University: Computer Security System Investigation Report
VerifiedAdded on 2022/12/19
|12
|1368
|37
Report
AI Summary
This report details a computer security investigation, beginning with the installation of a VMware image file and subsequent system security analysis. The investigation utilizes Kali Linux and Ubuntu to assess vulnerabilities and threats within the system. The report outlines steps for Ubuntu hardening, including keeping the system up-to-date, sudo configuration, SSH security, web server hardening, and malware checks. Results from Lynis auditing are presented, emphasizing the importance of a secure Windows system for the VM workstation. The report concludes with a system security proposal, offering vulnerability mitigation strategies such as removing unused network services, adding a security login banner, configuring a firewall, monitoring user activities, preventing IP spoofing, and hardening the networking layer. These measures aim to enhance the overall security posture of the system.

Computer Security-System Investigation
Student Name
University Name:
1
Student Name
University Name:
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task: 1 Installation of VMware Image File...........................................................................................3
Task: 2 System Security Investigation...................................................................................................8
Task: 3 Results......................................................................................................................................9
Task: 4 System Security Proposal.......................................................................................................10
References...........................................................................................................................................12
2
Task: 1 Installation of VMware Image File...........................................................................................3
Task: 2 System Security Investigation...................................................................................................8
Task: 3 Results......................................................................................................................................9
Task: 4 System Security Proposal.......................................................................................................10
References...........................................................................................................................................12
2
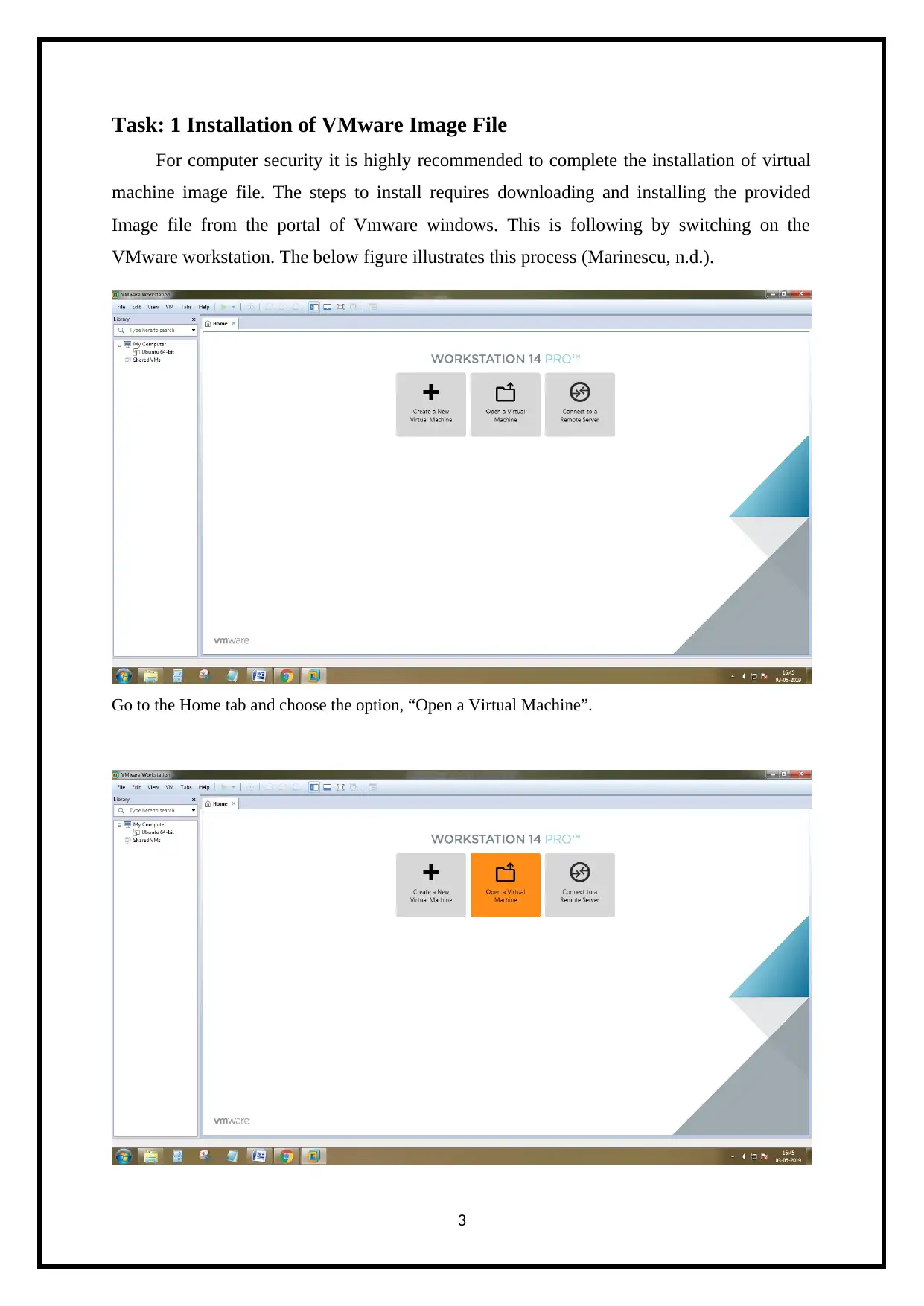
Task: 1 Installation of VMware Image File
For computer security it is highly recommended to complete the installation of virtual
machine image file. The steps to install requires downloading and installing the provided
Image file from the portal of Vmware windows. This is following by switching on the
VMware workstation. The below figure illustrates this process (Marinescu, n.d.).
Go to the Home tab and choose the option, “Open a Virtual Machine”.
3
For computer security it is highly recommended to complete the installation of virtual
machine image file. The steps to install requires downloading and installing the provided
Image file from the portal of Vmware windows. This is following by switching on the
VMware workstation. The below figure illustrates this process (Marinescu, n.d.).
Go to the Home tab and choose the option, “Open a Virtual Machine”.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
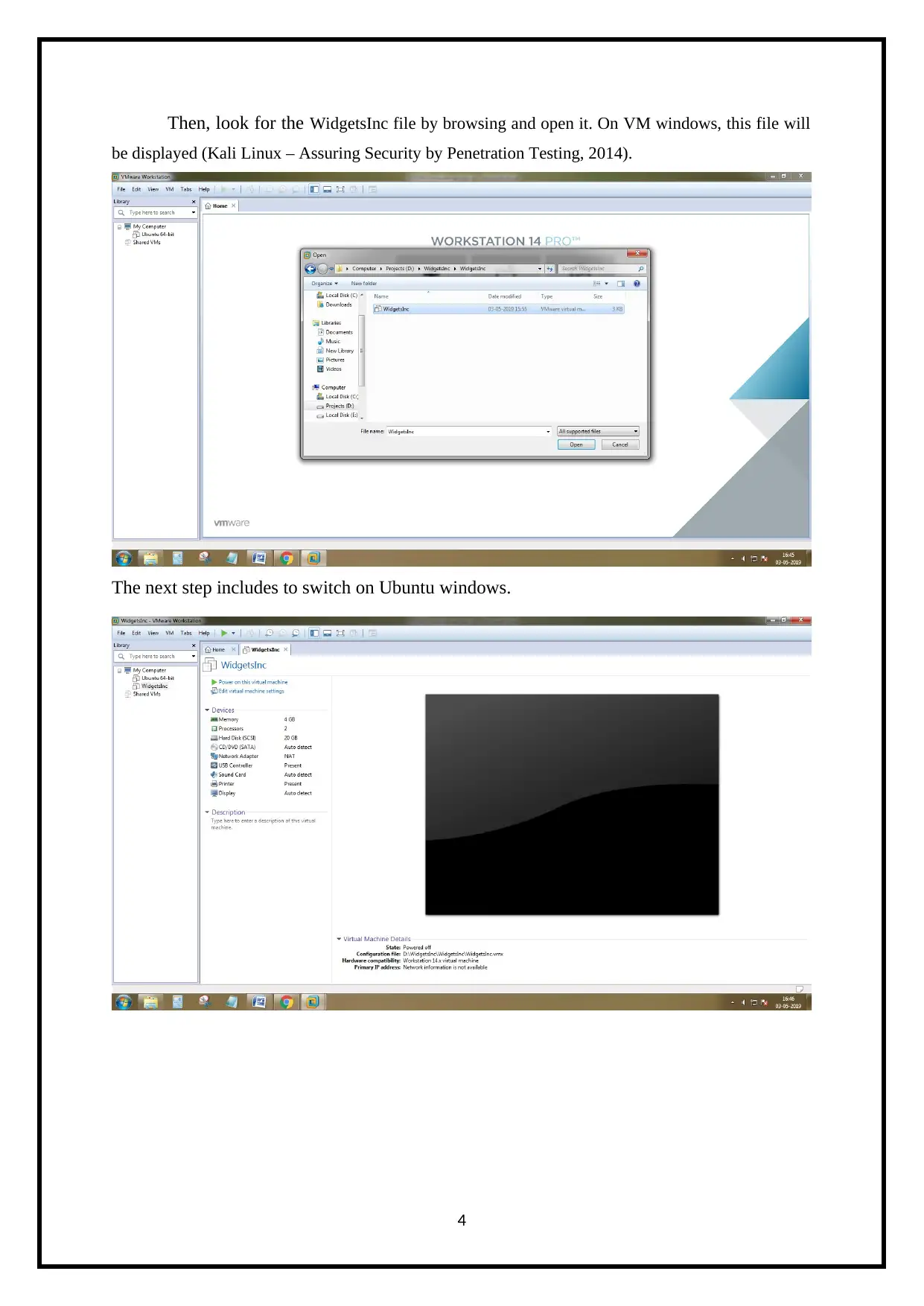
Then, look for the WidgetsInc file by browsing and open it. On VM windows, this file will
be displayed (Kali Linux – Assuring Security by Penetration Testing, 2014).
The next step includes to switch on Ubuntu windows.
4
be displayed (Kali Linux – Assuring Security by Penetration Testing, 2014).
The next step includes to switch on Ubuntu windows.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5
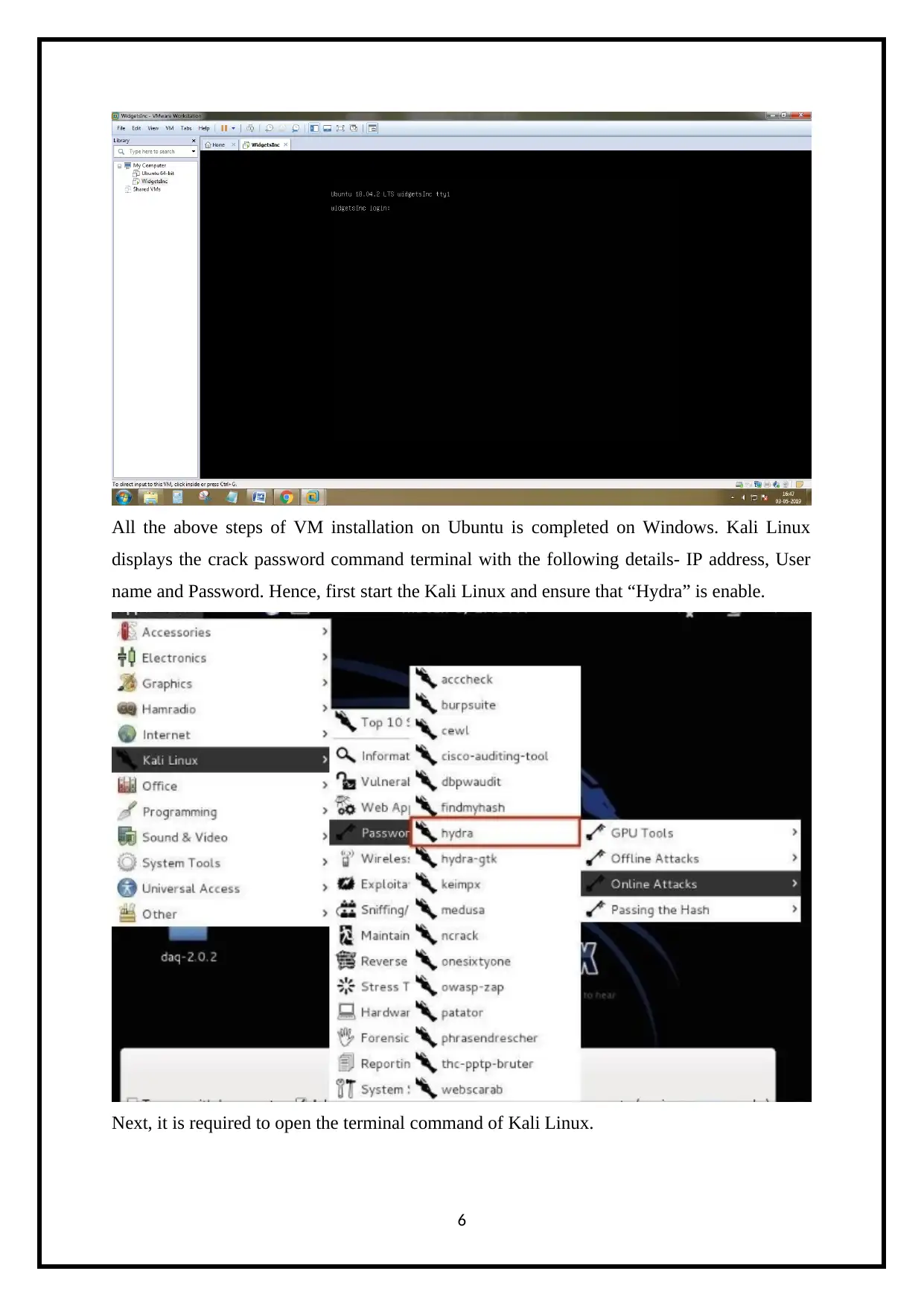
All the above steps of VM installation on Ubuntu is completed on Windows. Kali Linux
displays the crack password command terminal with the following details- IP address, User
name and Password. Hence, first start the Kali Linux and ensure that “Hydra” is enable.
Next, it is required to open the terminal command of Kali Linux.
6
displays the crack password command terminal with the following details- IP address, User
name and Password. Hence, first start the Kali Linux and ensure that “Hydra” is enable.
Next, it is required to open the terminal command of Kali Linux.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
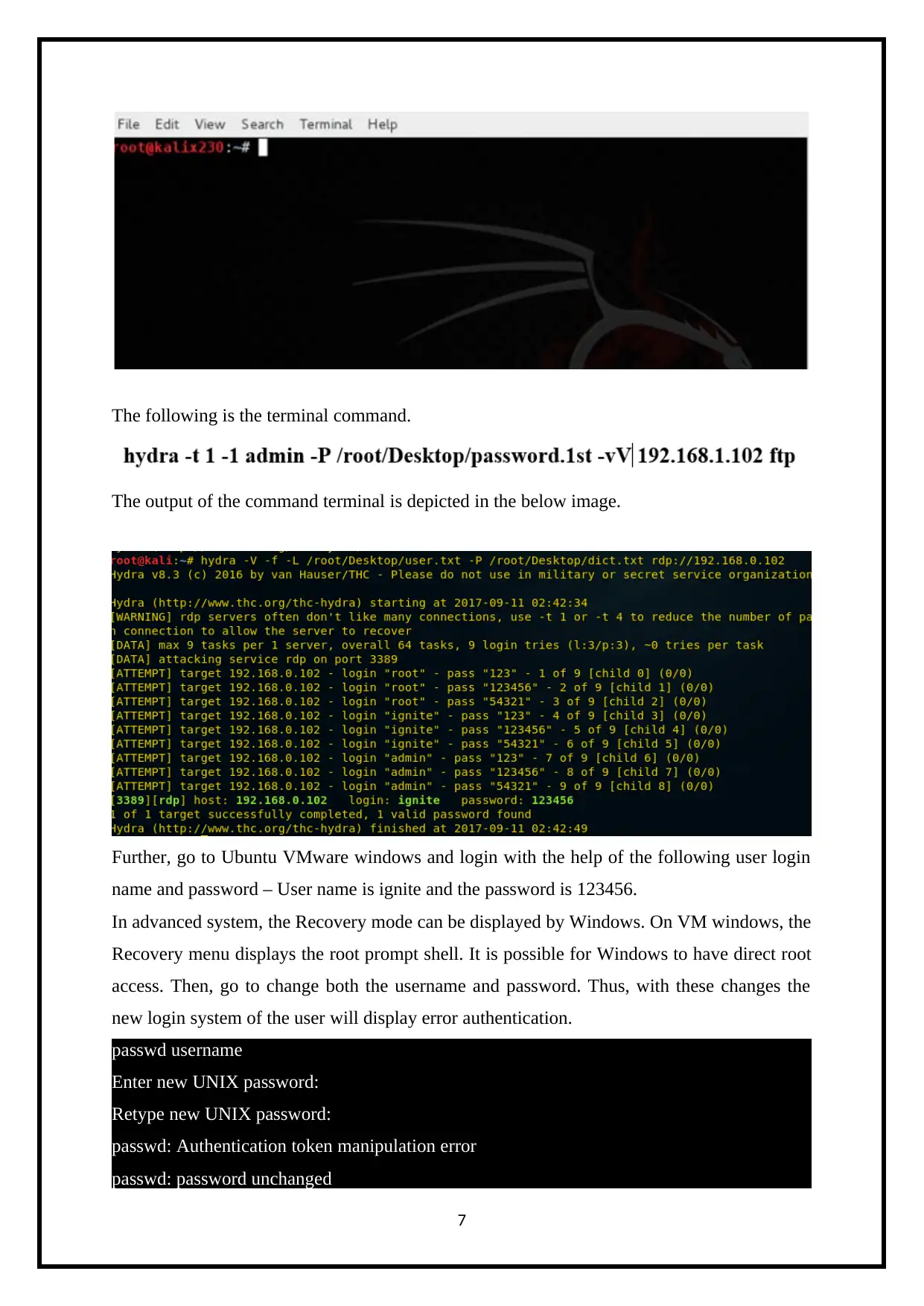
The following is the terminal command.
The output of the command terminal is depicted in the below image.
Further, go to Ubuntu VMware windows and login with the help of the following user login
name and password – User name is ignite and the password is 123456.
In advanced system, the Recovery mode can be displayed by Windows. On VM windows, the
Recovery menu displays the root prompt shell. It is possible for Windows to have direct root
access. Then, go to change both the username and password. Thus, with these changes the
new login system of the user will display error authentication.
passwd username
Enter new UNIX password:
Retype new UNIX password:
passwd: Authentication token manipulation error
passwd: password unchanged
7
The output of the command terminal is depicted in the below image.
Further, go to Ubuntu VMware windows and login with the help of the following user login
name and password – User name is ignite and the password is 123456.
In advanced system, the Recovery mode can be displayed by Windows. On VM windows, the
Recovery menu displays the root prompt shell. It is possible for Windows to have direct root
access. Then, go to change both the username and password. Thus, with these changes the
new login system of the user will display error authentication.
passwd username
Enter new UNIX password:
Retype new UNIX password:
passwd: Authentication token manipulation error
passwd: password unchanged
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The security issue authentication related to password change comprises of Security transmission
issues, Login password issue, SLL service issue, Web server stored service issue, and
Security malware issue (Parker, 2011).
Task: 2 System Security Investigation
The security of a system is evaluated for a given VM image file. This section gives
brief of the investigation related to system security on VM. The VM image files’
development could recognize vulnerabilities for the security system and the threats (Soyinka,
2012). On Ubuntu 18.04 is used for system security, which specifies the VM image file for
protecting the system’s security and vulnerabilities on Windows. The following steps are
used for Ubuntu hardening i.e., for its system security:
STEP 1: Keep System Up-To-Date
In VMware network workstations, the VMware has the capacity to lock certain
file on windows. It can even automatically update the system (Vuletić and
Nojković, 2018).
STEP 2: Sudo Configuration
UNIX- and Linux-based system’s sudo configuration are flexible enough for
running various configuration process.
STEP 3: Open SSH Security and Hardening
SSH security connects the server with the Ubuntu windows security. The
identification of windows security for configuring the SSH server the functional
& non-functional services are used. Lynis and SSH audit are the beneficial
security tools.
STEP 4: Web Server Hardening
Web server hardening assists in identifying the network speed on SSL and TLS
security. In Windows system, the SSL and TLS security requires setting high goal
service and Nginx configuration.
STEP 5: Malware availability must be checked
The following steps are required to check the occurrence of malware on the VM
workstation with the help of Linux system:
a) On windows, the safe mode must be entered.
b) Delete the temporary file.
c) Install a Malware scanner.
8
issues, Login password issue, SLL service issue, Web server stored service issue, and
Security malware issue (Parker, 2011).
Task: 2 System Security Investigation
The security of a system is evaluated for a given VM image file. This section gives
brief of the investigation related to system security on VM. The VM image files’
development could recognize vulnerabilities for the security system and the threats (Soyinka,
2012). On Ubuntu 18.04 is used for system security, which specifies the VM image file for
protecting the system’s security and vulnerabilities on Windows. The following steps are
used for Ubuntu hardening i.e., for its system security:
STEP 1: Keep System Up-To-Date
In VMware network workstations, the VMware has the capacity to lock certain
file on windows. It can even automatically update the system (Vuletić and
Nojković, 2018).
STEP 2: Sudo Configuration
UNIX- and Linux-based system’s sudo configuration are flexible enough for
running various configuration process.
STEP 3: Open SSH Security and Hardening
SSH security connects the server with the Ubuntu windows security. The
identification of windows security for configuring the SSH server the functional
& non-functional services are used. Lynis and SSH audit are the beneficial
security tools.
STEP 4: Web Server Hardening
Web server hardening assists in identifying the network speed on SSL and TLS
security. In Windows system, the SSL and TLS security requires setting high goal
service and Nginx configuration.
STEP 5: Malware availability must be checked
The following steps are required to check the occurrence of malware on the VM
workstation with the help of Linux system:
a) On windows, the safe mode must be entered.
b) Delete the temporary file.
c) Install a Malware scanner.
8
d) windows system security image file must be run on malware bytes.
The above mentioned steps ensure to maximize or minimize the security system.
Task: 3 Results
The Lynis on the Ubuntu 18.04 window is used to investigate the virtual machine
image file. For maintaining the image file’s profile a secure windows system is required for
the VM work station.
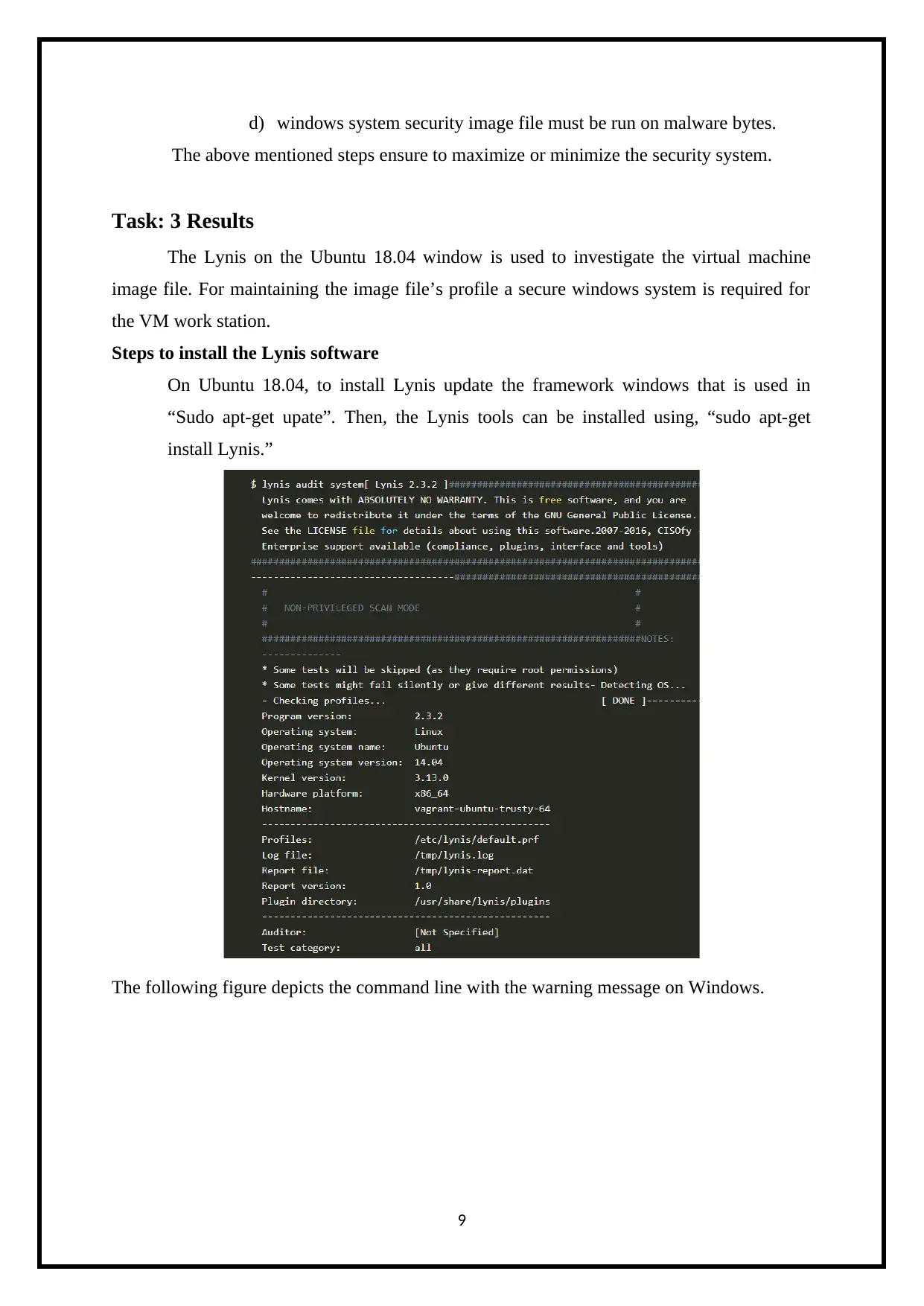
Steps to install the Lynis software
On Ubuntu 18.04, to install Lynis update the framework windows that is used in
“Sudo apt-get upate”. Then, the Lynis tools can be installed using, “sudo apt-get
install Lynis.”
The following figure depicts the command line with the warning message on Windows.
9
The above mentioned steps ensure to maximize or minimize the security system.
Task: 3 Results
The Lynis on the Ubuntu 18.04 window is used to investigate the virtual machine
image file. For maintaining the image file’s profile a secure windows system is required for
the VM work station.
Steps to install the Lynis software
On Ubuntu 18.04, to install Lynis update the framework windows that is used in
“Sudo apt-get upate”. Then, the Lynis tools can be installed using, “sudo apt-get
install Lynis.”
The following figure depicts the command line with the warning message on Windows.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Lynis auditing ensures to administer and mention the security protection information
to identify the vulnerabilities and increase the service quality by auditing security audits it
facilities suggestions to improvise the security level of the server with necessary information
such as, Id and solution for the VM workstation in Windows. The system security checks the
limitations first to improve a system’s security.
Task: 4 System Security Proposal
The problem of system security is resolved with this proposal which contains the following
vulnerability stages such as PHP vulnerable, Libxslt, Pacemaker, System end, and the Wget of
windows system.
LEVEL 1: The network facing services that are not in use should be removed.
In general, it is not compulsory to remove the networking services from your
system. However, it is a process that helps to minimize the attack surface for the
running processes and for the installed packages. For instance, the VM Windows’
listen service can be uninstalled including the TCP and UDP running services.
LEVEL 2: Add a security login banner
There are possibilities that the unwanted elements might be able to access the
server system. So, a larger positive impact on the server system can be facilitated
with security login banner.
LEVEL 3: Firewall Configuration
10
to identify the vulnerabilities and increase the service quality by auditing security audits it
facilities suggestions to improvise the security level of the server with necessary information
such as, Id and solution for the VM workstation in Windows. The system security checks the
limitations first to improve a system’s security.
Task: 4 System Security Proposal
The problem of system security is resolved with this proposal which contains the following
vulnerability stages such as PHP vulnerable, Libxslt, Pacemaker, System end, and the Wget of
windows system.
LEVEL 1: The network facing services that are not in use should be removed.
In general, it is not compulsory to remove the networking services from your
system. However, it is a process that helps to minimize the attack surface for the
running processes and for the installed packages. For instance, the VM Windows’
listen service can be uninstalled including the TCP and UDP running services.
LEVEL 2: Add a security login banner
There are possibilities that the unwanted elements might be able to access the
server system. So, a larger positive impact on the server system can be facilitated
with security login banner.
LEVEL 3: Firewall Configuration
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The firewall protects from unwanted inbound traffic, and gives necessary security
layers which benefit the user’s computer. It even gives information for blocking
the intuitions and network mapping.
LEVEL 4: Monitoring the User Activities
The monitoring of user activities ensures information security, which refers to
network activity monitoring along with application, data and network actions like
internet browsing activity of the users, unauthorized access to important files etc.
LEVEL 5: Prevent IP spoofing
Spoofing indicates a stupid act where a false factor is given reliably. Networking
represents significant IP spoof. Various spoilers can be generalized as follows, “A
wrong user sends the packets with the IP address, which denotes that the packets
are formed by a reliable machine.”
LEVEL 6: Harden the networking layer
It is easily possible to block the source routing of the incoming packets on the
respective Ubuntu server, where all the false IPs can be registered. After, this it is
necessary that the service command sudo sysctl –p must be restarted.
11
layers which benefit the user’s computer. It even gives information for blocking
the intuitions and network mapping.
LEVEL 4: Monitoring the User Activities
The monitoring of user activities ensures information security, which refers to
network activity monitoring along with application, data and network actions like
internet browsing activity of the users, unauthorized access to important files etc.
LEVEL 5: Prevent IP spoofing
Spoofing indicates a stupid act where a false factor is given reliably. Networking
represents significant IP spoof. Various spoilers can be generalized as follows, “A
wrong user sends the packets with the IP address, which denotes that the packets
are formed by a reliable machine.”
LEVEL 6: Harden the networking layer
It is easily possible to block the source routing of the incoming packets on the
respective Ubuntu server, where all the false IPs can be registered. After, this it is
necessary that the service command sudo sysctl –p must be restarted.
11

References
Kali Linux – Assuring Security by Penetration Testing. (2014). Network Security, 2014(8),
p.4.
Marinescu, D. (n.d.). Cloud computing.
Parker, S. (2011). Shell scripting. Hoboken, N.J.: Wiley.
Soyinka, W. (2012). Linux administration. New York, NY: McGraw-Hill Osborne Media.
Vuletić, D. and Nojković, N. (2018). Realization of a TCP Syn Flood Attack using Kali
Linux. Vojnotehnicki glasnik, 66(3), pp.640-649.
12
Kali Linux – Assuring Security by Penetration Testing. (2014). Network Security, 2014(8),
p.4.
Marinescu, D. (n.d.). Cloud computing.
Parker, S. (2011). Shell scripting. Hoboken, N.J.: Wiley.
Soyinka, W. (2012). Linux administration. New York, NY: McGraw-Hill Osborne Media.
Vuletić, D. and Nojković, N. (2018). Realization of a TCP Syn Flood Attack using Kali
Linux. Vojnotehnicki glasnik, 66(3), pp.640-649.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





