Comprehensive Report on Computer Systems: Design and Maintenance
VerifiedAdded on 2024/05/23
|40
|4341
|439
Report
AI Summary
This report provides a comprehensive overview of computer systems, covering their roles in various environments like hospitals, education, transport, gaming, and hotels. It details the hardware, software, and peripheral components of a computer system, including the CPU, storage devices, operating systems, application programs, and input/output devices. A comparison of different types of computer systems, such as microcomputers, minicomputers, mainframe computers, and supercomputers, is presented. The report also includes a system design specification tailored to a client's needs, along with an evaluation of its suitability. Furthermore, it describes the process of building and configuring a computer system to meet a specific design, including safety precautions, component installation, and software setup. The report concludes with routine maintenance tasks, such as physical cleaning, data backup, disk defragmentation, web history clearing, antivirus updates, and system service management, as well as hardware and software upgrades for performance enhancement. This document is available on Desklib, a platform offering AI-powered study tools and a wide array of student resources.

Computer System
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
Introduction......................................................................................................................................1
LO1..................................................................................................................................................2
1.1 explain the role of computer systems in different environments......................................2
1.2 explain the hardware, software and peripheral components of a computer system..........5
1.3 compare different types of computer systems.....................................................................11
LO2................................................................................................................................................13
2.1 produce a system design specification to meet a client’s needs..........................................13
2.2 evaluate the suitability of a system design specification.....................................................14
LO3................................................................................................................................................15
3.1 build and configure a computer system to meet a design specification..............................15
3.2 test and document a computer system.................................................................................24
LO4................................................................................................................................................27
4.1 perform routine maintenance tasks on a computer system..................................................27
4.2 upgrade the hardware and software on a computer system.................................................33
Conclusion.....................................................................................................................................34
References......................................................................................................................................35
Introduction......................................................................................................................................1
LO1..................................................................................................................................................2
1.1 explain the role of computer systems in different environments......................................2
1.2 explain the hardware, software and peripheral components of a computer system..........5
1.3 compare different types of computer systems.....................................................................11
LO2................................................................................................................................................13
2.1 produce a system design specification to meet a client’s needs..........................................13
2.2 evaluate the suitability of a system design specification.....................................................14
LO3................................................................................................................................................15
3.1 build and configure a computer system to meet a design specification..............................15
3.2 test and document a computer system.................................................................................24
LO4................................................................................................................................................27
4.1 perform routine maintenance tasks on a computer system..................................................27
4.2 upgrade the hardware and software on a computer system.................................................33
Conclusion.....................................................................................................................................34
References......................................................................................................................................35

LIST OF TABLES
Table 1: Comparison between different computer system............................................................11
Table 2: Computer specifications..................................................................................................13
Table 3: Common component in all the computer systems...........................................................13
Table 3: Test result........................................................................................................................24
Table 1: Comparison between different computer system............................................................11
Table 2: Computer specifications..................................................................................................13
Table 3: Common component in all the computer systems...........................................................13
Table 3: Test result........................................................................................................................24
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

LIST OF FIGURES
Figure 1 : Computer System used in hospitals................................................................................2
Figure 2: Computer used in schools................................................................................................3
Figure 3: Oyster Card used for various purposes............................................................................3
Figure 4: Computer used for playing games....................................................................................4
Figure 5: Computers for hotel management....................................................................................4
Figure 6:Intel core i7 processor.......................................................................................................5
Figure 7: Different storage devices in computer.............................................................................6
Figure 8: NIC (wireless adapter).....................................................................................................6
Figure 9: Common operating system...............................................................................................7
Figure 10: Various application programs........................................................................................8
Figure 11: Common Utility software...............................................................................................8
Figure 12: Manual input devices.....................................................................................................9
Figure 13:Output devices...............................................................................................................10
Figure 14: Different types of computer systems............................................................................11
Figure 15: Price of various computer systems...............................................................................12
Figure 16: Antistatic mat and wrist straps.....................................................................................15
Figure 17: Installing motherboard.................................................................................................16
Figure 18: Installing the processor.............................................................................................16
Figure 19: Installing the fan and heat sink.....................................................................................17
Figure 17: Installation of hard disk................................................................................................17
Figure 20: Filling the time, currency and language.......................................................................18
Figure 21: Product key for Windows 10........................................................................................19
Figure 22: License is accepted.......................................................................................................19
Figure 23: Installation type............................................................................................................20
Figure 24: The driver is installed...................................................................................................20
Figure 25: Status showing windows installation...........................................................................21
Figure 26: The narrator and magnifier are set...............................................................................21
Figure 27: Customize setting.........................................................................................................22
Figure 28: Owner Specification....................................................................................................22
Figure 29: Verification and authentication...................................................................................23
Figure 1 : Computer System used in hospitals................................................................................2
Figure 2: Computer used in schools................................................................................................3
Figure 3: Oyster Card used for various purposes............................................................................3
Figure 4: Computer used for playing games....................................................................................4
Figure 5: Computers for hotel management....................................................................................4
Figure 6:Intel core i7 processor.......................................................................................................5
Figure 7: Different storage devices in computer.............................................................................6
Figure 8: NIC (wireless adapter).....................................................................................................6
Figure 9: Common operating system...............................................................................................7
Figure 10: Various application programs........................................................................................8
Figure 11: Common Utility software...............................................................................................8
Figure 12: Manual input devices.....................................................................................................9
Figure 13:Output devices...............................................................................................................10
Figure 14: Different types of computer systems............................................................................11
Figure 15: Price of various computer systems...............................................................................12
Figure 16: Antistatic mat and wrist straps.....................................................................................15
Figure 17: Installing motherboard.................................................................................................16
Figure 18: Installing the processor.............................................................................................16
Figure 19: Installing the fan and heat sink.....................................................................................17
Figure 17: Installation of hard disk................................................................................................17
Figure 20: Filling the time, currency and language.......................................................................18
Figure 21: Product key for Windows 10........................................................................................19
Figure 22: License is accepted.......................................................................................................19
Figure 23: Installation type............................................................................................................20
Figure 24: The driver is installed...................................................................................................20
Figure 25: Status showing windows installation...........................................................................21
Figure 26: The narrator and magnifier are set...............................................................................21
Figure 27: Customize setting.........................................................................................................22
Figure 28: Owner Specification....................................................................................................22
Figure 29: Verification and authentication...................................................................................23
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Figure 30: Default app selection....................................................................................................23
Figure 31: Physical cleaning..........................................................................................................27
Figure 32: Cloud as backup...........................................................................................................28
Figure 33: Defragment and optimized drive option......................................................................28
Figure 34: Select and analyze hard drive.......................................................................................29
Figure 35: Optimize the hard drive................................................................................................29
Figure 36: Option to clear all web history.....................................................................................30
Figure 37: Select the type of web browser history to delete..........................................................30
Figure 38: Antivirus update...........................................................................................................31
Figure 39: Enabling and disabling various system services..........................................................32
Figure 31: Physical cleaning..........................................................................................................27
Figure 32: Cloud as backup...........................................................................................................28
Figure 33: Defragment and optimized drive option......................................................................28
Figure 34: Select and analyze hard drive.......................................................................................29
Figure 35: Optimize the hard drive................................................................................................29
Figure 36: Option to clear all web history.....................................................................................30
Figure 37: Select the type of web browser history to delete..........................................................30
Figure 38: Antivirus update...........................................................................................................31
Figure 39: Enabling and disabling various system services..........................................................32

Introduction
Computer are significant elements of present world. In this present report fundamentals of
computer system are studied including different environments such as home, education, business
where computers are highly used. Main purpose of using computers in any organization is to
attain efficiency, accuracy and reducing user’s workload. In this report studies are done about
role and function that computer system performs in various organization. Computer is composed
of various components which can be broadly classified as Hardware, software and peripheral
devices which will be discussed in the current report. The report will provide a comparison
between different type of computers that are for serving different purpose at different fields.
Design is provided in the report together with system specification for all the user in the network.
Configuration and installation of Computer system is illustrated below with various images.
Lastly, this report will discuss about routine maintenance task that is to be done along with
system upgrading for performance enhancement.
1
Computer are significant elements of present world. In this present report fundamentals of
computer system are studied including different environments such as home, education, business
where computers are highly used. Main purpose of using computers in any organization is to
attain efficiency, accuracy and reducing user’s workload. In this report studies are done about
role and function that computer system performs in various organization. Computer is composed
of various components which can be broadly classified as Hardware, software and peripheral
devices which will be discussed in the current report. The report will provide a comparison
between different type of computers that are for serving different purpose at different fields.
Design is provided in the report together with system specification for all the user in the network.
Configuration and installation of Computer system is illustrated below with various images.
Lastly, this report will discuss about routine maintenance task that is to be done along with
system upgrading for performance enhancement.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

LO1
1.1 explain the role of computer systems in different environments
Personal Computer Systems are typically used for routine work because of their various
advantages, such as accurate data handling, consistent work, and higher performance ability.
They help in storing, managing, compiling and processing different kinds of data, with a higher
level of efficiency. They enhance human accuracy for various tasks, and also provide various
platforms for different environments as under:
Hospitals: Systematic records are kept for the patients availing the hospital facility, and can be
typically accessed at the front desk itself. They also help with different surgical operations, by
giving a visual presentation of the patient’s condition, such as EGC Operation (Anderson and
Jay, 2012). Most of the hospitals’ managerial tasks can also be done on the systems, thus
increasing efficiency
Figure 1 : Computer System used in hospitals
(Source: https://www.shutterstock.com, ecg-monitor-patient-s-condition-in-operating-room-
close-up-heartbeat-on-screen-heart-rate-blood.html)
Education: These systems also help students and teachers both, by maintaining efficient records,
and offering the potential of technological learning to the students by means of visual aids.
Students can search for any desired information in Internet Search Engines from their library
computer systems, and gain the requisite information. The systems also assist the students with
their projects.
2
1.1 explain the role of computer systems in different environments
Personal Computer Systems are typically used for routine work because of their various
advantages, such as accurate data handling, consistent work, and higher performance ability.
They help in storing, managing, compiling and processing different kinds of data, with a higher
level of efficiency. They enhance human accuracy for various tasks, and also provide various
platforms for different environments as under:
Hospitals: Systematic records are kept for the patients availing the hospital facility, and can be
typically accessed at the front desk itself. They also help with different surgical operations, by
giving a visual presentation of the patient’s condition, such as EGC Operation (Anderson and
Jay, 2012). Most of the hospitals’ managerial tasks can also be done on the systems, thus
increasing efficiency
Figure 1 : Computer System used in hospitals
(Source: https://www.shutterstock.com, ecg-monitor-patient-s-condition-in-operating-room-
close-up-heartbeat-on-screen-heart-rate-blood.html)
Education: These systems also help students and teachers both, by maintaining efficient records,
and offering the potential of technological learning to the students by means of visual aids.
Students can search for any desired information in Internet Search Engines from their library
computer systems, and gain the requisite information. The systems also assist the students with
their projects.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Figure 2: Computer used in schools
(https://ace.iafor.org/, 2018)
Transport: Computer systems enhance the functioning of transport systems, by assisting in
booking tickets, reservations, and keeping passenger records. For instance, the Oyster Card in the
UK is used to give tickets to passengers on credit, which can be utilized to avail any means of
transportation to their needed location.
Figure 3: Oyster Card used for various purposes
(Source: https://www.shutterstock.com, 2018)
Gaming: Gamers are increasingly using computer systems due to the greater amount of
graphical and visual effects provided by these systems, which make the user feel as if he/she is in
a virtual arena with realistic looking objects and scenarios.
3
(https://ace.iafor.org/, 2018)
Transport: Computer systems enhance the functioning of transport systems, by assisting in
booking tickets, reservations, and keeping passenger records. For instance, the Oyster Card in the
UK is used to give tickets to passengers on credit, which can be utilized to avail any means of
transportation to their needed location.
Figure 3: Oyster Card used for various purposes
(Source: https://www.shutterstock.com, 2018)
Gaming: Gamers are increasingly using computer systems due to the greater amount of
graphical and visual effects provided by these systems, which make the user feel as if he/she is in
a virtual arena with realistic looking objects and scenarios.
3

Figure 4: Computer used for playing games
(Source: https://en.softonic.com, 2018)
Hotels: Customer data, worker data as well as other stakeholder data can be recorded in the
computer systems, and this facility is being increasingly used by hotels. Hotel managers also
utilize these systems to input the requisite data, and record it, so that the complex manual
procedures involved in clerical tasks can be avoided. Using these systems, decisions can be made
quickly, and client behaviour can also be routinely assessed.
Figure 5: Computers for hotel management
(Source: https://www.hospitalitynet.org/opinion/4080523.html, 2018)
4
(Source: https://en.softonic.com, 2018)
Hotels: Customer data, worker data as well as other stakeholder data can be recorded in the
computer systems, and this facility is being increasingly used by hotels. Hotel managers also
utilize these systems to input the requisite data, and record it, so that the complex manual
procedures involved in clerical tasks can be avoided. Using these systems, decisions can be made
quickly, and client behaviour can also be routinely assessed.
Figure 5: Computers for hotel management
(Source: https://www.hospitalitynet.org/opinion/4080523.html, 2018)
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1.2 explain the hardware, software and peripheral components of a computer system
Components of a computer system is broadly classified as hardware and software.
Hardware Components
Computer Hardware is the physical components or machineries that makes a computer system.
The common hardware is the memory, Central processing unit, storage device and Network
Interface Card.
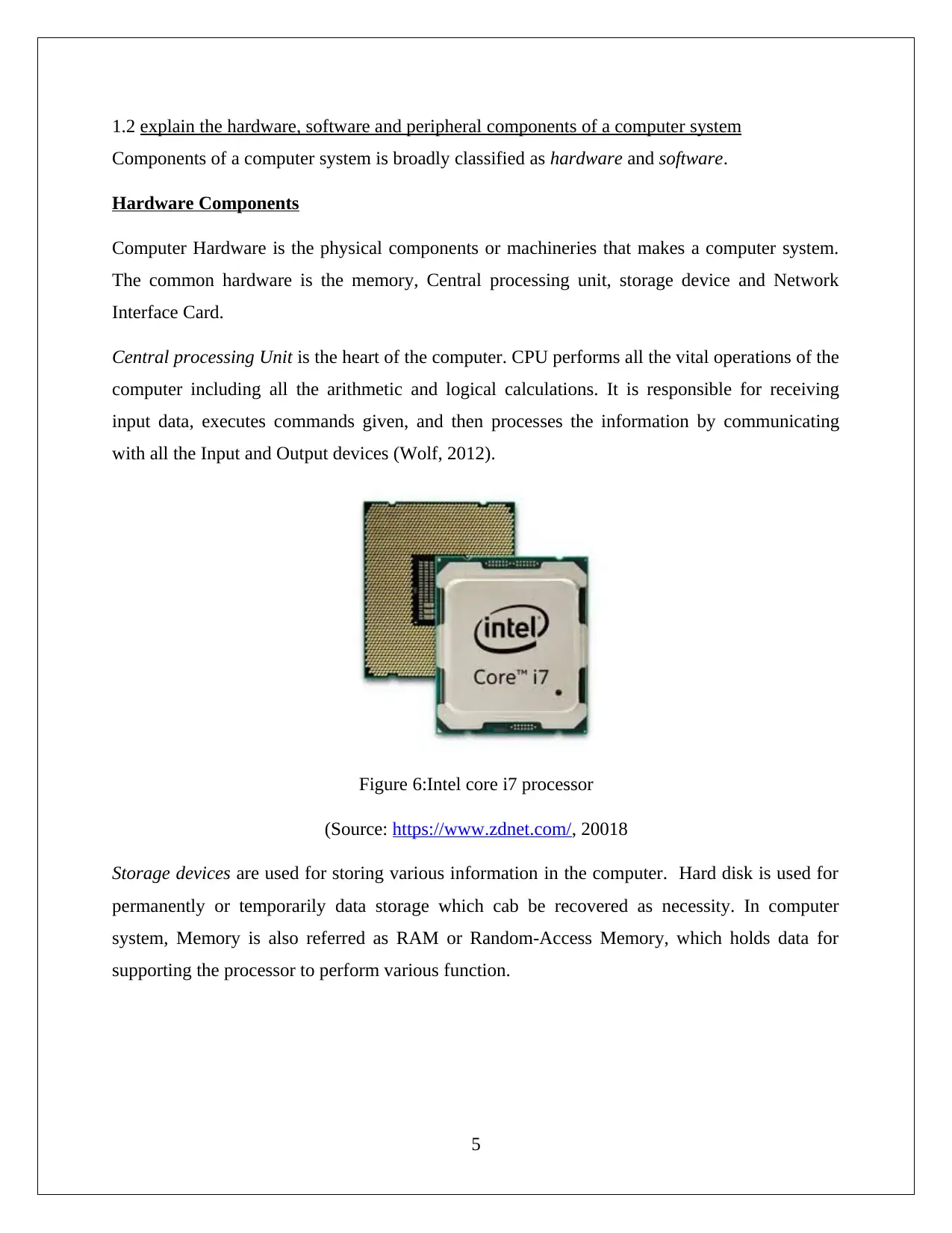
Central processing Unit is the heart of the computer. CPU performs all the vital operations of the
computer including all the arithmetic and logical calculations. It is responsible for receiving
input data, executes commands given, and then processes the information by communicating
with all the Input and Output devices (Wolf, 2012).
Figure 6:Intel core i7 processor
(Source: https://www.zdnet.com/, 20018
Storage devices are used for storing various information in the computer. Hard disk is used for
permanently or temporarily data storage which cab be recovered as necessity. In computer
system, Memory is also referred as RAM or Random-Access Memory, which holds data for
supporting the processor to perform various function.
5
Components of a computer system is broadly classified as hardware and software.
Hardware Components
Computer Hardware is the physical components or machineries that makes a computer system.
The common hardware is the memory, Central processing unit, storage device and Network
Interface Card.
Central processing Unit is the heart of the computer. CPU performs all the vital operations of the
computer including all the arithmetic and logical calculations. It is responsible for receiving
input data, executes commands given, and then processes the information by communicating
with all the Input and Output devices (Wolf, 2012).
Figure 6:Intel core i7 processor
(Source: https://www.zdnet.com/, 20018
Storage devices are used for storing various information in the computer. Hard disk is used for
permanently or temporarily data storage which cab be recovered as necessity. In computer
system, Memory is also referred as RAM or Random-Access Memory, which holds data for
supporting the processor to perform various function.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
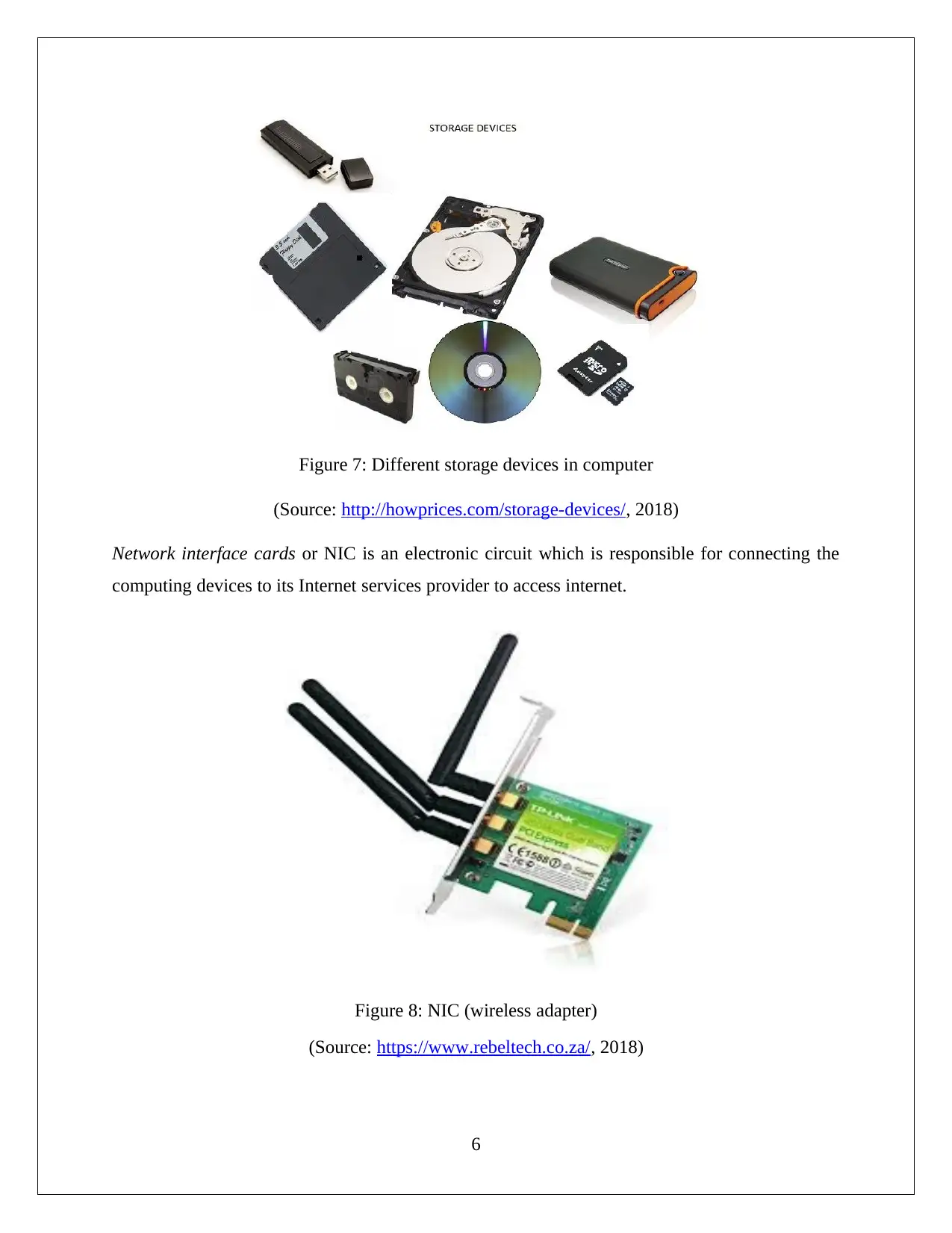
Figure 7: Different storage devices in computer
(Source: http://howprices.com/storage-devices/, 2018)
Network interface cards or NIC is an electronic circuit which is responsible for connecting the
computing devices to its Internet services provider to access internet.
Figure 8: NIC (wireless adapter)
(Source: https://www.rebeltech.co.za/, 2018)
6
(Source: http://howprices.com/storage-devices/, 2018)
Network interface cards or NIC is an electronic circuit which is responsible for connecting the
computing devices to its Internet services provider to access internet.
Figure 8: NIC (wireless adapter)
(Source: https://www.rebeltech.co.za/, 2018)
6

Software Components
Software are basically logical program that are used for monitoring, controlling and executing
various computer function. Software can be categorized into three types including
Operating system
Application software
Utility software.
Operating system: it is referred to a low-level software, it is responsible for managing all the
hardware and other software resources present in the computer system. The entire computer
system depends on the operating system for it running. OS forms an interface between the
computer hardware and user. Elementary responsibilities of OS are memory management, file
management, process management, and controlling peripheral devices and handling input and
output devices. IOS and Windows are two common OS (Lajoie and Derry, 2013).).
Figure 9: Common operating system
(Source: http://stmaryscc.com/getting-know-operating-system-computer/, 2018)
Application programs: these are software that are designed for performing of synchronized tasks
or operation. It takes help of the operating system services for the benefit of the computer user.
For an instance, database programs, games.
7
Software are basically logical program that are used for monitoring, controlling and executing
various computer function. Software can be categorized into three types including
Operating system
Application software
Utility software.
Operating system: it is referred to a low-level software, it is responsible for managing all the
hardware and other software resources present in the computer system. The entire computer
system depends on the operating system for it running. OS forms an interface between the
computer hardware and user. Elementary responsibilities of OS are memory management, file
management, process management, and controlling peripheral devices and handling input and
output devices. IOS and Windows are two common OS (Lajoie and Derry, 2013).).
Figure 9: Common operating system
(Source: http://stmaryscc.com/getting-know-operating-system-computer/, 2018)
Application programs: these are software that are designed for performing of synchronized tasks
or operation. It takes help of the operating system services for the benefit of the computer user.
For an instance, database programs, games.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 40
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




