MN506 System Management: Design, Installation, Configure Servers
VerifiedAdded on 2023/04/25
|16
|2573
|75
Report
AI Summary
This report outlines the development of a local area network (LAN) to support a Windows Server and Client environment, focusing on centralized authentication, print server configuration, and DHCP address pool management. The solution includes configuring services such as AD RMS, print services, DHCP, IIS for web hosting, and file server management. AAA service is enabled for centralized user authentication, and role-based access control is implemented using group policies. The configuration process involves setting up a prototype network, configuring RADIUS and TACACS+ for security, and enabling IIS components for web services. The report also details the use of file system ACLs and the Server Resource Manager for file access management. Demonstrations of the network solution are provided through screenshots, highlighting network device configurations and service implementations. The report concludes with a discussion of the feasibility study conducted to identify necessary roles and services for meeting the organization's business needs.

Running head: SYSTEM MANAGEMENT
Design, Installation and Configure Enterprise Network Servers
Name of the Student
Name of the University
Author’s Note
Design, Installation and Configure Enterprise Network Servers
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
SYSTEM MANAGEMENT
Table of Contents
Introduction.................................................................................................................................................2
Requirement analysis and identification of server roles & technologies.....................................................2
Configuration process description...............................................................................................................3
Configuration screenshots or commands....................................................................................................4
Summary...................................................................................................................................................12
Demonstrations.........................................................................................................................................12
Conclusions................................................................................................................................................14
Bibliography...............................................................................................................................................15
SYSTEM MANAGEMENT
Table of Contents
Introduction.................................................................................................................................................2
Requirement analysis and identification of server roles & technologies.....................................................2
Configuration process description...............................................................................................................3
Configuration screenshots or commands....................................................................................................4
Summary...................................................................................................................................................12
Demonstrations.........................................................................................................................................12
Conclusions................................................................................................................................................14
Bibliography...............................................................................................................................................15

2
SYSTEM MANAGEMENT
Introduction
For the development of the report the first scenario of development of a local area network
(LAN) to support Windows Server and Client Environment is selected. Here the organization has a
requirement to develop a centralized authentication system and print server configuration such that the
users connected in the local area network can use the network printer for the management of their
printing jobs. The server is also needed to be configured with DHCP address pool according the number
of department and VLANs created for subnetting the network. There are some other serveries that are
needed to be configured for increasing the efficiency of the users and workplace environment. For the
configuration of the network for People Software a research is done on their requirement and Windows
Server 2012 R2 is used for its configuration.
The report is prepared with the documentation of the details of requirement identified for the
development of the Local area network solution. The process need to be followed for the development
of the network is described in the report along with screenshots and commands. A summary of the
steps followed for the configuration is attached with the report and a prototype of the network is
configured for its demonstration and understanding its implementation in the real scenario.
Requirement analysis and identification of server roles &
technologies
The requirement of the development of local area network is needed to be identified for
development of a user centric design for the network solution. The users of the local area network
should be involved in the design and configuration of the network for identifying their needs and service
essential for the configuration of the server. The identification of the roles and technology is important
for gathering requirement for the configuration of the servers and deploy in the organizational network
for meeting the needs of the users. The user should be divided into multiple groups according to their
requirement to access the server resources and active directory should be configured for management
of the access of the users. An Ip address plan should be developed such that it can be followed for the
configuration to the DHCP service and allocate the IP address to the host connected in the local area
network. The LAN is developed following a client server architecture and a powerful server is needed to
be used for serving as a file server, print server and management of the centralized authentication. The
server is also needed to be configured with AAA for enabling centralized user authentication for keeping
the logs of the user and management of the resources. Decision is needed to be taken for the allocation
SYSTEM MANAGEMENT
Introduction
For the development of the report the first scenario of development of a local area network
(LAN) to support Windows Server and Client Environment is selected. Here the organization has a
requirement to develop a centralized authentication system and print server configuration such that the
users connected in the local area network can use the network printer for the management of their
printing jobs. The server is also needed to be configured with DHCP address pool according the number
of department and VLANs created for subnetting the network. There are some other serveries that are
needed to be configured for increasing the efficiency of the users and workplace environment. For the
configuration of the network for People Software a research is done on their requirement and Windows
Server 2012 R2 is used for its configuration.
The report is prepared with the documentation of the details of requirement identified for the
development of the Local area network solution. The process need to be followed for the development
of the network is described in the report along with screenshots and commands. A summary of the
steps followed for the configuration is attached with the report and a prototype of the network is
configured for its demonstration and understanding its implementation in the real scenario.
Requirement analysis and identification of server roles &
technologies
The requirement of the development of local area network is needed to be identified for
development of a user centric design for the network solution. The users of the local area network
should be involved in the design and configuration of the network for identifying their needs and service
essential for the configuration of the server. The identification of the roles and technology is important
for gathering requirement for the configuration of the servers and deploy in the organizational network
for meeting the needs of the users. The user should be divided into multiple groups according to their
requirement to access the server resources and active directory should be configured for management
of the access of the users. An Ip address plan should be developed such that it can be followed for the
configuration to the DHCP service and allocate the IP address to the host connected in the local area
network. The LAN is developed following a client server architecture and a powerful server is needed to
be used for serving as a file server, print server and management of the centralized authentication. The
server is also needed to be configured with AAA for enabling centralized user authentication for keeping
the logs of the user and management of the resources. Decision is needed to be taken for the allocation
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
SYSTEM MANAGEMENT
of different service and roles to the specific users and the users should be interviewed for identifying the
requirement and configure the server according to their needs.
The following are the identified services and rules that should be used for the configuration of
the network and given below:
AD RMS (Active Directory Rights Management Service)
Print service for sharing the printer that is connected with the local area network
DHCP for automatic allocation of IP address to the host connected in the local area network
Configuring the server with IIS service for configuring the server to host website
Configuring file server and management of the access to the user following group policy created
for the management of the access of users
Configuration process description
There are different authentication method such as centralized or distributed authentication
mechanism that can eb deployed for increasing the security of the network. Since the network of People
software is located in a single location a centralized authentication would be more suitable for it. The
server is needed to be configured with AAA service and a role based access control I needed to be
configured for granting permission to the users to use the resource. The system administrator is
responsible to create group policy and exclude the specific group of members to access the internal
resources of the organization. The servers can also be configured with access control list and firewall
configuration should be followed for restricting the user to access the files.
A range of Ip address should be excluded from the DHCP scope while configuring the pool for
configuring the servers with static IP address and eliminating the risk of DHCP conflict. A prototype of
the network is needed to be configured in a network simulating tool and a role based access control
should be used for granting permission for using the resources. The system administrator should be
flexible for grouping the people following the organizational framework. The RADIUS protocol should be
implemented for allowing the user to grant resources for example sharing of files and printers. It can
also be used for configuring the server for accessing different networks such as VPN, local and wireless
access. TACACS+ configuration should be used for increasing the security and accessing different types
of network devices such as routers, firewalls for enabling device administration.
IIS components on windows server is needed to be enabled from the server manager for
configuring the server with WEB service. During adding roles and features different components are
SYSTEM MANAGEMENT
of different service and roles to the specific users and the users should be interviewed for identifying the
requirement and configure the server according to their needs.
The following are the identified services and rules that should be used for the configuration of
the network and given below:
AD RMS (Active Directory Rights Management Service)
Print service for sharing the printer that is connected with the local area network
DHCP for automatic allocation of IP address to the host connected in the local area network
Configuring the server with IIS service for configuring the server to host website
Configuring file server and management of the access to the user following group policy created
for the management of the access of users
Configuration process description
There are different authentication method such as centralized or distributed authentication
mechanism that can eb deployed for increasing the security of the network. Since the network of People
software is located in a single location a centralized authentication would be more suitable for it. The
server is needed to be configured with AAA service and a role based access control I needed to be
configured for granting permission to the users to use the resource. The system administrator is
responsible to create group policy and exclude the specific group of members to access the internal
resources of the organization. The servers can also be configured with access control list and firewall
configuration should be followed for restricting the user to access the files.
A range of Ip address should be excluded from the DHCP scope while configuring the pool for
configuring the servers with static IP address and eliminating the risk of DHCP conflict. A prototype of
the network is needed to be configured in a network simulating tool and a role based access control
should be used for granting permission for using the resources. The system administrator should be
flexible for grouping the people following the organizational framework. The RADIUS protocol should be
implemented for allowing the user to grant resources for example sharing of files and printers. It can
also be used for configuring the server for accessing different networks such as VPN, local and wireless
access. TACACS+ configuration should be used for increasing the security and accessing different types
of network devices such as routers, firewalls for enabling device administration.
IIS components on windows server is needed to be enabled from the server manager for
configuring the server with WEB service. During adding roles and features different components are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
SYSTEM MANAGEMENT
needed to be enabled such as the common HTTP features, security, application development,
management tools. For the configuration of the WEB server ASP .NET can be used and the files should
be pasted in the WEB folder for running the site. The internal website if developed in PHP platform the
root is needed to be configured for enabling the PHP cgi module and handler mapping for running the
web pages.
For enabling the company to store the files on a separate file server and allowing only users with
appropriate access to access the files residing on the server the primary server is needed to be
configured with access control list. File system ACLs should be implemented and policies should be
created for management of the access of the user to reach the file server. Discretionary access control
should be applied where the owner of the file puts the access regulation for the group of users for
whom the file is created. The file server should be configured from the server resource manager for the
management of files and information residing on the server. Different services such as SMTP and FTP
services should be enabled and the activity should be evaluated for identification of usage pattern and
generating reports.
Configuration screenshots or commands
The following screenshot provides the details of configuration of AA service in the server connected in
the local area network of ” People Software”.
SYSTEM MANAGEMENT
needed to be enabled such as the common HTTP features, security, application development,
management tools. For the configuration of the WEB server ASP .NET can be used and the files should
be pasted in the WEB folder for running the site. The internal website if developed in PHP platform the
root is needed to be configured for enabling the PHP cgi module and handler mapping for running the
web pages.
For enabling the company to store the files on a separate file server and allowing only users with
appropriate access to access the files residing on the server the primary server is needed to be
configured with access control list. File system ACLs should be implemented and policies should be
created for management of the access of the user to reach the file server. Discretionary access control
should be applied where the owner of the file puts the access regulation for the group of users for
whom the file is created. The file server should be configured from the server resource manager for the
management of files and information residing on the server. Different services such as SMTP and FTP
services should be enabled and the activity should be evaluated for identification of usage pattern and
generating reports.
Configuration screenshots or commands
The following screenshot provides the details of configuration of AA service in the server connected in
the local area network of ” People Software”.
5
SYSTEM MANAGEMENT
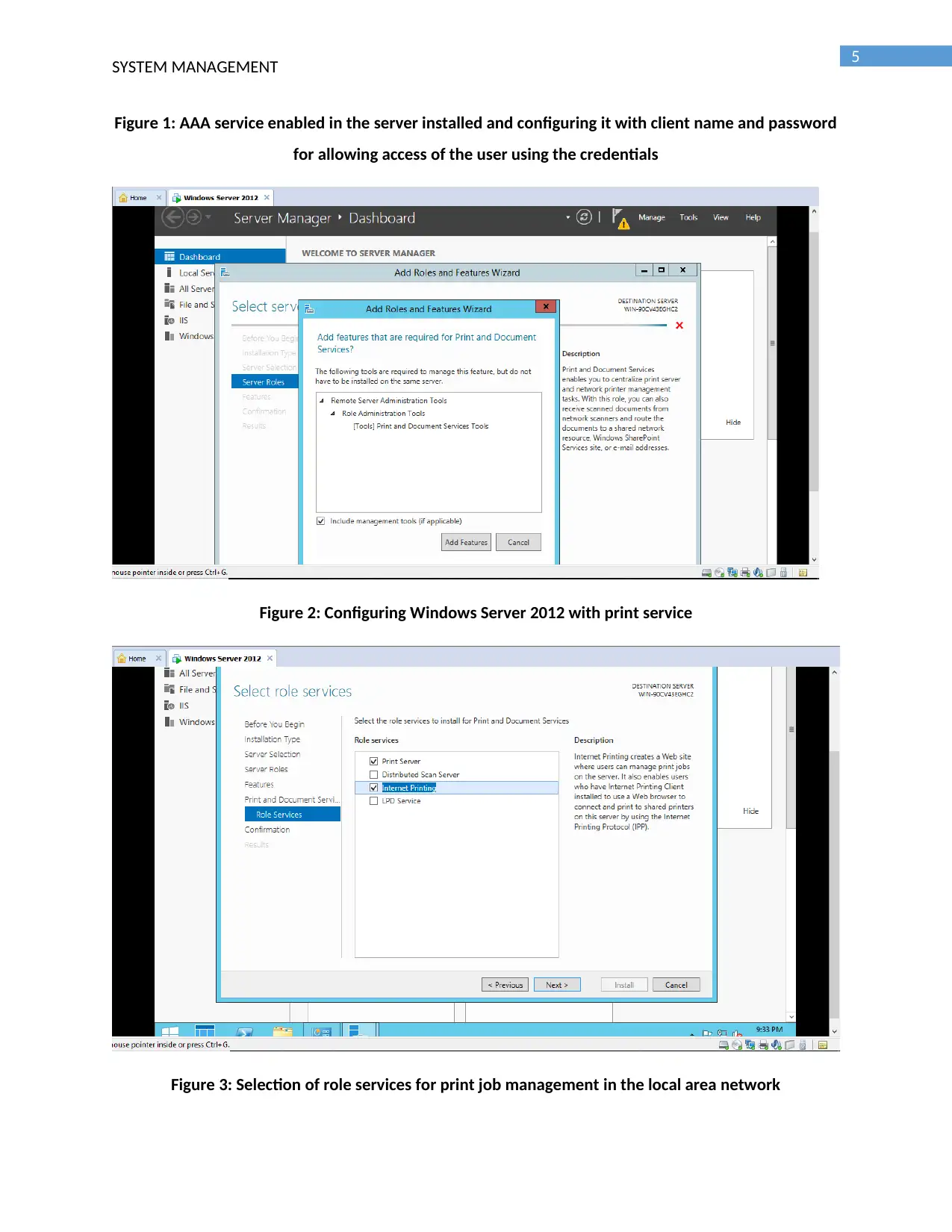
Figure 1: AAA service enabled in the server installed and configuring it with client name and password
for allowing access of the user using the credentials
Figure 2: Configuring Windows Server 2012 with print service
Figure 3: Selection of role services for print job management in the local area network
SYSTEM MANAGEMENT
Figure 1: AAA service enabled in the server installed and configuring it with client name and password
for allowing access of the user using the credentials
Figure 2: Configuring Windows Server 2012 with print service
Figure 3: Selection of role services for print job management in the local area network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
SYSTEM MANAGEMENT
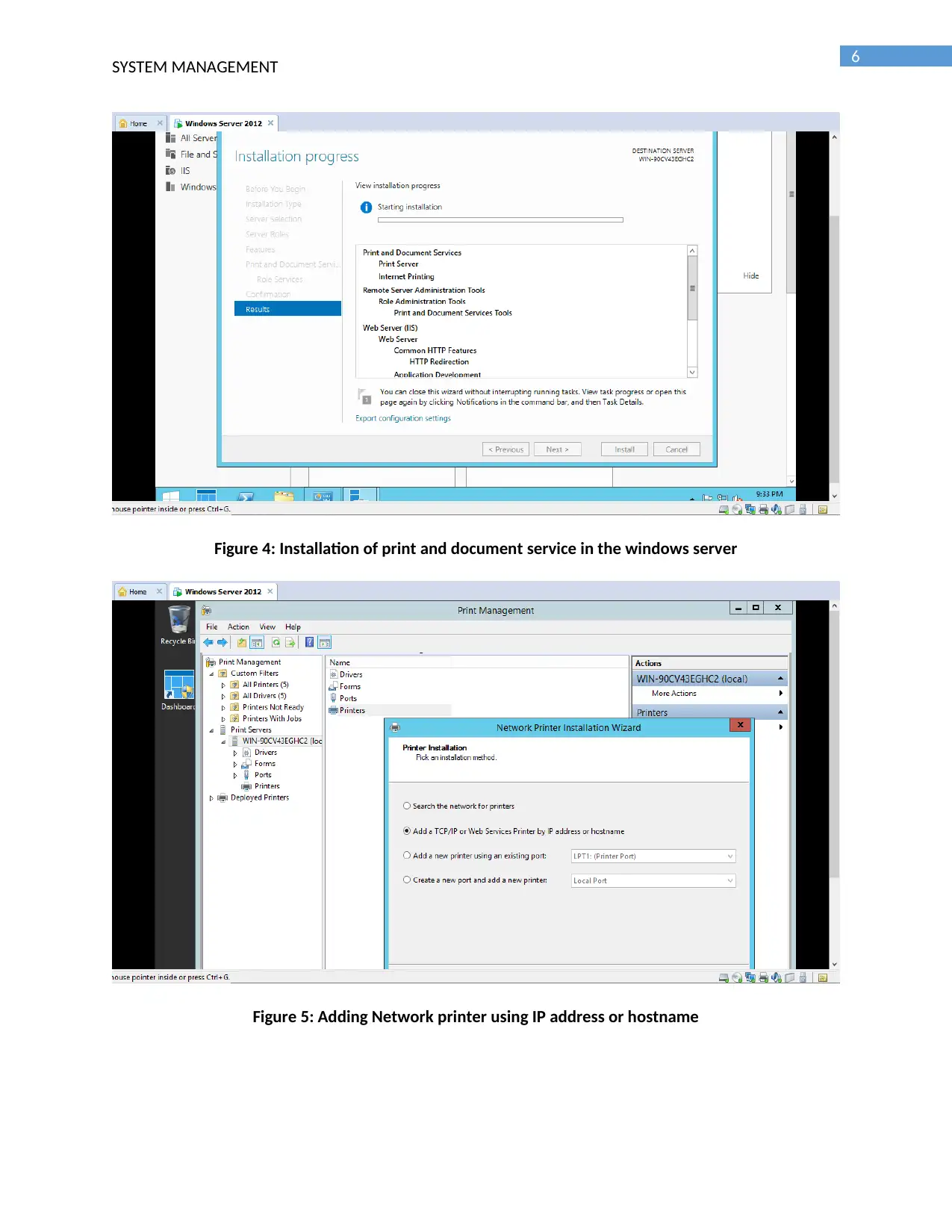
Figure 4: Installation of print and document service in the windows server
Figure 5: Adding Network printer using IP address or hostname
SYSTEM MANAGEMENT
Figure 4: Installation of print and document service in the windows server
Figure 5: Adding Network printer using IP address or hostname
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
SYSTEM MANAGEMENT
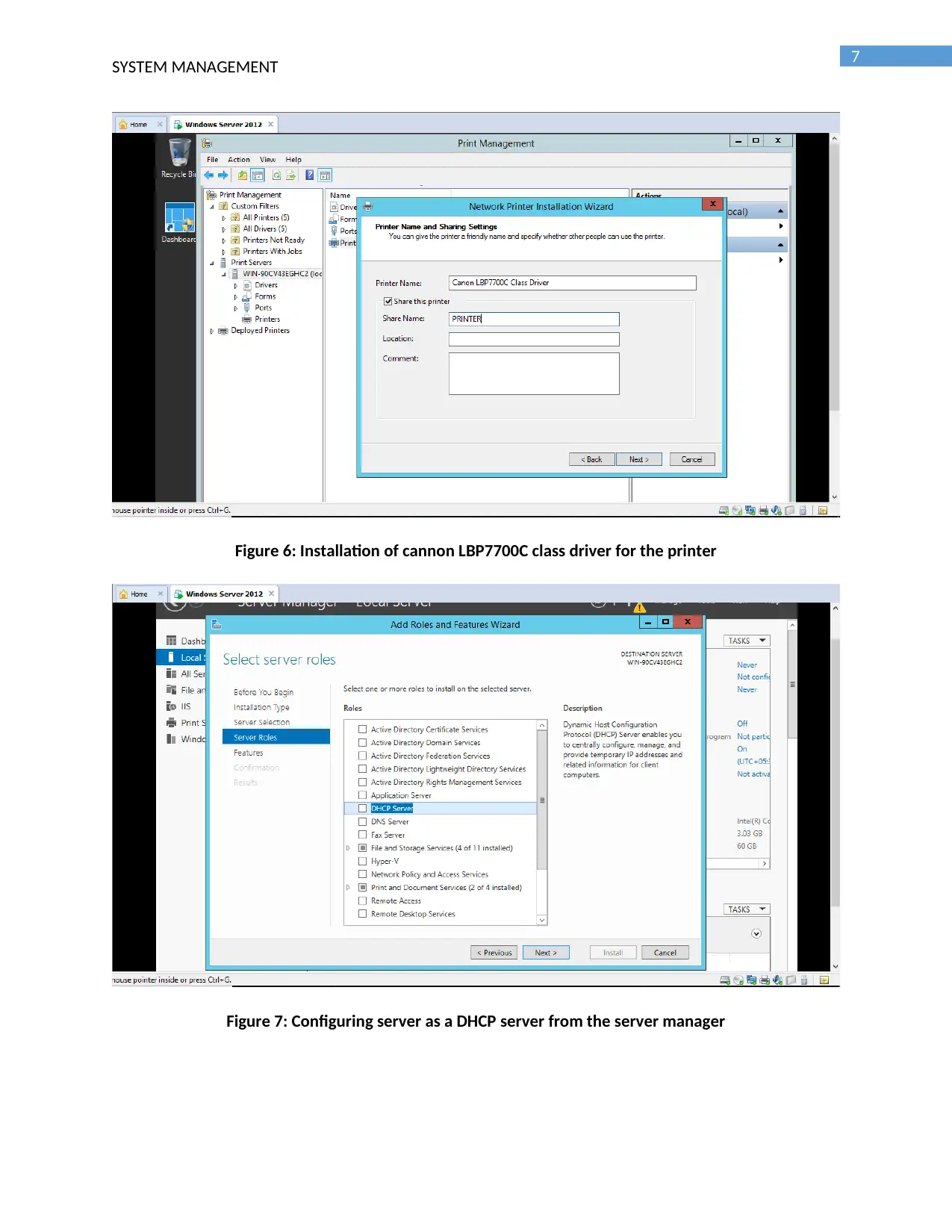
Figure 6: Installation of cannon LBP7700C class driver for the printer
Figure 7: Configuring server as a DHCP server from the server manager
SYSTEM MANAGEMENT
Figure 6: Installation of cannon LBP7700C class driver for the printer
Figure 7: Configuring server as a DHCP server from the server manager
8
SYSTEM MANAGEMENT
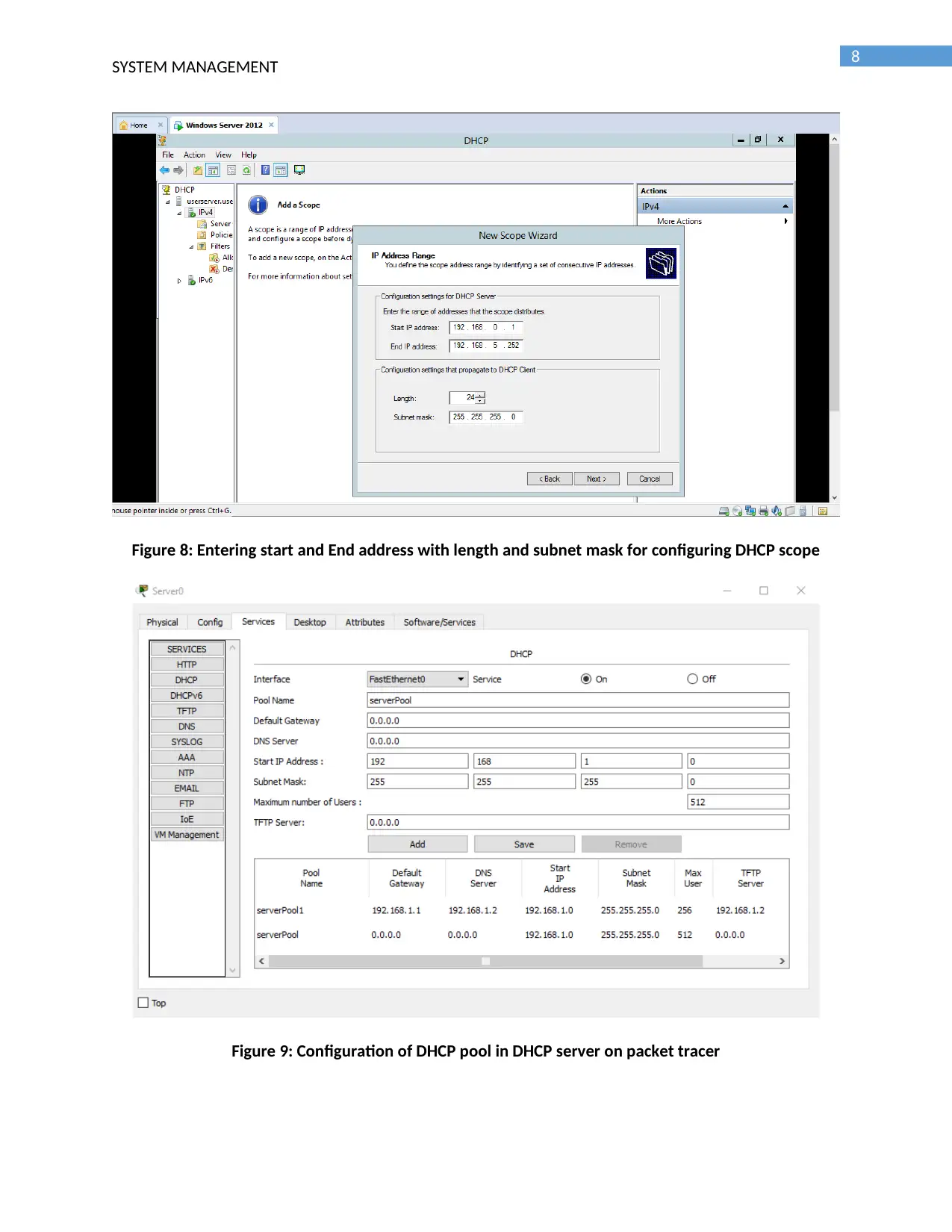
Figure 8: Entering start and End address with length and subnet mask for configuring DHCP scope
Figure 9: Configuration of DHCP pool in DHCP server on packet tracer
SYSTEM MANAGEMENT
Figure 8: Entering start and End address with length and subnet mask for configuring DHCP scope
Figure 9: Configuration of DHCP pool in DHCP server on packet tracer
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
SYSTEM MANAGEMENT
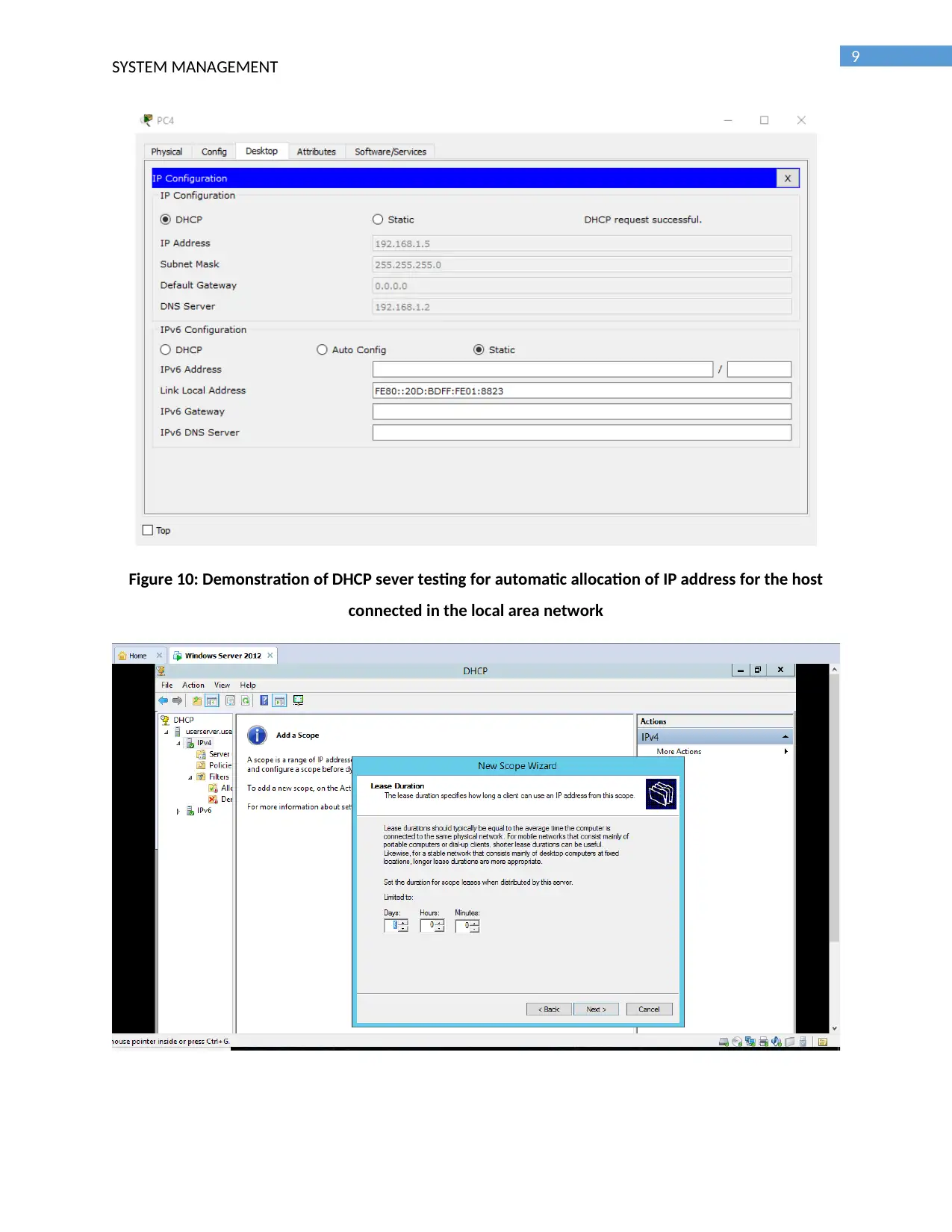
Figure 10: Demonstration of DHCP sever testing for automatic allocation of IP address for the host
connected in the local area network
SYSTEM MANAGEMENT
Figure 10: Demonstration of DHCP sever testing for automatic allocation of IP address for the host
connected in the local area network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
SYSTEM MANAGEMENT
Figure 11: Configuration of lease time for the DHCP scope for setting the expiry time of the address
allocated to the host
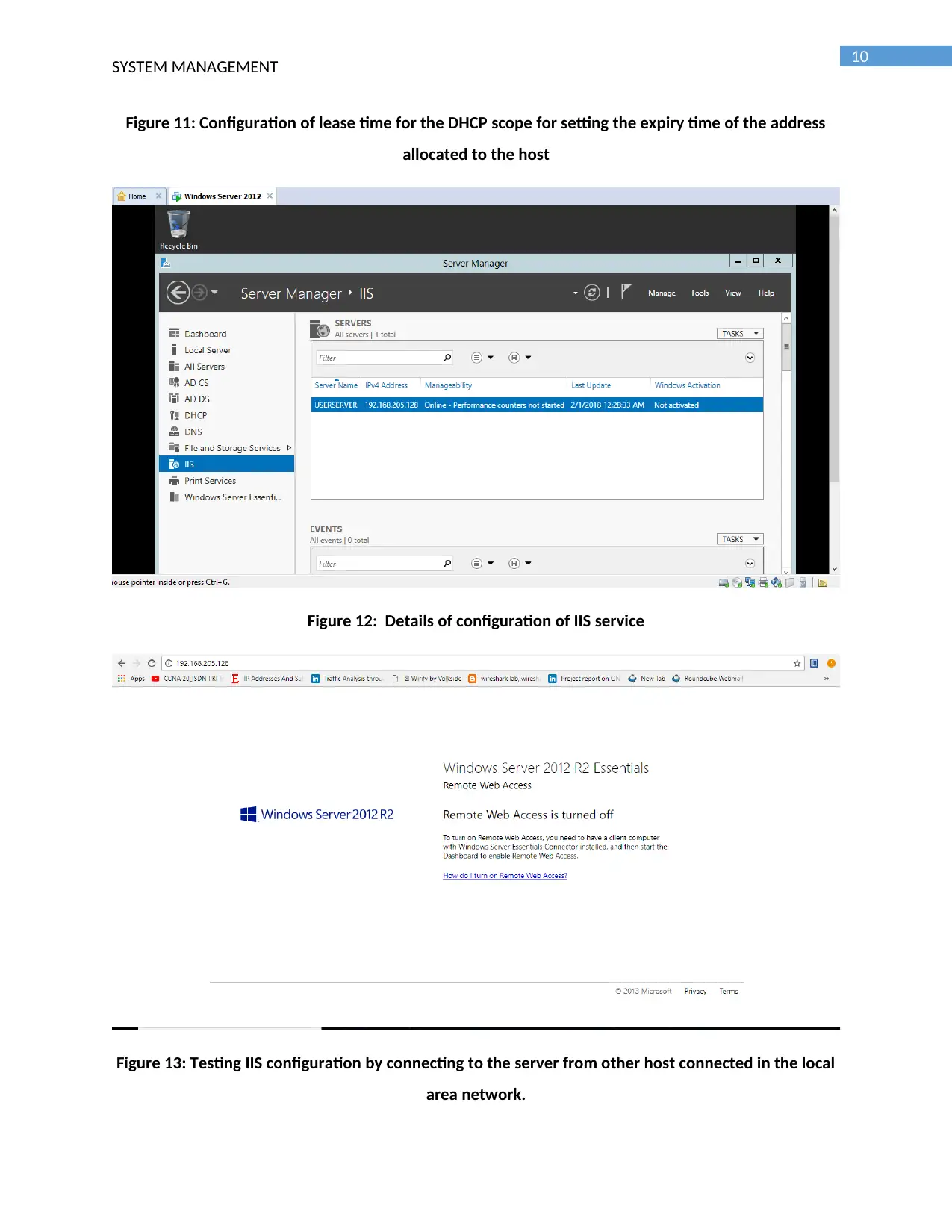
Figure 12: Details of configuration of IIS service
Figure 13: Testing IIS configuration by connecting to the server from other host connected in the local
area network.
SYSTEM MANAGEMENT
Figure 11: Configuration of lease time for the DHCP scope for setting the expiry time of the address
allocated to the host
Figure 12: Details of configuration of IIS service
Figure 13: Testing IIS configuration by connecting to the server from other host connected in the local
area network.
11
SYSTEM MANAGEMENT
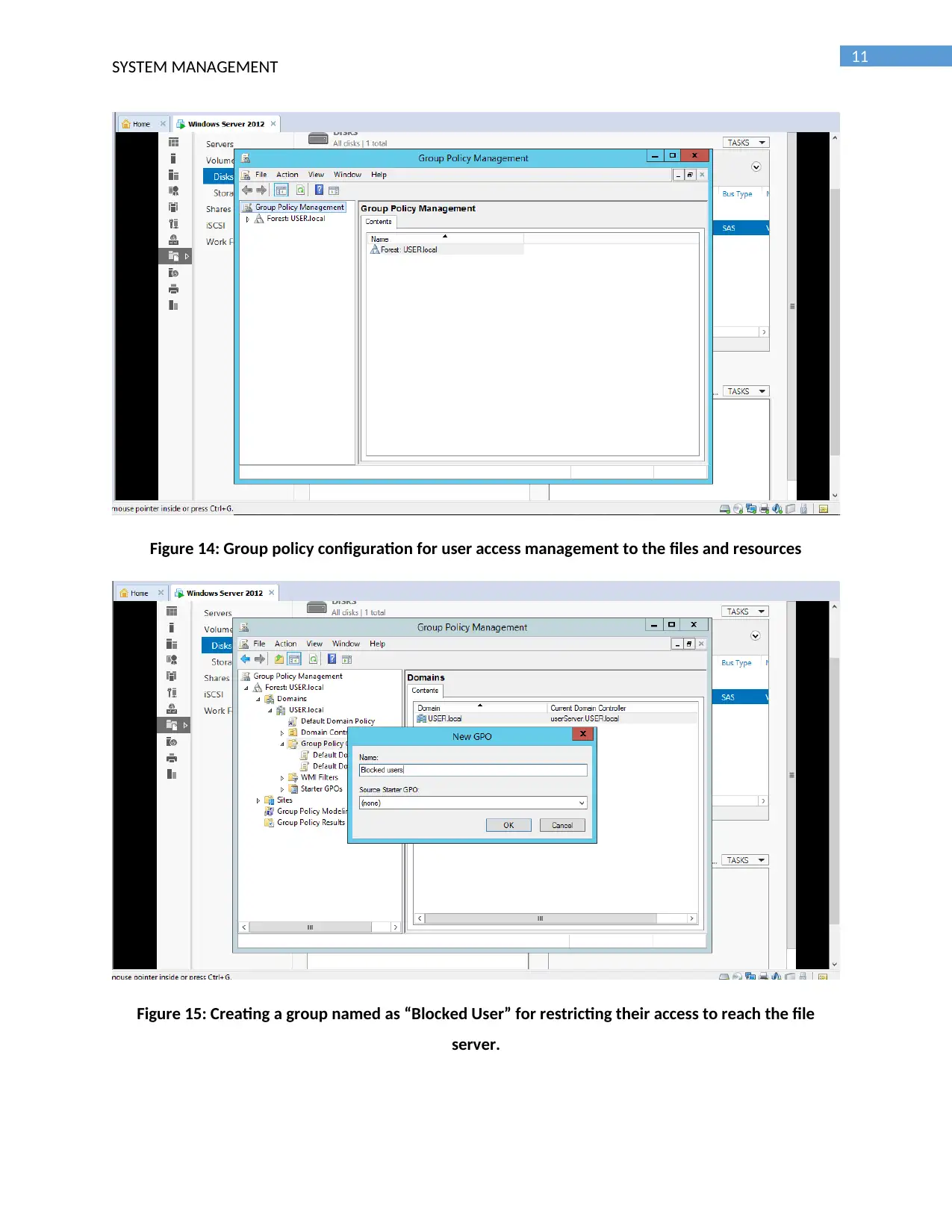
Figure 14: Group policy configuration for user access management to the files and resources
Figure 15: Creating a group named as “Blocked User” for restricting their access to reach the file
server.
SYSTEM MANAGEMENT
Figure 14: Group policy configuration for user access management to the files and resources
Figure 15: Creating a group named as “Blocked User” for restricting their access to reach the file
server.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





