BTEC HND in Computing & System Development: Systems Architecture
VerifiedAdded on 2021/05/20
|52
|8083
|1763
Homework Assignment
AI Summary
This assignment on Computer Systems Architecture provides a detailed exploration of computer systems, starting with an introduction to hardware and software components. It identifies and explains the main subsystems of a computer, including the CPU, main memory, and input/output subsystem, detailing their organization and interconnections. The assignment also examines the purpose and operation of the CPU, assessing its dependency and performance concerning associated systems and subsystems, considering factors like clock rate, calculation units, cache size, bus protocols, and sub-architecture design. Furthermore, it covers various operating systems, their purposes, uses, and hardware requirements, along with the architecture of operating systems like Linux, Windows, and Mac OS X. The assignment also explains the relationships between hardware and network addresses, including their use with regards to networking devices and components, and compares common physical and logical networking topologies, explaining their differences and purposes. Finally, it evaluates the OSI and TCP/IP models concerning hierarchy, layers, and services, including information on associated protocols and hardware, providing a comprehensive understanding of computer systems and networking.

UKCBC Computer Systems Architecture
Name of the student: MD.ABU SAYAD SAZZAD
Course: BTEC HND in COMPUTING & SYSTEM DEVELOPMENT
Student ID No: 17000101
Campus: WENTWORTH HOUSE
Name of the Module: Computer Systems Architecture
Introduce a computer system.
A computer is a complex system consisting of both hardware and software
components.
The Hardware:
Name of the student: MD.ABU SAYAD SAZZAD
Course: BTEC HND in COMPUTING & SYSTEM DEVELOPMENT
Student ID No: 17000101
Campus: WENTWORTH HOUSE
Name of the Module: Computer Systems Architecture
Introduce a computer system.
A computer is a complex system consisting of both hardware and software
components.
The Hardware:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The hardware is the machinery itself. It is made up of the physical parts or devices of
the computer system like the electronic Integrated Circuits (ICs), magnetic storage
media and other mechanical devices like input devices, output devices etc. All these
various hardware are linked together to form an effective functional unit. The various
types of hardware used in the computers, has evolved from vacuum tubes of the first
generation to Ultra Large Scale Integrated Circuits of the present generation.
The Software:
The computer hardware itself is not capable of doing anything on its own. It has to be
given explicit instructions to perform the specific task. The computer program is the
one which controls the processing activities of the computer. The computer thus
functions according to the instructions written in the program. Software mainly
consists of these computer programs, procedures and other documentation used in the
operation of a computer system. Software is a collection of programs which utilize
and enhance the capability of the hardware.
the computer system like the electronic Integrated Circuits (ICs), magnetic storage
media and other mechanical devices like input devices, output devices etc. All these
various hardware are linked together to form an effective functional unit. The various
types of hardware used in the computers, has evolved from vacuum tubes of the first
generation to Ultra Large Scale Integrated Circuits of the present generation.
The Software:
The computer hardware itself is not capable of doing anything on its own. It has to be
given explicit instructions to perform the specific task. The computer program is the
one which controls the processing activities of the computer. The computer thus
functions according to the instructions written in the program. Software mainly
consists of these computer programs, procedures and other documentation used in the
operation of a computer system. Software is a collection of programs which utilize
and enhance the capability of the hardware.
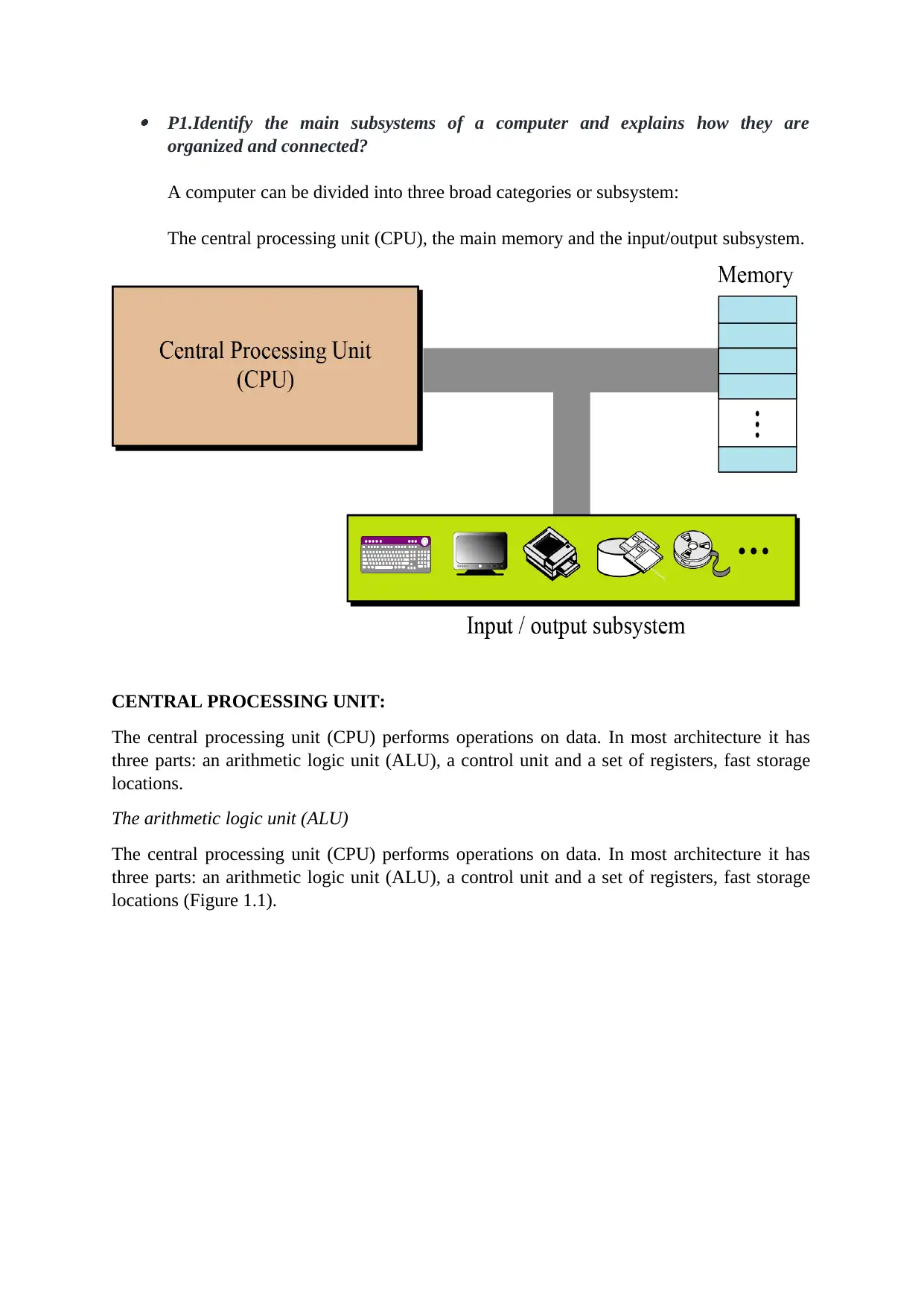
P1.Identify the main subsystems of a computer and explains how they are
organized and connected?
A computer can be divided into three broad categories or subsystem:
The central processing unit (CPU), the main memory and the input/output subsystem.
CENTRAL PROCESSING UNIT:
The central processing unit (CPU) performs operations on data. In most architecture it has
three parts: an arithmetic logic unit (ALU), a control unit and a set of registers, fast storage
locations.
The arithmetic logic unit (ALU)
The central processing unit (CPU) performs operations on data. In most architecture it has
three parts: an arithmetic logic unit (ALU), a control unit and a set of registers, fast storage
locations (Figure 1.1).
organized and connected?
A computer can be divided into three broad categories or subsystem:
The central processing unit (CPU), the main memory and the input/output subsystem.
CENTRAL PROCESSING UNIT:
The central processing unit (CPU) performs operations on data. In most architecture it has
three parts: an arithmetic logic unit (ALU), a control unit and a set of registers, fast storage
locations.
The arithmetic logic unit (ALU)
The central processing unit (CPU) performs operations on data. In most architecture it has
three parts: an arithmetic logic unit (ALU), a control unit and a set of registers, fast storage
locations (Figure 1.1).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
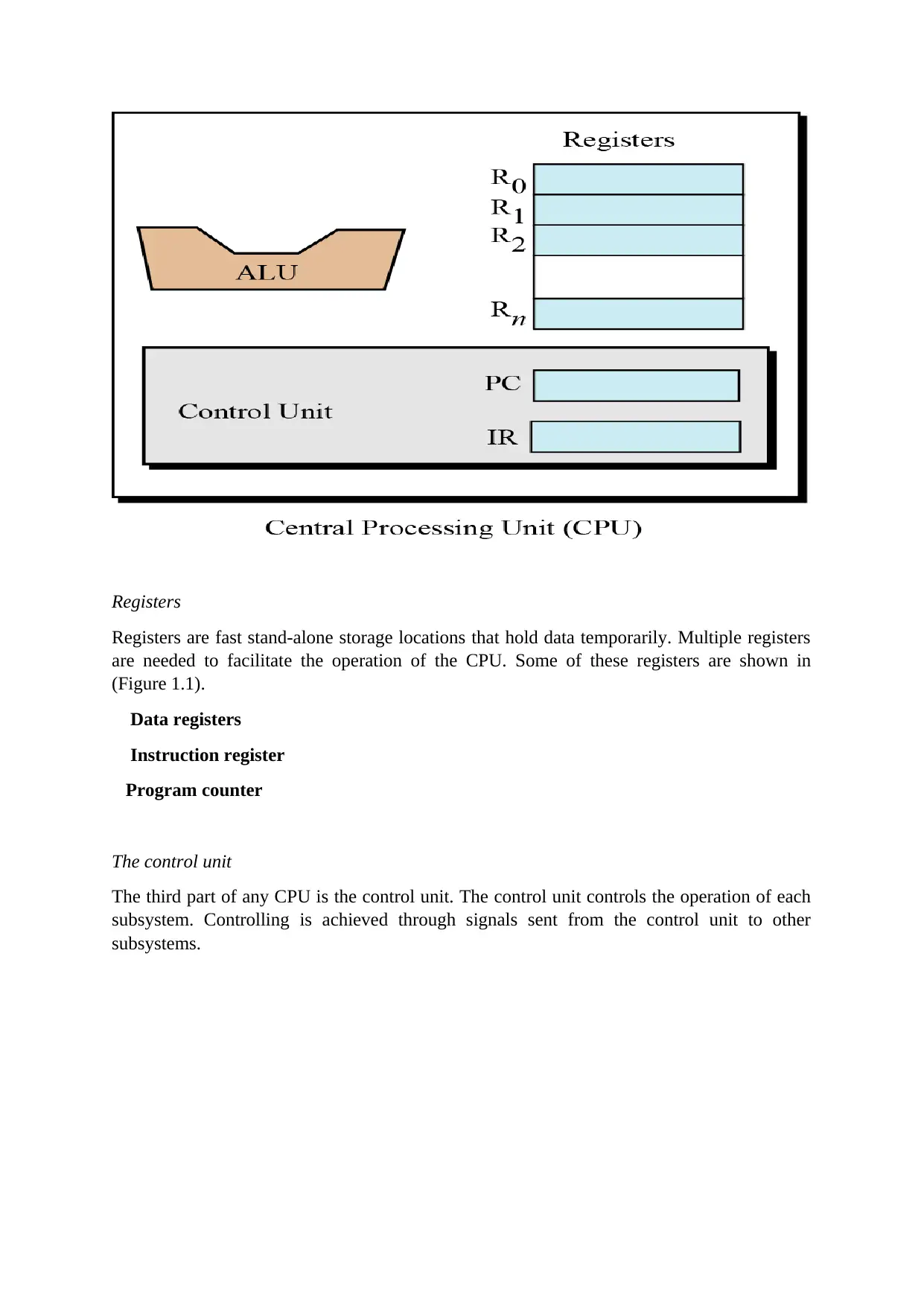
Registers
Registers are fast stand-alone storage locations that hold data temporarily. Multiple registers
are needed to facilitate the operation of the CPU. Some of these registers are shown in
(Figure 1.1).
Data registers
Instruction register
Program counter
The control unit
The third part of any CPU is the control unit. The control unit controls the operation of each
subsystem. Controlling is achieved through signals sent from the control unit to other
subsystems.
Registers are fast stand-alone storage locations that hold data temporarily. Multiple registers
are needed to facilitate the operation of the CPU. Some of these registers are shown in
(Figure 1.1).
Data registers
Instruction register
Program counter
The control unit
The third part of any CPU is the control unit. The control unit controls the operation of each
subsystem. Controlling is achieved through signals sent from the control unit to other
subsystems.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
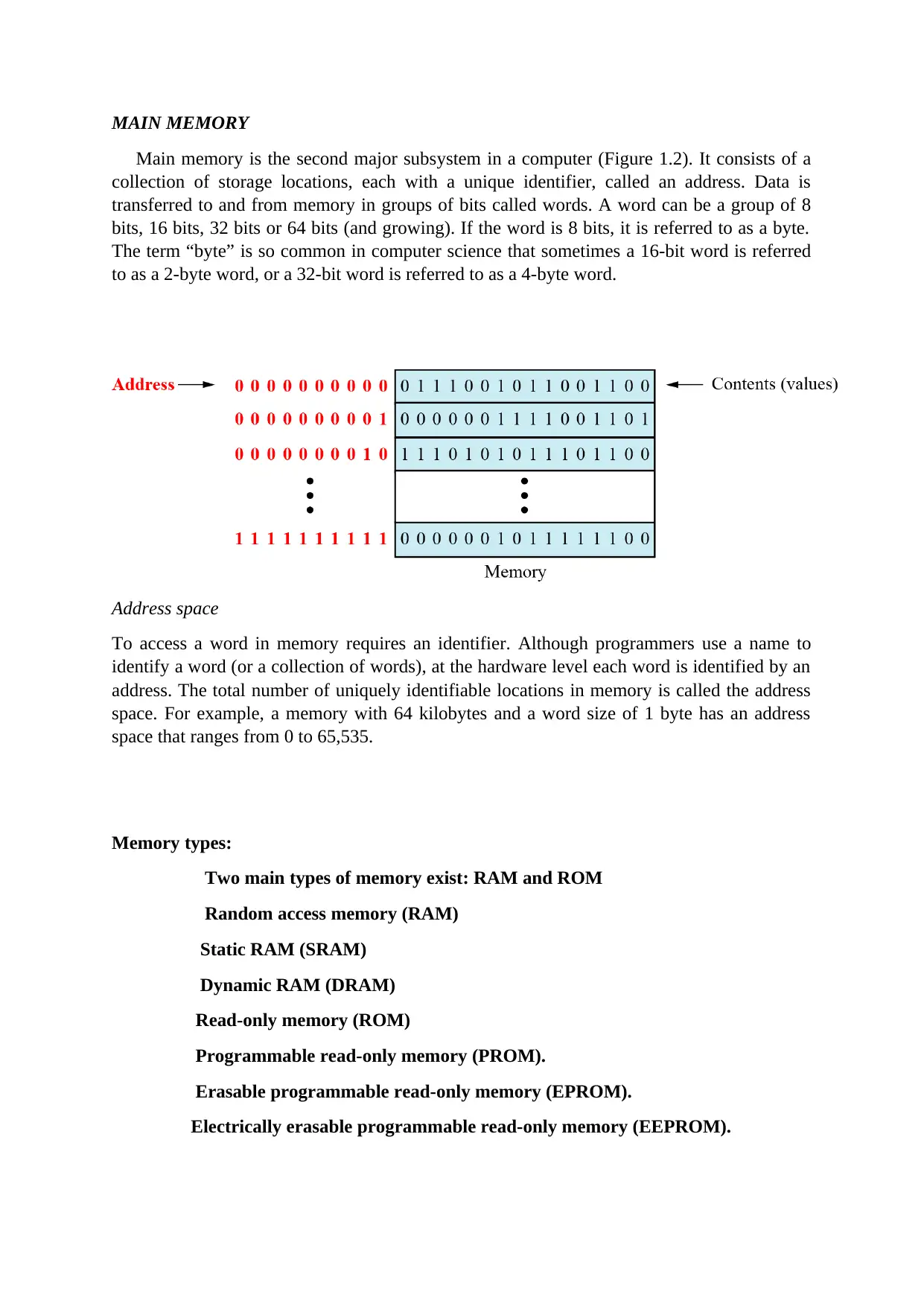
MAIN MEMORY
Main memory is the second major subsystem in a computer (Figure 1.2). It consists of a
collection of storage locations, each with a unique identifier, called an address. Data is
transferred to and from memory in groups of bits called words. A word can be a group of 8
bits, 16 bits, 32 bits or 64 bits (and growing). If the word is 8 bits, it is referred to as a byte.
The term “byte” is so common in computer science that sometimes a 16-bit word is referred
to as a 2-byte word, or a 32-bit word is referred to as a 4-byte word.
Address space
To access a word in memory requires an identifier. Although programmers use a name to
identify a word (or a collection of words), at the hardware level each word is identified by an
address. The total number of uniquely identifiable locations in memory is called the address
space. For example, a memory with 64 kilobytes and a word size of 1 byte has an address
space that ranges from 0 to 65,535.
Memory types:
Two main types of memory exist: RAM and ROM
Random access memory (RAM)
Static RAM (SRAM)
Dynamic RAM (DRAM)
Read-only memory (ROM)
Programmable read-only memory (PROM).
Erasable programmable read-only memory (EPROM).
Electrically erasable programmable read-only memory (EEPROM).
Main memory is the second major subsystem in a computer (Figure 1.2). It consists of a
collection of storage locations, each with a unique identifier, called an address. Data is
transferred to and from memory in groups of bits called words. A word can be a group of 8
bits, 16 bits, 32 bits or 64 bits (and growing). If the word is 8 bits, it is referred to as a byte.
The term “byte” is so common in computer science that sometimes a 16-bit word is referred
to as a 2-byte word, or a 32-bit word is referred to as a 4-byte word.
Address space
To access a word in memory requires an identifier. Although programmers use a name to
identify a word (or a collection of words), at the hardware level each word is identified by an
address. The total number of uniquely identifiable locations in memory is called the address
space. For example, a memory with 64 kilobytes and a word size of 1 byte has an address
space that ranges from 0 to 65,535.
Memory types:
Two main types of memory exist: RAM and ROM
Random access memory (RAM)
Static RAM (SRAM)
Dynamic RAM (DRAM)
Read-only memory (ROM)
Programmable read-only memory (PROM).
Erasable programmable read-only memory (EPROM).
Electrically erasable programmable read-only memory (EEPROM).
INPUT/OUTPUT SUBSYSTEM
The third major subsystem in a computer is the collection of devices referred to as the
input/output (I/O) subsystem. This subsystem allows a computer to communicate with the
outside world and to store programs and data even when the power is off. Input/output
devices can be divided into two broad categories: non-storage and storage devices.
SUBSYSTEM INTERCONNECTION
The previous sections outlined the characteristics of the three subsystems (CPU, main
memory, and I/O) in a stand-alone computer. In this section, we explore how these three
subsystems are interconnected. The interconnection plays an important role because
information needs to be exchanged between the three subsystems.
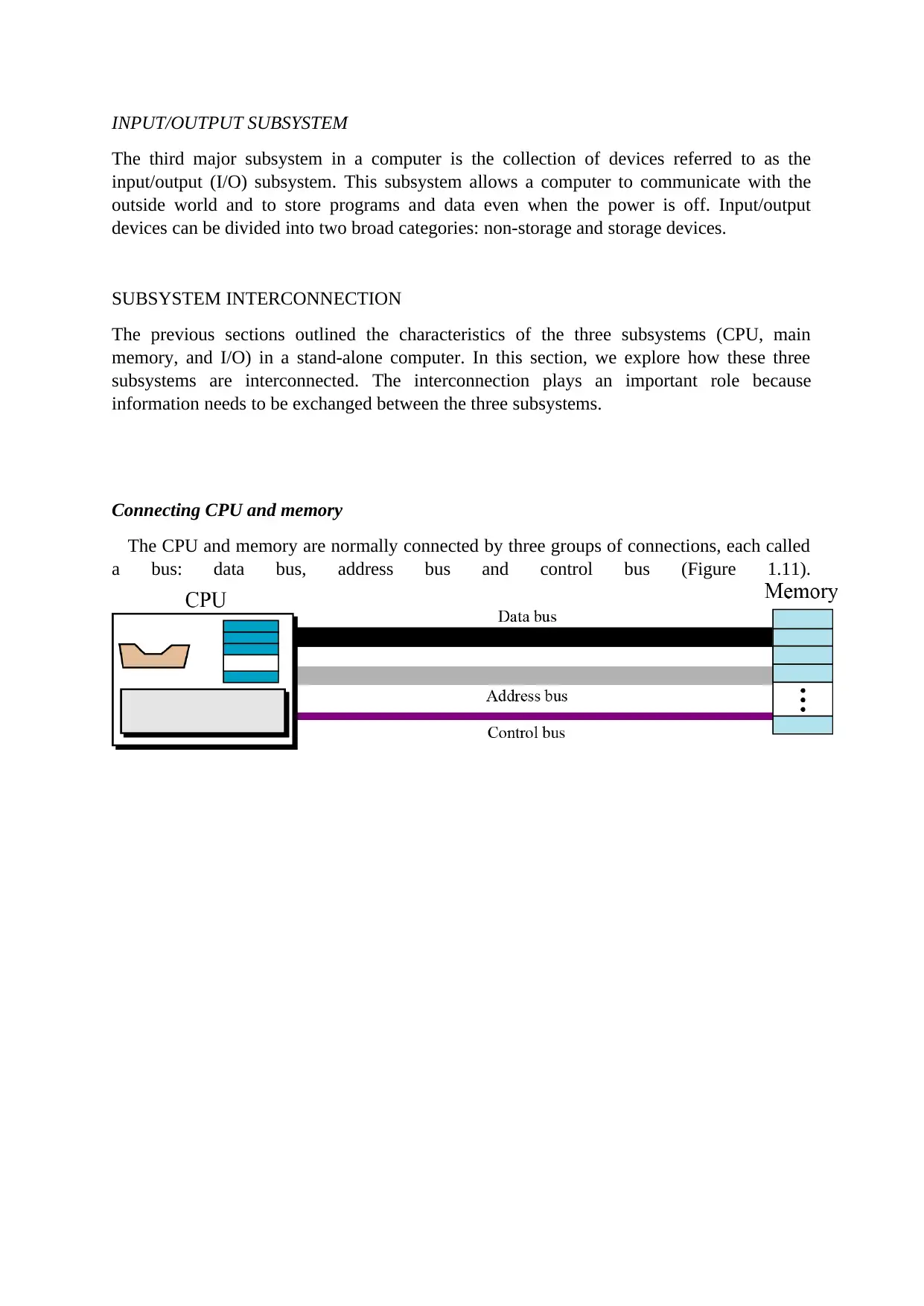
Connecting CPU and memory
The CPU and memory are normally connected by three groups of connections, each called
a bus: data bus, address bus and control bus (Figure 1.11).
The third major subsystem in a computer is the collection of devices referred to as the
input/output (I/O) subsystem. This subsystem allows a computer to communicate with the
outside world and to store programs and data even when the power is off. Input/output
devices can be divided into two broad categories: non-storage and storage devices.
SUBSYSTEM INTERCONNECTION
The previous sections outlined the characteristics of the three subsystems (CPU, main
memory, and I/O) in a stand-alone computer. In this section, we explore how these three
subsystems are interconnected. The interconnection plays an important role because
information needs to be exchanged between the three subsystems.
Connecting CPU and memory
The CPU and memory are normally connected by three groups of connections, each called
a bus: data bus, address bus and control bus (Figure 1.11).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
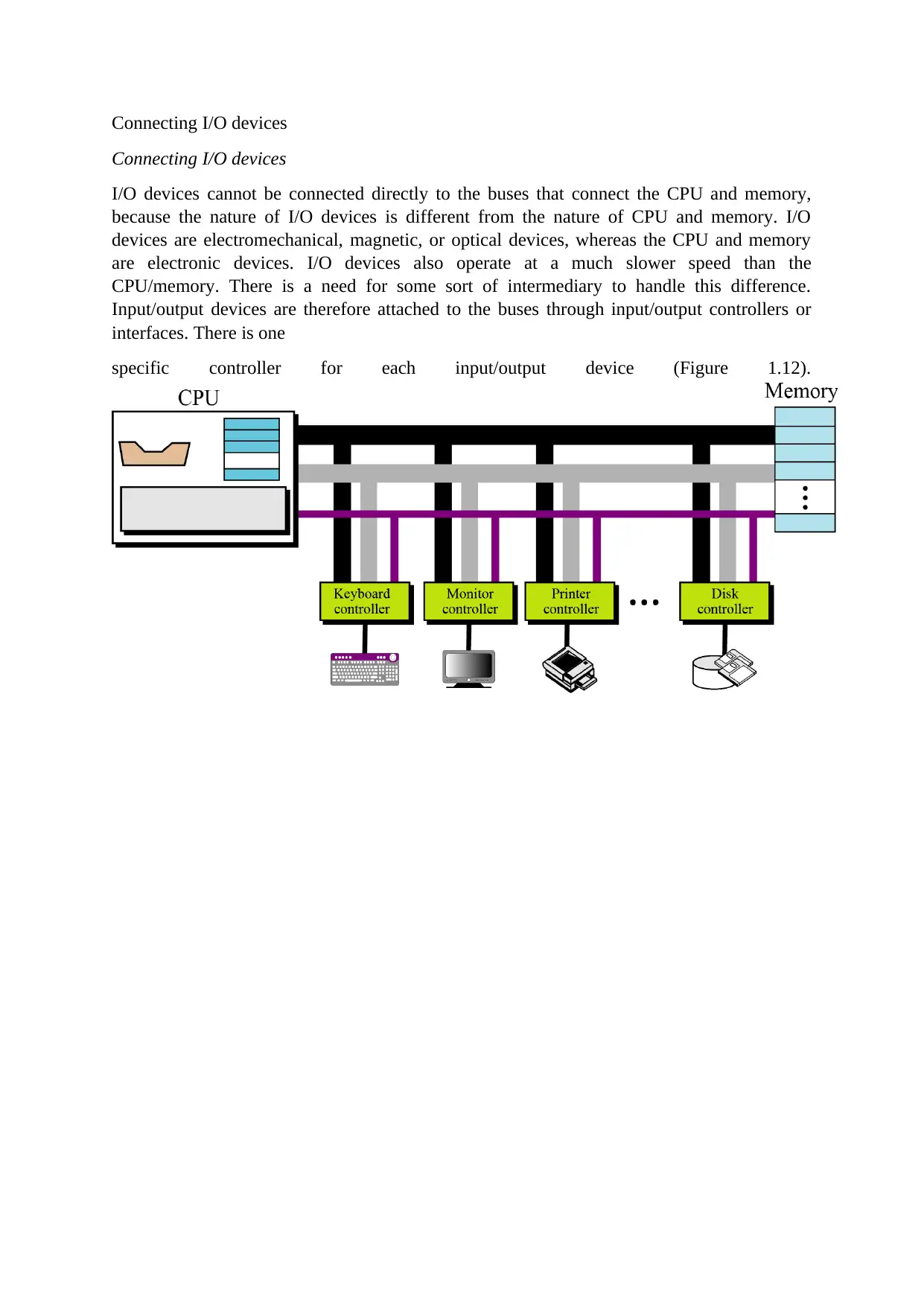
Connecting I/O devices
Connecting I/O devices
I/O devices cannot be connected directly to the buses that connect the CPU and memory,
because the nature of I/O devices is different from the nature of CPU and memory. I/O
devices are electromechanical, magnetic, or optical devices, whereas the CPU and memory
are electronic devices. I/O devices also operate at a much slower speed than the
CPU/memory. There is a need for some sort of intermediary to handle this difference.
Input/output devices are therefore attached to the buses through input/output controllers or
interfaces. There is one
specific controller for each input/output device (Figure 1.12).
Connecting I/O devices
I/O devices cannot be connected directly to the buses that connect the CPU and memory,
because the nature of I/O devices is different from the nature of CPU and memory. I/O
devices are electromechanical, magnetic, or optical devices, whereas the CPU and memory
are electronic devices. I/O devices also operate at a much slower speed than the
CPU/memory. There is a need for some sort of intermediary to handle this difference.
Input/output devices are therefore attached to the buses through input/output controllers or
interfaces. There is one
specific controller for each input/output device (Figure 1.12).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

P2
The purpose and operation of the CPU.
Central Processing Unit. The CPU (Central Processing Unit) is the part of a computer
system that is commonly referred to as the "brains" of a computer. The CPU is also
known as the processor or microprocessor. The CPU is responsible for executing a
sequence of stored instructions called a program.
A central processing unit (CPU) is the electronic circuitry within a computer that
carries out the instructions of a computer program by performing the basic arithmetic,
logical, control and input/output (I/O) operations specified by the instructions.
Assess CPU dependency and performance with regards to associated systems
and subsystems.
This can vary widely by CPU, and it primarily dependent on six things:
1. Clock Rate of the CPU - that is, how many internal operations-per-second
(nowadays measured in Gigahertz) does the CPU perform.
2. Number of available calculation units - generally speaking, those CPUs with
more execution units can perform more work per unit time than those with fewer
execution units. Typically, these days we measure this in "cores", though this isn't
technically correct. This speed is dependent on the specific workload, so you really
need to know what the typical workload of the CPU is, before this metric can be
applied.
3. Size of on-die caches - larger L1, L2, and L3 caches speed up memory access,
which leads to faster performance. There generally is a law of diminishing returns in
cache size, so bigger will not always give you better performance. In addition, certain
workloads are too big to fit into any reasonable cache size, so the performance of the
CPU isn't affected by cache size for those workloads.
4.Design of the CPU bus protocol - certain CPU bus protocols are more efficient
than others, and improvements in bus protocols lead to faster communications
between CPUs (in a multi-CPU system) and/or Memory and/or I/O subsystems.
5. Size and speed of the external buses - the "width" of the buses (as well as the
clock rate of such buses) attached to a CPU heavily influences the ability of the
attached subsystems to get data to the CPU. Data starvation is a primary cause of
perceived slowness in CPUs.
The purpose and operation of the CPU.
Central Processing Unit. The CPU (Central Processing Unit) is the part of a computer
system that is commonly referred to as the "brains" of a computer. The CPU is also
known as the processor or microprocessor. The CPU is responsible for executing a
sequence of stored instructions called a program.
A central processing unit (CPU) is the electronic circuitry within a computer that
carries out the instructions of a computer program by performing the basic arithmetic,
logical, control and input/output (I/O) operations specified by the instructions.
Assess CPU dependency and performance with regards to associated systems
and subsystems.
This can vary widely by CPU, and it primarily dependent on six things:
1. Clock Rate of the CPU - that is, how many internal operations-per-second
(nowadays measured in Gigahertz) does the CPU perform.
2. Number of available calculation units - generally speaking, those CPUs with
more execution units can perform more work per unit time than those with fewer
execution units. Typically, these days we measure this in "cores", though this isn't
technically correct. This speed is dependent on the specific workload, so you really
need to know what the typical workload of the CPU is, before this metric can be
applied.
3. Size of on-die caches - larger L1, L2, and L3 caches speed up memory access,
which leads to faster performance. There generally is a law of diminishing returns in
cache size, so bigger will not always give you better performance. In addition, certain
workloads are too big to fit into any reasonable cache size, so the performance of the
CPU isn't affected by cache size for those workloads.
4.Design of the CPU bus protocol - certain CPU bus protocols are more efficient
than others, and improvements in bus protocols lead to faster communications
between CPUs (in a multi-CPU system) and/or Memory and/or I/O subsystems.
5. Size and speed of the external buses - the "width" of the buses (as well as the
clock rate of such buses) attached to a CPU heavily influences the ability of the
attached subsystems to get data to the CPU. Data starvation is a primary cause of
perceived slowness in CPUs.

6. Design of the CPU sub architecture- engineers are continually refining and
improving the internal design of the CPU itself. Later generations of a CPU are
almost always faster, due to improved layout or new innovations which make
calculations faster (even given no change in any of the other above factors).
improving the internal design of the CPU itself. Later generations of a CPU are
almost always faster, due to improved layout or new innovations which make
calculations faster (even given no change in any of the other above factors).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
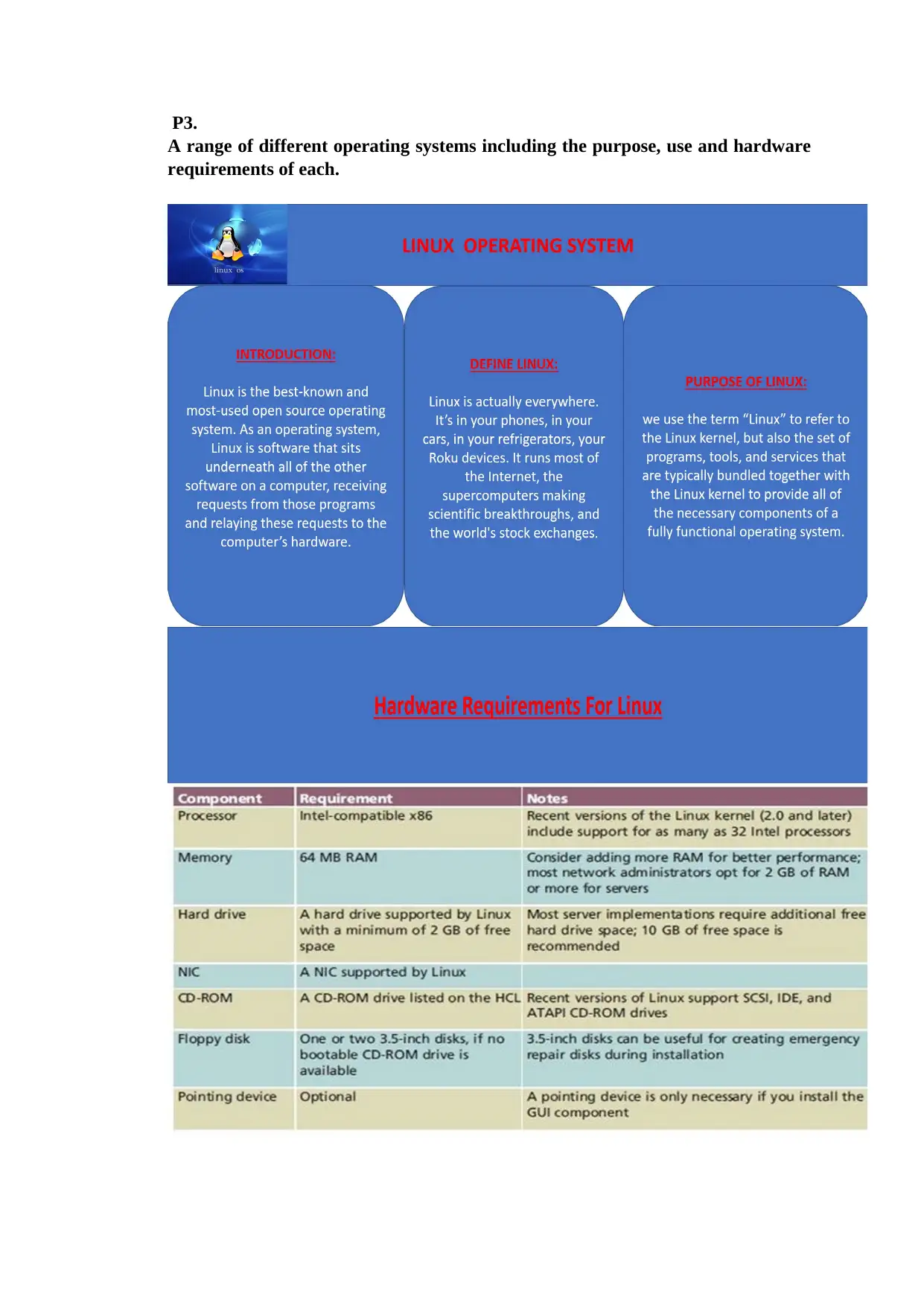
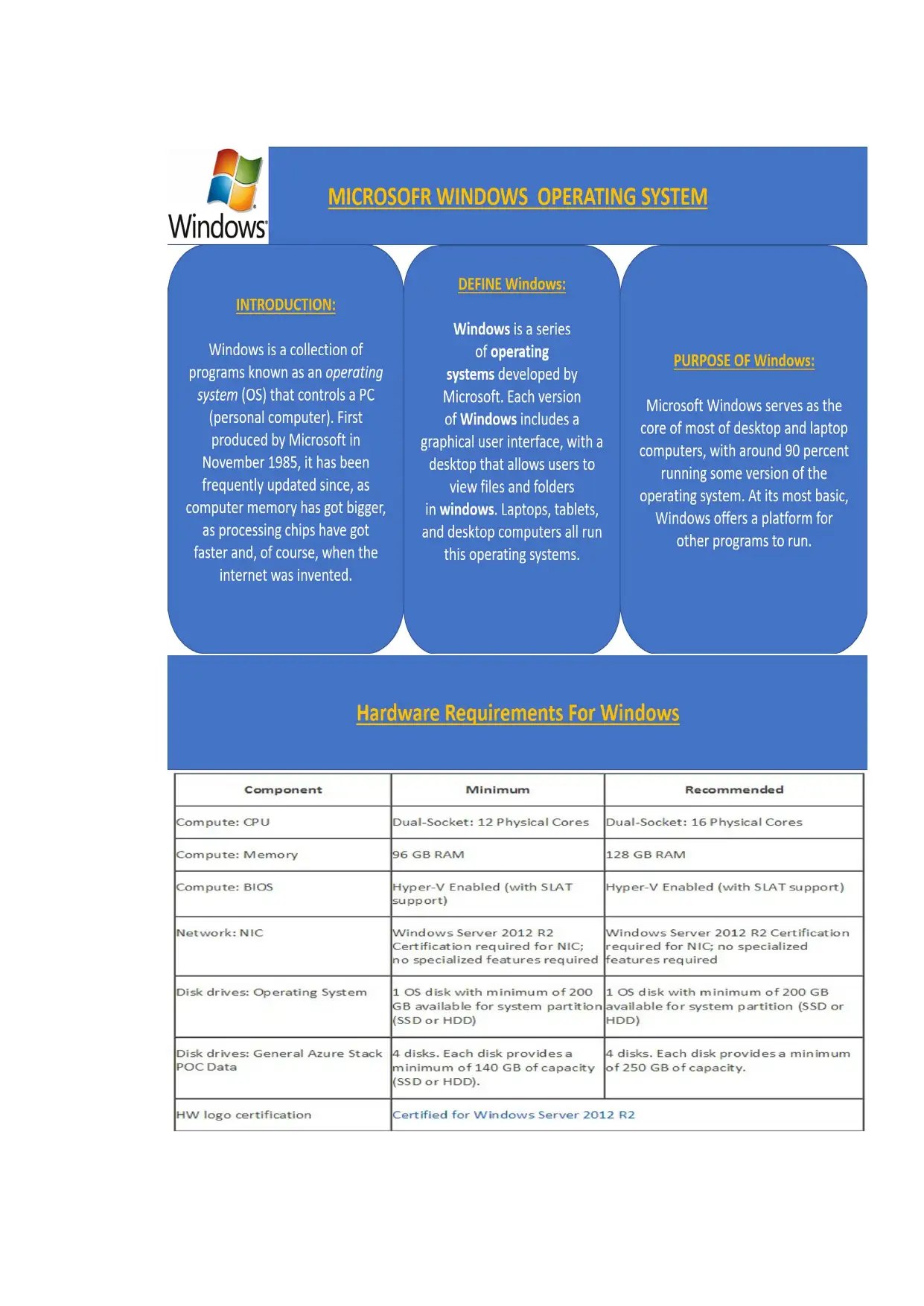
P3.
A range of different operating systems including the purpose, use and hardware
requirements of each.
A range of different operating systems including the purpose, use and hardware
requirements of each.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 52
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





![Operating System Architecture Report - [University Name], Semester 1](/_next/image/?url=https%3A%2F%2Fdesklib.com%2Fmedia%2Foperating-system-architecture-guide_page_2.jpg&w=256&q=75)