WUC 118/03 - Computers in a Networked Society TMA2 Assignment Solution
VerifiedAdded on 2023/06/04
|8
|1922
|93
Homework Assignment
AI Summary
This document provides comprehensive solutions to a Tutor Marked Assignment (TMA2) for the WUC 118/03 Computers in a Networked Society course. The assignment addresses key concepts from Unit 3 and Unit 4, including wired and wireless mediums for internet access, detailing dial-up access, DSL, cable connections, satellite, mobile methods, and Bluetooth/Wi-Fi. It identifies eight types of internet services like social networks, streaming, email, e-commerce, search engines, instant messengers, online forums, and the World Wide Web. The document also explores the pros and cons of social media, provides examples of IoT devices such as smartphones, door access, and switches, along with their functionalities and related challenges. Additionally, it covers five common cybercrimes in Malaysia, their types, and the importance of cyberlaws, along with five relevant cyberlaw acts in Malaysia, including the Communication and Multimedia Act 1998, Computer Crimes Act 1997, Copyright Act 1997, Digital Signature Act 1997, and Electronic Commerce Act 2006. References are provided to support the solutions.

Computers in network society
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computers
Answer 1
It can be seen that there are 3 methods related to wired medium and wireless medium.
a.) 3 methods of wired medium
1.) Dial up access: this is one of the famous wired connection through which it can be easy
to gather the information and also data can be transmitted in a proper manner.
2.) Digital subscriber line: it is a technology for maintaining high bandwidth information to
the houses and also it helps the small companies over ordinary copper telephone lines.
3.) Cable connections: it is also one of the wired connection in which the channels can be
shown easily with the help of cable connections. Like there are many companies who are
offering cable connections like Airtel and Dish TV (Peyton and Kelly 2016).
3 medium of wireless medium
1.) Satellite: it is one of the wireless connection through which it can be easy to connect the
internet without any wireless connections.
2.) Mobile methods: This is also the wireless connection through which it can be easy to
connect the internet through mobile network.
3.) Bluetooth and Wi-Fi: It is also one of the connections which can help to connect with the
data and information can be transferred easily (Neal, Woodard, and Striegel 2015).
b.) Eight types of internet services are
1.) Online social network: to access the online social network it has been seen that internet
services are necessary.
2.) Streaming services: internet services are related to Netflix, Hulu and Amazon instant.
3.) Email: Internet is necessary to access email which also helps to transmit the data.
4.) E-commerce: Through internet it can be easy to access the ecommerce sites. Products
can be sold and purchased easily.
5.) Search engine: Through internet it can be easy to search the products and to access the
data easily.
6.) Instant messenger: It is also one of the platform through which the messages can be
transferred and in this the use of internet is necessary.
1
Answer 1
It can be seen that there are 3 methods related to wired medium and wireless medium.
a.) 3 methods of wired medium
1.) Dial up access: this is one of the famous wired connection through which it can be easy
to gather the information and also data can be transmitted in a proper manner.
2.) Digital subscriber line: it is a technology for maintaining high bandwidth information to
the houses and also it helps the small companies over ordinary copper telephone lines.
3.) Cable connections: it is also one of the wired connection in which the channels can be
shown easily with the help of cable connections. Like there are many companies who are
offering cable connections like Airtel and Dish TV (Peyton and Kelly 2016).
3 medium of wireless medium
1.) Satellite: it is one of the wireless connection through which it can be easy to connect the
internet without any wireless connections.
2.) Mobile methods: This is also the wireless connection through which it can be easy to
connect the internet through mobile network.
3.) Bluetooth and Wi-Fi: It is also one of the connections which can help to connect with the
data and information can be transferred easily (Neal, Woodard, and Striegel 2015).
b.) Eight types of internet services are
1.) Online social network: to access the online social network it has been seen that internet
services are necessary.
2.) Streaming services: internet services are related to Netflix, Hulu and Amazon instant.
3.) Email: Internet is necessary to access email which also helps to transmit the data.
4.) E-commerce: Through internet it can be easy to access the ecommerce sites. Products
can be sold and purchased easily.
5.) Search engine: Through internet it can be easy to search the products and to access the
data easily.
6.) Instant messenger: It is also one of the platform through which the messages can be
transferred and in this the use of internet is necessary.
1

Computers
7.) Online forum: through internet it has been seen that it can be easy to focus on the
discussion forum (Kang et al. 2015).
8.) World Wide Web: is considered as the web in which it can be easy to search about the
data in an easy manner.
c.) Pros and cons of social media and social networking
3 Pros are
1.) Helps to connect with the people on the global platform
2.) Wide scope for the business owners
3.) Proper and instant communication
Cons
1.)Issues related to privacy
2.)Information overwhelm
3.)Cyber bullying (Perrin 2015)
So, these are the factors related to the pros and cons of social media marketing.
Answer 2
loT devices are considered as one of the popular devices.
a.) Five example of lOT devices
1.) Smart phones: It is also one of the Lot devices in which there are range of mobile
phones of different companies like Samsung and Apple.
2.) Door access: Through lOT it can be easy to access the doors.
3.) Switch: One of the best examples of lOT is switches.
4.) FordPass smart- link: it is a subscription based dongle that can help in plugging into
the cars. Through this it can be easy to track the cars.
5.) Nano leaf light panels: it is the owned application for Android and iOS devices.
b.) LoT devices works in an effective manner. It has been seen that it can help to maintain
the amounts of the internet traffic and it also consist of the data that can be considered to
make the device useful. This technology also helps to maintain the real information and
in the homes it can be easy to maintain safety. In the workplace it can be to enhance the
level of productivity. In the homes it can be seen that loT is related with the switches that
can help to keep the homes safe. It also helps in accessing the doors. There is a new
2
7.) Online forum: through internet it has been seen that it can be easy to focus on the
discussion forum (Kang et al. 2015).
8.) World Wide Web: is considered as the web in which it can be easy to search about the
data in an easy manner.
c.) Pros and cons of social media and social networking
3 Pros are
1.) Helps to connect with the people on the global platform
2.) Wide scope for the business owners
3.) Proper and instant communication
Cons
1.)Issues related to privacy
2.)Information overwhelm
3.)Cyber bullying (Perrin 2015)
So, these are the factors related to the pros and cons of social media marketing.
Answer 2
loT devices are considered as one of the popular devices.
a.) Five example of lOT devices
1.) Smart phones: It is also one of the Lot devices in which there are range of mobile
phones of different companies like Samsung and Apple.
2.) Door access: Through lOT it can be easy to access the doors.
3.) Switch: One of the best examples of lOT is switches.
4.) FordPass smart- link: it is a subscription based dongle that can help in plugging into
the cars. Through this it can be easy to track the cars.
5.) Nano leaf light panels: it is the owned application for Android and iOS devices.
b.) LoT devices works in an effective manner. It has been seen that it can help to maintain
the amounts of the internet traffic and it also consist of the data that can be considered to
make the device useful. This technology also helps to maintain the real information and
in the homes it can be easy to maintain safety. In the workplace it can be to enhance the
level of productivity. In the homes it can be seen that loT is related with the switches that
can help to keep the homes safe. It also helps in accessing the doors. There is a new
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Computers
system which is given to manage the doors and switches of the homes. In ford cars the
system is available through which it can be easy to track the cars. Nano leaf light panels
are considered as the Lot devices through which it can be easy to manage the activities in
the android devices (Mandula et al. 2015)
c.) There are various challenges related to security related to smart phones. It has been seen
that challenge relates with ensuring the data privacy and integrity and also with the secure
communication. With the smart phones the issue can be related to the managing the
device updates. FordPass smart- link the issue can take place related to the detecting of
vulnerabilities and incidents. The lOT related to device states that the security is one of
the issue or challenge.
So, these are the devices that are related to lOT.
Answer 3
a) FIVE (5) common cybercrimes in Malaysia are:
1.) Cyber-attacks: It is one of the attacks which are attempted by the hackers to damage
or destroy the computer network or system.
2.) Cyber harassment: It is one of the cybercrimes in which people annoy each other.
3.) Intrusion attempt: It is related with the unauthorized access to a system or the
network.
4.) Malicious codes: it is the code that is used to elaborate the code in the software
system.
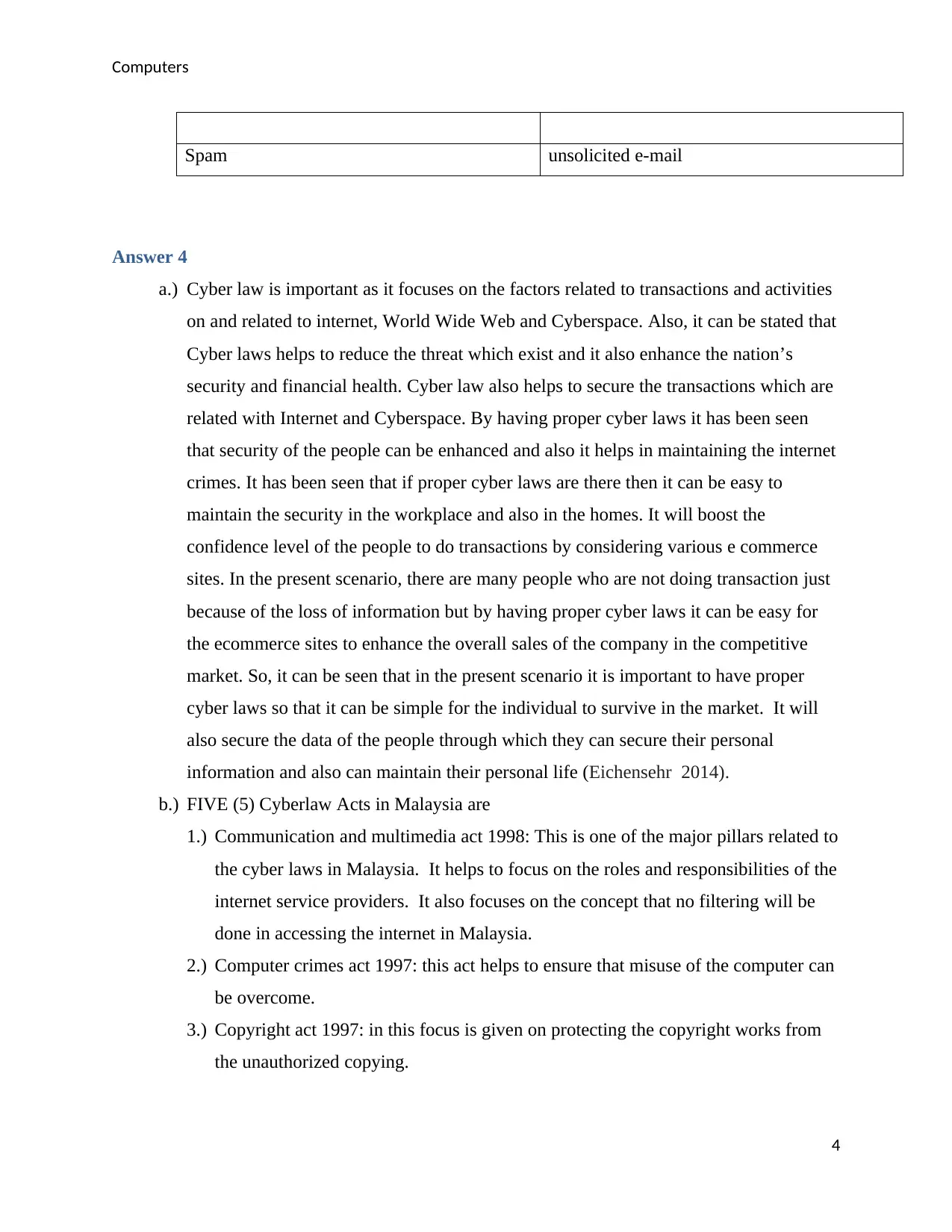
5.) Spam: Spam is related with unsolicited emails and also sent by the multiple mailing
lists. It is send to the third party and it affects the other mails of the person (Rahman
2015).
b) Type of cybercrime for each of the common cybercrimes identified in (a) are:
Cybercrime Type
Cyber attacks Social media platform
Cyber harassment Group chat and religious harassment
Intrusion attempt installation of malicious programs
Malicious codes Worms, Trojan horses
3
system which is given to manage the doors and switches of the homes. In ford cars the
system is available through which it can be easy to track the cars. Nano leaf light panels
are considered as the Lot devices through which it can be easy to manage the activities in
the android devices (Mandula et al. 2015)
c.) There are various challenges related to security related to smart phones. It has been seen
that challenge relates with ensuring the data privacy and integrity and also with the secure
communication. With the smart phones the issue can be related to the managing the
device updates. FordPass smart- link the issue can take place related to the detecting of
vulnerabilities and incidents. The lOT related to device states that the security is one of
the issue or challenge.
So, these are the devices that are related to lOT.
Answer 3
a) FIVE (5) common cybercrimes in Malaysia are:
1.) Cyber-attacks: It is one of the attacks which are attempted by the hackers to damage
or destroy the computer network or system.
2.) Cyber harassment: It is one of the cybercrimes in which people annoy each other.
3.) Intrusion attempt: It is related with the unauthorized access to a system or the
network.
4.) Malicious codes: it is the code that is used to elaborate the code in the software
system.
5.) Spam: Spam is related with unsolicited emails and also sent by the multiple mailing
lists. It is send to the third party and it affects the other mails of the person (Rahman
2015).
b) Type of cybercrime for each of the common cybercrimes identified in (a) are:
Cybercrime Type
Cyber attacks Social media platform
Cyber harassment Group chat and religious harassment
Intrusion attempt installation of malicious programs
Malicious codes Worms, Trojan horses
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Computers
Spam unsolicited e-mail
Answer 4
a.) Cyber law is important as it focuses on the factors related to transactions and activities
on and related to internet, World Wide Web and Cyberspace. Also, it can be stated that
Cyber laws helps to reduce the threat which exist and it also enhance the nation’s
security and financial health. Cyber law also helps to secure the transactions which are
related with Internet and Cyberspace. By having proper cyber laws it has been seen
that security of the people can be enhanced and also it helps in maintaining the internet
crimes. It has been seen that if proper cyber laws are there then it can be easy to
maintain the security in the workplace and also in the homes. It will boost the
confidence level of the people to do transactions by considering various e commerce
sites. In the present scenario, there are many people who are not doing transaction just
because of the loss of information but by having proper cyber laws it can be easy for
the ecommerce sites to enhance the overall sales of the company in the competitive
market. So, it can be seen that in the present scenario it is important to have proper
cyber laws so that it can be simple for the individual to survive in the market. It will
also secure the data of the people through which they can secure their personal
information and also can maintain their personal life (Eichensehr 2014).
b.) FIVE (5) Cyberlaw Acts in Malaysia are
1.) Communication and multimedia act 1998: This is one of the major pillars related to
the cyber laws in Malaysia. It helps to focus on the roles and responsibilities of the
internet service providers. It also focuses on the concept that no filtering will be
done in accessing the internet in Malaysia.
2.) Computer crimes act 1997: this act helps to ensure that misuse of the computer can
be overcome.
3.) Copyright act 1997: in this focus is given on protecting the copyright works from
the unauthorized copying.
4
Spam unsolicited e-mail
Answer 4
a.) Cyber law is important as it focuses on the factors related to transactions and activities
on and related to internet, World Wide Web and Cyberspace. Also, it can be stated that
Cyber laws helps to reduce the threat which exist and it also enhance the nation’s
security and financial health. Cyber law also helps to secure the transactions which are
related with Internet and Cyberspace. By having proper cyber laws it has been seen
that security of the people can be enhanced and also it helps in maintaining the internet
crimes. It has been seen that if proper cyber laws are there then it can be easy to
maintain the security in the workplace and also in the homes. It will boost the
confidence level of the people to do transactions by considering various e commerce
sites. In the present scenario, there are many people who are not doing transaction just
because of the loss of information but by having proper cyber laws it can be easy for
the ecommerce sites to enhance the overall sales of the company in the competitive
market. So, it can be seen that in the present scenario it is important to have proper
cyber laws so that it can be simple for the individual to survive in the market. It will
also secure the data of the people through which they can secure their personal
information and also can maintain their personal life (Eichensehr 2014).
b.) FIVE (5) Cyberlaw Acts in Malaysia are
1.) Communication and multimedia act 1998: This is one of the major pillars related to
the cyber laws in Malaysia. It helps to focus on the roles and responsibilities of the
internet service providers. It also focuses on the concept that no filtering will be
done in accessing the internet in Malaysia.
2.) Computer crimes act 1997: this act helps to ensure that misuse of the computer can
be overcome.
3.) Copyright act 1997: in this focus is given on protecting the copyright works from
the unauthorized copying.
4

Computers
4.) Digital signature act 1997: This act enforced to assist in preventing on line
transaction frauds. It also offers both licensing and regulation of certification
authorities (Alwi, Ismail, and Ahmad 2016).
5.) Electronic commerce act 2006: This act will offer a legal recognition of the
electronic messages related to the commercial transactions. It also helps to offer
proper legal requirement that will help to fulfill the use of electronic messages.
5
4.) Digital signature act 1997: This act enforced to assist in preventing on line
transaction frauds. It also offers both licensing and regulation of certification
authorities (Alwi, Ismail, and Ahmad 2016).
5.) Electronic commerce act 2006: This act will offer a legal recognition of the
electronic messages related to the commercial transactions. It also helps to offer
proper legal requirement that will help to fulfill the use of electronic messages.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Computers
References
Alwi, Najwa HM, Habibah B. Ismail, and Fatin Ahmad. (2016). "Mobile Learning-
Cyberlaw Course, the Application Development and Students Perceptions."
Eichensehr, Kristen E. "The cyber-law of nations. (2014). " Geo. LJ103, 317.
Kang, Ruogu, Laura Dabbish, Nathaniel Fruchter, and Sara Kiesler. 2015."my data just
goes everywhere:” user mental models of the internet and implications for privacy and
security." In Symposium on Usable Privacy and Security (SOUPS), pp. 39-52.
Berkeley, CA: USENIX Association.
Mandula, Kumar, Ramu Parupalli, CH AS Murty, E. Magesh, and Rutul Lunagariya. 2015.
"Mobile based home automation using Internet of Things (IoT)." In Control,
Instrumentation, Communication and Computational Technologies (ICCICCT), 2015
International Conference on, pp. 340-343. IEEE.
Neal, Tempestt J., Damon L. Woodard, and Aaron D. Striegel. 2015. "Mobile device
application, bluetooth, and wi-fi usage data as behavioral biometric traits."
In Biometrics Theory, Applications and Systems (BTAS), 2015 IEEE 7th International
Conference on, pp. 1-6. IEEE.
Perrin, Andrew. "Social media usage. 2015: " Pew research center. 52-68.
Peyton, Anthony, and John Kelly. 2016. "Signal processing apparatuses and methods for
identifying cable connections between ports." U.S. Patent 9,395,399, issued July 19.
Rahman, Rizal. 2017. "The Need for More Legal Materials for Better Understanding of
Malware and Badware Threats in Malaysia." Mediterranean Journal of Social
Sciences 8, no. 1, 134-138.
6
References
Alwi, Najwa HM, Habibah B. Ismail, and Fatin Ahmad. (2016). "Mobile Learning-
Cyberlaw Course, the Application Development and Students Perceptions."
Eichensehr, Kristen E. "The cyber-law of nations. (2014). " Geo. LJ103, 317.
Kang, Ruogu, Laura Dabbish, Nathaniel Fruchter, and Sara Kiesler. 2015."my data just
goes everywhere:” user mental models of the internet and implications for privacy and
security." In Symposium on Usable Privacy and Security (SOUPS), pp. 39-52.
Berkeley, CA: USENIX Association.
Mandula, Kumar, Ramu Parupalli, CH AS Murty, E. Magesh, and Rutul Lunagariya. 2015.
"Mobile based home automation using Internet of Things (IoT)." In Control,
Instrumentation, Communication and Computational Technologies (ICCICCT), 2015
International Conference on, pp. 340-343. IEEE.
Neal, Tempestt J., Damon L. Woodard, and Aaron D. Striegel. 2015. "Mobile device
application, bluetooth, and wi-fi usage data as behavioral biometric traits."
In Biometrics Theory, Applications and Systems (BTAS), 2015 IEEE 7th International
Conference on, pp. 1-6. IEEE.
Perrin, Andrew. "Social media usage. 2015: " Pew research center. 52-68.
Peyton, Anthony, and John Kelly. 2016. "Signal processing apparatuses and methods for
identifying cable connections between ports." U.S. Patent 9,395,399, issued July 19.
Rahman, Rizal. 2017. "The Need for More Legal Materials for Better Understanding of
Malware and Badware Threats in Malaysia." Mediterranean Journal of Social
Sciences 8, no. 1, 134-138.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computers
7
7
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





