University Computing Assignment: TCP, Subnetting, CSS, and Patents
VerifiedAdded on 2023/04/21
|10
|2467
|461
Homework Assignment
AI Summary
This computing assignment solution covers several key concepts in computer science and networking. It begins with an explanation of the Transmission Control Protocol (TCP), focusing on cumulative and selective acknowledgement schemes and their efficiency. The solution then delves into subnetting for Class C addresses, including binary representations, subnet calculations, and practical applications. Following this, the assignment addresses different ways of implementing CSS in HTML documents, discussing inline, document-level, and external style sheets, along with their precedence. Finally, the assignment explores the topic of software patents, presenting arguments for and against their use, and discussing their impact on innovation and business.

Running head: INTRODUCTION TO COMPUTING
Introduction to Computing
Name of the Student
Name of the University
Author’s Note
Introduction to Computing
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INTRODUCTION TO COMPUTING
Answer to Question 1:
The transmission control Protocol (TCP) is used for implementation of positive
acknowledgement with retransmission. The acknowledgement scheme of TCP is known as
cumulative since it reports the number of streams that has been accumulated. There are both
advantage and disadvantage of the cumulative acknowledgements. The main advantage of
cumulative acknowledgement is that both can be easily generated and is unambiguous in
nature (Martinez, Cataldo and Heredia 2016). There is another advantage that is the
acknowledgement that are lost does not needs forced retransmission. There is a major
disadvantage that is the sender of the data packet does not have any information about the
unsuccessful retransmission but it only receives a single position in the data stream that is
received.
For understanding the reason of information lack about the successful transmission making
cumulative acknowledgement less efficient the windows spanning 5000 octets and having
starting position of 101 and if the sender transmits the data segmented in five frames. If the
first frame is lost and the other frames reaches to the destination an acknowledgement is
received for each of the frame received by the user (Shang et al. 2016). The problem is that
the acknowledgement specifies the octet numbered 101 and waits for the next highest
contiguous octet. There are no possible methodology that can be used by the receiver to
inform the sender that a major portion of the data for the current window has arrived.
In case of occurrence of the time out from the side of sender a choice is needed to be
made for the two inefficient schemes. The choice is that all the five segments can be
retransmitted or the single lost frame is retransmitted. But for this scenario the retransmission
of the five frae is inefficient since after receiving the first frame the receiver sends an
acknowledge that all the data has been received (Goralski 2017). But if the sender has to send
INTRODUCTION TO COMPUTING
Answer to Question 1:
The transmission control Protocol (TCP) is used for implementation of positive
acknowledgement with retransmission. The acknowledgement scheme of TCP is known as
cumulative since it reports the number of streams that has been accumulated. There are both
advantage and disadvantage of the cumulative acknowledgements. The main advantage of
cumulative acknowledgement is that both can be easily generated and is unambiguous in
nature (Martinez, Cataldo and Heredia 2016). There is another advantage that is the
acknowledgement that are lost does not needs forced retransmission. There is a major
disadvantage that is the sender of the data packet does not have any information about the
unsuccessful retransmission but it only receives a single position in the data stream that is
received.
For understanding the reason of information lack about the successful transmission making
cumulative acknowledgement less efficient the windows spanning 5000 octets and having
starting position of 101 and if the sender transmits the data segmented in five frames. If the
first frame is lost and the other frames reaches to the destination an acknowledgement is
received for each of the frame received by the user (Shang et al. 2016). The problem is that
the acknowledgement specifies the octet numbered 101 and waits for the next highest
contiguous octet. There are no possible methodology that can be used by the receiver to
inform the sender that a major portion of the data for the current window has arrived.
In case of occurrence of the time out from the side of sender a choice is needed to be
made for the two inefficient schemes. The choice is that all the five segments can be
retransmitted or the single lost frame is retransmitted. But for this scenario the retransmission
of the five frae is inefficient since after receiving the first frame the receiver sends an
acknowledge that all the data has been received (Goralski 2017). But if the sender has to send
2
INTRODUCTION TO COMPUTING
the only lost frame it needs to wait for the acknowledgement before deciding the how much
and what data is needed to be retransmitted. A simple positive acknowledgement is reverted
and for this the advantage of having the large window can be loosed.
Embedding the way of handling the timeout and retransmission is an ideal solution for
the TCP protocol. It is similar with the other transmission control protocol and it expects
acknowledgement of destination after receiving new octet from data stream. Each time when
a segment is sent a timer is started by the TCP and it waits for the acknowledgement. In case
the timer expires before receiving the acknowledgement it is assumed that the segment is
either lost or corrupted and it is retransmitted again (Thisted 2017). For understanding the
difference between the TCP and other network protocols we should keep in mind that TCP is
intended for using in internet environment. The segment that is travelling between machine
pairs may be sent in single and less delay network or it can be sent via multiple networks
acting as an intermediator with multiple number of hops. Thus it is impossible to estimate the
time when the acknowledgement would be received.
Answer to Question 2:
a. Subnet masks for class C addresses
Subnet Mask Subnet mask in binary Number of
subnets
Number of
hosts
255.255.255.0 11111111 11111111 11111111
00000000
20 = 1 28 - 2 = 254
255.255.255.128 11111111 11111111 11111111
10000000
21 = 2 27 - 2 = 126
255.255.255.192 11111111 11111111 11111111
11000000
22 = 4 26 – 2 = 62
INTRODUCTION TO COMPUTING
the only lost frame it needs to wait for the acknowledgement before deciding the how much
and what data is needed to be retransmitted. A simple positive acknowledgement is reverted
and for this the advantage of having the large window can be loosed.
Embedding the way of handling the timeout and retransmission is an ideal solution for
the TCP protocol. It is similar with the other transmission control protocol and it expects
acknowledgement of destination after receiving new octet from data stream. Each time when
a segment is sent a timer is started by the TCP and it waits for the acknowledgement. In case
the timer expires before receiving the acknowledgement it is assumed that the segment is
either lost or corrupted and it is retransmitted again (Thisted 2017). For understanding the
difference between the TCP and other network protocols we should keep in mind that TCP is
intended for using in internet environment. The segment that is travelling between machine
pairs may be sent in single and less delay network or it can be sent via multiple networks
acting as an intermediator with multiple number of hops. Thus it is impossible to estimate the
time when the acknowledgement would be received.
Answer to Question 2:
a. Subnet masks for class C addresses
Subnet Mask Subnet mask in binary Number of
subnets
Number of
hosts
255.255.255.0 11111111 11111111 11111111
00000000
20 = 1 28 - 2 = 254
255.255.255.128 11111111 11111111 11111111
10000000
21 = 2 27 - 2 = 126
255.255.255.192 11111111 11111111 11111111
11000000
22 = 4 26 – 2 = 62
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
INTRODUCTION TO COMPUTING
255.255.255.224 11111111 11111111 11111111
11100000
23 = 8 25 – 2 = 30
255.255.255.240 11111111 11111111 11111111
11110000
24 = 16 24 – 2 = 14
255.255.255.248 11111111.11111111.11111000
00000000
25 =32 23 – 2 =6
255.255.255.252 11111111 11111111 11111111
11111100
26 =64 22 – 2 = 2
255.255.255.255 11111111 11111111 11111111
11111111
27 = 128 21 – 2 = 0
b. 7 of the subnet calculated in the above table is usable in practice since there some usable
address remained after subnetting the network address. The subnet 255.255.255.252 can be
used for configuring the router interfaces that are used for interconnecting two routers. The
other subnets can be used for subnetting IP address for different departments based on the
number of users in each department. The last subnet 255.255.255.255 is unusable for network
configuration.
c. 2 is subtracted from the network IDs because two of the IP address 0 and 127 are kept in
reserve as these have special meanings. One of the IP address is used for broadcasting the
network information to the neighbouring hosts connected in the network and the other IP
address performs loop back functionality.
d. The CIDR Notation of the network with the IP address 201.168.67.0 and subnet mask is
given below:
201.168.67.0/25
INTRODUCTION TO COMPUTING
255.255.255.224 11111111 11111111 11111111
11100000
23 = 8 25 – 2 = 30
255.255.255.240 11111111 11111111 11111111
11110000
24 = 16 24 – 2 = 14
255.255.255.248 11111111.11111111.11111000
00000000
25 =32 23 – 2 =6
255.255.255.252 11111111 11111111 11111111
11111100
26 =64 22 – 2 = 2
255.255.255.255 11111111 11111111 11111111
11111111
27 = 128 21 – 2 = 0
b. 7 of the subnet calculated in the above table is usable in practice since there some usable
address remained after subnetting the network address. The subnet 255.255.255.252 can be
used for configuring the router interfaces that are used for interconnecting two routers. The
other subnets can be used for subnetting IP address for different departments based on the
number of users in each department. The last subnet 255.255.255.255 is unusable for network
configuration.
c. 2 is subtracted from the network IDs because two of the IP address 0 and 127 are kept in
reserve as these have special meanings. One of the IP address is used for broadcasting the
network information to the neighbouring hosts connected in the network and the other IP
address performs loop back functionality.
d. The CIDR Notation of the network with the IP address 201.168.67.0 and subnet mask is
given below:
201.168.67.0/25
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INTRODUCTION TO COMPUTING
Answer to Question 3:
a. The following are the three ways of implementation of CSS in HTML documents such as:
i. inline
ii. Document level, and
iii. External Style Sheet
The following are the example of identification of HTML code that is used for each way of
applying CSS in the HTML file that is given:
Inline
h1{
color: blue;
}
Document level
<style>
h2{color: red;}
</style>
<meta charset="UTF-8">
<h2 style="color:red;">Lightbulb joke</h2>
<h2 style="color:orange;">Knock knock joke</h2>
<h2 style="color:yellow;">Pun</h2>
External Style Sheet
<!DOCTYPE html>
INTRODUCTION TO COMPUTING
Answer to Question 3:
a. The following are the three ways of implementation of CSS in HTML documents such as:
i. inline
ii. Document level, and
iii. External Style Sheet
The following are the example of identification of HTML code that is used for each way of
applying CSS in the HTML file that is given:
Inline
h1{
color: blue;
}
Document level
<style>
h2{color: red;}
</style>
<meta charset="UTF-8">
<h2 style="color:red;">Lightbulb joke</h2>
<h2 style="color:orange;">Knock knock joke</h2>
<h2 style="color:yellow;">Pun</h2>
External Style Sheet
<!DOCTYPE html>

5
INTRODUCTION TO COMPUTING
<html lang ="en">
<head>
<link rel="stylesheet" href="blueHeadings.css">
b. The precedence is located in the browser default rules, external style sheet rules, embedded
styles and inline style rules. The specific rules can take more precedent than the general rules
and the rules that are at the ned of the style sheet can take precedence than the front rules.
The closeness of the rule to the content increases the precedence and cascading of the rules
begins with further and reaches to the closest to the content. The browsers have built in
default style sheet and its cascade starts with the styles. If there is no predefined style sheet
the styles of the browser is used and it is slightly different in each of the browser. The style
sheet of the browser is overridden by the external style sheet rules and if there are more than
one style sheet they are applied in listed order. The embedded style are next order of
precedence and if there are more than one rule they are placed in the external style sheet. The
inline styles are closer to the content and are in top precedence.
Answer to Question 4:
I think that patenting of software is a good idea for encouraging innovation and
stimulating business because patent helps in protecting one’s idea with the application of
legal means. In the current age of internet multinational business models has evolved and the
current strains are there. If a technology is patented the technology it provides a monopoly for
the technology for a period of 20 years. The technology can be used by other personnel for
exploitation once the patient expires and it helps encouraging further inventive activity
because an incentive can be received for the commercially developed technology (Urban
2016). This type of activity helps in encouraging the technological advancement. It is
difficult to measure the encouragement of innovation and different types of research is
INTRODUCTION TO COMPUTING
<html lang ="en">
<head>
<link rel="stylesheet" href="blueHeadings.css">
b. The precedence is located in the browser default rules, external style sheet rules, embedded
styles and inline style rules. The specific rules can take more precedent than the general rules
and the rules that are at the ned of the style sheet can take precedence than the front rules.
The closeness of the rule to the content increases the precedence and cascading of the rules
begins with further and reaches to the closest to the content. The browsers have built in
default style sheet and its cascade starts with the styles. If there is no predefined style sheet
the styles of the browser is used and it is slightly different in each of the browser. The style
sheet of the browser is overridden by the external style sheet rules and if there are more than
one style sheet they are applied in listed order. The embedded style are next order of
precedence and if there are more than one rule they are placed in the external style sheet. The
inline styles are closer to the content and are in top precedence.
Answer to Question 4:
I think that patenting of software is a good idea for encouraging innovation and
stimulating business because patent helps in protecting one’s idea with the application of
legal means. In the current age of internet multinational business models has evolved and the
current strains are there. If a technology is patented the technology it provides a monopoly for
the technology for a period of 20 years. The technology can be used by other personnel for
exploitation once the patient expires and it helps encouraging further inventive activity
because an incentive can be received for the commercially developed technology (Urban
2016). This type of activity helps in encouraging the technological advancement. It is
difficult to measure the encouragement of innovation and different types of research is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
INTRODUCTION TO COMPUTING
analysed for identification of effect of impact. From the different research it has been found
that if the patent application is not approved the chances of invention that it can make in the
market reduces to 1%. And if patient is granted the financial return in the business increases
by 40 to 50 percent. Patenting of the software and campaigns helps in measuring the roles for
encouraging the trend of innovation and business methods (Kiebzak, Rafert and Tucker
2016). Patient of a software would help the inventors to promote their discoveries and
maximize their returns either by commercializing and the information can be protected.
Protection can be offered with patenting the system and the flow of information would be
secured from the external agents. As an real life example the growth of the smart phone
industry can be seen where the technology have grown with the help of patent and cross
licensing for producing extraordinary smartphones that are successful today.
The success of the patent cannot be proved theoretically due to the high rate of
economic growth and innovation. The exogenous factor such as dynamism of the market,
efficacy in governmental and legal institution, the capital availability and the countless
factors are complex factor and is interdependent and causes isolation to the patents alone
(Tran 2015). Patent of a system is strongly correlated with economic prosperity, knowledge
diffusion and growth in economy. In the lifecycle of technology patents plays an important
role and the competitive technology can be protected with licensing the financial opportunity.
Patenting protects the software from exploitation without permission and it acts an important
tool for allowing innovators gaining exclusivity for a new process and development of a
strong market position and earning profit and revenue using the licensing.
The protection of software is applied in the stage of research and development for the
development of new technology. There are different departments of a company such as
specialized lawyer and research units that plays a key role in development of inventions and
preparing patent application and obtain, maintain and exploit patents (Zhang and Fang 2016).
INTRODUCTION TO COMPUTING
analysed for identification of effect of impact. From the different research it has been found
that if the patent application is not approved the chances of invention that it can make in the
market reduces to 1%. And if patient is granted the financial return in the business increases
by 40 to 50 percent. Patenting of the software and campaigns helps in measuring the roles for
encouraging the trend of innovation and business methods (Kiebzak, Rafert and Tucker
2016). Patient of a software would help the inventors to promote their discoveries and
maximize their returns either by commercializing and the information can be protected.
Protection can be offered with patenting the system and the flow of information would be
secured from the external agents. As an real life example the growth of the smart phone
industry can be seen where the technology have grown with the help of patent and cross
licensing for producing extraordinary smartphones that are successful today.
The success of the patent cannot be proved theoretically due to the high rate of
economic growth and innovation. The exogenous factor such as dynamism of the market,
efficacy in governmental and legal institution, the capital availability and the countless
factors are complex factor and is interdependent and causes isolation to the patents alone
(Tran 2015). Patent of a system is strongly correlated with economic prosperity, knowledge
diffusion and growth in economy. In the lifecycle of technology patents plays an important
role and the competitive technology can be protected with licensing the financial opportunity.
Patenting protects the software from exploitation without permission and it acts an important
tool for allowing innovators gaining exclusivity for a new process and development of a
strong market position and earning profit and revenue using the licensing.
The protection of software is applied in the stage of research and development for the
development of new technology. There are different departments of a company such as
specialized lawyer and research units that plays a key role in development of inventions and
preparing patent application and obtain, maintain and exploit patents (Zhang and Fang 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
INTRODUCTION TO COMPUTING
It is the role of the inventor to disclose patented inventions sufficiently to the public such that
other can access the new knowledge and develop the technology further. The invention can
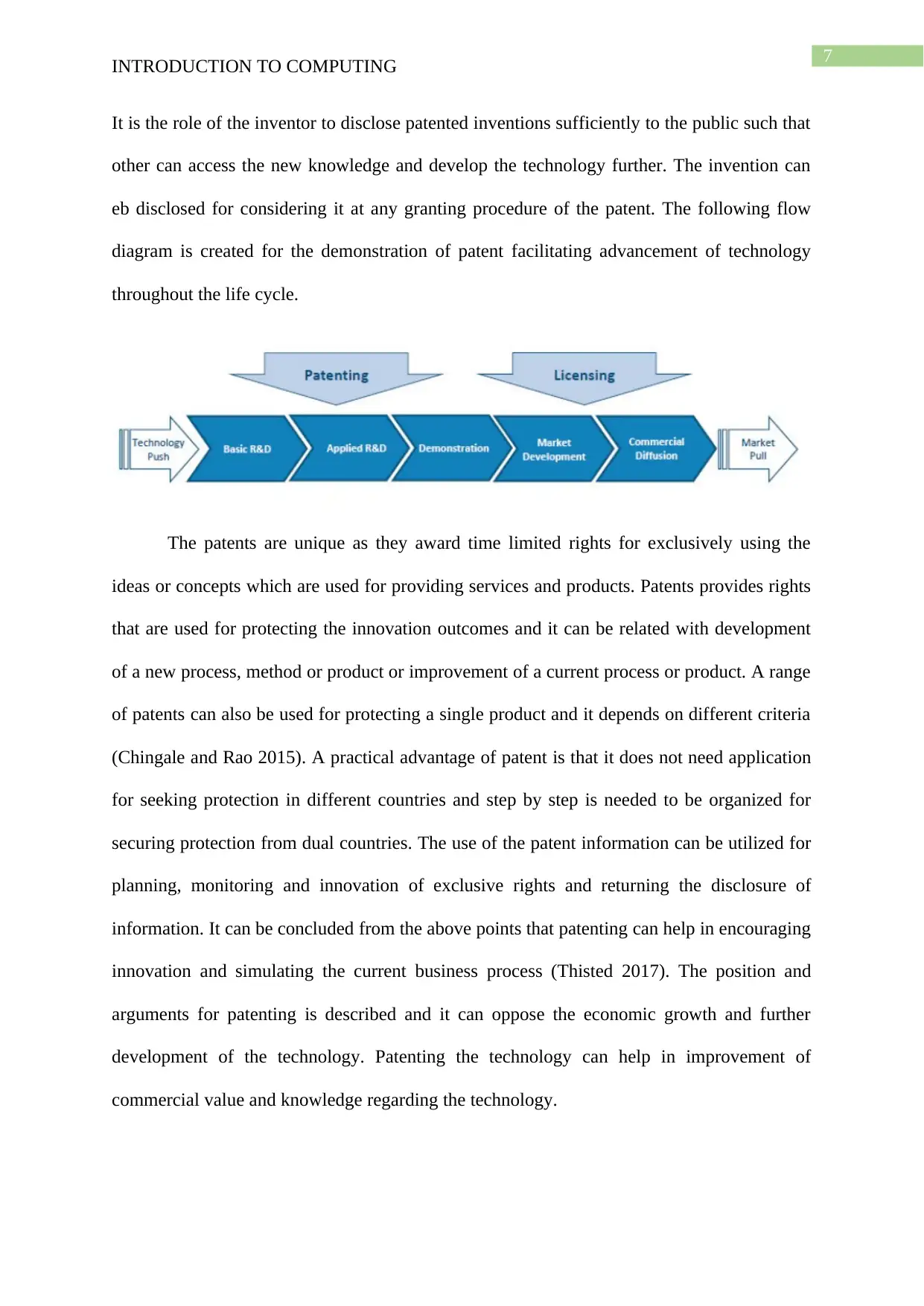
eb disclosed for considering it at any granting procedure of the patent. The following flow
diagram is created for the demonstration of patent facilitating advancement of technology
throughout the life cycle.
The patents are unique as they award time limited rights for exclusively using the
ideas or concepts which are used for providing services and products. Patents provides rights
that are used for protecting the innovation outcomes and it can be related with development
of a new process, method or product or improvement of a current process or product. A range
of patents can also be used for protecting a single product and it depends on different criteria
(Chingale and Rao 2015). A practical advantage of patent is that it does not need application
for seeking protection in different countries and step by step is needed to be organized for
securing protection from dual countries. The use of the patent information can be utilized for
planning, monitoring and innovation of exclusive rights and returning the disclosure of
information. It can be concluded from the above points that patenting can help in encouraging
innovation and simulating the current business process (Thisted 2017). The position and
arguments for patenting is described and it can oppose the economic growth and further
development of the technology. Patenting the technology can help in improvement of
commercial value and knowledge regarding the technology.
INTRODUCTION TO COMPUTING
It is the role of the inventor to disclose patented inventions sufficiently to the public such that
other can access the new knowledge and develop the technology further. The invention can
eb disclosed for considering it at any granting procedure of the patent. The following flow
diagram is created for the demonstration of patent facilitating advancement of technology
throughout the life cycle.
The patents are unique as they award time limited rights for exclusively using the
ideas or concepts which are used for providing services and products. Patents provides rights
that are used for protecting the innovation outcomes and it can be related with development
of a new process, method or product or improvement of a current process or product. A range
of patents can also be used for protecting a single product and it depends on different criteria
(Chingale and Rao 2015). A practical advantage of patent is that it does not need application
for seeking protection in different countries and step by step is needed to be organized for
securing protection from dual countries. The use of the patent information can be utilized for
planning, monitoring and innovation of exclusive rights and returning the disclosure of
information. It can be concluded from the above points that patenting can help in encouraging
innovation and simulating the current business process (Thisted 2017). The position and
arguments for patenting is described and it can oppose the economic growth and further
development of the technology. Patenting the technology can help in improvement of
commercial value and knowledge regarding the technology.

8
INTRODUCTION TO COMPUTING
Bibliography
Alani, M.M., 2017. Domestic Router Functions Configuration. In Guide to Cisco Routers
Configuration (pp. 11-39). Springer, Cham.
Chingale, R. and Rao, S.D., 2015. Software Patent in India: A Comparative Judicial and
Empirical Overview.
Goralski, W., 2017. The illustrated network: how TCP/IP works in a modern network.
Morgan Kaufmann.
Johnson, E.H., Akpan, U.I. and Agbeb, N.S., 2016. Analysis of Improved Shortest Path First
Algorithm (Ispfa) for Enhanced Interior Gateway Routing Protocol (Eigrp). American
Journal of Engineering and Technology Management, 1(3), pp.25-30.
Kennedy, W.J. and Gentle, J.E., 2018. Statistical computing. Routledge.
Kiebzak, S., Rafert, G. and Tucker, C.E., 2016. The effect of patent litigation and patent
assertion entities on entrepreneurial activity. Research Policy, 45(1), pp.218-231.
Li, J., Li, D., Huang, Y., Cheng, Y. and Ling, R., 2017, June. Quick NAT: High performance
NAT system on commodity platforms. In Local and Metropolitan Area Networks
(LANMAN), 2017 IEEE International Symposium on (pp. 1-2). IEEE.
Martinez, D.A., Cataldo, A. and Heredia, R.R., 2016. TCP/IP Communication for a De-
Manufacturing Transport Line. In Memorias de Congresos UTP (Vol. 1, No. 1, pp. 56-59).
Shang, W., Yu, Y., Droms, R. and Zhang, L., 2016. Challenges in IoT networking via TCP/IP
architecture. Technical Report NDN-0038. NDN Project.
Syed, Z.A., 2017. IP Addressing.
Thisted, R.A., 2017. Elements of statistical computing: Numerical computation. Routledge.
INTRODUCTION TO COMPUTING
Bibliography
Alani, M.M., 2017. Domestic Router Functions Configuration. In Guide to Cisco Routers
Configuration (pp. 11-39). Springer, Cham.
Chingale, R. and Rao, S.D., 2015. Software Patent in India: A Comparative Judicial and
Empirical Overview.
Goralski, W., 2017. The illustrated network: how TCP/IP works in a modern network.
Morgan Kaufmann.
Johnson, E.H., Akpan, U.I. and Agbeb, N.S., 2016. Analysis of Improved Shortest Path First
Algorithm (Ispfa) for Enhanced Interior Gateway Routing Protocol (Eigrp). American
Journal of Engineering and Technology Management, 1(3), pp.25-30.
Kennedy, W.J. and Gentle, J.E., 2018. Statistical computing. Routledge.
Kiebzak, S., Rafert, G. and Tucker, C.E., 2016. The effect of patent litigation and patent
assertion entities on entrepreneurial activity. Research Policy, 45(1), pp.218-231.
Li, J., Li, D., Huang, Y., Cheng, Y. and Ling, R., 2017, June. Quick NAT: High performance
NAT system on commodity platforms. In Local and Metropolitan Area Networks
(LANMAN), 2017 IEEE International Symposium on (pp. 1-2). IEEE.
Martinez, D.A., Cataldo, A. and Heredia, R.R., 2016. TCP/IP Communication for a De-
Manufacturing Transport Line. In Memorias de Congresos UTP (Vol. 1, No. 1, pp. 56-59).
Shang, W., Yu, Y., Droms, R. and Zhang, L., 2016. Challenges in IoT networking via TCP/IP
architecture. Technical Report NDN-0038. NDN Project.
Syed, Z.A., 2017. IP Addressing.
Thisted, R.A., 2017. Elements of statistical computing: Numerical computation. Routledge.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
INTRODUCTION TO COMPUTING
Tran, J.L., 2015. Software Patents: A One-Year Review of Alice v. CLS Bank. J. Pat. &
Trademark Off. Soc'y, 97, p.532.
Urban, J., 2016. A Proposal for a Defensive Patent License.
Zhang, T. and Fang, J., 2016. For IP Transaction Practitioners and IP Managers (Relating to
Deal Structure of Patent Acquisitions, IP Monetization, Patent Cross-Licensing, or
Technology Transfers). World Scientific Book Chapters, pp.282-325.
INTRODUCTION TO COMPUTING
Tran, J.L., 2015. Software Patents: A One-Year Review of Alice v. CLS Bank. J. Pat. &
Trademark Off. Soc'y, 97, p.532.
Urban, J., 2016. A Proposal for a Defensive Patent License.
Zhang, T. and Fang, J., 2016. For IP Transaction Practitioners and IP Managers (Relating to
Deal Structure of Patent Acquisitions, IP Monetization, Patent Cross-Licensing, or
Technology Transfers). World Scientific Book Chapters, pp.282-325.
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


