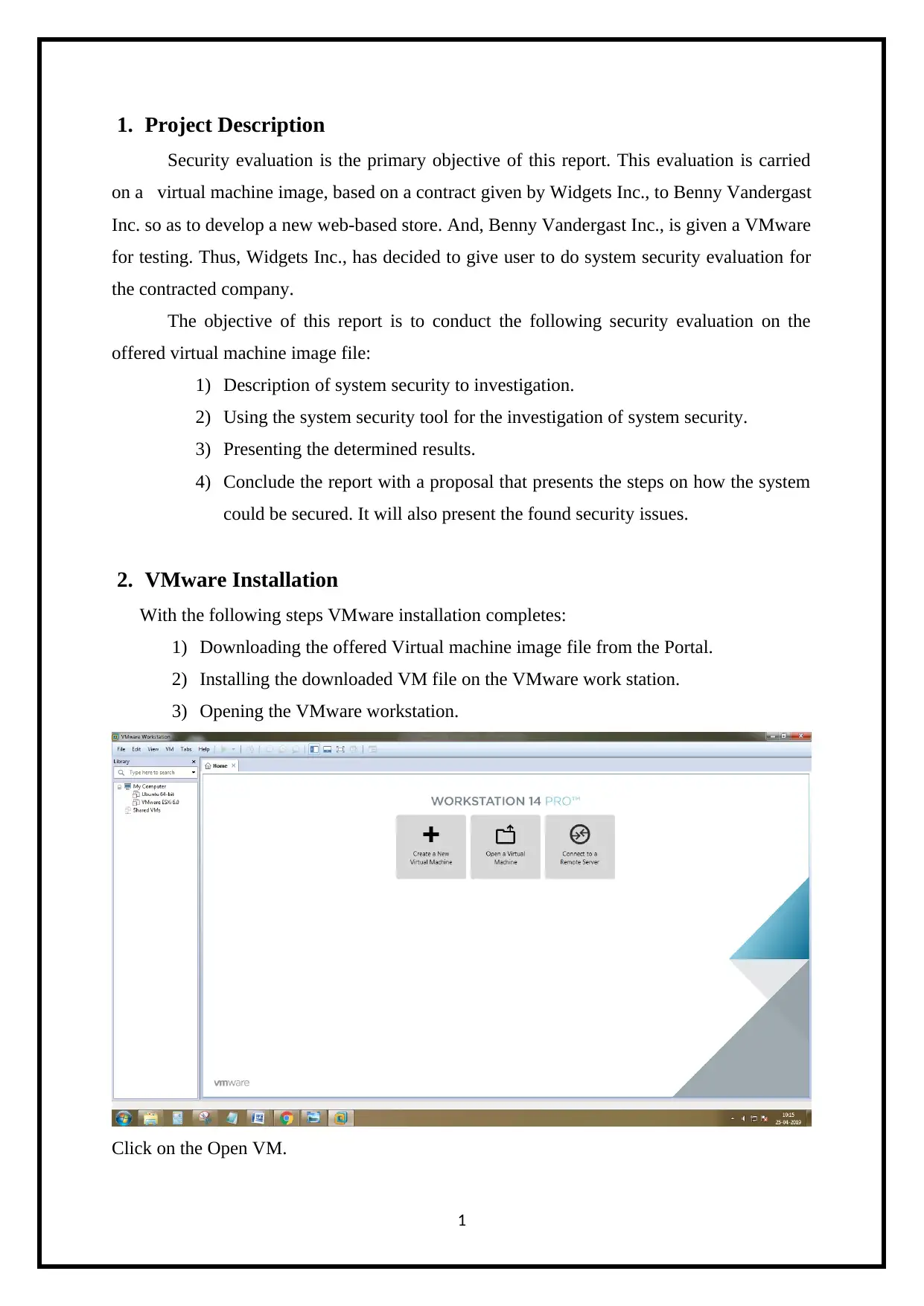
1. Project Description
Security evaluation is the primary objective of this report. This evaluation is carried
on a virtual machine image, based on a contract given by Widgets Inc., to Benny Vandergast
Inc. so as to develop a new web-based store. And, Benny Vandergast Inc., is given a VMware
for testing. Thus, Widgets Inc., has decided to give user to do system security evaluation for
the contracted company.
The objective of this report is to conduct the following security evaluation on the
offered virtual machine image file:
1) Description of system security to investigation.
2) Using the system security tool for the investigation of system security.
3) Presenting the determined results.
4) Conclude the report with a proposal that presents the steps on how the system
could be secured. It will also present the found security issues.
2. VMware Installation
With the following steps VMware installation completes:
1) Downloading the offered Virtual machine image file from the Portal.
2) Installing the downloaded VM file on the VMware work station.
3) Opening the VMware workstation.
Click on the Open VM.
1
Security evaluation is the primary objective of this report. This evaluation is carried
on a virtual machine image, based on a contract given by Widgets Inc., to Benny Vandergast
Inc. so as to develop a new web-based store. And, Benny Vandergast Inc., is given a VMware
for testing. Thus, Widgets Inc., has decided to give user to do system security evaluation for
the contracted company.
The objective of this report is to conduct the following security evaluation on the
offered virtual machine image file:
1) Description of system security to investigation.
2) Using the system security tool for the investigation of system security.
3) Presenting the determined results.
4) Conclude the report with a proposal that presents the steps on how the system
could be secured. It will also present the found security issues.
2. VMware Installation
With the following steps VMware installation completes:
1) Downloading the offered Virtual machine image file from the Portal.
2) Installing the downloaded VM file on the VMware work station.
3) Opening the VMware workstation.
Click on the Open VM.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
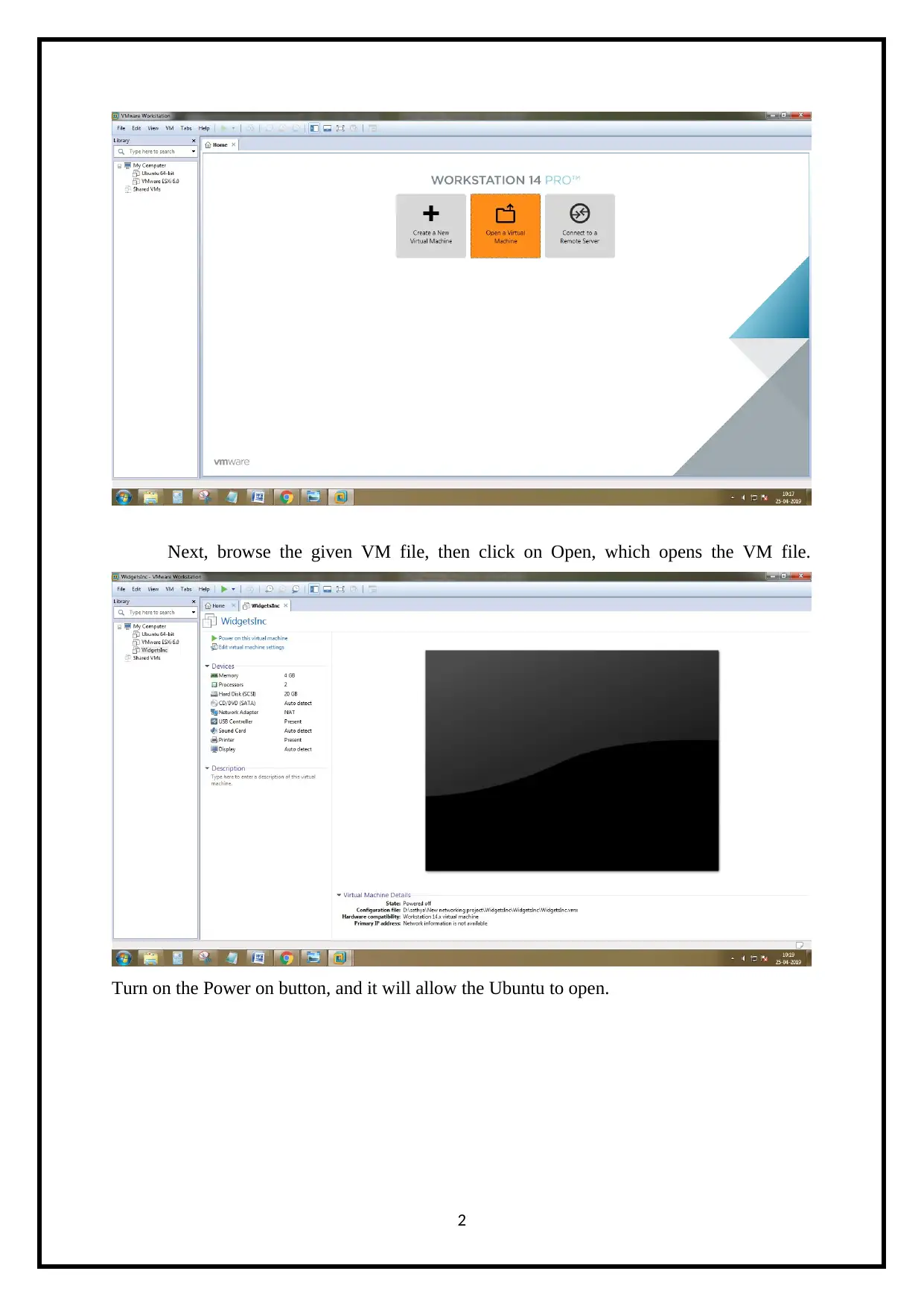
Next, browse the given VM file, then click on Open, which opens the VM file.
Turn on the Power on button, and it will allow the Ubuntu to open.
2
Turn on the Power on button, and it will allow the Ubuntu to open.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
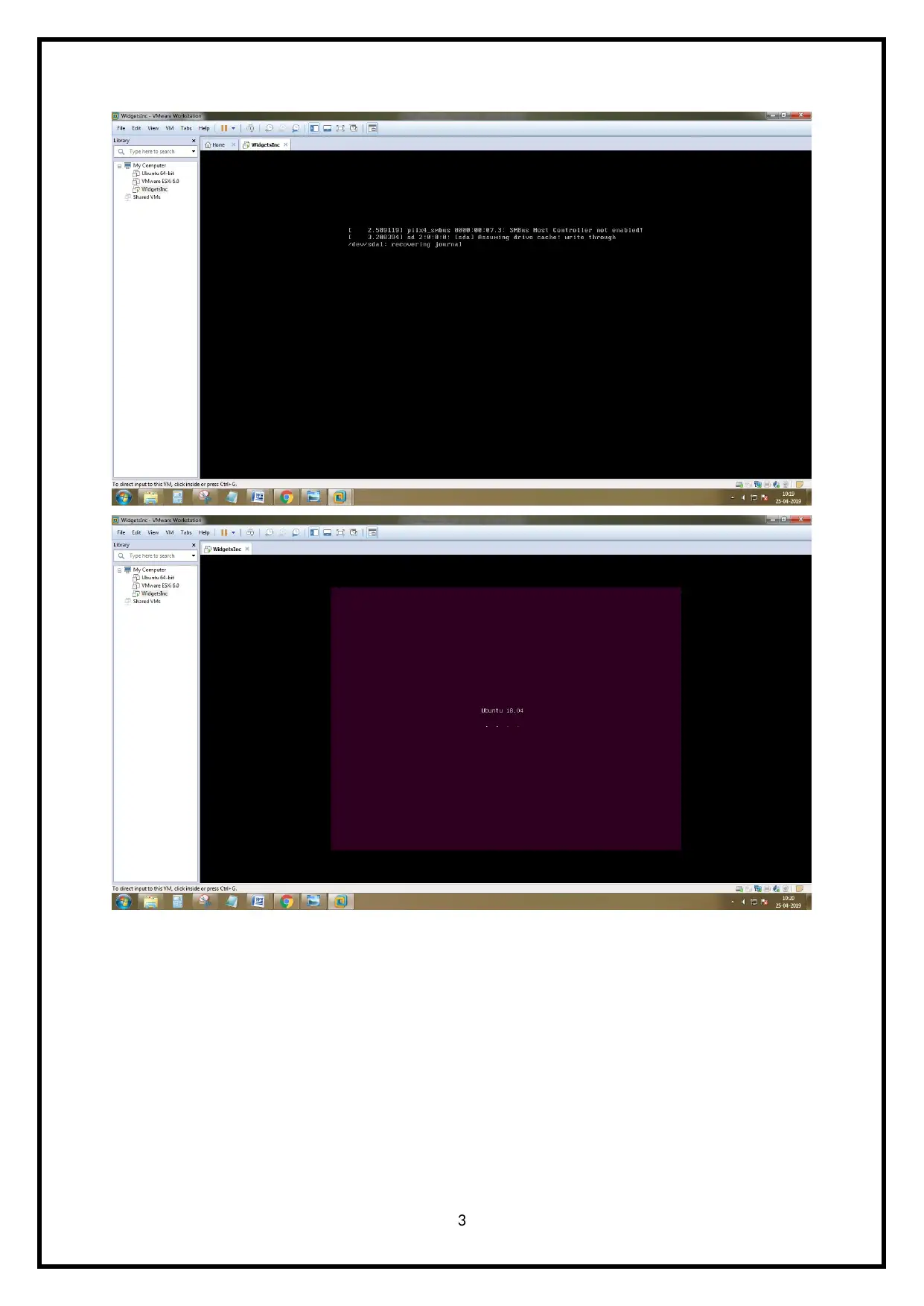
3
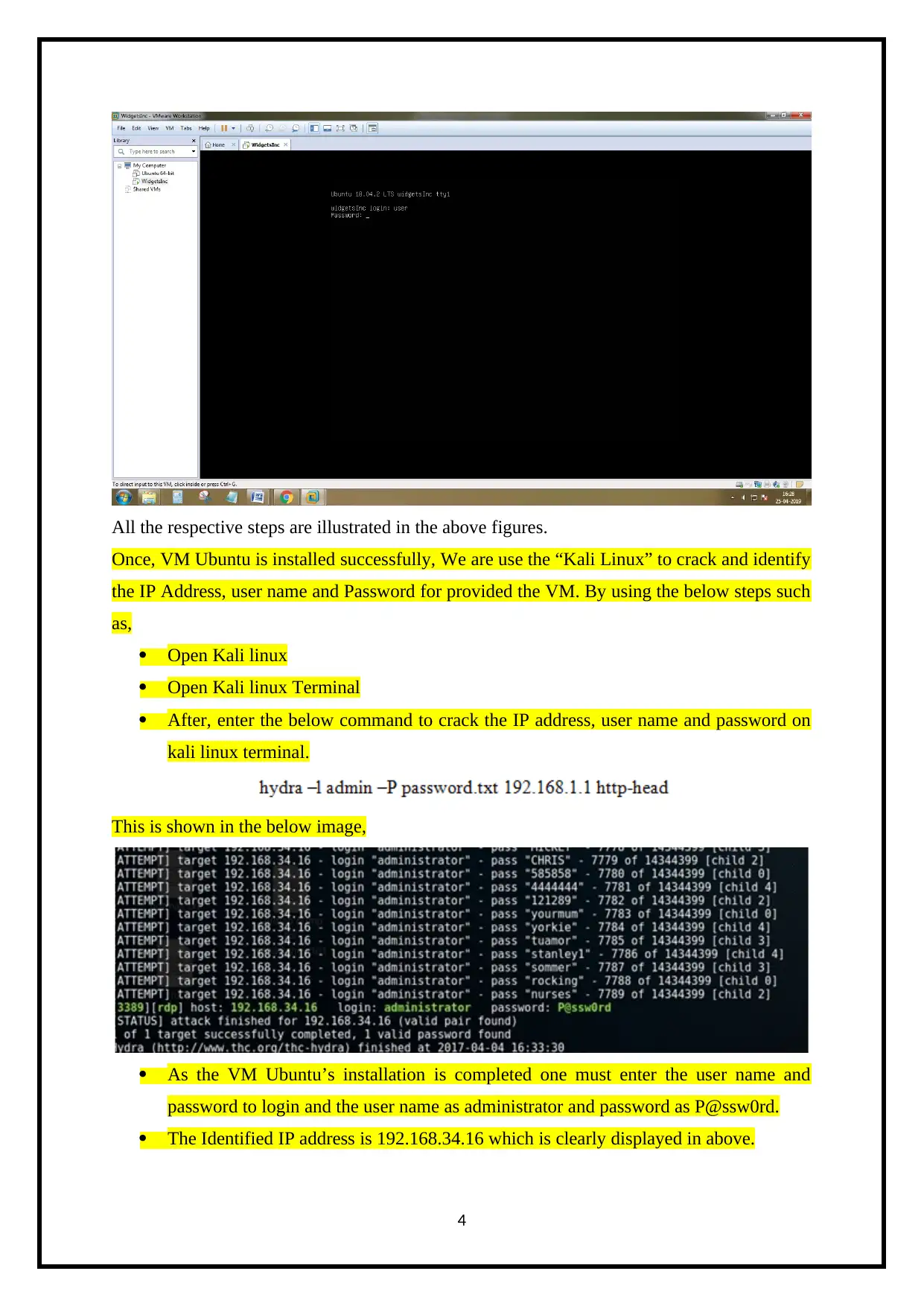
All the respective steps are illustrated in the above figures.
Once, VM Ubuntu is installed successfully, We are use the “Kali Linux” to crack and identify
the IP Address, user name and Password for provided the VM. By using the below steps such
as,
Open Kali linux
Open Kali linux Terminal
After, enter the below command to crack the IP address, user name and password on
kali linux terminal.
This is shown in the below image,
As the VM Ubuntu’s installation is completed one must enter the user name and
password to login and the user name as administrator and password as P@ssw0rd.
The Identified IP address is 192.168.34.16 which is clearly displayed in above.
4
Once, VM Ubuntu is installed successfully, We are use the “Kali Linux” to crack and identify
the IP Address, user name and Password for provided the VM. By using the below steps such
as,
Open Kali linux
Open Kali linux Terminal
After, enter the below command to crack the IP address, user name and password on
kali linux terminal.
This is shown in the below image,
As the VM Ubuntu’s installation is completed one must enter the user name and
password to login and the user name as administrator and password as P@ssw0rd.
The Identified IP address is 192.168.34.16 which is clearly displayed in above.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
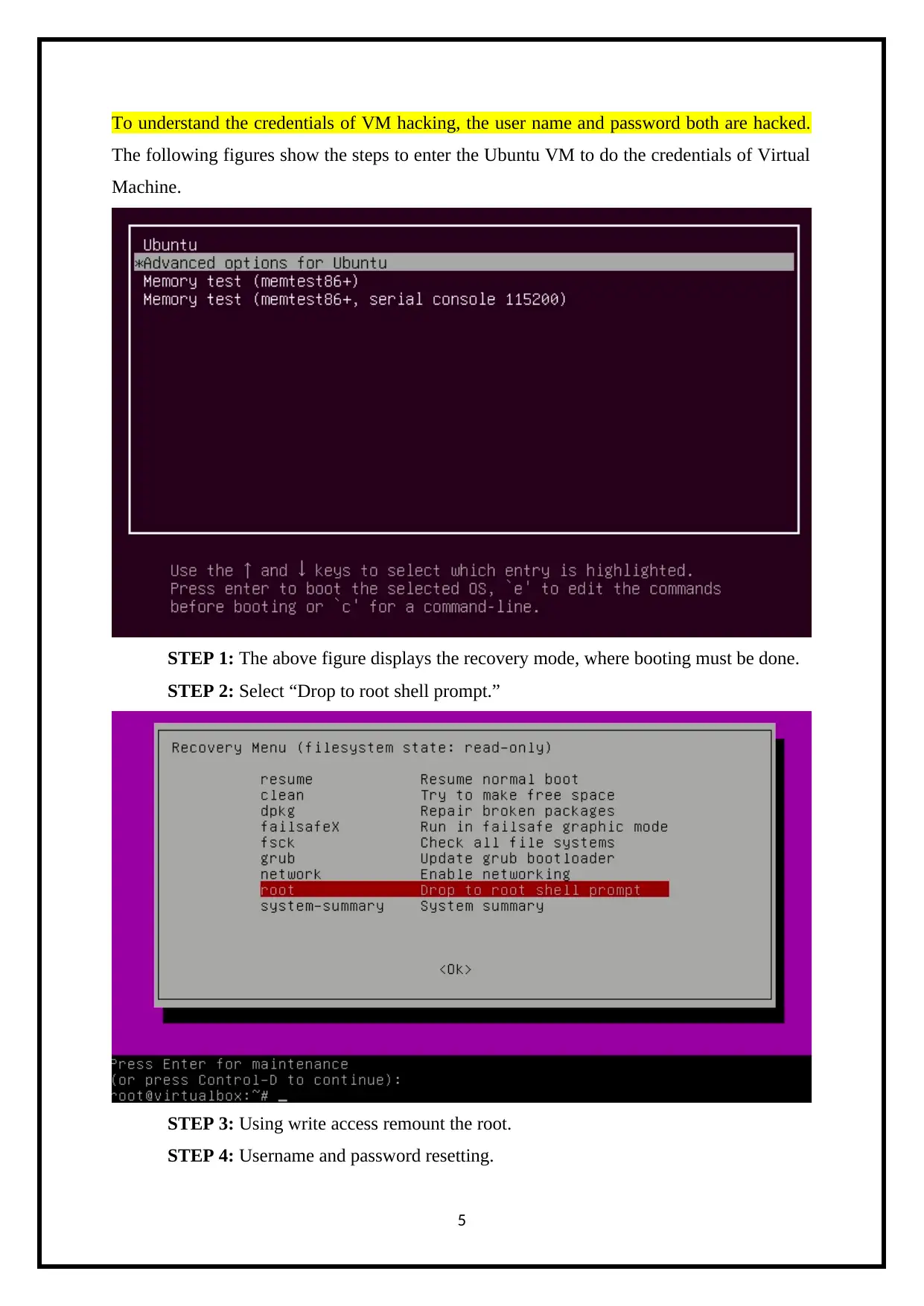
To understand the credentials of VM hacking, the user name and password both are hacked.
The following figures show the steps to enter the Ubuntu VM to do the credentials of Virtual
Machine.
STEP 1: The above figure displays the recovery mode, where booting must be done.
STEP 2: Select “Drop to root shell prompt.”
STEP 3: Using write access remount the root.
STEP 4: Username and password resetting.
5
The following figures show the steps to enter the Ubuntu VM to do the credentials of Virtual
Machine.
STEP 1: The above figure displays the recovery mode, where booting must be done.
STEP 2: Select “Drop to root shell prompt.”
STEP 3: Using write access remount the root.
STEP 4: Username and password resetting.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STEP 5: Authentication manipulation error occurs when a new password is entered.
Error is seen due to the file system being mounted with read access only. Thus, it
requires changing and remounting of the file system. The password must be reset the
password. When the user logins, the Ubuntu VM show the security issues such as- Encrypt
data communication issues, Web server hardening issues, Network services issues on VM
instance, Backup issues, Security patches, Password setting issues, Malware Issues and Open
SSL issues (Bosworth, Kabay and Whyne, n.d.).
3. Description of how investigate the System Security
In order to investigate the system security, one has to stop the threats from spreading,
identify the major threat, then prioritize the identified threats, perform various investigations
related to the used infrastructure, minimize the risks gateways, provide visibility of attacks,
use technology and effective tools to help improve the security, and when the threats are
identified take immediate steps to mitigate the same.
In this section the virtual machine image file given by the contracted company is
used. The virtual machine image file helps in easing the system operation and delivery of
applications. The virtual machine deployment helps in declining various installation and
configuration issues. The system is checked based on standard security protocols and policies
(Buchanan, 2014).
Here, for the given VM image file as Ubuntu 18.04, the security evaluation uses
international standards to certify the computer security. Only this can give assurance to the
system administrators and professionals, that the security requirements are met. Further, the
configurations are evaluated and necessary configuration changes can be done. Next, it
continues with full disk encryption as it maximizes data storage protection. The necessary
data is encrypted and hidden by the user to secure the stored data. Only, then the software are
updated on Ubuntu 18.0, to protect against vulnerabilities.
The Ubuntu hardening measures are implemented by using the system security, and it
follows the below mentioned steps:
6
Error is seen due to the file system being mounted with read access only. Thus, it
requires changing and remounting of the file system. The password must be reset the
password. When the user logins, the Ubuntu VM show the security issues such as- Encrypt
data communication issues, Web server hardening issues, Network services issues on VM
instance, Backup issues, Security patches, Password setting issues, Malware Issues and Open
SSL issues (Bosworth, Kabay and Whyne, n.d.).
3. Description of how investigate the System Security
In order to investigate the system security, one has to stop the threats from spreading,
identify the major threat, then prioritize the identified threats, perform various investigations
related to the used infrastructure, minimize the risks gateways, provide visibility of attacks,
use technology and effective tools to help improve the security, and when the threats are
identified take immediate steps to mitigate the same.
In this section the virtual machine image file given by the contracted company is
used. The virtual machine image file helps in easing the system operation and delivery of
applications. The virtual machine deployment helps in declining various installation and
configuration issues. The system is checked based on standard security protocols and policies
(Buchanan, 2014).
Here, for the given VM image file as Ubuntu 18.04, the security evaluation uses
international standards to certify the computer security. Only this can give assurance to the
system administrators and professionals, that the security requirements are met. Further, the
configurations are evaluated and necessary configuration changes can be done. Next, it
continues with full disk encryption as it maximizes data storage protection. The necessary
data is encrypted and hidden by the user to secure the stored data. Only, then the software are
updated on Ubuntu 18.0, to protect against vulnerabilities.
The Ubuntu hardening measures are implemented by using the system security, and it
follows the below mentioned steps:
6

i. Sudo Configuration
Superusersdo is also known as Sudo, which at the root level is used to set the
permissions for using particular system commands. Its commands helps to give
trusted users and administrative system access, irrespective of sharing a password of a
root user.
ii. Allowing particular Users
Add security login banner to secure the server. The following command helps
to mention the particular users who could login to SSH service (Gollmann, 2011),
AllowUsersaccountName
iii. Opening Hardening and SSH security
In Linux systems, the Open SSH helps in administering the system. It is run
using the default configurations. It helps to open the potential gateways for the
system. It ever offers SSH security. It evaluates the SSH status and performs SSH
configuration test. X11 forwarding is used to secure SSH server configuration and
settings. It then disables the rhosts. The following SSH security settings must be
carried out- Disable the rhosts, do DNS hostname check, utilize X11 forwarding,
disable any empty passwords, try maximum authentications, utilize the hash known
hosts and then set the SSH protocols.
On Ubuntu, to perform system security, SSH security utilizes a couple of
tools, they are (Halton and Weaver, 2016):
1. Lynis
2. ssh - audit
iv. Web Server Hardening
It is a process which enhances the server security buy using several methods. It
optimizes SSL and TLS to achieve the following:
1. High level privilege setting
The web server however doesn’t contain any secret information, yet has few
sensitive areas for which it has to practice system security hardening. Thus,
SSL certificate and web server configuring is essential, with tuning.
2. Configuration of Nginx
The web server configuration as Nginx helps the system in hardening and
tuning its security. The old protocols are disabled and gives permission to
TLS, as those protocols were weak. The right tool is decided to maintain the
connections and learns the steps of securing the data, using encryption. It
7
Superusersdo is also known as Sudo, which at the root level is used to set the
permissions for using particular system commands. Its commands helps to give
trusted users and administrative system access, irrespective of sharing a password of a
root user.
ii. Allowing particular Users
Add security login banner to secure the server. The following command helps
to mention the particular users who could login to SSH service (Gollmann, 2011),
AllowUsersaccountName
iii. Opening Hardening and SSH security
In Linux systems, the Open SSH helps in administering the system. It is run
using the default configurations. It helps to open the potential gateways for the
system. It ever offers SSH security. It evaluates the SSH status and performs SSH
configuration test. X11 forwarding is used to secure SSH server configuration and
settings. It then disables the rhosts. The following SSH security settings must be
carried out- Disable the rhosts, do DNS hostname check, utilize X11 forwarding,
disable any empty passwords, try maximum authentications, utilize the hash known
hosts and then set the SSH protocols.
On Ubuntu, to perform system security, SSH security utilizes a couple of
tools, they are (Halton and Weaver, 2016):
1. Lynis
2. ssh - audit
iv. Web Server Hardening
It is a process which enhances the server security buy using several methods. It
optimizes SSL and TLS to achieve the following:
1. High level privilege setting
The web server however doesn’t contain any secret information, yet has few
sensitive areas for which it has to practice system security hardening. Thus,
SSL certificate and web server configuring is essential, with tuning.
2. Configuration of Nginx
The web server configuration as Nginx helps the system in hardening and
tuning its security. The old protocols are disabled and gives permission to
TLS, as those protocols were weak. The right tool is decided to maintain the
connections and learns the steps of securing the data, using encryption. It
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

secures the web server by using the features of HTTPS. It finds the malicious
traffic; installs file integrity monitoring; configures the backups; and conducts
a thorough Linux security audit with the help of suitable system security tool.
4. Description of Result
This section will show the obtained results in this report. In the system security
investigation is carried out by using Lynis auditing tool. A virtual machine image will be
audited to check the system security of Ubuntu 18.04. The installation procedure of Lynis is
presented below with illustrative figures (Halton et al., 2017).
For Ubuntu 18.04, to install Lynis create a directory for Lynis installation.
The new version of Lynis is downloaded and stored in the created directory. The following
wget command is used during this step.
Extract the downloaded Lynis tar.gz file.
In the directory, run Lynis command.
The result is shown as follows.
8
traffic; installs file integrity monitoring; configures the backups; and conducts
a thorough Linux security audit with the help of suitable system security tool.
4. Description of Result
This section will show the obtained results in this report. In the system security
investigation is carried out by using Lynis auditing tool. A virtual machine image will be
audited to check the system security of Ubuntu 18.04. The installation procedure of Lynis is
presented below with illustrative figures (Halton et al., 2017).
For Ubuntu 18.04, to install Lynis create a directory for Lynis installation.
The new version of Lynis is downloaded and stored in the created directory. The following
wget command is used during this step.
Extract the downloaded Lynis tar.gz file.
In the directory, run Lynis command.
The result is shown as follows.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
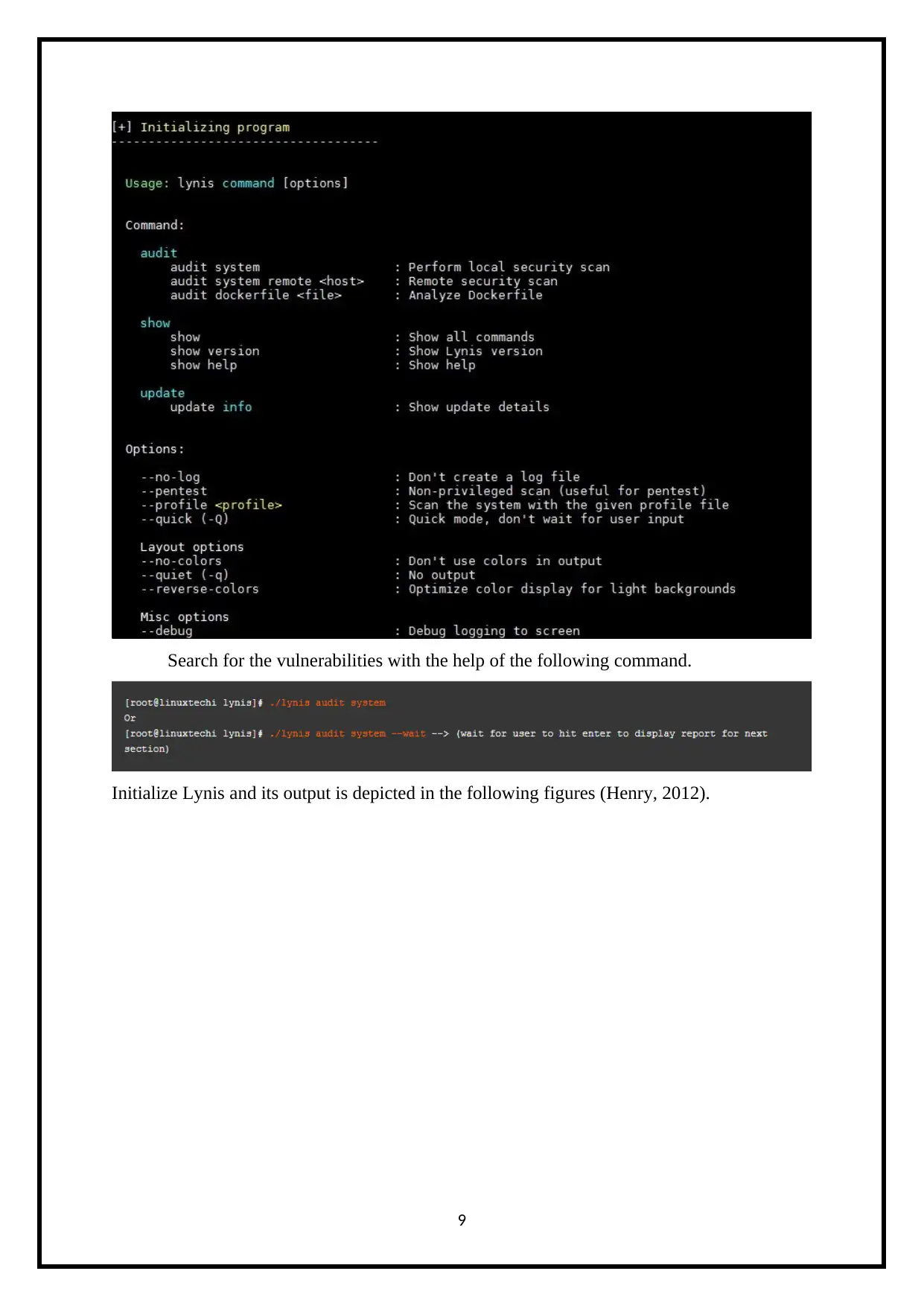
Search for the vulnerabilities with the help of the following command.
Initialize Lynis and its output is depicted in the following figures (Henry, 2012).
9
Initialize Lynis and its output is depicted in the following figures (Henry, 2012).
9
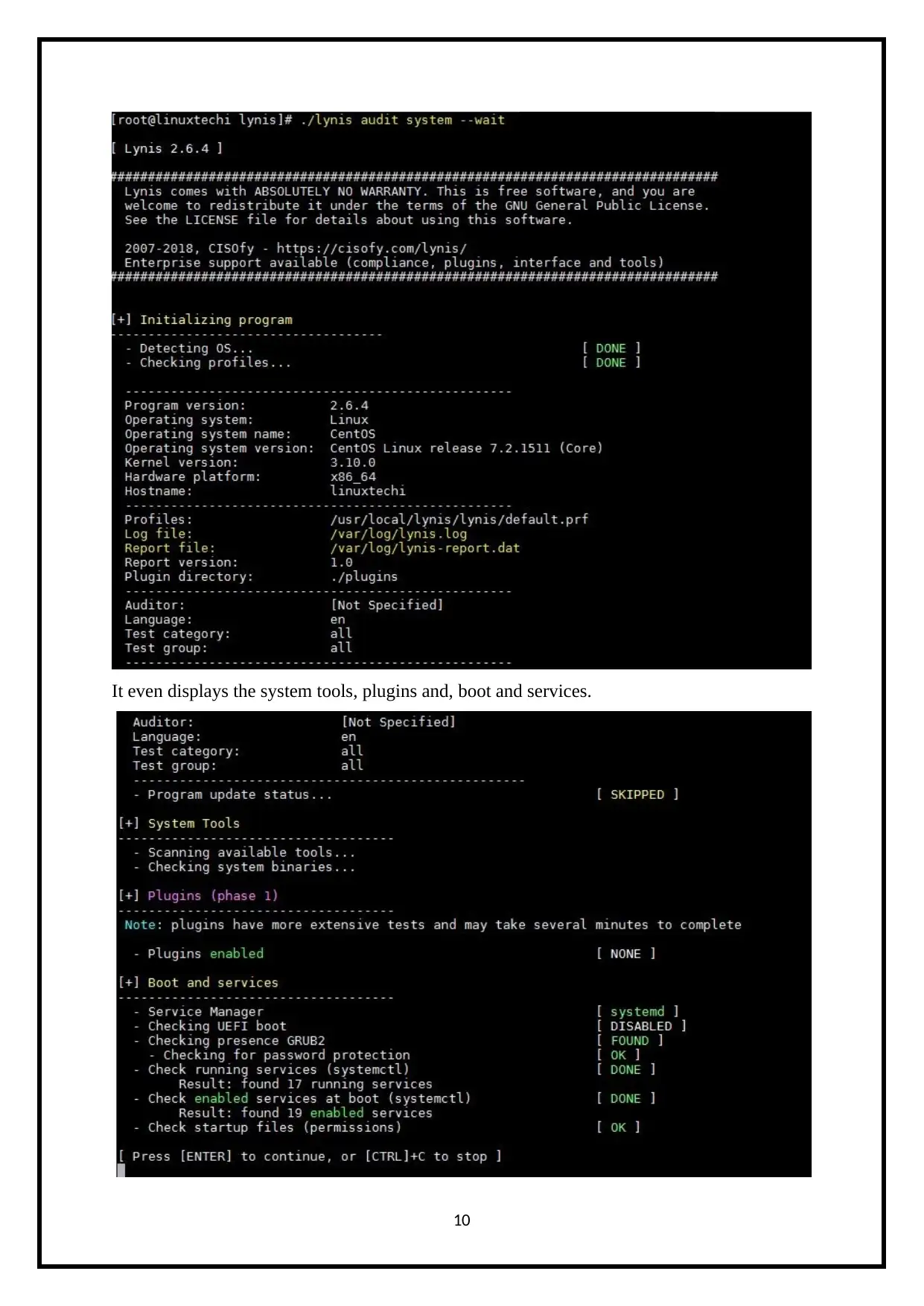
It even displays the system tools, plugins and, boot and services.
10
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





