OUA SP4 COSC2651 Security in Computing and IT Assignment 2
VerifiedAdded on 2022/08/18
|3
|619
|13
Homework Assignment
AI Summary
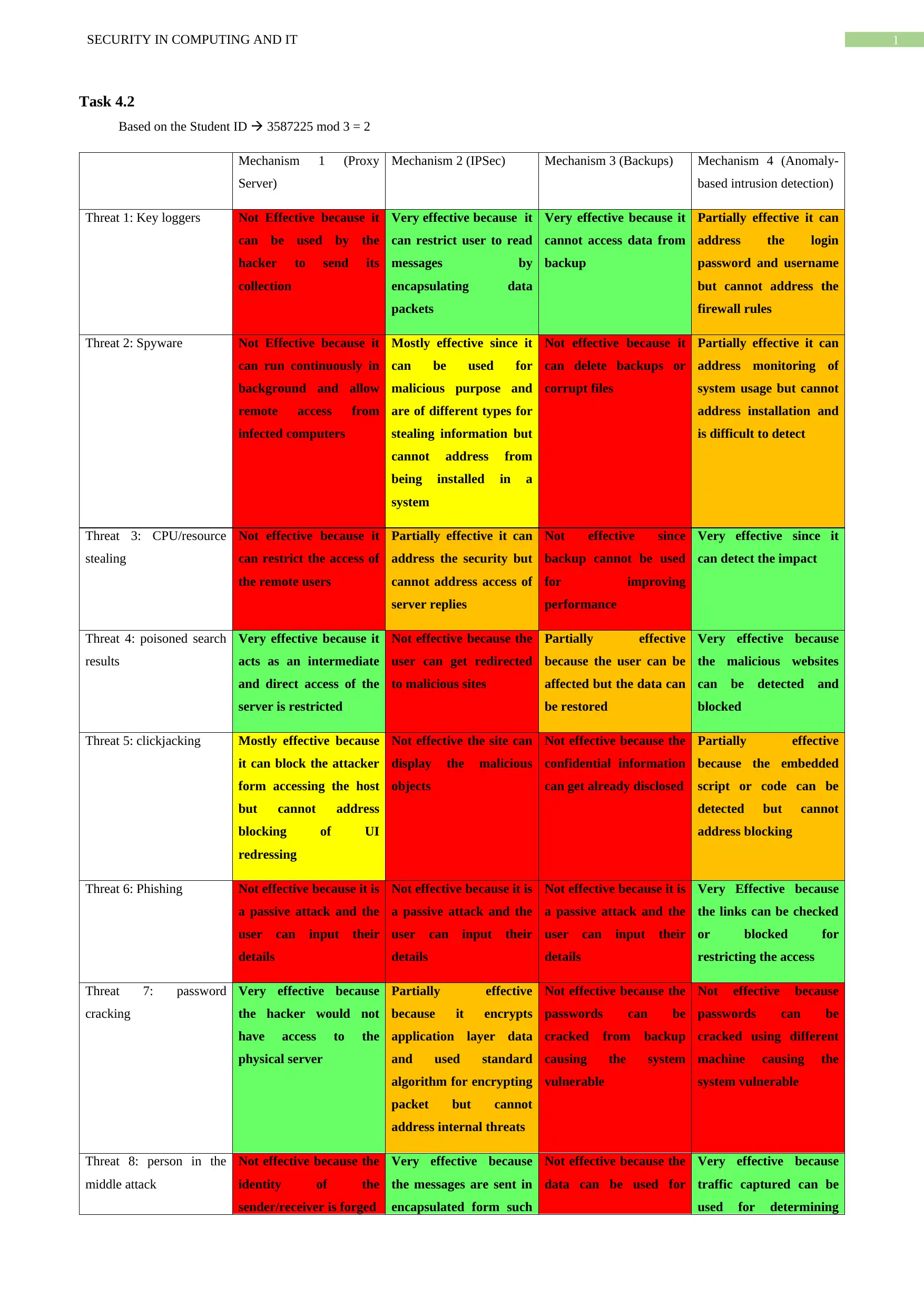
This assignment solution for Security in Computing and IT (COSC2651/CPT251) addresses various aspects of cybersecurity. Task 1 explores techniques for deciphering encrypted messages, including automated and manual approaches, along with estimations of decryption time and methods to enhance or hinder the process. Task 2 analyzes the effectiveness of different security mechanisms (proxy server, IPSec, backups, and anomaly-based intrusion detection) against various threats like key loggers, spyware, CPU/resource stealing, poisoned search results, clickjacking, phishing, password cracking, person-in-the-middle attacks, and ransomware. The analysis evaluates the effectiveness of each mechanism against each threat, providing detailed reasoning. The assignment also includes questions on cryptography, authentication, and security mechanisms.
1 out of 3









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)