COIT20246 Assignment: Computing Architecture, Networking, and Hackers
VerifiedAdded on 2020/03/28
|13
|4270
|67
Homework Assignment
AI Summary
This assignment, submitted by KORRAPATI JYOTHI VENKATESH BABU (Student Number: 12053123), addresses several key areas in computing and networking. It begins by summarizing the contributions of John von Neumann to modern computing architecture, highlighting his work on stored-program computers. The assignment then examines Ken Thompson's invention of the Unix operating system, followed by a discussion of ARPANET's role in the development of the internet. It also includes a summary of Point-to-Point Protocol (PPP) as a Layer 2 data link protocol, differentiating it from Ethernet. Additionally, the assignment explores the activities of Gary McKinnon, a famous hacker, and concludes with a summary of virtual reality as a future networking technology and its potential impact on society. The assignment relies on research from various sources, properly cited using the Harvard referencing style, to provide a comprehensive overview of these topics.
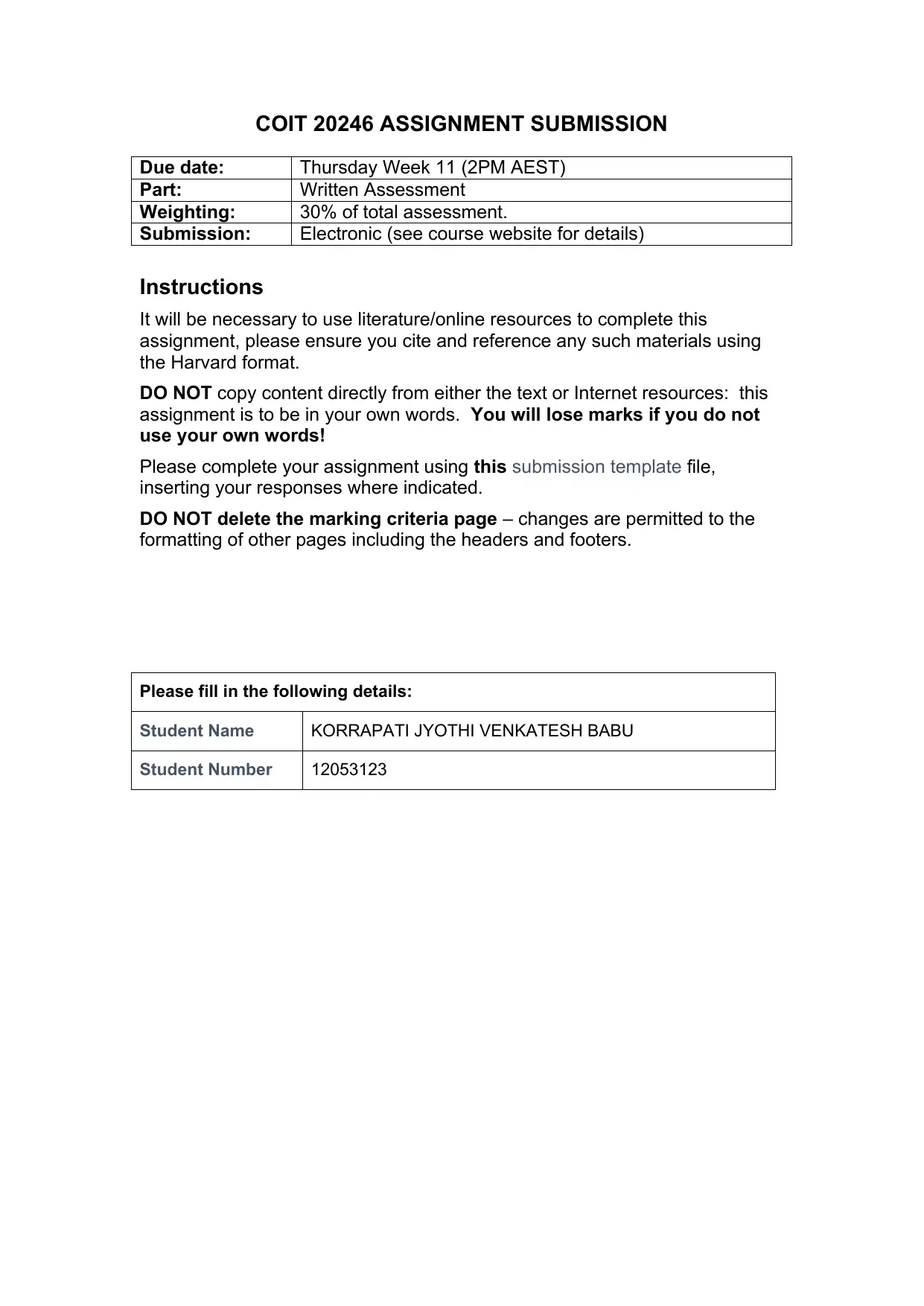
COIT 20246 ASSIGNMENT SUBMISSION
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
It will be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using
the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not
use your own words!
Please complete your assignment using this submission template file,
inserting your responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name KORRAPATI JYOTHI VENKATESH BABU
Student Number 12053123
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
It will be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using
the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not
use your own words!
Please complete your assignment using this submission template file,
inserting your responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name KORRAPATI JYOTHI VENKATESH BABU
Student Number 12053123
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 1
The text discusses the elements of modern computing architecture however is largely silent
on the individuals who played a role in its development. Find and summarise a resource that
describes ONE such individual. The individual should have had a significant influence on the
development of computers and/or components of modern computing architecture.
Title and Reference:
John von Neumann – Father Of Modern Computing Architecture
Harvard Reference - Von Neumann, J., 2012. The computer and the brain. Yale
University Press.
URL - http://www.computinghistory.org.uk/det/3665/john-von-neumann/
Summary:
The resource talks about John von Neumann’s contributions towards developing the
modern architecture for computing. This highlights how Neumann had undertaken a
study to demonstrate that computers could have a simple and definite structure but
still manage to perform any sort of computation without any hardware modifications
(Von Neumann 2012).
The reason for selecting this resource is that, this briefly explains the role of a person
named, John von Neumann who is regarded as the father of modern computing
architecture and states the role he had played to develop the structure. John von
Neumann, who was a mathematician, through his study had contributed a fresh
understanding on how one can organize and build fast computers.
The main points discussed in the resource are :
a) The resource explains how Neumann developed an understanding that a
simple structure of computer could also carry out tasks if they are properly
programmed and without any hardware modification.
b) The contribution of Neumann comes from the fact that an understanding was
developed regarding the way modern computers must be made to organize and
build. This is regarded as a technique for stored programs which had become a
base in the future generations of high speed computers.
The resource was useful because the information related to an individual who had
contributed in the development of modern computer architecture, was appropriately
found, through Neumann’s invaluable contributions.
The text discusses the elements of modern computing architecture however is largely silent
on the individuals who played a role in its development. Find and summarise a resource that
describes ONE such individual. The individual should have had a significant influence on the
development of computers and/or components of modern computing architecture.
Title and Reference:
John von Neumann – Father Of Modern Computing Architecture
Harvard Reference - Von Neumann, J., 2012. The computer and the brain. Yale
University Press.
URL - http://www.computinghistory.org.uk/det/3665/john-von-neumann/
Summary:
The resource talks about John von Neumann’s contributions towards developing the
modern architecture for computing. This highlights how Neumann had undertaken a
study to demonstrate that computers could have a simple and definite structure but
still manage to perform any sort of computation without any hardware modifications
(Von Neumann 2012).
The reason for selecting this resource is that, this briefly explains the role of a person
named, John von Neumann who is regarded as the father of modern computing
architecture and states the role he had played to develop the structure. John von
Neumann, who was a mathematician, through his study had contributed a fresh
understanding on how one can organize and build fast computers.
The main points discussed in the resource are :
a) The resource explains how Neumann developed an understanding that a
simple structure of computer could also carry out tasks if they are properly
programmed and without any hardware modification.
b) The contribution of Neumann comes from the fact that an understanding was
developed regarding the way modern computers must be made to organize and
build. This is regarded as a technique for stored programs which had become a
base in the future generations of high speed computers.
The resource was useful because the information related to an individual who had
contributed in the development of modern computer architecture, was appropriately
found, through Neumann’s invaluable contributions.

Week 2
The text discusses the components and activities of operating systems however is largely
silent on the individuals who played a role in their development. Find and summarise a
resource that describes ONEsuch individual. The individual should have had a significant
influence on the writing or development of operating systems.
Title and Reference:
Ken Thompson – Inventor Of Unix Operating System.
Harvard Reference - McPherson, T., 2013. US operating systems at mid-
century. Race after the Internet.
Lam, M., 2015. Data structures and Algorithms.
Mishra, A. and Dixit, A.M., 2013. A Secure Software Engineering Perspective.
URL - https://www.unixmen.com/ken-thompson-unix-systems-father/
Summary:
Ken Thompson was invented a Unix operating system and the resources are used for
this person. After many years of discovery, Unix is one of the best operating system
that has been taken into consideration.
The resource was only taken into consideration because it gives a proper outlook of
an individual, who is concerned with the invention of the operating system
(McPherson 2013). The resources gives proper description on the Kenneth Thompson
who is the part of the Bell systems and afterwards the decision is made to discover the
Unix operating system in the year 1969 (Lam 2015).
There are various points that gives main focus on the resources and that are :
a) The UNIX operating system was launched by Kenneth Thompson in 1969.
b) There are various amendments that are taken into consideration in 1970
which is concerned with the operating system.
c) In 1972 Kenneth described more about the operating system which is related
with the programming in the C language.
d) The steps which have been taken ensured the Potential growth for the UNIX
operating system.
The resources are considered as useful information and also it is has collected in an
easy manner. The main aim of the task is to consider the individual who is engaged
to conduct the activities that are concerned to invent the Unix operating system to a
great extent in enhancing the development (Mishra and Dixit 2013). The resource
helped in accumulating the information for serving the purpose of the task where
details regarding a developer developing the operating system could be framed in the
best possible manner.
The text discusses the components and activities of operating systems however is largely
silent on the individuals who played a role in their development. Find and summarise a
resource that describes ONEsuch individual. The individual should have had a significant
influence on the writing or development of operating systems.
Title and Reference:
Ken Thompson – Inventor Of Unix Operating System.
Harvard Reference - McPherson, T., 2013. US operating systems at mid-
century. Race after the Internet.
Lam, M., 2015. Data structures and Algorithms.
Mishra, A. and Dixit, A.M., 2013. A Secure Software Engineering Perspective.
URL - https://www.unixmen.com/ken-thompson-unix-systems-father/
Summary:
Ken Thompson was invented a Unix operating system and the resources are used for
this person. After many years of discovery, Unix is one of the best operating system
that has been taken into consideration.
The resource was only taken into consideration because it gives a proper outlook of
an individual, who is concerned with the invention of the operating system
(McPherson 2013). The resources gives proper description on the Kenneth Thompson
who is the part of the Bell systems and afterwards the decision is made to discover the
Unix operating system in the year 1969 (Lam 2015).
There are various points that gives main focus on the resources and that are :
a) The UNIX operating system was launched by Kenneth Thompson in 1969.
b) There are various amendments that are taken into consideration in 1970
which is concerned with the operating system.
c) In 1972 Kenneth described more about the operating system which is related
with the programming in the C language.
d) The steps which have been taken ensured the Potential growth for the UNIX
operating system.
The resources are considered as useful information and also it is has collected in an
easy manner. The main aim of the task is to consider the individual who is engaged
to conduct the activities that are concerned to invent the Unix operating system to a
great extent in enhancing the development (Mishra and Dixit 2013). The resource
helped in accumulating the information for serving the purpose of the task where
details regarding a developer developing the operating system could be framed in the
best possible manner.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week 3
The Internet didn’t just appear – it was an evolution from earlier networks. Find and
summarise a resource that describes ONEof the networks that led to the development of the
modern Internet.
Title and Reference:
ARPANET – Led To The Development Of Internet.
Harvard Reference - Dutton, W.H., 2013. Internet studies: The foundations of a
transformative field. Browser Download This Paper.
Russell, A.L., 2012, October. Histories of Networking vs. the History of the Internet. In SIGCIS
Workshop (Vol. 7).
URL : https://www.livescience.com/20727-internet-history.html
Summary:
The resource deals with the detailed description of one network, named ARPANET
which ultimately had led to the evolution of modern Internet. ARPANET was created
by Leonard Kleinrock in the year 1961, which has been the driving force towards the
creation of the modern internet (Dutton 2013).
The main reason is that the resource provides all the relevant information regarding
how the modern internet got evolved through ARPANET and the role which
ARPANET developers played for developing the protocols required for the modern
internet to function. The TCP and IP, which are well known nowadays, were the
protocols used by ARPANET and now these have become the standard protocols for
the internet (Russell 2012).
The key information covered in the resource are :
i) ARPANET or Advanced Research Project’s Agency Network was the predecessor
for internet, which is the backbone for the numerous amount of mails, facebook posts,
tweets that take place nowadays.
ii) This resource contains a series of timeline events starting way back from the year
1965 when two computers in Lincoln Lab of MIT communicated with one another
using a technology called packet-switching.
iii) The year 1973 saw the global networking concept becoming a reality as
University College of London and Norway’s Royal Radar Establishment connected to
ARPANET. This gave birth to the term Internet.
The resource was useful because all the relevant information for the task could be
gathered and put forward for better understanding and cite out the usefulness in using
the internet for all relevant purposes.
The Internet didn’t just appear – it was an evolution from earlier networks. Find and
summarise a resource that describes ONEof the networks that led to the development of the
modern Internet.
Title and Reference:
ARPANET – Led To The Development Of Internet.
Harvard Reference - Dutton, W.H., 2013. Internet studies: The foundations of a
transformative field. Browser Download This Paper.
Russell, A.L., 2012, October. Histories of Networking vs. the History of the Internet. In SIGCIS
Workshop (Vol. 7).
URL : https://www.livescience.com/20727-internet-history.html
Summary:
The resource deals with the detailed description of one network, named ARPANET
which ultimately had led to the evolution of modern Internet. ARPANET was created
by Leonard Kleinrock in the year 1961, which has been the driving force towards the
creation of the modern internet (Dutton 2013).
The main reason is that the resource provides all the relevant information regarding
how the modern internet got evolved through ARPANET and the role which
ARPANET developers played for developing the protocols required for the modern
internet to function. The TCP and IP, which are well known nowadays, were the
protocols used by ARPANET and now these have become the standard protocols for
the internet (Russell 2012).
The key information covered in the resource are :
i) ARPANET or Advanced Research Project’s Agency Network was the predecessor
for internet, which is the backbone for the numerous amount of mails, facebook posts,
tweets that take place nowadays.
ii) This resource contains a series of timeline events starting way back from the year
1965 when two computers in Lincoln Lab of MIT communicated with one another
using a technology called packet-switching.
iii) The year 1973 saw the global networking concept becoming a reality as
University College of London and Norway’s Royal Radar Establishment connected to
ARPANET. This gave birth to the term Internet.
The resource was useful because all the relevant information for the task could be
gathered and put forward for better understanding and cite out the usefulness in using
the internet for all relevant purposes.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 4
Ethernet is an example of a Layer Two (L2) data link protocol that is discussed in the text.
Find and summarise a resource that describes the features and uses of ONE other L2
protocol that is not discussed in the text (i.e. NOT Ethernet).
Title and Reference:
Point-to-Point Protocol – A Link Between Nodes
Harvard Reference - Foxworthy, M., Chandran, G. and Lau, J., Viasat, Inc.,
2013. Access node/gateway to access node/gateway layer-2 connectivity (end-to-end).
U.S. Patent 8,345,650.
URL - http://www.ccnablog.com/ppp-point-to-point-protocol/
Summary:
The resource talks about the details regarding Point-to-Point Protocol, where the uses
and how the protocol carries out the operations are discussed.
The resource was selected mainly because of the fact that all relevant information
pertaining to the task got compiled in one place. The task requires to take into account
certain uses and features of this Layer Two Protocol. The relevant details help to
discuss in length details regarding Point-to-Point Protocol (Foxworthy et al.2013).
The features of Point-to-Point Protocol are :
i) The PPP has the provision of Link Quality Management through
which the quality of the link gets monitored. The Link gets shut
down once PPR detects a number of errors on a link.
ii) PPP uses Password Authentication Protocol or Challenge
Handshake Authentication Protocol to authenticate the users and
thereby prevent the unauthorised access for people dealing in
frauds.
Some of the uses of Point-to-Point Protocol are :
i) The protocol uses Link Control Protocol to establish, configure and
test the validity of the link.
ii) Frames get encapsulated through the usage of HDLC Protocol
iii) This protocol also uses Network Control Protocols for the purpose of
negotiating the different protocols of layer 3.
iv) Point-to-Point Protocol uses mainly LCP or Link Control Protocol
for operations.
The resource was useful because all the relevant information regarding the
requirements of task could be managed quite efficiently and easily. The features and
uses of Point-to-Point Protocol could be easily identified by going through the
resource.
Ethernet is an example of a Layer Two (L2) data link protocol that is discussed in the text.
Find and summarise a resource that describes the features and uses of ONE other L2
protocol that is not discussed in the text (i.e. NOT Ethernet).
Title and Reference:
Point-to-Point Protocol – A Link Between Nodes
Harvard Reference - Foxworthy, M., Chandran, G. and Lau, J., Viasat, Inc.,
2013. Access node/gateway to access node/gateway layer-2 connectivity (end-to-end).
U.S. Patent 8,345,650.
URL - http://www.ccnablog.com/ppp-point-to-point-protocol/
Summary:
The resource talks about the details regarding Point-to-Point Protocol, where the uses
and how the protocol carries out the operations are discussed.
The resource was selected mainly because of the fact that all relevant information
pertaining to the task got compiled in one place. The task requires to take into account
certain uses and features of this Layer Two Protocol. The relevant details help to
discuss in length details regarding Point-to-Point Protocol (Foxworthy et al.2013).
The features of Point-to-Point Protocol are :
i) The PPP has the provision of Link Quality Management through
which the quality of the link gets monitored. The Link gets shut
down once PPR detects a number of errors on a link.
ii) PPP uses Password Authentication Protocol or Challenge
Handshake Authentication Protocol to authenticate the users and
thereby prevent the unauthorised access for people dealing in
frauds.
Some of the uses of Point-to-Point Protocol are :
i) The protocol uses Link Control Protocol to establish, configure and
test the validity of the link.
ii) Frames get encapsulated through the usage of HDLC Protocol
iii) This protocol also uses Network Control Protocols for the purpose of
negotiating the different protocols of layer 3.
iv) Point-to-Point Protocol uses mainly LCP or Link Control Protocol
for operations.
The resource was useful because all the relevant information regarding the
requirements of task could be managed quite efficiently and easily. The features and
uses of Point-to-Point Protocol could be easily identified by going through the
resource.

Week 5
The text mentions the role of hackers in attacks on networked infrastructure. Find and
summarise a resource that describes ONE famous or well-known hacker.
Title and Reference:
Gary McKinnon – Hacker Who Hacked Into The Database Of NASA
Harvard Referennce - Ledingham, R. and Mills, R., 2015. A preliminary study of autism
and cybercrime in the context of international law enforcement. Advances in Autism, 1(1),
pp.2-11.
Anto, Y., 2012. The Art of Hacking. ANTO.
URL - http://fourthkind.com/ufo-hacker-gary-mckinnon-story/
Summary:
The resource deals with a famous hacker, named Gary McKinnon, who had hacked
into the database of NASA other government agencies for accumulating evidence on
UFO (Ledingham and Mills 2015). The resource gives a brief overview of the hacker
regarding his nationality and background, from where the information can be gathered
that he is a part-time IT technician and stays in the United Kingdom. The information
provided in the resource talks about how McKinnon had single handedly broken
through into the computer networks of US Navy, Air Force, US Army, Pentagon and
of course offices of NASA (Anto 2012).
The main reason behind selecting this resource is because, the content deals with the
information which is relevant with the task in hand. The requirement of the task is to
describe one famous or well-known hacker and this resource provides exactly that.
This has enough information to fulfil all the requirements.
The main points covered in the resource are :
i) Gary McKinnon, a famous hacker is a citizen of UK and he is a part-time technician
of IT .
ii) He has hacked into the systems of US Government Agenices and also into the
databases of NASA.
iii) He is known to have hacked into a total of 97 computers for 5 government
agencies.
The resource was useful because all the relevant information pertaining to the
completion of task was present. The
The text mentions the role of hackers in attacks on networked infrastructure. Find and
summarise a resource that describes ONE famous or well-known hacker.
Title and Reference:
Gary McKinnon – Hacker Who Hacked Into The Database Of NASA
Harvard Referennce - Ledingham, R. and Mills, R., 2015. A preliminary study of autism
and cybercrime in the context of international law enforcement. Advances in Autism, 1(1),
pp.2-11.
Anto, Y., 2012. The Art of Hacking. ANTO.
URL - http://fourthkind.com/ufo-hacker-gary-mckinnon-story/
Summary:
The resource deals with a famous hacker, named Gary McKinnon, who had hacked
into the database of NASA other government agencies for accumulating evidence on
UFO (Ledingham and Mills 2015). The resource gives a brief overview of the hacker
regarding his nationality and background, from where the information can be gathered
that he is a part-time IT technician and stays in the United Kingdom. The information
provided in the resource talks about how McKinnon had single handedly broken
through into the computer networks of US Navy, Air Force, US Army, Pentagon and
of course offices of NASA (Anto 2012).
The main reason behind selecting this resource is because, the content deals with the
information which is relevant with the task in hand. The requirement of the task is to
describe one famous or well-known hacker and this resource provides exactly that.
This has enough information to fulfil all the requirements.
The main points covered in the resource are :
i) Gary McKinnon, a famous hacker is a citizen of UK and he is a part-time technician
of IT .
ii) He has hacked into the systems of US Government Agenices and also into the
databases of NASA.
iii) He is known to have hacked into a total of 97 computers for 5 government
agencies.
The resource was useful because all the relevant information pertaining to the
completion of task was present. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week 6
Society is increasingly reliant on networks and network technologies but they are evolving at
a rapid pace. Find and summarise a resource that describes ONE example of a future
networking technology or trend that will impact society.
Title and Reference:
Virtual Reality – Technology For The Future
Harvard Reference - Biocca, F. and Levy, M.R. eds., 2013. Communication in the age
of virtual reality. Routledge.
URL - http://changes-of-tomorrow.hyperisland.com/technology
Summary:
The resource talks about the advent of Virtual Reality, which refers to a computer
technology that helps generate a three-dimensional image and the image seems to
surround the user. Though the concept of Virtual Reality has been around for over 45
years, only for the last 3-4 years that the true power of this unique technology has
made way to quite a few small developers, which has helped to start off with the
innovation (Biocca & Levy 2013).
The main reason behind selecting this resource is because the resource talks about a
technology, Virtual Reality, which is expected to take the world by storm. With
internet already making things incredibly easy for people to lead their lives, as getting
information from across the world is just few clicks away, now with the concept of
Virtual Technology, people can experience three-dimensional image easily just the
way they can make video calls.
The main points covered in the resource are:
a) Virtual Reality provides an unique experience where three-dimensional image
can be seen which can give the feeling of physical presence.
b) The technology of Virtual Reality is extremely powerful as well as affordable.
c) The whole understanding of reality will change, enabling everyone across the
world to get involved.
d) The growth for the next three years are set to rise well above the demand which
the world had seen for iPhones.
The main reason behind selecting the resource is that the resource has provided all the
essential information required to present this task by covering all the requirements.
Society is increasingly reliant on networks and network technologies but they are evolving at
a rapid pace. Find and summarise a resource that describes ONE example of a future
networking technology or trend that will impact society.
Title and Reference:
Virtual Reality – Technology For The Future
Harvard Reference - Biocca, F. and Levy, M.R. eds., 2013. Communication in the age
of virtual reality. Routledge.
URL - http://changes-of-tomorrow.hyperisland.com/technology
Summary:
The resource talks about the advent of Virtual Reality, which refers to a computer
technology that helps generate a three-dimensional image and the image seems to
surround the user. Though the concept of Virtual Reality has been around for over 45
years, only for the last 3-4 years that the true power of this unique technology has
made way to quite a few small developers, which has helped to start off with the
innovation (Biocca & Levy 2013).
The main reason behind selecting this resource is because the resource talks about a
technology, Virtual Reality, which is expected to take the world by storm. With
internet already making things incredibly easy for people to lead their lives, as getting
information from across the world is just few clicks away, now with the concept of
Virtual Technology, people can experience three-dimensional image easily just the
way they can make video calls.
The main points covered in the resource are:
a) Virtual Reality provides an unique experience where three-dimensional image
can be seen which can give the feeling of physical presence.
b) The technology of Virtual Reality is extremely powerful as well as affordable.
c) The whole understanding of reality will change, enabling everyone across the
world to get involved.
d) The growth for the next three years are set to rise well above the demand which
the world had seen for iPhones.
The main reason behind selecting the resource is that the resource has provided all the
essential information required to present this task by covering all the requirements.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 7
The text mentions social business and the impact of the use of social networking platforms.
Find and summarise a resource that describes the history of the development of ONE such
social media platform.
Title and Reference:
Social Media’s Role In Modern Business World
Harvard Reference - Sinkovics, N., Sinkovics, R.R. and Yamin, M., 2014. The role of
social value creation in business model formulation at the bottom of the pyramid–
implications for MNEs?. International Business Review, 23(4), pp.692-707.
Kasemsap, K., 2017. Mastering social media in the modern business world. In Social media
listening and monitoring for business applications (pp. 18-44). IGI Global.
URL - https://www.forbes.com/sites/moneywisewomen/2012/08/08/the-developing-
role-of-social-media-in-the-modern-business-world/#270d27e56fd6
Summary:
Despite Social Media being a relatively recent phenomena, still this is surely
becoming an increasingly integral part of any business, who is primarily looking to
grow customers by reaching out to them through their marketing strategies. The
resource elaborates about the need for businesses to have strong social media
presence apart from grabbing the attention in traditional marketplace. The fact that the
resource talks about fulfilling the objectives of an organization through digital means
is equally important as compared to traditional marketing strategies goes to show that
the importance of social media presence is paramount.
The main reason behind selecting this resource is that the resource vividly describes
how a social media platform helps businesses to grow as people are more engaged in
facebook and other social media channels and they are aware of the presence of
different companies through different facebook pages, through which they can
interact with their cutomers (Sinkovics, Sinkovics and Yamin 2014). Businesses use
their facebook pages for getting their products marketed, provide certain offers and
also help build brands.
The main points covered are about the changing trends for the world of business, how
important existence of businesses in social media is, has also been depicted through
the resource.
The resource was useful because they had highlighted different social media
platforms and their respective contribution towards making businesses digitally
sound. Talking of one platform would be facebook, where businesses maintain their
respective pages to attract the attention of customers and communicate with them on
personal levels (Kasemsap 2017).
The text mentions social business and the impact of the use of social networking platforms.
Find and summarise a resource that describes the history of the development of ONE such
social media platform.
Title and Reference:
Social Media’s Role In Modern Business World
Harvard Reference - Sinkovics, N., Sinkovics, R.R. and Yamin, M., 2014. The role of
social value creation in business model formulation at the bottom of the pyramid–
implications for MNEs?. International Business Review, 23(4), pp.692-707.
Kasemsap, K., 2017. Mastering social media in the modern business world. In Social media
listening and monitoring for business applications (pp. 18-44). IGI Global.
URL - https://www.forbes.com/sites/moneywisewomen/2012/08/08/the-developing-
role-of-social-media-in-the-modern-business-world/#270d27e56fd6
Summary:
Despite Social Media being a relatively recent phenomena, still this is surely
becoming an increasingly integral part of any business, who is primarily looking to
grow customers by reaching out to them through their marketing strategies. The
resource elaborates about the need for businesses to have strong social media
presence apart from grabbing the attention in traditional marketplace. The fact that the
resource talks about fulfilling the objectives of an organization through digital means
is equally important as compared to traditional marketing strategies goes to show that
the importance of social media presence is paramount.
The main reason behind selecting this resource is that the resource vividly describes
how a social media platform helps businesses to grow as people are more engaged in
facebook and other social media channels and they are aware of the presence of
different companies through different facebook pages, through which they can
interact with their cutomers (Sinkovics, Sinkovics and Yamin 2014). Businesses use
their facebook pages for getting their products marketed, provide certain offers and
also help build brands.
The main points covered are about the changing trends for the world of business, how
important existence of businesses in social media is, has also been depicted through
the resource.
The resource was useful because they had highlighted different social media
platforms and their respective contribution towards making businesses digitally
sound. Talking of one platform would be facebook, where businesses maintain their
respective pages to attract the attention of customers and communicate with them on
personal levels (Kasemsap 2017).

Week 8
With the advent of mass data collection and storage has come data mining. Find and
summarise a resource that describes ONE example where data mining has been used
successfully by a business. You should not use any examples covered in the textbook.
Title and Reference:
Amazon – Organization Which Has Successfully Used Big Data.
Harvard References - Berinsky, A.J., Huber, G.A. and Lenz, G.S., 2012. Evaluating online
labor markets for experimental research: Amazon. com's Mechanical Turk. Political
Analysis, 20(3), pp.351-368.
Hashem, I.A.T., Yaqoob, I., Anuar, N.B., Mokhtar, S., Gani, A. and Khan, S.U., 2015. The rise
of “big data” on cloud computing: Review and open research issues. Information Systems, 47,
pp.98-115.
URL - https://www.smartdatacollective.com/lessons-how-amazon-uses-big-data/
Summary:
The resource talks about how data mining has been used effectively by Amazon,
which is a E-Commerce and Cloud Computing Company. Data Mining is nothing but
the practice through which the already existing databases are examined, so as to
generate new information (Berinsky, Huber and Lenz 2012). The resource provides
the details regarding the expertise shown by Amazon by handling big data in an
effective manner over a period of years.
The reason for selecting this resource is that the content available in the article suits
the task and help to fulfil the requirements. The resource emphasizes on the fact how
the global giant has successfully gathered data, analyse and then implement analytics
of those data. Through the extensive analysis of data, the company has only used
them for their own purpose but also helped others in effectively leveraging data and
thereby let them enjoy the benefits (Hashem et al. 2015).
The main points covered in the resource are :
i) Accumulation of big data is not an easy job
ii) A whole lot of expertise and understanding are required on how to use big data in
an effective manner to yield the desired results through extensive analysis.
iii) Amazon, the global giant and leader in technology innovation has used big data in
a very effective manner
The resource was useful because the resource has highlighted the effects of data
mining and how Amazon has accumulated data for serving their own purpose and also
help others in delivering useful and effective services.
With the advent of mass data collection and storage has come data mining. Find and
summarise a resource that describes ONE example where data mining has been used
successfully by a business. You should not use any examples covered in the textbook.
Title and Reference:
Amazon – Organization Which Has Successfully Used Big Data.
Harvard References - Berinsky, A.J., Huber, G.A. and Lenz, G.S., 2012. Evaluating online
labor markets for experimental research: Amazon. com's Mechanical Turk. Political
Analysis, 20(3), pp.351-368.
Hashem, I.A.T., Yaqoob, I., Anuar, N.B., Mokhtar, S., Gani, A. and Khan, S.U., 2015. The rise
of “big data” on cloud computing: Review and open research issues. Information Systems, 47,
pp.98-115.
URL - https://www.smartdatacollective.com/lessons-how-amazon-uses-big-data/
Summary:
The resource talks about how data mining has been used effectively by Amazon,
which is a E-Commerce and Cloud Computing Company. Data Mining is nothing but
the practice through which the already existing databases are examined, so as to
generate new information (Berinsky, Huber and Lenz 2012). The resource provides
the details regarding the expertise shown by Amazon by handling big data in an
effective manner over a period of years.
The reason for selecting this resource is that the content available in the article suits
the task and help to fulfil the requirements. The resource emphasizes on the fact how
the global giant has successfully gathered data, analyse and then implement analytics
of those data. Through the extensive analysis of data, the company has only used
them for their own purpose but also helped others in effectively leveraging data and
thereby let them enjoy the benefits (Hashem et al. 2015).
The main points covered in the resource are :
i) Accumulation of big data is not an easy job
ii) A whole lot of expertise and understanding are required on how to use big data in
an effective manner to yield the desired results through extensive analysis.
iii) Amazon, the global giant and leader in technology innovation has used big data in
a very effective manner
The resource was useful because the resource has highlighted the effects of data
mining and how Amazon has accumulated data for serving their own purpose and also
help others in delivering useful and effective services.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week 9
One of the greatest success stories in application development in recent times has been the
popularity of mobile apps. Find and summarise a resource that describes the story of ONE
successful mobile app developer.
Title and Reference
Success Story Of Jan Koum – Founder of WhatsApp
Harvard Reference - Ndedi, A. and Kingsley, K.M., 2017. Understanding How Failing a Job
Interview May Be a Source of Innovation: The Case of WhatsApp Founders. In Managing
Knowledge and Innovation for Business Sustainability in Africa (pp. 83-92). Springer
International Publishing.
Olson, P., 2015. The rags-to-riches tale of how Jan Koum built WhatsApp into Facebook’s
new $19 billion baby.
URL - http://www.rediff.com/money/slide-show/slide-show-1-special-tech-the-amazing-
success-story-of-whatsapps-architect-jan-koum/20140220.htm#1
Summary:
The resource talks about the successful development of the most popular app in this
present generation, WhatsApp which was developed by Jan Koum in the year 2009.
Through this resource, all relevant information regarding how the app got developed
and over time, the way the app has captured everyone’s attention and become a
massive success, has been accumulated (Ndedi and Kingsley 2017).
The reason behind selecting this resource is because, the content is relevant and deals
with information regarding an app, which is a household name for everyone who has
an Android phone with him or her. This resource provides information related to the
founder Jan Koum, who rose above all the rejections he had faced in corporate world
and founded an app, which has done wonders for the world (Olson 2015).
The main points discussed in the resource are :
i) Jan Koum developed WhatsApp in the year 2009 and after they got acquired by
Facebook in 2014, the developer had become a billionaire.
ii) Koum has a stake of 45% in the company
iii) The resource gives an overview of the incredible journey which Koum had gone
through
The usefulness of the resource comes from the fact that all the relevant information
regarding an individual, Jan Koum in this case, is discussed who provides an
incredible success story through the development of most popular app in recent times,
WhatsApp
One of the greatest success stories in application development in recent times has been the
popularity of mobile apps. Find and summarise a resource that describes the story of ONE
successful mobile app developer.
Title and Reference
Success Story Of Jan Koum – Founder of WhatsApp
Harvard Reference - Ndedi, A. and Kingsley, K.M., 2017. Understanding How Failing a Job
Interview May Be a Source of Innovation: The Case of WhatsApp Founders. In Managing
Knowledge and Innovation for Business Sustainability in Africa (pp. 83-92). Springer
International Publishing.
Olson, P., 2015. The rags-to-riches tale of how Jan Koum built WhatsApp into Facebook’s
new $19 billion baby.
URL - http://www.rediff.com/money/slide-show/slide-show-1-special-tech-the-amazing-
success-story-of-whatsapps-architect-jan-koum/20140220.htm#1
Summary:
The resource talks about the successful development of the most popular app in this
present generation, WhatsApp which was developed by Jan Koum in the year 2009.
Through this resource, all relevant information regarding how the app got developed
and over time, the way the app has captured everyone’s attention and become a
massive success, has been accumulated (Ndedi and Kingsley 2017).
The reason behind selecting this resource is because, the content is relevant and deals
with information regarding an app, which is a household name for everyone who has
an Android phone with him or her. This resource provides information related to the
founder Jan Koum, who rose above all the rejections he had faced in corporate world
and founded an app, which has done wonders for the world (Olson 2015).
The main points discussed in the resource are :
i) Jan Koum developed WhatsApp in the year 2009 and after they got acquired by
Facebook in 2014, the developer had become a billionaire.
ii) Koum has a stake of 45% in the company
iii) The resource gives an overview of the incredible journey which Koum had gone
through
The usefulness of the resource comes from the fact that all the relevant information
regarding an individual, Jan Koum in this case, is discussed who provides an
incredible success story through the development of most popular app in recent times,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 10
While information systems and technology deliver many benefits to society, they can also
result in (sometimes inadvertent) negative effects and outcomes. Find and summarise a
resource that describes ONE example of where the use of an information system or
technology has led to negative consequences for humans.
Title and Reference:
Negative Effects Of Technology On Humans
Harvard Reference : Maurino, D.E., Reason, J., Johnston, N. and Lee, R.B., 2017. Beyond
aviation human factors: Safety in high technology systems. Routledge.
Dong, G., Hu, Y., Lin, X. and Lu, Q., 2013. What makes Internet addicts continue playing
online even when faced by severe negative consequences? Possible explanations from an
fMRI study. Biological psychology, 94(2), pp.282-289.
URL : http://myessaypoint.com/negative-effects-of-technology-on-our-lives
Summary:
The resource talks about the adverse effects which technology usage has had on
mankind. Internet is regarded as technology in true sense of the term but on actual
front, internet is just one aspect of the technology that people come across in their
daily walks of life. Everything that is seen in and around people are in some way or
the other bound by technology (Maurino et al. 2017). Technology has surely eased the
lifestyle for people but they have resulted in having adverse effects on mankind. The
impacts have had led to dire consequences for human beings.
The reason behind selecting this resource is that the resource provides all the
information relevant for completing this task in the desired manner. The numerous
side effects of technology portrayed through the resource has emphasized on the fact
that the benefits acquired through usage of technology have been overshadowed by
the negative impacts they have had on people and the environment as a whole (Dong
et al. 2013).
The main points or key information covered in the resource are :
i) Usage of technology has led to the depletion of natural resources, which have come
for a great expense to the environment.
ii) Manufacturing of products in an irresponsible manner has led to the pollution of
air, water , land and filled them up with toxic substances
The resource was useful because all the relevant information regarding the task in
hand has been gathered and used in an appropriate manner.
While information systems and technology deliver many benefits to society, they can also
result in (sometimes inadvertent) negative effects and outcomes. Find and summarise a
resource that describes ONE example of where the use of an information system or
technology has led to negative consequences for humans.
Title and Reference:
Negative Effects Of Technology On Humans
Harvard Reference : Maurino, D.E., Reason, J., Johnston, N. and Lee, R.B., 2017. Beyond
aviation human factors: Safety in high technology systems. Routledge.
Dong, G., Hu, Y., Lin, X. and Lu, Q., 2013. What makes Internet addicts continue playing
online even when faced by severe negative consequences? Possible explanations from an
fMRI study. Biological psychology, 94(2), pp.282-289.
URL : http://myessaypoint.com/negative-effects-of-technology-on-our-lives
Summary:
The resource talks about the adverse effects which technology usage has had on
mankind. Internet is regarded as technology in true sense of the term but on actual
front, internet is just one aspect of the technology that people come across in their
daily walks of life. Everything that is seen in and around people are in some way or
the other bound by technology (Maurino et al. 2017). Technology has surely eased the
lifestyle for people but they have resulted in having adverse effects on mankind. The
impacts have had led to dire consequences for human beings.
The reason behind selecting this resource is that the resource provides all the
information relevant for completing this task in the desired manner. The numerous
side effects of technology portrayed through the resource has emphasized on the fact
that the benefits acquired through usage of technology have been overshadowed by
the negative impacts they have had on people and the environment as a whole (Dong
et al. 2013).
The main points or key information covered in the resource are :
i) Usage of technology has led to the depletion of natural resources, which have come
for a great expense to the environment.
ii) Manufacturing of products in an irresponsible manner has led to the pollution of
air, water , land and filled them up with toxic substances
The resource was useful because all the relevant information regarding the task in
hand has been gathered and used in an appropriate manner.
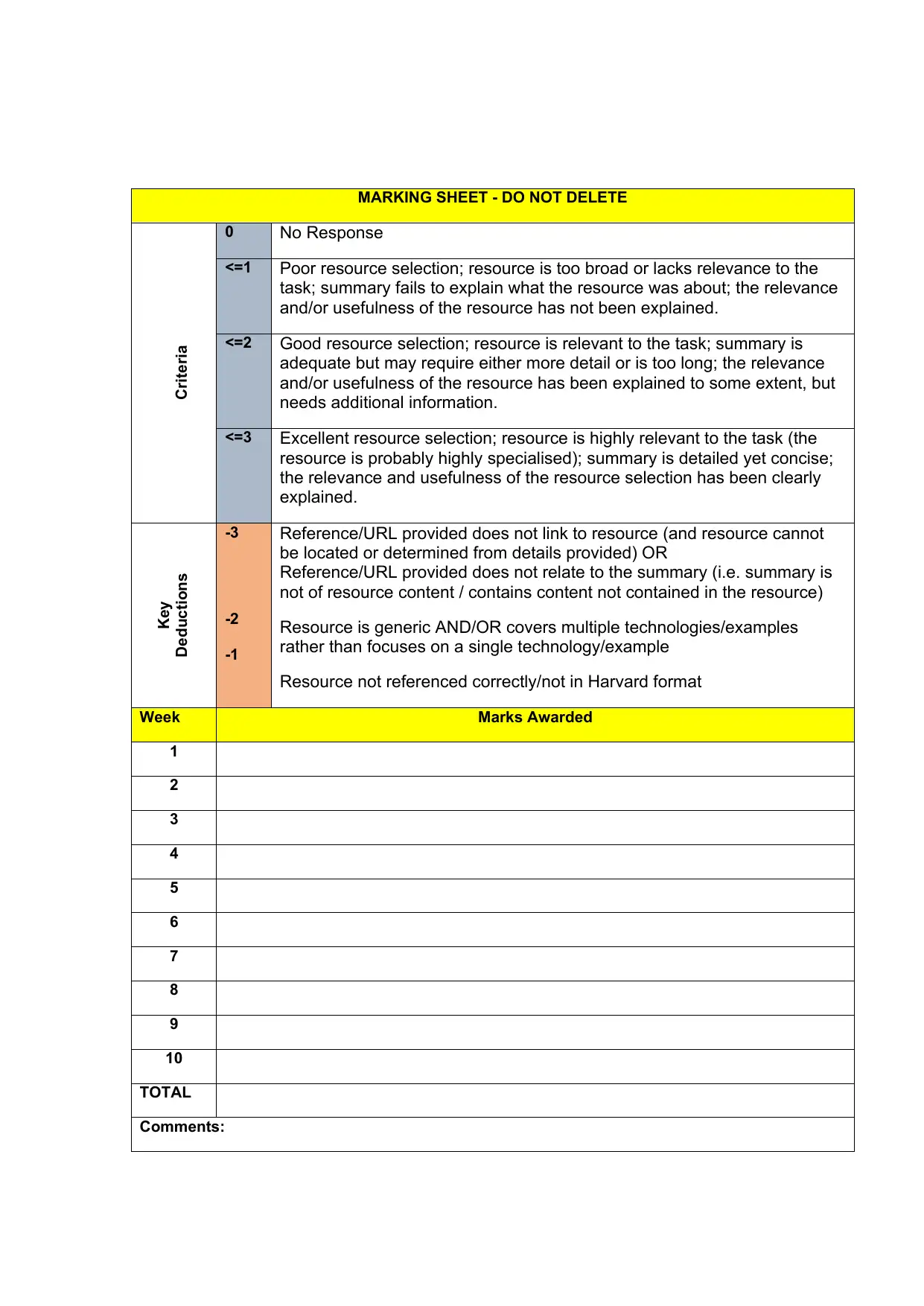
MARKING SHEET - DO NOT DELETE
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





