Impact of Computer Systems on Business Development
VerifiedAdded on 2021/04/19
|9
|2117
|32
Report
AI Summary
This report provides a comprehensive overview of computer systems and their impact on modern business operations. It begins by detailing the hardware and software components essential for computer systems, including motherboards, networking cards, graphics cards, processors, hard drives, USB ports, and monitors, as well as system, utility, and application software. The report then explores how computers have revolutionized business, enabling better organization, data storage, and efficiency. It discusses the benefits of computerization, such as improved file management and cost savings, while also addressing potential risks, including repetitive stress injuries, data security threats, and ergonomic hazards. The report further examines the potential dangers of computer ergonomics, emphasizing the importance of reducing stress and fatigue through proper workplace design and practices. It also delves into data protection, outlining the requirements of the Data Protection Act and the European Data Protection Directive, highlighting the importance of fair data processing and individual rights. Finally, the report provides a list of relevant references.

report
[Document subtitle]
[Document subtitle]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Answer 1:.........................................................................................................................................2
Answer 2:.........................................................................................................................................3
Answer 3:.........................................................................................................................................4
Answer 4:.........................................................................................................................................6
References........................................................................................................................................8
Answer 1:.........................................................................................................................................2
Answer 2:.........................................................................................................................................3
Answer 3:.........................................................................................................................................4
Answer 4:.........................................................................................................................................6
References........................................................................................................................................8

Answer 1:
For the hardware system, there are different components which are used for the modern system:
a. The Motherboard
They are important for handling the technological devices which includes the different hard
drives, processor, memory and the ports mainly the USD.
b. The networking cards
They are for the integration to the motherboard to provide a way to connect to the network and
internet. The computers have the network card integration for connecting to Wi-Fi.
c. Graphics Cards
The categories are: integrated and expansion; where the expansion is the separate card connected
to the expansion port. This helps in creating proper images (Inyukina et al., 2016).
d. Processor
The important part of CPY for handing the instructions and the computer programs which are in
the memory of computer.
e. Hard drive
They are the programs and the files which are stored and comprise of the magnetized disks that
have the disks spin to read and then write data.
f. USB Ports
They are for covering the connections of different cables, connectors and communication.
g. Monitor
They are for handling the monitoring through HDMI or VGA which includes the display with
higher definition images and the Video Graphics Array (Glass et al., 2017).
The software components are the system, utilities and application software
a. System Software
For the hardware system, there are different components which are used for the modern system:
a. The Motherboard
They are important for handling the technological devices which includes the different hard
drives, processor, memory and the ports mainly the USD.
b. The networking cards
They are for the integration to the motherboard to provide a way to connect to the network and
internet. The computers have the network card integration for connecting to Wi-Fi.
c. Graphics Cards
The categories are: integrated and expansion; where the expansion is the separate card connected
to the expansion port. This helps in creating proper images (Inyukina et al., 2016).
d. Processor
The important part of CPY for handing the instructions and the computer programs which are in
the memory of computer.
e. Hard drive
They are the programs and the files which are stored and comprise of the magnetized disks that
have the disks spin to read and then write data.
f. USB Ports
They are for covering the connections of different cables, connectors and communication.
g. Monitor
They are for handling the monitoring through HDMI or VGA which includes the display with
higher definition images and the Video Graphics Array (Glass et al., 2017).
The software components are the system, utilities and application software
a. System Software
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

They are able to manage and then control the different hardware components with proper
interaction between the hardware and the other software. The system software is important for
the operation where the device drivers are also included in this category.
b. Utility Software
They are like anti-virus software, firewalls and the disk defragmenter which help in properly
maintaining and then protecting system. It does not directly interface with the hardware.
c. Application Software
The designing is to allow the user for completing the specific tasks and the different set of tasks.
This includes the programs that are set with the web browsers and the office software. They are
for the proper management and system maintenance (Ehrensberger & O’Brien, 2015).
Answer 2:
The computers have been able to help improve the way in which the business operates. The
technology has advanced with the major focus on allowing the applications of different types of
software. This can help the business to properly track the files and the other documents,
schedules and the deadlines. The computers help in allowing the business to properly organise
the information with the ability to store the larger amount of data which is convenient and easily
available at no-cost (Bundgaard, 2017). The ability of computer is to allow the company to
organise the files effectively to properly handle the management of time and its productivity.
The self-sufficiency is other factor, with cost effectiveness and speed that helps in allowing the
company to save the payroll of staff and the other equipment. The networking and the
inexpensive computers are set so that the company can easily store the data and save on the cost
of any file storage.
There are threats of using the computer which includes the repetitive stress injury, vision
problems, headache. Apart from this, the data can easily be hacked by the hackers if it is not
password protected. Hence, the company needs to assure about the same before storing any data
in the computer at workplace (Crossman, 2015).
Risks
interaction between the hardware and the other software. The system software is important for
the operation where the device drivers are also included in this category.
b. Utility Software
They are like anti-virus software, firewalls and the disk defragmenter which help in properly
maintaining and then protecting system. It does not directly interface with the hardware.
c. Application Software
The designing is to allow the user for completing the specific tasks and the different set of tasks.
This includes the programs that are set with the web browsers and the office software. They are
for the proper management and system maintenance (Ehrensberger & O’Brien, 2015).
Answer 2:
The computers have been able to help improve the way in which the business operates. The
technology has advanced with the major focus on allowing the applications of different types of
software. This can help the business to properly track the files and the other documents,
schedules and the deadlines. The computers help in allowing the business to properly organise
the information with the ability to store the larger amount of data which is convenient and easily
available at no-cost (Bundgaard, 2017). The ability of computer is to allow the company to
organise the files effectively to properly handle the management of time and its productivity.
The self-sufficiency is other factor, with cost effectiveness and speed that helps in allowing the
company to save the payroll of staff and the other equipment. The networking and the
inexpensive computers are set so that the company can easily store the data and save on the cost
of any file storage.
There are threats of using the computer which includes the repetitive stress injury, vision
problems, headache. Apart from this, the data can easily be hacked by the hackers if it is not
password protected. Hence, the company needs to assure about the same before storing any data
in the computer at workplace (Crossman, 2015).
Risks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The risks associated with the computer systems is the overuse injuries of the hand, with obesity
as there is no physical work that is being done. There are other problems like the muscle and the
joint problems, strain in the eyes as well as the behavioural problems due to the aggressive
behaviour (Certo, 2015).
Hazards
There are different hazards related to the health and the data security as well. The health could be
damaged with the carpal tunnel syndrome, and the repetitive injury strain, with eye strain due to
the computer and the vision syndromes. Hence, it is important to regularly exercise as well. On
the other hand, if the data is publicly available without much user encryption, then it can lead to
major loss of data. The malware scams and the phishing problems are related to the computer
security issues.
Potential dangers
With major reliability of the data on the computer, there are issues of the slow performance of
computer, erratic computer behaviours and the unexplained loss of data. It could lead to the
frequent crash of the computer and thereby, a major loss of the data security as well.
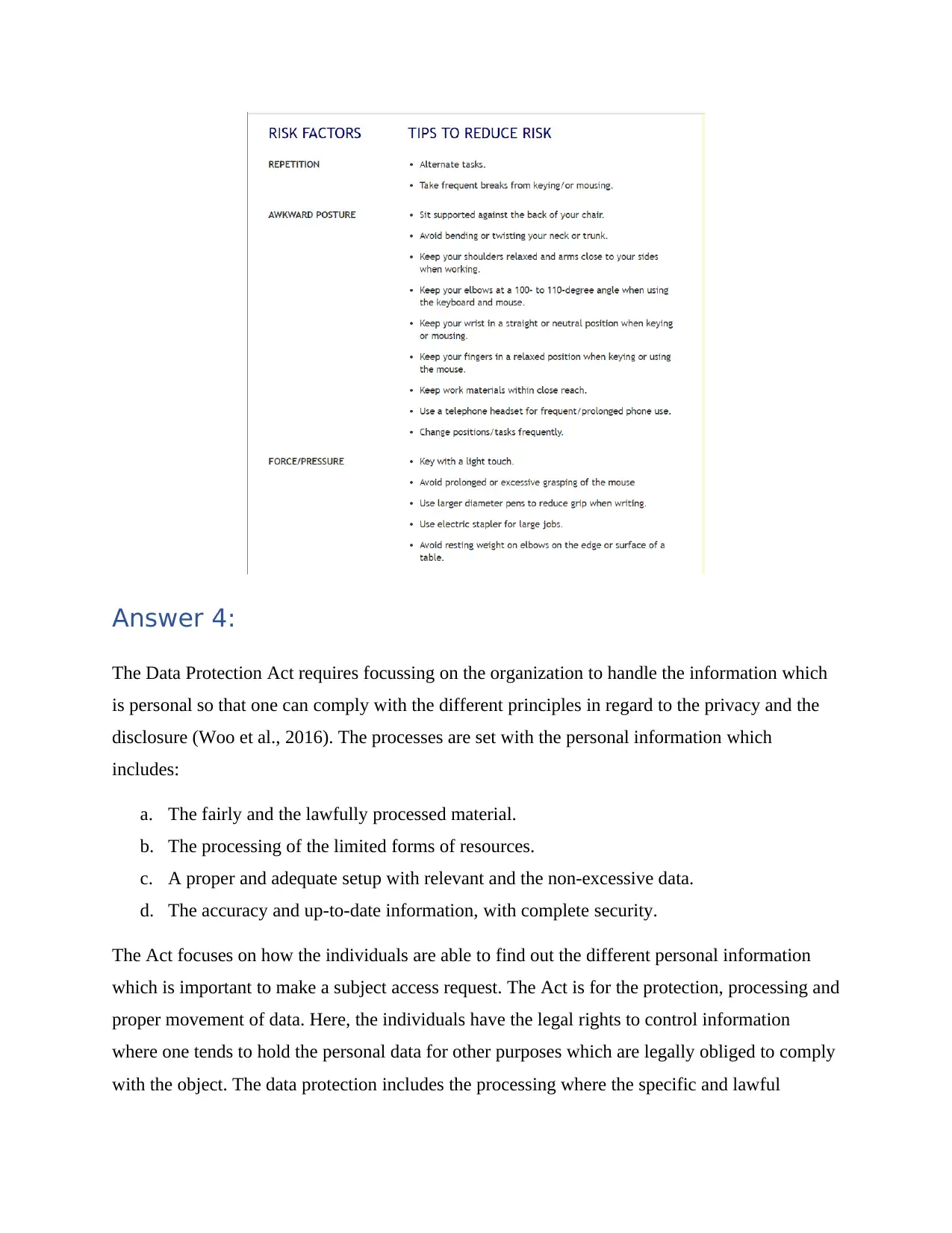
Answer 3:
The potential danger related to the computer ergonomics is the stress and strain that the people
have to face after spending their time in front of the computer. They stress their bodies without
mainly realizing about the wrists, sitting without foot support and then straining to look as well.
Here, the practices could also lead to the trauma disorders or some injuries which tend to create a
major impact on health (Cheklin et al., 2016). The ergonomics is the study which is mainly to
reduce the stress and the fatigue or the injuries with improvement in the designing of product and
the arrangement of the workplace. Some of the risks factors include:
a. The awkward positions where the body postures are mainly to determine the joints and the
muscles for the activity. The example is about poor positions which include keeping the
computer mouse far from the keyboard or in a straight line from the seat.
as there is no physical work that is being done. There are other problems like the muscle and the
joint problems, strain in the eyes as well as the behavioural problems due to the aggressive
behaviour (Certo, 2015).
Hazards
There are different hazards related to the health and the data security as well. The health could be
damaged with the carpal tunnel syndrome, and the repetitive injury strain, with eye strain due to
the computer and the vision syndromes. Hence, it is important to regularly exercise as well. On
the other hand, if the data is publicly available without much user encryption, then it can lead to
major loss of data. The malware scams and the phishing problems are related to the computer
security issues.
Potential dangers
With major reliability of the data on the computer, there are issues of the slow performance of
computer, erratic computer behaviours and the unexplained loss of data. It could lead to the
frequent crash of the computer and thereby, a major loss of the data security as well.
Answer 3:
The potential danger related to the computer ergonomics is the stress and strain that the people
have to face after spending their time in front of the computer. They stress their bodies without
mainly realizing about the wrists, sitting without foot support and then straining to look as well.
Here, the practices could also lead to the trauma disorders or some injuries which tend to create a
major impact on health (Cheklin et al., 2016). The ergonomics is the study which is mainly to
reduce the stress and the fatigue or the injuries with improvement in the designing of product and
the arrangement of the workplace. Some of the risks factors include:
a. The awkward positions where the body postures are mainly to determine the joints and the
muscles for the activity. The example is about poor positions which include keeping the
computer mouse far from the keyboard or in a straight line from the seat.

b. The duration wherein the person keeps on holding the static position at a given task. The
longer the muscle group is used, there is a greater probability of the localized and the general
fatigue as well (Wille & Sajous, 2018).
c. The repetitive motions are performed only in an infrequent manner, and even if they are
performed, then this results in the major hard to the body. The changing tasks during the day or
taking the breaks at the time of periodic breaks can help in providing the muscles a major time
which is for recovering from the unstressed state. It is important to focus on leading the potential
work with musculoskeletal problems. The awareness of the risks is to avoid any discomfort and
the injury at the time of using a computer.
d. The environmental or the force/pressure could be a major risk which could be reduced with
the glare on the computer screen with properly adjusting the placement and the tilt.
Hence, it is important for the body to modify the body mechanics by wearing the eyeglasses,
with adapting to the sitting positions. There is a need to rest your wrists at the time of breaks so
that the body gets some rest (Palidano & Tabasso, 2014). The adjustment of the work patterns
tends to reduce the prolonged computer time, as and when possible. The breaking of the work
into smaller segments and then switching in between the tasks helps in using the different
motions. The movement has different benefits which relax the tissues to reduce fatigue etc.
longer the muscle group is used, there is a greater probability of the localized and the general
fatigue as well (Wille & Sajous, 2018).
c. The repetitive motions are performed only in an infrequent manner, and even if they are
performed, then this results in the major hard to the body. The changing tasks during the day or
taking the breaks at the time of periodic breaks can help in providing the muscles a major time
which is for recovering from the unstressed state. It is important to focus on leading the potential
work with musculoskeletal problems. The awareness of the risks is to avoid any discomfort and
the injury at the time of using a computer.
d. The environmental or the force/pressure could be a major risk which could be reduced with
the glare on the computer screen with properly adjusting the placement and the tilt.
Hence, it is important for the body to modify the body mechanics by wearing the eyeglasses,
with adapting to the sitting positions. There is a need to rest your wrists at the time of breaks so
that the body gets some rest (Palidano & Tabasso, 2014). The adjustment of the work patterns
tends to reduce the prolonged computer time, as and when possible. The breaking of the work
into smaller segments and then switching in between the tasks helps in using the different
motions. The movement has different benefits which relax the tissues to reduce fatigue etc.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Answer 4:
The Data Protection Act requires focussing on the organization to handle the information which
is personal so that one can comply with the different principles in regard to the privacy and the
disclosure (Woo et al., 2016). The processes are set with the personal information which
includes:
a. The fairly and the lawfully processed material.
b. The processing of the limited forms of resources.
c. A proper and adequate setup with relevant and the non-excessive data.
d. The accuracy and up-to-date information, with complete security.
The Act focuses on how the individuals are able to find out the different personal information
which is important to make a subject access request. The Act is for the protection, processing and
proper movement of data. Here, the individuals have the legal rights to control information
where one tends to hold the personal data for other purposes which are legally obliged to comply
with the object. The data protection includes the processing where the specific and lawful
The Data Protection Act requires focussing on the organization to handle the information which
is personal so that one can comply with the different principles in regard to the privacy and the
disclosure (Woo et al., 2016). The processes are set with the personal information which
includes:
a. The fairly and the lawfully processed material.
b. The processing of the limited forms of resources.
c. A proper and adequate setup with relevant and the non-excessive data.
d. The accuracy and up-to-date information, with complete security.
The Act focuses on how the individuals are able to find out the different personal information
which is important to make a subject access request. The Act is for the protection, processing and
proper movement of data. Here, the individuals have the legal rights to control information
where one tends to hold the personal data for other purposes which are legally obliged to comply
with the object. The data protection includes the processing where the specific and lawful
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

purposes are processes in the manner which is compatible with the purpose. The data is
processed and is not kept for the longer time than it is necessary. In order to handle the personal
data, it should be processed through the fair treatments where the processing includes the legal
obligations and includes a proper carrying out of the public functions. there is a need to pursue
the legitimate interests of controlling the data or the third parties. The needs of the individual are
to collect the personal data and the use in its purpose (Peterson & McCleery, 2014). The
European Data Protection Directive focus on how the informed indication of data signifies an
agreement to personal data which relates to him after being processes. It is important that the
consent is properly done according to the age and the capacity of the individuals. The
organization needs to focus on continuously hold or make use of personal data after the
relationship is set at the individual ends (Davis, 2016). The Data Protection Act is mainly to
specify the personalized data which could be processed according to the strict set of conditions
mainly in the form of consent.
processed and is not kept for the longer time than it is necessary. In order to handle the personal
data, it should be processed through the fair treatments where the processing includes the legal
obligations and includes a proper carrying out of the public functions. there is a need to pursue
the legitimate interests of controlling the data or the third parties. The needs of the individual are
to collect the personal data and the use in its purpose (Peterson & McCleery, 2014). The
European Data Protection Directive focus on how the informed indication of data signifies an
agreement to personal data which relates to him after being processes. It is important that the
consent is properly done according to the age and the capacity of the individuals. The
organization needs to focus on continuously hold or make use of personal data after the
relationship is set at the individual ends (Davis, 2016). The Data Protection Act is mainly to
specify the personalized data which could be processed according to the strict set of conditions
mainly in the form of consent.

References
Bundgaard, K., 2017. Translator Attitudes towards Translator-Computer Interaction-Findings from a
Workplace Study. HERMES-Journal of Language and Communication in Business, (56), pp.125-144.
Certo, S., 2015. Supervision: Concepts and skill-building. McGraw-Hill Higher Education.
Cheklin, M., Mueller, F.F. and Greuter, S., 2016, June. Designing mediated nurturing play with dogs to
alleviate workplace stress. In Proceedings of the 2016 ACM Conference Companion Publication on
Designing Interactive Systems (pp. 153-156). ACM.
Crossman, J.E., 2015. Being on the outer: The risks and benefits of spiritual self-disclosure in the
Australian workplace. Journal of Management & Organization, 21(6), pp.772-785.
Davis, R. N. (2016). Redefining the Workplace: Technology and the Modern Judicial Chambers. Legal
Writing: J. Legal Writing Inst., 21, 5.
Ehrensberger-Dow, M. and O'Brien, S., 2015. Ergonomics of the translation workplace. Translation
Spaces, 4(1).
Glass, N., Hanson, G.C., Anger, W.K., Laharnar, N., Campbell, J.C., Weinstein, M. and Perrin, N., 2017.
Computer‐based training (CBT) intervention reduces workplace violence and harassment for homecare
workers. American journal of industrial medicine, 60(7), pp.635-643.
Inyukina, T.A., Klasner, G.G. and Gorb, S.S., 2016. A computer in the workplace: the benefits and harms.
In International Scientific and Practical Conference World science (Vol. 1, No. 8, pp. 19-20). ROST.
Peterson, K. and McCleery, E., 2014. Evidence Brief: The Effectiveness of Mandatory Computer-Based
Trainings on Government Ethics, Workplace Harassment, or Privacy and Information Security-Related
Topics.
Polidano, C. and Tabasso, D., 2014. Making it real: The benefits of workplace learning in upper-
secondary vocational education and training courses. Economics of Education Review, 42, pp.130-146.
Wille, S. and Sajous-Brady, D., 2018. The inclusive and accessible workplace. Communications of the
ACM, 61(2), pp.24-26.
Woo, E.H.C., White, P. and Lai, C.W.K., 2016. Ergonomics standards and guidelines for computer
workstation design and the impact on users’ health–a review. Ergonomics, 59(3), pp.464-475.
Bundgaard, K., 2017. Translator Attitudes towards Translator-Computer Interaction-Findings from a
Workplace Study. HERMES-Journal of Language and Communication in Business, (56), pp.125-144.
Certo, S., 2015. Supervision: Concepts and skill-building. McGraw-Hill Higher Education.
Cheklin, M., Mueller, F.F. and Greuter, S., 2016, June. Designing mediated nurturing play with dogs to
alleviate workplace stress. In Proceedings of the 2016 ACM Conference Companion Publication on
Designing Interactive Systems (pp. 153-156). ACM.
Crossman, J.E., 2015. Being on the outer: The risks and benefits of spiritual self-disclosure in the
Australian workplace. Journal of Management & Organization, 21(6), pp.772-785.
Davis, R. N. (2016). Redefining the Workplace: Technology and the Modern Judicial Chambers. Legal
Writing: J. Legal Writing Inst., 21, 5.
Ehrensberger-Dow, M. and O'Brien, S., 2015. Ergonomics of the translation workplace. Translation
Spaces, 4(1).
Glass, N., Hanson, G.C., Anger, W.K., Laharnar, N., Campbell, J.C., Weinstein, M. and Perrin, N., 2017.
Computer‐based training (CBT) intervention reduces workplace violence and harassment for homecare
workers. American journal of industrial medicine, 60(7), pp.635-643.
Inyukina, T.A., Klasner, G.G. and Gorb, S.S., 2016. A computer in the workplace: the benefits and harms.
In International Scientific and Practical Conference World science (Vol. 1, No. 8, pp. 19-20). ROST.
Peterson, K. and McCleery, E., 2014. Evidence Brief: The Effectiveness of Mandatory Computer-Based
Trainings on Government Ethics, Workplace Harassment, or Privacy and Information Security-Related
Topics.
Polidano, C. and Tabasso, D., 2014. Making it real: The benefits of workplace learning in upper-
secondary vocational education and training courses. Economics of Education Review, 42, pp.130-146.
Wille, S. and Sajous-Brady, D., 2018. The inclusive and accessible workplace. Communications of the
ACM, 61(2), pp.24-26.
Woo, E.H.C., White, P. and Lai, C.W.K., 2016. Ergonomics standards and guidelines for computer
workstation design and the impact on users’ health–a review. Ergonomics, 59(3), pp.464-475.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





