ICT287 Computer Security: Attack Surface and Legacy Code Analysis
VerifiedAdded on 2022/12/27
|5
|1084
|51
Report
AI Summary
This report analyzes the computer security vulnerabilities of "Planet of the Grapes," a local wine and spirit merchant. The report identifies network-level attacks stemming from remote access services, including the CVE-2019-0708 vulnerability in Remote Desktop Services and potential exploits of Cisco ADSL routers. It also addresses physical attack surfaces, highlighting weaknesses in physical security and the potential for social engineering. Furthermore, the report examines legacy code vulnerabilities, specifically focusing on buffer overflow issues in the credit card verification software, offering recommendations such as staff training, alternative programming languages, and the deployment of security tools to mitigate these risks. The report provides references to support its findings and recommendations.

Name of University
Computer Security
Student Name
Course Name
Submission Date
Computer Security
Student Name
Course Name
Submission Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ATTACK SURFACE MODELLING
Attack surface is a point on a network system at which an attacker can exploit to gain
access in order to perform security violation. Attack surfaces are categorised as network attack
surface, software attack surface and human attack surface (Misra and Sumit, 2017). Network
attack surfaces are launched through the networks. Software attack surface is made up of the
source code and functionalities of software. Human attack surface are usually led by
unauthenticated users. Planet of the Grapes is vulnerable to both digital and physical attack
surfaces.
Network level attacks
These attacks are aimed at exploiting basic network protocols in order to gain access to a
system. One of the network surface attacks at Planet of the Grapes network is the user's remote
access services. According to a report by Microsoft (2019), remote code execution vulnerability
exists in Remote Desktop Services that when exploited, it can allow an attacker to execute
random code on the objective system. This vulnerability has been documented at CVE-2019-
0708. In addition, the remote access service opens up a lot of loop holes in the system since
most of the computers are configured to default user accounts -Admin and User. This can open
up attacks such as Man-in-the Middle Attacks (MiTM) and Denial of Service (Network Level
Authentication). The lack of specific user accounts exposes the network to an array of issues if
one account is compromised. Audit trail also becomes an issue since there is no central
administrative control. This could have been implemented by utilizing Active Directory security
features.
Another network surface attack is exploiting Cisco ADSL Routers CVE-2017-11587
Directory Traversal Vulnerability. This vulnerability can allow an attackers to send crafted
requests with directory-traversal sequences ('../') to read random files in the setting of the system
which may help the intruder in additional attacks. Local computers should also be well
configured to mitigate exploitation of know default setting like admin, root and user default
accounts.
Attack surface is a point on a network system at which an attacker can exploit to gain
access in order to perform security violation. Attack surfaces are categorised as network attack
surface, software attack surface and human attack surface (Misra and Sumit, 2017). Network
attack surfaces are launched through the networks. Software attack surface is made up of the
source code and functionalities of software. Human attack surface are usually led by
unauthenticated users. Planet of the Grapes is vulnerable to both digital and physical attack
surfaces.
Network level attacks
These attacks are aimed at exploiting basic network protocols in order to gain access to a
system. One of the network surface attacks at Planet of the Grapes network is the user's remote
access services. According to a report by Microsoft (2019), remote code execution vulnerability
exists in Remote Desktop Services that when exploited, it can allow an attacker to execute
random code on the objective system. This vulnerability has been documented at CVE-2019-
0708. In addition, the remote access service opens up a lot of loop holes in the system since
most of the computers are configured to default user accounts -Admin and User. This can open
up attacks such as Man-in-the Middle Attacks (MiTM) and Denial of Service (Network Level
Authentication). The lack of specific user accounts exposes the network to an array of issues if
one account is compromised. Audit trail also becomes an issue since there is no central
administrative control. This could have been implemented by utilizing Active Directory security
features.
Another network surface attack is exploiting Cisco ADSL Routers CVE-2017-11587
Directory Traversal Vulnerability. This vulnerability can allow an attackers to send crafted
requests with directory-traversal sequences ('../') to read random files in the setting of the system
which may help the intruder in additional attacks. Local computers should also be well
configured to mitigate exploitation of know default setting like admin, root and user default
accounts.

Physical attacks
Physical attack surface target access to network endpoint devices, including desktop
systems, laptops, mobile devices, USB ports and improperly discarded hard drives. Physical
attack surface can be exploited through inside threats such us employees and social engineering.
Planet of the Grapes has a very weak physical security. It is very highly vulnerable to social
engineering attack, break in and theft. Attackers can be-friend casual and even fulltime staff to
manipulate them into giving out their login credentials. In addition, there is not proper control on
physical access to computers within the network. The company needs to put in place door access
security measure to make sure that only those staff with access can get to the back office. Servers
should be kept away from general working area and the area should always be locked and
monitored. Sharing of user accounts should not be allowed at any moment. This can encourage
data theft, sabotage and social engineering. There should be a central administrative security
control in place to mitigate this. This can easily be implemented through installation of Active
Directory features.
LEGACY CODE
The credit card verification software is prone to buffer overflow vulnerability. This is a
vulnerability that happens when someone sends data to a process that is greater than the input
variable is able to contain. The additional input information overflows the program's input buffer
and overwrites another part of the program's memory space. This can lead to exploitation of
other variables in the platform leading to unforeseen modification in the program's behaviour.
Buffer overflow can be manifested as stack buffer overflow, NOP Sled attack, heap overflow or
jump-to-register attack.
In C language, this attack is targeted to strcpy, gets, scanf, sprintf and strcat library
function where the sizes of strings are not verified (Olivier et al, 2015). An attacker will
essentially exploit these functions by handling unrestricted, external input to the running
program as trustworthy data (Mark and Peter, 2010). The library function gets does not check for
buffer length and can be exploited. Also strcpy, strcpy, strcat and strcmp functions do not check
buffer lengths and may very well overwrite memory zone contiguous to the intended destination.
Upon exploitation, an attacker can cause the credit card program to crash, corrupt credit card
Physical attack surface target access to network endpoint devices, including desktop
systems, laptops, mobile devices, USB ports and improperly discarded hard drives. Physical
attack surface can be exploited through inside threats such us employees and social engineering.
Planet of the Grapes has a very weak physical security. It is very highly vulnerable to social
engineering attack, break in and theft. Attackers can be-friend casual and even fulltime staff to
manipulate them into giving out their login credentials. In addition, there is not proper control on
physical access to computers within the network. The company needs to put in place door access
security measure to make sure that only those staff with access can get to the back office. Servers
should be kept away from general working area and the area should always be locked and
monitored. Sharing of user accounts should not be allowed at any moment. This can encourage
data theft, sabotage and social engineering. There should be a central administrative security
control in place to mitigate this. This can easily be implemented through installation of Active
Directory features.
LEGACY CODE
The credit card verification software is prone to buffer overflow vulnerability. This is a
vulnerability that happens when someone sends data to a process that is greater than the input
variable is able to contain. The additional input information overflows the program's input buffer
and overwrites another part of the program's memory space. This can lead to exploitation of
other variables in the platform leading to unforeseen modification in the program's behaviour.
Buffer overflow can be manifested as stack buffer overflow, NOP Sled attack, heap overflow or
jump-to-register attack.
In C language, this attack is targeted to strcpy, gets, scanf, sprintf and strcat library
function where the sizes of strings are not verified (Olivier et al, 2015). An attacker will
essentially exploit these functions by handling unrestricted, external input to the running
program as trustworthy data (Mark and Peter, 2010). The library function gets does not check for
buffer length and can be exploited. Also strcpy, strcpy, strcat and strcmp functions do not check
buffer lengths and may very well overwrite memory zone contiguous to the intended destination.
Upon exploitation, an attacker can cause the credit card program to crash, corrupt credit card
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
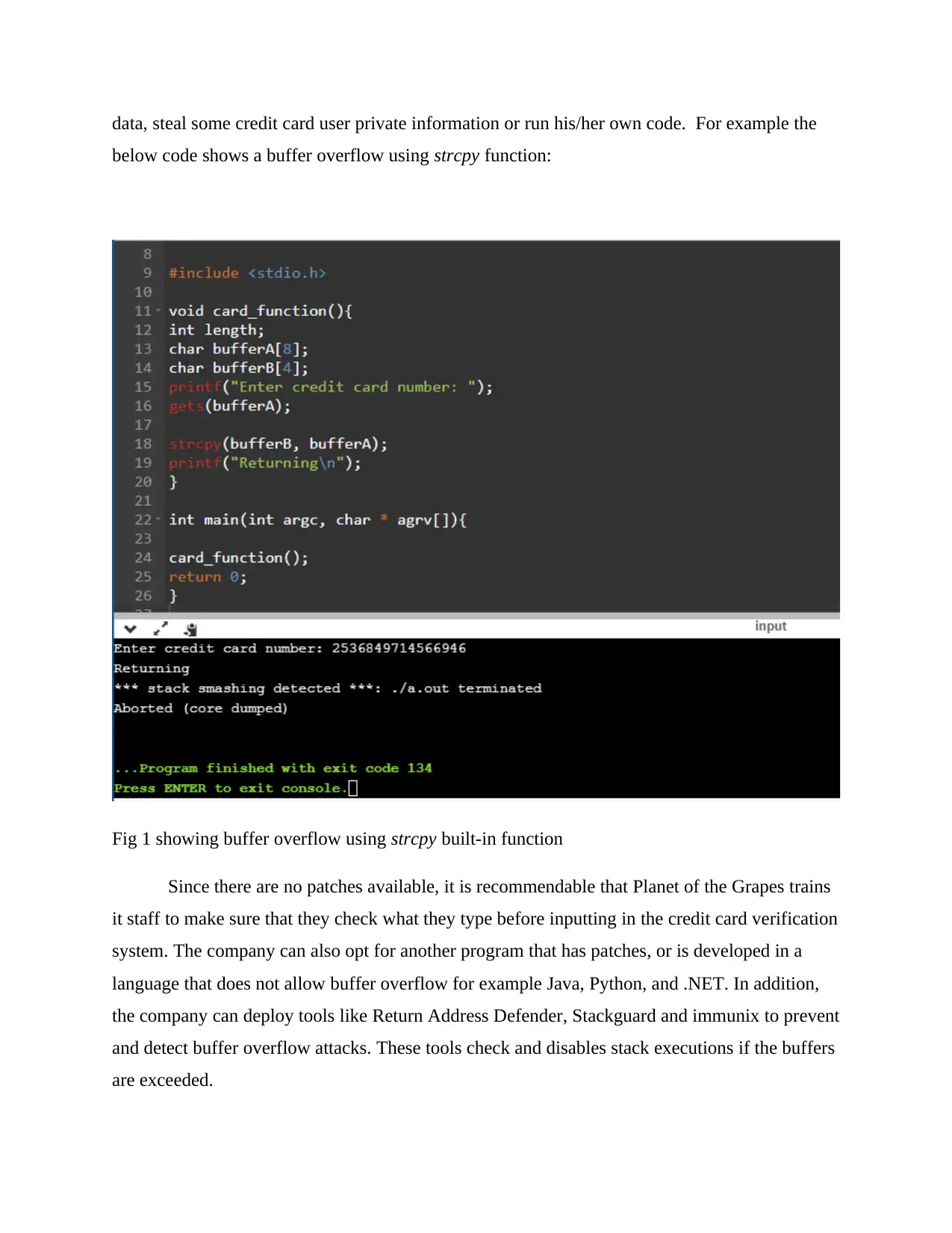
data, steal some credit card user private information or run his/her own code. For example the
below code shows a buffer overflow using strcpy function:
Fig 1 showing buffer overflow using strcpy built-in function
Since there are no patches available, it is recommendable that Planet of the Grapes trains
it staff to make sure that they check what they type before inputting in the credit card verification
system. The company can also opt for another program that has patches, or is developed in a
language that does not allow buffer overflow for example Java, Python, and .NET. In addition,
the company can deploy tools like Return Address Defender, Stackguard and immunix to prevent
and detect buffer overflow attacks. These tools check and disables stack executions if the buffers
are exceeded.
below code shows a buffer overflow using strcpy function:
Fig 1 showing buffer overflow using strcpy built-in function
Since there are no patches available, it is recommendable that Planet of the Grapes trains
it staff to make sure that they check what they type before inputting in the credit card verification
system. The company can also opt for another program that has patches, or is developed in a
language that does not allow buffer overflow for example Java, Python, and .NET. In addition,
the company can deploy tools like Return Address Defender, Stackguard and immunix to prevent
and detect buffer overflow attacks. These tools check and disables stack executions if the buffers
are exceeded.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Cisco (2017). Multiple Cisco ADSL Routers CVE-2017-11587 Directory Traversal Vulnerability
Published Aug 23 2017. Retrieved from https://www.securityfocus.com/bid/100484/info
Mark S., Peter S. (2010). Handbook of Information and Communication Security. New York.
Springer Science & Business Media
Microsoft (2019). CVE-2019-0708 Remote Desktop Services Remote Code Execution
Vulnerability Security Vulnerability. Published 05/14/2019. Retrieved 13 June 2019 from
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-0708
Misra S., Sumit G. (2017). Network Routing: Fundamentals, Applications, and Emerging
Technologies. United Kingdom, John Wiley & Sons
Olivier C., José C., Slimane H., Leszek M., Joaquim F. (2015). Enterprise Information Systems:
16th International Conference, ICEIS 2014, Lisbon, Portugal, April 27-30, 2014, Revised
Selected Papers
Cisco (2017). Multiple Cisco ADSL Routers CVE-2017-11587 Directory Traversal Vulnerability
Published Aug 23 2017. Retrieved from https://www.securityfocus.com/bid/100484/info
Mark S., Peter S. (2010). Handbook of Information and Communication Security. New York.
Springer Science & Business Media
Microsoft (2019). CVE-2019-0708 Remote Desktop Services Remote Code Execution
Vulnerability Security Vulnerability. Published 05/14/2019. Retrieved 13 June 2019 from
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-0708
Misra S., Sumit G. (2017). Network Routing: Fundamentals, Applications, and Emerging
Technologies. United Kingdom, John Wiley & Sons
Olivier C., José C., Slimane H., Leszek M., Joaquim F. (2015). Enterprise Information Systems:
16th International Conference, ICEIS 2014, Lisbon, Portugal, April 27-30, 2014, Revised
Selected Papers
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





