Managing a Successful Computing Project: Security in Applications
VerifiedAdded on 2024/07/01
|24
|4785
|412
Report
AI Summary
This report details the management of a computing project focused on identifying and addressing security vulnerabilities in computer applications developed by Intellectsoft, a UK-based software development organization. The project aims to ensure confidentiality, integrity, and availability (CIA) of applications by identifying potential threats and implementing sustainable solutions. The report includes a project management plan, outlining cost, scope, time, quality, communication, risk, and resource considerations. It incorporates a work breakdown structure and Gantt chart for effective project execution. The research methodology involves both qualitative data collection from online resources and interviews, and quantitative data collection through questionnaires. Data analysis leads to recommendations for enhancing security, supported by an evaluation of the tools and techniques used. The report concludes with a reflection on the value of the research in meeting project objectives and improving learning and performance. Desklib provides access to this and other solved assignments.

Managing a Successful
Computing Project
1
Computing Project
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
Introduction......................................................................................................................................1
LO1.................................................................................................................................................. 2
P1 Devise project aims and objectives of chosen scenario..........................................................2
P2 Produce a project management plan.......................................................................................3
M1 Comprehensive project management plan............................................................................5
P3 Work break down structure and Gantt chart...........................................................................5
LO2.................................................................................................................................................. 8
P4 Carry out small-scale research by applying qualitative and quantitative research methods. .8
M2. Evaluate the accuracy and reliability of different research methods applied.....................10
LO3................................................................................................................................................ 12
P5 Analyse research and data using appropriate tools and techniques......................................12
P6. Communicate appropriate recommendations as a result of research and data analysis to
draw valid and meaningful conclusions....................................................................................15
M3. Evaluate the selection of appropriate tools and techniques for accuracy and authenticity to
support and justify recommendations........................................................................................ 16
LO4................................................................................................................................................ 17
P7 Reflect on the value of undertaking the research to meet stated objectives and own learning
and performance........................................................................................................................ 17
M4 Evaluate the value of the project management process and use of quality research to meet
stated objectives and support own learning and performance...................................................18
Conclusion..................................................................................................................................... 19
References......................................................................................................................................20
2
Introduction......................................................................................................................................1
LO1.................................................................................................................................................. 2
P1 Devise project aims and objectives of chosen scenario..........................................................2
P2 Produce a project management plan.......................................................................................3
M1 Comprehensive project management plan............................................................................5
P3 Work break down structure and Gantt chart...........................................................................5
LO2.................................................................................................................................................. 8
P4 Carry out small-scale research by applying qualitative and quantitative research methods. .8
M2. Evaluate the accuracy and reliability of different research methods applied.....................10
LO3................................................................................................................................................ 12
P5 Analyse research and data using appropriate tools and techniques......................................12
P6. Communicate appropriate recommendations as a result of research and data analysis to
draw valid and meaningful conclusions....................................................................................15
M3. Evaluate the selection of appropriate tools and techniques for accuracy and authenticity to
support and justify recommendations........................................................................................ 16
LO4................................................................................................................................................ 17
P7 Reflect on the value of undertaking the research to meet stated objectives and own learning
and performance........................................................................................................................ 17
M4 Evaluate the value of the project management process and use of quality research to meet
stated objectives and support own learning and performance...................................................18
Conclusion..................................................................................................................................... 19
References......................................................................................................................................20
2

LIST OF FIGURES
Figure 1: Work Breakdown Structure..............................................................................................6
3
Figure 1: Work Breakdown Structure..............................................................................................6
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

LIST OF TABLES
Table 1: Cost Estimation................................................................................................................. 3
Table 2: Milestone Schedule........................................................................................................... 5
Table 3: Gantt chart.........................................................................................................................6
4
Table 1: Cost Estimation................................................................................................................. 3
Table 2: Milestone Schedule........................................................................................................... 5
Table 3: Gantt chart.........................................................................................................................6
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
Project management involves various processes for entire execution and implementation of
project. The current project is based on understanding and identifying security issues in
development of various computer applications by Intellectsoft which is a software and
application development software organization in UK. The report will focus on establishing
project aims and objectives along with work breakdown structure and Gantt chart. It will conduct
small scale research along with data collection so that appropriate recommendations can be
applied. Last section of the report will focus on importance of project management process as
well as quality research to meet stated objectives.
1
Project management involves various processes for entire execution and implementation of
project. The current project is based on understanding and identifying security issues in
development of various computer applications by Intellectsoft which is a software and
application development software organization in UK. The report will focus on establishing
project aims and objectives along with work breakdown structure and Gantt chart. It will conduct
small scale research along with data collection so that appropriate recommendations can be
applied. Last section of the report will focus on importance of project management process as
well as quality research to meet stated objectives.
1

LO1
P1 Devise project aims and objectives of chosen scenario
Overview of project
Internet enabled devices are helpful in enhancing business activities as well as plays an important
role in supporting routine operations. Intellectsoft operates as a software development
organization in UK and provides development of large number of applications along with
customised software solutions (Rana et.al.2016). The current project is related to protect the
computer applications in terms of security beneficial for both the organization and customers of
the organization. The main objective of the organization is to achieve three major requirements
such as confidentiality, integrity and availability. Therefore it is important to identify the impact
of vulnerabilities on various systems and its utilities. The project will help to identify security
issues as well as threats along with potential solutions that will resolve the issues to greater
extend.
Aim of the project
The project is to meet the expectation of integrity, availability and confidentiality in each and
every application developed by the organization. It also aims to provide better understanding of
potential threats as well as vulnerabilities on various computing systems as well as to take
appropriate measures to minimise the impact of vulnerabilities with the help of sustainable and
stable solutions (Perez and Kumar, 2017). Motive of the project is to execute entire project with
higher quality and performance so that security threats and issues can be eliminated.
Objectives of the project
To identify the importance of computing devices in maintaining the security of computer
applications developed by the organization as well as how CIA information is beneficial
for the organization.
To determine the security vulnerabilities as well as issues as well as how it influence
business relationships and operations
To determine the loss suffered by business while compromising security
2
P1 Devise project aims and objectives of chosen scenario
Overview of project
Internet enabled devices are helpful in enhancing business activities as well as plays an important
role in supporting routine operations. Intellectsoft operates as a software development
organization in UK and provides development of large number of applications along with
customised software solutions (Rana et.al.2016). The current project is related to protect the
computer applications in terms of security beneficial for both the organization and customers of
the organization. The main objective of the organization is to achieve three major requirements
such as confidentiality, integrity and availability. Therefore it is important to identify the impact
of vulnerabilities on various systems and its utilities. The project will help to identify security
issues as well as threats along with potential solutions that will resolve the issues to greater
extend.
Aim of the project
The project is to meet the expectation of integrity, availability and confidentiality in each and
every application developed by the organization. It also aims to provide better understanding of
potential threats as well as vulnerabilities on various computing systems as well as to take
appropriate measures to minimise the impact of vulnerabilities with the help of sustainable and
stable solutions (Perez and Kumar, 2017). Motive of the project is to execute entire project with
higher quality and performance so that security threats and issues can be eliminated.
Objectives of the project
To identify the importance of computing devices in maintaining the security of computer
applications developed by the organization as well as how CIA information is beneficial
for the organization.
To determine the security vulnerabilities as well as issues as well as how it influence
business relationships and operations
To determine the loss suffered by business while compromising security
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
To take measures to monitor and control the performance as well as quality of the project
so that appropriate recommendations can be implemented to enhance security in
Intellectsoft (Mohanty et.al.2018).
P2 Produce a project management plan
Project management plan involves various considerations as well as activities that are to be
considered for achieving goals and objectives in an effective manner. Entire plan focuses on
effective utilisation and allocation of resources as per their capabilities. All the activities in plan
are conducted within business scope and constraints (Kerzner and Kerzner, 2017). Project
management plan plays an important role in entire execution of the project and encourage
communication so that essential information regarding project can be circulated among
stakeholders in a better manner. Major activities in project of ensuring security of computer
applications developed by the organization are explained as:
Cost: Essential requirement of project are hardware and software elements to monitor and
measure the issues of vulnerabilities in computer applications. In addition to this, experts are
hired to identify the issues as well as to find potential solution to minimise the impact of security
issues on computer applications. Overall estimation of cost needed in the project is:
Table 1: Cost Estimation
Costing area Approximate cost
Expertise cost $1000
Software $250
Additional hardware $300
Training and development $600
Change control $250
Documentation $80
Risk handling $150
Contract and agreements $550
Total $3180
3
so that appropriate recommendations can be implemented to enhance security in
Intellectsoft (Mohanty et.al.2018).
P2 Produce a project management plan
Project management plan involves various considerations as well as activities that are to be
considered for achieving goals and objectives in an effective manner. Entire plan focuses on
effective utilisation and allocation of resources as per their capabilities. All the activities in plan
are conducted within business scope and constraints (Kerzner and Kerzner, 2017). Project
management plan plays an important role in entire execution of the project and encourage
communication so that essential information regarding project can be circulated among
stakeholders in a better manner. Major activities in project of ensuring security of computer
applications developed by the organization are explained as:
Cost: Essential requirement of project are hardware and software elements to monitor and
measure the issues of vulnerabilities in computer applications. In addition to this, experts are
hired to identify the issues as well as to find potential solution to minimise the impact of security
issues on computer applications. Overall estimation of cost needed in the project is:
Table 1: Cost Estimation
Costing area Approximate cost
Expertise cost $1000
Software $250
Additional hardware $300
Training and development $600
Change control $250
Documentation $80
Risk handling $150
Contract and agreements $550
Total $3180
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Scope: Entire project and associated activities are to identify the issues in terms of security in
various computing devices. It has higher focus on reviewing logical as well as physical security
issues so that data security can be enhanced. In addition to this, it has scope to meet the risk
associated with project and its impact on business organization involved in development of
computer applications (Marchewka, 2014).
Time: Entire project can be undertaken effectively with completion of all the activities in the
time period of 6 months. Margin of a month is considered for recovering the risk factors as well
as to handle the activities associated with change management. Time is scheduled for conducting
sub activities of the plan so that entire project can be accomplished on time.
Quality: Project is conducted and planned to check the desired level of quality of the project.
Various activities in context to security check of computer applications are merged with various
other activities to get better outcomes. Desires quality in current project is defined in terms of
higher data security with the support of computing resources.
Communication: It is essential step in project execution and appropriate methods of
communication must be adopted to convey information related to project among the people
involved in undertaking various activities of the project. Intellectsoft convey and share
information using telephones and mails along with written reports for depicting the outcomes of
project activities.
Risk: Project planning, controlling, monitoring and execution are a critical task and therefore
risks are associated with time, cost, resources and quality. For effective management of funs and
time, it is essential to utilise resources in an effective manner. Steps must be taken to minimise or
eliminate the risk factors (Heagney, 2016).
Resources: Security threats can be eliminated with the support of skilled resources and experts to
meet organizational objectives. Security controlling and monitoring tools are essential for
improving the performance of networks. In addition to this, hardware and software components
are required to measure the loop holes in the security. Therefore organization must select
appropriate tool for measuring security threats as well as recruitment of skilled human resources
and experts is essential.
4
various computing devices. It has higher focus on reviewing logical as well as physical security
issues so that data security can be enhanced. In addition to this, it has scope to meet the risk
associated with project and its impact on business organization involved in development of
computer applications (Marchewka, 2014).
Time: Entire project can be undertaken effectively with completion of all the activities in the
time period of 6 months. Margin of a month is considered for recovering the risk factors as well
as to handle the activities associated with change management. Time is scheduled for conducting
sub activities of the plan so that entire project can be accomplished on time.
Quality: Project is conducted and planned to check the desired level of quality of the project.
Various activities in context to security check of computer applications are merged with various
other activities to get better outcomes. Desires quality in current project is defined in terms of
higher data security with the support of computing resources.
Communication: It is essential step in project execution and appropriate methods of
communication must be adopted to convey information related to project among the people
involved in undertaking various activities of the project. Intellectsoft convey and share
information using telephones and mails along with written reports for depicting the outcomes of
project activities.
Risk: Project planning, controlling, monitoring and execution are a critical task and therefore
risks are associated with time, cost, resources and quality. For effective management of funs and
time, it is essential to utilise resources in an effective manner. Steps must be taken to minimise or
eliminate the risk factors (Heagney, 2016).
Resources: Security threats can be eliminated with the support of skilled resources and experts to
meet organizational objectives. Security controlling and monitoring tools are essential for
improving the performance of networks. In addition to this, hardware and software components
are required to measure the loop holes in the security. Therefore organization must select
appropriate tool for measuring security threats as well as recruitment of skilled human resources
and experts is essential.
4
M1 Comprehensive project management plan
Project management plan includes scheduling of project as well as development of milestones so
that goals and objectives can be achieved in a better manner (Harrison and Lock, 2017). The
organization can undertake priority along with distribution theory so that resources are utilised in
an effective manner.
Table 2: Milestone Schedule
Activity Milestone
(days)
Progress
Planning 25 Completed
Engineering requirements 20 Completed
Communication for project designing 15 Completed
Potential solutions framework 45 75%
Implementation 15 25%
Testing 15 20%
Post-implementation 10 0%
P3 Work break down structure and Gantt chart
Work break down structure is crucial in defining roles and responsibilities of employees
involved in project development process. It is beneficial in undertaking project activities with
higher performance and quality with the effective co ordination among team members. In
addition to this it is supportive in meeting desired goals and objectives. The main aim of project
management is to achieve time, scope and cost of the project. If the execution and
implementation of project fail to meet there requirements then overall effectiveness of the project
will be hampered.
5
Project management plan includes scheduling of project as well as development of milestones so
that goals and objectives can be achieved in a better manner (Harrison and Lock, 2017). The
organization can undertake priority along with distribution theory so that resources are utilised in
an effective manner.
Table 2: Milestone Schedule
Activity Milestone
(days)
Progress
Planning 25 Completed
Engineering requirements 20 Completed
Communication for project designing 15 Completed
Potential solutions framework 45 75%
Implementation 15 25%
Testing 15 20%
Post-implementation 10 0%
P3 Work break down structure and Gantt chart
Work break down structure is crucial in defining roles and responsibilities of employees
involved in project development process. It is beneficial in undertaking project activities with
higher performance and quality with the effective co ordination among team members. In
addition to this it is supportive in meeting desired goals and objectives. The main aim of project
management is to achieve time, scope and cost of the project. If the execution and
implementation of project fail to meet there requirements then overall effectiveness of the project
will be hampered.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
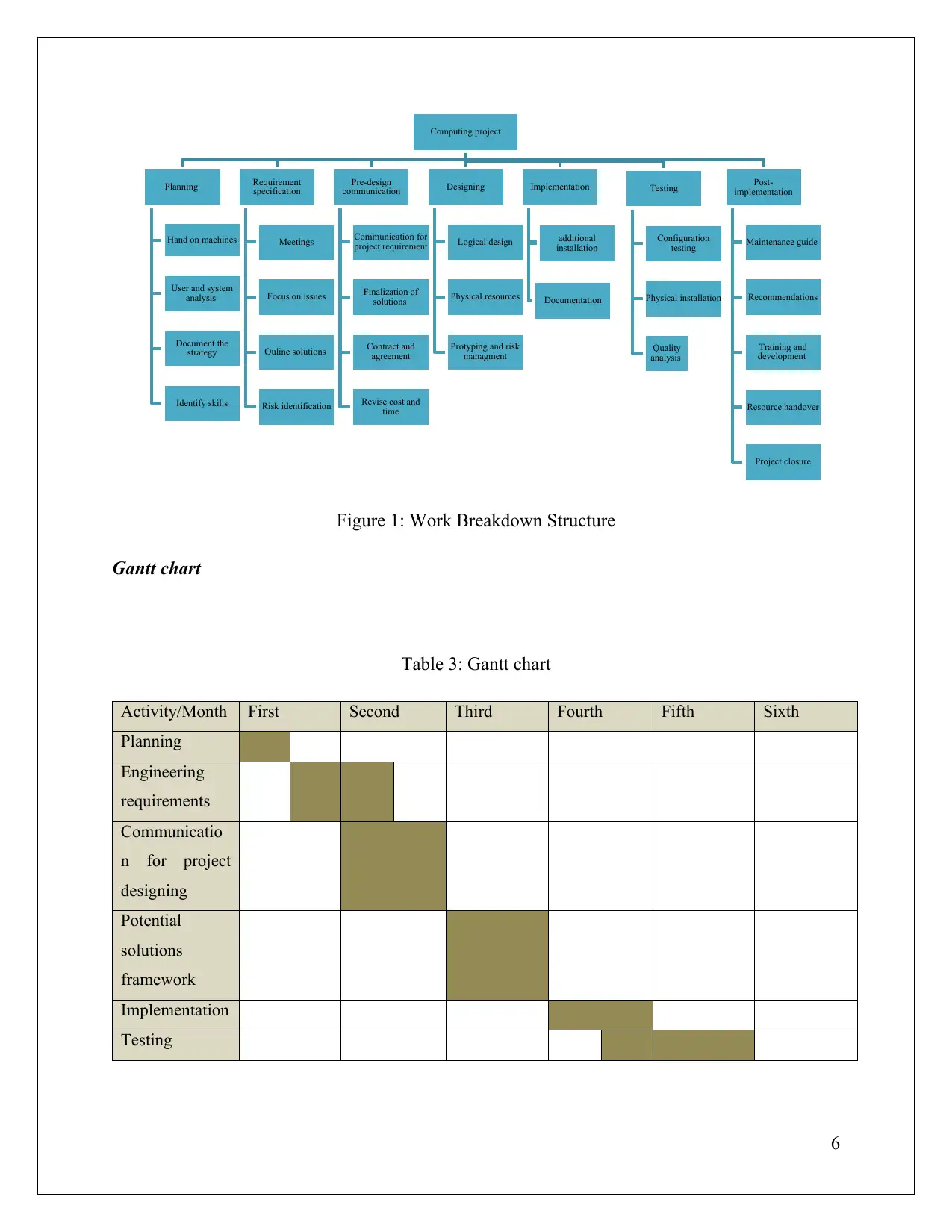
Figure 1: Work Breakdown Structure
Gantt chart
Table 3: Gantt chart
Activity/Month First Second Third Fourth Fifth Sixth
Planning
Engineering
requirements
Communicatio
n for project
designing
Potential
solutions
framework
Implementation
Testing
6
Computing project
Planning
Hand on machines
User and system
analysis
Document the
strategy
Identify skills
Requirement
specification
Meetings
Focus on issues
Ouline solutions
Risk identification
Pre-design
communication
Communication for
project requirement
Finalization of
solutions
Contract and
agreement
Revise cost and
time
Designing
Logical design
Physical resources
Protyping and risk
managment
Implementation
Configuration of
device and software
additional
installation
Documentation
Testing
Configuration
testing
Physical installation
Quality
analysis
Post-
implementation
Maintenance guide
Recommendations
Training and
development
Resource handover
Project closure
Gantt chart
Table 3: Gantt chart
Activity/Month First Second Third Fourth Fifth Sixth
Planning
Engineering
requirements
Communicatio
n for project
designing
Potential
solutions
framework
Implementation
Testing
6
Computing project
Planning
Hand on machines
User and system
analysis
Document the
strategy
Identify skills
Requirement
specification
Meetings
Focus on issues
Ouline solutions
Risk identification
Pre-design
communication
Communication for
project requirement
Finalization of
solutions
Contract and
agreement
Revise cost and
time
Designing
Logical design
Physical resources
Protyping and risk
managment
Implementation
Configuration of
device and software
additional
installation
Documentation
Testing
Configuration
testing
Physical installation
Quality
analysis
Post-
implementation
Maintenance guide
Recommendations
Training and
development
Resource handover
Project closure
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Post-
implementation
7
implementation
7

LO2
P4 Carry out small-scale research by applying qualitative and quantitative research methods
In the current project, both qualitative and quantitative approaches are beneficial in identifying
vulnerabilities and the factors that put negative impact on business activities. Intellectsoft has
higher focus on conducting qualitative research for gathering of information from various
sources such as books, online websites and journals. Research enables to synthesize data in more
appropriate manner (Brannen, 2017). Quantitative Research on other hand is beneficial in
understanding impacts of security issues as well as to find potential solutions to minimise the
issues.
Qualitative research
Internet in current scenario has helped large number of organizations especially in software
development sector in sharing of data with the help of remote connected devices. Users are
highly dependent on various computing devices for higher availability of data and as well as
effective storage but at the same time poor configuration and less effective security is harmful in
revealing of data to various other users in entire network. Development of application with the
support of internet enabled devices has higher threat of increase in securities, vulnerabilities as
well as issues and therefore appropriate steps must be taken to protect the stored data and
information against data breaches (Smith, 2015). It has been identified that such type of data
breaches highly affects the business relationship with partners as well as its brand reputation in
the market. Some of the other factors such as unauthorised accessibility as well as viruses are
because of lack of knowledge of human resources as well as less advanced technology to manage
security of data.
To conduct the Qualitative research, data is collected from online literatures and websites as well
as books, journals and magazines. Interviews are conducted to collect the information in context
to CIA triad of the computer applications from the employees of relevant organization. Below
are some of the questions to identify security issues and threats of computing devices:
1. What is your opinion on security of devices and storage of data in the business?
8
P4 Carry out small-scale research by applying qualitative and quantitative research methods
In the current project, both qualitative and quantitative approaches are beneficial in identifying
vulnerabilities and the factors that put negative impact on business activities. Intellectsoft has
higher focus on conducting qualitative research for gathering of information from various
sources such as books, online websites and journals. Research enables to synthesize data in more
appropriate manner (Brannen, 2017). Quantitative Research on other hand is beneficial in
understanding impacts of security issues as well as to find potential solutions to minimise the
issues.
Qualitative research
Internet in current scenario has helped large number of organizations especially in software
development sector in sharing of data with the help of remote connected devices. Users are
highly dependent on various computing devices for higher availability of data and as well as
effective storage but at the same time poor configuration and less effective security is harmful in
revealing of data to various other users in entire network. Development of application with the
support of internet enabled devices has higher threat of increase in securities, vulnerabilities as
well as issues and therefore appropriate steps must be taken to protect the stored data and
information against data breaches (Smith, 2015). It has been identified that such type of data
breaches highly affects the business relationship with partners as well as its brand reputation in
the market. Some of the other factors such as unauthorised accessibility as well as viruses are
because of lack of knowledge of human resources as well as less advanced technology to manage
security of data.
To conduct the Qualitative research, data is collected from online literatures and websites as well
as books, journals and magazines. Interviews are conducted to collect the information in context
to CIA triad of the computer applications from the employees of relevant organization. Below
are some of the questions to identify security issues and threats of computing devices:
1. What is your opinion on security of devices and storage of data in the business?
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





