CO4509 - Computer Security: Memcrashed Vulnerability Analysis
VerifiedAdded on 2023/04/25
|12
|4100
|244
Report
AI Summary
This report provides a detailed analysis of Memcached vulnerabilities, focusing on the Memcrashed DDoS attack. It begins by explaining the principles and workings of Memcached, highlighting its use in speeding up web applications by caching data. The report then describes the Memcrashed vulnerability, detailing how attackers can exploit it for DDoS attacks by amplifying traffic through vulnerable Memcached servers. It explores the methods used to perform these exploits, including IP address spoofing, and discusses potential solutions such as disabling UDP support and isolating Memcached servers. Furthermore, the report predicts the effectiveness of Memcrashed attacks, particularly in extortion practices, and includes a vulnerability report outlining proof-of-concept exploits and mitigation strategies. The analysis also examines the impact of these attacks on organizations and potential methods for preventing them. Desklib offers this report, along with other solved assignments and past papers, to aid students in their studies.

Running head: CO4509 - COMPUTER SECURITY
CO4509 - Computer Security
Name of the Student
Name of the University
Author’s Note
CO4509 - Computer Security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CO4509 - COMPUTER SECURITY
Table of Contents
Introduction................................................................................................................................2
Principles of Key Value Database..............................................................................................2
Working of Memcached and its use...........................................................................................3
Description of Memcrashed...................................................................................................3
Performing Exploits and solution for Memcrashed...................................................................4
Prediction and Effectiveness on Memcrashed impacts..............................................................6
Memcrashed Vulnerability report..............................................................................................7
Conclusion..................................................................................................................................9
References................................................................................................................................10
CO4509 - COMPUTER SECURITY
Table of Contents
Introduction................................................................................................................................2
Principles of Key Value Database..............................................................................................2
Working of Memcached and its use...........................................................................................3
Description of Memcrashed...................................................................................................3
Performing Exploits and solution for Memcrashed...................................................................4
Prediction and Effectiveness on Memcrashed impacts..............................................................6
Memcrashed Vulnerability report..............................................................................................7
Conclusion..................................................................................................................................9
References................................................................................................................................10

2
CO4509 - COMPUTER SECURITY
Introduction
The report is prepared on memcrashed vulnerabilities for describing the functionality
of memcache and its workings on different types of attacks. The report describes impact of
memcacrashed and it is exploited for analysing its impact. Memcache is used for speeding up
the cache mechanism and it stores all the important thing that can be applied for speeding the
delivery of web assets. The latency can be minimized if the distance between the assets is
minimized. Memcached is an memory caching system that is open source and it helps in
speeding dynamic web application with the reduction of loads in the database (Marathe et
al.2017). The data objects are stored in the dynamic memory for reducing the loads and thus
it can be said that Memcached acts as a short term memory for the applications. Key values
are used for the objects and small arbitrary strings that may include API, database calls and
page rendering. The components of Memcached allows the server and client working
together for increasing the efficiency of cached data and increase its efficiency (Choi et al.
2018). The client software is used for giving a list of available Memcached server and a client
based hash algorithm is used for selection of server that are based on key. The server
software helps in storing the keys and their values for the hash table and LRU is used for
determining the old data and throwing out of the memory for reusing it.
Principles of Key Value Database
Memcached works with four components that allows the system to retrieve and store
data. The components have a expiration time, raw data and key and it works as the following
stage:
A piece of data is requested by the client and is checked by the Memcached for
checking that if it is needed to be stored in cache.
There may be different outcomes such as if the data is stored in cache, the data is
needed to be returned from Memcached and there is not need for checking the
database. In case if the data is not stored in the cache a query is made for retrieving
the data and store it in the Memcached.
If there is a change in information and the values are expired the information gets
updated in Memcached and it is to be ensured that the contents that are delivered to the client
are fresh.
CO4509 - COMPUTER SECURITY
Introduction
The report is prepared on memcrashed vulnerabilities for describing the functionality
of memcache and its workings on different types of attacks. The report describes impact of
memcacrashed and it is exploited for analysing its impact. Memcache is used for speeding up
the cache mechanism and it stores all the important thing that can be applied for speeding the
delivery of web assets. The latency can be minimized if the distance between the assets is
minimized. Memcached is an memory caching system that is open source and it helps in
speeding dynamic web application with the reduction of loads in the database (Marathe et
al.2017). The data objects are stored in the dynamic memory for reducing the loads and thus
it can be said that Memcached acts as a short term memory for the applications. Key values
are used for the objects and small arbitrary strings that may include API, database calls and
page rendering. The components of Memcached allows the server and client working
together for increasing the efficiency of cached data and increase its efficiency (Choi et al.
2018). The client software is used for giving a list of available Memcached server and a client
based hash algorithm is used for selection of server that are based on key. The server
software helps in storing the keys and their values for the hash table and LRU is used for
determining the old data and throwing out of the memory for reusing it.
Principles of Key Value Database
Memcached works with four components that allows the system to retrieve and store
data. The components have a expiration time, raw data and key and it works as the following
stage:
A piece of data is requested by the client and is checked by the Memcached for
checking that if it is needed to be stored in cache.
There may be different outcomes such as if the data is stored in cache, the data is
needed to be returned from Memcached and there is not need for checking the
database. In case if the data is not stored in the cache a query is made for retrieving
the data and store it in the Memcached.
If there is a change in information and the values are expired the information gets
updated in Memcached and it is to be ensured that the contents that are delivered to the client
are fresh.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CO4509 - COMPUTER SECURITY
There are different Memcached server and multiple clients in a typical setup and hash
algorithm are used by the client for determining the use of Memcached storage server and
distributing the loads (Bremler-Barr et al. 2017). A second hash is also computed for
determining what is needed to be stored in the hash tables. There are some points that are
included in the Memcached architecture such as data is send to a single server, servers does
not shares data and the values are kept in the RAM of the server.
Working of Memcached and its use
There are different ways that can be used for installing Memcached and it depends on
the type of the system and there is a variation in the methods. For the Linux operating system
a simple command apt-get install Memcached can be used and the command varies for the
different version of Linux (Carra and Michiardi 2016). There are different ways for installing
the Memcached and it is needed to be considered after analysing the requirement of the client
server environment.
The above figure shows the architecture of Memcached servers and here the cache is
separated from the application for giving better control to manage the cache from the
separated servers. The server capacity can be increased based on the size of the cache without
having any affect on the application.
Description of Memcrashed
There are many researchers who have reported against Memcached since it is used by
the attacker for powering the DDoS attack and are known as Memcached DDoS attack. Since
Memcached is an opensource it has designed distributing memory caching for speeding the
dynamic web application and alleviating the loads in database. The clients can communicate
with the servers with Memcached using the UDP or TCP port 1211. Thus there is a
possibility that the attacker can abuse the Memcached for the amplification for DDoS attacks
and it can spike up compromising the security of the client server architecture (Luo et al.
2016). The Memcached servers can be involved by the attacker for increasing the
effectiveness of the attack. It can be done simply by sending a request message to the targeted
server on port 1121 and implementing IP address spoofing with the IP address of the victim.
Few bytes are used for sending the request and its response is expected to be thousands times
bigger which results in amplifying the attack and 51000 times than the initial request. A
research is done in uptick in Memcached amplification attacks that ranges from 100mbps to
500gbps. The attacks amplifies is sourced from the port 11211 having packet size of 1428
CO4509 - COMPUTER SECURITY
There are different Memcached server and multiple clients in a typical setup and hash
algorithm are used by the client for determining the use of Memcached storage server and
distributing the loads (Bremler-Barr et al. 2017). A second hash is also computed for
determining what is needed to be stored in the hash tables. There are some points that are
included in the Memcached architecture such as data is send to a single server, servers does
not shares data and the values are kept in the RAM of the server.
Working of Memcached and its use
There are different ways that can be used for installing Memcached and it depends on
the type of the system and there is a variation in the methods. For the Linux operating system
a simple command apt-get install Memcached can be used and the command varies for the
different version of Linux (Carra and Michiardi 2016). There are different ways for installing
the Memcached and it is needed to be considered after analysing the requirement of the client
server environment.
The above figure shows the architecture of Memcached servers and here the cache is
separated from the application for giving better control to manage the cache from the
separated servers. The server capacity can be increased based on the size of the cache without
having any affect on the application.
Description of Memcrashed
There are many researchers who have reported against Memcached since it is used by
the attacker for powering the DDoS attack and are known as Memcached DDoS attack. Since
Memcached is an opensource it has designed distributing memory caching for speeding the
dynamic web application and alleviating the loads in database. The clients can communicate
with the servers with Memcached using the UDP or TCP port 1211. Thus there is a
possibility that the attacker can abuse the Memcached for the amplification for DDoS attacks
and it can spike up compromising the security of the client server architecture (Luo et al.
2016). The Memcached servers can be involved by the attacker for increasing the
effectiveness of the attack. It can be done simply by sending a request message to the targeted
server on port 1121 and implementing IP address spoofing with the IP address of the victim.
Few bytes are used for sending the request and its response is expected to be thousands times
bigger which results in amplifying the attack and 51000 times than the initial request. A
research is done in uptick in Memcached amplification attacks that ranges from 100mbps to
500gbps. The attacks amplifies is sourced from the port 11211 having packet size of 1428
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
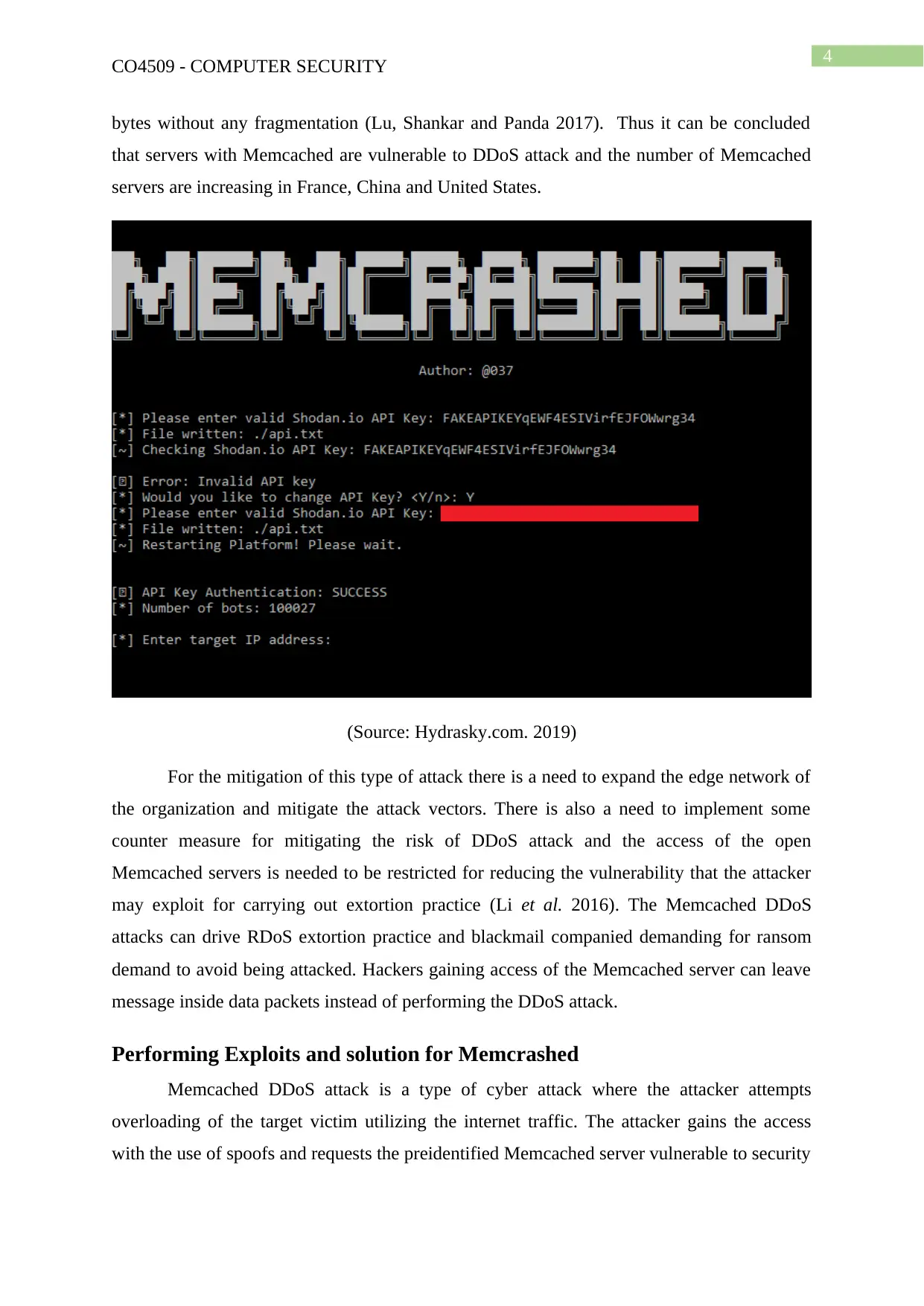
4
CO4509 - COMPUTER SECURITY
bytes without any fragmentation (Lu, Shankar and Panda 2017). Thus it can be concluded
that servers with Memcached are vulnerable to DDoS attack and the number of Memcached
servers are increasing in France, China and United States.
(Source: Hydrasky.com. 2019)
For the mitigation of this type of attack there is a need to expand the edge network of
the organization and mitigate the attack vectors. There is also a need to implement some
counter measure for mitigating the risk of DDoS attack and the access of the open
Memcached servers is needed to be restricted for reducing the vulnerability that the attacker
may exploit for carrying out extortion practice (Li et al. 2016). The Memcached DDoS
attacks can drive RDoS extortion practice and blackmail companied demanding for ransom
demand to avoid being attacked. Hackers gaining access of the Memcached server can leave
message inside data packets instead of performing the DDoS attack.
Performing Exploits and solution for Memcrashed
Memcached DDoS attack is a type of cyber attack where the attacker attempts
overloading of the target victim utilizing the internet traffic. The attacker gains the access
with the use of spoofs and requests the preidentified Memcached server vulnerable to security
CO4509 - COMPUTER SECURITY
bytes without any fragmentation (Lu, Shankar and Panda 2017). Thus it can be concluded
that servers with Memcached are vulnerable to DDoS attack and the number of Memcached
servers are increasing in France, China and United States.
(Source: Hydrasky.com. 2019)
For the mitigation of this type of attack there is a need to expand the edge network of
the organization and mitigate the attack vectors. There is also a need to implement some
counter measure for mitigating the risk of DDoS attack and the access of the open
Memcached servers is needed to be restricted for reducing the vulnerability that the attacker
may exploit for carrying out extortion practice (Li et al. 2016). The Memcached DDoS
attacks can drive RDoS extortion practice and blackmail companied demanding for ransom
demand to avoid being attacked. Hackers gaining access of the Memcached server can leave
message inside data packets instead of performing the DDoS attack.
Performing Exploits and solution for Memcrashed
Memcached DDoS attack is a type of cyber attack where the attacker attempts
overloading of the target victim utilizing the internet traffic. The attacker gains the access
with the use of spoofs and requests the preidentified Memcached server vulnerable to security

5
CO4509 - COMPUTER SECURITY
risk and floods the victim targeted with internet traffic which is potentially overwhelming
with the resources of the victim (Liao and Peng 2017). The internet infrastructure of the
target is overloaded such that it cannot process new requests and the regular traffic should not
access different sources from the internet causing denial of service.
(Source: Noise.getoto.net. 2018)
DDoS attacks can abuse the Memcached servers and it is possible since the
organization that are operating the servers may fail in implementation of the basic security
practices that can get the attacker to access the server. The UDP support is needed to be
disabled and the Memcached servers are needed to be isolated such that future attacks can be
stopped and exposure to internet is needed to be mitigated. It also helps in fixing the IP
spoofing and vulnerable protocol attacks. The internet service providers are needed to defeat
this types of attacks and fix different vulnerable protocols (Gupta et al. 2017). A large hash
table can be produced with the help of Memcached and it can be distributed with multiple
machine for faster operation and increasing the functionality of the system. The current
architecture of Memcached used client server architecture and the server is responsible for
maintaining key value associative array and the client populates the array and the querry is
done with the help of keys and it needed to be 250 bytes longer and it should have a value of
1mb (Dao 2018). Client side libraries are used by the client and for establishing a connection
with the server and exposing the service port 1211. It have support for TCP and UDP
protocol and the servers information is known to all the client but the servers does not
communicate with each other.
CO4509 - COMPUTER SECURITY
risk and floods the victim targeted with internet traffic which is potentially overwhelming
with the resources of the victim (Liao and Peng 2017). The internet infrastructure of the
target is overloaded such that it cannot process new requests and the regular traffic should not
access different sources from the internet causing denial of service.
(Source: Noise.getoto.net. 2018)
DDoS attacks can abuse the Memcached servers and it is possible since the
organization that are operating the servers may fail in implementation of the basic security
practices that can get the attacker to access the server. The UDP support is needed to be
disabled and the Memcached servers are needed to be isolated such that future attacks can be
stopped and exposure to internet is needed to be mitigated. It also helps in fixing the IP
spoofing and vulnerable protocol attacks. The internet service providers are needed to defeat
this types of attacks and fix different vulnerable protocols (Gupta et al. 2017). A large hash
table can be produced with the help of Memcached and it can be distributed with multiple
machine for faster operation and increasing the functionality of the system. The current
architecture of Memcached used client server architecture and the server is responsible for
maintaining key value associative array and the client populates the array and the querry is
done with the help of keys and it needed to be 250 bytes longer and it should have a value of
1mb (Dao 2018). Client side libraries are used by the client and for establishing a connection
with the server and exposing the service port 1211. It have support for TCP and UDP
protocol and the servers information is known to all the client but the servers does not
communicate with each other.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
CO4509 - COMPUTER SECURITY
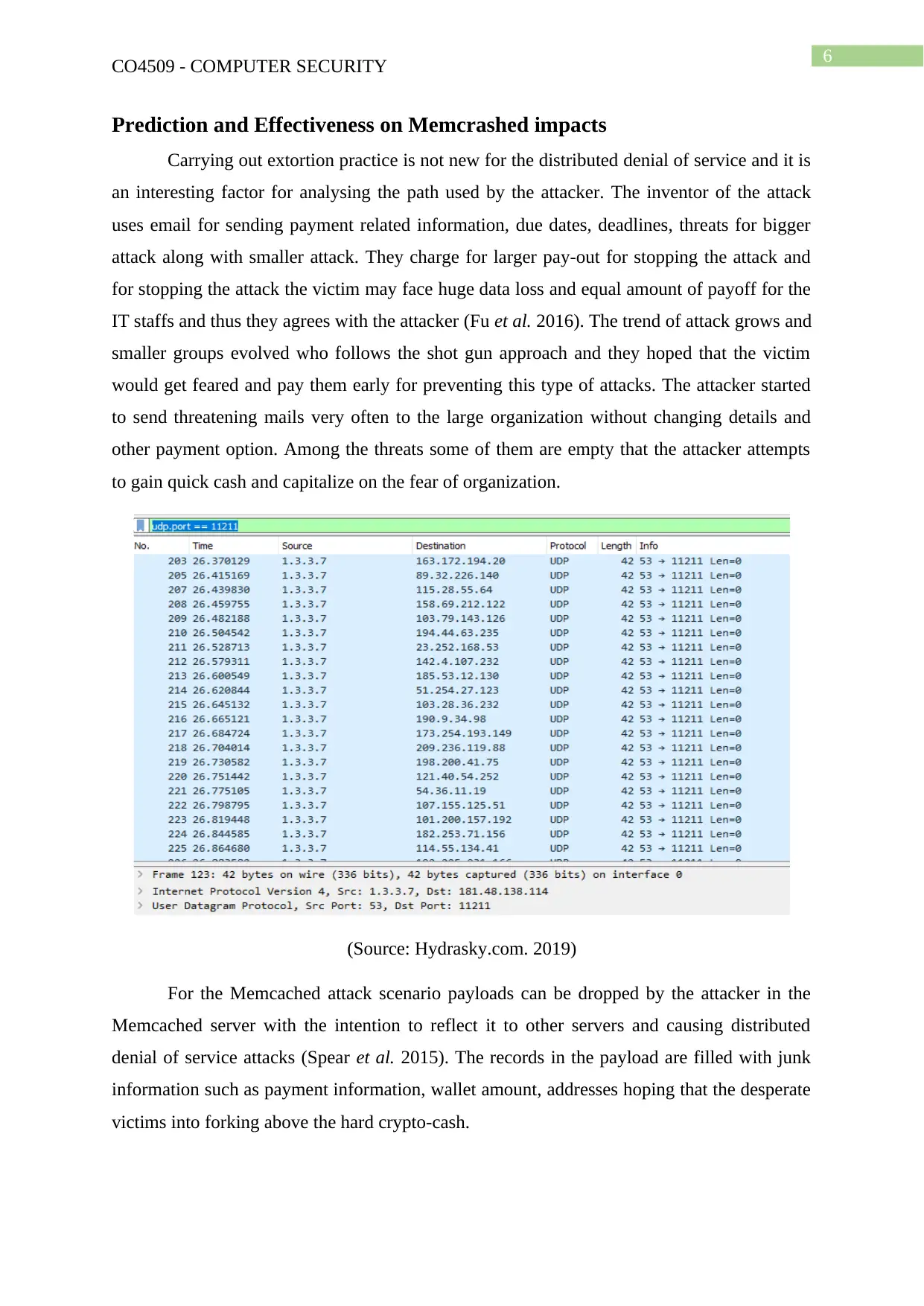
Prediction and Effectiveness on Memcrashed impacts
Carrying out extortion practice is not new for the distributed denial of service and it is
an interesting factor for analysing the path used by the attacker. The inventor of the attack
uses email for sending payment related information, due dates, deadlines, threats for bigger
attack along with smaller attack. They charge for larger pay-out for stopping the attack and
for stopping the attack the victim may face huge data loss and equal amount of payoff for the
IT staffs and thus they agrees with the attacker (Fu et al. 2016). The trend of attack grows and
smaller groups evolved who follows the shot gun approach and they hoped that the victim
would get feared and pay them early for preventing this type of attacks. The attacker started
to send threatening mails very often to the large organization without changing details and
other payment option. Among the threats some of them are empty that the attacker attempts
to gain quick cash and capitalize on the fear of organization.
(Source: Hydrasky.com. 2019)
For the Memcached attack scenario payloads can be dropped by the attacker in the
Memcached server with the intention to reflect it to other servers and causing distributed
denial of service attacks (Spear et al. 2015). The records in the payload are filled with junk
information such as payment information, wallet amount, addresses hoping that the desperate
victims into forking above the hard crypto-cash.
CO4509 - COMPUTER SECURITY
Prediction and Effectiveness on Memcrashed impacts
Carrying out extortion practice is not new for the distributed denial of service and it is
an interesting factor for analysing the path used by the attacker. The inventor of the attack
uses email for sending payment related information, due dates, deadlines, threats for bigger
attack along with smaller attack. They charge for larger pay-out for stopping the attack and
for stopping the attack the victim may face huge data loss and equal amount of payoff for the
IT staffs and thus they agrees with the attacker (Fu et al. 2016). The trend of attack grows and
smaller groups evolved who follows the shot gun approach and they hoped that the victim
would get feared and pay them early for preventing this type of attacks. The attacker started
to send threatening mails very often to the large organization without changing details and
other payment option. Among the threats some of them are empty that the attacker attempts
to gain quick cash and capitalize on the fear of organization.
(Source: Hydrasky.com. 2019)
For the Memcached attack scenario payloads can be dropped by the attacker in the
Memcached server with the intention to reflect it to other servers and causing distributed
denial of service attacks (Spear et al. 2015). The records in the payload are filled with junk
information such as payment information, wallet amount, addresses hoping that the desperate
victims into forking above the hard crypto-cash.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CO4509 - COMPUTER SECURITY
The group and the actor that appears leveraging the technique can utilize the same
technique of attacks using the same amount, wallet address for different victims of multiple
industries. There is no suggestions that can be provided to track the reaction of the target with
neither any contact information, payment notification and detailed instructions (Cheng et al.
2017). If the victims pays the amount in the wallet requested by the client the attacker would
have all the information about the target and stop the attack.
The attacker uses live journals for implementing changes in the application and before
Memcached the database might be contacted by the application. The query can also be
replaced by the Memcached request if there is an existence of the Memcached instance the
data portion would contain the values of columns (Marathe et al. 2017). If there is no
existence in Memcached the performance of the application the point is selected against the
database for populating Memcached along with result. The addressed range of LiveJournal
selects and joins with changing the queries for returning the primary key values and avoiding
hidden joins from index to full table.
Memcrashed Vulnerability report
There are different distinct proofs of concept that can be used for amplification of
DDoS attack and it can be used by any of the attacker for releasing payload on the targeted
device. There are different vulnerable Memcached servers and PoC code written in Python
that is reliable on Shodan search engine for getting a list of the servers and use them for
DDoS attack. There are different other languages that are used for writing the exploit codes
and getting the list of the Memcached server. In case the PoC exploits for Memcached DDoS
attack a kill switch can be used for addressing the vulnerability of Memcached (Bremler-Barr
et al. 2017). If the issue is exploited in the Memcached server then it can cause attacker to
steal or modify data from the company’s server. The researcher made an important discovery
that the introduction of the kill switch can help in mitigating different types of vulnerabilities
in the network. Currently there are over 95000 number of servers globally that allows
connection using TCP and UDP port 1211 using internet and many confidential servers can
also be included in the DDoS attacks (Luo et al. 2016). If there is a need for the client to read
the values corresponding with a certain key the library of the client computes the hash of the
corresponding key for determining the server that is needed to be utilized. A simple form of
shrading is and scalable share nothing architecture across the server is needed to be created
and a second hash value is computed by the server for storing and reading the corresponding
CO4509 - COMPUTER SECURITY
The group and the actor that appears leveraging the technique can utilize the same
technique of attacks using the same amount, wallet address for different victims of multiple
industries. There is no suggestions that can be provided to track the reaction of the target with
neither any contact information, payment notification and detailed instructions (Cheng et al.
2017). If the victims pays the amount in the wallet requested by the client the attacker would
have all the information about the target and stop the attack.
The attacker uses live journals for implementing changes in the application and before
Memcached the database might be contacted by the application. The query can also be
replaced by the Memcached request if there is an existence of the Memcached instance the
data portion would contain the values of columns (Marathe et al. 2017). If there is no
existence in Memcached the performance of the application the point is selected against the
database for populating Memcached along with result. The addressed range of LiveJournal
selects and joins with changing the queries for returning the primary key values and avoiding
hidden joins from index to full table.
Memcrashed Vulnerability report
There are different distinct proofs of concept that can be used for amplification of
DDoS attack and it can be used by any of the attacker for releasing payload on the targeted
device. There are different vulnerable Memcached servers and PoC code written in Python
that is reliable on Shodan search engine for getting a list of the servers and use them for
DDoS attack. There are different other languages that are used for writing the exploit codes
and getting the list of the Memcached server. In case the PoC exploits for Memcached DDoS
attack a kill switch can be used for addressing the vulnerability of Memcached (Bremler-Barr
et al. 2017). If the issue is exploited in the Memcached server then it can cause attacker to
steal or modify data from the company’s server. The researcher made an important discovery
that the introduction of the kill switch can help in mitigating different types of vulnerabilities
in the network. Currently there are over 95000 number of servers globally that allows
connection using TCP and UDP port 1211 using internet and many confidential servers can
also be included in the DDoS attacks (Luo et al. 2016). If there is a need for the client to read
the values corresponding with a certain key the library of the client computes the hash of the
corresponding key for determining the server that is needed to be utilized. A simple form of
shrading is and scalable share nothing architecture across the server is needed to be created
and a second hash value is computed by the server for storing and reading the corresponding

8
CO4509 - COMPUTER SECURITY
value. The value are kept generally in the RAM and if there is a case that the server runs out
of memory the oldest values residing in the memory are discarded. Thus there is a need to
treat the Memcached as a transitory cache since it is not possible to assume that the data that
is stored in Memcached is there for their needs (Liao and Peng 2017). There are different
other database for example MemcachedDB and couchbase Server that helps in providing
persistent storage while maintaining a compatibility of the Memcached protocol. The cached
data of each of the client can be read if the same hash algorithm is used by all the client and
for the typical deployment environment there are many servers and clients present in the
network. It is possible that Memcached can be used in a single computer that can act
simultaneously as server and client. Since the hash table size is very large and there is
limitation for availing memory for all the servers that forms a cluster in the data center (Fu et
al. 2016). In case there is a need of Web publishing with the presence of wide audience and
high volumes of data are needed to be managed it is needed to be stretched to many
gigabytes. Here Memcached is valuable equally for this situation and there is more number of
request for the content and cost of receiving a particular content is also higher.
The Memcached server are needed to be deployed in the trusted network where it is
free for the client to contact with the server. There are some cases that the Memcached
servers are deployed in an untrusted environment where the network administrator controls
the flow of data packets and exercise control for the client to connect with the server. Thus
for this reason Memcached server can be combined with SASL authentication support with
binary protocol support for increasing the security of the framework (Cheng et al. 2017). In
case of trusted organization Memcached flat trust model contains security implication. For
the simplicity of the model the different Memcached operation is needed to be equally
treated. The client who have a need to access entries of low security in the cache helps in
gaining access for the entries in the cache even in case where we need higher security. The
entry in the cache can be retrieved in case the cache key can be predicted, found or guessed
using an exhaustive search (Choi et al. 2018). Different attempt can be made for isolating
reading data and setting for web publishing and high volume situation. The content server
facing outward have access to read Memcached that have the content pages but does not have
write access. If new content is needed to be published and the content is not present in
Memcached it sends a request to the content generating server and which is not publicly
accessible for the creation of the content and adding to the Memcached (Carra and Michiardi
2016). For serving the content the content server retrieves it from the Memcached.
CO4509 - COMPUTER SECURITY
value. The value are kept generally in the RAM and if there is a case that the server runs out
of memory the oldest values residing in the memory are discarded. Thus there is a need to
treat the Memcached as a transitory cache since it is not possible to assume that the data that
is stored in Memcached is there for their needs (Liao and Peng 2017). There are different
other database for example MemcachedDB and couchbase Server that helps in providing
persistent storage while maintaining a compatibility of the Memcached protocol. The cached
data of each of the client can be read if the same hash algorithm is used by all the client and
for the typical deployment environment there are many servers and clients present in the
network. It is possible that Memcached can be used in a single computer that can act
simultaneously as server and client. Since the hash table size is very large and there is
limitation for availing memory for all the servers that forms a cluster in the data center (Fu et
al. 2016). In case there is a need of Web publishing with the presence of wide audience and
high volumes of data are needed to be managed it is needed to be stretched to many
gigabytes. Here Memcached is valuable equally for this situation and there is more number of
request for the content and cost of receiving a particular content is also higher.
The Memcached server are needed to be deployed in the trusted network where it is
free for the client to contact with the server. There are some cases that the Memcached
servers are deployed in an untrusted environment where the network administrator controls
the flow of data packets and exercise control for the client to connect with the server. Thus
for this reason Memcached server can be combined with SASL authentication support with
binary protocol support for increasing the security of the framework (Cheng et al. 2017). In
case of trusted organization Memcached flat trust model contains security implication. For
the simplicity of the model the different Memcached operation is needed to be equally
treated. The client who have a need to access entries of low security in the cache helps in
gaining access for the entries in the cache even in case where we need higher security. The
entry in the cache can be retrieved in case the cache key can be predicted, found or guessed
using an exhaustive search (Choi et al. 2018). Different attempt can be made for isolating
reading data and setting for web publishing and high volume situation. The content server
facing outward have access to read Memcached that have the content pages but does not have
write access. If new content is needed to be published and the content is not present in
Memcached it sends a request to the content generating server and which is not publicly
accessible for the creation of the content and adding to the Memcached (Carra and Michiardi
2016). For serving the content the content server retrieves it from the Memcached.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CO4509 - COMPUTER SECURITY
The Memcached servers that are misconfigured can help in launching DDoS attack in
a large scale by the hacker. The Memcached protocol has a factor of amplification with the
use of UDP protocol because it have many victims that causes denial of service. It is a simple
process to convert object or database creating queries into a Memcached. The Memcached
value having an unique key is checked by the client and if there is no result a database is
selected and a unique key is set utilizing the Memcached API function (Luo et al. 2016). In
case of modification of API call incorrect data would be fetched by the server and wrong
information would be updated in the database. A call can eb created for updating the cached
data and matching it with the new data in database and it should be assumed that the query is
success. The cache can also be invalidated with the Memcached delete function such that
subsequent fetching of cache can result in cache miss. As an alternative cache invalidation
strategy can be used for storing random number as an agreed entry for cache and
incorporating the number as a key and storing a particular entry type (Dao 2018). For
invalidating the entries at once the random number is needed to be changed and the existing
entries should not be referenced and expired or recycled.
Conclusion
From the above report it can be concluded that the Memcached servers are vulnerable
to DDoS attacks since some of the organization fails to implement basic security practice in
their organization. There is a need for identifying the threats acting on the business such that
the abuse of misconfigured Memcached server is eliminated and the organization is secured
from the future attacks. From researching on the risk it is identified that disabling the UDP
port in the Memcached server can help in reducing the risk. The Memcached server is needed
to be isolated from the internet for eliminating the risk associated with the denial of service
attacks. The attacks in future can be deflected by fixing the vulnerable protocol and IP
spoofing, if IP spoofing is permissible over the internet. The Memcached design architecture
is simple and can be deployed easily for solving different problems for management of large
data caches. It is an API which is available for different languages for increasing the
efficiency of a WEB application environment. Apart from the advantages there are different
disadvantages of application of Memcached because if the servers are not secured it can be
misused by hacker for causing distributed denial of service attacks.
CO4509 - COMPUTER SECURITY
The Memcached servers that are misconfigured can help in launching DDoS attack in
a large scale by the hacker. The Memcached protocol has a factor of amplification with the
use of UDP protocol because it have many victims that causes denial of service. It is a simple
process to convert object or database creating queries into a Memcached. The Memcached
value having an unique key is checked by the client and if there is no result a database is
selected and a unique key is set utilizing the Memcached API function (Luo et al. 2016). In
case of modification of API call incorrect data would be fetched by the server and wrong
information would be updated in the database. A call can eb created for updating the cached
data and matching it with the new data in database and it should be assumed that the query is
success. The cache can also be invalidated with the Memcached delete function such that
subsequent fetching of cache can result in cache miss. As an alternative cache invalidation
strategy can be used for storing random number as an agreed entry for cache and
incorporating the number as a key and storing a particular entry type (Dao 2018). For
invalidating the entries at once the random number is needed to be changed and the existing
entries should not be referenced and expired or recycled.
Conclusion
From the above report it can be concluded that the Memcached servers are vulnerable
to DDoS attacks since some of the organization fails to implement basic security practice in
their organization. There is a need for identifying the threats acting on the business such that
the abuse of misconfigured Memcached server is eliminated and the organization is secured
from the future attacks. From researching on the risk it is identified that disabling the UDP
port in the Memcached server can help in reducing the risk. The Memcached server is needed
to be isolated from the internet for eliminating the risk associated with the denial of service
attacks. The attacks in future can be deflected by fixing the vulnerable protocol and IP
spoofing, if IP spoofing is permissible over the internet. The Memcached design architecture
is simple and can be deployed easily for solving different problems for management of large
data caches. It is an API which is available for different languages for increasing the
efficiency of a WEB application environment. Apart from the advantages there are different
disadvantages of application of Memcached because if the servers are not secured it can be
misused by hacker for causing distributed denial of service attacks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
CO4509 - COMPUTER SECURITY
References
Bremler-Barr, A., Hay, D., Moyal, I. and Schiff, L., 2017, June. Load balancing memcached
traffic using software defined networking. In 2017 IFIP Networking Conference (IFIP
Networking) and Workshops (pp. 1-9). IEEE.
Burke, I.D., Herbert, A. and Mooi, R., 2018, September. Using network flow data to analyse
distributed reflection denial of service (DRDoS) attacks, as observed on the South African
national research and education network (SANReN): a postmortem analysis of the
memcached attack on the SANReN. In Proceedings of the Annual Conference of the South
African Institute of Computer Scientists and Information Technologists (pp. 164-170). ACM.
Carra, D. and Michiardi, P., 2016. Memory Partitioning and Management in
Memcached. IEEE Transactions on Services Computing.
Cheng, W., Ren, F., Jiang, W. and Zhang, T., 2017, June. Modeling and Analyzing Latency
in the Memcached system. In 2017 IEEE 37th International Conference on Distributed
Computing Systems (ICDCS) (pp. 538-548). IEEE.
Choi, J., Lian, R., Li, Z., Canis, A. and Anderson, J., 2018, June. Accelerating Memcached
on AWS Cloud FPGAs. In Proceedings of the 9th International Symposium on Highly-
Efficient Accelerators and Reconfigurable Technologies (p. 2). ACM.
Dao, T.C., 2018, June. In-Memory Hadoop on Supercomputers Using Memcached-Like
Nodes for Data Storage Only. In 2018 IEEE 20th International Conference on High
Performance Computing and Communications; IEEE 16th International Conference on
Smart City; IEEE 4th International Conference on Data Science and Systems
(HPCC/SmartCity/DSS) (pp. 820-827). IEEE.
Fu, H., SinghaRoy, K., Venkata, M.G., Zhu, Y. and Yu, W., 2016, August. SHMemCache:
enabling memcached on the OpenSHMEM global address model. In Workshop on
OpenSHMEM and Related Technologies (pp. 131-145). Springer, Cham.
Gupta, P., Ahmad, R., Shrivastava, M., Kumar, P. and Sinha, M.K., 2017, July. Improve
performance of machine translation service using memcached. In 2017 17th International
Conference on Computational Science and Its Applications (ICCSA) (pp. 1-8). IEEE.
CO4509 - COMPUTER SECURITY
References
Bremler-Barr, A., Hay, D., Moyal, I. and Schiff, L., 2017, June. Load balancing memcached
traffic using software defined networking. In 2017 IFIP Networking Conference (IFIP
Networking) and Workshops (pp. 1-9). IEEE.
Burke, I.D., Herbert, A. and Mooi, R., 2018, September. Using network flow data to analyse
distributed reflection denial of service (DRDoS) attacks, as observed on the South African
national research and education network (SANReN): a postmortem analysis of the
memcached attack on the SANReN. In Proceedings of the Annual Conference of the South
African Institute of Computer Scientists and Information Technologists (pp. 164-170). ACM.
Carra, D. and Michiardi, P., 2016. Memory Partitioning and Management in
Memcached. IEEE Transactions on Services Computing.
Cheng, W., Ren, F., Jiang, W. and Zhang, T., 2017, June. Modeling and Analyzing Latency
in the Memcached system. In 2017 IEEE 37th International Conference on Distributed
Computing Systems (ICDCS) (pp. 538-548). IEEE.
Choi, J., Lian, R., Li, Z., Canis, A. and Anderson, J., 2018, June. Accelerating Memcached
on AWS Cloud FPGAs. In Proceedings of the 9th International Symposium on Highly-
Efficient Accelerators and Reconfigurable Technologies (p. 2). ACM.
Dao, T.C., 2018, June. In-Memory Hadoop on Supercomputers Using Memcached-Like
Nodes for Data Storage Only. In 2018 IEEE 20th International Conference on High
Performance Computing and Communications; IEEE 16th International Conference on
Smart City; IEEE 4th International Conference on Data Science and Systems
(HPCC/SmartCity/DSS) (pp. 820-827). IEEE.
Fu, H., SinghaRoy, K., Venkata, M.G., Zhu, Y. and Yu, W., 2016, August. SHMemCache:
enabling memcached on the OpenSHMEM global address model. In Workshop on
OpenSHMEM and Related Technologies (pp. 131-145). Springer, Cham.
Gupta, P., Ahmad, R., Shrivastava, M., Kumar, P. and Sinha, M.K., 2017, July. Improve
performance of machine translation service using memcached. In 2017 17th International
Conference on Computational Science and Its Applications (ICCSA) (pp. 1-8). IEEE.

11
CO4509 - COMPUTER SECURITY
Hydrasky.com. (2019). MEMCRASHED- Memcached DDoS Exploit Tool – All things in
moderation. [online] Available at: https://hydrasky.com/network-security/memcrashed-
memcached-ddos-exploit-tool/ [Accessed 23 Mar. 2019].
Li, Y., Wang, H., Zhao, X., Sun, H. and Zhang, T., 2016, October. Applying Software-based
Memory Error Correction for In-Memory Key-Value Store: Case Studies on Memcached and
RAMCloud. In Proceedings of the Second International Symposium on Memory Systems (pp.
268-278). ACM.
Liao, J. and Peng, X., 2017. A Data-Consistency Scheme for the Distributed-Cache Storage
of the Memcached System. Journal of Computing Science and Engineering, 11(3), pp.92-99.
Lu, X., Shankar, D. and Panda, D.K., 2017. Scalable and Distributed Key-Value Store-based
Data Management Using RDMA-Memcached. IEEE Data Eng. Bull., 40(1), pp.50-61.
Luo, Q., Zhang, Y., Guo, C. and Liu, J., 2016, December. Compression and De-calcification
for Memcached. In 2016 IEEE 18th International Conference on High Performance
Computing and Communications; IEEE 14th International Conference on Smart City; IEEE
2nd International Conference on Data Science and Systems (HPCC/SmartCity/DSS) (pp.
341-347). IEEE.
Marathe, V.J., Seltzer, M., Byan, S. and Harris, T., 2017. Persistent memcached: Bringing
legacy code to byte-addressable persistent memory. In 9th {USENIX} Workshop on Hot
Topics in Storage and File Systems (HotStorage 17).
Noise.getoto.net. (2018). XXEinjector – Automatic XXE Injection Tool For Exploitation |
Noise. [online] Available at: https://noise.getoto.net/2018/05/05/xxeinjector-automatic-xxe-
injection-tool-for-exploitation/ [Accessed 23 Mar. 2019].
Spear, M., Ruan, W., Liu, Y. and Vyas, T., 2015. Case study: Using transactions in
memcached. In Transactional Memory. Foundations, Algorithms, Tools, and
Applications (pp. 449-467). Springer, Cham.
CO4509 - COMPUTER SECURITY
Hydrasky.com. (2019). MEMCRASHED- Memcached DDoS Exploit Tool – All things in
moderation. [online] Available at: https://hydrasky.com/network-security/memcrashed-
memcached-ddos-exploit-tool/ [Accessed 23 Mar. 2019].
Li, Y., Wang, H., Zhao, X., Sun, H. and Zhang, T., 2016, October. Applying Software-based
Memory Error Correction for In-Memory Key-Value Store: Case Studies on Memcached and
RAMCloud. In Proceedings of the Second International Symposium on Memory Systems (pp.
268-278). ACM.
Liao, J. and Peng, X., 2017. A Data-Consistency Scheme for the Distributed-Cache Storage
of the Memcached System. Journal of Computing Science and Engineering, 11(3), pp.92-99.
Lu, X., Shankar, D. and Panda, D.K., 2017. Scalable and Distributed Key-Value Store-based
Data Management Using RDMA-Memcached. IEEE Data Eng. Bull., 40(1), pp.50-61.
Luo, Q., Zhang, Y., Guo, C. and Liu, J., 2016, December. Compression and De-calcification
for Memcached. In 2016 IEEE 18th International Conference on High Performance
Computing and Communications; IEEE 14th International Conference on Smart City; IEEE
2nd International Conference on Data Science and Systems (HPCC/SmartCity/DSS) (pp.
341-347). IEEE.
Marathe, V.J., Seltzer, M., Byan, S. and Harris, T., 2017. Persistent memcached: Bringing
legacy code to byte-addressable persistent memory. In 9th {USENIX} Workshop on Hot
Topics in Storage and File Systems (HotStorage 17).
Noise.getoto.net. (2018). XXEinjector – Automatic XXE Injection Tool For Exploitation |
Noise. [online] Available at: https://noise.getoto.net/2018/05/05/xxeinjector-automatic-xxe-
injection-tool-for-exploitation/ [Accessed 23 Mar. 2019].
Spear, M., Ruan, W., Liu, Y. and Vyas, T., 2015. Case study: Using transactions in
memcached. In Transactional Memory. Foundations, Algorithms, Tools, and
Applications (pp. 449-467). Springer, Cham.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





