Detailed Security Vulnerability Assessment Report for WidgetsInc VM
VerifiedAdded on 2023/01/06
|23
|3636
|97
Report
AI Summary
This report details a security vulnerability assessment of the WidgetsInc virtual machine image. The assessment utilizes Kali Linux and various tools, including Nmap, Masscan, Metasploit, and Nikto, to identify security issues. The methodology includes information gathering, port scanning, web scanning, and SQL injection attempts. The report highlights vulnerabilities related to authentication, authorization, and access controls, such as those found in the ProFTPD service and the distCC daemon. Results show open ports, identified services, and potential exploit paths. The report concludes with recommendations to address the identified vulnerabilities and improve the overall security posture of the virtual machine, which can help the company eliminate the different vulnerability issues and develop their new web-based store.

Running head: COMPUTERS SECURITY
Computer Security
Name of the Student
Name of the University
Author’s Note
Computer Security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
COMPUTERS SECURITY
Executive Summary
The report is prepared for analysis of the security vulnerability of the WidgetsInc virtual machine
image that has been provided for evaluation. For performing the vulnerability test we have
selected kali linux and different tools to identify the security issue with the image. The report
provides a shot description of each of the process performed for the evaluation of vulnerability.
The results that are obtained from the tests are described and the security issues are addressed
that can help the company to eliminate the different vulnerability issues and develop their new
web-based store.
COMPUTERS SECURITY
Executive Summary
The report is prepared for analysis of the security vulnerability of the WidgetsInc virtual machine
image that has been provided for evaluation. For performing the vulnerability test we have
selected kali linux and different tools to identify the security issue with the image. The report
provides a shot description of each of the process performed for the evaluation of vulnerability.
The results that are obtained from the tests are described and the security issues are addressed
that can help the company to eliminate the different vulnerability issues and develop their new
web-based store.

2
COMPUTERS SECURITY
Table of Contents
Overview..........................................................................................................................................3
Summary of Results.........................................................................................................................3
Methodology....................................................................................................................................4
Scope............................................................................................................................................4
Information Gathering.................................................................................................................5
IP and MAC Address...................................................................................................................6
Virtual Host.................................................................................................................................7
Scanning......................................................................................................................................8
Port Scan..................................................................................................................................8
Framework.............................................................................................................................12
WEB Scan..............................................................................................................................14
SQL Injection Scan................................................................................................................17
Test Logs.......................................................................................................................................17
Result and Recommendations........................................................................................................19
Bibliography..................................................................................................................................20
COMPUTERS SECURITY
Table of Contents
Overview..........................................................................................................................................3
Summary of Results.........................................................................................................................3
Methodology....................................................................................................................................4
Scope............................................................................................................................................4
Information Gathering.................................................................................................................5
IP and MAC Address...................................................................................................................6
Virtual Host.................................................................................................................................7
Scanning......................................................................................................................................8
Port Scan..................................................................................................................................8
Framework.............................................................................................................................12
WEB Scan..............................................................................................................................14
SQL Injection Scan................................................................................................................17
Test Logs.......................................................................................................................................17
Result and Recommendations........................................................................................................19
Bibliography..................................................................................................................................20
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
COMPUTERS SECURITY
Overview
Ethical hacking is used for performing the attack on the virtual machine of WidgetInc and
finding the security weakness of the computer system and handling the attacked environment.
For performing the test different types of attacks are performed on the host and the result of the
attack are observed for identification of the weak point that can compromise the victim Virtual
Machine. Flags are used for penetrating as root user, other normal users for the exploitation of
the configuration issues and finding desired vulnerability.
The report demonstrates the testing logs, results and recommendation that was used for
compromising the security of the targeted host.
Summary of Results
After performing the penetration testing the victim virtual machine is found to be
vulnerable to different types of network attacks that are related to authentication, authorization
and access controls. Authentication using non-plaintext as for example DIGEST-MD5 resulted in
increasing the possibility of unauthroised access for the web application and have a negative
impact on the user data residing in the database of the server. The services that are available for
the users are examined thoroughly with the use of payloads, encoders, exploits and encoders. A
documented security weakness is used by the module for the execution of arbitrary commands
for the targeted victim and run distCC daemon command without checking authorization.
The service named ProFTPD that is used for enhancing the FTP server and feature of
Apache configuration syntax contains the different virtual, anonymous and permission based
FTP servers that is used for the test and the favorable output is documented.
COMPUTERS SECURITY
Overview
Ethical hacking is used for performing the attack on the virtual machine of WidgetInc and
finding the security weakness of the computer system and handling the attacked environment.
For performing the test different types of attacks are performed on the host and the result of the
attack are observed for identification of the weak point that can compromise the victim Virtual
Machine. Flags are used for penetrating as root user, other normal users for the exploitation of
the configuration issues and finding desired vulnerability.
The report demonstrates the testing logs, results and recommendation that was used for
compromising the security of the targeted host.
Summary of Results
After performing the penetration testing the victim virtual machine is found to be
vulnerable to different types of network attacks that are related to authentication, authorization
and access controls. Authentication using non-plaintext as for example DIGEST-MD5 resulted in
increasing the possibility of unauthroised access for the web application and have a negative
impact on the user data residing in the database of the server. The services that are available for
the users are examined thoroughly with the use of payloads, encoders, exploits and encoders. A
documented security weakness is used by the module for the execution of arbitrary commands
for the targeted victim and run distCC daemon command without checking authorization.
The service named ProFTPD that is used for enhancing the FTP server and feature of
Apache configuration syntax contains the different virtual, anonymous and permission based
FTP servers that is used for the test and the favorable output is documented.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
COMPUTERS SECURITY
Kali Linux offers different type of security tools for analyzing the potential problem and
vulnerabilities of a host by bypassing password security, cracking tools and recovering the
password from the stored data. The packages available in Kali Linux is a mixture of different
algorithm and cracking strategies like brute force, dictionary attack and is found to be most
productive in penetration testing.
The vulnerability of the Web server is tested for finding the problems with software and
server misconfigurations. A checking is done on the default files and programs that are outdated
and is vulnerable to different types of network attacks.
Methodology
Multiple number of steps are performed for beginning the scope of vulnerability test and
is ended with reporting the output of the test. A self-performing test is used with the modes that
can be used by the attacker for controlling the execution of different types of attack and prevent
it from harming the system (Hall and Watson 2016). The approach of vulnerability test is not
limited to automated and manual scans and finding the verification. The false positives and the
error in outputs can be eliminated with the implementation of manual scanning and verification
of the configurations.
Scope
The scope of performing the vulnerability test on the VMware image to gather
information about the security configuration and services. Since no information is provided
about the virtual image it falls under Gray box testing category multiple tools are used for
gathering information about the image file (Regalado et al. 2015). The network adapter in
COMPUTERS SECURITY
Kali Linux offers different type of security tools for analyzing the potential problem and
vulnerabilities of a host by bypassing password security, cracking tools and recovering the
password from the stored data. The packages available in Kali Linux is a mixture of different
algorithm and cracking strategies like brute force, dictionary attack and is found to be most
productive in penetration testing.
The vulnerability of the Web server is tested for finding the problems with software and
server misconfigurations. A checking is done on the default files and programs that are outdated
and is vulnerable to different types of network attacks.
Methodology
Multiple number of steps are performed for beginning the scope of vulnerability test and
is ended with reporting the output of the test. A self-performing test is used with the modes that
can be used by the attacker for controlling the execution of different types of attack and prevent
it from harming the system (Hall and Watson 2016). The approach of vulnerability test is not
limited to automated and manual scans and finding the verification. The false positives and the
error in outputs can be eliminated with the implementation of manual scanning and verification
of the configurations.
Scope
The scope of performing the vulnerability test on the VMware image to gather
information about the security configuration and services. Since no information is provided
about the virtual image it falls under Gray box testing category multiple tools are used for
gathering information about the image file (Regalado et al. 2015). The network adapter in
5
COMPUTERS SECURITY
vmware is changed from NAT to host only for identifying the IP address of the machine and Kali
linux is used for getting more visibility for the targeted host with IP address 192.168.202.129.
Information Gathering
Before accessing the targeted victim, a research is performed for gathering information
from third party sources such as identifying the IP address of the host, hack attempts made on the
machine, information about the operating system, services running on different ports, Open
ports, etc. for using it later and perform the exploitation (Conteh and Schmick 2016).
COMPUTERS SECURITY
vmware is changed from NAT to host only for identifying the IP address of the machine and Kali
linux is used for getting more visibility for the targeted host with IP address 192.168.202.129.
Information Gathering
Before accessing the targeted victim, a research is performed for gathering information
from third party sources such as identifying the IP address of the host, hack attempts made on the
machine, information about the operating system, services running on different ports, Open
ports, etc. for using it later and perform the exploitation (Conteh and Schmick 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
COMPUTERS SECURITY
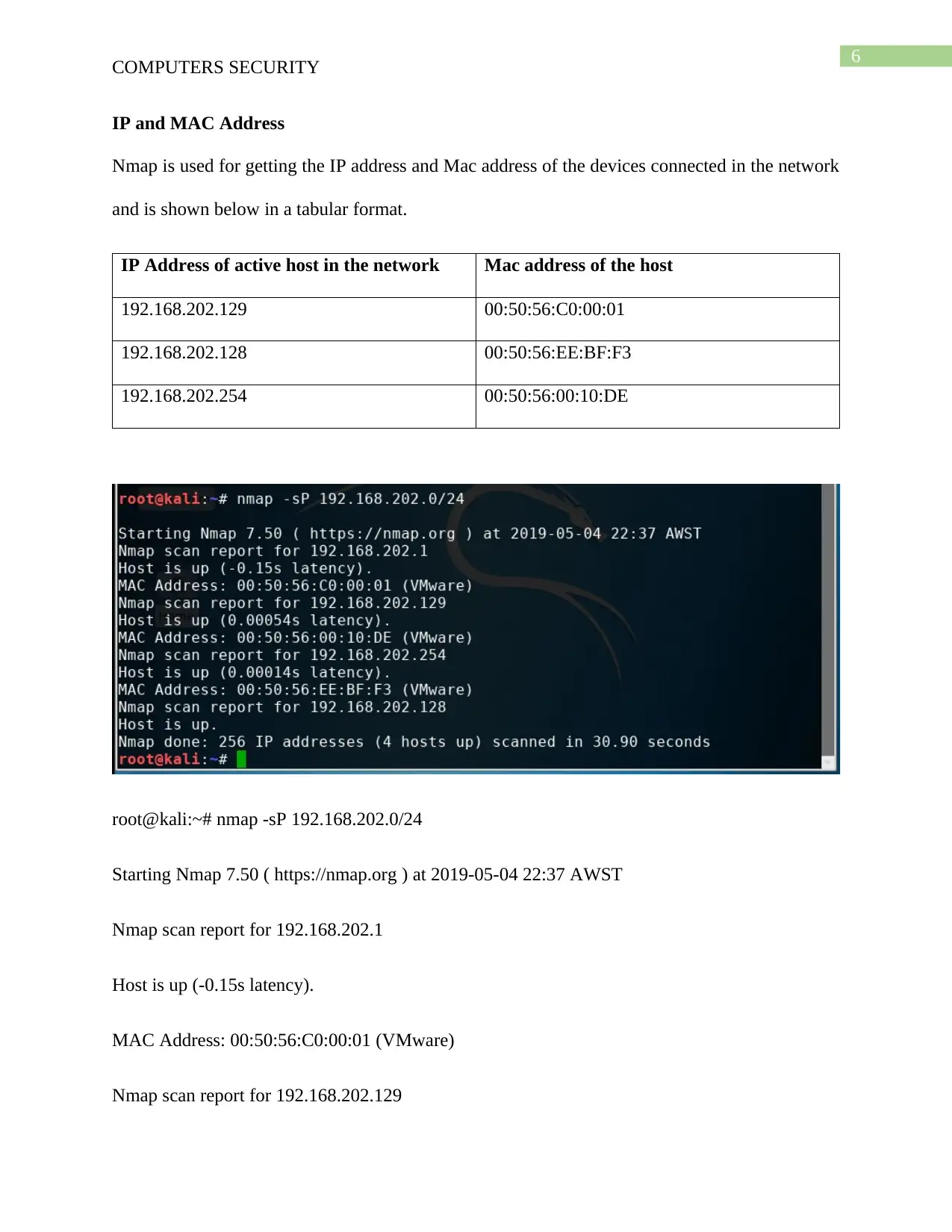
IP and MAC Address
Nmap is used for getting the IP address and Mac address of the devices connected in the network
and is shown below in a tabular format.
IP Address of active host in the network Mac address of the host
192.168.202.129 00:50:56:C0:00:01
192.168.202.128 00:50:56:EE:BF:F3
192.168.202.254 00:50:56:00:10:DE
root@kali:~# nmap -sP 192.168.202.0/24
Starting Nmap 7.50 ( https://nmap.org ) at 2019-05-04 22:37 AWST
Nmap scan report for 192.168.202.1
Host is up (-0.15s latency).
MAC Address: 00:50:56:C0:00:01 (VMware)
Nmap scan report for 192.168.202.129
COMPUTERS SECURITY
IP and MAC Address
Nmap is used for getting the IP address and Mac address of the devices connected in the network
and is shown below in a tabular format.
IP Address of active host in the network Mac address of the host
192.168.202.129 00:50:56:C0:00:01
192.168.202.128 00:50:56:EE:BF:F3
192.168.202.254 00:50:56:00:10:DE
root@kali:~# nmap -sP 192.168.202.0/24
Starting Nmap 7.50 ( https://nmap.org ) at 2019-05-04 22:37 AWST
Nmap scan report for 192.168.202.1
Host is up (-0.15s latency).
MAC Address: 00:50:56:C0:00:01 (VMware)
Nmap scan report for 192.168.202.129
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
COMPUTERS SECURITY
Host is up (0.00054s latency).
MAC Address: 00:50:56:00:10:DE (VMware)
Nmap scan report for 192.168.202.254
Host is up (0.00014s latency).
MAC Address: 00:50:56:EE:BF:F3 (VMware)
Nmap scan report for 192.168.202.128
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 30.90 seconds
root@kali:~#
Virtual Host
The virtual PC used the IP address same as the website address and thus if the virtual server can
be compromised it can also compromise the security of the website. The same vulnerability can
be found on the website of WidgetInc since the virtual server is used for hosting the site.
IP Address Website Content
192.168.202.129 Widget Inc
COMPUTERS SECURITY
Host is up (0.00054s latency).
MAC Address: 00:50:56:00:10:DE (VMware)
Nmap scan report for 192.168.202.254
Host is up (0.00014s latency).
MAC Address: 00:50:56:EE:BF:F3 (VMware)
Nmap scan report for 192.168.202.128
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 30.90 seconds
root@kali:~#
Virtual Host
The virtual PC used the IP address same as the website address and thus if the virtual server can
be compromised it can also compromise the security of the website. The same vulnerability can
be found on the website of WidgetInc since the virtual server is used for hosting the site.
IP Address Website Content
192.168.202.129 Widget Inc
8
COMPUTERS SECURITY
Scanning
There are different types of scans that are performed for identifying the vulnerability of the
victim virtual image and they are given in the following steps.
Port Scan
Used tool: Masscan
Description: It is a port scanner that is capable of performing survey on a large scale for the
internet or the intranet network. The default rate of transmit of the tool is 100 packet per second
but it can be modified for getting a faster scan result upto 25 million packet per second and the
rate is more than enough for scanning the internet with 3 minute for finding a port (Holzer and
Lerums 2016).
COMPUTERS SECURITY
Scanning
There are different types of scans that are performed for identifying the vulnerability of the
victim virtual image and they are given in the following steps.
Port Scan
Used tool: Masscan
Description: It is a port scanner that is capable of performing survey on a large scale for the
internet or the intranet network. The default rate of transmit of the tool is 100 packet per second
but it can be modified for getting a faster scan result upto 25 million packet per second and the
rate is more than enough for scanning the internet with 3 minute for finding a port (Holzer and
Lerums 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
COMPUTERS SECURITY
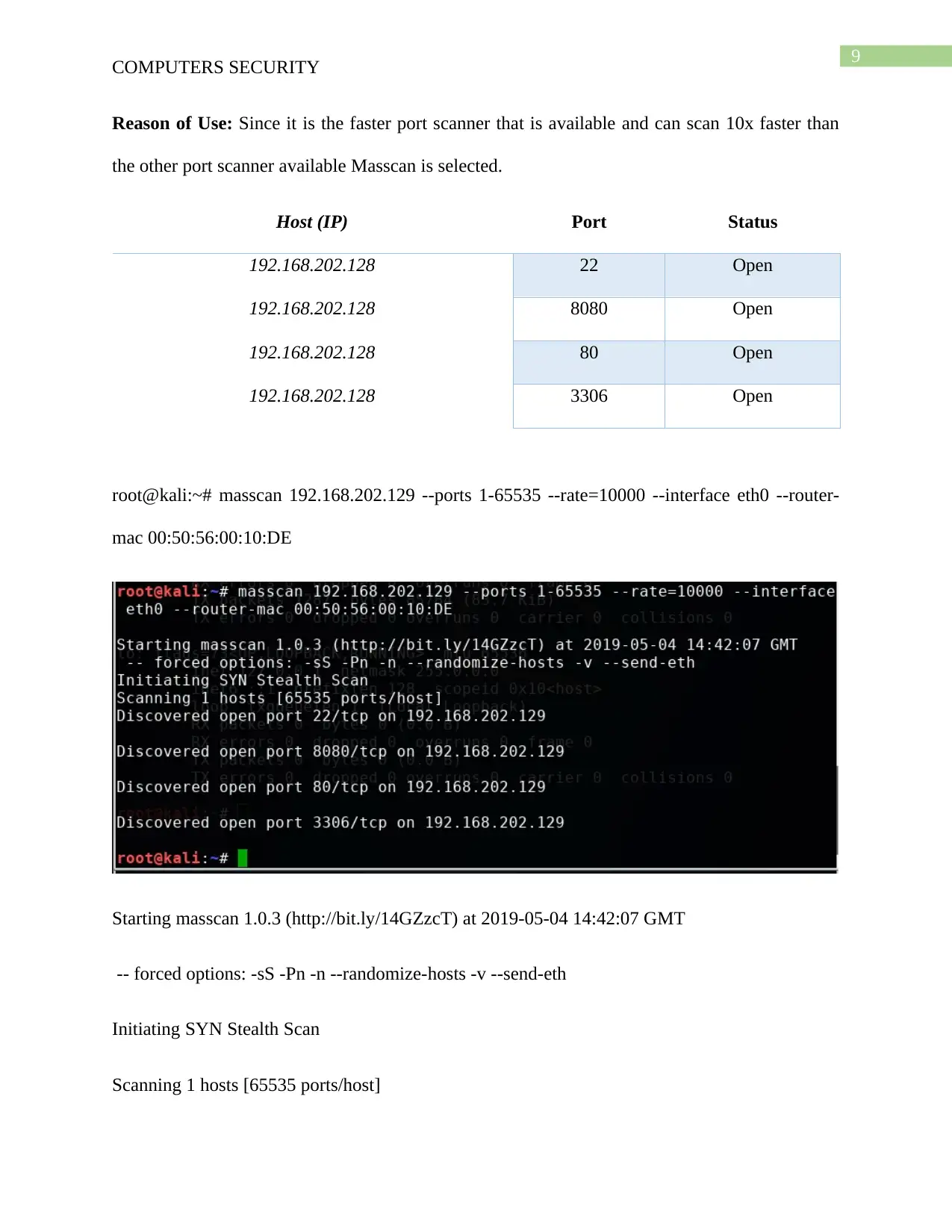
Reason of Use: Since it is the faster port scanner that is available and can scan 10x faster than
the other port scanner available Masscan is selected.
Host (IP) Port Status
192.168.202.128 22 Open
192.168.202.128 8080 Open
192.168.202.128 80 Open
192.168.202.128 3306 Open
root@kali:~# masscan 192.168.202.129 --ports 1-65535 --rate=10000 --interface eth0 --router-
mac 00:50:56:00:10:DE
Starting masscan 1.0.3 (http://bit.ly/14GZzcT) at 2019-05-04 14:42:07 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
COMPUTERS SECURITY
Reason of Use: Since it is the faster port scanner that is available and can scan 10x faster than
the other port scanner available Masscan is selected.
Host (IP) Port Status
192.168.202.128 22 Open
192.168.202.128 8080 Open
192.168.202.128 80 Open
192.168.202.128 3306 Open
root@kali:~# masscan 192.168.202.129 --ports 1-65535 --rate=10000 --interface eth0 --router-
mac 00:50:56:00:10:DE
Starting masscan 1.0.3 (http://bit.ly/14GZzcT) at 2019-05-04 14:42:07 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
COMPUTERS SECURITY
Discovered open port 22/tcp on 192.168.202.129
Discovered open port 8080/tcp on 192.168.202.129
Discovered open port 80/tcp on 192.168.202.129
Discovered open port 3306/tcp on 192.168.202.129
Tool Used: Nmap
Description: It is also termed as network mapper and is available in the internet as an open
source network monitoring tool that can help in exploring the network and security auditing.
Reason of Use: Raw IP packets are used by Nmap for determining the available host connected
in the network and the services offered by the host (Oriyano 2016). Many other details such as
the operating system details running on the targeted IP address, filters and firewall types that are
used can also be determined with other characters shown in the table below:
Host (IP) Status Version Services
192.168.202.129 22 Open ssh 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux;
protocol 2.0)
192.168.202.129 80 Open http Apache httpd 2.4.29 ((Ubuntu))
192.168.202.129 3306 Open Mysql (unauthorized)
192.168.202.129 8080 Open http Apache Tomcat
COMPUTERS SECURITY
Discovered open port 22/tcp on 192.168.202.129
Discovered open port 8080/tcp on 192.168.202.129
Discovered open port 80/tcp on 192.168.202.129
Discovered open port 3306/tcp on 192.168.202.129
Tool Used: Nmap
Description: It is also termed as network mapper and is available in the internet as an open
source network monitoring tool that can help in exploring the network and security auditing.
Reason of Use: Raw IP packets are used by Nmap for determining the available host connected
in the network and the services offered by the host (Oriyano 2016). Many other details such as
the operating system details running on the targeted IP address, filters and firewall types that are
used can also be determined with other characters shown in the table below:
Host (IP) Status Version Services
192.168.202.129 22 Open ssh 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux;
protocol 2.0)
192.168.202.129 80 Open http Apache httpd 2.4.29 ((Ubuntu))
192.168.202.129 3306 Open Mysql (unauthorized)
192.168.202.129 8080 Open http Apache Tomcat
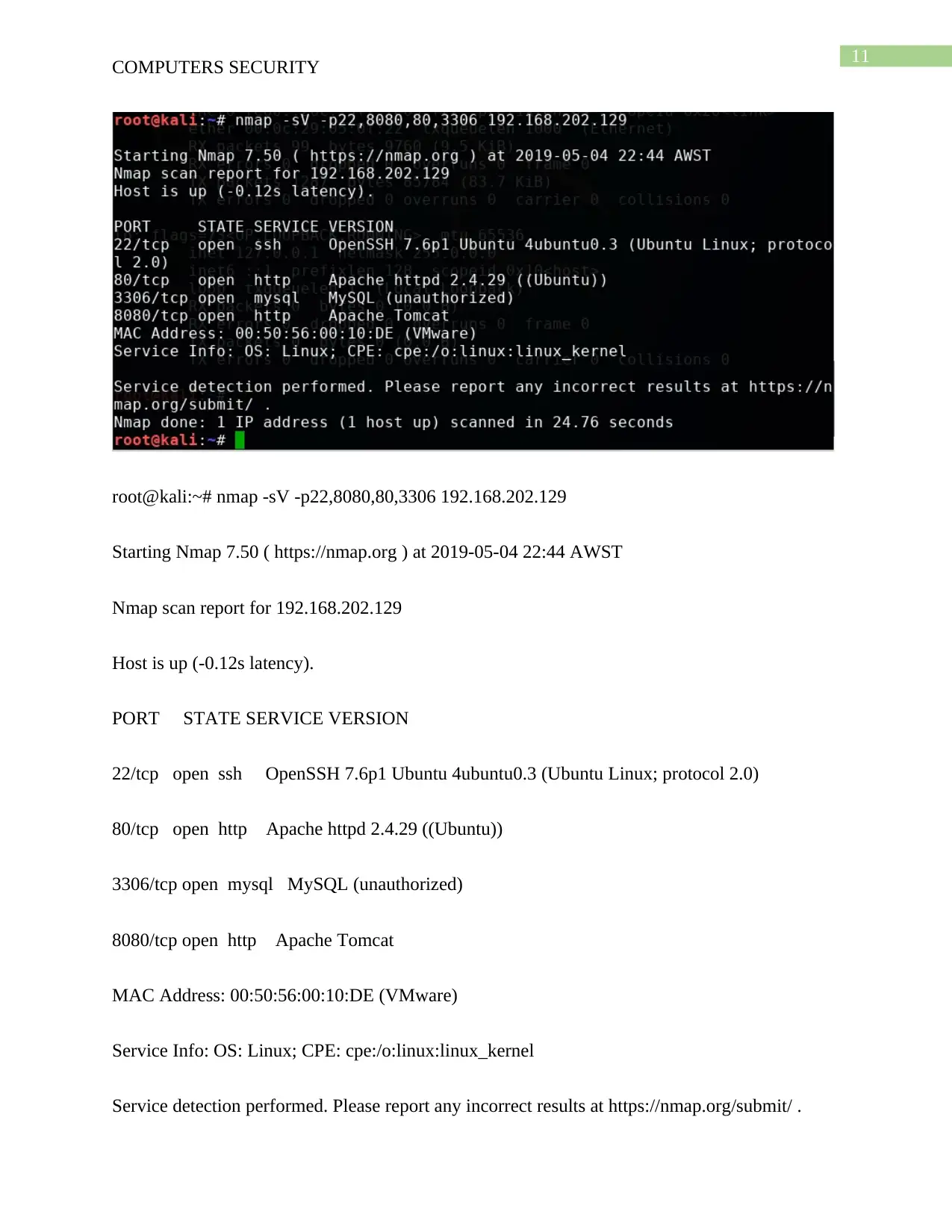
11
COMPUTERS SECURITY
root@kali:~# nmap -sV -p22,8080,80,3306 192.168.202.129
Starting Nmap 7.50 ( https://nmap.org ) at 2019-05-04 22:44 AWST
Nmap scan report for 192.168.202.129
Host is up (-0.12s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
3306/tcp open mysql MySQL (unauthorized)
8080/tcp open http Apache Tomcat
MAC Address: 00:50:56:00:10:DE (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
COMPUTERS SECURITY
root@kali:~# nmap -sV -p22,8080,80,3306 192.168.202.129
Starting Nmap 7.50 ( https://nmap.org ) at 2019-05-04 22:44 AWST
Nmap scan report for 192.168.202.129
Host is up (-0.12s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
3306/tcp open mysql MySQL (unauthorized)
8080/tcp open http Apache Tomcat
MAC Address: 00:50:56:00:10:DE (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





