Analysis of Modern Computing Architecture and Network Technologies
VerifiedAdded on 2020/02/24
|10
|4031
|123
Homework Assignment
AI Summary
This assignment explores the evolution of modern computing architecture and network technologies through six weekly analyses of key individuals, protocols, and trends. The first week examines John McCarthy's contributions to Artificial Intelligence, highlighting his vision for intelligent machines and their impact on modern AI. Week two focuses on Linus Torvalds and the development of the Linux operating system, detailing his programming innovations and the open-source nature of the system. The third week delves into the NSFNET, showcasing its role in the development of the modern internet. Week four contrasts the token ring protocol with Ethernet, emphasizing the former's role as a data link protocol and its eventual displacement by Ethernet. The fifth week discusses the hacker Gary McKinnon, examining his exploits and the vulnerabilities he exposed in network infrastructure. Finally, the sixth week looks at the future of networking, specifically the potential of wireless data links using drones for improved connectivity. The assignment draws on various online resources to support the analysis and provide context for each topic.

Please fill in the following details:
Student Name Patel MeghabenRockeykumar.
Student Number 12051284
Week 1
The text discusses the elements of modern computing architecture however is largely silent
on the individuals who played a role in its development. Find and summarise a resource that
describes ONE such individual. The individual should have had a significant influence on the
development of computers and/or components of modern computing architecture.
Title and Reference:
Title – Artificial Intelligence.
Reference – Childs, M. 2011, ‘John McCarthy: Computer Scientist Known as the father of AI’
[Online] Independent. Available at: http://www.independent.co.uk/news/obituaries/john-
mccarthy-computer-scientist-known-as-the-father-of-ai-6255307.html [Accessed 1 Nov.
2011].
Summary:
This article describes one individual who played a significant role in development of modern
computing architecture. I chose this article because it summarises the role of John Mccarthy
is development of AI. John McCarthy is known as the father of AI or Artificial Intelligence due
to his remarkable achievement in the field of Artificial Intelligence. Artificial intelligence is a
field of developing intelligent machines that reduces the human labour.
In this article the author describes how exceptionally brilliant and a bright child McCarthy
Student Name Patel MeghabenRockeykumar.
Student Number 12051284
Week 1
The text discusses the elements of modern computing architecture however is largely silent
on the individuals who played a role in its development. Find and summarise a resource that
describes ONE such individual. The individual should have had a significant influence on the
development of computers and/or components of modern computing architecture.
Title and Reference:
Title – Artificial Intelligence.
Reference – Childs, M. 2011, ‘John McCarthy: Computer Scientist Known as the father of AI’
[Online] Independent. Available at: http://www.independent.co.uk/news/obituaries/john-
mccarthy-computer-scientist-known-as-the-father-of-ai-6255307.html [Accessed 1 Nov.
2011].
Summary:
This article describes one individual who played a significant role in development of modern
computing architecture. I chose this article because it summarises the role of John Mccarthy
is development of AI. John McCarthy is known as the father of AI or Artificial Intelligence due
to his remarkable achievement in the field of Artificial Intelligence. Artificial intelligence is a
field of developing intelligent machines that reduces the human labour.
In this article the author describes how exceptionally brilliant and a bright child McCarthy
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
was. His interest and quest to develop machines began right after attending a symposium on
‘cerebral Mechanism in behaviour’. John McCarthy was the one to term the coin Artificial
Intelligence. The achievements of John McCarthy have earned him many honours such as
Turting Award for his contribution in the field of Artificial Intelligence.
The most interesting part of this article is that it explains how McCarthy aimed at exploring
different ways a machine being able to reason like a human could do. Therefore, he
developed Artificial intelligence with an aim to make a machine capable of abstract thought,
problem solving and self-improvement.
I found this article interesting as it thoroughly described the technology of Artificial Intelligence
and how John McCarthy believed that every aspect of learning and intelligence could reflect
to the principle very precisely and a machine can possibly be developed to stimulate it as
well. This article made me think about his contribution to the field of Artificial intelligence
which is huge as he laid the foundation of the modern Artificial intelligence that has
remarkable uses and advantages in today’s world.
Week 2
The text discusses the components and activities of operating systems however is largely
silent on the individuals who played a role in their development. Find and summarise a
resource that describes ONEsuch individual. The individual should have had a significant
influence on the writing or development of operating systems.
Title and Reference:
Title – Linux Operating System
Reference – Operating-system.org. 2017, ‘History of the Linux Kernel.’ [online] Available at:
http://www.operating-system.org/betriebssystem/_english/bs-linux.htm
[Accessed 31 Aug. 2017].
URL: http://www.operating-system.org/betriebssystem/_english/bs-linux.htm
Summary:
This article discusses about Linus Torvalds who developed a Linux operating System. I chose
this article as it describes how Linus Torvalds used to program his own driver for the floppy
controller.
This article describes how Linus Torvalds intensively learned the programming of hardware
and gained improved knowledge about the Sinclair Computer with Q-DOS.
The most interesting part of this article is that it describes how Linus had always used Unix
operating system. This operating system was particularly used in the universities at that time.
However, the source code of Minix is open source and any modification to it are bounded by
license condition. Linus therefore did not find the terminal emulator program in Minix good or
acceptable, and thus began his own project in order to code his own and improved terminal
emulator with added function in hardware level. Furthermore, the most interesting part of the
article is that it describes the process by which Linus programmed his own drivers for
accessing the data medium and file system. These additional functionalities enabled the
software for being capable of downloading and uploading from internet.
I found this article useful since it discussed in detail the new operating system which was
derived from the concepts of Minix but was developed from scratch by Linus. However, the
development environment was Minix, it contained the GNU shell bash, and CNU C- compiler
and therefore it is called GNU or Linux. In August 1991, the source code was made easily
and freely accessible by ftp and therefore, Linux is still widely used as operating system.
‘cerebral Mechanism in behaviour’. John McCarthy was the one to term the coin Artificial
Intelligence. The achievements of John McCarthy have earned him many honours such as
Turting Award for his contribution in the field of Artificial Intelligence.
The most interesting part of this article is that it explains how McCarthy aimed at exploring
different ways a machine being able to reason like a human could do. Therefore, he
developed Artificial intelligence with an aim to make a machine capable of abstract thought,
problem solving and self-improvement.
I found this article interesting as it thoroughly described the technology of Artificial Intelligence
and how John McCarthy believed that every aspect of learning and intelligence could reflect
to the principle very precisely and a machine can possibly be developed to stimulate it as
well. This article made me think about his contribution to the field of Artificial intelligence
which is huge as he laid the foundation of the modern Artificial intelligence that has
remarkable uses and advantages in today’s world.
Week 2
The text discusses the components and activities of operating systems however is largely
silent on the individuals who played a role in their development. Find and summarise a
resource that describes ONEsuch individual. The individual should have had a significant
influence on the writing or development of operating systems.
Title and Reference:
Title – Linux Operating System
Reference – Operating-system.org. 2017, ‘History of the Linux Kernel.’ [online] Available at:
http://www.operating-system.org/betriebssystem/_english/bs-linux.htm
[Accessed 31 Aug. 2017].
URL: http://www.operating-system.org/betriebssystem/_english/bs-linux.htm
Summary:
This article discusses about Linus Torvalds who developed a Linux operating System. I chose
this article as it describes how Linus Torvalds used to program his own driver for the floppy
controller.
This article describes how Linus Torvalds intensively learned the programming of hardware
and gained improved knowledge about the Sinclair Computer with Q-DOS.
The most interesting part of this article is that it describes how Linus had always used Unix
operating system. This operating system was particularly used in the universities at that time.
However, the source code of Minix is open source and any modification to it are bounded by
license condition. Linus therefore did not find the terminal emulator program in Minix good or
acceptable, and thus began his own project in order to code his own and improved terminal
emulator with added function in hardware level. Furthermore, the most interesting part of the
article is that it describes the process by which Linus programmed his own drivers for
accessing the data medium and file system. These additional functionalities enabled the
software for being capable of downloading and uploading from internet.
I found this article useful since it discussed in detail the new operating system which was
derived from the concepts of Minix but was developed from scratch by Linus. However, the
development environment was Minix, it contained the GNU shell bash, and CNU C- compiler
and therefore it is called GNU or Linux. In August 1991, the source code was made easily
and freely accessible by ftp and therefore, Linux is still widely used as operating system.
Week 3
The Internet didn’t just appear – it was an evolution from earlier networks. Find and
summarise a resource that describes ONEof the networks that led to the development of the
modern Internet.
Title and Reference:
Title – NSFNET – National Science Foundation Network.
Reference – Livinginternet.com, 2017. ‘NSFNET - The Internet Launching Pad ‘ [online]
Available at: http://www.livinginternet.com/i/ii_nsfnet.htm
[Accessed 31 Aug. 2017].
URL: http://www.livinginternet.com/i/ii_nsfnet.htm
Summary:
This article describes how modern internet evolved from earlier networks. This article
describes the emergence of modern internet as a result of the evolution from the earlier
network. One such network is the NSFT or national Science Foundation Network.
This article describes how NSFNET was the driver or initiator of the first period of modern
internet. NSFNET is program coordinated and evolving project sponsored by the National
Science foundation. It is the backbone of the research computing that was deployed in mid
1980s. This network was established to provide high speed connection among the five super
computers present in the National Science foundation. The article puts light to the fact how
NSF promptly became a part of the hierarchical series of network.
The most interesting aspect of this article is that, it describes how NSF helped in the
development of regional networks that were able to carry traffic from different individual
organizations.
The article further describes how NFSNET soon became the backbone of the other
commercial networks. This network underwent many updates and by the year 1994, the traffic
of NSFNET exceeded 10 trillion bytes. NFSNET was a wide area network, which replaced the
ARPANET as the primary network of the government.
I found this particular article helpful as it highlights the journey of NSF’s network which was
mainly built for the super computers, to becoming the backbone of modern computer due to
its improved performance, public funding and private industry partnership.
Week 4
Ethernet is an example of a Layer Two (L2) data link protocol that is discussed in the text.
Find and summarise a resource that describes the features and uses of ONE other L2
protocol that is not discussed in the text (i.e. NOT Ethernet).
Title and Reference:
Title- Token Ring
Reference- Lifewire, 2017, ‘What is Token Ring and How Does it Work?’ [online] Available at:
https://www.lifewire.com/what-is-token-ring-817952
[Accessed 31 Aug. 2017].
URL: https://www.lifewire.com/what-is-token-ring-817952
Summary:
This article describes a layer two data link protocol. Token ring is an example of layer 2 data
link protocol. I chose this article because it clearly defines and describes Token Rings. It is a
local area network in which a node is allowed to transmit data only in possession of a
The Internet didn’t just appear – it was an evolution from earlier networks. Find and
summarise a resource that describes ONEof the networks that led to the development of the
modern Internet.
Title and Reference:
Title – NSFNET – National Science Foundation Network.
Reference – Livinginternet.com, 2017. ‘NSFNET - The Internet Launching Pad ‘ [online]
Available at: http://www.livinginternet.com/i/ii_nsfnet.htm
[Accessed 31 Aug. 2017].
URL: http://www.livinginternet.com/i/ii_nsfnet.htm
Summary:
This article describes how modern internet evolved from earlier networks. This article
describes the emergence of modern internet as a result of the evolution from the earlier
network. One such network is the NSFT or national Science Foundation Network.
This article describes how NSFNET was the driver or initiator of the first period of modern
internet. NSFNET is program coordinated and evolving project sponsored by the National
Science foundation. It is the backbone of the research computing that was deployed in mid
1980s. This network was established to provide high speed connection among the five super
computers present in the National Science foundation. The article puts light to the fact how
NSF promptly became a part of the hierarchical series of network.
The most interesting aspect of this article is that, it describes how NSF helped in the
development of regional networks that were able to carry traffic from different individual
organizations.
The article further describes how NFSNET soon became the backbone of the other
commercial networks. This network underwent many updates and by the year 1994, the traffic
of NSFNET exceeded 10 trillion bytes. NFSNET was a wide area network, which replaced the
ARPANET as the primary network of the government.
I found this particular article helpful as it highlights the journey of NSF’s network which was
mainly built for the super computers, to becoming the backbone of modern computer due to
its improved performance, public funding and private industry partnership.
Week 4
Ethernet is an example of a Layer Two (L2) data link protocol that is discussed in the text.
Find and summarise a resource that describes the features and uses of ONE other L2
protocol that is not discussed in the text (i.e. NOT Ethernet).
Title and Reference:
Title- Token Ring
Reference- Lifewire, 2017, ‘What is Token Ring and How Does it Work?’ [online] Available at:
https://www.lifewire.com/what-is-token-ring-817952
[Accessed 31 Aug. 2017].
URL: https://www.lifewire.com/what-is-token-ring-817952
Summary:
This article describes a layer two data link protocol. Token ring is an example of layer 2 data
link protocol. I chose this article because it clearly defines and describes Token Rings. It is a
local area network in which a node is allowed to transmit data only in possession of a
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
sequence of bits or tokens.
The article describes that in this network, all the computers are connected in a ring or star
topology for transferring tokens from host to host. The hosts that have a token which contains
the details of the destination of information to be send can send the data.
The most interesting part of this article is that, it highlights the significant use of token ring.
Token Rings prevent the networks from colliding in a network segment. This is possible
because, only the token holder is allowed to transfer data.
I found this article useful as it discusses the how token ring became one of the most widely
deployed protocol of IBM’s protocol which was released back in 1980s. Token ring was one of
the most widely used LANs before Ethernet. The article further elaborates how Ethernet was
able to knock down token ring in the market because of its low price. Token ring is more
expensive than Ethernet and therefore, could not hold the market for a longer time. The
working principle of token ring is also more complex than that of Ethernet and the speed is
slow as well. However, token ring is one of the significant resources of the data link layer.
Week 5
The text mentions the role of hackers in attacks on networked infrastructure. Find and
summarise a resource that describes ONE famous or well-known hacker.
Title and Reference:
Title- Gary McKinnon the famous hacker
Reference- Purba, N. and Purba, N, 2017 ‘Gary McKinnon reveals detail on NASA data
breach and ‘extraterrestrial life’. [online] WeLiveSecurity. Available at:
https://www.welivesecurity.com/2015/12/08/gary-mckinnon-reveals-detail-on-nasa-data-
breach-and-extraterrestrial-life/
[Accessed 31 Aug. 2017].
URL: https://www.welivesecurity.com/2015/12/08/gary-mckinnon-reveals-detail-on-nasa-data-
breach-and-extraterrestrial-life/
Summary:
This article discusses the role of a hacker in attacks on network infrastructure. I chose this
article, as it discusses about an infamous hacker Gary McKinnon. Gary McKinnon was born
in February 1966 and is a Scottish system administrator and a famous hacker. He was
accused of hacking the biggest military computer hack of recent times.
This article describes the involvement of Gary McKinnon in hacking the united States Military
Database. He was accused of forging and hacking the united states military and even NASA
computers. He deleted critical and confidential files from the operating systems of the
computer posting a message which read “your security is crap”. He was also accused of
deleting the weapons log at the Earle Naval weapons station in the year 2001 paralysing the
network of 300 computers.
McKinnon however, never admitted all these allegations. The most important aspect of this
article is that it describes how McKinnon was able to access the top-secret documents of the
military computer with the help of a program called Landsearch. He was able to gain the
control over domain with the help of this program and it also provided the power to search
files and folders on every machines.
I found this article useful as it reveals that McKinnon suffered with Asperger’s Syndrome.
Gary McKinnon is accused of serious crime and it is thought that he is seriously ill and suffers
from Asperger’s syndrome and depressive illness. McKinnon’s aim of hacking the computer
systems of NASA was that, he was searching for the information about the UFOs. McKinnon
has now started a small SEO business, which uses his technical computer skills.
The article describes that in this network, all the computers are connected in a ring or star
topology for transferring tokens from host to host. The hosts that have a token which contains
the details of the destination of information to be send can send the data.
The most interesting part of this article is that, it highlights the significant use of token ring.
Token Rings prevent the networks from colliding in a network segment. This is possible
because, only the token holder is allowed to transfer data.
I found this article useful as it discusses the how token ring became one of the most widely
deployed protocol of IBM’s protocol which was released back in 1980s. Token ring was one of
the most widely used LANs before Ethernet. The article further elaborates how Ethernet was
able to knock down token ring in the market because of its low price. Token ring is more
expensive than Ethernet and therefore, could not hold the market for a longer time. The
working principle of token ring is also more complex than that of Ethernet and the speed is
slow as well. However, token ring is one of the significant resources of the data link layer.
Week 5
The text mentions the role of hackers in attacks on networked infrastructure. Find and
summarise a resource that describes ONE famous or well-known hacker.
Title and Reference:
Title- Gary McKinnon the famous hacker
Reference- Purba, N. and Purba, N, 2017 ‘Gary McKinnon reveals detail on NASA data
breach and ‘extraterrestrial life’. [online] WeLiveSecurity. Available at:
https://www.welivesecurity.com/2015/12/08/gary-mckinnon-reveals-detail-on-nasa-data-
breach-and-extraterrestrial-life/
[Accessed 31 Aug. 2017].
URL: https://www.welivesecurity.com/2015/12/08/gary-mckinnon-reveals-detail-on-nasa-data-
breach-and-extraterrestrial-life/
Summary:
This article discusses the role of a hacker in attacks on network infrastructure. I chose this
article, as it discusses about an infamous hacker Gary McKinnon. Gary McKinnon was born
in February 1966 and is a Scottish system administrator and a famous hacker. He was
accused of hacking the biggest military computer hack of recent times.
This article describes the involvement of Gary McKinnon in hacking the united States Military
Database. He was accused of forging and hacking the united states military and even NASA
computers. He deleted critical and confidential files from the operating systems of the
computer posting a message which read “your security is crap”. He was also accused of
deleting the weapons log at the Earle Naval weapons station in the year 2001 paralysing the
network of 300 computers.
McKinnon however, never admitted all these allegations. The most important aspect of this
article is that it describes how McKinnon was able to access the top-secret documents of the
military computer with the help of a program called Landsearch. He was able to gain the
control over domain with the help of this program and it also provided the power to search
files and folders on every machines.
I found this article useful as it reveals that McKinnon suffered with Asperger’s Syndrome.
Gary McKinnon is accused of serious crime and it is thought that he is seriously ill and suffers
from Asperger’s syndrome and depressive illness. McKinnon’s aim of hacking the computer
systems of NASA was that, he was searching for the information about the UFOs. McKinnon
has now started a small SEO business, which uses his technical computer skills.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser


Week 6
Society is increasingly reliant on networks and network technologies but they are evolving at
a rapid pace. Find and summarise a resource that describes ONE example of a future
networking technology or trend that will impact society.
Title and Reference:
Title: Wireless data links for drones
Reference: Jain, 2017, Available at:
http://www.cse.wustl.edu/~jain/papers/ftp/uas_dl.pdf
[Accessed 31 Aug. 2017].
URL: http://www.cse.wustl.edu/~jain/papers/ftp/uas_dl.pdf
Summary:
This article discusses an example of future network. I chose this article as it describes
Wireless networking. Wireless networking is definitely the trendsetter of today’s world. The
bandwidth permitted for the internet access in airplane is however, very limited.
In this article, the author proposes a solution to this problem. As a solution to this problem
drones are employed for providing a high speed wireless networking feasible even over a
long distance. Many industry researchers are working in this project. The project aims at
providing a streamline communication between the Drones or Unnamed Ariel vehicle (UAV)
and the manned aircraft.
The most interesting part of this article is that, it describes the feasibility of this proposal. This
is quite feasible because drones can be easily propelled and present in the sky. This project if
implemented can benefit not only the airplanes but also the trains and cars will be benefited
from the wireless network, which is able to sustain high bandwidth, across wide distances and
at a very high speed. This is however, the major challenge in this project as well.
I found this article helpful as it discusses the challenges to build this system. The key
challenge in developing this system is that, the spectrum needs to include the high speed
aircraft in a limited or narrow availability of radio frequency spectrum. The major challenge in
aeronautical data link is the mobility. WiFi does not offer much mobility and the coverage is
only few hundred meters. The article concludes with the fact that idea of wireless data link
drones would be very efficient.
Week 7
The text mentions social business and the impact of the use of social networking platforms.
Find and summarise a resource that describes the history of the development of ONE such
social media platform.
Title and Reference:
Title: History of Twitter
Reference: Lifewire, 2017 ‘The History of Twitter You Didn't Know’ [online] Available
at:
https://www.lifewire.com/history-of-twitter-3288854
[Accessed 31 Aug. 2017].
URL: https://www.lifewire.com/history-of-twitter-3288854
Summary:
This article describes the social business and the impact of the use of social networking. I
chose this article as it discusses one such social networking platform twitter. Twitter is a
famous and widely used social media platform.
This article describes how Jack Dorsey and Evan Williams developed twitter as they were
Society is increasingly reliant on networks and network technologies but they are evolving at
a rapid pace. Find and summarise a resource that describes ONE example of a future
networking technology or trend that will impact society.
Title and Reference:
Title: Wireless data links for drones
Reference: Jain, 2017, Available at:
http://www.cse.wustl.edu/~jain/papers/ftp/uas_dl.pdf
[Accessed 31 Aug. 2017].
URL: http://www.cse.wustl.edu/~jain/papers/ftp/uas_dl.pdf
Summary:
This article discusses an example of future network. I chose this article as it describes
Wireless networking. Wireless networking is definitely the trendsetter of today’s world. The
bandwidth permitted for the internet access in airplane is however, very limited.
In this article, the author proposes a solution to this problem. As a solution to this problem
drones are employed for providing a high speed wireless networking feasible even over a
long distance. Many industry researchers are working in this project. The project aims at
providing a streamline communication between the Drones or Unnamed Ariel vehicle (UAV)
and the manned aircraft.
The most interesting part of this article is that, it describes the feasibility of this proposal. This
is quite feasible because drones can be easily propelled and present in the sky. This project if
implemented can benefit not only the airplanes but also the trains and cars will be benefited
from the wireless network, which is able to sustain high bandwidth, across wide distances and
at a very high speed. This is however, the major challenge in this project as well.
I found this article helpful as it discusses the challenges to build this system. The key
challenge in developing this system is that, the spectrum needs to include the high speed
aircraft in a limited or narrow availability of radio frequency spectrum. The major challenge in
aeronautical data link is the mobility. WiFi does not offer much mobility and the coverage is
only few hundred meters. The article concludes with the fact that idea of wireless data link
drones would be very efficient.
Week 7
The text mentions social business and the impact of the use of social networking platforms.
Find and summarise a resource that describes the history of the development of ONE such
social media platform.
Title and Reference:
Title: History of Twitter
Reference: Lifewire, 2017 ‘The History of Twitter You Didn't Know’ [online] Available
at:
https://www.lifewire.com/history-of-twitter-3288854
[Accessed 31 Aug. 2017].
URL: https://www.lifewire.com/history-of-twitter-3288854
Summary:
This article describes the social business and the impact of the use of social networking. I
chose this article as it discusses one such social networking platform twitter. Twitter is a
famous and widely used social media platform.
This article describes how Jack Dorsey and Evan Williams developed twitter as they were
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
finding a way to send text on their mobile phones. On March 2006, jack send his first tweet
just creating a revolution in the field of communication.
The most interesting part of this article is that, it explains the idea of developing this social
media plat for emerged. The name twitter was inspired by Flickr, which was a photo sharing
service. The dictionary meaning of the word twitter is ‘a short burst of inconsequential
information’, which according to Jack was perfect. The social media platform, which was born
on 2006, now has almost 200 million users and about 460000 fresh twitter accounts are
created on a daily basis. This social media platform become very popular over a short period
of time and now, more than 140 million tweets are sent on a daily basis.
I found this article helpful as it clearly describes how the business of twitter has grown over
the years as well. In the year 2008, it had only 8 employees, and now it has more than 400.
The allowed length of each tweet is 140 characters, this is because the carrier limit of SMS is
160 characters and the founders wanted to leave some space for the username as well. It
now makes revenue of $150 million annually.
Week 8
With the advent of mass data collection and storage has come data mining. Find and
summarise a resource that describes ONE example where data mining has been used
successfully by a business. You should not use any examples covered in the textbook.
Title and Reference:
Title: Netflix
Reference : Kissmetrics,2017, ‘How Netflix Uses Analytics To Select Movies, Create
Content, & Make Multimillion Dollar Decisions’ [online] Available at:
https://blog.kissmetrics.com/how-netflix-uses-analytics/
[Accessed 31 Aug. 2017].
URL: https://blog.kissmetrics.com/how-netflix-uses-analytics/
Summary:
This article describes how data mining can be used successfully by a business. I chose this
article as it describes one such platform, Netflix. Netflix is the most popular internet TV
steaming service over the world. Netflix is expanding to a number of countries and has
recently announced the expansion into 130 new countries.
The most important aspect of this article is that it clearly defines the importance of data
mining in the business of Netflix. The article describes the business of the Netflix is mainly
data driven as claimed by the CEO of Netflix, Reed Hastings. Netflix is deemed as a global
TV brand and therefore, it is very essential for the organization to know the perspectives and
views of different people in order to expand their business. Netflix thus uses data mining and
scans millions of data in order to predict which shows and movies users would normally like
to watch using the services of the Netflix.
I found this article useful as it clearly describes the business strategy of Netflix. Netflix stores
a ton of data of their existing users, which includes the content they watch and for how much
time. It also contains the demographic data as well. The company uses this information in
order to predict the successful content to be screamed and also helps in determining the
success points. Data mining procedure in Netflix includes a well-refined algorithm, which
helps in predicting the likes and dislikes of their users. Thus, data mining is an important
aspect of business in Netflix and is successfully implemented by the organization, which
helped in the growth of their business considerably.
just creating a revolution in the field of communication.
The most interesting part of this article is that, it explains the idea of developing this social
media plat for emerged. The name twitter was inspired by Flickr, which was a photo sharing
service. The dictionary meaning of the word twitter is ‘a short burst of inconsequential
information’, which according to Jack was perfect. The social media platform, which was born
on 2006, now has almost 200 million users and about 460000 fresh twitter accounts are
created on a daily basis. This social media platform become very popular over a short period
of time and now, more than 140 million tweets are sent on a daily basis.
I found this article helpful as it clearly describes how the business of twitter has grown over
the years as well. In the year 2008, it had only 8 employees, and now it has more than 400.
The allowed length of each tweet is 140 characters, this is because the carrier limit of SMS is
160 characters and the founders wanted to leave some space for the username as well. It
now makes revenue of $150 million annually.
Week 8
With the advent of mass data collection and storage has come data mining. Find and
summarise a resource that describes ONE example where data mining has been used
successfully by a business. You should not use any examples covered in the textbook.
Title and Reference:
Title: Netflix
Reference : Kissmetrics,2017, ‘How Netflix Uses Analytics To Select Movies, Create
Content, & Make Multimillion Dollar Decisions’ [online] Available at:
https://blog.kissmetrics.com/how-netflix-uses-analytics/
[Accessed 31 Aug. 2017].
URL: https://blog.kissmetrics.com/how-netflix-uses-analytics/
Summary:
This article describes how data mining can be used successfully by a business. I chose this
article as it describes one such platform, Netflix. Netflix is the most popular internet TV
steaming service over the world. Netflix is expanding to a number of countries and has
recently announced the expansion into 130 new countries.
The most important aspect of this article is that it clearly defines the importance of data
mining in the business of Netflix. The article describes the business of the Netflix is mainly
data driven as claimed by the CEO of Netflix, Reed Hastings. Netflix is deemed as a global
TV brand and therefore, it is very essential for the organization to know the perspectives and
views of different people in order to expand their business. Netflix thus uses data mining and
scans millions of data in order to predict which shows and movies users would normally like
to watch using the services of the Netflix.
I found this article useful as it clearly describes the business strategy of Netflix. Netflix stores
a ton of data of their existing users, which includes the content they watch and for how much
time. It also contains the demographic data as well. The company uses this information in
order to predict the successful content to be screamed and also helps in determining the
success points. Data mining procedure in Netflix includes a well-refined algorithm, which
helps in predicting the likes and dislikes of their users. Thus, data mining is an important
aspect of business in Netflix and is successfully implemented by the organization, which
helped in the growth of their business considerably.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Week 9
One of the greatest success stories in application development in recent times has been the
popularity of mobile apps. Find and summarise a resource that describes the story of ONE
successful mobile app developer.
Title and Reference:
Title: Jan Koum: Watsapp founder
Reference- Medium, 2017, ‘5 Things You Can Learn From The Story Of WhatsApp –
The Story Of Grip – Medium’ [online] Available at:
https://medium.com/the-story-of-grip/5-things-every-founder-can-learn-from-the-
story-of-whatsapp-b6496bc4f54d
[Accessed 31 Aug. 2017].
URL: https://medium.com/the-story-of-grip/5-things-every-founder-can-learn-from-the-story-
of-whatsapp-b6496bc4f54d
Summary:
This article describes the popularity of one mobile app. I chose this article as it deals one of
the most popular apps, Watsapp. Watsapp is one of the most widely used messaging apps of
the recent time. Watsapp has totally changed the landscape of messaging. Koum and his co
founder Brain Acton have founded one of the largest mobile messaging platforms, which
eventually became the world’s largest messaging platform in mobile.
The most important aspect of this article is that it describes that the success of Watsapp lies
in the fact that it made instant messaging very affordable for the users and revolutionized in
the field and standard of communication. Koum was a part of a famous hacker network
named woowoo. He went to san Jose state university in order to study maths but was
dropped out, when David File, the co founder of Yahoo offered him to work for him.
I found this article useful as it describes how the idea of developing WatsApp came into place
and hoe it became so popular in a short time. Kaoum came out with the idea of watsapp in
the year 2009 while watching a movie in a friend’s place. His idea was to circulate
notifications to the friends but developed it as an instant messaging app. Watsapp became
successful, as it is simple, secure and fast. It aimed at developing a messaging app with
which people would be able to communicate without any interference. People loved this app
and it became an instant hit among the masses.
Week 10
While information systems and technology deliver many benefits to society, they can also
result in (sometimes inadvertent) negative effects and outcomes. Find and summarise a
resource that describes ONE example of where the use of an information system or
technology has led to negative consequences for humans.
Title and Reference:
Title: Negative Consequence of Information Technology
Reference- Smallbusiness.chron.com ,2017, ‘The Disadvantages of Information
Technology in Business’ [online] Available at:
http://smallbusiness.chron.com/disadvantages-information-technology-business-
4020.html
[Accessed 31 Aug. 2017].
URL: https://medium.com/the-story-of-grip/5-things-every-founder-can-learn-from-the-story-
of-whatsapp-b6496bc4f54d
Summary:
One of the greatest success stories in application development in recent times has been the
popularity of mobile apps. Find and summarise a resource that describes the story of ONE
successful mobile app developer.
Title and Reference:
Title: Jan Koum: Watsapp founder
Reference- Medium, 2017, ‘5 Things You Can Learn From The Story Of WhatsApp –
The Story Of Grip – Medium’ [online] Available at:
https://medium.com/the-story-of-grip/5-things-every-founder-can-learn-from-the-
story-of-whatsapp-b6496bc4f54d
[Accessed 31 Aug. 2017].
URL: https://medium.com/the-story-of-grip/5-things-every-founder-can-learn-from-the-story-
of-whatsapp-b6496bc4f54d
Summary:
This article describes the popularity of one mobile app. I chose this article as it deals one of
the most popular apps, Watsapp. Watsapp is one of the most widely used messaging apps of
the recent time. Watsapp has totally changed the landscape of messaging. Koum and his co
founder Brain Acton have founded one of the largest mobile messaging platforms, which
eventually became the world’s largest messaging platform in mobile.
The most important aspect of this article is that it describes that the success of Watsapp lies
in the fact that it made instant messaging very affordable for the users and revolutionized in
the field and standard of communication. Koum was a part of a famous hacker network
named woowoo. He went to san Jose state university in order to study maths but was
dropped out, when David File, the co founder of Yahoo offered him to work for him.
I found this article useful as it describes how the idea of developing WatsApp came into place
and hoe it became so popular in a short time. Kaoum came out with the idea of watsapp in
the year 2009 while watching a movie in a friend’s place. His idea was to circulate
notifications to the friends but developed it as an instant messaging app. Watsapp became
successful, as it is simple, secure and fast. It aimed at developing a messaging app with
which people would be able to communicate without any interference. People loved this app
and it became an instant hit among the masses.
Week 10
While information systems and technology deliver many benefits to society, they can also
result in (sometimes inadvertent) negative effects and outcomes. Find and summarise a
resource that describes ONE example of where the use of an information system or
technology has led to negative consequences for humans.
Title and Reference:
Title: Negative Consequence of Information Technology
Reference- Smallbusiness.chron.com ,2017, ‘The Disadvantages of Information
Technology in Business’ [online] Available at:
http://smallbusiness.chron.com/disadvantages-information-technology-business-
4020.html
[Accessed 31 Aug. 2017].
URL: https://medium.com/the-story-of-grip/5-things-every-founder-can-learn-from-the-story-
of-whatsapp-b6496bc4f54d
Summary:

Thi article describes the negative consequence of IT. I chose this article as it clearly defines
the negative impact of IT on humans.
the article describes that the negative impact of the information system for humans is
definitely the loss of employment. The modern information system is capable of doing many
works that reduces the workload of an individual considerably.
Perhaps the most important aspect of this article is that. It defines the role of machines
against humans. As the machine is doing all the works of the individual, the organizations do
not have to invest on manual employment. With the improvement of technology, the tasks
that were previously performed by the human employees are now carried out by the
computers systems and therefore, the job opportunity of human is considerably reduced. The
employees who are sacked from the companies due to an improved information system may
find it difficult to get a secure job in future.
I found this article helpful as it clearly describes that fact that, with the involvement of the
modern information system, a number of issues in the security of data also arise. If data
breach takes place by any means, it, may lead to the serious loss of the organization and also
the employees as well. Previously all the data were manually kept, but with the involvement of
the information system, all the data can be stored and retrieved with a touch of a button. The
article concludes with the fact that information systems are vulnerable to security breaches,
which might lead to considerable losses to the organization.
the negative impact of IT on humans.
the article describes that the negative impact of the information system for humans is
definitely the loss of employment. The modern information system is capable of doing many
works that reduces the workload of an individual considerably.
Perhaps the most important aspect of this article is that. It defines the role of machines
against humans. As the machine is doing all the works of the individual, the organizations do
not have to invest on manual employment. With the improvement of technology, the tasks
that were previously performed by the human employees are now carried out by the
computers systems and therefore, the job opportunity of human is considerably reduced. The
employees who are sacked from the companies due to an improved information system may
find it difficult to get a secure job in future.
I found this article helpful as it clearly describes that fact that, with the involvement of the
modern information system, a number of issues in the security of data also arise. If data
breach takes place by any means, it, may lead to the serious loss of the organization and also
the employees as well. Previously all the data were manually kept, but with the involvement of
the information system, all the data can be stored and retrieved with a touch of a button. The
article concludes with the fact that information systems are vulnerable to security breaches,
which might lead to considerable losses to the organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
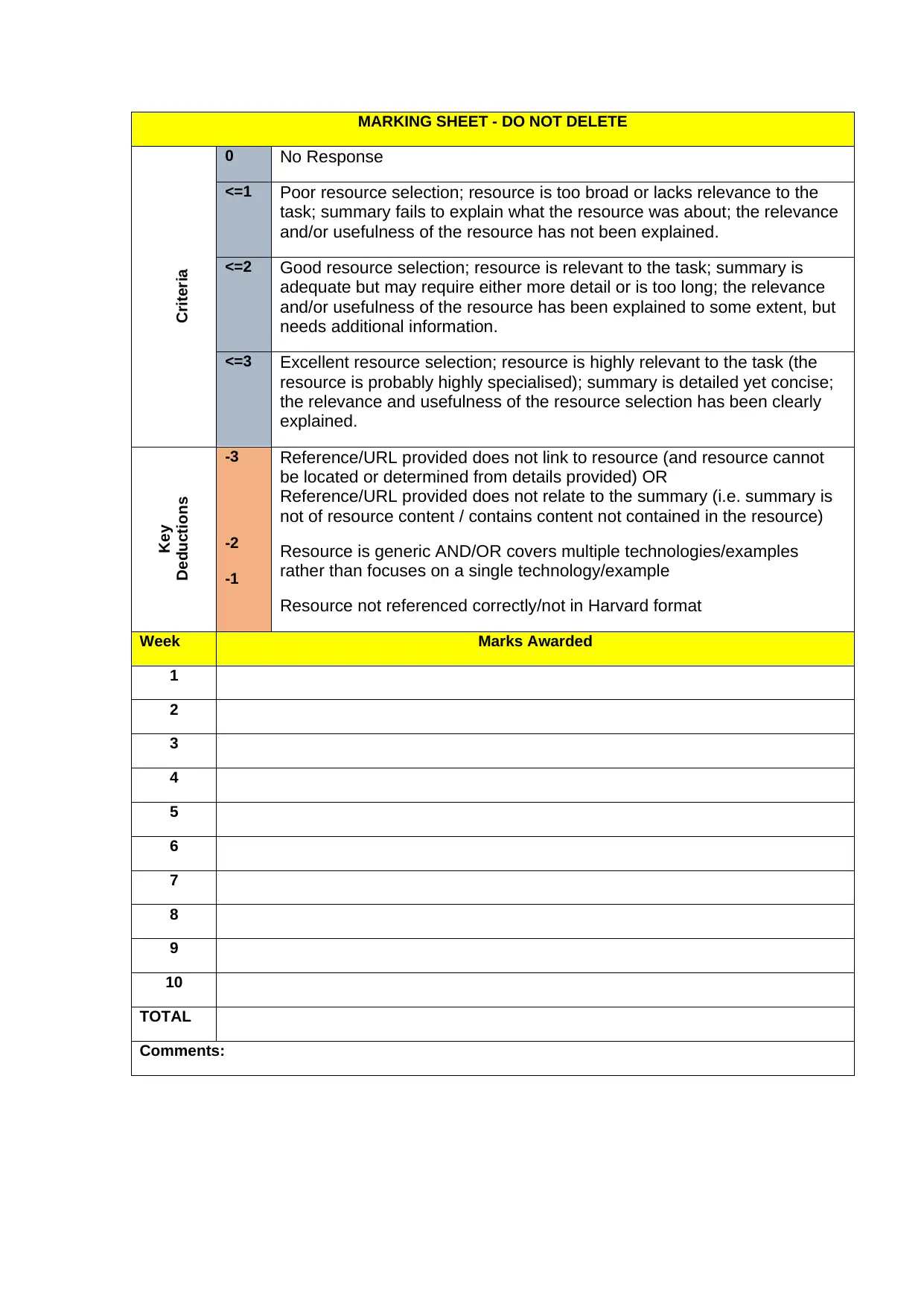
MARKING SHEET - DO NOT DELETE
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





