Analyzing Content Delivery Networks (CDN) and CPDoS Exploits
VerifiedAdded on 2022/09/12
|16
|3157
|12
Report
AI Summary
This report provides a comprehensive analysis of Content Delivery Networks (CDNs) and Cache Poisoning Denial-of-Service (CPDoS) attacks. It begins by explaining the principles and usage of CDNs, emphasizing their role in improving internet communication and enhancing website loading times. The report then delves into the specifics of CPDoS exploits, including HTTP Header Oversize (HHO), HTTP Meta Character (HMC), and HTTP Method Override (HMO) attacks. It details how these attacks compromise CDN security by manipulating HTTP headers and cache mechanisms to deliver error pages instead of the intended content. Furthermore, the report outlines the impact of CPDoS attacks on network performance and security, including the distribution of error pages across edge servers. Finally, it discusses mitigation strategies, such as deploying Web Application Firewalls (WAFs) and excluding error pages from caching, to safeguard against these exploits and ensure smoother network operations. This report is a valuable resource for understanding and addressing the vulnerabilities associated with CDNs and CPDoS attacks.

Running head: - CDN AND CPDOS
CDN AND CPDOS
Name of the Student
Name of the University
Author Note
CDN AND CPDOS
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CDN AND CPDOS
Abstract
CDN have been designed to improve the communication over the internet and to enhance the
particular speed of the internet connection for improving the internet connectivity. As a
reason, this discussion has been undertaken to highlight the brief explanation of CDN along
with the working principle of the same along with their particular usage. Following this,
CPDoS attacks have been identified as a threat posed towards the CDNs that has been briefly
explained along with the various types of the same. Lastly, the discussion also states the
impacts that CPDoS has upon the connection and the ways to mitigate the threats for a
smoother functioning of the networks and internet connection.
Abstract
CDN have been designed to improve the communication over the internet and to enhance the
particular speed of the internet connection for improving the internet connectivity. As a
reason, this discussion has been undertaken to highlight the brief explanation of CDN along
with the working principle of the same along with their particular usage. Following this,
CPDoS attacks have been identified as a threat posed towards the CDNs that has been briefly
explained along with the various types of the same. Lastly, the discussion also states the
impacts that CPDoS has upon the connection and the ways to mitigate the threats for a
smoother functioning of the networks and internet connection.

2CDN AND CPDOS
Table of Contents
1. Introduction:...........................................................................................................................3
2. Principle and Usage of CDN:.................................................................................................3
3. Description of CPDoS exploit:...............................................................................................5
4. Performing CPDoS exploit and solutions:.............................................................................7
5. Impact of CPDoS:................................................................................................................10
6. Conclusion:..........................................................................................................................12
7. References:...........................................................................................................................13
Table of Contents
1. Introduction:...........................................................................................................................3
2. Principle and Usage of CDN:.................................................................................................3
3. Description of CPDoS exploit:...............................................................................................5
4. Performing CPDoS exploit and solutions:.............................................................................7
5. Impact of CPDoS:................................................................................................................10
6. Conclusion:..........................................................................................................................12
7. References:...........................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CDN AND CPDOS
1. Introduction:
Content Delivery Network is the term that is shortened to CDN referring to a network
that has been created as well as distributed over a large geographical area having the
inclusion of proxy servers and that of data centres (Berger, Sitaraman and Harchol-Balter
2017). The primary objective that this network deals with is to provide with high availability
as well as high performance in regards to the distributing of variously existing services to the
end users along with their connected devices. CDN had come into the existence in the year of
late 1990s for alleviating the particular performance of the internet functioning at that
particular period. Since that time, CDN have risen to act as a primary contributor towards the
internet connectivity that is provisioned to individuals all around the world including the likes
of internet objects, software, social media platforms, downloadable commodities as well as
video on demand. This discussion has been undertaken to put forwards the principles of CDN
and the CPDoS exploits that take place within the CDNs (Zhao et al. 2019). Following this, a
proper explanation of how the CPDoS carries out as well as the relative solution to the
exploits shall be highlighted. Lastly, impacts of such exploits have been briefly explained.
2. Principle and Usage of CDN:
CDN are commonly the abbreviation that stands for Content Delivery Network that
specifically refers to the particular fact of a network that has been designed and
geographically scattered among a collection of servers that carry out the work together as a
group for delivering of faster content on the internet.
CDN provisions with the allowance to carry out a quicker transfer of objects loading
on the web having the inclusion of HTML pages, videos, JavaScript files, style sheets as well
as images (Retal et al. 2017). The CDN services is popular and continues to experience a
significant increase within the usage in regards to the present condition of the web traffic that
1. Introduction:
Content Delivery Network is the term that is shortened to CDN referring to a network
that has been created as well as distributed over a large geographical area having the
inclusion of proxy servers and that of data centres (Berger, Sitaraman and Harchol-Balter
2017). The primary objective that this network deals with is to provide with high availability
as well as high performance in regards to the distributing of variously existing services to the
end users along with their connected devices. CDN had come into the existence in the year of
late 1990s for alleviating the particular performance of the internet functioning at that
particular period. Since that time, CDN have risen to act as a primary contributor towards the
internet connectivity that is provisioned to individuals all around the world including the likes
of internet objects, software, social media platforms, downloadable commodities as well as
video on demand. This discussion has been undertaken to put forwards the principles of CDN
and the CPDoS exploits that take place within the CDNs (Zhao et al. 2019). Following this, a
proper explanation of how the CPDoS carries out as well as the relative solution to the
exploits shall be highlighted. Lastly, impacts of such exploits have been briefly explained.
2. Principle and Usage of CDN:
CDN are commonly the abbreviation that stands for Content Delivery Network that
specifically refers to the particular fact of a network that has been designed and
geographically scattered among a collection of servers that carry out the work together as a
group for delivering of faster content on the internet.
CDN provisions with the allowance to carry out a quicker transfer of objects loading
on the web having the inclusion of HTML pages, videos, JavaScript files, style sheets as well
as images (Retal et al. 2017). The CDN services is popular and continues to experience a
significant increase within the usage in regards to the present condition of the web traffic that
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CDN AND CPDOS
is specifically served through a CDN network. This also has the inclusion of majorly existing
sites such as Amazon, Facebook as well as Netflix. In addition to this, if the CDN network
has been properly configured then it can also provision a particular website with protection
against many malicious threats that exist online such as the likes of DDoS attacks.
Figure-1: Content Delivery Network
(Source- Nguyen, Iacono and Federrath 2019)
However, it has to be kept in mind that CDN is not a web host and does not carry the
potential capability to host contents along with the fact that it does not provision a helping
hand to the cache related content present on the edge network. This significantly brings a
degree of improvement within the performance of the website (Sung et al. 2016). In regards
to this, it has been visibly identified that majority of the websites face a problem in terms of
performance needs from the traditional hosts and hence, such companies opt for the content
delivery network to solve this particular issue. The CDNs are a primary source of reducing
the bandwidth, improving the security as well as preventing the interruptions that are caused
is specifically served through a CDN network. This also has the inclusion of majorly existing
sites such as Amazon, Facebook as well as Netflix. In addition to this, if the CDN network
has been properly configured then it can also provision a particular website with protection
against many malicious threats that exist online such as the likes of DDoS attacks.
Figure-1: Content Delivery Network
(Source- Nguyen, Iacono and Federrath 2019)
However, it has to be kept in mind that CDN is not a web host and does not carry the
potential capability to host contents along with the fact that it does not provision a helping
hand to the cache related content present on the edge network. This significantly brings a
degree of improvement within the performance of the website (Sung et al. 2016). In regards
to this, it has been visibly identified that majority of the websites face a problem in terms of
performance needs from the traditional hosts and hence, such companies opt for the content
delivery network to solve this particular issue. The CDNs are a primary source of reducing
the bandwidth, improving the security as well as preventing the interruptions that are caused

5CDN AND CPDOS
in the service that makes the CDN to be a popular choice over the traditional hosts in the
current cyber world.
The CDNs are used for the following purposes that act as a benefit in using the same
(Huang et al. 2019). These are,
i) Improvement of website loading time- this is done by distributing the content in a
much closer proximity to the visitors of the website with the proper usage of a
CDN server located nearby that makes the visitors experience to a faster loading
time of the particular webpage.
ii) Reduction of bandwidth costs- the costs directly associated with the bandwidth
required for the purpose of hosting the website refers to a primary expense related
to having a website (Sarddar, Roy and Sen 2017). Hence, caching or other kinds
of optimizations, the CDNs have been able to bring in a reduction within the
associated price for the origin server that shall reduce the overall costing for the
owners.
iii) Increasing of content- huge chunks of traffic or might as well be failures of the
hardware modules can bring in an interruption within the normal functioning of
the website. This provisions the CDN, which can handle the increasing traffic in a
better way as well as deal with the failures occurring within the hardware better
than the original servers that exists.
iv) Improvement of website security- CDN networks can greatly improve the security
with the help of DDoS mitigation, optimizations as well as improving the
certificates related to security (Triukose and Rabinovich 2016).
in the service that makes the CDN to be a popular choice over the traditional hosts in the
current cyber world.
The CDNs are used for the following purposes that act as a benefit in using the same
(Huang et al. 2019). These are,
i) Improvement of website loading time- this is done by distributing the content in a
much closer proximity to the visitors of the website with the proper usage of a
CDN server located nearby that makes the visitors experience to a faster loading
time of the particular webpage.
ii) Reduction of bandwidth costs- the costs directly associated with the bandwidth
required for the purpose of hosting the website refers to a primary expense related
to having a website (Sarddar, Roy and Sen 2017). Hence, caching or other kinds
of optimizations, the CDNs have been able to bring in a reduction within the
associated price for the origin server that shall reduce the overall costing for the
owners.
iii) Increasing of content- huge chunks of traffic or might as well be failures of the
hardware modules can bring in an interruption within the normal functioning of
the website. This provisions the CDN, which can handle the increasing traffic in a
better way as well as deal with the failures occurring within the hardware better
than the original servers that exists.
iv) Improvement of website security- CDN networks can greatly improve the security
with the help of DDoS mitigation, optimizations as well as improving the
certificates related to security (Triukose and Rabinovich 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CDN AND CPDOS
3. Description of CPDoS exploit:
CPDoS commonly abbreviates for Cache Poisoning Denial-of-Service attacks that
was found out by the German Cyber Security researchers belonging to the Cologne
University and the University of Hamburg. They had specifically derived this attack that
provisions the particular attackers with a special allowance (Jia et al. 2017). With the use of
this allowance, the attacker can compel a particular webpage or an entire website for
delivering a page that is an error instead of the original one that the respective visitor had
tried to access while searching up with the help of the URL. Web caching refers to a primary
component of the modernised architecture, in which the particular cache puts forward the
promotion of performing the website as well as offering with an additional form of protection
such as the likes of DoS attack.
Figure-2: CPDoS Attack
(Source- DiBenedetto and Papadopoulos 2016)
The basic blue print of how the attack gets carried out has been described below with
the help of the following points (Nguyen, Iacono and Federrath 2019). These are,
i) The particular attacker sends a potential request of a common HTTP command
that has the primary inclusion of a maliciously active header painting a target
upon the resource of the victim provisioned by some existing web server. This
particular request made is significantly processed by that of the intermediately
existing cache, while on the other hand the malicious header remains recessive.
3. Description of CPDoS exploit:
CPDoS commonly abbreviates for Cache Poisoning Denial-of-Service attacks that
was found out by the German Cyber Security researchers belonging to the Cologne
University and the University of Hamburg. They had specifically derived this attack that
provisions the particular attackers with a special allowance (Jia et al. 2017). With the use of
this allowance, the attacker can compel a particular webpage or an entire website for
delivering a page that is an error instead of the original one that the respective visitor had
tried to access while searching up with the help of the URL. Web caching refers to a primary
component of the modernised architecture, in which the particular cache puts forward the
promotion of performing the website as well as offering with an additional form of protection
such as the likes of DoS attack.
Figure-2: CPDoS Attack
(Source- DiBenedetto and Papadopoulos 2016)
The basic blue print of how the attack gets carried out has been described below with
the help of the following points (Nguyen, Iacono and Federrath 2019). These are,
i) The particular attacker sends a potential request of a common HTTP command
that has the primary inclusion of a maliciously active header painting a target
upon the resource of the victim provisioned by some existing web server. This
particular request made is significantly processed by that of the intermediately
existing cache, while on the other hand the malicious header remains recessive.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CDN AND CPDOS
ii) This cache then particular forwards the command to the originated server since,
the server has no storage functions to store the original or a fresh copy (Brown
and Willink 2018). Back at the server, this particular processing of the request is
done provoking an error in regards to the existence of the malicious header that is
still contained in the same.
iii) As a result of this, the originated server takes the visitor to a page of error that
specifically gets into the storage by the existing cache keeping apart from the
resource that had been originally asked for.
iv) This provides a satisfaction to the attacker knowing that the upcoming of an error
highlights the fact of a successful attack (DiBenedetto and Papadopoulos 2016).
v) Following this, the users or the visitor who have been still trying to get hold of the
targeted webpage with consecutive requests showing a page of error rather than
the original one.
Figure-3: CPDoS Attack steps
(Source- AbdAllah, Zulkernine and Hassanein 2018)
ii) This cache then particular forwards the command to the originated server since,
the server has no storage functions to store the original or a fresh copy (Brown
and Willink 2018). Back at the server, this particular processing of the request is
done provoking an error in regards to the existence of the malicious header that is
still contained in the same.
iii) As a result of this, the originated server takes the visitor to a page of error that
specifically gets into the storage by the existing cache keeping apart from the
resource that had been originally asked for.
iv) This provides a satisfaction to the attacker knowing that the upcoming of an error
highlights the fact of a successful attack (DiBenedetto and Papadopoulos 2016).
v) Following this, the users or the visitor who have been still trying to get hold of the
targeted webpage with consecutive requests showing a page of error rather than
the original one.
Figure-3: CPDoS Attack steps
(Source- AbdAllah, Zulkernine and Hassanein 2018)

8CDN AND CPDOS
4. Performing CPDoS exploit and solutions:
CPDoS exploits can be performed in three different variations that exists (AbdAllah,
Zulkernine and Hassanein 2018). The three varieties of CPDoS attacks are,
i) HTTP Header Oversize (HHO) - HTTP header has the primary inclusion of vital
information that belongs to the intermediary systems along with the web servers.
This has the primary inclusion of header fields or the meta data that is related to
the caches present on the media types that are supported by the clients such as the
likes of languages as well as encodings (Prabadevi et al. 2019). In regards to this,
the standard of the HTTP does not put forward a definition of the size limit
belonging to the headers for HTTP requests. In relation to this, the CPDoS attacks
of the HHO type takes place in places where the web application specifically
accepts larger size for the header rather than the origin server.
Figure-4: HHO CPDoS Attack
(Source- Prabadevi et al. 2019)
4. Performing CPDoS exploit and solutions:
CPDoS exploits can be performed in three different variations that exists (AbdAllah,
Zulkernine and Hassanein 2018). The three varieties of CPDoS attacks are,
i) HTTP Header Oversize (HHO) - HTTP header has the primary inclusion of vital
information that belongs to the intermediary systems along with the web servers.
This has the primary inclusion of header fields or the meta data that is related to
the caches present on the media types that are supported by the clients such as the
likes of languages as well as encodings (Prabadevi et al. 2019). In regards to this,
the standard of the HTTP does not put forward a definition of the size limit
belonging to the headers for HTTP requests. In relation to this, the CPDoS attacks
of the HHO type takes place in places where the web application specifically
accepts larger size for the header rather than the origin server.
Figure-4: HHO CPDoS Attack
(Source- Prabadevi et al. 2019)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CDN AND CPDOS
ii) HTTP Meta Character (HMC) – this particular attack works in a similar way to
that of the HHO CPDoS attack. However, instead of sending a header that has
been oversized, this particular attack makes tries and bypasses a cache that
consists of the requested header also having the containment of the meta character
(Sakhawat et al. 2018). Meta characters are of the likes such as \n, \r or \a.
Figure-5: HMC CPDoS Attack
(Source- Sakhawat et al. 2018)
iii) HTTP Method Override Attack (HMO)- this particular attack provisions with
multiple methods belonging to the HTTP to that of the web servers as well as the
clients for carrying out transactions through the use of internet. GET, DELETE,
POST as well as PUT are the commonly used methods of HTTP within the
internet based applications along with the REST based services on the web
(Prabadevi, Jeyanthi and Abraham 2020). In this, multiply existing medium such
as the likes of load balancers, firewalls, the proxies as well as the caches are
provisioned support from the GET as well as the POST.
ii) HTTP Meta Character (HMC) – this particular attack works in a similar way to
that of the HHO CPDoS attack. However, instead of sending a header that has
been oversized, this particular attack makes tries and bypasses a cache that
consists of the requested header also having the containment of the meta character
(Sakhawat et al. 2018). Meta characters are of the likes such as \n, \r or \a.
Figure-5: HMC CPDoS Attack
(Source- Sakhawat et al. 2018)
iii) HTTP Method Override Attack (HMO)- this particular attack provisions with
multiple methods belonging to the HTTP to that of the web servers as well as the
clients for carrying out transactions through the use of internet. GET, DELETE,
POST as well as PUT are the commonly used methods of HTTP within the
internet based applications along with the REST based services on the web
(Prabadevi, Jeyanthi and Abraham 2020). In this, multiply existing medium such
as the likes of load balancers, firewalls, the proxies as well as the caches are
provisioned support from the GET as well as the POST.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
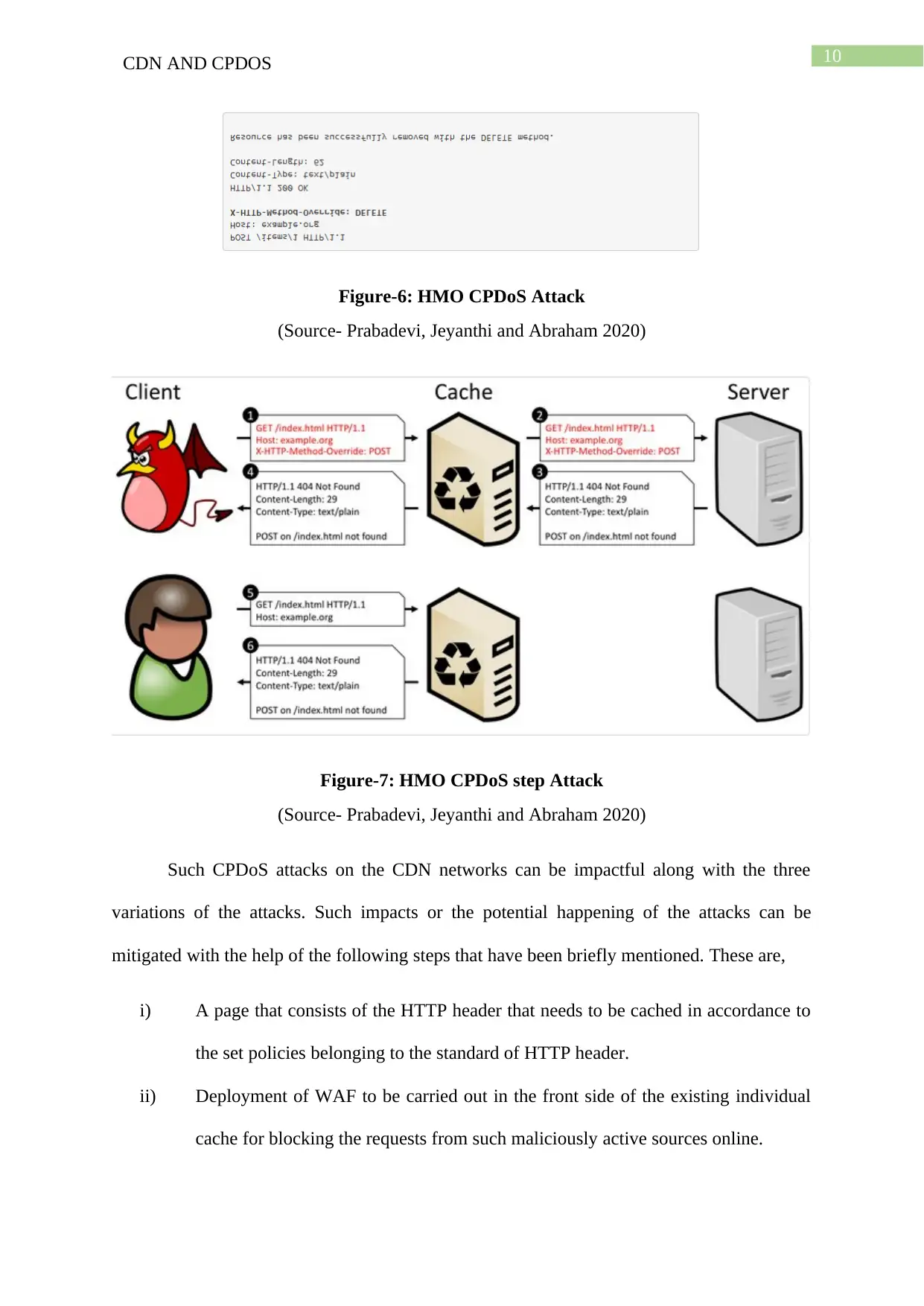
10CDN AND CPDOS
Figure-6: HMO CPDoS Attack
(Source- Prabadevi, Jeyanthi and Abraham 2020)
Figure-7: HMO CPDoS step Attack
(Source- Prabadevi, Jeyanthi and Abraham 2020)
Such CPDoS attacks on the CDN networks can be impactful along with the three
variations of the attacks. Such impacts or the potential happening of the attacks can be
mitigated with the help of the following steps that have been briefly mentioned. These are,
i) A page that consists of the HTTP header that needs to be cached in accordance to
the set policies belonging to the standard of HTTP header.
ii) Deployment of WAF to be carried out in the front side of the existing individual
cache for blocking the requests from such maliciously active sources online.
Figure-6: HMO CPDoS Attack
(Source- Prabadevi, Jeyanthi and Abraham 2020)
Figure-7: HMO CPDoS step Attack
(Source- Prabadevi, Jeyanthi and Abraham 2020)
Such CPDoS attacks on the CDN networks can be impactful along with the three
variations of the attacks. Such impacts or the potential happening of the attacks can be
mitigated with the help of the following steps that have been briefly mentioned. These are,
i) A page that consists of the HTTP header that needs to be cached in accordance to
the set policies belonging to the standard of HTTP header.
ii) Deployment of WAF to be carried out in the front side of the existing individual
cache for blocking the requests from such maliciously active sources online.

11CDN AND CPDOS
iii) The last effective method that can be deployed for carrying out the activity of
excluding the pages of error from the method of caching.
5. Impact of CPDoS:
Once the page showing error has come up, the CDN network gets distributed to all the
edge servers and the relative location around the globe. The map that follows this discussion
puts forward a proper illustration of the distance to which the error page has been distributed
in regards to multiple locations of the edge servers throughout the entire CDN network
(Meghana, Subashri and Vimal 2017). However, not all the existing edge servers get
impacted by every CPDoS attacks, referring to the fact that the clients at those particular
locations of the edge servers have been served with the genuine page that had been initially
searched by the respective visitors in regards to obtain resources from the particular website.
iii) The last effective method that can be deployed for carrying out the activity of
excluding the pages of error from the method of caching.
5. Impact of CPDoS:
Once the page showing error has come up, the CDN network gets distributed to all the
edge servers and the relative location around the globe. The map that follows this discussion
puts forward a proper illustration of the distance to which the error page has been distributed
in regards to multiple locations of the edge servers throughout the entire CDN network
(Meghana, Subashri and Vimal 2017). However, not all the existing edge servers get
impacted by every CPDoS attacks, referring to the fact that the clients at those particular
locations of the edge servers have been served with the genuine page that had been initially
searched by the respective visitors in regards to obtain resources from the particular website.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





