Comprehensive Report on Managing and Controlling ICT Project Risks
VerifiedAdded on 2024/06/27
|18
|3712
|249
Report
AI Summary
This report provides a comprehensive overview of managing and controlling risks in ICT projects. It covers the five stages of the risk management process, emphasizing the importance of the initial identification phase. The report discusses how organizational planning documents and risk policies aid in risk identification, providing examples of internal and external risks. It details the outcomes of risk identification and analysis steps, along with response strategies for common IT project risks like unclear scope, technology changes, and lack of planning. Different risk managing methods, the use of risk matrices, and the importance of risk registers and management plans are explained. The report also addresses impact analysis, risk treatment actions, risk escalation, audits, corrective and preventive actions, contingency plans, and the outcomes of risk monitoring. Furthermore, it discusses change requests, external influential factors, risk reviews, and the necessity of stakeholder involvement in risk management planning. This document is available on Desklib, a platform offering a variety of study tools and resources for students.

Manage and control ICT project risks –
Part A
1
Part A
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction......................................................................................................................................3
1. What are the five stages of Risk management process? Why the first step is important from an
organisational point of view?...........................................................................................................4
2. Why organisational Planning document and Risk policies are helpful in the risk identifications
process? Explain in brief with examples if possible........................................................................5
3. Give a few examples of internal and external risks for an ICT project. Give at least five
examples for each............................................................................................................................6
4. What are the outcome/output for each of the following Risk management steps?.....................7
Risk Identifications......................................................................................................................7
Risk Analysis...............................................................................................................................7
5. What will be your risk response strategy for an IT project you are working in for each of the
following risks and why?.................................................................................................................8
Confusion and unclear scope definition.......................................................................................8
Sudden change in ICT technology...............................................................................................8
Not having any risk management plan or contingency plan........................................................8
6. What are the different risk managing methods? Explain in brief................................................9
7. What is a risk matrix? How do you calculate Total risk from that matrix?...............................10
8. What is a risk register? What are the typical information stored in a risk register?..................10
9. What is a risk management plan? Who would you involve in preparing a risk management
plan and why?................................................................................................................................10
2
Introduction......................................................................................................................................3
1. What are the five stages of Risk management process? Why the first step is important from an
organisational point of view?...........................................................................................................4
2. Why organisational Planning document and Risk policies are helpful in the risk identifications
process? Explain in brief with examples if possible........................................................................5
3. Give a few examples of internal and external risks for an ICT project. Give at least five
examples for each............................................................................................................................6
4. What are the outcome/output for each of the following Risk management steps?.....................7
Risk Identifications......................................................................................................................7
Risk Analysis...............................................................................................................................7
5. What will be your risk response strategy for an IT project you are working in for each of the
following risks and why?.................................................................................................................8
Confusion and unclear scope definition.......................................................................................8
Sudden change in ICT technology...............................................................................................8
Not having any risk management plan or contingency plan........................................................8
6. What are the different risk managing methods? Explain in brief................................................9
7. What is a risk matrix? How do you calculate Total risk from that matrix?...............................10
8. What is a risk register? What are the typical information stored in a risk register?..................10
9. What is a risk management plan? Who would you involve in preparing a risk management
plan and why?................................................................................................................................10
2

10. What is an impact analysis? When and why it is done for risk management in a project?.....11
11. What are some of the likely actions you may take in an IT project as a part of risk treatment?
Your answer will depend on the risks you have identified for example.......................................11
12. Apart from the standard risk response strategies, often a strategy is used called “Risk
escalation”. What that does mean and why it is important for the project manager?....................11
13. What is a risk audit? Who perform risk audit and why it is necessary?..................................12
14. Explain the following two in relation to risk monitoring process:..........................................12
Corrective actions......................................................................................................................12
Preventive actions......................................................................................................................12
15. What is a contingency plan? Why and when it is prepared in the risk management cycle?...12
16. What are the typical outcomes of the risk monitoring process? Explain any one of those in
brief from an IT project if you can................................................................................................13
17. What is a change request? As project manager of an IT project, under what circumstances
you may need to prepare a change request? Give examples.........................................................13
18. Give examples of a few external influential factors which requires a risk management plan to
be updated. Explain one of those in brief......................................................................................13
19. What is risk review? Why and when reviews are done?.........................................................14
20. Explain why stakeholders’ involvement is necessary in risk management planning process
and why sign off is necessary for the plan prepared?....................................................................14
Conclusion.....................................................................................................................................15
References......................................................................................................................................16
3
11. What are some of the likely actions you may take in an IT project as a part of risk treatment?
Your answer will depend on the risks you have identified for example.......................................11
12. Apart from the standard risk response strategies, often a strategy is used called “Risk
escalation”. What that does mean and why it is important for the project manager?....................11
13. What is a risk audit? Who perform risk audit and why it is necessary?..................................12
14. Explain the following two in relation to risk monitoring process:..........................................12
Corrective actions......................................................................................................................12
Preventive actions......................................................................................................................12
15. What is a contingency plan? Why and when it is prepared in the risk management cycle?...12
16. What are the typical outcomes of the risk monitoring process? Explain any one of those in
brief from an IT project if you can................................................................................................13
17. What is a change request? As project manager of an IT project, under what circumstances
you may need to prepare a change request? Give examples.........................................................13
18. Give examples of a few external influential factors which requires a risk management plan to
be updated. Explain one of those in brief......................................................................................13
19. What is risk review? Why and when reviews are done?.........................................................14
20. Explain why stakeholders’ involvement is necessary in risk management planning process
and why sign off is necessary for the plan prepared?....................................................................14
Conclusion.....................................................................................................................................15
References......................................................................................................................................16
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
The whole concept is based upon the risk analysis and risk evaluation ways that have been based
upon the overall factors that might be involved in the development of software’s in ICT and as
per that there has been reviews and audits that have been planned simultaneously. There has been
various meetings and conferences that have been prepared so as to see the reflection in the
development of the software and use it in future. The reviews have highlighted various measures
to be taken on each step so as to make sure most of the issues are being resolved on the way of
development of the softwares. There has been effective involvement of the stakeholders and the
respective changes made according to that has also been seen here.
5
The whole concept is based upon the risk analysis and risk evaluation ways that have been based
upon the overall factors that might be involved in the development of software’s in ICT and as
per that there has been reviews and audits that have been planned simultaneously. There has been
various meetings and conferences that have been prepared so as to see the reflection in the
development of the software and use it in future. The reviews have highlighted various measures
to be taken on each step so as to make sure most of the issues are being resolved on the way of
development of the softwares. There has been effective involvement of the stakeholders and the
respective changes made according to that has also been seen here.
5

1. What are the five stages of Risk management process? Why is the first step important
from an organizational point of view?
Step 1- Identification of risk- In this method, the risk is identified and seen effectively the
various reasons for the occurrence of the risk and seeing the effect of the same on the scenario. It
is the most important step as the whole planning is based upon this analysis.
Step 2- Analyze the risk – Here the risk is analyzed and seen the relevance and consequence of
each risk.
Step 3- Rank the risk- This decides the severity and importance of the risk in the evaluation of
the same further process are done.
Step 4- Treat the risk- Strategies are made to resolve the issues creating risks.
Step 5- Monitor and review the risk- Periodic monitoring and evaluation is done to avoid the
same in future (Dellinger, 2013).
6
from an organizational point of view?
Step 1- Identification of risk- In this method, the risk is identified and seen effectively the
various reasons for the occurrence of the risk and seeing the effect of the same on the scenario. It
is the most important step as the whole planning is based upon this analysis.
Step 2- Analyze the risk – Here the risk is analyzed and seen the relevance and consequence of
each risk.
Step 3- Rank the risk- This decides the severity and importance of the risk in the evaluation of
the same further process are done.
Step 4- Treat the risk- Strategies are made to resolve the issues creating risks.
Step 5- Monitor and review the risk- Periodic monitoring and evaluation is done to avoid the
same in future (Dellinger, 2013).
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2. Why organizational Planning document and Risk policies are helpful in the risk
identifications process? Explain in brief with examples if possible
The risk has been analyzed and rated as per the documented policies and practices that have been
designed by professionals in order to give the company an idea and respective framework in
order to let them work upon that effectively. In the ICT it is required to see the software policies
and documentation before being used in the development and analysis of risk in the process. For
example, ISO is the standard used in the security and other services to check the methods used in
the safety of the documents.
7
identifications process? Explain in brief with examples if possible
The risk has been analyzed and rated as per the documented policies and practices that have been
designed by professionals in order to give the company an idea and respective framework in
order to let them work upon that effectively. In the ICT it is required to see the software policies
and documentation before being used in the development and analysis of risk in the process. For
example, ISO is the standard used in the security and other services to check the methods used in
the safety of the documents.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
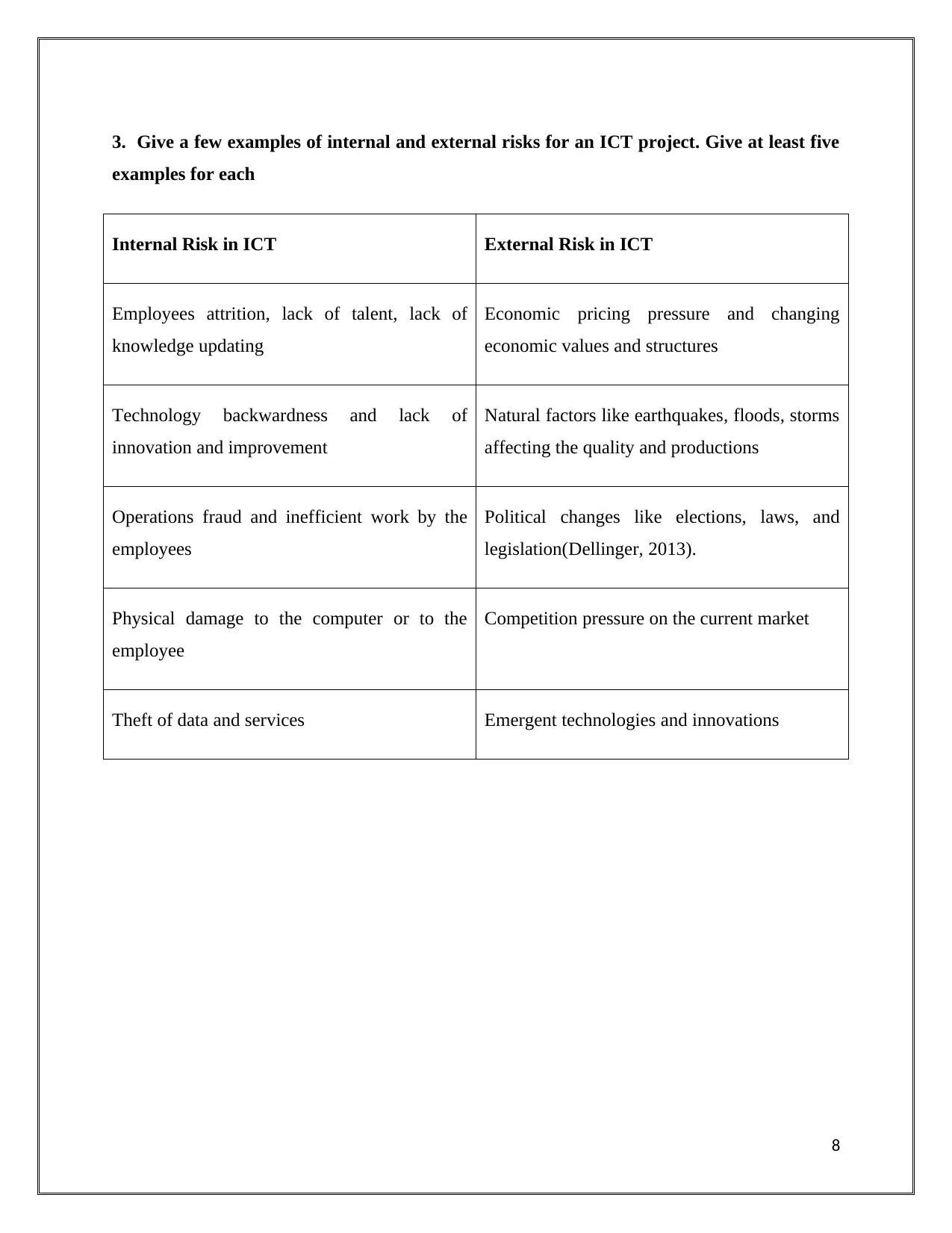
3. Give a few examples of internal and external risks for an ICT project. Give at least five
examples for each
Internal Risk in ICT External Risk in ICT
Employees attrition, lack of talent, lack of
knowledge updating
Economic pricing pressure and changing
economic values and structures
Technology backwardness and lack of
innovation and improvement
Natural factors like earthquakes, floods, storms
affecting the quality and productions
Operations fraud and inefficient work by the
employees
Political changes like elections, laws, and
legislation(Dellinger, 2013).
Physical damage to the computer or to the
employee
Competition pressure on the current market
Theft of data and services Emergent technologies and innovations
8
examples for each
Internal Risk in ICT External Risk in ICT
Employees attrition, lack of talent, lack of
knowledge updating
Economic pricing pressure and changing
economic values and structures
Technology backwardness and lack of
innovation and improvement
Natural factors like earthquakes, floods, storms
affecting the quality and productions
Operations fraud and inefficient work by the
employees
Political changes like elections, laws, and
legislation(Dellinger, 2013).
Physical damage to the computer or to the
employee
Competition pressure on the current market
Theft of data and services Emergent technologies and innovations
8

4. What is the outcome/output for each of the following Risk management steps?
Risk Identifications
Risk Analysis
a) Risk Identifications- The risk identification helps in the identification of the causes that
have been causing the risk and the relative effect has been seen on the quality of the
production. The identification helps in identifying the methods that have been used in
order to see the effective strategy and the methods best fit to resolve them.
b) Risk Analysis- This helps in the analysis of the severity and the relative effect on the
livelihood and ICT development. Based upon there has been a strategy that has been
made in order to resolve the risk and take protective measures for future (Dellinger,
2013).
9
Risk Identifications
Risk Analysis
a) Risk Identifications- The risk identification helps in the identification of the causes that
have been causing the risk and the relative effect has been seen on the quality of the
production. The identification helps in identifying the methods that have been used in
order to see the effective strategy and the methods best fit to resolve them.
b) Risk Analysis- This helps in the analysis of the severity and the relative effect on the
livelihood and ICT development. Based upon there has been a strategy that has been
made in order to resolve the risk and take protective measures for future (Dellinger,
2013).
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

5. What will be your risk response strategy for an IT project you are working in for each of
the following risks and why?
Confusion and unclear scope definition
A sudden change in ICT technology
Not having any risk management plan or contingency plan
Confusion and unclear scope definition- Monitor and prepare the risk assessment
methods and techniques to identify the meaning of the respective ICT tool.
A sudden change in ICT technology- Mitigation of the work and making appropriate
plans to deal with the technology and making future technologies aware and updated as
per that.
Not having any risk management plan or contingency plan- Acceptance of the lack of
knowledge in the current issue and then monitor and prepare a plan to manage the risk in
the future and avoid such issues in future respectively. This develops future ICT
strategies as well (Massad, 2013).
10
the following risks and why?
Confusion and unclear scope definition
A sudden change in ICT technology
Not having any risk management plan or contingency plan
Confusion and unclear scope definition- Monitor and prepare the risk assessment
methods and techniques to identify the meaning of the respective ICT tool.
A sudden change in ICT technology- Mitigation of the work and making appropriate
plans to deal with the technology and making future technologies aware and updated as
per that.
Not having any risk management plan or contingency plan- Acceptance of the lack of
knowledge in the current issue and then monitor and prepare a plan to manage the risk in
the future and avoid such issues in future respectively. This develops future ICT
strategies as well (Massad, 2013).
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

6. What are the different risk managing methods? Explain in brief
The different risk management methods are-
Avoidance- this method is used to stop any source or any method that has been providing
jeopardy to the business.
Reduction- This step is taken to minimize the effects of the causes and related ways that have
been used in order to reduce the factors and prioritizing the things effectively.
Transfer- This step is used to transfer the risk causing the element to external or other resources
and taking others help in the same.
Acceptance- This method is used to accept the current features and respectively use the same in
the development of new sources and strategies in the same.
11
The different risk management methods are-
Avoidance- this method is used to stop any source or any method that has been providing
jeopardy to the business.
Reduction- This step is taken to minimize the effects of the causes and related ways that have
been used in order to reduce the factors and prioritizing the things effectively.
Transfer- This step is used to transfer the risk causing the element to external or other resources
and taking others help in the same.
Acceptance- This method is used to accept the current features and respectively use the same in
the development of new sources and strategies in the same.
11

7. What is a risk matrix? How do you calculate Total risk from that matrix?
The risk management matrix helps in analyzing the respective ways in which the impact on the
likelihood has been conducted and seen. This may range from the low , medium and high
intensity in which they can be used in order to see the respective effect of the same on the
analysis of risk involved in the ICT software and technology. There may be different versions of
the same or different companies who have been using it in the analysis and ranking of their risks
so to make strategies based upon them in future.
8. What is a risk register? What is the typical information stored in a risk register?
Risk registers are sometimes called risk logs that have been used in order to keep a log of the
risks. They are mostly used from the beginning of the activity and is thus keeping records in the
place to see the effective way in which it can be used in the going forward in the overall
development and analysis of the same in the risk evaluation and development .they might use
qualitative or quantitate risk evaluation of the same in order to see the same in the business
improvement. They are very effective in monitoring and controlling the risk (Massad, 2013).
9. What is a risk management plan? Who would you involve in preparing a risk
management plan and why?
Risk management plan is the plan that has been constructed after the risk is identified of on the
procurement of any risk. It involves various features that have been used in order to identify the
risk, analyze the same and using them in the effective utilization of resources so as to minimize
the effects and occurrence of the same in future. The management plan includes all the decoding
function and the senior members, along with there has been other planning and implementation
managers in the organization. After that the plan also involves all the operational and
implementing work force, they work on the achievement of the goals of the company.
12
The risk management matrix helps in analyzing the respective ways in which the impact on the
likelihood has been conducted and seen. This may range from the low , medium and high
intensity in which they can be used in order to see the respective effect of the same on the
analysis of risk involved in the ICT software and technology. There may be different versions of
the same or different companies who have been using it in the analysis and ranking of their risks
so to make strategies based upon them in future.
8. What is a risk register? What is the typical information stored in a risk register?
Risk registers are sometimes called risk logs that have been used in order to keep a log of the
risks. They are mostly used from the beginning of the activity and is thus keeping records in the
place to see the effective way in which it can be used in the going forward in the overall
development and analysis of the same in the risk evaluation and development .they might use
qualitative or quantitate risk evaluation of the same in order to see the same in the business
improvement. They are very effective in monitoring and controlling the risk (Massad, 2013).
9. What is a risk management plan? Who would you involve in preparing a risk
management plan and why?
Risk management plan is the plan that has been constructed after the risk is identified of on the
procurement of any risk. It involves various features that have been used in order to identify the
risk, analyze the same and using them in the effective utilization of resources so as to minimize
the effects and occurrence of the same in future. The management plan includes all the decoding
function and the senior members, along with there has been other planning and implementation
managers in the organization. After that the plan also involves all the operational and
implementing work force, they work on the achievement of the goals of the company.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





