University Computer Security Issues Report: WannaCry and Petya
VerifiedAdded on 2022/12/23
|13
|1223
|90
Report
AI Summary
This report delves into the intricacies of contemporary computer security, focusing on two prominent ransomware attacks: WannaCry and Petya. The report begins with a detailed walkthrough of how each ransomware operates in a live setting, visually representing the attack stages with supporting graphics and discussions. It then identifies and explains the real-world settings each ransomware targeted, including the timing of attacks, specific names, outcomes, financial and device impacts, breached security aims, and actions taken by organizations. The analysis covers the technical aspects of the attacks, the consequences of the breaches, and the responses taken to mitigate the issues, providing a comprehensive understanding of these significant cyber threats. The report includes flowcharts, screenshots, and references to provide a clear and in-depth understanding of the topic.

Running head: CONTEMPORARY COMPUTER SECURITY ISSUES
Contemporary Computer Security Issues
Name of the Student
Name of the University
Author Note
Contemporary Computer Security Issues
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CONTEMPORARY COMPUTER SECURITY ISSUES
Table of Contents
Part 1: A detailed walk-through of how WannaCry and Petya ransomware operate in a
live setting..........................................................................................................................2
Part 2: Identification and explanation of the real-world setting each of WannaCry and
Petya ransomware has attacked........................................................................................10
a. When did the attack occur and was it given a specific name?.....................................10
b. What was the outcome of your chosen incident?.........................................................10
c. What was the impact of your chosen incident (financial, devices affected, etc.)?.......10
d. Which aim(s) of security was breached and what were the consequences?................11
e. What specific action(s) did the vendor/company/organisation take to address the
issue?................................................................................................................................11
References................................................................................................................................12
Table of Contents
Part 1: A detailed walk-through of how WannaCry and Petya ransomware operate in a
live setting..........................................................................................................................2
Part 2: Identification and explanation of the real-world setting each of WannaCry and
Petya ransomware has attacked........................................................................................10
a. When did the attack occur and was it given a specific name?.....................................10
b. What was the outcome of your chosen incident?.........................................................10
c. What was the impact of your chosen incident (financial, devices affected, etc.)?.......10
d. Which aim(s) of security was breached and what were the consequences?................11
e. What specific action(s) did the vendor/company/organisation take to address the
issue?................................................................................................................................11
References................................................................................................................................12

2CONTEMPORARY COMPUTER SECURITY ISSUES
Part 1: A detailed walk-through of how WannaCry and Petya ransomware operate in a
live setting
WannaCry
Figure 1: Live Demo of WannaCry Ransomware
(Source: Delaney, 2019)
Figure 2: Normal Setup where the files are still available in a computer
Part 1: A detailed walk-through of how WannaCry and Petya ransomware operate in a
live setting
WannaCry
Figure 1: Live Demo of WannaCry Ransomware
(Source: Delaney, 2019)
Figure 2: Normal Setup where the files are still available in a computer
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CONTEMPORARY COMPUTER SECURITY ISSUES
(Source: Delaney, 2019)
Figure 3: WannaCry Decryptor Properties
(Source: Delaney, 2019)
(Source: Delaney, 2019)
Figure 3: WannaCry Decryptor Properties
(Source: Delaney, 2019)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CONTEMPORARY COMPUTER SECURITY ISSUES
Figure 4: WannaCry Decryptor .exe file variant
(Source: Delaney, 2019)
Figure 5: A typical WannaCry Ransomware attack
(Source: Delaney, 2019)
Figure 6: Typical WannaCry attack
Figure 4: WannaCry Decryptor .exe file variant
(Source: Delaney, 2019)
Figure 5: A typical WannaCry Ransomware attack
(Source: Delaney, 2019)
Figure 6: Typical WannaCry attack

5CONTEMPORARY COMPUTER SECURITY ISSUES
(Source: Delaney, 2019)
Figure 7: WannaCry attack encrypted all files in the background
(Source: Delaney, 2019)
The Steps that have been followed about clearly provides distinct example of how a
WannaCry attack occurs and has the ability of encrypting all the files that would be used by
an individual in their own system.
(Source: Delaney, 2019)
Figure 7: WannaCry attack encrypted all files in the background
(Source: Delaney, 2019)
The Steps that have been followed about clearly provides distinct example of how a
WannaCry attack occurs and has the ability of encrypting all the files that would be used by
an individual in their own system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
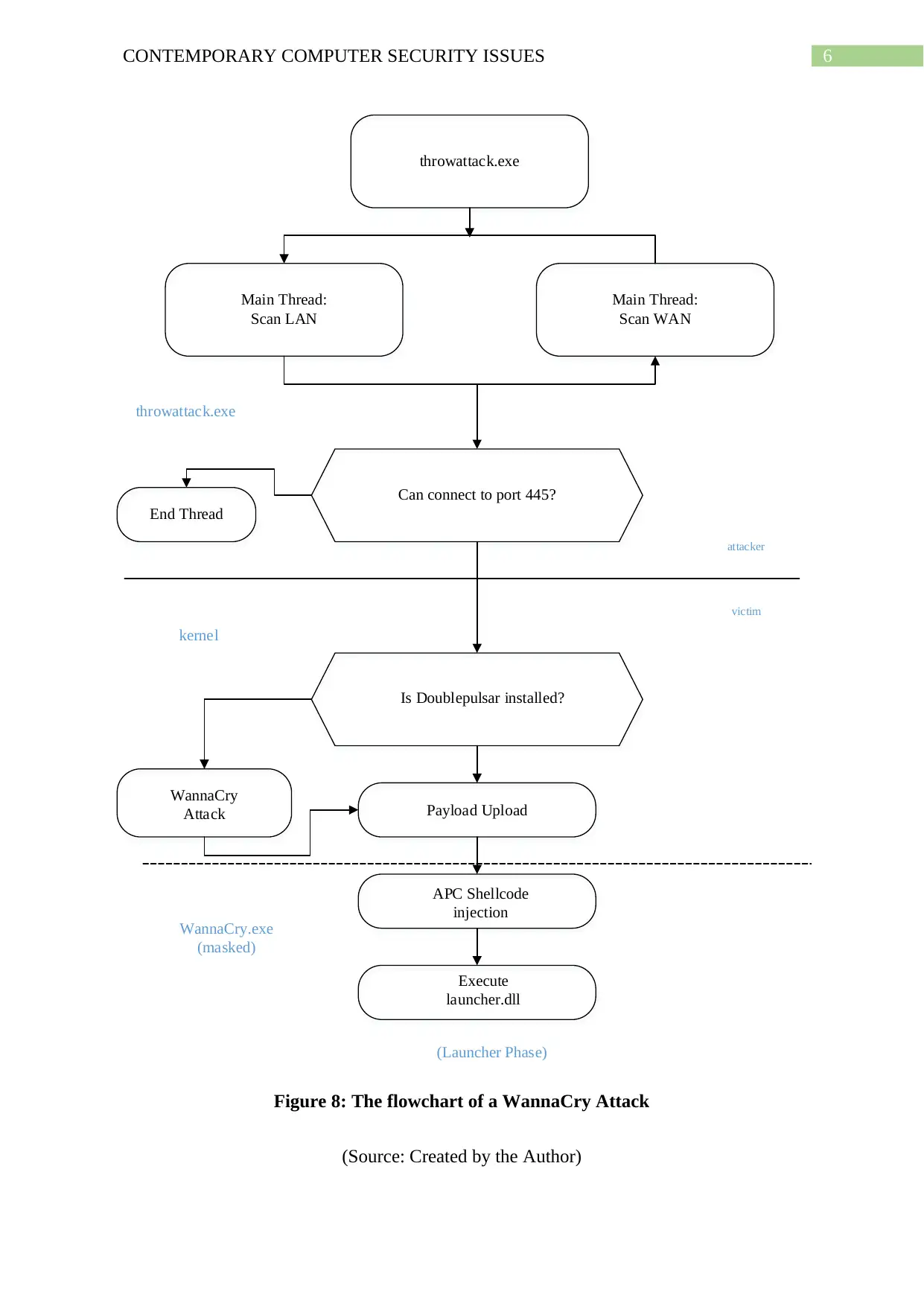
6CONTEMPORARY COMPUTER SECURITY ISSUES
Figure 8: The flowchart of a WannaCry Attack
(Source: Created by the Author)
throwattack.exe
Main Thread:
Scan LAN
Main Thread:
Scan WAN
Can connect to port 445?
End Thread
Is Doublepulsar installed?
WannaCry
Attack Payload Upload
APC Shellcode
injection
Execute
launcher.dll
throwattack.exe
kernel
WannaCry.exe
(masked)
(Launcher Phase)
attacker
victim
Figure 8: The flowchart of a WannaCry Attack
(Source: Created by the Author)
throwattack.exe
Main Thread:
Scan LAN
Main Thread:
Scan WAN
Can connect to port 445?
End Thread
Is Doublepulsar installed?
WannaCry
Attack Payload Upload
APC Shellcode
injection
Execute
launcher.dll
throwattack.exe
kernel
WannaCry.exe
(masked)
(Launcher Phase)
attacker
victim
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CONTEMPORARY COMPUTER SECURITY ISSUES
Petya
Figure 9: Renaming a file
(Source: Petrenko et al., 2018)
Figure 10: Renamed the file to .exe
(Source: Petrenko et al., 2018)
Petya
Figure 9: Renaming a file
(Source: Petrenko et al., 2018)
Figure 10: Renamed the file to .exe
(Source: Petrenko et al., 2018)
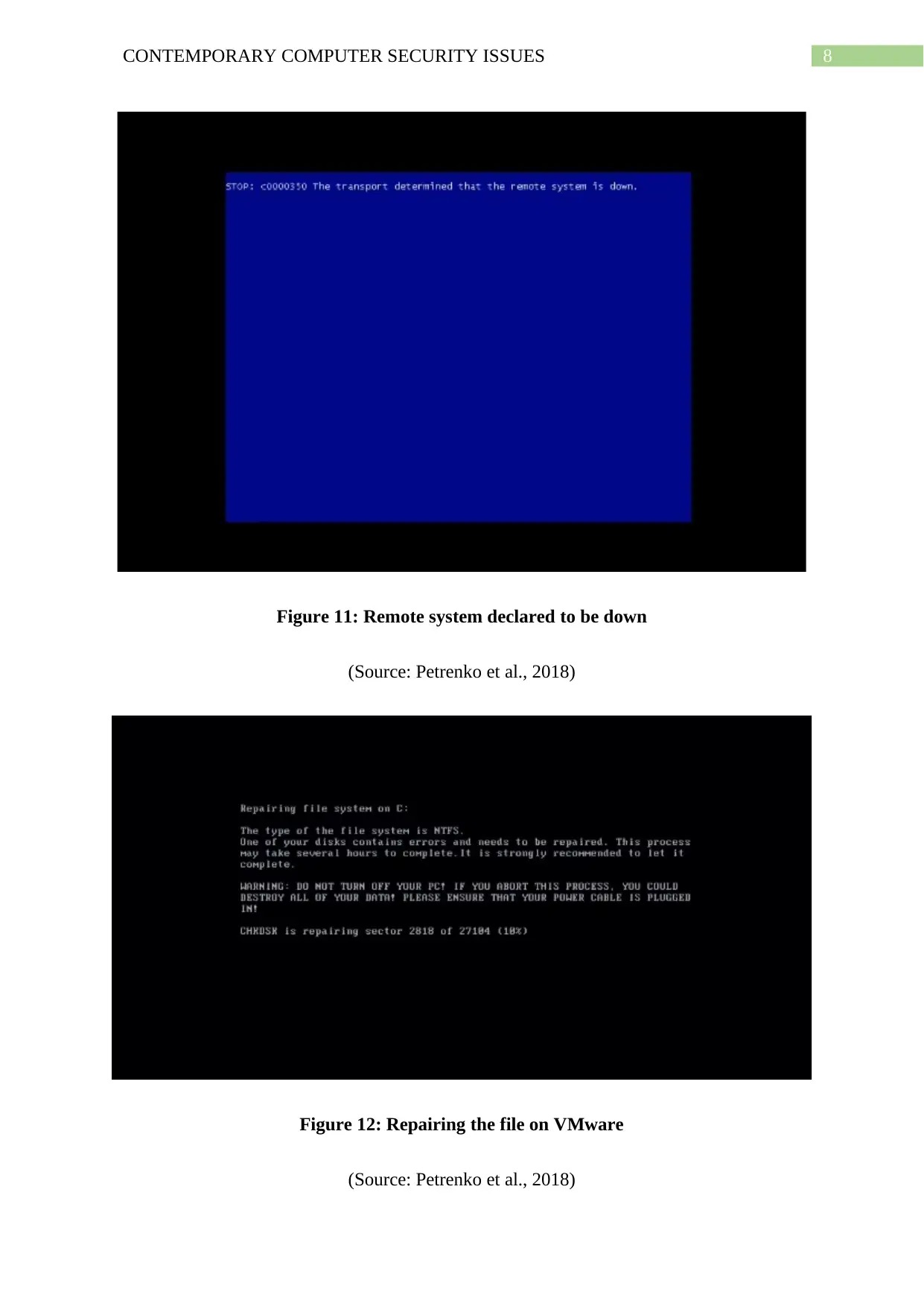
8CONTEMPORARY COMPUTER SECURITY ISSUES
Figure 11: Remote system declared to be down
(Source: Petrenko et al., 2018)
Figure 12: Repairing the file on VMware
(Source: Petrenko et al., 2018)
Figure 11: Remote system declared to be down
(Source: Petrenko et al., 2018)
Figure 12: Repairing the file on VMware
(Source: Petrenko et al., 2018)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CONTEMPORARY COMPUTER SECURITY ISSUES
Figure 13: Petya Attack
(Source: Petrenko et al., 2018)
Figure 14: Flowchart of a general Petya attack
Figure 13: Petya Attack
(Source: Petrenko et al., 2018)
Figure 14: Flowchart of a general Petya attack
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CONTEMPORARY COMPUTER SECURITY ISSUES
(Source: Dellaney, 2019)
Part 2: Identification and explanation of the real-world setting each of WannaCry and
Petya ransomware has attacked
a. When did the attack occur and was it given a specific name?
The WannaCry attack occurred in May 2017 worldwide which was followed by a
ransomware crypto war and this targeted several computers running on the operating system
of Microsoft windows by encrypting the data and then demanding run some for decrypting
them further with the payment through cryptocurrency Bitcoins (Delaney, 2019). On the
other hand, Petya is encrypting ransomware which was discovered in the early 2016 and this
is a malware that also targets the computer system based on the operating system of
Microsoft Windows (Petrenko et al., 2018). These are mostly found to be infecting the boot
record while executing any payload which has been encrypting the file system of hard drive
and then prevents that device running on windows to boot further.
b. What was the outcome of your chosen incident?
The outcome of the Petya Attack meets many organisations lose their applications and
operating system deployments where systems were taken out from The attack and the
significantly had to delete the ability for the organisations by which they could recover the
business operations that were hacked by the attack (Delaney, 2019).
c. What was the impact of your chosen incident (financial, devices affected, etc.)?
Several organisations where losing most reliable business operations and the impact
was such that it also affected the British advertising companies and also the American
pharmaceutical companies including the national oil companies and various multinational
organisations where they lost almost an estimated cost between 200 million USD and 300
million USD revenues (Aidan, 2017). The alliance that were built between the Secretary
(Source: Dellaney, 2019)
Part 2: Identification and explanation of the real-world setting each of WannaCry and
Petya ransomware has attacked
a. When did the attack occur and was it given a specific name?
The WannaCry attack occurred in May 2017 worldwide which was followed by a
ransomware crypto war and this targeted several computers running on the operating system
of Microsoft windows by encrypting the data and then demanding run some for decrypting
them further with the payment through cryptocurrency Bitcoins (Delaney, 2019). On the
other hand, Petya is encrypting ransomware which was discovered in the early 2016 and this
is a malware that also targets the computer system based on the operating system of
Microsoft Windows (Petrenko et al., 2018). These are mostly found to be infecting the boot
record while executing any payload which has been encrypting the file system of hard drive
and then prevents that device running on windows to boot further.
b. What was the outcome of your chosen incident?
The outcome of the Petya Attack meets many organisations lose their applications and
operating system deployments where systems were taken out from The attack and the
significantly had to delete the ability for the organisations by which they could recover the
business operations that were hacked by the attack (Delaney, 2019).
c. What was the impact of your chosen incident (financial, devices affected, etc.)?
Several organisations where losing most reliable business operations and the impact
was such that it also affected the British advertising companies and also the American
pharmaceutical companies including the national oil companies and various multinational
organisations where they lost almost an estimated cost between 200 million USD and 300
million USD revenues (Aidan, 2017). The alliance that were built between the Secretary

11CONTEMPORARY COMPUTER SECURITY ISSUES
Generals in various countries lost their strength over cyber defences and also the Article 5
principle of collective defence was triggered.
d. Which aim(s) of security was breached and what were the consequences?
The national security was breed at that point of time where the organisations where
building alliance is in between countries and this would have had huge impact as the
cybersecurity strength that was the basis of these strengthening relationships were attacked
(Aidan, 2017).
e. What specific action(s) did the vendor/company/organisation take to address the
issue?
The Europol had urgently responded to the reports of the cyber-attack and also
involved the members of the different states from European Union where the homeland
security was also involved in United States for coordinating with their local partners and then
the Trump administration blamed Russia for all the attacks. Although for the mitigation of
attacks the possible stop to the encryption process of the infected computers could be found
through a fictitious chkdsk screen that was followed based on the terms of use and the read
only files named perf.c and perfc.dat (Aidan, 2017).
Generals in various countries lost their strength over cyber defences and also the Article 5
principle of collective defence was triggered.
d. Which aim(s) of security was breached and what were the consequences?
The national security was breed at that point of time where the organisations where
building alliance is in between countries and this would have had huge impact as the
cybersecurity strength that was the basis of these strengthening relationships were attacked
(Aidan, 2017).
e. What specific action(s) did the vendor/company/organisation take to address the
issue?
The Europol had urgently responded to the reports of the cyber-attack and also
involved the members of the different states from European Union where the homeland
security was also involved in United States for coordinating with their local partners and then
the Trump administration blamed Russia for all the attacks. Although for the mitigation of
attacks the possible stop to the encryption process of the infected computers could be found
through a fictitious chkdsk screen that was followed based on the terms of use and the read
only files named perf.c and perfc.dat (Aidan, 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



