CO4509 Computer Security Assignment: Memcrashed Vulnerability Report
VerifiedAdded on 2023/04/08
|11
|2518
|404
Report
AI Summary
This report provides a comprehensive analysis of the Memcrashed vulnerability, a significant threat in computer security. It begins by explaining the principles of key/value databases, crucial for understanding Memcached's functionality. The report then delves into the Memcrashed exploit, detailing how it leverages UDP packets and vulnerabilities in Memcached servers to launch devastating DDoS attacks. It also describes the exploit's mechanics, including IP spoofing and amplification techniques. Furthermore, the report explores various solutions and mitigation strategies to defend against Memcrashed, such as binding ports, implementing anti-spoofing measures (BCP38 & 84), and disabling UDP traffic. Finally, it offers predictions on the future importance and effectiveness of Memcrashed, considering the potential for continued attacks and the need for proactive security measures, emphasizing the importance of staying informed and implementing robust security practices to safeguard against this persistent threat. The report is a valuable resource for understanding and addressing the challenges posed by the Memcrashed exploit. This assignment is contributed by a student to be published on the website Desklib, a platform which provides all the necessary AI based study tools for students.

Running head: COMPUTER SECURITY
Computer Security
Name of the Student
Name of the University
Author Note:
Computer Security
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1COMPUTER SECURITY
Table of Contents
Introduction......................................................................................................................................2
Discussion........................................................................................................................................2
Principles of key/value databases...............................................................................................2
Description of Memcrashed Exploit............................................................................................4
Description of any solution to memcrashed Exploit....................................................................5
Future importance and effectiveness of memcrashed..................................................................7
Conclusion.......................................................................................................................................8
References........................................................................................................................................9
Table of Contents
Introduction......................................................................................................................................2
Discussion........................................................................................................................................2
Principles of key/value databases...............................................................................................2
Description of Memcrashed Exploit............................................................................................4
Description of any solution to memcrashed Exploit....................................................................5
Future importance and effectiveness of memcrashed..................................................................7
Conclusion.......................................................................................................................................8
References........................................................................................................................................9

2COMPUTER SECURITY
Introduction
Memcached protocol is a well-known mechanism which is required for assisting load
balancing of memory demands of large web services in the multiple servers. It is mainly done so
that server does not waste the allocated memory (Bhuyan, Bhattacharyya and Kalita, 2015). It is
very effective in nature and is used by various organization like Facebook for managing huge
quality of data. The Memcrashed incident comes into picture due to exploitation of Memcached
DDoS tool. It is completely written in Python language that allows the user to send forged UDP
packets to the server. It is completely obtained from Shodan. The vulnerability of this particular
attack is made possible due to the fact memcached server does not have any kind of
authentication on the port 11211 (Bawany, Shamsi and Salah 2017). Any kind of client can
establish connection and can generate commands without any kind of hesitation. Memory
injection technique can be used for proper amplification which is there in proof of concept
(POC) code.
The report mainly focuses on the key principles and value in the database. After that, a
list of description has been provided with respect to memcrashed exploit. A list of solution has
been provided for tackling the memcrashed exploit. The last section of the report deals with
future importance and effectiveness for memcrashed.
Discussion
Principles of key/value databases
Key-value database is considered to be very much effective in nature due to its design in
comparison to traditional RDBMS. Schema-less data are generally stored in key-value database.
In this particular kind of database, data is stored in the associative arrays (Xu and Liu 2016).
Introduction
Memcached protocol is a well-known mechanism which is required for assisting load
balancing of memory demands of large web services in the multiple servers. It is mainly done so
that server does not waste the allocated memory (Bhuyan, Bhattacharyya and Kalita, 2015). It is
very effective in nature and is used by various organization like Facebook for managing huge
quality of data. The Memcrashed incident comes into picture due to exploitation of Memcached
DDoS tool. It is completely written in Python language that allows the user to send forged UDP
packets to the server. It is completely obtained from Shodan. The vulnerability of this particular
attack is made possible due to the fact memcached server does not have any kind of
authentication on the port 11211 (Bawany, Shamsi and Salah 2017). Any kind of client can
establish connection and can generate commands without any kind of hesitation. Memory
injection technique can be used for proper amplification which is there in proof of concept
(POC) code.
The report mainly focuses on the key principles and value in the database. After that, a
list of description has been provided with respect to memcrashed exploit. A list of solution has
been provided for tackling the memcrashed exploit. The last section of the report deals with
future importance and effectiveness for memcrashed.
Discussion
Principles of key/value databases
Key-value database is considered to be very much effective in nature due to its design in
comparison to traditional RDBMS. Schema-less data are generally stored in key-value database.
In this particular kind of database, data is stored in the associative arrays (Xu and Liu 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3COMPUTER SECURITY
Data entries in the associative arrays are provided in the map table. Hash table or dictionary are
also known map tables. The associative arrays are nothing but collection of various kind of array
and pairs for data which is stored. The main function of associative array is to store the array that
binds the key and values in a together way.
Key-Value database is designed in such a way that it can store the required data in
document format (David and Thomas 2015). Key-Value database makes use of YAML, XML
and lastly JSON for handling of data in much better way.
It comes up with some typical operations like Set and deletes on the given data which is
stored in proper(Tapsell, Akram and Markantonakis 2018). Some of the main performance
factors of key-value database can be provided below:
Overall response time or latency of data access
Although the overall number of request can be satisfied in given period.
In the scenario of Memcached, it makes use of web service based system which has high
number of request of user in the given time. After gaining the user request by the help of key,
web services can gain access to the object from nearby cluster (Mousavi and St-Hilaire, 2015). If
anyhow the user can gain access to Memcached node, then it will be stated as cache hit. By the
help of this particular mechanism, user can gain access to real back-end database which is not
needed. All the expensive kind of disk input and output can be avoided.
Memcached server port that is 11211 is known to be open and UDP that is default
enabled for vulnerability. It allows the UDP packets in which return is allowed by small bytes
which are required to be sent (Ain et al. 2016). When memcached server tries to make reply to
the request it can sent back the IP addressed which is spoofed and made possible through packet
forgery. The request requires to be modified into a set of request of instruction data which is
Data entries in the associative arrays are provided in the map table. Hash table or dictionary are
also known map tables. The associative arrays are nothing but collection of various kind of array
and pairs for data which is stored. The main function of associative array is to store the array that
binds the key and values in a together way.
Key-Value database is designed in such a way that it can store the required data in
document format (David and Thomas 2015). Key-Value database makes use of YAML, XML
and lastly JSON for handling of data in much better way.
It comes up with some typical operations like Set and deletes on the given data which is
stored in proper(Tapsell, Akram and Markantonakis 2018). Some of the main performance
factors of key-value database can be provided below:
Overall response time or latency of data access
Although the overall number of request can be satisfied in given period.
In the scenario of Memcached, it makes use of web service based system which has high
number of request of user in the given time. After gaining the user request by the help of key,
web services can gain access to the object from nearby cluster (Mousavi and St-Hilaire, 2015). If
anyhow the user can gain access to Memcached node, then it will be stated as cache hit. By the
help of this particular mechanism, user can gain access to real back-end database which is not
needed. All the expensive kind of disk input and output can be avoided.
Memcached server port that is 11211 is known to be open and UDP that is default
enabled for vulnerability. It allows the UDP packets in which return is allowed by small bytes
which are required to be sent (Ain et al. 2016). When memcached server tries to make reply to
the request it can sent back the IP addressed which is spoofed and made possible through packet
forgery. The request requires to be modified into a set of request of instruction data which is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4COMPUTER SECURITY
stored. After that, the data is retrieved in one of the packets. By the help of Shodan API, this
particular technique can be used for storing data on large number of vulnerable Memcached
server. It will ultimately cause denial of service attack by which it can reach 1 terabyte per
second with minimum effort.
Description of Memcrashed Exploit
Memcrashed exploit can take place by forging packets through user datagram protocol.
An attacker can gain Memcached denial service vulnerability for initiation of record-breaking
DDoS attack (Hoque, Bhattacharyya and Kalita 2016). The biggest problem encountered in this
particular attack is forging of the given requirement. For proper working of the attack, the source
of Memcached server needs to be spoofed. The general idea behind all the amplification attack is
considered to be very similar in nature. An IP-spoofing attacker can send request to the
vulnerable UDP based server. UDP server does not understand the request which is forged
makes preparation for this particular response (Behal and Kumar 2017). This particular issue
comes into picture when large number of response is delivered to an unsuspecting host. It is all
about overwhelming of resources and more specifically the network.
DNS amplification based attack makes use of DNS reflection and amplification technique
which is needed for forming potent DDoS. Attacker spoof the IP spend a request to the UDP
server in this case of Memcached server. At this instance, DNS server responds back to the
victim, not to the host (Fouladi, Kayatas and Anarim 2016). It will ultimately result in draining
of target resources and resulting denial of service attack. The next part of this attack is
amplification of DNS. It is achieved by making use of vulnerabilities in the misconfigured
server-based attacks. It is all about the ability to change small query into a large one. The size of
query is around 15 bytes in size but it can trigger a response around 134 kb (Dong et al., 2016). It
stored. After that, the data is retrieved in one of the packets. By the help of Shodan API, this
particular technique can be used for storing data on large number of vulnerable Memcached
server. It will ultimately cause denial of service attack by which it can reach 1 terabyte per
second with minimum effort.
Description of Memcrashed Exploit
Memcrashed exploit can take place by forging packets through user datagram protocol.
An attacker can gain Memcached denial service vulnerability for initiation of record-breaking
DDoS attack (Hoque, Bhattacharyya and Kalita 2016). The biggest problem encountered in this
particular attack is forging of the given requirement. For proper working of the attack, the source
of Memcached server needs to be spoofed. The general idea behind all the amplification attack is
considered to be very similar in nature. An IP-spoofing attacker can send request to the
vulnerable UDP based server. UDP server does not understand the request which is forged
makes preparation for this particular response (Behal and Kumar 2017). This particular issue
comes into picture when large number of response is delivered to an unsuspecting host. It is all
about overwhelming of resources and more specifically the network.
DNS amplification based attack makes use of DNS reflection and amplification technique
which is needed for forming potent DDoS. Attacker spoof the IP spend a request to the UDP
server in this case of Memcached server. At this instance, DNS server responds back to the
victim, not to the host (Fouladi, Kayatas and Anarim 2016). It will ultimately result in draining
of target resources and resulting denial of service attack. The next part of this attack is
amplification of DNS. It is achieved by making use of vulnerabilities in the misconfigured
server-based attacks. It is all about the ability to change small query into a large one. The size of
query is around 15 bytes in size but it can trigger a response around 134 kb (Dong et al., 2016). It
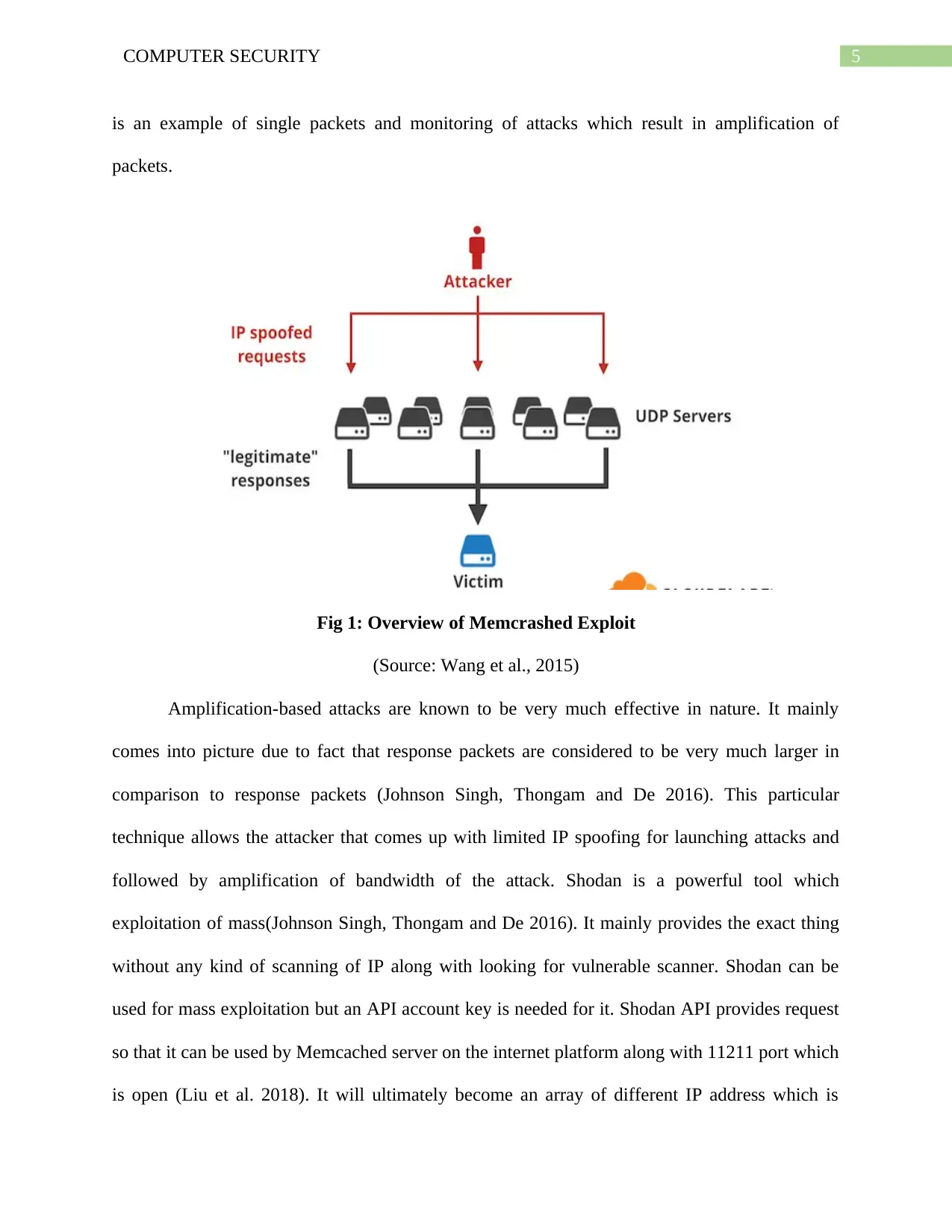
5COMPUTER SECURITY
is an example of single packets and monitoring of attacks which result in amplification of
packets.
Fig 1: Overview of Memcrashed Exploit
(Source: Wang et al., 2015)
Amplification-based attacks are known to be very much effective in nature. It mainly
comes into picture due to fact that response packets are considered to be very much larger in
comparison to response packets (Johnson Singh, Thongam and De 2016). This particular
technique allows the attacker that comes up with limited IP spoofing for launching attacks and
followed by amplification of bandwidth of the attack. Shodan is a powerful tool which
exploitation of mass(Johnson Singh, Thongam and De 2016). It mainly provides the exact thing
without any kind of scanning of IP along with looking for vulnerable scanner. Shodan can be
used for mass exploitation but an API account key is needed for it. Shodan API provides request
so that it can be used by Memcached server on the internet platform along with 11211 port which
is open (Liu et al. 2018). It will ultimately become an array of different IP address which is
is an example of single packets and monitoring of attacks which result in amplification of
packets.
Fig 1: Overview of Memcrashed Exploit
(Source: Wang et al., 2015)
Amplification-based attacks are known to be very much effective in nature. It mainly
comes into picture due to fact that response packets are considered to be very much larger in
comparison to response packets (Johnson Singh, Thongam and De 2016). This particular
technique allows the attacker that comes up with limited IP spoofing for launching attacks and
followed by amplification of bandwidth of the attack. Shodan is a powerful tool which
exploitation of mass(Johnson Singh, Thongam and De 2016). It mainly provides the exact thing
without any kind of scanning of IP along with looking for vulnerable scanner. Shodan can be
used for mass exploitation but an API account key is needed for it. Shodan API provides request
so that it can be used by Memcached server on the internet platform along with 11211 port which
is open (Liu et al. 2018). It will ultimately become an array of different IP address which is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6COMPUTER SECURITY
easily vulnerable server. Memcached server only requires proper authentication so that it can
establish connection and issue required commands.
Description of any solution to memcrashed Exploit
At present, two distinct proof of concept based attack code can be used for Memcached
amplification technique that has been released till date. It is very dangerous in nature because
any people can make use of this to launch Memcached based DDoS attack. One of the PoC based
code is written in Python scripting language that makes use of Shodan based API (Ghiëtte and
Doerr 2018). It is needed for updating the list of vulnerable in the Memcached server. On the
contrary, the second exploit code is completely written in C programming language. It makes use
of list of vulnerable Memcached server. Currently, there are two PoC exploits for Memcached
DDoS have been released till date. Various experts around the globe have come up with kill
switch mechanism for addressing the Memcached vulnerability (Tapsell, Akram and
Markantonakis 2018). Organization around the globe have come up with exploitation issues in
the memcached server that allows the user to make necessary modification for stealing data.
DDoS attacks are abusing the server of Memcached as much as possible in current
scenario. It is mainly done because of the fact organization have failed to implement some of the
basic security practices. In this particular attack, hackers can target the system and can send the
query to various server (Westoahu.hawaii.edu2019). Apart from this, the request can go around
50,000 bigger than the query which is provided to the server. In this way, malicious traffic can be
provided to the victim site. This particular kind of attack is considered to be reflection of attacks.
There are mainly three steps which can be taken for mitigating the attack like
Both the IP address and ports can be mitigated by binding the Memcached in proper way.
User needs to understand the fact that server is accessible by another user easily (Bhuyan,
easily vulnerable server. Memcached server only requires proper authentication so that it can
establish connection and issue required commands.
Description of any solution to memcrashed Exploit
At present, two distinct proof of concept based attack code can be used for Memcached
amplification technique that has been released till date. It is very dangerous in nature because
any people can make use of this to launch Memcached based DDoS attack. One of the PoC based
code is written in Python scripting language that makes use of Shodan based API (Ghiëtte and
Doerr 2018). It is needed for updating the list of vulnerable in the Memcached server. On the
contrary, the second exploit code is completely written in C programming language. It makes use
of list of vulnerable Memcached server. Currently, there are two PoC exploits for Memcached
DDoS have been released till date. Various experts around the globe have come up with kill
switch mechanism for addressing the Memcached vulnerability (Tapsell, Akram and
Markantonakis 2018). Organization around the globe have come up with exploitation issues in
the memcached server that allows the user to make necessary modification for stealing data.
DDoS attacks are abusing the server of Memcached as much as possible in current
scenario. It is mainly done because of the fact organization have failed to implement some of the
basic security practices. In this particular attack, hackers can target the system and can send the
query to various server (Westoahu.hawaii.edu2019). Apart from this, the request can go around
50,000 bigger than the query which is provided to the server. In this way, malicious traffic can be
provided to the victim site. This particular kind of attack is considered to be reflection of attacks.
There are mainly three steps which can be taken for mitigating the attack like
Both the IP address and ports can be mitigated by binding the Memcached in proper way.
User needs to understand the fact that server is accessible by another user easily (Bhuyan,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7COMPUTER SECURITY
Bhattacharyya and Kalita, 2015). It is mainly done so that it is public less accessible by
users.
The fact needs to be taken into account that upstream provider is linked to failure so that
the primary one is flooded.
User needs to implement BCP38 & 84 which is anti-spoofing method. It is mainly done
so that user can have spoofed attack which is used in DDoS attack(Fouladi, Kayatas and
Anarim 2016).
Future importance and effectiveness of men crashed
In the upcoming days, the fact can be taken into account that the problem does not go
away easily (Bawany, Shamsi and Salah 2017). It is because of the fact that it is publically
exposed and poorly configured server. The attack makes use of shoddily secured Memcached
server database server which is required for amplifying against the given target (Hoque,
Bhattacharyya and Kalita 2016). UDP can address the spoof of victim and can address a small
packet in the Memcached server. It does not require any kind of authenticated traffic need in the
given place. Server can easily respond by firing back around 50,000 times in case if the data is
received (Xu and Liu 2016). Memcached DDoS attack can work at a time clocking rate of 1.7
tbsp. At present, there are some mitigation techniques like blocking UDP traffic from port
number of 11211. It is the default traffic for Memcached server. Apart from this, operators of
Memcached server needs to look down their system so that they can avoid any kind of denial of
service attack.
On 28 Feb 2018 GitHub has encountered an attack which is around 1.35 terabytes per
second (David and Thomas 2015). It is considered to be as one of the most powerful attacks till
date. Smaller attacks can occur but these will be testing attack vector which focuses on smaller
Bhattacharyya and Kalita, 2015). It is mainly done so that it is public less accessible by
users.
The fact needs to be taken into account that upstream provider is linked to failure so that
the primary one is flooded.
User needs to implement BCP38 & 84 which is anti-spoofing method. It is mainly done
so that user can have spoofed attack which is used in DDoS attack(Fouladi, Kayatas and
Anarim 2016).
Future importance and effectiveness of men crashed
In the upcoming days, the fact can be taken into account that the problem does not go
away easily (Bawany, Shamsi and Salah 2017). It is because of the fact that it is publically
exposed and poorly configured server. The attack makes use of shoddily secured Memcached
server database server which is required for amplifying against the given target (Hoque,
Bhattacharyya and Kalita 2016). UDP can address the spoof of victim and can address a small
packet in the Memcached server. It does not require any kind of authenticated traffic need in the
given place. Server can easily respond by firing back around 50,000 times in case if the data is
received (Xu and Liu 2016). Memcached DDoS attack can work at a time clocking rate of 1.7
tbsp. At present, there are some mitigation techniques like blocking UDP traffic from port
number of 11211. It is the default traffic for Memcached server. Apart from this, operators of
Memcached server needs to look down their system so that they can avoid any kind of denial of
service attack.
On 28 Feb 2018 GitHub has encountered an attack which is around 1.35 terabytes per
second (David and Thomas 2015). It is considered to be as one of the most powerful attacks till
date. Smaller attacks can occur but these will be testing attack vector which focuses on smaller

8COMPUTER SECURITY
scale application. GitHub is a well-known example about the fact that how attacks have effect on
DDoS attack in their field with the amount of Memcached server in different region of the world
(Mousavi and St-Hilaire, 2015). It is expected that there will more DDoS attack in the near
future.
In the coming days, there are few steps that should be taken for preventing Memcached
server from use in DDoS attack like
UDP port needs to be disabled if it is not in use.
Firewalls servers from the internet platform.
User should not develop by making use of UDP.
ISP need to fix the vulnerable protocols and IP spoofing.
Conclusion
The above pages of the report help in concluding the fact that this report is all about
memcrashed attack. DDoS attack is considered to appear suddenly and effective operation of halt
operation in the given time. With the passage of time, developers, system administrator, and
lastly internet service providers are becoming very much aware of the issue. Memcached server
needs to be fixed so that they can reduce the attack vector. This particular attack is considered to
be operational plan which is required for handling and recovery of effective downtime and
associated damages. The number of vulnerability of Memcached server through Shodan which
has dropped from 100,000 to 40,000. In the coming days, it can be expected that the number will
continue to drop. For mitigating the attack, a list of steps can be easily taken.
scale application. GitHub is a well-known example about the fact that how attacks have effect on
DDoS attack in their field with the amount of Memcached server in different region of the world
(Mousavi and St-Hilaire, 2015). It is expected that there will more DDoS attack in the near
future.
In the coming days, there are few steps that should be taken for preventing Memcached
server from use in DDoS attack like
UDP port needs to be disabled if it is not in use.
Firewalls servers from the internet platform.
User should not develop by making use of UDP.
ISP need to fix the vulnerable protocols and IP spoofing.
Conclusion
The above pages of the report help in concluding the fact that this report is all about
memcrashed attack. DDoS attack is considered to appear suddenly and effective operation of halt
operation in the given time. With the passage of time, developers, system administrator, and
lastly internet service providers are becoming very much aware of the issue. Memcached server
needs to be fixed so that they can reduce the attack vector. This particular attack is considered to
be operational plan which is required for handling and recovery of effective downtime and
associated damages. The number of vulnerability of Memcached server through Shodan which
has dropped from 100,000 to 40,000. In the coming days, it can be expected that the number will
continue to drop. For mitigating the attack, a list of steps can be easily taken.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9COMPUTER SECURITY
References
Ain, A., Bhuyan, M.H., Bhattacharyya, D.K. and Kalita, J.K., 2016. Rank Correlation for Low-
Rate DDoS Attack Detection: An Empirical Evaluation. IJ Network Security, 18(3), pp.474-480.
Bawany, N.Z., Shamsi, J.A. and Salah, K., 2017. DDoS attack detection and mitigation using
SDN: methods, practices, and solutions. Arabian Journal for Science and Engineering, 42(2),
pp.425-441.
Behal, S. and Kumar, K., 2017. Characterization and Comparison of DDoS Attack Tools and
Traffic Generators: A Review. IJ Network Security, 19(3), pp.383-393.
Bhuyan, M.H., Bhattacharyya, D.K. and Kalita, J.K., 2015. An empirical evaluation of
information metrics for low-rate and high-rate DDoS attack detection. Pattern Recognition
Letters, 51, pp.1-7.
David, J. and Thomas, C., 2015. DDoS attack detection using fast entropy approach on flow-
based network traffic. Procedia Computer Science, 50, pp.30-36.
Dong, P., Du, X., Zhang, H. and Xu, T., 2016, May. A detection method for a novel DDoS attack
against SDN controllers by vast new low-traffic flows. In 2016 IEEE International Conference
on Communications (ICC) (pp. 1-6). IEEE.
Fouladi, R.F., Kayatas, C.E. and Anarim, E., 2016, June. Frequency based DDoS attack
detection approach using naive Bayes classification. In 2016 39th International Conference on
Telecommunications and Signal Processing (TSP) (pp. 104-107). IEEE.
Ghiëtte, V. and Doerr, C., 2018, August. How Media Reports Trigger Copycats: An Analysis of
the Brewing of the Largest Packet Storm to Date. In Proceedings of the 2018 Workshop on
Traffic Measurements for Cybersecurity (pp. 8-13). ACM.
References
Ain, A., Bhuyan, M.H., Bhattacharyya, D.K. and Kalita, J.K., 2016. Rank Correlation for Low-
Rate DDoS Attack Detection: An Empirical Evaluation. IJ Network Security, 18(3), pp.474-480.
Bawany, N.Z., Shamsi, J.A. and Salah, K., 2017. DDoS attack detection and mitigation using
SDN: methods, practices, and solutions. Arabian Journal for Science and Engineering, 42(2),
pp.425-441.
Behal, S. and Kumar, K., 2017. Characterization and Comparison of DDoS Attack Tools and
Traffic Generators: A Review. IJ Network Security, 19(3), pp.383-393.
Bhuyan, M.H., Bhattacharyya, D.K. and Kalita, J.K., 2015. An empirical evaluation of
information metrics for low-rate and high-rate DDoS attack detection. Pattern Recognition
Letters, 51, pp.1-7.
David, J. and Thomas, C., 2015. DDoS attack detection using fast entropy approach on flow-
based network traffic. Procedia Computer Science, 50, pp.30-36.
Dong, P., Du, X., Zhang, H. and Xu, T., 2016, May. A detection method for a novel DDoS attack
against SDN controllers by vast new low-traffic flows. In 2016 IEEE International Conference
on Communications (ICC) (pp. 1-6). IEEE.
Fouladi, R.F., Kayatas, C.E. and Anarim, E., 2016, June. Frequency based DDoS attack
detection approach using naive Bayes classification. In 2016 39th International Conference on
Telecommunications and Signal Processing (TSP) (pp. 104-107). IEEE.
Ghiëtte, V. and Doerr, C., 2018, August. How Media Reports Trigger Copycats: An Analysis of
the Brewing of the Largest Packet Storm to Date. In Proceedings of the 2018 Workshop on
Traffic Measurements for Cybersecurity (pp. 8-13). ACM.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10COMPUTER SECURITY
Hoque, N., Bhattacharyya, D.K. and Kalita, J.K., 2016, January. A novel measure for low-rate
and high-rate DDoS attack detection using multivariate data analysis. In 2016 8th International
Conference on Communication Systems and Networks (COMSNETS) (pp. 1-2). IEEE.
Johnson Singh, K., Thongam, K. and De, T., 2016. Entropy-based application layer DDoS attack
detection using artificial neural networks. Entropy, 18(10), p.350.
Liu, Z., Jin, H., Hu, Y.C. and Bailey, M., 2018. Practical proactive DDoS-attack mitigation via
endpoint-driven in-network traffic control. IEEE/ACM Transactions on Networking, 26(4),
pp.1948-1961.
Mousavi, S.M. and St-Hilaire, M., 2015, February. Early detection of DDoS attacks against SDN
controllers. In 2015 International Conference on Computing, Networking and Communications
(ICNC) (pp. 77-81). IEEE.
Tapsell, J., Akram, R.N. and Markantonakis, K., 2018. An evaluation of the security of the
Bitcoin Peer-to-Peer Network. arXiv preprint arXiv:1805.10259.
Wang, B., Zheng, Y., Lou, W. and Hou, Y.T., 2015. DDoS attack protection in the era of cloud
computing and software-defined networking. Computer Networks, 81, pp.308-319.
Westoahu.hawaii.edu. (2019). Memcached Server Attacks – UHWO Cyber Security. [online]
Available at: https://westoahu.hawaii.edu/cyber/memcached-server-attacks/ [Accessed 19 Mar.
2019].
Xu, Y. and Liu, Y., 2016, April. DDoS attack detection under SDN context. In IEEE INFOCOM
2016-The 35th Annual IEEE International Conference on Computer Communications (pp. 1-9).
IEEE.
Hoque, N., Bhattacharyya, D.K. and Kalita, J.K., 2016, January. A novel measure for low-rate
and high-rate DDoS attack detection using multivariate data analysis. In 2016 8th International
Conference on Communication Systems and Networks (COMSNETS) (pp. 1-2). IEEE.
Johnson Singh, K., Thongam, K. and De, T., 2016. Entropy-based application layer DDoS attack
detection using artificial neural networks. Entropy, 18(10), p.350.
Liu, Z., Jin, H., Hu, Y.C. and Bailey, M., 2018. Practical proactive DDoS-attack mitigation via
endpoint-driven in-network traffic control. IEEE/ACM Transactions on Networking, 26(4),
pp.1948-1961.
Mousavi, S.M. and St-Hilaire, M., 2015, February. Early detection of DDoS attacks against SDN
controllers. In 2015 International Conference on Computing, Networking and Communications
(ICNC) (pp. 77-81). IEEE.
Tapsell, J., Akram, R.N. and Markantonakis, K., 2018. An evaluation of the security of the
Bitcoin Peer-to-Peer Network. arXiv preprint arXiv:1805.10259.
Wang, B., Zheng, Y., Lou, W. and Hou, Y.T., 2015. DDoS attack protection in the era of cloud
computing and software-defined networking. Computer Networks, 81, pp.308-319.
Westoahu.hawaii.edu. (2019). Memcached Server Attacks – UHWO Cyber Security. [online]
Available at: https://westoahu.hawaii.edu/cyber/memcached-server-attacks/ [Accessed 19 Mar.
2019].
Xu, Y. and Liu, Y., 2016, April. DDoS attack detection under SDN context. In IEEE INFOCOM
2016-The 35th Annual IEEE International Conference on Computer Communications (pp. 1-9).
IEEE.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




