University Computer Security: Virtual Machine Evaluation Report
VerifiedAdded on 2023/01/23
|21
|3764
|57
Report
AI Summary
This report presents a comprehensive security evaluation of a virtual machine image, undertaken as part of a computer security assignment. The project's aim was to assess the security posture of a VM provided by 'Benny Vandergast Inc.' for 'Widgets Inc.' The evaluation involved installing VMware, identifying the VM's IP address, and gaining access to the system using Kali Linux and penetration testing techniques. The report details the security investigation process, including the use of tools like Hydra to discover credentials. Findings include vulnerabilities related to encrypted data communication, security patches, network services, web server hardening, password settings, OpenSSL, and malware. The report explores system security investigation methods, including security assessments based on international standards and the implementation of security tools. Furthermore, it details system hardening techniques, such as using strong passwords, disk encryption, automatic security updates, and web server hardening. The report also proposes various measures to secure the system, addressing identified security issues and offering recommendations for improving the overall security posture of the VM. References to cited sources are included throughout the report to support the findings and recommendations.

University
Semester
Computer Security
Student ID
Student Name
Submission Date
Semester
Computer Security
Student ID
Student Name
Submission Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Aim of the Project..........................................................................................................................1
2. VMware Installation......................................................................................................................1
3. System Security Investigation........................................................................................................7
4. Results.........................................................................................................................................13
5. Proposal on System Security.......................................................................................................15
References...........................................................................................................................................18
1. Aim of the Project..........................................................................................................................1
2. VMware Installation......................................................................................................................1
3. System Security Investigation........................................................................................................7
4. Results.........................................................................................................................................13
5. Proposal on System Security.......................................................................................................15
References...........................................................................................................................................18

1. Aim of the Project
Today, system Security indicates serious issue which can be caused due to various
reasons. This report will shed light on all the reasons, its impact and solution. In computing,
a Virtual Machine (VM) is a reflection of a Computer system, which depends on the
computer architecture and gives functionality of a physical computer.In this report two firms
are involved namely, “Widgets Inc.” and “Benny Vandergast Inc.” Widgets Inc., is the firm
that gives the virtual machine image, whereas the other firm has given a VMware to be tested
for security reasons and will be utilized for a new web-based store.
The overall aim is to evaluate security for the given VM images. Thus, various
security aspects will be inspected and tested, for recognizing any kind of loop holes and
security problems. For this task, it is suggested to utilize some special security evaluation
tool. With Security evaluation the Virtual Machine Image files will be tested and the below
mentioned parameters will be considered:
A. Explanation on the system security’s investigation.
B. Implementation of system security tool for investigating the system security,
with outcomes.
C. A system security proposal along with the identified security problems
(DONG et al., 2010).
2. VMware Installation
The following are the installation steps to be followed:
On the Portal, the given Virtual machine image file should be downloaded.
Next, complete the installation of VMware work station.
Open it when once installed.
The below represented image helps to understand the above mentioned steps,
1
Today, system Security indicates serious issue which can be caused due to various
reasons. This report will shed light on all the reasons, its impact and solution. In computing,
a Virtual Machine (VM) is a reflection of a Computer system, which depends on the
computer architecture and gives functionality of a physical computer.In this report two firms
are involved namely, “Widgets Inc.” and “Benny Vandergast Inc.” Widgets Inc., is the firm
that gives the virtual machine image, whereas the other firm has given a VMware to be tested
for security reasons and will be utilized for a new web-based store.
The overall aim is to evaluate security for the given VM images. Thus, various
security aspects will be inspected and tested, for recognizing any kind of loop holes and
security problems. For this task, it is suggested to utilize some special security evaluation
tool. With Security evaluation the Virtual Machine Image files will be tested and the below
mentioned parameters will be considered:
A. Explanation on the system security’s investigation.
B. Implementation of system security tool for investigating the system security,
with outcomes.
C. A system security proposal along with the identified security problems
(DONG et al., 2010).
2. VMware Installation
The following are the installation steps to be followed:
On the Portal, the given Virtual machine image file should be downloaded.
Next, complete the installation of VMware work station.
Open it when once installed.
The below represented image helps to understand the above mentioned steps,
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
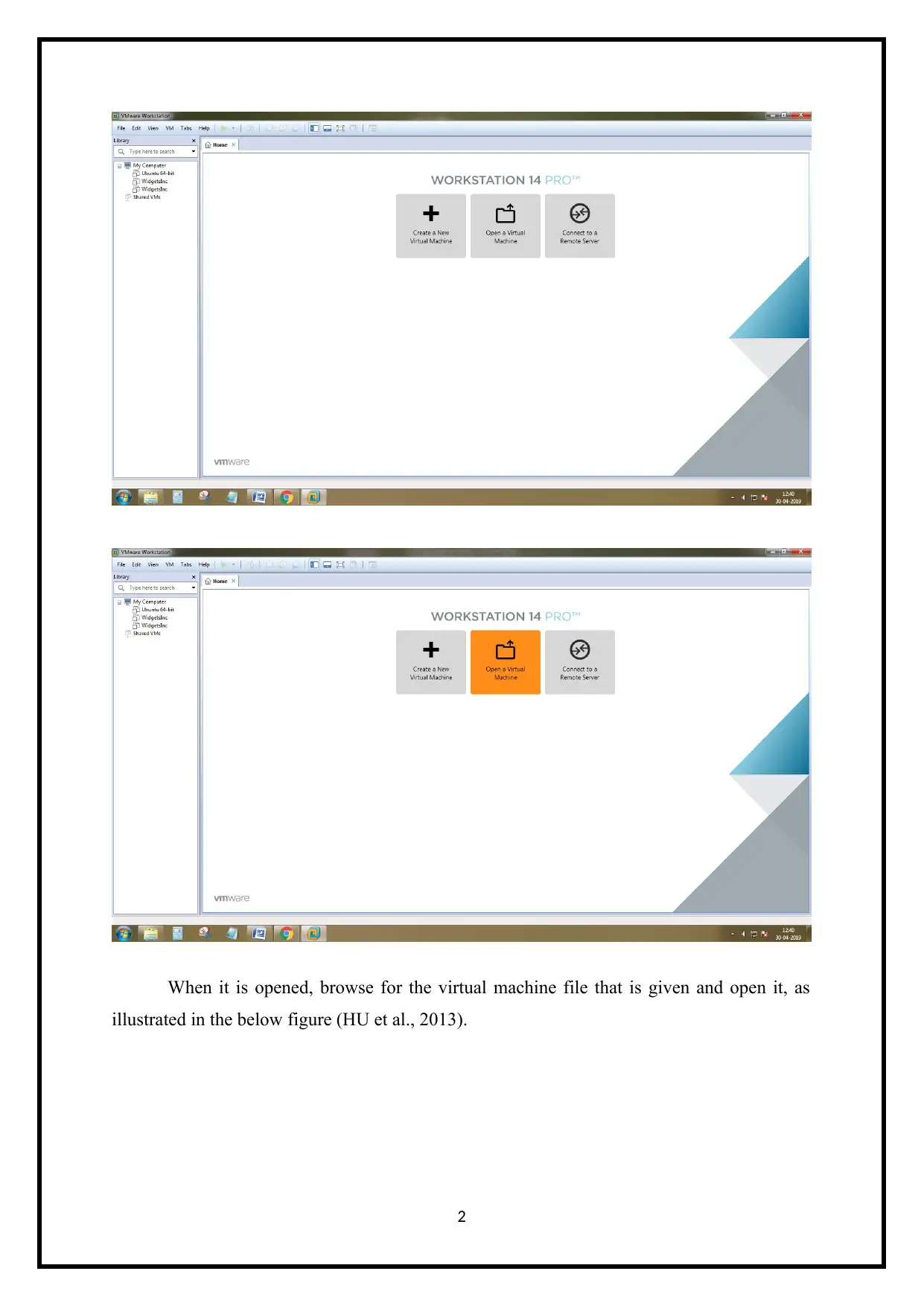
When it is opened, browse for the virtual machine file that is given and open it, as
illustrated in the below figure (HU et al., 2013).
2
illustrated in the below figure (HU et al., 2013).
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
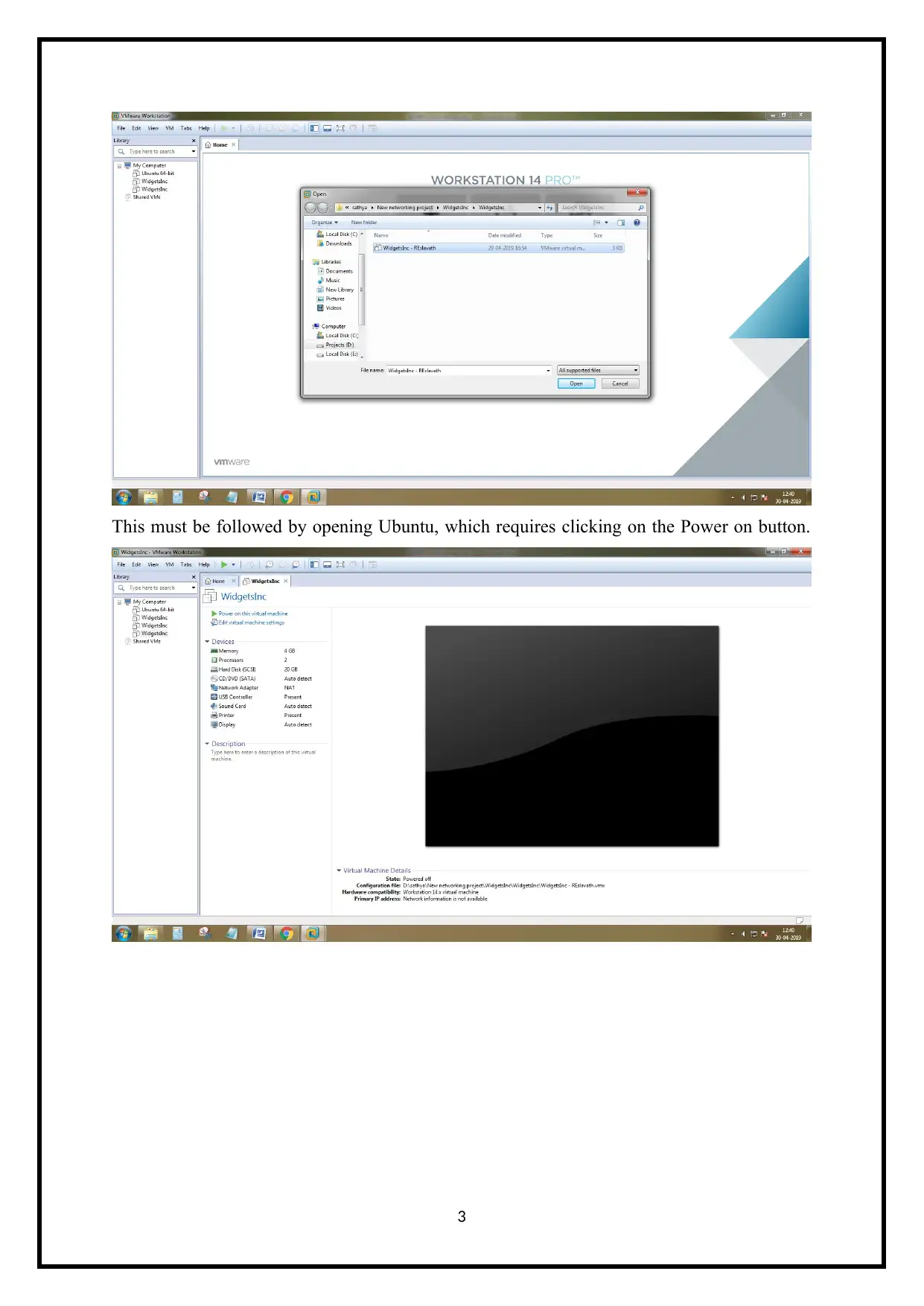
This must be followed by opening Ubuntu, which requires clicking on the Power on button.
3
3
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
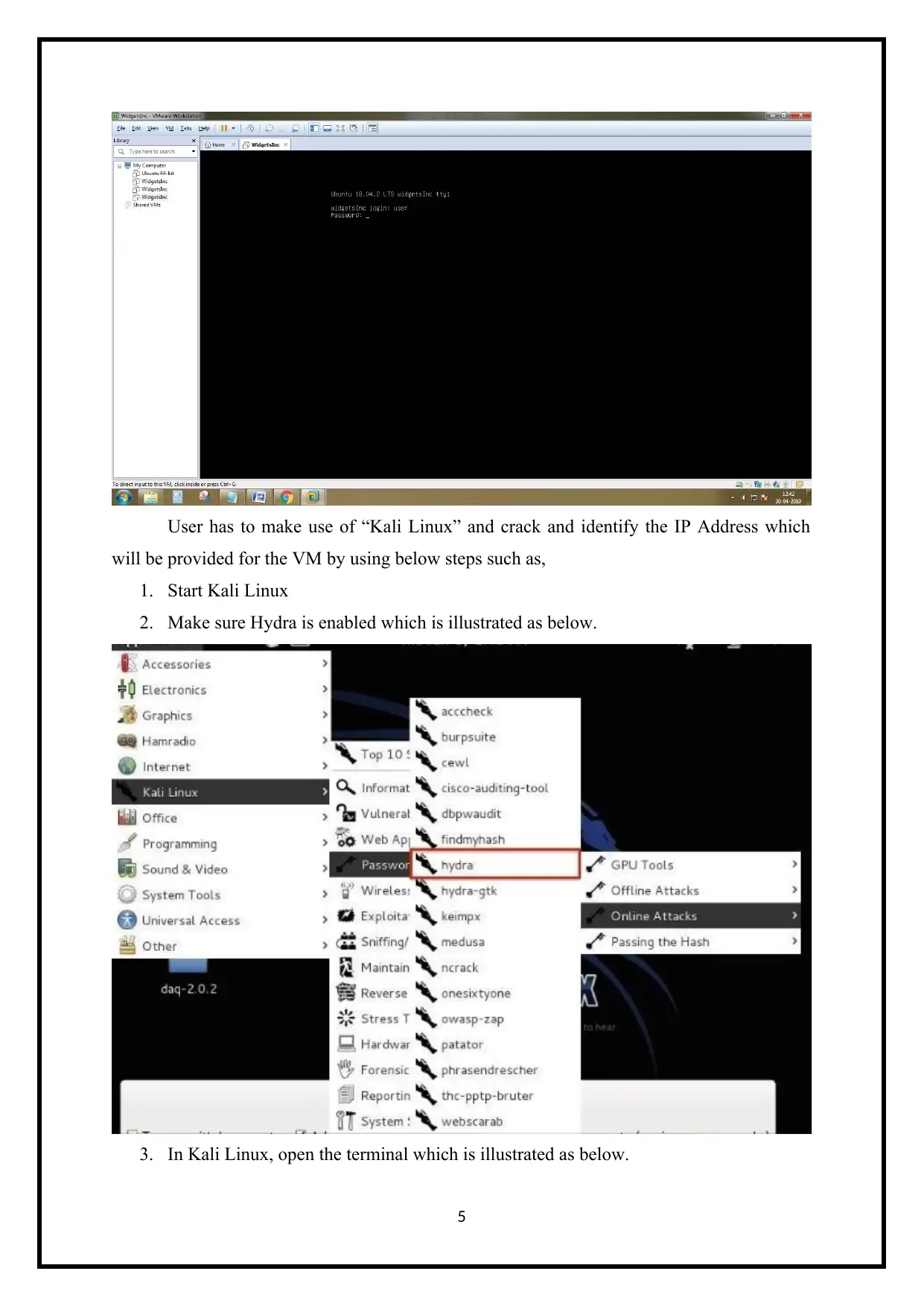
User has to make use of “Kali Linux” and crack and identify the IP Address which
will be provided for the VM by using below steps such as,
1. Start Kali Linux
2. Make sure Hydra is enabled which is illustrated as below.
3. In Kali Linux, open the terminal which is illustrated as below.
5
will be provided for the VM by using below steps such as,
1. Start Kali Linux
2. Make sure Hydra is enabled which is illustrated as below.
3. In Kali Linux, open the terminal which is illustrated as below.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4. By crack the IP address, user name and password by using the below command on
terminal,
hydra -t 1 -1 admin -P /root/Desktop/password.1st -vV 192.168.1.1 ftp
It is illustrated as below.
6
terminal,
hydra -t 1 -1 admin -P /root/Desktop/password.1st -vV 192.168.1.1 ftp
It is illustrated as below.
6
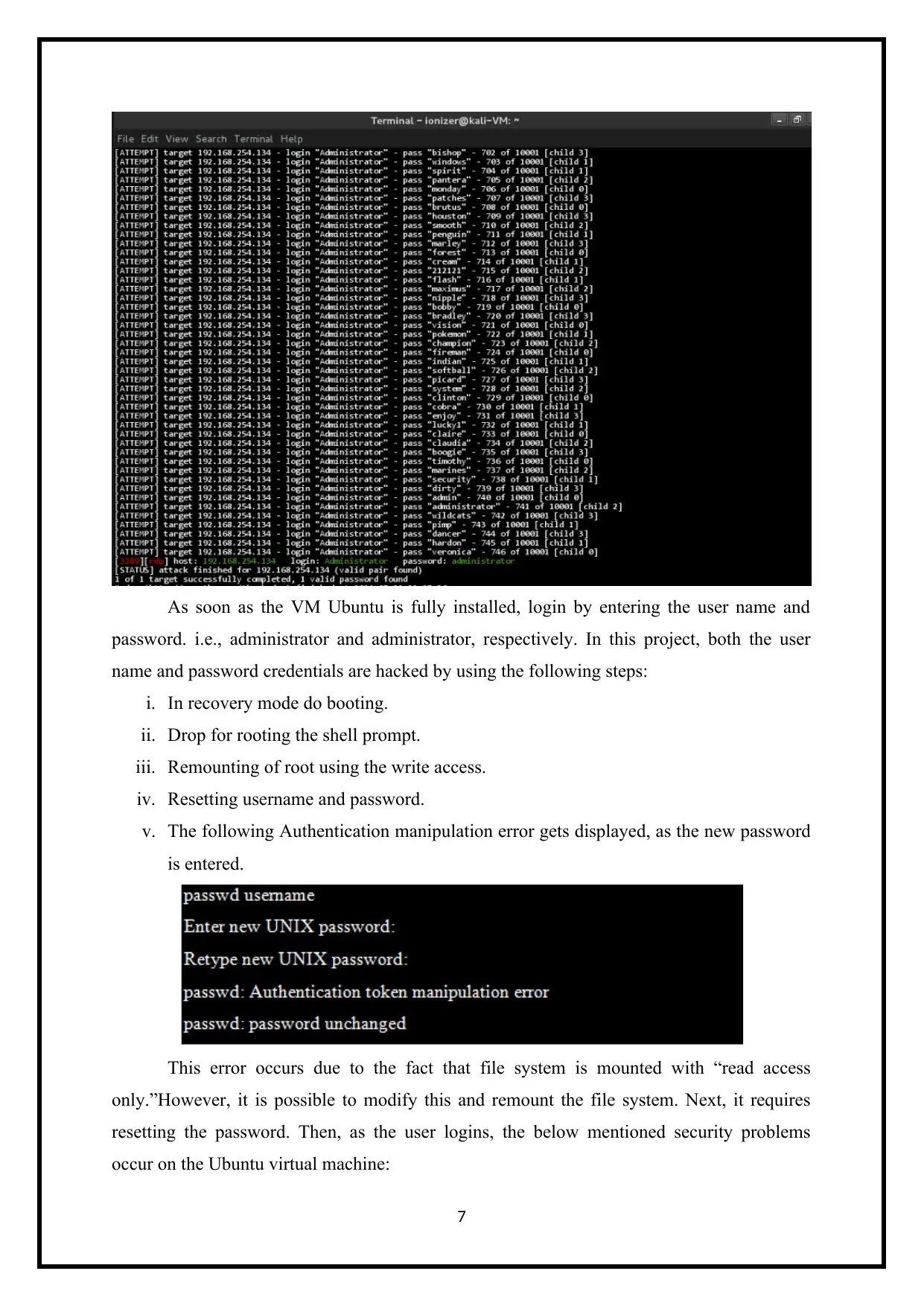
As soon as the VM Ubuntu is fully installed, login by entering the user name and
password. i.e., administrator and administrator, respectively. In this project, both the user
name and password credentials are hacked by using the following steps:
i. In recovery mode do booting.
ii. Drop for rooting the shell prompt.
iii. Remounting of root using the write access.
iv. Resetting username and password.
v. The following Authentication manipulation error gets displayed, as the new password
is entered.
This error occurs due to the fact that file system is mounted with “read access
only.”However, it is possible to modify this and remount the file system. Next, it requires
resetting the password. Then, as the user logins, the below mentioned security problems
occur on the Ubuntu virtual machine:
7
password. i.e., administrator and administrator, respectively. In this project, both the user
name and password credentials are hacked by using the following steps:
i. In recovery mode do booting.
ii. Drop for rooting the shell prompt.
iii. Remounting of root using the write access.
iv. Resetting username and password.
v. The following Authentication manipulation error gets displayed, as the new password
is entered.
This error occurs due to the fact that file system is mounted with “read access
only.”However, it is possible to modify this and remount the file system. Next, it requires
resetting the password. Then, as the user logins, the below mentioned security problems
occur on the Ubuntu virtual machine:
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

When the data is transmitted via network, the encrypt data communication
problems occur related to monitoring of the encrypted data, along with
password.
Security patches
Network services problems on the VM instance.
Web server hardening problems
Password setting problems
Open SSL problems
Backup problems
Malware problems
3. System Security Investigation
For security evaluation of a system on a given virtual machine image file this section
sheds light on the investigation of system security on the VM. The assessment or evaluation
of security is utilized to look at the system to decide the compliance of the system based on
specifications, security standards, and model. It is watching the system’s functional behaviour
by endeavouring to enter the system. As Ubuntu 18.04, in the given VM image file, security
assessment in the international standard for computer security certification is utilized to gives
a confirmation that an item fulfils a characterized arrangement of security needs. The security
prerequisites’ specification is utilized to indicate the security targets (Jendrosch et al., 2014).
The security evaluation is utilized to do changes in the configuration and use the extra
packages. Further, it assesses the configuration manual for disclosing how to set up the
assessed configuration to give the data to the admin and client, which can be guarantee on
system operation’s security. Security assessment uses full disk encryption to expand the data
assurance in the system. It enables the users to encryption and ensure protection of data. It
also carried out software updates on Ubuntu 18.04. It is significant part to evaluate the
security that is utilized to offer assurance against any vulnerabilities.
The below depicted figures show how with the help of Ubuntu OS, system security
and system hardening can be performed.
8
problems occur related to monitoring of the encrypted data, along with
password.
Security patches
Network services problems on the VM instance.
Web server hardening problems
Password setting problems
Open SSL problems
Backup problems
Malware problems
3. System Security Investigation
For security evaluation of a system on a given virtual machine image file this section
sheds light on the investigation of system security on the VM. The assessment or evaluation
of security is utilized to look at the system to decide the compliance of the system based on
specifications, security standards, and model. It is watching the system’s functional behaviour
by endeavouring to enter the system. As Ubuntu 18.04, in the given VM image file, security
assessment in the international standard for computer security certification is utilized to gives
a confirmation that an item fulfils a characterized arrangement of security needs. The security
prerequisites’ specification is utilized to indicate the security targets (Jendrosch et al., 2014).
The security evaluation is utilized to do changes in the configuration and use the extra
packages. Further, it assesses the configuration manual for disclosing how to set up the
assessed configuration to give the data to the admin and client, which can be guarantee on
system operation’s security. Security assessment uses full disk encryption to expand the data
assurance in the system. It enables the users to encryption and ensure protection of data. It
also carried out software updates on Ubuntu 18.04. It is significant part to evaluate the
security that is utilized to offer assurance against any vulnerabilities.
The below depicted figures show how with the help of Ubuntu OS, system security
and system hardening can be performed.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
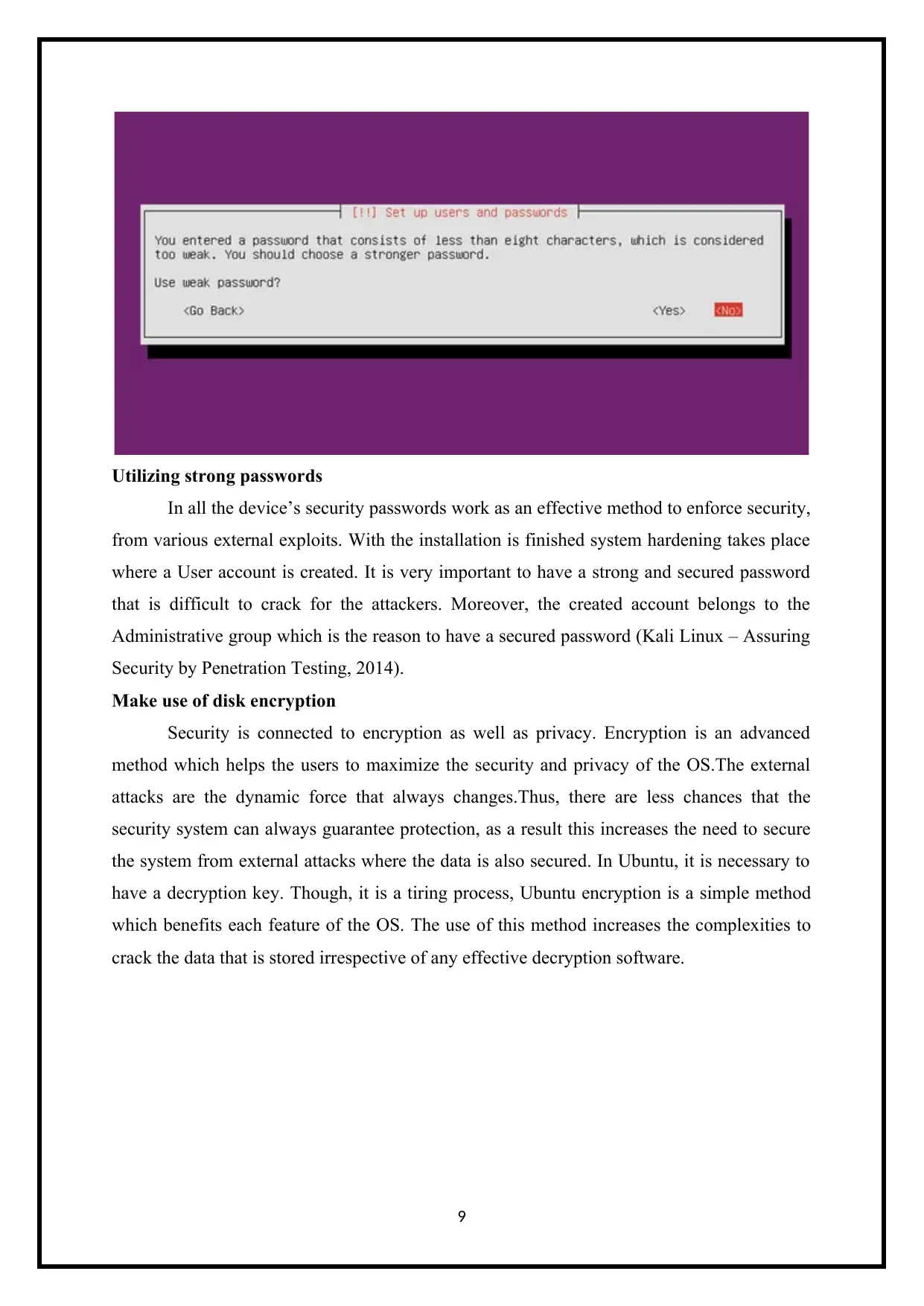
Utilizing strong passwords
In all the device’s security passwords work as an effective method to enforce security,
from various external exploits. With the installation is finished system hardening takes place
where a User account is created. It is very important to have a strong and secured password
that is difficult to crack for the attackers. Moreover, the created account belongs to the
Administrative group which is the reason to have a secured password (Kali Linux – Assuring
Security by Penetration Testing, 2014).
Make use of disk encryption
Security is connected to encryption as well as privacy. Encryption is an advanced
method which helps the users to maximize the security and privacy of the OS.The external
attacks are the dynamic force that always changes.Thus, there are less chances that the
security system can always guarantee protection, as a result this increases the need to secure
the system from external attacks where the data is also secured. In Ubuntu, it is necessary to
have a decryption key. Though, it is a tiring process, Ubuntu encryption is a simple method
which benefits each feature of the OS. The use of this method increases the complexities to
crack the data that is stored irrespective of any effective decryption software.
9
In all the device’s security passwords work as an effective method to enforce security,
from various external exploits. With the installation is finished system hardening takes place
where a User account is created. It is very important to have a strong and secured password
that is difficult to crack for the attackers. Moreover, the created account belongs to the
Administrative group which is the reason to have a secured password (Kali Linux – Assuring
Security by Penetration Testing, 2014).
Make use of disk encryption
Security is connected to encryption as well as privacy. Encryption is an advanced
method which helps the users to maximize the security and privacy of the OS.The external
attacks are the dynamic force that always changes.Thus, there are less chances that the
security system can always guarantee protection, as a result this increases the need to secure
the system from external attacks where the data is also secured. In Ubuntu, it is necessary to
have a decryption key. Though, it is a tiring process, Ubuntu encryption is a simple method
which benefits each feature of the OS. The use of this method increases the complexities to
crack the data that is stored irrespective of any effective decryption software.
9
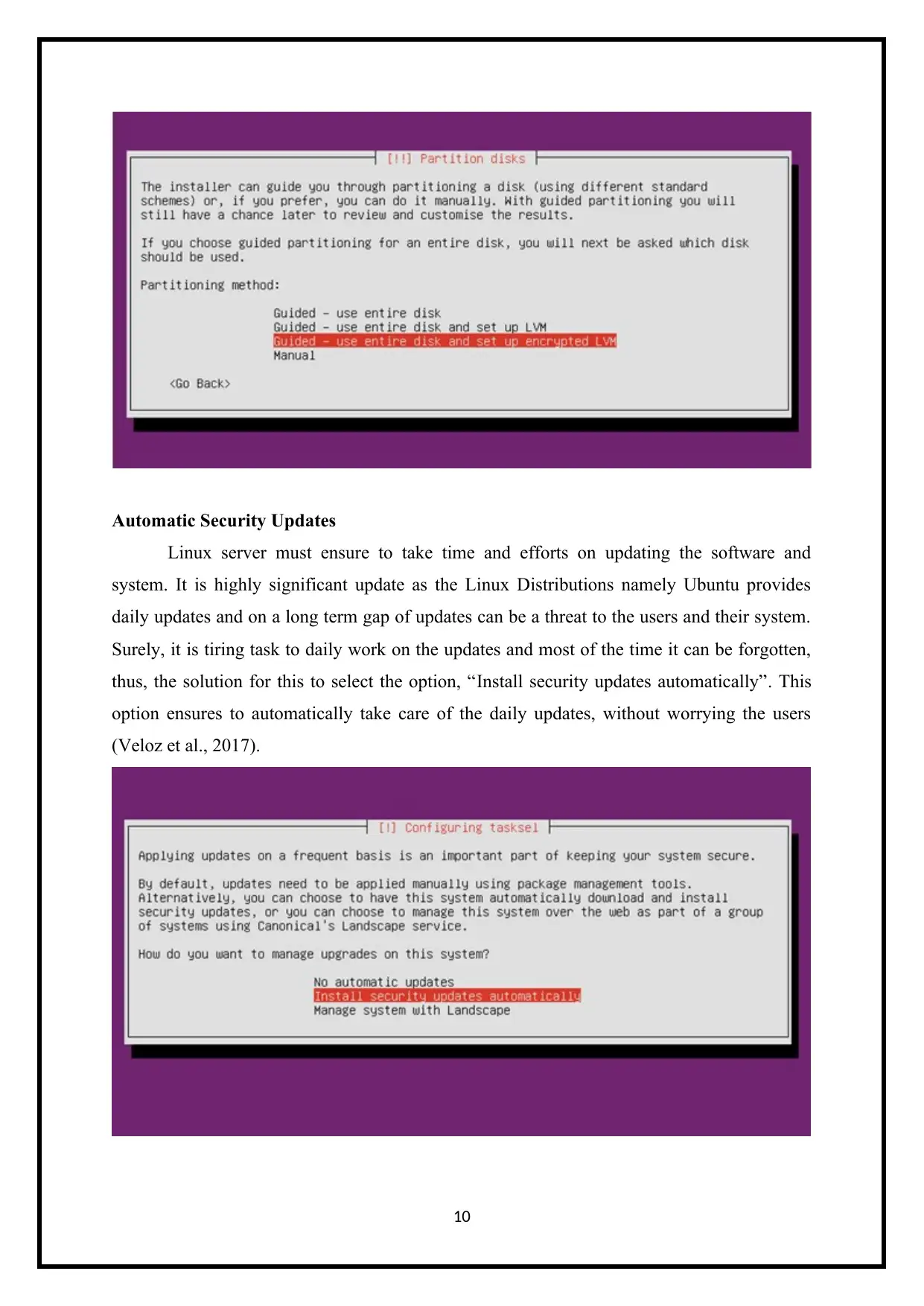
Automatic Security Updates
Linux server must ensure to take time and efforts on updating the software and
system. It is highly significant update as the Linux Distributions namely Ubuntu provides
daily updates and on a long term gap of updates can be a threat to the users and their system.
Surely, it is tiring task to daily work on the updates and most of the time it can be forgotten,
thus, the solution for this to select the option, “Install security updates automatically”. This
option ensures to automatically take care of the daily updates, without worrying the users
(Veloz et al., 2017).
10
Linux server must ensure to take time and efforts on updating the software and
system. It is highly significant update as the Linux Distributions namely Ubuntu provides
daily updates and on a long term gap of updates can be a threat to the users and their system.
Surely, it is tiring task to daily work on the updates and most of the time it can be forgotten,
thus, the solution for this to select the option, “Install security updates automatically”. This
option ensures to automatically take care of the daily updates, without worrying the users
(Veloz et al., 2017).
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





