Cloud Computing SaaS Model: Confidentiality Analysis for SMEs
VerifiedAdded on 2020/05/04
|42
|11679
|214
Report
AI Summary
This report delves into the confidentiality issues surrounding the Software-as-a-Service (SaaS) model within cloud computing, specifically targeting small businesses. It examines the SaaS paradigm, highlighting its confidentiality challenges across data security, application security, and deployment security. The study investigates changes in reporting data confidentiality issues and identifies factors that compromise data security within small business contexts. The research employs a metadata methodology, drawing from literature reviews, including online journals and articles, to analyze the security threats and provide potential solutions, such as auditing processes, RAID, and security policies, to mitigate these issues. The report includes an introduction, literature review, research contribution, and a concluding summary, providing a detailed analysis of the factors affecting data security and the implications of SaaS adoption for small and medium enterprises (SMEs). The report emphasizes the importance of data confidentiality, integrity, and availability in the SaaS model.

Running head: CLOUD COMPUTING
Cloud Computing
Name of the Student
Name of the University
Author’s Note
Cloud Computing
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CLOUD COMPUTING
Abstract
SaaS model is delivering of web-based applications over internet. The software is being
hosted at the service provider’s site and all the maintenance work is become responsibility of
the providers. The paper is focused on analyzing the confidentiality issues of SaaS model of
the cloud computing into the small businesses. Mainly, this particular paper analyzes the
Software as a Service (SaaS) paradigm and highlighted its confidentiality issues. SaaS is a
cloud model, which is offered into the public, private and hybrid network. Cloud computing
paradigm has both negative and positive effects into the security of the customer’s data. The
services providers are hesitant to combine of the business with SaaS due to its confidentiality
issues while are attracted to their benefits. This paper analyzes the challenges of SaaS across
security of data, security of application as well as deployment security of SaaS. It investigates
significant changes to reporting of confidentiality data issues and finds factors, which
compromise data security over the small business.
Keywords: SaaS model, confidentiality issues, web-based applications, security of data.
CLOUD COMPUTING
Abstract
SaaS model is delivering of web-based applications over internet. The software is being
hosted at the service provider’s site and all the maintenance work is become responsibility of
the providers. The paper is focused on analyzing the confidentiality issues of SaaS model of
the cloud computing into the small businesses. Mainly, this particular paper analyzes the
Software as a Service (SaaS) paradigm and highlighted its confidentiality issues. SaaS is a
cloud model, which is offered into the public, private and hybrid network. Cloud computing
paradigm has both negative and positive effects into the security of the customer’s data. The
services providers are hesitant to combine of the business with SaaS due to its confidentiality
issues while are attracted to their benefits. This paper analyzes the challenges of SaaS across
security of data, security of application as well as deployment security of SaaS. It investigates
significant changes to reporting of confidentiality data issues and finds factors, which
compromise data security over the small business.
Keywords: SaaS model, confidentiality issues, web-based applications, security of data.

2
CLOUD COMPUTING
Table of Contents
Chapter 1: Introduction..............................................................................................................4
1.1 Background.......................................................................................................................4
1.2 Description of Problem.....................................................................................................4
1.3 Scope of the research........................................................................................................6
1.4 Research Objectives.........................................................................................................6
1.5 Research Questions..........................................................................................................6
1.6 Research methodology.....................................................................................................7
1.7 Report Structure................................................................................................................7
Chapter 2: Literature Review.....................................................................................................9
2.1 Introduction......................................................................................................................9
2.2 Security and Information security....................................................................................9
2.3 Concept of Software-as-a-Service (SaaS) Cloud Computing........................................10
2.4 Legal and governmental data confidentiality issues of SaaS model of Cloud computing
in small business...................................................................................................................11
2.5 Data security issues in the SaaS model of cloud computing in the small business........12
2.6 Security Solutions...........................................................................................................15
2.7 Limitation of the review.................................................................................................18
Chapter 3: Research Contribution............................................................................................20
Chapter 4: Summary................................................................................................................31
4.1 Summary.........................................................................................................................31
CLOUD COMPUTING
Table of Contents
Chapter 1: Introduction..............................................................................................................4
1.1 Background.......................................................................................................................4
1.2 Description of Problem.....................................................................................................4
1.3 Scope of the research........................................................................................................6
1.4 Research Objectives.........................................................................................................6
1.5 Research Questions..........................................................................................................6
1.6 Research methodology.....................................................................................................7
1.7 Report Structure................................................................................................................7
Chapter 2: Literature Review.....................................................................................................9
2.1 Introduction......................................................................................................................9
2.2 Security and Information security....................................................................................9
2.3 Concept of Software-as-a-Service (SaaS) Cloud Computing........................................10
2.4 Legal and governmental data confidentiality issues of SaaS model of Cloud computing
in small business...................................................................................................................11
2.5 Data security issues in the SaaS model of cloud computing in the small business........12
2.6 Security Solutions...........................................................................................................15
2.7 Limitation of the review.................................................................................................18
Chapter 3: Research Contribution............................................................................................20
Chapter 4: Summary................................................................................................................31
4.1 Summary.........................................................................................................................31
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CLOUD COMPUTING
4.2 Future Works..................................................................................................................32
References................................................................................................................................33
CLOUD COMPUTING
4.2 Future Works..................................................................................................................32
References................................................................................................................................33
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
CLOUD COMPUTING
Chapter 1: Introduction
1.1 Background
Cloud computing has been in-demand technology by many organization in the market in
the recent years. Cloud Computing has attracted many business organization to avail cloud
services in their business. It is provided various services to the business organization
including low-cost implementation, easy setup and scalability. Adoption of SaaS applications
allowed the business to save the cost of information technology. The SaaS model has no such
physical requirements for indirect allocation since it is not actually distributed and organized
instantly(Almorsy, M; Grundy, J; Muller, I, 2016).The security of the data and information
has been enhanced with the implementation of the cloud computing in the business
organization. Adoption of the SaaS model introduces some confidentiality issues related to
implementation of cloud services. SaaS solutions store the data of the small business such as
documents, billing data, contracts and others on the remote server (Hashizume, Rosado,
Fernández-Medina, & Fernandez, 2013). One of the most important concerns is to protect the
data confidentiality contained into the documents. The data of the business are replaced and
developed by various applications as well as services. The small business company verifies
the confidentiality properties assessing exchanges among workstations and SaaS services to
check if data is protected regarding SSL.
1.2 Description of Problem
The cloud computing and Software-as-a-Service (SaaS) has attracted many small
businesses. There have been many advantages of the SaaS in the small business enterprises.
On the other hand, there have been security issues prevailing in the SaaS model. The
deployment of the cloud services has able to provide various services to the business
organization in the market. The use of the cloud computing has some limitation including the
CLOUD COMPUTING
Chapter 1: Introduction
1.1 Background
Cloud computing has been in-demand technology by many organization in the market in
the recent years. Cloud Computing has attracted many business organization to avail cloud
services in their business. It is provided various services to the business organization
including low-cost implementation, easy setup and scalability. Adoption of SaaS applications
allowed the business to save the cost of information technology. The SaaS model has no such
physical requirements for indirect allocation since it is not actually distributed and organized
instantly(Almorsy, M; Grundy, J; Muller, I, 2016).The security of the data and information
has been enhanced with the implementation of the cloud computing in the business
organization. Adoption of the SaaS model introduces some confidentiality issues related to
implementation of cloud services. SaaS solutions store the data of the small business such as
documents, billing data, contracts and others on the remote server (Hashizume, Rosado,
Fernández-Medina, & Fernandez, 2013). One of the most important concerns is to protect the
data confidentiality contained into the documents. The data of the business are replaced and
developed by various applications as well as services. The small business company verifies
the confidentiality properties assessing exchanges among workstations and SaaS services to
check if data is protected regarding SSL.
1.2 Description of Problem
The cloud computing and Software-as-a-Service (SaaS) has attracted many small
businesses. There have been many advantages of the SaaS in the small business enterprises.
On the other hand, there have been security issues prevailing in the SaaS model. The
deployment of the cloud services has able to provide various services to the business
organization in the market. The use of the cloud computing has some limitation including the
5
CLOUD COMPUTING
threats and risk of the data and information of organization (Burton, 2013). The cloud
computing has able to provide flexibility and on-demand services to the business organization
in the market; therefore, it has created a need in the market for the small enterprises. The
security problems are become critical into cloud computing as new dimensions are entered
into problem scope focused on architecture of SaaS model, layers and elasticity.
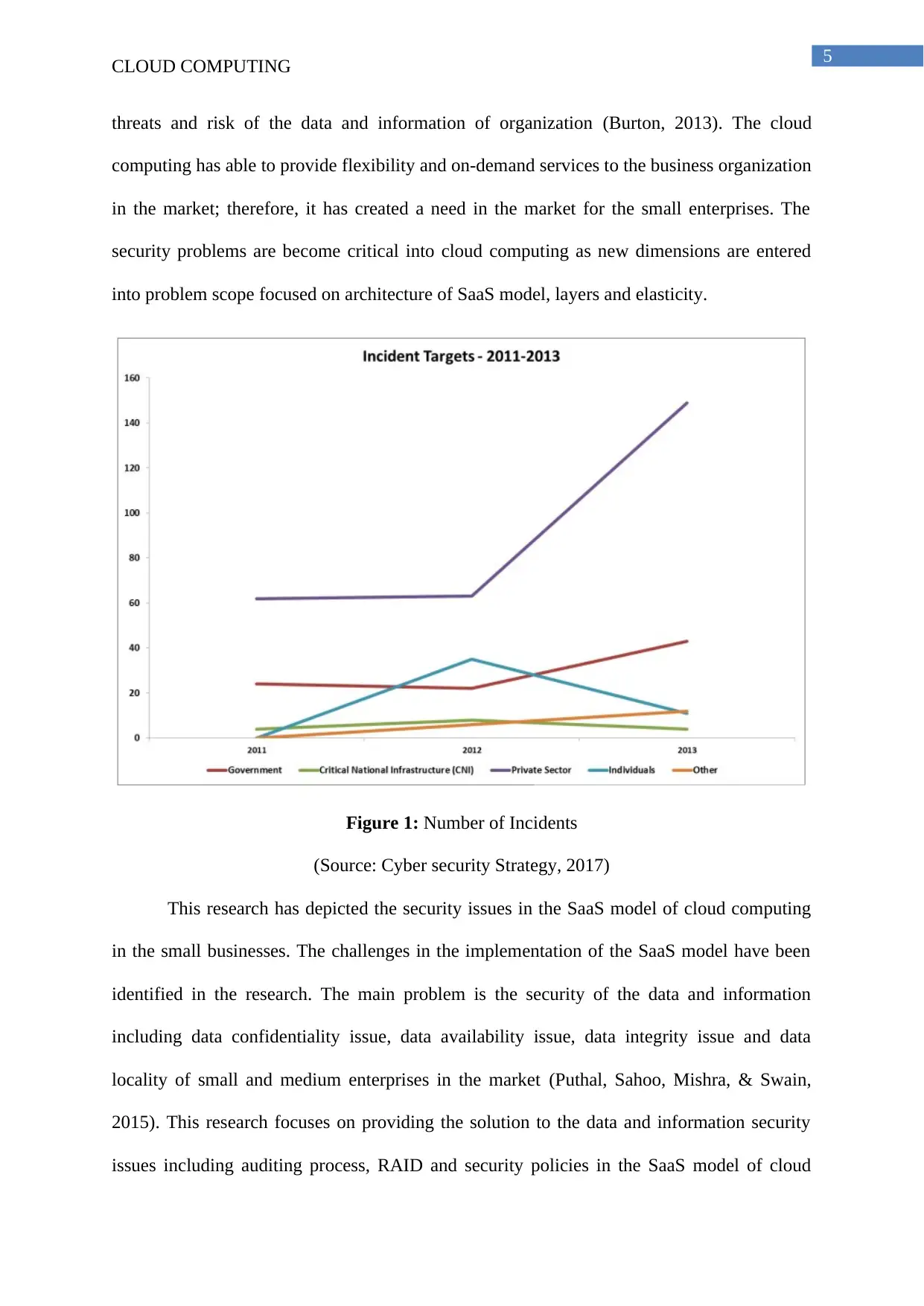
Figure 1: Number of Incidents
(Source: Cyber security Strategy, 2017)
This research has depicted the security issues in the SaaS model of cloud computing
in the small businesses. The challenges in the implementation of the SaaS model have been
identified in the research. The main problem is the security of the data and information
including data confidentiality issue, data availability issue, data integrity issue and data
locality of small and medium enterprises in the market (Puthal, Sahoo, Mishra, & Swain,
2015). This research focuses on providing the solution to the data and information security
issues including auditing process, RAID and security policies in the SaaS model of cloud
CLOUD COMPUTING
threats and risk of the data and information of organization (Burton, 2013). The cloud
computing has able to provide flexibility and on-demand services to the business organization
in the market; therefore, it has created a need in the market for the small enterprises. The
security problems are become critical into cloud computing as new dimensions are entered
into problem scope focused on architecture of SaaS model, layers and elasticity.
Figure 1: Number of Incidents
(Source: Cyber security Strategy, 2017)
This research has depicted the security issues in the SaaS model of cloud computing
in the small businesses. The challenges in the implementation of the SaaS model have been
identified in the research. The main problem is the security of the data and information
including data confidentiality issue, data availability issue, data integrity issue and data
locality of small and medium enterprises in the market (Puthal, Sahoo, Mishra, & Swain,
2015). This research focuses on providing the solution to the data and information security
issues including auditing process, RAID and security policies in the SaaS model of cloud
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CLOUD COMPUTING
computing in small businesses. The security of the data and information has been minimized
with the results and outcomes of the research.
1.3Scope of the research
The scope of the research is to focus on the confidentiality issues in the SaaS model of
cloud computing environment in small business, individual and government agency. It also
mitigates the challenges including data confidentiality issue, data availability issue, data
integrity issue and data locality and faced by the small enterprises. The research also analyzes
the data confidentiality factors which compromises with security of SaaS services into the
cloud computing.
1.4Research Objectives
The security threats have been prevailing in the business organization. The aim of the
research is to identify and mitigate security issues in SaaS model of cloud computing
environment in small enterprises. The objectives of the research have been discussed below:
To investigate if there is a significant change to the reporting of confidentiality data
issues since the introduction of SaaS computing technology
To discover and find the factors which compromise the data security of small
businesses with respect to confidentiality of data while using the SaaS services of
cloud computing
1.5 Research Questions
Following are the research questions:
1. Has there been a change in the type of confidentiality security issues?
2. What are the confidentiality issues among business, individual and government
agency when using SaaS services of cloud computing technology in the small
businesses?
CLOUD COMPUTING
computing in small businesses. The security of the data and information has been minimized
with the results and outcomes of the research.
1.3Scope of the research
The scope of the research is to focus on the confidentiality issues in the SaaS model of
cloud computing environment in small business, individual and government agency. It also
mitigates the challenges including data confidentiality issue, data availability issue, data
integrity issue and data locality and faced by the small enterprises. The research also analyzes
the data confidentiality factors which compromises with security of SaaS services into the
cloud computing.
1.4Research Objectives
The security threats have been prevailing in the business organization. The aim of the
research is to identify and mitigate security issues in SaaS model of cloud computing
environment in small enterprises. The objectives of the research have been discussed below:
To investigate if there is a significant change to the reporting of confidentiality data
issues since the introduction of SaaS computing technology
To discover and find the factors which compromise the data security of small
businesses with respect to confidentiality of data while using the SaaS services of
cloud computing
1.5 Research Questions
Following are the research questions:
1. Has there been a change in the type of confidentiality security issues?
2. What are the confidentiality issues among business, individual and government
agency when using SaaS services of cloud computing technology in the small
businesses?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CLOUD COMPUTING
3. Which of the identified data confidentiality factors compromises the security of SaaS
services in cloud computing, are reported to have a significant impact on small
businesses?
1.6Research methodology
The research has used Metadata methodology and data is collected from literature
review including online journals and articles. Metadata is such a data which provides
information from other data. There are three types of metadata: descriptive, structural and
administrative. In this particular research, descriptive metadata is used for studying the
confidentiality issues ofSaaS model of the cloud-computing environment in the small
businesses. This type of metadata described the resources for purpose like discovery and
observation. It takes information from the peer reviewed journal article’s abstract and
keywords. Each of the service providers tune metadata of the application to offer with
customized observation. Metadata management is the basis of the security platform. The
information is achieved by the users with wide range of configurations and features which are
stored into the form of metadata.
1.7Report Structure
This report comprises of four chapters including Introduction, Literature review,
Research Contribution, and Summary. The first chapter deals with the introduction of the
research topic. It comprises of Background, scope, Research objectives, methodology and
report structure. The research topic has been clearly described in the background of the
research. The research aim, objectives and questions are mentioned in the first chapter. The
overview of the research methodology has been provided in the chapter.
The second chapter is Literature review. This chapter critically discusses the concept
of the research topic and SaaS model in Cloud Computing environment. The impact of the
CLOUD COMPUTING
3. Which of the identified data confidentiality factors compromises the security of SaaS
services in cloud computing, are reported to have a significant impact on small
businesses?
1.6Research methodology
The research has used Metadata methodology and data is collected from literature
review including online journals and articles. Metadata is such a data which provides
information from other data. There are three types of metadata: descriptive, structural and
administrative. In this particular research, descriptive metadata is used for studying the
confidentiality issues ofSaaS model of the cloud-computing environment in the small
businesses. This type of metadata described the resources for purpose like discovery and
observation. It takes information from the peer reviewed journal article’s abstract and
keywords. Each of the service providers tune metadata of the application to offer with
customized observation. Metadata management is the basis of the security platform. The
information is achieved by the users with wide range of configurations and features which are
stored into the form of metadata.
1.7Report Structure
This report comprises of four chapters including Introduction, Literature review,
Research Contribution, and Summary. The first chapter deals with the introduction of the
research topic. It comprises of Background, scope, Research objectives, methodology and
report structure. The research topic has been clearly described in the background of the
research. The research aim, objectives and questions are mentioned in the first chapter. The
overview of the research methodology has been provided in the chapter.
The second chapter is Literature review. This chapter critically discusses the concept
of the research topic and SaaS model in Cloud Computing environment. The impact of the

8
CLOUD COMPUTING
security threats in the SaaS model of cloud computing environment has been identified in the
chapter. There are various factors that are affecting the Small businesses are discussed in
literature review. Different theories and models are discussed in the chapter related to the
cloud computing. A proper narrative literature review of the research topic has been provided
in the chapter.
The third chapter deals with the research contribution. A proper analysis of the
literature review has been discussed in this chapter the collection of data and information has
been done in this chapter. The chapter discusses the various sources of the data collection and
its analysis. The analysis of the literature review is done for fulfilling the goal and objectives
of the research. The research has been successfully fulfilled with the help of proper analysis.
The last chapter is the summary of the research. This chapter provides the summary of all the
findings and analysis that has been done in the research. A proper conclusion if the research
has been provided with detailed information. The objectives of the research have been
successfully satisfied that depicts successful completion of the study.
CLOUD COMPUTING
security threats in the SaaS model of cloud computing environment has been identified in the
chapter. There are various factors that are affecting the Small businesses are discussed in
literature review. Different theories and models are discussed in the chapter related to the
cloud computing. A proper narrative literature review of the research topic has been provided
in the chapter.
The third chapter deals with the research contribution. A proper analysis of the
literature review has been discussed in this chapter the collection of data and information has
been done in this chapter. The chapter discusses the various sources of the data collection and
its analysis. The analysis of the literature review is done for fulfilling the goal and objectives
of the research. The research has been successfully fulfilled with the help of proper analysis.
The last chapter is the summary of the research. This chapter provides the summary of all the
findings and analysis that has been done in the research. A proper conclusion if the research
has been provided with detailed information. The objectives of the research have been
successfully satisfied that depicts successful completion of the study.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CLOUD COMPUTING
Chapter 2: Literature Review
2.1 Introduction
SaaS is a component into the architecture of cloud computing. The application is
offered directly by the service provider that bundles of SaaS offerings from unified
application program. SaaS models create an efficient software delivery mechanism for the IT
departments to deploy and support of applications for managing services that SaaS
application provides.Confidentiality is defined as prevention from the unauthorized
disclosure of the data and information.The confidentiality areas into the cloud computing
includes of intellectual property rights, encryption as well as interference.There are various
theories and models of the cloud computing has been explained in this chapter. The use of the
cloud computing in the business organization is to be depicted in this chapter. The literature
review of the research topic provides clear and concise information about the research topic.
2.2 Security and Information privacy
The security of the information and data is an important element in the business
organization. The data security over the internet has been a critical element in the world.
Different business organization is suffering from the risk in a security of the data and
information over the internet. Guaranteeing the classification, respectability and accessibility,
otherwise called the CIA triangle, has been viewed as the business standard for a long while
now (Abbas, Farooq, & Afghan, 2015).
While these attributes stay of most extreme significance, the fast improvement
encompassing the IT segment implies this definition must be extended keeping in mind end
goal to epitomize the new security circumstance. (Singh & Chatterjee, 2017)reported that
data and correspondence innovation (ICT) can seemingly be viewed as subcomponent of data
security since data security incorporates insurance of hidden assets.
CLOUD COMPUTING
Chapter 2: Literature Review
2.1 Introduction
SaaS is a component into the architecture of cloud computing. The application is
offered directly by the service provider that bundles of SaaS offerings from unified
application program. SaaS models create an efficient software delivery mechanism for the IT
departments to deploy and support of applications for managing services that SaaS
application provides.Confidentiality is defined as prevention from the unauthorized
disclosure of the data and information.The confidentiality areas into the cloud computing
includes of intellectual property rights, encryption as well as interference.There are various
theories and models of the cloud computing has been explained in this chapter. The use of the
cloud computing in the business organization is to be depicted in this chapter. The literature
review of the research topic provides clear and concise information about the research topic.
2.2 Security and Information privacy
The security of the information and data is an important element in the business
organization. The data security over the internet has been a critical element in the world.
Different business organization is suffering from the risk in a security of the data and
information over the internet. Guaranteeing the classification, respectability and accessibility,
otherwise called the CIA triangle, has been viewed as the business standard for a long while
now (Abbas, Farooq, & Afghan, 2015).
While these attributes stay of most extreme significance, the fast improvement
encompassing the IT segment implies this definition must be extended keeping in mind end
goal to epitomize the new security circumstance. (Singh & Chatterjee, 2017)reported that
data and correspondence innovation (ICT) can seemingly be viewed as subcomponent of data
security since data security incorporates insurance of hidden assets.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
CLOUD COMPUTING
2.3 Concept of Software-as-a-Service (SaaS) Cloud Computing
Different companies are not able to afford costly software that is available in the
market. Therefore, they are not able to use attest technology in the market. The cloud
computing has helped in availing this costly software on a rent. This allows Small businesses
to afford this software and grows in the market (Shahzad & Hussain, 2013). The conventional
model of software appropriation, in which software is bought for and introduced on PCs, is in
some cases alluded to as Software-as-a-Product. Software-as-a-Service is a software
appropriation demonstrate in which applications are facilitated by a merchant or, on the other
hand specialist co-op and influenced accessible to clients over a system, ordinarily Internet
(Burns, Posey, Courtney, Roberts, & Nanayakkara, 2017). SaaS is turning into an undeniably
predominant conveyance demonstrate as fundamental innovations, that help web
administrations, benefit arranged design (SOA) develop and new formative methodologies
end up noticeably well known (Lin & Liao, 2017).
SaaS is frequently connected with a compensation subscription-licensing model.
Meanwhile, a broadband benefit has turned out to be progressively accessible to help client
access from more ranges everywhere. The cloud computing is a model that helps in enabling
ubiquitous and on-demand network access for a pool of computing resources. This also helps
in providing fast and efficient services with minimal managing effort and service provider
interaction. As commented by (Rittinghouse & Ransome, 2016), cloud computing was able to
provide different advantages to the business organization and other customers in the market.
The use of the cloud computing has minimized the service effort in the market. The cloud
computing provides efficiency and flexibility to the computing resources. It aimed at
providing maximum services at minimal cost (Burton, 2013) .
.
CLOUD COMPUTING
2.3 Concept of Software-as-a-Service (SaaS) Cloud Computing
Different companies are not able to afford costly software that is available in the
market. Therefore, they are not able to use attest technology in the market. The cloud
computing has helped in availing this costly software on a rent. This allows Small businesses
to afford this software and grows in the market (Shahzad & Hussain, 2013). The conventional
model of software appropriation, in which software is bought for and introduced on PCs, is in
some cases alluded to as Software-as-a-Product. Software-as-a-Service is a software
appropriation demonstrate in which applications are facilitated by a merchant or, on the other
hand specialist co-op and influenced accessible to clients over a system, ordinarily Internet
(Burns, Posey, Courtney, Roberts, & Nanayakkara, 2017). SaaS is turning into an undeniably
predominant conveyance demonstrate as fundamental innovations, that help web
administrations, benefit arranged design (SOA) develop and new formative methodologies
end up noticeably well known (Lin & Liao, 2017).
SaaS is frequently connected with a compensation subscription-licensing model.
Meanwhile, a broadband benefit has turned out to be progressively accessible to help client
access from more ranges everywhere. The cloud computing is a model that helps in enabling
ubiquitous and on-demand network access for a pool of computing resources. This also helps
in providing fast and efficient services with minimal managing effort and service provider
interaction. As commented by (Rittinghouse & Ransome, 2016), cloud computing was able to
provide different advantages to the business organization and other customers in the market.
The use of the cloud computing has minimized the service effort in the market. The cloud
computing provides efficiency and flexibility to the computing resources. It aimed at
providing maximum services at minimal cost (Burton, 2013) .
.

11
CLOUD COMPUTING
On the other hand, (Albaroodi, Manickam, & Singh, 2014) argued that there are
various security challenges of the SaaS model. Data of the customers are important assets for
the users, which are required to keep secure. SaaS consumers are not aware of keeping strong
access system to prevent any unauthorized access. The transmission channel among the
service provider as well as users is not consideredsecure. Some of the service providers are
used of SSL during their login session. Proper data backup are taken to minimize impact of
any security challenges.
2.4Legal and governmental data confidentiality issues of SaaS model of Cloud
computing in small business
Government has legal authority for the organization to turn their own technology
against the customers in the market. There needs to be no disruption in use of the SaaS model
in the company. Some of the relevant cyber laws have been working for protecting the
information of the small business organization in the market. The expectation of the
confidentiality of the data and information of the small business organization has been an
important part of the laws. The legal consideration of the data confidentiality has been prior
to the internet users of small businesses. The data and information of the government have
been breached from the companies. Cybersecurity is a risk that should be mainstreamed for
business. Technical specialists need to speak to business leaders in ways that can be
understood attacks (Ramachandra, Iftikhar, & Khan, 2017). Governments need to think how
they can mobilize their societies; how they can orient them to take collective action to protect
themselves. It requires sustained senior-level political attention. In addition, it is the same for
companies it requires the attention of the c-suite.
The Government needs to build up a National Cyber security Centre inside the
Government Communications security Bureau (Cyber security Strategy, 2017).The National
Cyber security Centre will expand on existing digital security and data affirmation abilities to
CLOUD COMPUTING
On the other hand, (Albaroodi, Manickam, & Singh, 2014) argued that there are
various security challenges of the SaaS model. Data of the customers are important assets for
the users, which are required to keep secure. SaaS consumers are not aware of keeping strong
access system to prevent any unauthorized access. The transmission channel among the
service provider as well as users is not consideredsecure. Some of the service providers are
used of SSL during their login session. Proper data backup are taken to minimize impact of
any security challenges.
2.4Legal and governmental data confidentiality issues of SaaS model of Cloud
computing in small business
Government has legal authority for the organization to turn their own technology
against the customers in the market. There needs to be no disruption in use of the SaaS model
in the company. Some of the relevant cyber laws have been working for protecting the
information of the small business organization in the market. The expectation of the
confidentiality of the data and information of the small business organization has been an
important part of the laws. The legal consideration of the data confidentiality has been prior
to the internet users of small businesses. The data and information of the government have
been breached from the companies. Cybersecurity is a risk that should be mainstreamed for
business. Technical specialists need to speak to business leaders in ways that can be
understood attacks (Ramachandra, Iftikhar, & Khan, 2017). Governments need to think how
they can mobilize their societies; how they can orient them to take collective action to protect
themselves. It requires sustained senior-level political attention. In addition, it is the same for
companies it requires the attention of the c-suite.
The Government needs to build up a National Cyber security Centre inside the
Government Communications security Bureau (Cyber security Strategy, 2017).The National
Cyber security Centre will expand on existing digital security and data affirmation abilities to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 42
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




