Design Framework for Event-Triggered Control Systems Under DoS Attacks
VerifiedAdded on 2022/11/13
|13
|17036
|378
Report
AI Summary
This research paper, published in IEEE TRANSACTIONS ON CONTROL OF NETWORK SYSTEMS, VOL. 4, NO. 1, MARCH 2017, introduces a systematic design framework for output-based dynamic event-triggered control (ETC) systems under denial-of-service (DoS) attacks. The authors, V. S. Dolk, P. Tesi, C. De Persis, and W. P. M. H. Heemels, address the vulnerability of networked control systems (NCSs) to DoS attacks, which disrupt communication channels. The proposed ETC scheme aims to tolerate DoS signals characterized by frequency and duration properties, ensuring stability, performance, and Zeno-freeness. The paper explores the tradeoffs between performance, robustness to DoS attacks, and communication resource utilization. It provides a detailed NCS model, problem statement, and design conditions for dynamic event-triggered strategies. The research highlights the importance of output-based control, which is particularly relevant in practical scenarios where full state information may not be available. The design methodology is demonstrated through a case study of cooperative adaptive cruise control, illustrating the practical implications of the proposed framework. The paper's findings contribute to the advancement of resilient and resource-aware control strategies in cyber-physical systems.

IEEE TRANSACTIONS ON CONTROL OF NETWORK SYSTEMS, VOL. 4, NO. 1, MARCH 2017 93
Event-Triggered Control Systems Under
Denial-of-Service Attacks
V. S. Dolk, P. Tesi, C. De Persis, and W. P. M. H. Heemels, Fellow, IEEE
Abstract—In this paper, we propose a systematic design frame-
work for output-based dynamic event-triggered control (ETC) sys-
tems under denial-of-service (DoS) attacks. These malicious DoS
attacks are intended to interfere with the communication chan-
nel causing periods in time at which transmission of measurement
data is impossible. We show that the proposed ETC scheme, if well
designed, can tolerate a class of DoS signals characterized by fre-
quency and duration properties without jeopardizing the stability,
performance and Zeno-freeness of the ETC system. In fact, the
design procedure of the ETC condition allows tradeoffs between
performance, robustness to DoS attacks, and utilization of commu-
nication resources. The main results will be illustrated by means
of a numerical example.
Index Terms—Denial-of-service attacks, dynamic output-
based control, event-triggered control, input-to-output stabil-
ity, networked control systems, resilient control, resource-aware
control.
I. INTRODUCTION
THE field of cyber-physical systems (CPS) and, in particu-
lar, networked control systems (NCSs) is rapidly emerging
due to a wide range of potential applications. However, there is a
strong need for novel analysis and synthesis tools in control the-
ory to guarantee safe and secure operation despite the presence
of possible malicious attacks [2]. Especially for safety-critical
applications, such as intelligent transport systems and power
grids, this is of high importance and requires the integration of
cybersecurity and control strategies.
One of the main concerns in NCSs with respect to security is
deception attacks and denial-of-service (DoS) attacks. Decep-
tion attacks are intended to tamper transmitted data packages
causing false feedback information, see for more details, e.g.,
Manuscript received September 30, 2015; revised July 1, 2016; accepted
September 7, 2016. Date of publication September 23, 2016; date of current
version March 16, 2017. A preliminary and much shorter version of this work
was accepted for presentation at the 54th IEEE Conference on Decision and
Control [1]. This work was supported in part by the STW project “Integrated
design approach for safety-critical real-time automotive systems” (No. 12698)
and in part by the Innovational Research Incentives Scheme under VICI Grant
“Wireless control systems: A new frontier in automation” (No. 11382) awarded
by NWO (The Netherlands Organization for Scientific Research) and STW
(Dutch Technology Foundation). Recommended by Associate Editor P. Cheng.
V. Dolk and M. Heemels are with the Control Systems Technology group,
Dept. of Mechanical Eng., Eindhoven University of Technology, Eindhoven
5600 MB, The Netherlands (e-mail: v.s.dolk@tue.nl; m.heemels@tue.nl).
C. De Persis and P. Tesi are with Faculty of Mathematics and Natural Sci-
ences, University of Groningen, The Netherlands (e-mail: c.de.persis@rug.nl;
p.tesi@rug.nl).
Digital Object Identifier 10.1109/TCNS.2016.2613445
[3] and the reference therein, whereas DoS attacks, induced by
radio-interference signals (also referred to as jamming signals),
typically cause periods in time at which communication is not
possible, see, for instance, [4]. In this paper, we focus on the
latter type of attack. To be more concrete, we are interested in
creating control strategies that render the overall closed-loop
system resilient to DoS attacks which occur according to some
unknown strategy with the aim of impeding the communication
of sensor measurements.
In addition to this resilience requirement described before,
the control strategy needs to deal with the inherent imperfec-
tions of networked communication. Communication in NCSs
is, in general, packet based and thus measurement data can only
be transmitted at discrete time instants. Moreover, especially
since a communication network is often shared with multiple
devices, the communication resources are restricted. Hence, a
resource-aware and resilient control approach, which aims to
only schedule the transmission of data when needed to maintain
the desired stability and performance criteria, is a requisite. In a
nutshell, the control problem addressed in this paper is to design
a control law that limits the transmission of sensor data while
realizing desired closed-loop stability and performance criteria
despite the presence of DoS attacks.
The proposed solution to this challenging design problem is
to adopt an event-triggered control (ETC) strategy, in which
transmission times are determined online by means of well-
designed triggering rules which rely on, for example, sensor
measurements of the system. The introduction of this feedback
in the sampling process enables ETC schemes to reduce the uti-
lization of communication resources without jeopardizing con-
trol performance. In contrast to periodic time-triggered control
schemes, ETC schemes aim to only transmit data when needed
to maintain desired closed-loop properties. However, the ma-
jority of the literature on ETC strategies does not consider cy-
bersecurity issues, such as DoS attacks. Notable exceptions are
[5]–[7]. In [7], a method was proposed to identify features of
DoS attacks in order to improve the scheduling of transmissions
in the sense that the DoS periods are being avoided. However,
this approach turns out to be effective only when the DoS attacks
are “well-structured” over time, for example, in case of a peri-
odic jamming signal. In [5] and [6], a more general and more
realistic DoS attack model is used based on the frequency and
duration of the attacker’s actions. These constraints are quite
natural, as in reality, also the jammers resources are not infi-
nite and several provisions can be taken to mitigate these DoS
attacks. In addition, no assumptions regarding the underlying
2325-5870 © 2016 IEEE. Personal use is permitted, but republication/redistribution requires IEEE permission.
See http://www.ieee.org/publications standards/publications/rights/index.html for more information.
Event-Triggered Control Systems Under
Denial-of-Service Attacks
V. S. Dolk, P. Tesi, C. De Persis, and W. P. M. H. Heemels, Fellow, IEEE
Abstract—In this paper, we propose a systematic design frame-
work for output-based dynamic event-triggered control (ETC) sys-
tems under denial-of-service (DoS) attacks. These malicious DoS
attacks are intended to interfere with the communication chan-
nel causing periods in time at which transmission of measurement
data is impossible. We show that the proposed ETC scheme, if well
designed, can tolerate a class of DoS signals characterized by fre-
quency and duration properties without jeopardizing the stability,
performance and Zeno-freeness of the ETC system. In fact, the
design procedure of the ETC condition allows tradeoffs between
performance, robustness to DoS attacks, and utilization of commu-
nication resources. The main results will be illustrated by means
of a numerical example.
Index Terms—Denial-of-service attacks, dynamic output-
based control, event-triggered control, input-to-output stabil-
ity, networked control systems, resilient control, resource-aware
control.
I. INTRODUCTION
THE field of cyber-physical systems (CPS) and, in particu-
lar, networked control systems (NCSs) is rapidly emerging
due to a wide range of potential applications. However, there is a
strong need for novel analysis and synthesis tools in control the-
ory to guarantee safe and secure operation despite the presence
of possible malicious attacks [2]. Especially for safety-critical
applications, such as intelligent transport systems and power
grids, this is of high importance and requires the integration of
cybersecurity and control strategies.
One of the main concerns in NCSs with respect to security is
deception attacks and denial-of-service (DoS) attacks. Decep-
tion attacks are intended to tamper transmitted data packages
causing false feedback information, see for more details, e.g.,
Manuscript received September 30, 2015; revised July 1, 2016; accepted
September 7, 2016. Date of publication September 23, 2016; date of current
version March 16, 2017. A preliminary and much shorter version of this work
was accepted for presentation at the 54th IEEE Conference on Decision and
Control [1]. This work was supported in part by the STW project “Integrated
design approach for safety-critical real-time automotive systems” (No. 12698)
and in part by the Innovational Research Incentives Scheme under VICI Grant
“Wireless control systems: A new frontier in automation” (No. 11382) awarded
by NWO (The Netherlands Organization for Scientific Research) and STW
(Dutch Technology Foundation). Recommended by Associate Editor P. Cheng.
V. Dolk and M. Heemels are with the Control Systems Technology group,
Dept. of Mechanical Eng., Eindhoven University of Technology, Eindhoven
5600 MB, The Netherlands (e-mail: v.s.dolk@tue.nl; m.heemels@tue.nl).
C. De Persis and P. Tesi are with Faculty of Mathematics and Natural Sci-
ences, University of Groningen, The Netherlands (e-mail: c.de.persis@rug.nl;
p.tesi@rug.nl).
Digital Object Identifier 10.1109/TCNS.2016.2613445
[3] and the reference therein, whereas DoS attacks, induced by
radio-interference signals (also referred to as jamming signals),
typically cause periods in time at which communication is not
possible, see, for instance, [4]. In this paper, we focus on the
latter type of attack. To be more concrete, we are interested in
creating control strategies that render the overall closed-loop
system resilient to DoS attacks which occur according to some
unknown strategy with the aim of impeding the communication
of sensor measurements.
In addition to this resilience requirement described before,
the control strategy needs to deal with the inherent imperfec-
tions of networked communication. Communication in NCSs
is, in general, packet based and thus measurement data can only
be transmitted at discrete time instants. Moreover, especially
since a communication network is often shared with multiple
devices, the communication resources are restricted. Hence, a
resource-aware and resilient control approach, which aims to
only schedule the transmission of data when needed to maintain
the desired stability and performance criteria, is a requisite. In a
nutshell, the control problem addressed in this paper is to design
a control law that limits the transmission of sensor data while
realizing desired closed-loop stability and performance criteria
despite the presence of DoS attacks.
The proposed solution to this challenging design problem is
to adopt an event-triggered control (ETC) strategy, in which
transmission times are determined online by means of well-
designed triggering rules which rely on, for example, sensor
measurements of the system. The introduction of this feedback
in the sampling process enables ETC schemes to reduce the uti-
lization of communication resources without jeopardizing con-
trol performance. In contrast to periodic time-triggered control
schemes, ETC schemes aim to only transmit data when needed
to maintain desired closed-loop properties. However, the ma-
jority of the literature on ETC strategies does not consider cy-
bersecurity issues, such as DoS attacks. Notable exceptions are
[5]–[7]. In [7], a method was proposed to identify features of
DoS attacks in order to improve the scheduling of transmissions
in the sense that the DoS periods are being avoided. However,
this approach turns out to be effective only when the DoS attacks
are “well-structured” over time, for example, in case of a peri-
odic jamming signal. In [5] and [6], a more general and more
realistic DoS attack model is used based on the frequency and
duration of the attacker’s actions. These constraints are quite
natural, as in reality, also the jammers resources are not infi-
nite and several provisions can be taken to mitigate these DoS
attacks. In addition, no assumptions regarding the underlying
2325-5870 © 2016 IEEE. Personal use is permitted, but republication/redistribution requires IEEE permission.
See http://www.ieee.org/publications standards/publications/rights/index.html for more information.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

94 IEEE TRANSACTIONS ON CONTROL OF NETWORK SYSTEMS, VOL. 4, NO. 1, MARCH 2017
jamming strategy of the attacker are made. Moreover, in con-
trast to stochastic packet dropout models, this characterization
enables capturing a wide class of DoS attacks, including trivial,
periodic, random, and protocol-aware jamming attacks [4], [8].
A drawback of the approaches in [5]–[7] is that these ap-
proaches are restricted to the case of static state feedback which
requires the availability of full state information. Clearly, in
practice, this is a strong assumption as only in rare cases the full
state variable is available for feedback. For this reason, it is of
interest to study event-triggered NCSs subject to DoS attacks
that rely on output measurements only. To the best of our knowl-
edge, the output feedback case in the context of DoS attacks has
never been addressed in the literature. This is not surprising as,
especially in the presence of disturbances, extending existing
ETC schemes that rely on state feedback to the output-based
ETC schemes (even without DoS attacks) is far from trivial as
shown in [9] and [10]. Therefore, we propose in this paper a
novel systematic design methodology for output-based resilient
and resource-aware dynamic ETC strategies for a class of non-
linear systems subject to disturbances. We prove that under the
proposed design conditions, the resulting closed-loop system is
input-to-output stable with finite-induced L ∞ -gains (peak-to-
peak gains). Interestingly, this result is of independent interest
in the context of switched systems under average-dwell time
conditions, see also [11].
To enable practical implementation of the ETC scheme, it
is important to guarantee that the time between consecutive
transmission attempts is strictly positive and preferably lower
bounded by a positive constant. By exploiting the Zeno-freeness
property of the ETC scheme presented in [12] and [13], we show
that for the proposed ETC scheme, such a positive minimal-
interevent time (MIET) exists by design despite the presence of
disturbances and/or DoS attacks. By employing the DoS char-
acterization as presented in [5] and [6], the obtained results hold
for wide classes of relevant DoS attacks. As a matter of fact,
as already mentioned, no assumptions regarding the underlying
strategy of the attacker are needed, which makes the proposed
scheme applicable in many contexts. The design procedure is
demonstrated on a case study of cooperative adaptive cruise
control. The numerical example reveals and illustrates a trade-
off between robustness with respect to DoS attacks, network
utilization, and performance guarantees.
The remainder of this paper is organized as follows. After
presenting the necessary preliminaries and notational conven-
tions in Section II, we introduce the event-triggered networked
control setup subject to DoS attacks in Section III leading to
the problem statement. This event-triggered NCS setup is for-
malized in Section IV by means of hybrid models resulting in
a mathematically rigorous problem formulation. In Section V,
we characterize DoS attacks in terms of frequency and duration
and, based on this characterization, we provide design condi-
tions for the proposed dynamic event-triggered strategy such
that stability and performance properties are satisfied. The ob-
tained design framework is illustrated by means of a numerical
example in Section VI. Finally, we provide the concluding re-
marks in Section VII.
Fig. 1. Schematic representation of the event-triggered NCS considered in
this paper which consists of the interconnection of P, C, and N and where the
transmission instants are determined by an event-triggering mechanism (ETM).
Moreover, we assume an acknowledgement scheme is available, meaning that
the ETM has knowledge about the reception of packages at the controller side.
II. DEFINITIONS AND PRELIMINARIES
The following notational conventions will be used in this pa-
per. N denotes the set of all non-negative integers, N>0 is the
set of all positive integers, R is the field of all real numbers and
R0 is the set of all non-negative reals. For N ∈ N, we write
the set {1, 2, . . . , N }as ¯N . For N vectors xi ∈ Rni , i ∈ ¯N , we
denote the vector obtained by stacking all vectors in one (col-
umn) vector x ∈ Rn with n = N
i=1 ni by (x1, x2, . . . , xN ) ,
that is, (x1, x2, . . . , xN ) = x1 x2 · · · xN . The vec-
tors in RN consisting of all ones and zeros, are denoted by
1N and 0N , respectively. By | · |and ·, · , we denote the Eu-
clidean norm and the usual inner product of real vectors, re-
spectively. For a real symmetric matrix A, λmax(A) denotes
the largest eigenvalue of A. I N denotes the identity matrix
of dimension N × N and if N is clear from the context, we
write I . A function α : R0 → R 0 is said to be of class K
if it is continuous, strictly increasing, and α(0) = 0. It is said
to be of class K ∞ if it is of class K and it is unbounded. A
continuous function β : R0 × R0 → R 0 is said to be of
class KL if, for each fixed s, the mapping r → β(r, s) be-
longs to class K , and for each fixed r, the mapping β(r, s)
is decreasing with respect to s and β(r, s) → 0as s → ∞ . A
continuous function γ : R0 × R0 × R0 → R 0 is said to
be of class KLL if, for each r 0 , γ(·, ·, r)and γ(·, r, ·)be-
long to class KL . A function f : R n → R n is said to be lo-
cally Lipschitz continuous if for each x0 ∈ Rn there exist con-
stants δ > 0and L > 0 such that for all x ∈ Rn we have that
|x − x0| δ ⇒ |f (x) − f (x 0)| L|x − x 0|.
III. NCS MODEL AND PROBLEM STATEMENT
In this section, we present the networked control setup and the
dynamic event-triggering mechanism employed by this NCS.
Moreover, we describe how this NCS is affected by DoS at-
tacks. Based on these descriptions, we formulate the problem
statement.
A. Networked Control Configuration
Consider the feedback control configuration depicted in
Fig. 1. In this configuration, the sensor measurements of a plant
P are being transmitted to a (dynamic) output-based controller
jamming strategy of the attacker are made. Moreover, in con-
trast to stochastic packet dropout models, this characterization
enables capturing a wide class of DoS attacks, including trivial,
periodic, random, and protocol-aware jamming attacks [4], [8].
A drawback of the approaches in [5]–[7] is that these ap-
proaches are restricted to the case of static state feedback which
requires the availability of full state information. Clearly, in
practice, this is a strong assumption as only in rare cases the full
state variable is available for feedback. For this reason, it is of
interest to study event-triggered NCSs subject to DoS attacks
that rely on output measurements only. To the best of our knowl-
edge, the output feedback case in the context of DoS attacks has
never been addressed in the literature. This is not surprising as,
especially in the presence of disturbances, extending existing
ETC schemes that rely on state feedback to the output-based
ETC schemes (even without DoS attacks) is far from trivial as
shown in [9] and [10]. Therefore, we propose in this paper a
novel systematic design methodology for output-based resilient
and resource-aware dynamic ETC strategies for a class of non-
linear systems subject to disturbances. We prove that under the
proposed design conditions, the resulting closed-loop system is
input-to-output stable with finite-induced L ∞ -gains (peak-to-
peak gains). Interestingly, this result is of independent interest
in the context of switched systems under average-dwell time
conditions, see also [11].
To enable practical implementation of the ETC scheme, it
is important to guarantee that the time between consecutive
transmission attempts is strictly positive and preferably lower
bounded by a positive constant. By exploiting the Zeno-freeness
property of the ETC scheme presented in [12] and [13], we show
that for the proposed ETC scheme, such a positive minimal-
interevent time (MIET) exists by design despite the presence of
disturbances and/or DoS attacks. By employing the DoS char-
acterization as presented in [5] and [6], the obtained results hold
for wide classes of relevant DoS attacks. As a matter of fact,
as already mentioned, no assumptions regarding the underlying
strategy of the attacker are needed, which makes the proposed
scheme applicable in many contexts. The design procedure is
demonstrated on a case study of cooperative adaptive cruise
control. The numerical example reveals and illustrates a trade-
off between robustness with respect to DoS attacks, network
utilization, and performance guarantees.
The remainder of this paper is organized as follows. After
presenting the necessary preliminaries and notational conven-
tions in Section II, we introduce the event-triggered networked
control setup subject to DoS attacks in Section III leading to
the problem statement. This event-triggered NCS setup is for-
malized in Section IV by means of hybrid models resulting in
a mathematically rigorous problem formulation. In Section V,
we characterize DoS attacks in terms of frequency and duration
and, based on this characterization, we provide design condi-
tions for the proposed dynamic event-triggered strategy such
that stability and performance properties are satisfied. The ob-
tained design framework is illustrated by means of a numerical
example in Section VI. Finally, we provide the concluding re-
marks in Section VII.
Fig. 1. Schematic representation of the event-triggered NCS considered in
this paper which consists of the interconnection of P, C, and N and where the
transmission instants are determined by an event-triggering mechanism (ETM).
Moreover, we assume an acknowledgement scheme is available, meaning that
the ETM has knowledge about the reception of packages at the controller side.
II. DEFINITIONS AND PRELIMINARIES
The following notational conventions will be used in this pa-
per. N denotes the set of all non-negative integers, N>0 is the
set of all positive integers, R is the field of all real numbers and
R0 is the set of all non-negative reals. For N ∈ N, we write
the set {1, 2, . . . , N }as ¯N . For N vectors xi ∈ Rni , i ∈ ¯N , we
denote the vector obtained by stacking all vectors in one (col-
umn) vector x ∈ Rn with n = N
i=1 ni by (x1, x2, . . . , xN ) ,
that is, (x1, x2, . . . , xN ) = x1 x2 · · · xN . The vec-
tors in RN consisting of all ones and zeros, are denoted by
1N and 0N , respectively. By | · |and ·, · , we denote the Eu-
clidean norm and the usual inner product of real vectors, re-
spectively. For a real symmetric matrix A, λmax(A) denotes
the largest eigenvalue of A. I N denotes the identity matrix
of dimension N × N and if N is clear from the context, we
write I . A function α : R0 → R 0 is said to be of class K
if it is continuous, strictly increasing, and α(0) = 0. It is said
to be of class K ∞ if it is of class K and it is unbounded. A
continuous function β : R0 × R0 → R 0 is said to be of
class KL if, for each fixed s, the mapping r → β(r, s) be-
longs to class K , and for each fixed r, the mapping β(r, s)
is decreasing with respect to s and β(r, s) → 0as s → ∞ . A
continuous function γ : R0 × R0 × R0 → R 0 is said to
be of class KLL if, for each r 0 , γ(·, ·, r)and γ(·, r, ·)be-
long to class KL . A function f : R n → R n is said to be lo-
cally Lipschitz continuous if for each x0 ∈ Rn there exist con-
stants δ > 0and L > 0 such that for all x ∈ Rn we have that
|x − x0| δ ⇒ |f (x) − f (x 0)| L|x − x 0|.
III. NCS MODEL AND PROBLEM STATEMENT
In this section, we present the networked control setup and the
dynamic event-triggering mechanism employed by this NCS.
Moreover, we describe how this NCS is affected by DoS at-
tacks. Based on these descriptions, we formulate the problem
statement.
A. Networked Control Configuration
Consider the feedback control configuration depicted in
Fig. 1. In this configuration, the sensor measurements of a plant
P are being transmitted to a (dynamic) output-based controller

DOLK et al.: EVENT-TRIGGERED CONTROL SYSTEMS UNDER DENIAL-OF-SERVICE ATTACKS 95
C over a network N . The continuous-time plant P is given by
P : ˙xp = fp(xp, u, w)
y = gp(xp), (1)
where w ∈ Rnw is a disturbance input, xp ∈ Rnp is the state
vector, u ∈ Rnu is the control input and y ∈ Rny is the
measured output of plant P . The (dynamic) output-based con-
troller C is given by
C : ˙xc = fc(xc, ˆy)
u = gc(xc, ˆy), (2)
where xc ∈ Rnc denotes the controller state,ˆy ∈ Rny represents
the most recently received output measurement of the plant
at the controller C, and u ∈ Rnu is the controller output. The
performance output is given by z = q(x), where z ∈ Rnz and
x = (xp, xc).
Typically, the communication over the network N is packet
based, which implies that the output measurementsy can only be
transmitted at discrete instants in time, i.e., at times tj , j ∈ N,
satisfying 0 t 0 < t1 < t2 < . . .. Hence, at each transmission
instant tj , j ∈ N, the value of ˆy is updated/jumps according
to ˆy(t +
j ) = y(tj ), for all j ∈ N (assuming for the moment that
no DoS attacks are present). Here, we consider ˆy as a left-
continuous signal in the sense thatˆy(t) = lims→t ˆy(s). Further-
more, we assume that the value ofˆy evolves in a zero-order-hold
(ZOH) fashion in the sense that in between updates, the vari-
able ˆy is held constant, i.e., ˙ˆy(t) = 0for all t ∈ (tj , tj +1) with
j ∈ N. The functions f p and f c are assumed to be continuous
and the functions gp and gc are assumed to be continuously
differentiable.
Remark 1: For the sake of brevity, we consider the control
configuration presented in Fig. 1 in which we consider dynamic
controllers as in (2) and only sensor measurements are transmit-
ted over the network. However, the framework presented in this
paper also applies to other configurations, such as decentralized
control setups as described in [13] and [14].
B. DoS Attacks
A DoS attack is defined as a period in time at which the com-
munication is blocked by a malicious attacker. Hence, when a
transmission of y(tj ) is attempted at transmission time tj and a
DoS attack is active, the attempt will fail and, thus, the value of
ˆy cannot be updated toy(tj ). Obviously, this can have detrimen-
tal effects on the stability and performance of the closed-loop
system.
In general, DoS attacks lead to a sequence of time intervals
{Hn }n∈N , where the n-th time interval Hn , given by Hn :=
{hn } ∪ [hn , hn + τn ), represents the n-th DoS attack (period).
Hence, hn ∈ R0 denotes the time instant at which then-th DoS
interval commences andτn ∈ R0 denotes the length of then-th
DoS interval. The collection of all sequences{Hn }n∈N of DoS
attacks without overlap, i.e., that satisfy 0 h 0 h 0 + τ0 <
h1 h 1 + τ1 < h2 < . . .is denoted by I D oS.
Moreover, for a given {Hn }n∈N ∈ ID oS, we define the col-
lection of times at which a DoS attack is active by
T :=
n∈N
Hn , (3)
where we do not explicitly write the dependency of T on
{Hn }n∈N ∈ ID oS assuming it is clear from the context. By
means of this definition, we can now describe the jump/update
of ˆy as in (2) for each transmission attempt at time tj ∈ R0 ,
j ∈ N as
ˆy(t +
j ) = y(tj ), when tj /∈ T
ˆy(tj ), when tj ∈ T ,
and, accordingly, the update of the transmission errore := ˆy − y
as
e(t+
j ) =
⎧
⎨
⎩
0, when tj /∈ T
e(tj ), when tj ∈ T ,
(4)
for each j ∈ N.
C. Event-Based Communication
As already mentioned in the introduction, in comparison with
time-triggered control, ETC is much more suitable for balancing
network utilization and control performance. See also [15]–[18]
for some early approaches of ETC and see [19] for a recent
overview.
In this paper, we follow a design philosophy based on a
dynamic event-triggered control scheme [12], [13], [20]–[23],
which has several advantages over their static counterparts, see
[1], [12], [20], [22] and [23] for more details on these advan-
tages. A dynamic triggering condition in the context of this
paper will take the form
t0 = 0, tj +1 := inf t > tj + τm (t)
m iet | η(t) < 0 , (5)
for all j ∈ N, η(0) = 0, where m(t) ∈ {0, 1}is an auxiliary
variable used to keep track of whether the most recent trans-
mission attempt at time t ∈ R0 was successful (m(t) = 0)or
not (m(t) = 1)(due to DoS attacks), τ0
m iet, τ1
m iet ∈ R>0 are
(enforced) lower bounds on the minimum interevent times (MI-
ETs) for the cases that m(t) = 0and m(t) = 1, respectively,
and η ∈ Ris an auxiliary variable. Let us remark that, in gen-
eral, if possible, it is helpful to schedule transmission attempts
more often when a DoS attack is active in order to determine
earlier when the DoS attack is over. For this reason, we con-
sider two different waiting times τ0
m iet, τ1
m iet and we choose
τ1
m iet τ 0
m iet. The variable η evolves according to
˙η(t) = ˜Ψ(m(t), o(t), η(t)), when t ∈ (tj , tj +1] (6)
η(t+
j ) =
⎧
⎨
⎩
η0(e(tj )), when tj /∈ T
η(tj ), when tj ∈ T ,
(7)
where o = (y, e, τ, φ) ∈ O := Rny × Rny × R0 × λ, λ−1
with λ ∈ (0, 1)representing the information locally available
C over a network N . The continuous-time plant P is given by
P : ˙xp = fp(xp, u, w)
y = gp(xp), (1)
where w ∈ Rnw is a disturbance input, xp ∈ Rnp is the state
vector, u ∈ Rnu is the control input and y ∈ Rny is the
measured output of plant P . The (dynamic) output-based con-
troller C is given by
C : ˙xc = fc(xc, ˆy)
u = gc(xc, ˆy), (2)
where xc ∈ Rnc denotes the controller state,ˆy ∈ Rny represents
the most recently received output measurement of the plant
at the controller C, and u ∈ Rnu is the controller output. The
performance output is given by z = q(x), where z ∈ Rnz and
x = (xp, xc).
Typically, the communication over the network N is packet
based, which implies that the output measurementsy can only be
transmitted at discrete instants in time, i.e., at times tj , j ∈ N,
satisfying 0 t 0 < t1 < t2 < . . .. Hence, at each transmission
instant tj , j ∈ N, the value of ˆy is updated/jumps according
to ˆy(t +
j ) = y(tj ), for all j ∈ N (assuming for the moment that
no DoS attacks are present). Here, we consider ˆy as a left-
continuous signal in the sense thatˆy(t) = lims→t ˆy(s). Further-
more, we assume that the value ofˆy evolves in a zero-order-hold
(ZOH) fashion in the sense that in between updates, the vari-
able ˆy is held constant, i.e., ˙ˆy(t) = 0for all t ∈ (tj , tj +1) with
j ∈ N. The functions f p and f c are assumed to be continuous
and the functions gp and gc are assumed to be continuously
differentiable.
Remark 1: For the sake of brevity, we consider the control
configuration presented in Fig. 1 in which we consider dynamic
controllers as in (2) and only sensor measurements are transmit-
ted over the network. However, the framework presented in this
paper also applies to other configurations, such as decentralized
control setups as described in [13] and [14].
B. DoS Attacks
A DoS attack is defined as a period in time at which the com-
munication is blocked by a malicious attacker. Hence, when a
transmission of y(tj ) is attempted at transmission time tj and a
DoS attack is active, the attempt will fail and, thus, the value of
ˆy cannot be updated toy(tj ). Obviously, this can have detrimen-
tal effects on the stability and performance of the closed-loop
system.
In general, DoS attacks lead to a sequence of time intervals
{Hn }n∈N , where the n-th time interval Hn , given by Hn :=
{hn } ∪ [hn , hn + τn ), represents the n-th DoS attack (period).
Hence, hn ∈ R0 denotes the time instant at which then-th DoS
interval commences andτn ∈ R0 denotes the length of then-th
DoS interval. The collection of all sequences{Hn }n∈N of DoS
attacks without overlap, i.e., that satisfy 0 h 0 h 0 + τ0 <
h1 h 1 + τ1 < h2 < . . .is denoted by I D oS.
Moreover, for a given {Hn }n∈N ∈ ID oS, we define the col-
lection of times at which a DoS attack is active by
T :=
n∈N
Hn , (3)
where we do not explicitly write the dependency of T on
{Hn }n∈N ∈ ID oS assuming it is clear from the context. By
means of this definition, we can now describe the jump/update
of ˆy as in (2) for each transmission attempt at time tj ∈ R0 ,
j ∈ N as
ˆy(t +
j ) = y(tj ), when tj /∈ T
ˆy(tj ), when tj ∈ T ,
and, accordingly, the update of the transmission errore := ˆy − y
as
e(t+
j ) =
⎧
⎨
⎩
0, when tj /∈ T
e(tj ), when tj ∈ T ,
(4)
for each j ∈ N.
C. Event-Based Communication
As already mentioned in the introduction, in comparison with
time-triggered control, ETC is much more suitable for balancing
network utilization and control performance. See also [15]–[18]
for some early approaches of ETC and see [19] for a recent
overview.
In this paper, we follow a design philosophy based on a
dynamic event-triggered control scheme [12], [13], [20]–[23],
which has several advantages over their static counterparts, see
[1], [12], [20], [22] and [23] for more details on these advan-
tages. A dynamic triggering condition in the context of this
paper will take the form
t0 = 0, tj +1 := inf t > tj + τm (t)
m iet | η(t) < 0 , (5)
for all j ∈ N, η(0) = 0, where m(t) ∈ {0, 1}is an auxiliary
variable used to keep track of whether the most recent trans-
mission attempt at time t ∈ R0 was successful (m(t) = 0)or
not (m(t) = 1)(due to DoS attacks), τ0
m iet, τ1
m iet ∈ R>0 are
(enforced) lower bounds on the minimum interevent times (MI-
ETs) for the cases that m(t) = 0and m(t) = 1, respectively,
and η ∈ Ris an auxiliary variable. Let us remark that, in gen-
eral, if possible, it is helpful to schedule transmission attempts
more often when a DoS attack is active in order to determine
earlier when the DoS attack is over. For this reason, we con-
sider two different waiting times τ0
m iet, τ1
m iet and we choose
τ1
m iet τ 0
m iet. The variable η evolves according to
˙η(t) = ˜Ψ(m(t), o(t), η(t)), when t ∈ (tj , tj +1] (6)
η(t+
j ) =
⎧
⎨
⎩
η0(e(tj )), when tj /∈ T
η(tj ), when tj ∈ T ,
(7)
where o = (y, e, τ, φ) ∈ O := Rny × Rny × R0 × λ, λ−1
with λ ∈ (0, 1)representing the information locally available
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

96 IEEE TRANSACTIONS ON CONTROL OF NETWORK SYSTEMS, VOL. 4, NO. 1, MARCH 2017
at the event-triggering mechanism (ETM) (see Fig. 1) in-
cluding the output measurements y ∈ Rny , the transmission
error e := ˆy − y, and the auxiliary variables τ ∈ R0 and
φ ∈ λ, λ−1 . The variables τ and φ are discussed in more de-
tail in Section IV. Observe that by taking τ0
m iet, τ1
m iet ∈ R>0,
Zeno behavior is excluded from the ETC system since the next
event can only occur after at leastτ1
m iet time units have elapsed,
i.e., tj +1 − tj τ 1
m iet, for each j ∈ N. In Section V-B and
Section V-C, we specify how to select τ0
m iet, τ1
m iet, ˜Ψ and η0
such that desirable closed-loop stability and performance re-
quirements are met.
D. Problem Formulation
Given the descriptions above, the problem considered in this
work can now roughly be stated as follows. Propose a system-
atic design procedure for ˜Ψ, η0, τ0
m iet, and τ1
m iet such that the
interconnection (P, C, N )with P and C as in (1) and (2), re-
spectively, and the transmission attempts being generated by
(5)–(7), satisfies desired asymptotic stability criteria and per-
formance criteria, in terms of the so-called peak-to-peak gain
despite the presence of the DoS attacks {Hn }n∈N ∈ ID oS that
satisfy constraints in terms of frequency and duration.
In the next section, we introduce a complete mathematical
(hybrid) model for the event-triggered closed-loop NCS setup,
definitions of DoS frequency and duration, and relevant stability
and performance notions, leading to a more formal problem
formulation.
IV. MATHEMATICAL FORMULATION OF THE
EVENT-TRIGGERED CONTROL SETUP
In this section, we reformulate the dynamics of the event-
triggered NCS subject to DoS attacks in the form of the hybrid
model HT given by
˙ξ = F (ξ, w), when ξ ∈ C, (8a)
ξ + = G T (ξ), when ξ ∈ D, (8b)
see [24] for details on this hybrid modelling framework.
Let us remark that the hybrid systems considered in this
paper have time regularization (or dwell time) and exter-
nal inputs only appearing in the flow map. The latter al-
low us to employ the following signal norm definitions in-
spired by [21]. For any hybrid signal ζ (·, ·)defined on
dom ζ ⊂ R0 × N , we define the L ∞ -norm of ζ as ζ ∞ :=
supj∈N ess sup{t∈R|(t,j )∈dom ζ }|ζ (t, j)| . Observe that this
signal norm definition is similar to the corresponding classical
continuous-time norm. In this paper, we employ the same nota-
tion for the L ∞ -norm of hybrid time signals and conventional
continuous-time signals. Moreover, due to the aforementioned
properties and notational convenience, we consider the distur-
bance input w : R0 → R nw to be a time signal instead of a
hybrid signal and use the usual definition for the L ∞ -norm.
A. Hybrid Model
To describe the NCS setup as discussed before in terms of
flow equations (8a) and jump equations (8b), we first need
to introduce a few auxiliary variables, namely, the timer vari-
ables s, τ ∈ R0 representing the overall time and the time
elapsed since the most recent transmission attempt, respectively.
Moreover, we also introduce an additional auxiliary variable
φ ∈ λ, λ−1 , where λ ∈ (0, 1)is a tuning parameter to be spec-
ified, used in the triggering condition and part of o as already
mentioned in Section III-C. By combining these auxiliary vari-
ables with (1), (2), and (7), the flow map of the interconnection
(P, C, N )can be defined as
F (ξ, w) := f (x, e, w), g(x, e, w), 1, 1, 0,
˜Ψ(m, o, η), fφ (τ, m, φ), (9)
where ξ = (x, e, τ, s, m, η, φ) ∈ X := Rnx × Rny × R0 ×
R0 × {0, 1} × R0 × λ, λ−1 with nx = np + nc and λ ∈
(0, 1). Moreover, the functions f and g follow from (1) and (2)
and are given by
f (x, e, w) = f p(xp, gc(xc, gp(xp) + e), w)
f c(xc, gp(xp) + e) , (10)
g(x, e, w) = −
∂gp
∂xp
(xp)f p(xp, gc(xc, gp(xp) + e), w),(11)
and f φ will be specified later. In accordance with (5), we define
the flow set as
C := {ξ ∈ X | τ τm
m iet ∨ η 0} . (12)
Based on (4) and (7), we specify the jump map as
GT (ξ) := G0(ξ), when ξ ∈ D ∧ s /∈ T
G1(ξ), when ξ ∈ D ∧ s ∈ T , (13)
where
G0(ξ) = (x, 0, 0, s, 0, η0(e), λ) (14)
G1(ξ) = (x, e, 0, s, 1, η, φ) , (15)
such that ξ + = G0(ξ) corresponds to a successful transmission
attempt and ξ + = G1(ξ) to a failed transmission attempt.
Finally, the jump set is given by
D := {ξ ∈ X | τ τm
m iet ∧ η 0} . (16)
The time constants τ0
m iet and τ1
m iet and the functions ˜Ψ, η0 and
f φ are specified in Section V. Observe that the hybrid system de-
scription presented above leads to more solutions than induced
by the triggering condition given by (5) and (7).1
Moreover, observe that the hybrid system HT as described
by (8)–(16) is parameterized by the collection of time intervals
at which DoS attacks are active as defined in (3). Therefore, we
write explicitly the dependence of HT on T .
1We foresee that the results in [24, Ch. 6 and 7] on well-posed hybrid systems
can relatively easily be used to obtain robustness properties with respect to
arbitrarily small vanishing perturbations on the flow map, jump map, and all
states. Note, however, that the focus of this paper is to obtain a robustness
result with respect to DoS attacks, which require different and new techniques.
To not complicate the exposition of the novel techniques by introducing more
technicalities needed to also address the robustness properties studied in [24], we
describe only the new results, although they can be combined with the existing
robustness results of [24].
at the event-triggering mechanism (ETM) (see Fig. 1) in-
cluding the output measurements y ∈ Rny , the transmission
error e := ˆy − y, and the auxiliary variables τ ∈ R0 and
φ ∈ λ, λ−1 . The variables τ and φ are discussed in more de-
tail in Section IV. Observe that by taking τ0
m iet, τ1
m iet ∈ R>0,
Zeno behavior is excluded from the ETC system since the next
event can only occur after at leastτ1
m iet time units have elapsed,
i.e., tj +1 − tj τ 1
m iet, for each j ∈ N. In Section V-B and
Section V-C, we specify how to select τ0
m iet, τ1
m iet, ˜Ψ and η0
such that desirable closed-loop stability and performance re-
quirements are met.
D. Problem Formulation
Given the descriptions above, the problem considered in this
work can now roughly be stated as follows. Propose a system-
atic design procedure for ˜Ψ, η0, τ0
m iet, and τ1
m iet such that the
interconnection (P, C, N )with P and C as in (1) and (2), re-
spectively, and the transmission attempts being generated by
(5)–(7), satisfies desired asymptotic stability criteria and per-
formance criteria, in terms of the so-called peak-to-peak gain
despite the presence of the DoS attacks {Hn }n∈N ∈ ID oS that
satisfy constraints in terms of frequency and duration.
In the next section, we introduce a complete mathematical
(hybrid) model for the event-triggered closed-loop NCS setup,
definitions of DoS frequency and duration, and relevant stability
and performance notions, leading to a more formal problem
formulation.
IV. MATHEMATICAL FORMULATION OF THE
EVENT-TRIGGERED CONTROL SETUP
In this section, we reformulate the dynamics of the event-
triggered NCS subject to DoS attacks in the form of the hybrid
model HT given by
˙ξ = F (ξ, w), when ξ ∈ C, (8a)
ξ + = G T (ξ), when ξ ∈ D, (8b)
see [24] for details on this hybrid modelling framework.
Let us remark that the hybrid systems considered in this
paper have time regularization (or dwell time) and exter-
nal inputs only appearing in the flow map. The latter al-
low us to employ the following signal norm definitions in-
spired by [21]. For any hybrid signal ζ (·, ·)defined on
dom ζ ⊂ R0 × N , we define the L ∞ -norm of ζ as ζ ∞ :=
supj∈N ess sup{t∈R|(t,j )∈dom ζ }|ζ (t, j)| . Observe that this
signal norm definition is similar to the corresponding classical
continuous-time norm. In this paper, we employ the same nota-
tion for the L ∞ -norm of hybrid time signals and conventional
continuous-time signals. Moreover, due to the aforementioned
properties and notational convenience, we consider the distur-
bance input w : R0 → R nw to be a time signal instead of a
hybrid signal and use the usual definition for the L ∞ -norm.
A. Hybrid Model
To describe the NCS setup as discussed before in terms of
flow equations (8a) and jump equations (8b), we first need
to introduce a few auxiliary variables, namely, the timer vari-
ables s, τ ∈ R0 representing the overall time and the time
elapsed since the most recent transmission attempt, respectively.
Moreover, we also introduce an additional auxiliary variable
φ ∈ λ, λ−1 , where λ ∈ (0, 1)is a tuning parameter to be spec-
ified, used in the triggering condition and part of o as already
mentioned in Section III-C. By combining these auxiliary vari-
ables with (1), (2), and (7), the flow map of the interconnection
(P, C, N )can be defined as
F (ξ, w) := f (x, e, w), g(x, e, w), 1, 1, 0,
˜Ψ(m, o, η), fφ (τ, m, φ), (9)
where ξ = (x, e, τ, s, m, η, φ) ∈ X := Rnx × Rny × R0 ×
R0 × {0, 1} × R0 × λ, λ−1 with nx = np + nc and λ ∈
(0, 1). Moreover, the functions f and g follow from (1) and (2)
and are given by
f (x, e, w) = f p(xp, gc(xc, gp(xp) + e), w)
f c(xc, gp(xp) + e) , (10)
g(x, e, w) = −
∂gp
∂xp
(xp)f p(xp, gc(xc, gp(xp) + e), w),(11)
and f φ will be specified later. In accordance with (5), we define
the flow set as
C := {ξ ∈ X | τ τm
m iet ∨ η 0} . (12)
Based on (4) and (7), we specify the jump map as
GT (ξ) := G0(ξ), when ξ ∈ D ∧ s /∈ T
G1(ξ), when ξ ∈ D ∧ s ∈ T , (13)
where
G0(ξ) = (x, 0, 0, s, 0, η0(e), λ) (14)
G1(ξ) = (x, e, 0, s, 1, η, φ) , (15)
such that ξ + = G0(ξ) corresponds to a successful transmission
attempt and ξ + = G1(ξ) to a failed transmission attempt.
Finally, the jump set is given by
D := {ξ ∈ X | τ τm
m iet ∧ η 0} . (16)
The time constants τ0
m iet and τ1
m iet and the functions ˜Ψ, η0 and
f φ are specified in Section V. Observe that the hybrid system de-
scription presented above leads to more solutions than induced
by the triggering condition given by (5) and (7).1
Moreover, observe that the hybrid system HT as described
by (8)–(16) is parameterized by the collection of time intervals
at which DoS attacks are active as defined in (3). Therefore, we
write explicitly the dependence of HT on T .
1We foresee that the results in [24, Ch. 6 and 7] on well-posed hybrid systems
can relatively easily be used to obtain robustness properties with respect to
arbitrarily small vanishing perturbations on the flow map, jump map, and all
states. Note, however, that the focus of this paper is to obtain a robustness
result with respect to DoS attacks, which require different and new techniques.
To not complicate the exposition of the novel techniques by introducing more
technicalities needed to also address the robustness properties studied in [24], we
describe only the new results, although they can be combined with the existing
robustness results of [24].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

DOLK et al.: EVENT-TRIGGERED CONTROL SYSTEMS UNDER DENIAL-OF-SERVICE ATTACKS 97
B. Constraints on DoS Sequence
Since it is reasonable to assume that the attacker’s resources
are not infinite and that measures can be taken to mitigate mali-
cious DoS attacks, a natural characterization of DoS attacks can
be given in terms of DoS frequency and DoS duration as in [5],
see also Remark 2 below. Therefore, we define the collection of
times within the interval [T1, T2], with T2 T 1 0 , at which
DoS attacks are active as
Ξ(T1, T2) := [T1, T2] ∩ T (17)
with T as in (3) and the collection of time instants within the
interval [T1, T2] at which communication is possible as
Θ(T1, T2) := [T1, T2]\Ξ(T1, T2).
Consider a collection{Ii }, i ∈¯N of N intervals that do not over-
lap, i.e.,I i ∩ Ij = ∅for all i, j ∈ ¯N , i = j, and letI = i∈ ¯N I i .
We denote with |I | the sum of the lengths of all intervals I i ,
i ∈ ¯N . Consequently,|Ξ(T1, T2)| denotes the total length of the
DoS attacks within the interval[T1, T2]. Consider the following
definitions.
Definition 1: [6], [11] (DoS Frequency): Let {Hn }n∈N ∈
I D oS and let n(T1, T2) denote the number of DoS off/on
transitions occurring in the interval [T1, T2), i.e., n(T1, T2) =
card{n ∈ N | hn ∈ [T1, T2)}, where card denotes the number
of elements in the set. We say that a given sequence of DoS
attacks {Hn }n∈N satisfies the DoS frequency constraint for a
given τD ∈ R>0, and a given ν ∈ R0 , if for all T1, T2 ∈ R0
with T2 T 1
n(T1, T2) ν + T2 − T1
τD
. (18)
We denote the class of sequences of DoS intervals that satisfy
this DoS frequency constraint by I D oS,f r eq(ν, τD ).
Definition 2: [6] (DoS Duration): We say that a sequence of
DoS attacks specified by {Hn }n∈N ∈ ID oS satisfies the DoS
duration constraint for a given T ∈ R>1 and a given ς ∈ R0 ,
if for all T1, T2 ∈ R0 with T2 T 1
|Ξ(T1, T2)| < ς +T2 − T1
T . (19)
We denote the class of all sequences of DoS intervals that satisfy
this DoS durationconstraint by I D oS,dur (ς, T ).
We will also use the notation I D oS(ν, τD , ς , T )for ν, ς ∈
R0 , τD ∈ R>0 and T ∈ R>1 to denote the intersection
I D oS,f r eq(ν, τD ) ∩ ID oS,dur (ς, T ). We call a sequence of
DoS attacks that satisfies {Hn }n∈N ∈ ID oS(ν, τD , ς , T ), a
(ν, τD , ς , T )-DoS sequence for short. Moreover, we also define
the class of hybrid systems, which are generated by(ν, τD , ς , T )-
DoS sequences as H(ν, τD , ς, T ) := {HT | T as in (3) with
{Hn }n∈N ∈ ID oS(ν, τD , ς , T )}.
Remark 2: Observe that Definitions 1 and 2 make no as-
sumptions regarding the attacker’s underlying strategy since
they only indicate limitations in terms of the frequency and
duration of DoS attacks. From a practical point of view, Def-
initions 1 and 2 are natural as well since there exist several
techniques to mitigate jamming attacks, for example, spreading
techniques and high-pass filtering. As a consequence, the fre-
quency and duration of DoS attacks can indeed be restrained by
exploiting such techniques, see, for example, [4] and [8].
Of course, the desired control objectives, in general, cannot
be achieved in case the DoS frequency and/or DoS duration can
be arbitrarily large, i.e., in case τD → 0 or T = 1, respectively,
as in that case, every communication attempt can be blocked by
the attacker with the consequence that the system is in open loop
all of the time. Fortunately, as already mentioned in Remark 2,
several provisions can be taken in order to mitigate DoS attacks
with the aim to limit the frequency and duration of the time
intervals over which communication is effectively denied.
C. Mathematical Problem Formulation
To specify desirable stability and performance properties,
we introduce the following definitions that use the concepts
of hybrid time domains and corresponding solutions [24]. In
this paper, we assume that all hybrid trajectories start in the set
X0 := {ξ ∈ X | τ τ0
m iet, s = 0, η = 0, φ = φm iet}, (20)
where φm iet will be specified in Section V-B. Observe that this
assumption only reflects the initialization of the ETM variables,
which can be freely chosen, while we do not put any (initial)
constraints on the plant and the controller states x = (xp, xc)
and the initial knowledge of ˆy at the controller side.
Definition 3: A hybrid system HT is said to be persis-
tently flowing with respect to initial state set X0 if all maximal
solutions2 ξ with ξ(0, 0) ∈ X0 have unbounded domains in the
t-direction, i.e., supt dom ξ = ∞.
Definition 4: Let ν, ς ∈ R0 , τD ∈ R>0 and T ∈ R>1 be
given. A closed set A ⊂ X is said to be uniformly globally
asymptotically stable (UGAS) for the class of hybrid systems
H(ν, τD , ς , T )with respect to initial state set X0 if all systems
HT ∈ H(ν, τD , ς , T )are persistently flowing with respect to
initial state set X0 and there exists a function β ∈ KLL such
that for any HT ∈ H(ν, τD , ς , T )and for any initial condition
ξ(0, 0) ∈ X0, all corresponding solutions ξ of H T with w = 0
satisfy
|ξ(t, j)|A β (|ξ(0, 0)|A , t, j) (21)
for all (t, j) ∈dom ξ. The closed set A is said to be uni-
formly globally exponentially stable (UGES) for the class
of hybrid systems H(ν, τD , ς , T ), if the above holds with
β(r, t, j) = M r exp(−(t + j))for some M 0 and > 0 .
Definition 5: Let ϑ, ν, ς ∈ R0 , τD ∈ R>0 and T ∈ R>1 be
given. A closed set A ⊂ X is said to be L ∞ -stable with an
induced L ∞ -gain less than or equal to ϑ for the class of hybrid
systems H(ν, τD , ς , T ), if all systems HT ∈ H(ν, τD , ς , T )are
persistently flowing with respect to initial state setX0 and there
exists a K ∞ -function β such that for any HT ∈ H(ν, τD , ς , T ),
exogenous input w ∈ L∞ , and any initial condition ξ(0, 0) ∈
X0, each corresponding solution to HT satisfies
z L ∞ β(|ξ(0, 0)|A ) + ϑw L ∞ . (22)
We can now formalize the problem, which was loosely stated
at the end of Section III.
2[24, Ch. 2] A solution ξ to H T is maximal if there does not exist another
solution ¯ξ to HT such that dom ξ is a proper subset of dom ¯ξ and ξ(t, j) =
¯ξ(t, j )for all (t, j) ∈ dom ξ.
B. Constraints on DoS Sequence
Since it is reasonable to assume that the attacker’s resources
are not infinite and that measures can be taken to mitigate mali-
cious DoS attacks, a natural characterization of DoS attacks can
be given in terms of DoS frequency and DoS duration as in [5],
see also Remark 2 below. Therefore, we define the collection of
times within the interval [T1, T2], with T2 T 1 0 , at which
DoS attacks are active as
Ξ(T1, T2) := [T1, T2] ∩ T (17)
with T as in (3) and the collection of time instants within the
interval [T1, T2] at which communication is possible as
Θ(T1, T2) := [T1, T2]\Ξ(T1, T2).
Consider a collection{Ii }, i ∈¯N of N intervals that do not over-
lap, i.e.,I i ∩ Ij = ∅for all i, j ∈ ¯N , i = j, and letI = i∈ ¯N I i .
We denote with |I | the sum of the lengths of all intervals I i ,
i ∈ ¯N . Consequently,|Ξ(T1, T2)| denotes the total length of the
DoS attacks within the interval[T1, T2]. Consider the following
definitions.
Definition 1: [6], [11] (DoS Frequency): Let {Hn }n∈N ∈
I D oS and let n(T1, T2) denote the number of DoS off/on
transitions occurring in the interval [T1, T2), i.e., n(T1, T2) =
card{n ∈ N | hn ∈ [T1, T2)}, where card denotes the number
of elements in the set. We say that a given sequence of DoS
attacks {Hn }n∈N satisfies the DoS frequency constraint for a
given τD ∈ R>0, and a given ν ∈ R0 , if for all T1, T2 ∈ R0
with T2 T 1
n(T1, T2) ν + T2 − T1
τD
. (18)
We denote the class of sequences of DoS intervals that satisfy
this DoS frequency constraint by I D oS,f r eq(ν, τD ).
Definition 2: [6] (DoS Duration): We say that a sequence of
DoS attacks specified by {Hn }n∈N ∈ ID oS satisfies the DoS
duration constraint for a given T ∈ R>1 and a given ς ∈ R0 ,
if for all T1, T2 ∈ R0 with T2 T 1
|Ξ(T1, T2)| < ς +T2 − T1
T . (19)
We denote the class of all sequences of DoS intervals that satisfy
this DoS durationconstraint by I D oS,dur (ς, T ).
We will also use the notation I D oS(ν, τD , ς , T )for ν, ς ∈
R0 , τD ∈ R>0 and T ∈ R>1 to denote the intersection
I D oS,f r eq(ν, τD ) ∩ ID oS,dur (ς, T ). We call a sequence of
DoS attacks that satisfies {Hn }n∈N ∈ ID oS(ν, τD , ς , T ), a
(ν, τD , ς , T )-DoS sequence for short. Moreover, we also define
the class of hybrid systems, which are generated by(ν, τD , ς , T )-
DoS sequences as H(ν, τD , ς, T ) := {HT | T as in (3) with
{Hn }n∈N ∈ ID oS(ν, τD , ς , T )}.
Remark 2: Observe that Definitions 1 and 2 make no as-
sumptions regarding the attacker’s underlying strategy since
they only indicate limitations in terms of the frequency and
duration of DoS attacks. From a practical point of view, Def-
initions 1 and 2 are natural as well since there exist several
techniques to mitigate jamming attacks, for example, spreading
techniques and high-pass filtering. As a consequence, the fre-
quency and duration of DoS attacks can indeed be restrained by
exploiting such techniques, see, for example, [4] and [8].
Of course, the desired control objectives, in general, cannot
be achieved in case the DoS frequency and/or DoS duration can
be arbitrarily large, i.e., in case τD → 0 or T = 1, respectively,
as in that case, every communication attempt can be blocked by
the attacker with the consequence that the system is in open loop
all of the time. Fortunately, as already mentioned in Remark 2,
several provisions can be taken in order to mitigate DoS attacks
with the aim to limit the frequency and duration of the time
intervals over which communication is effectively denied.
C. Mathematical Problem Formulation
To specify desirable stability and performance properties,
we introduce the following definitions that use the concepts
of hybrid time domains and corresponding solutions [24]. In
this paper, we assume that all hybrid trajectories start in the set
X0 := {ξ ∈ X | τ τ0
m iet, s = 0, η = 0, φ = φm iet}, (20)
where φm iet will be specified in Section V-B. Observe that this
assumption only reflects the initialization of the ETM variables,
which can be freely chosen, while we do not put any (initial)
constraints on the plant and the controller states x = (xp, xc)
and the initial knowledge of ˆy at the controller side.
Definition 3: A hybrid system HT is said to be persis-
tently flowing with respect to initial state set X0 if all maximal
solutions2 ξ with ξ(0, 0) ∈ X0 have unbounded domains in the
t-direction, i.e., supt dom ξ = ∞.
Definition 4: Let ν, ς ∈ R0 , τD ∈ R>0 and T ∈ R>1 be
given. A closed set A ⊂ X is said to be uniformly globally
asymptotically stable (UGAS) for the class of hybrid systems
H(ν, τD , ς , T )with respect to initial state set X0 if all systems
HT ∈ H(ν, τD , ς , T )are persistently flowing with respect to
initial state set X0 and there exists a function β ∈ KLL such
that for any HT ∈ H(ν, τD , ς , T )and for any initial condition
ξ(0, 0) ∈ X0, all corresponding solutions ξ of H T with w = 0
satisfy
|ξ(t, j)|A β (|ξ(0, 0)|A , t, j) (21)
for all (t, j) ∈dom ξ. The closed set A is said to be uni-
formly globally exponentially stable (UGES) for the class
of hybrid systems H(ν, τD , ς , T ), if the above holds with
β(r, t, j) = M r exp(−(t + j))for some M 0 and > 0 .
Definition 5: Let ϑ, ν, ς ∈ R0 , τD ∈ R>0 and T ∈ R>1 be
given. A closed set A ⊂ X is said to be L ∞ -stable with an
induced L ∞ -gain less than or equal to ϑ for the class of hybrid
systems H(ν, τD , ς , T ), if all systems HT ∈ H(ν, τD , ς , T )are
persistently flowing with respect to initial state setX0 and there
exists a K ∞ -function β such that for any HT ∈ H(ν, τD , ς , T ),
exogenous input w ∈ L∞ , and any initial condition ξ(0, 0) ∈
X0, each corresponding solution to HT satisfies
z L ∞ β(|ξ(0, 0)|A ) + ϑw L ∞ . (22)
We can now formalize the problem, which was loosely stated
at the end of Section III.
2[24, Ch. 2] A solution ξ to H T is maximal if there does not exist another
solution ¯ξ to HT such that dom ξ is a proper subset of dom ¯ξ and ξ(t, j) =
¯ξ(t, j )for all (t, j) ∈ dom ξ.
98 IEEE TRANSACTIONS ON CONTROL OF NETWORK SYSTEMS, VOL. 4, NO. 1, MARCH 2017
Problem 1: Given ν ∈ R0 , τD ∈ R>0, ς ∈ R0 and T ∈
R>1, provide design conditions for the values ofτ0
m iet, τ1
m iet ∈
R>0 and the functions ˜Ψ, η0 as in the event generator given
by (5) and (7) and f φ as in (9), such that the closed set
A := {ξ ∈ X | x = 0, e = 0}is UGES and/or, in the presence
of disturbances, has a finite-induced L ∞ -gain for the class of
hybrid systems H(ν, τD , ς , T ).
V. DESIGN CONDITIONS AND STABILITY GUARANTEES
In Section V-B and Section V-C, the time constantsτ0
m iet and
τ1
m iet, and the function f φ are specified and design conditions
for the functions ˜Ψ and η0 are presented leading to a solution
for Problem 1. In order to specify the design conditions, we
first start with the required preliminaries consisting of stability
and performance conditions for time-triggered NCSs taken from
[25] and [26] in Section V-A.
A. Preliminaries
Consider the following condition.
Condition 1: [25], [26]. There exists a locally Lipschitz
function W : Rny → R 0 , a continuous function H : R nx ×
Rnw → R , and constants L 0, c W , and ¯cW , such that
1) for all e ∈ Rne it holds that
cW |e| W (e) ¯ cW |e|, (23)
2) for all x ∈ Rnx , and almost all e ∈ Rny it holds that
∂W (e)
∂e , g(x, e, w) LW (e) + H(x, w). (24)
In addition, there exists a locally Lipschitz function V :
Rnx → R 0 , and a positive semi-definite function : R ny →
R0 and constants ρV , ρW , γ, cV , ¯cV , cz > 0, such that
1) for all x ∈ Rnx
cV |x|2 V (x) ¯ cV |x|2, cz |q(x)|2 V (x), (25)
2) for all e ∈ Rny , w ∈ Rnw and almost all x ∈ Rnx
∇V (x), f (x, e, w) −ρ V V (x) − (|y|) − H2(x, w)
+ (γ2 − ρW )W 2(e) + θ2|w|2, (26)
3) the constants ρW and γ satisfy ρW γ 2.
Let us remark that for linear systems, the conditions above
can be obtained systematically by solving a multiobjective linear
matrix inequality (LMI) problem, see [12], [13], and [26] for
more details. Also, several classes of nonlinear systems satisfy
these conditions, see [13].
B. Minimal Interevent Time
As already mentioned, τ0
m iet and τ1
m iet (and φm iet, ˜Ψ, f φ
and η0) should be chosen appropriately in the sense that de-
sirable closed-loop stability and performance requirements can
be achieved. To do so, we specify the function 3 f φ : R0 ×
3Observe that the flow mapF as given in (9) is discontinuous inτ due to (27).
However, due to the facts that ˙τ = 1and the right-hand side of (27) is Lipschitz
continuous, we find by means of the Carath´eodory’s existence theorem that this
does not cause any problems in the uniqueness and existence of solutions
{0, 1} × R0 → R as
f φ(τ, m, φ) :=
(m − 1) 2Lφ + γ(φ2 + 1) , for τ τ 0
m iet,
0, for τ > τ0
m iet, (27)
with L and γ as given in Condition 1. The time constants τ0
m iet
and τ1
m iet can be chosen less than or equal to the maximally
allowable transmission interval bound (in this work referred to
as ¯τm iet) given in [25] as
¯τm iet :=
⎧
⎪⎪⎪⎪⎪⎪⎪⎪⎪⎪⎪⎪⎨
⎪⎪⎪⎪⎪⎪⎪⎪⎪⎪⎪⎪⎩
1
Lr arctan
⎛
⎜
⎝ r(1 − λ)
2 λ
1 + λ
γ
L − 1 + 1 + λ
⎞
⎟
⎠ , γ > L
1
L
1 − λ
1 + λ
, γ = L
1
Lr arctanh
⎛
⎜
⎝ r(1 − λ)
2 λ
λ + 1
γ
L − 1 + 1 + λ
⎞
⎟
⎠ , γ < L,
(28)
where r = |(γ/L) 2 − 1|. Note that by selecting τ0
m iet and
τ1
m iet equal to the right-hand side of (28), indeed longer (aver-
age) transmission intervals are realized compared to time-based
(worst-case) specifications as discussed in Section III-C.
Lemma 1: [25] Let ¯τm iet be given by (28), then the solution
to
˙˜φ = −2L˜φ − γ ˜φ2 + 1 (29)
with ˜φ(0) = λ−1 satisfying ˜φ(t) ∈ [λ, λ−1]for allt ∈ [0, ¯τm iet],
and ˜φ(¯τm iet) = λ.
Finally, we define
φm iet := ˜φ(τ0
m iet), (30)
where ˜φ is the solution to (29) with ˜φ(0) = λ−1 and note again
that τ1
m iet τ 0
m iet ¯ τm iet.
C. Stability and Performance Guarantees
Theorem 2: Consider the class of hybrid systems
H(ν, τD , ς , T )with ν, ς ∈ R0 , τD ∈ R>0, T ∈ R>1 and let
Condition 1 be satisfied withτ1
m iet τ 0
m iet ¯ τm iet with ¯τm iet
as in (28) and withf φ and φm iet as in (27) and (30), respectively.
Moreover, suppose that the following three conditions hold:
1) The DoS frequency parameter τD and the DoS duration
parameter T satisfy
τ1
m iet
τD
+ 1
T < ω1
ω1 + ω2
, (31)
where
ω1 = min ρV , λρW
γ , ω2 = (¯γ − ρW )
γφm iet
(32)
and
¯γ := γ 2φm ietL + γ(1 + φ2
m iet) . (33)
Problem 1: Given ν ∈ R0 , τD ∈ R>0, ς ∈ R0 and T ∈
R>1, provide design conditions for the values ofτ0
m iet, τ1
m iet ∈
R>0 and the functions ˜Ψ, η0 as in the event generator given
by (5) and (7) and f φ as in (9), such that the closed set
A := {ξ ∈ X | x = 0, e = 0}is UGES and/or, in the presence
of disturbances, has a finite-induced L ∞ -gain for the class of
hybrid systems H(ν, τD , ς , T ).
V. DESIGN CONDITIONS AND STABILITY GUARANTEES
In Section V-B and Section V-C, the time constantsτ0
m iet and
τ1
m iet, and the function f φ are specified and design conditions
for the functions ˜Ψ and η0 are presented leading to a solution
for Problem 1. In order to specify the design conditions, we
first start with the required preliminaries consisting of stability
and performance conditions for time-triggered NCSs taken from
[25] and [26] in Section V-A.
A. Preliminaries
Consider the following condition.
Condition 1: [25], [26]. There exists a locally Lipschitz
function W : Rny → R 0 , a continuous function H : R nx ×
Rnw → R , and constants L 0, c W , and ¯cW , such that
1) for all e ∈ Rne it holds that
cW |e| W (e) ¯ cW |e|, (23)
2) for all x ∈ Rnx , and almost all e ∈ Rny it holds that
∂W (e)
∂e , g(x, e, w) LW (e) + H(x, w). (24)
In addition, there exists a locally Lipschitz function V :
Rnx → R 0 , and a positive semi-definite function : R ny →
R0 and constants ρV , ρW , γ, cV , ¯cV , cz > 0, such that
1) for all x ∈ Rnx
cV |x|2 V (x) ¯ cV |x|2, cz |q(x)|2 V (x), (25)
2) for all e ∈ Rny , w ∈ Rnw and almost all x ∈ Rnx
∇V (x), f (x, e, w) −ρ V V (x) − (|y|) − H2(x, w)
+ (γ2 − ρW )W 2(e) + θ2|w|2, (26)
3) the constants ρW and γ satisfy ρW γ 2.
Let us remark that for linear systems, the conditions above
can be obtained systematically by solving a multiobjective linear
matrix inequality (LMI) problem, see [12], [13], and [26] for
more details. Also, several classes of nonlinear systems satisfy
these conditions, see [13].
B. Minimal Interevent Time
As already mentioned, τ0
m iet and τ1
m iet (and φm iet, ˜Ψ, f φ
and η0) should be chosen appropriately in the sense that de-
sirable closed-loop stability and performance requirements can
be achieved. To do so, we specify the function 3 f φ : R0 ×
3Observe that the flow mapF as given in (9) is discontinuous inτ due to (27).
However, due to the facts that ˙τ = 1and the right-hand side of (27) is Lipschitz
continuous, we find by means of the Carath´eodory’s existence theorem that this
does not cause any problems in the uniqueness and existence of solutions
{0, 1} × R0 → R as
f φ(τ, m, φ) :=
(m − 1) 2Lφ + γ(φ2 + 1) , for τ τ 0
m iet,
0, for τ > τ0
m iet, (27)
with L and γ as given in Condition 1. The time constants τ0
m iet
and τ1
m iet can be chosen less than or equal to the maximally
allowable transmission interval bound (in this work referred to
as ¯τm iet) given in [25] as
¯τm iet :=
⎧
⎪⎪⎪⎪⎪⎪⎪⎪⎪⎪⎪⎪⎨
⎪⎪⎪⎪⎪⎪⎪⎪⎪⎪⎪⎪⎩
1
Lr arctan
⎛
⎜
⎝ r(1 − λ)
2 λ
1 + λ
γ
L − 1 + 1 + λ
⎞
⎟
⎠ , γ > L
1
L
1 − λ
1 + λ
, γ = L
1
Lr arctanh
⎛
⎜
⎝ r(1 − λ)
2 λ
λ + 1
γ
L − 1 + 1 + λ
⎞
⎟
⎠ , γ < L,
(28)
where r = |(γ/L) 2 − 1|. Note that by selecting τ0
m iet and
τ1
m iet equal to the right-hand side of (28), indeed longer (aver-
age) transmission intervals are realized compared to time-based
(worst-case) specifications as discussed in Section III-C.
Lemma 1: [25] Let ¯τm iet be given by (28), then the solution
to
˙˜φ = −2L˜φ − γ ˜φ2 + 1 (29)
with ˜φ(0) = λ−1 satisfying ˜φ(t) ∈ [λ, λ−1]for allt ∈ [0, ¯τm iet],
and ˜φ(¯τm iet) = λ.
Finally, we define
φm iet := ˜φ(τ0
m iet), (30)
where ˜φ is the solution to (29) with ˜φ(0) = λ−1 and note again
that τ1
m iet τ 0
m iet ¯ τm iet.
C. Stability and Performance Guarantees
Theorem 2: Consider the class of hybrid systems
H(ν, τD , ς , T )with ν, ς ∈ R0 , τD ∈ R>0, T ∈ R>1 and let
Condition 1 be satisfied withτ1
m iet τ 0
m iet ¯ τm iet with ¯τm iet
as in (28) and withf φ and φm iet as in (27) and (30), respectively.
Moreover, suppose that the following three conditions hold:
1) The DoS frequency parameter τD and the DoS duration
parameter T satisfy
τ1
m iet
τD
+ 1
T < ω1
ω1 + ω2
, (31)
where
ω1 = min ρV , λρW
γ , ω2 = (¯γ − ρW )
γφm iet
(32)
and
¯γ := γ 2φm ietL + γ(1 + φ2
m iet) . (33)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

DOLK et al.: EVENT-TRIGGERED CONTROL SYSTEMS UNDER DENIAL-OF-SERVICE ATTACKS 99
2) The function ˜Ψ is given by
˜Ψ(m, o, η) = Ψ(o) − σ(η), when m = 0,
−(1 − ω(τ, m)), when m = 1, (34)
where σ is a K ∞ -function that satisfiesσ(s) ω 1s for all
s ∈ R0 , the function Ψ : O → R is given by
Ψ(o) = (|y|) + ¯γω(τ, m)W2(e) (35)
with
ω(τ, m) := 1, for 0 τ τ m
m iet
0, for τ > τm
m iet, (36)
for τ ∈ R0 and with ¯γ as given in (33).
3) The function η0 is given by η0(e) = γφm ietW 2(e).
Then, the closed set A = {ξ ∈ X | x = 0, e = 0}is UGES
and isL ∞ -stable with a finite inducedL ∞ -gain less than or equal
to θ κ
cz β∗ with cz as in (25) and where κ := eς∗(ω1 +ω2 ) , ς∗ :=
ς + ντ1
m iet, β∗ = ω1 − (ω1 + ω2)/T ∗ and T∗ := τD T /(τD +
τ1
m ietT ), for the class of hybrid systems H(ν, τD , ς , T ).
The proof is provided in the Appendix. Observe that the con-
dition given in item 1) imposes restrictions on the DoS parame-
ters τD and T in terms of other system parameters. As such, the
frequency and duration of the allowable DoS attacks are lim-
ited. Moreover, observe that the DoS parameters ν, τD , ς and
T affect the guaranteed L ∞ -gain of the system which illustrates
the tradeoff between robustness with respect to DoS attacks and
performance in the sense that, in general, robustness comes at
the cost of performance.
Observe that in case communication is allowed, the transmis-
sions are scheduled in an event-based fashion (to save valuable
communication resources) whereas in case the communication
is denied, the next transmission is scheduled again after τ1
m iet
time units (to determine when the DoS attack is over) since when
m = 1, which implies thatη = 0at the previous transmission at-
tempt, ˜Ψ(m, o, η) = 0for 0 τ τ 1
m iet and ˜Ψ(m, o, η) = −1
for τ > τ1
m iet. Hence, when m = 1and τ > τ1
m iet , a next jump
occurs as flow condition η 0 will be violated.
Remark 3: Note that this implementation requires the knowl-
edge about when DoS attacks are blocking transmissions, which
could be realized by means of acknowledgements as illustrated
in Fig. 1. Let us remark that the ETM can easily be adjusted
such that it is not required that acknowledgements are being
received instantaneously. For example, the acknowledgement is
allowed to be delayed with, at most, τ1
m iet time units if after
each transmission instant, the ETM keeps track of the evolution
of η for both cases that the transmission has been successful or
denied. For the brevity of exposition, this feature has, however,
been omitted.
The presented framework does not require an acknowledge-
ment scheme when purely periodic sampling with intersampling
time τ1
m iet is employed. The same design conditions lead to the
same guarantees in this case.
Remark 4: The proposed framework can also be used for the
design of a static triggering mechanism, namely
tj +1 := inf t > tj + τ
m (t)
m iet | Ψ(o) 0 , (37)
with t0 = 0and with Ψ as in (35).
VI. CASE STUDY ON COOPERATIVE ADAPTIVE
CRUISE CONTROL
In this section, we illustrate the main result by means of a
case study on cooperative adaptive cruise control (CACC). As
shown in [27], in the context of vehicle platooning, wireless
communication between vehicles can have a significant contri-
bution to improving traffic throughput and safety. For a platoon
of two identical vehicles equipped with CACC, the functions f
and gas in (9) are given byf (x, e, w) = A11x + A12e + A13w
and g(x, e, w) = A21x + A22e + A23w, where
A11 =
⎡
⎢
⎢
⎢
⎢
⎢
⎢
⎢
⎢
⎢
⎢
⎢
⎢
⎣
− 1
τc
1
τc
0 0 0 0
0 − 1
h 0 0 0 0
0 0 0 1 −h 0
1 0 0 0 −1 0
0 0 0 0 − 1
τc
1
τc
0 1
h
kp
h
kd
h −kd − 1
h
⎤
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎦
A12 =
&
0 0 0 0 0 1
h
'
,
A13 =
&
0 1
h 0 0 0 0
'
,
A21 =
&
0 1
h 0 0 0 0
'
, A22 = 0, A23 = −1
h
with τc ∈ R>0 a time-constant corresponding to the driveline
dynamics, h ∈ R>0 the time headway (desired time between the
two vehicles) andkp, kd ∈ R>0 the controller gains. Moreover,
the input w represents the control input of the leading vehicle.
See, e.g., [27] for more details. For this example, we use the
following parameter valuesτc = 0.15, h = 0.6, kp = 0.2, kd =
0.7. To comply with safety, one of the control objectives is to
keep the error with respect to the vehicle desired distance small
and therefore we define the performance output as z = Cz x,
where
Cz = 0 0 1 0 0 0 ,
which corresponds to the spacing error between the two vehicles.
The measured output y as in (1) is the desired acceleration of
the leading vehicle and is given by y = Cy x, where
Cy = 0 1 0 0 0 0 ,
and is available at the ETM to determine the transmission in-
stants.
Before the ETM design and the stability and performance
analysis, we first have to guarantee that Condition 1 is met.
For the vehicle platoon system described above, we can take
2) The function ˜Ψ is given by
˜Ψ(m, o, η) = Ψ(o) − σ(η), when m = 0,
−(1 − ω(τ, m)), when m = 1, (34)
where σ is a K ∞ -function that satisfiesσ(s) ω 1s for all
s ∈ R0 , the function Ψ : O → R is given by
Ψ(o) = (|y|) + ¯γω(τ, m)W2(e) (35)
with
ω(τ, m) := 1, for 0 τ τ m
m iet
0, for τ > τm
m iet, (36)
for τ ∈ R0 and with ¯γ as given in (33).
3) The function η0 is given by η0(e) = γφm ietW 2(e).
Then, the closed set A = {ξ ∈ X | x = 0, e = 0}is UGES
and isL ∞ -stable with a finite inducedL ∞ -gain less than or equal
to θ κ
cz β∗ with cz as in (25) and where κ := eς∗(ω1 +ω2 ) , ς∗ :=
ς + ντ1
m iet, β∗ = ω1 − (ω1 + ω2)/T ∗ and T∗ := τD T /(τD +
τ1
m ietT ), for the class of hybrid systems H(ν, τD , ς , T ).
The proof is provided in the Appendix. Observe that the con-
dition given in item 1) imposes restrictions on the DoS parame-
ters τD and T in terms of other system parameters. As such, the
frequency and duration of the allowable DoS attacks are lim-
ited. Moreover, observe that the DoS parameters ν, τD , ς and
T affect the guaranteed L ∞ -gain of the system which illustrates
the tradeoff between robustness with respect to DoS attacks and
performance in the sense that, in general, robustness comes at
the cost of performance.
Observe that in case communication is allowed, the transmis-
sions are scheduled in an event-based fashion (to save valuable
communication resources) whereas in case the communication
is denied, the next transmission is scheduled again after τ1
m iet
time units (to determine when the DoS attack is over) since when
m = 1, which implies thatη = 0at the previous transmission at-
tempt, ˜Ψ(m, o, η) = 0for 0 τ τ 1
m iet and ˜Ψ(m, o, η) = −1
for τ > τ1
m iet. Hence, when m = 1and τ > τ1
m iet , a next jump
occurs as flow condition η 0 will be violated.
Remark 3: Note that this implementation requires the knowl-
edge about when DoS attacks are blocking transmissions, which
could be realized by means of acknowledgements as illustrated
in Fig. 1. Let us remark that the ETM can easily be adjusted
such that it is not required that acknowledgements are being
received instantaneously. For example, the acknowledgement is
allowed to be delayed with, at most, τ1
m iet time units if after
each transmission instant, the ETM keeps track of the evolution
of η for both cases that the transmission has been successful or
denied. For the brevity of exposition, this feature has, however,
been omitted.
The presented framework does not require an acknowledge-
ment scheme when purely periodic sampling with intersampling
time τ1
m iet is employed. The same design conditions lead to the
same guarantees in this case.
Remark 4: The proposed framework can also be used for the
design of a static triggering mechanism, namely
tj +1 := inf t > tj + τ
m (t)
m iet | Ψ(o) 0 , (37)
with t0 = 0and with Ψ as in (35).
VI. CASE STUDY ON COOPERATIVE ADAPTIVE
CRUISE CONTROL
In this section, we illustrate the main result by means of a
case study on cooperative adaptive cruise control (CACC). As
shown in [27], in the context of vehicle platooning, wireless
communication between vehicles can have a significant contri-
bution to improving traffic throughput and safety. For a platoon
of two identical vehicles equipped with CACC, the functions f
and gas in (9) are given byf (x, e, w) = A11x + A12e + A13w
and g(x, e, w) = A21x + A22e + A23w, where
A11 =
⎡
⎢
⎢
⎢
⎢
⎢
⎢
⎢
⎢
⎢
⎢
⎢
⎢
⎣
− 1
τc
1
τc
0 0 0 0
0 − 1
h 0 0 0 0
0 0 0 1 −h 0
1 0 0 0 −1 0
0 0 0 0 − 1
τc
1
τc
0 1
h
kp
h
kd
h −kd − 1
h
⎤
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎦
A12 =
&
0 0 0 0 0 1
h
'
,
A13 =
&
0 1
h 0 0 0 0
'
,
A21 =
&
0 1
h 0 0 0 0
'
, A22 = 0, A23 = −1
h
with τc ∈ R>0 a time-constant corresponding to the driveline
dynamics, h ∈ R>0 the time headway (desired time between the
two vehicles) andkp, kd ∈ R>0 the controller gains. Moreover,
the input w represents the control input of the leading vehicle.
See, e.g., [27] for more details. For this example, we use the
following parameter valuesτc = 0.15, h = 0.6, kp = 0.2, kd =
0.7. To comply with safety, one of the control objectives is to
keep the error with respect to the vehicle desired distance small
and therefore we define the performance output as z = Cz x,
where
Cz = 0 0 1 0 0 0 ,
which corresponds to the spacing error between the two vehicles.
The measured output y as in (1) is the desired acceleration of
the leading vehicle and is given by y = Cy x, where
Cy = 0 1 0 0 0 0 ,
and is available at the ETM to determine the transmission in-
stants.
Before the ETM design and the stability and performance
analysis, we first have to guarantee that Condition 1 is met.
For the vehicle platoon system described above, we can take
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
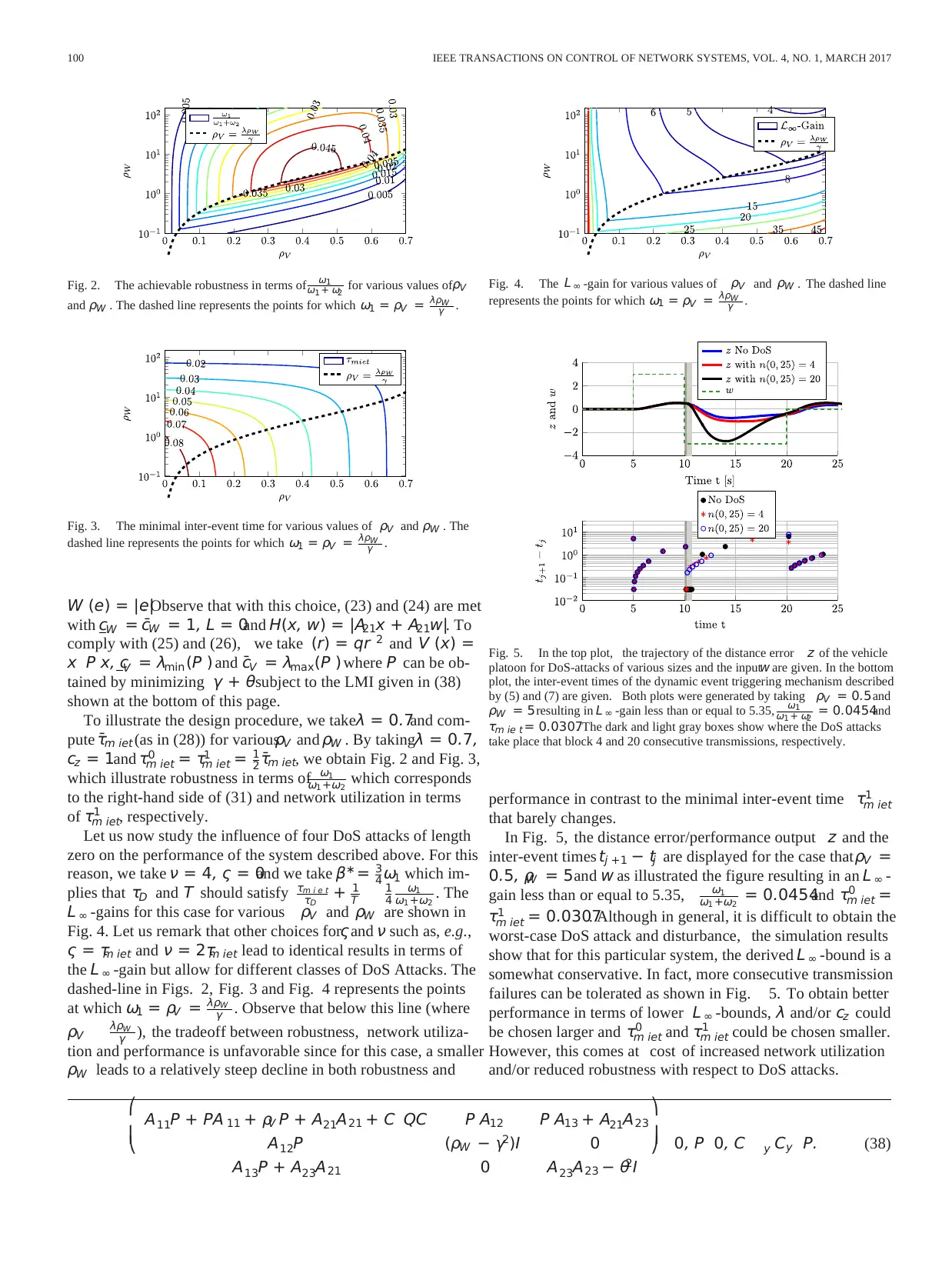
100 IEEE TRANSACTIONS ON CONTROL OF NETWORK SYSTEMS, VOL. 4, NO. 1, MARCH 2017
Fig. 2. The achievable robustness in terms of ω1
ω1 + ω2 for various values ofρV
and ρW . The dashed line represents the points for which ω1 = ρV = λρW
γ .
Fig. 3. The minimal inter-event time for various values of ρV and ρW . The
dashed line represents the points for which ω1 = ρV = λρW
γ .
W (e) = |e|. Observe that with this choice, (23) and (24) are met
with cW = ¯cW = 1, L = 0and H(x, w) = |A21x + A21w|. To
comply with (25) and (26), we take (r) = qr 2 and V (x) =
x P x, cV = λmin (P ) and ¯cV = λmax(P ) where P can be ob-
tained by minimizing γ + θsubject to the LMI given in (38)
shown at the bottom of this page.
To illustrate the design procedure, we takeλ = 0.7and com-
pute ¯τm iet (as in (28)) for variousρV and ρW . By takingλ = 0.7,
cz = 1and τ0
m iet = τ1
m iet = 1
2 ¯τm iet, we obtain Fig. 2 and Fig. 3,
which illustrate robustness in terms of ω1
ω1 +ω2 which corresponds
to the right-hand side of (31) and network utilization in terms
of τ1
m iet, respectively.
Let us now study the influence of four DoS attacks of length
zero on the performance of the system described above. For this
reason, we take ν = 4, ς = 0and we take β∗ = 3
4 ω1 which im-
plies that τD and T should satisfy τm i e t
τD + 1
T
1
4
ω1
ω1 +ω2 . The
L ∞ -gains for this case for various ρV and ρW are shown in
Fig. 4. Let us remark that other choices forςand ν such as, e.g.,
ς = τm iet and ν = 2τm iet lead to identical results in terms of
the L ∞ -gain but allow for different classes of DoS Attacks. The
dashed-line in Figs. 2, Fig. 3 and Fig. 4 represents the points
at which ω1 = ρV = λρW
γ . Observe that below this line (where
ρV λρW
γ ), the tradeoff between robustness, network utiliza-
tion and performance is unfavorable since for this case, a smaller
ρW leads to a relatively steep decline in both robustness and
Fig. 4. The L ∞ -gain for various values of ρV and ρW . The dashed line
represents the points for which ω1 = ρV = λρW
γ .
Fig. 5. In the top plot, the trajectory of the distance error z of the vehicle
platoon for DoS-attacks of various sizes and the inputw are given. In the bottom
plot, the inter-event times of the dynamic event triggering mechanism described
by (5) and (7) are given. Both plots were generated by taking ρV = 0.5and
ρW = 5resulting in L ∞ -gain less than or equal to 5.35, ω1
ω1 + ω2 = 0.0454and
τm ie t = 0.0307. The dark and light gray boxes show where the DoS attacks
take place that block 4 and 20 consecutive transmissions, respectively.
performance in contrast to the minimal inter-event time τ1
m iet
that barely changes.
In Fig. 5, the distance error/performance output z and the
inter-event times tj +1 − tj are displayed for the case thatρV =
0.5, ρW = 5and w as illustrated the figure resulting in an L ∞ -
gain less than or equal to 5.35, ω1
ω1 +ω2 = 0.0454and τ0
m iet =
τ1
m iet = 0.0307. Although in general, it is difficult to obtain the
worst-case DoS attack and disturbance, the simulation results
show that for this particular system, the derived L ∞ -bound is a
somewhat conservative. In fact, more consecutive transmission
failures can be tolerated as shown in Fig. 5. To obtain better
performance in terms of lower L ∞ -bounds, λ and/or cz could
be chosen larger and τ0
m iet and τ1
m iet could be chosen smaller.
However, this comes at cost of increased network utilization
and/or reduced robustness with respect to DoS attacks.
⎛
⎜
⎝
A11P + PA 11 + ρV P + A21A21 + C QC P A12 P A13 + A21A23
A12P (ρW − γ2)I 0
A13P + A23A21 0 A23A23 − θ2I
⎞
⎟
⎠ 0, P 0, C y Cy P. (38)
Fig. 2. The achievable robustness in terms of ω1
ω1 + ω2 for various values ofρV
and ρW . The dashed line represents the points for which ω1 = ρV = λρW
γ .
Fig. 3. The minimal inter-event time for various values of ρV and ρW . The
dashed line represents the points for which ω1 = ρV = λρW
γ .
W (e) = |e|. Observe that with this choice, (23) and (24) are met
with cW = ¯cW = 1, L = 0and H(x, w) = |A21x + A21w|. To
comply with (25) and (26), we take (r) = qr 2 and V (x) =
x P x, cV = λmin (P ) and ¯cV = λmax(P ) where P can be ob-
tained by minimizing γ + θsubject to the LMI given in (38)
shown at the bottom of this page.
To illustrate the design procedure, we takeλ = 0.7and com-
pute ¯τm iet (as in (28)) for variousρV and ρW . By takingλ = 0.7,
cz = 1and τ0
m iet = τ1
m iet = 1
2 ¯τm iet, we obtain Fig. 2 and Fig. 3,
which illustrate robustness in terms of ω1
ω1 +ω2 which corresponds
to the right-hand side of (31) and network utilization in terms
of τ1
m iet, respectively.
Let us now study the influence of four DoS attacks of length
zero on the performance of the system described above. For this
reason, we take ν = 4, ς = 0and we take β∗ = 3
4 ω1 which im-
plies that τD and T should satisfy τm i e t
τD + 1
T
1
4
ω1
ω1 +ω2 . The
L ∞ -gains for this case for various ρV and ρW are shown in
Fig. 4. Let us remark that other choices forςand ν such as, e.g.,
ς = τm iet and ν = 2τm iet lead to identical results in terms of
the L ∞ -gain but allow for different classes of DoS Attacks. The
dashed-line in Figs. 2, Fig. 3 and Fig. 4 represents the points
at which ω1 = ρV = λρW
γ . Observe that below this line (where
ρV λρW
γ ), the tradeoff between robustness, network utiliza-
tion and performance is unfavorable since for this case, a smaller
ρW leads to a relatively steep decline in both robustness and
Fig. 4. The L ∞ -gain for various values of ρV and ρW . The dashed line
represents the points for which ω1 = ρV = λρW
γ .
Fig. 5. In the top plot, the trajectory of the distance error z of the vehicle
platoon for DoS-attacks of various sizes and the inputw are given. In the bottom
plot, the inter-event times of the dynamic event triggering mechanism described
by (5) and (7) are given. Both plots were generated by taking ρV = 0.5and
ρW = 5resulting in L ∞ -gain less than or equal to 5.35, ω1
ω1 + ω2 = 0.0454and
τm ie t = 0.0307. The dark and light gray boxes show where the DoS attacks
take place that block 4 and 20 consecutive transmissions, respectively.
performance in contrast to the minimal inter-event time τ1
m iet
that barely changes.
In Fig. 5, the distance error/performance output z and the
inter-event times tj +1 − tj are displayed for the case thatρV =
0.5, ρW = 5and w as illustrated the figure resulting in an L ∞ -
gain less than or equal to 5.35, ω1
ω1 +ω2 = 0.0454and τ0
m iet =
τ1
m iet = 0.0307. Although in general, it is difficult to obtain the
worst-case DoS attack and disturbance, the simulation results
show that for this particular system, the derived L ∞ -bound is a
somewhat conservative. In fact, more consecutive transmission
failures can be tolerated as shown in Fig. 5. To obtain better
performance in terms of lower L ∞ -bounds, λ and/or cz could
be chosen larger and τ0
m iet and τ1
m iet could be chosen smaller.
However, this comes at cost of increased network utilization
and/or reduced robustness with respect to DoS attacks.
⎛
⎜
⎝
A11P + PA 11 + ρV P + A21A21 + C QC P A12 P A13 + A21A23
A12P (ρW − γ2)I 0
A13P + A23A21 0 A23A23 − θ2I
⎞
⎟
⎠ 0, P 0, C y Cy P. (38)

DOLK et al.: EVENT-TRIGGERED CONTROL SYSTEMS UNDER DENIAL-OF-SERVICE ATTACKS 101
VII. CONCLUSION
In this work, we addressed the design of resource-aware and
resilient control strategies for networked control systems (NCS)
subject to malicious Denial-of-service (DoS) attacks. In par-
ticular, the control and communication strategy was based on
an output-based event-triggered control scheme applicable to a
class of non-linear feedback systems that are subject to exoge-
nous disturbances. The proposed framework led to guarantees
regarding the existence of a robust strictly positive lower bound
on the inter-event times despite the presence of disturbances
and DoS attacks. Additionally, based on the natural assumption
that DoS attacks are restricted in terms of frequency and dura-
tion, we showed that desired stability and performance criteria
in terms of induced L ∞ -gains can be guaranteed.
APPENDIX
Proof of Theorem 2: The main idea behind the proof is to
regard the closed-loop system HT as a system switching be-
tween a stable hybrid model (when effectively no DoS attack
is active) and an unstable mode (when effectively a DoS attack
is active). Inspired by the concept of average dwell-time [11],
we can then exploit the duration and frequency constraints of
the DoS attacks to conclude UGES (or L ∞ -stability a finite in-
duced L ∞ -gain) of the set A for the class of hybrid systems
H(ν, τD , ς , T ). For clarity of exposition, the proof consists of
four steps. In the proof, we often omit the (hybrid) time argu-
ments of the solution ξ of a hybrid system HT and we do not
mention dom ξ explicitly.
Step I: Lyapunov/storage function analysis. Let R (X0)
denote all the reachable states of a hybrid system HT ∈
H(ν, τD , ς , T )for ξ(0, 0) ∈ X0, see also [24, Chapter 6].
Lemma 3: For any χ ∈ R (X0) it holds that
1) {m = 1 ∨ τ τ0
m iet} ⇔ φ = φm iet
2) λ−1 φ φ m iet
3) η 0
Moreover, for allχ ∈ R(X0)\D there exists an ε > 0and an
absolutely continuous functionz : [0, ε] → Rn such thatz(0) =
χ, ˙z(t) = F (z(t))for almost all t ∈ [0, ε]and z(t) ∈ Cfor all
t ∈ (0, ε].
The proof is omitted for the sake of brevity. Consider the
candidate Lyapunov/storage function,
U(ξ) = V (x) + γφW2(e) + η. (39)
Given the second and third item of Lemma 3 and the fact that
according to Condition 1,V and W satisfy (25) and (23), respec-
tively, and γ > 0, we find that there exists a positive constant
cU ∈ R0 such that
cU |ξ|2
A U (ξ), (40)
for all ξ ∈ R (X0) where A = {ξ ∈ X | x = 0, e = 0}. Hence,
U constitutes a suitable candidate Lyapunov/storage function
for the cases w = 0and w = 0, respectively.
To study the stability and the performance, we will discuss
how the functionU evolves over time by considering both jumps
(when ξ ∈ D), and flows (when ξ ∈ C).
Jumps: We can see from (14) and (27) that at trans-
mission events when communication is possible, i.e., if ξ ∈
R (X0) and ξ ∈ D and s /∈ T (and thus η = 0), we have
that U (ξ+ ) − U(ξ) = −γφW2(e) + η0(e). By recalling that
η0 = γφm ietW2(e), the first item of Lemma 3 and by using the
fact that τ τ 0
m iet when ξ ∈ D, we have that
U (ξ+ ) − U (ξ) = 0, (41)
when ξ ∈ R (X0) ∩ D and s /∈ T (and thus τ τ 0
m iet). At
transmission times during a DoS attack, i.e., when ξ ∈ D, and
s ∈ T, (41) holds as well sincee+ = e, φ+ = φ, η+ = η = 0
and x + = x.
Flows: For the bounds on U during flow we consider two
cases depending on whether the most recent transmission at-
tempt was successful (m = 0)or not (m = 1).
Case I (m = 0): From (24), (26) and (27), we can derive that
for almost all ξ ∈ R (X0) with m = 0and for w ∈ Rnw ,
∇U (ξ), F (ξ, w) −(|y|) − H 2(x, w) + γ2W 2(e)
+ 2γφW (e) (LW (e) + H(x, w))
− ω(τ, 0)γW2(e) 2Lφ + γ φ2 + 1
− ρW W 2(e) − ρV V (x) +˜Ψ(m, o, η) + θ2|w|2
−ρ V V (x) − ρW W 2(e) − M (ξ, w) +˜Ψ(m, o, η)
+ θ2|w|2, (42)
with ω(τ, m)as in (36) and where M given by
M(ξ, w) =
⎧
⎨
⎩
M 1(ξ, w), for 0 τ τ 0
m iet,
M 2(ξ, w), for τ > τ0
m iet,
(43)
where for all ξ ∈ Xand w ∈ Rnw
M 1(ξ, w) : = (|y|) + (H(x, w) − γφW (e))2 , (44)
M 2(ξ, w) : = (|y|) + H 2(x, w) − 2γφW (e)H(x, w)
− γ2 + 2γφL W 2(e). (45)
By using the fact that 2γφW (e)H(x, w) γ2φ2W2(e) +
H 2(x, w), we can conclude from (35) and (43) that Ψ(o)
M (ξ, w)for all o ∈ O. Using the latter fact, we obtain from
(34) and (42) that form = 0, ∇U (ξ), F (ξ, w) −ρV V (x) −
ρW W 2(e) − ω1η + θ2|w|2. By using Lemma 3 and the fact that
V (x) c ¯V |x|2 due to (25), we can conclude that for almost all
ξ ∈ R (X0) with m = 0and for w ∈ Rnw , we have that
∇U (ξ), F (ξ, w) −ω 1U (ξ) + θ2|w|2, (46)
with ω1 as in (32).
Case II (m = 1): Observe that form = 1, we have that ˙φ = 0
and ˙η = 0due to (7), (27) and (34), respectively. Hence, it holds
that for almost all ξ ∈ R (X0) with m = 1and for all w ∈ Rnw
∇U (ξ), F (ξ, w) −(|y|) − H 2(x, w) + γ2W 2(e)
+ 2γφW (e) (LW (e) + H(x, w))
− ρW W (e) − ρV V (x) + θ2|w|2.
VII. CONCLUSION
In this work, we addressed the design of resource-aware and
resilient control strategies for networked control systems (NCS)
subject to malicious Denial-of-service (DoS) attacks. In par-
ticular, the control and communication strategy was based on
an output-based event-triggered control scheme applicable to a
class of non-linear feedback systems that are subject to exoge-
nous disturbances. The proposed framework led to guarantees
regarding the existence of a robust strictly positive lower bound
on the inter-event times despite the presence of disturbances
and DoS attacks. Additionally, based on the natural assumption
that DoS attacks are restricted in terms of frequency and dura-
tion, we showed that desired stability and performance criteria
in terms of induced L ∞ -gains can be guaranteed.
APPENDIX
Proof of Theorem 2: The main idea behind the proof is to
regard the closed-loop system HT as a system switching be-
tween a stable hybrid model (when effectively no DoS attack
is active) and an unstable mode (when effectively a DoS attack
is active). Inspired by the concept of average dwell-time [11],
we can then exploit the duration and frequency constraints of
the DoS attacks to conclude UGES (or L ∞ -stability a finite in-
duced L ∞ -gain) of the set A for the class of hybrid systems
H(ν, τD , ς , T ). For clarity of exposition, the proof consists of
four steps. In the proof, we often omit the (hybrid) time argu-
ments of the solution ξ of a hybrid system HT and we do not
mention dom ξ explicitly.
Step I: Lyapunov/storage function analysis. Let R (X0)
denote all the reachable states of a hybrid system HT ∈
H(ν, τD , ς , T )for ξ(0, 0) ∈ X0, see also [24, Chapter 6].
Lemma 3: For any χ ∈ R (X0) it holds that
1) {m = 1 ∨ τ τ0
m iet} ⇔ φ = φm iet
2) λ−1 φ φ m iet
3) η 0
Moreover, for allχ ∈ R(X0)\D there exists an ε > 0and an
absolutely continuous functionz : [0, ε] → Rn such thatz(0) =
χ, ˙z(t) = F (z(t))for almost all t ∈ [0, ε]and z(t) ∈ Cfor all
t ∈ (0, ε].
The proof is omitted for the sake of brevity. Consider the
candidate Lyapunov/storage function,
U(ξ) = V (x) + γφW2(e) + η. (39)
Given the second and third item of Lemma 3 and the fact that
according to Condition 1,V and W satisfy (25) and (23), respec-
tively, and γ > 0, we find that there exists a positive constant
cU ∈ R0 such that
cU |ξ|2
A U (ξ), (40)
for all ξ ∈ R (X0) where A = {ξ ∈ X | x = 0, e = 0}. Hence,
U constitutes a suitable candidate Lyapunov/storage function
for the cases w = 0and w = 0, respectively.
To study the stability and the performance, we will discuss
how the functionU evolves over time by considering both jumps
(when ξ ∈ D), and flows (when ξ ∈ C).
Jumps: We can see from (14) and (27) that at trans-
mission events when communication is possible, i.e., if ξ ∈
R (X0) and ξ ∈ D and s /∈ T (and thus η = 0), we have
that U (ξ+ ) − U(ξ) = −γφW2(e) + η0(e). By recalling that
η0 = γφm ietW2(e), the first item of Lemma 3 and by using the
fact that τ τ 0
m iet when ξ ∈ D, we have that
U (ξ+ ) − U (ξ) = 0, (41)
when ξ ∈ R (X0) ∩ D and s /∈ T (and thus τ τ 0
m iet). At
transmission times during a DoS attack, i.e., when ξ ∈ D, and
s ∈ T, (41) holds as well sincee+ = e, φ+ = φ, η+ = η = 0
and x + = x.
Flows: For the bounds on U during flow we consider two
cases depending on whether the most recent transmission at-
tempt was successful (m = 0)or not (m = 1).
Case I (m = 0): From (24), (26) and (27), we can derive that
for almost all ξ ∈ R (X0) with m = 0and for w ∈ Rnw ,
∇U (ξ), F (ξ, w) −(|y|) − H 2(x, w) + γ2W 2(e)
+ 2γφW (e) (LW (e) + H(x, w))
− ω(τ, 0)γW2(e) 2Lφ + γ φ2 + 1
− ρW W 2(e) − ρV V (x) +˜Ψ(m, o, η) + θ2|w|2
−ρ V V (x) − ρW W 2(e) − M (ξ, w) +˜Ψ(m, o, η)
+ θ2|w|2, (42)
with ω(τ, m)as in (36) and where M given by
M(ξ, w) =
⎧
⎨
⎩
M 1(ξ, w), for 0 τ τ 0
m iet,
M 2(ξ, w), for τ > τ0
m iet,
(43)
where for all ξ ∈ Xand w ∈ Rnw
M 1(ξ, w) : = (|y|) + (H(x, w) − γφW (e))2 , (44)
M 2(ξ, w) : = (|y|) + H 2(x, w) − 2γφW (e)H(x, w)
− γ2 + 2γφL W 2(e). (45)
By using the fact that 2γφW (e)H(x, w) γ2φ2W2(e) +
H 2(x, w), we can conclude from (35) and (43) that Ψ(o)
M (ξ, w)for all o ∈ O. Using the latter fact, we obtain from
(34) and (42) that form = 0, ∇U (ξ), F (ξ, w) −ρV V (x) −
ρW W 2(e) − ω1η + θ2|w|2. By using Lemma 3 and the fact that
V (x) c ¯V |x|2 due to (25), we can conclude that for almost all
ξ ∈ R (X0) with m = 0and for w ∈ Rnw , we have that
∇U (ξ), F (ξ, w) −ω 1U (ξ) + θ2|w|2, (46)
with ω1 as in (32).
Case II (m = 1): Observe that form = 1, we have that ˙φ = 0
and ˙η = 0due to (7), (27) and (34), respectively. Hence, it holds
that for almost all ξ ∈ R (X0) with m = 1and for all w ∈ Rnw
∇U (ξ), F (ξ, w) −(|y|) − H 2(x, w) + γ2W 2(e)
+ 2γφW (e) (LW (e) + H(x, w))
− ρW W (e) − ρV V (x) + θ2|w|2.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

102 IEEE TRANSACTIONS ON CONTROL OF NETWORK SYSTEMS, VOL. 4, NO. 1, MARCH 2017
Using the fact that 2γφW (e)H(x, w) γ2φ2W2(e) +
H 2(x, w), and Lemma 3 we obtain that ∇U (ξ), F (ξ, w)
(¯γ − ρW )W 2(e) + θ2|w|2 with ¯γ as in (33). Hence, it holds
that for almost all ξ ∈ R (X0) with m = 1and all w ∈ Rnw
∇U (ξ), F (ξ, w) ω 2U (ξ) + θ2|w|2 (47)
with ω2 as in (32). In fact, observe that since ω2 > 0 due to
Condition 1, (47) also holds when m = 0.
Observe that a system HT ∈ H(ν, τD , ς , T )does not exhibit
Zeno-behaviour due to a strictly positive MIET. Moreover, ob-
serve that finite escape-times are excluded from the system due
to the bounds on the statesx and eas in (40), (41), (46), (47) and
the fact that the trajectories of the state variablesτ, s, m, η, and
φ do not exhibit finite escape-times. Given the aforementioned
facts and the last property mentioned in Lemma 3, we can con-
clude that a system HT ∈ H(ν, τD , ς , T )with ξ(0, 0) ∈ X0 is
indeed persistently flowing with respect to initial state set X0.
Step II: Characterization of stable and unstable modes. In
the previous step, we have shown how the Lyapunov/storage
function behaves for both the cases where m = 0and m = 1,
see (46) (m = 0)and (47) (m = 1). To use average dwell-time
arguments, it is needed to determine the collection of time in-
stants at which either m = 0or m = 1. Unfortunately, this can
not directly be related to T , since the value of ˆy is typically not
updated immediately after a DoS interval has ended due toτ1
m iet
being a lower bound on the inter-event timestj +1 − tj , j ∈ N,
for which transmission time tj corresponds to an unsuccessful
transmission attempt. For this reason, we will consider the “ef-
fective” DoS attacks, decompose the time axis accordingly and
relate these “effective” DoS attacks to T via the collection of
DoS intervals as given in (17). To do so, we first define for a
given maximal solution ξ, the collection of time instants in the
interval [T1, T2], with T2 T 1, at which the most recent trans-
mission attempt was successful and at which no DoS attack is
active as
¯Θξ(T1, T2) := ( ¯t ∈ (T1, T2) |
¯t /∈ T and ∀j ∈ N, (¯t, j) ∈dom ξ ⇒ m(¯t, j) = 0
) . (48)
The system HT is said to be in the stable mode (satisfying (46))
at a time instant t if t ∈ ¯Θξ(0, ∞). In addition, we define the
collection of “effective” DoS attacks in the interval [T1, T2],
with T2 T 1 as
Ξξ(T1, T2) := [T1, T2]/ ¯Θξ(T1, T2). (49)
Likewise, the system is said to be in the unstable mode (satisfy-
ing (47)) at a time instant t if t ∈ Ξξ(0, ∞). Since for T1, T2 ∈
R0 with T2 T 1, ¯Θξ(T1, T2) ∪ Ξξ(T1, T2) = [T1, T2], we
can write ¯Θξ(T1, T2) and Ξξ(T1, T2) as follows
Ξξ(T1, T2) :=
k∈N
Zk ∩ [T1, T2], (50)
and
¯Θξ(T1, T2) :=
k∈N
Wk−1 ∩ [T1, T2], (51)
where for k ∈ N
Zk := [ζk , ζk + vk ) when vk > 0,
{ζk } when vk = 0,
Wk := [ζk + vk , ζk+1 ) when vk > 0,
(ζk , ζk+1 ) when vk = 0,
where vk denotes the time elapsed between ζk and the next
successful transmission attempt, and where ζ0 := h0 where
W−1 = [0, ζ0) when h0 > 0 and W−1 = ∅when h0 = 0. The
collection of effective DoS attacks can be related to the original
collection of DoS intervals as given in (17) as
|Ξξ(T1, T2)| |Ξ(T 1, T2)| + (1 + n(T1, T2))τ1
m iet, (52)
for all T1, T2 ∈ R0 with T2 T 1, where n(T1, T2) denotes
the number of DoS attacks in the interval [T1, T2). Indeed, due
to the finite sampling rate, the effective DoS interval ¯Hn is
extended with maximally τ1
m iet time units compared to Hn ,
n ∈ N. Since this extension might also occur at the begin-
ning of an interval [T1, T2), the collection of effective DoS
attacks over the interval [T1, T2) is at most prolonged with
(1 + n(T1, T2))τ1
m iet time units. Observe that the latter is not
the case if T1 ∈ k∈N Wk−1 ∪ {0}, i.e.,
|Ξξ(T1, T2)| |Ξ(T 1, T2)| + n(T1, T2)τ1
m iet, (53)
for all T1 ∈ k∈N Wk−1 ∪ {0} and all T2 ∈ RT 1 . By
means of Definition 1 and Definition 2 for the specific values of
τD and T , we find that according to (53)
|Ξξ(T1, T2)| ς ∗+ T2 − T1
T∗
, (54)
where ς∗ := ς + ντ1
m iet and T∗ := τD T /(τD + τ1
m ietT )for all
T1 ∈ k∈N Wk−1 ∪ {0}and all T2 ∈ RT 1 .
In summary, in this second step of the proof, we defined ef-
fective DoS sequences, which led to the intervals Zk and Wk ,
k ∈ N, representing the stable and (possibly) unstable mode of
the system, respectively. Furthermore, we showed how this ef-
fective DoS is related to the original DoS sequence. This relation
will be important in the stability and performance analysis.
Step III: Time-trajectory bounds on Lyapunov/storage func-
tion. As already mentioned, the collection of time instants at
which either m = 0or m = 1can not directly be related to T .
However, we can deduce the following implications regarding a
trajectory ξ with ξ(0, 0) ∈ X0 and the stable and unstable mode
descriptions
(t, j) ∈ (Wk × N) ∩dom ξ ⇒ m(t, j) = 0,
(t, j) ∈ (Zk × N) ∩dom ξ ⇒ (m(t, j) = 0or m(t, j) = 1).
Based on these implications, (41), (46) and (47), we have that
for all (t, j) ∈ (Wk × N) ∩dom ξ, k ∈ N ∪ {−1}
U (ξ(t, j)) e −ω1 (t−ζk −vk ) U (ξ(ζk + vk , j))
+ θ2
* t
(ζk +vk )
e−ω1 (t−s) |w(s)|2ds (55)
Using the fact that 2γφW (e)H(x, w) γ2φ2W2(e) +
H 2(x, w), and Lemma 3 we obtain that ∇U (ξ), F (ξ, w)
(¯γ − ρW )W 2(e) + θ2|w|2 with ¯γ as in (33). Hence, it holds
that for almost all ξ ∈ R (X0) with m = 1and all w ∈ Rnw
∇U (ξ), F (ξ, w) ω 2U (ξ) + θ2|w|2 (47)
with ω2 as in (32). In fact, observe that since ω2 > 0 due to
Condition 1, (47) also holds when m = 0.
Observe that a system HT ∈ H(ν, τD , ς , T )does not exhibit
Zeno-behaviour due to a strictly positive MIET. Moreover, ob-
serve that finite escape-times are excluded from the system due
to the bounds on the statesx and eas in (40), (41), (46), (47) and
the fact that the trajectories of the state variablesτ, s, m, η, and
φ do not exhibit finite escape-times. Given the aforementioned
facts and the last property mentioned in Lemma 3, we can con-
clude that a system HT ∈ H(ν, τD , ς , T )with ξ(0, 0) ∈ X0 is
indeed persistently flowing with respect to initial state set X0.
Step II: Characterization of stable and unstable modes. In
the previous step, we have shown how the Lyapunov/storage
function behaves for both the cases where m = 0and m = 1,
see (46) (m = 0)and (47) (m = 1). To use average dwell-time
arguments, it is needed to determine the collection of time in-
stants at which either m = 0or m = 1. Unfortunately, this can
not directly be related to T , since the value of ˆy is typically not
updated immediately after a DoS interval has ended due toτ1
m iet
being a lower bound on the inter-event timestj +1 − tj , j ∈ N,
for which transmission time tj corresponds to an unsuccessful
transmission attempt. For this reason, we will consider the “ef-
fective” DoS attacks, decompose the time axis accordingly and
relate these “effective” DoS attacks to T via the collection of
DoS intervals as given in (17). To do so, we first define for a
given maximal solution ξ, the collection of time instants in the
interval [T1, T2], with T2 T 1, at which the most recent trans-
mission attempt was successful and at which no DoS attack is
active as
¯Θξ(T1, T2) := ( ¯t ∈ (T1, T2) |
¯t /∈ T and ∀j ∈ N, (¯t, j) ∈dom ξ ⇒ m(¯t, j) = 0
) . (48)
The system HT is said to be in the stable mode (satisfying (46))
at a time instant t if t ∈ ¯Θξ(0, ∞). In addition, we define the
collection of “effective” DoS attacks in the interval [T1, T2],
with T2 T 1 as
Ξξ(T1, T2) := [T1, T2]/ ¯Θξ(T1, T2). (49)
Likewise, the system is said to be in the unstable mode (satisfy-
ing (47)) at a time instant t if t ∈ Ξξ(0, ∞). Since for T1, T2 ∈
R0 with T2 T 1, ¯Θξ(T1, T2) ∪ Ξξ(T1, T2) = [T1, T2], we
can write ¯Θξ(T1, T2) and Ξξ(T1, T2) as follows
Ξξ(T1, T2) :=
k∈N
Zk ∩ [T1, T2], (50)
and
¯Θξ(T1, T2) :=
k∈N
Wk−1 ∩ [T1, T2], (51)
where for k ∈ N
Zk := [ζk , ζk + vk ) when vk > 0,
{ζk } when vk = 0,
Wk := [ζk + vk , ζk+1 ) when vk > 0,
(ζk , ζk+1 ) when vk = 0,
where vk denotes the time elapsed between ζk and the next
successful transmission attempt, and where ζ0 := h0 where
W−1 = [0, ζ0) when h0 > 0 and W−1 = ∅when h0 = 0. The
collection of effective DoS attacks can be related to the original
collection of DoS intervals as given in (17) as
|Ξξ(T1, T2)| |Ξ(T 1, T2)| + (1 + n(T1, T2))τ1
m iet, (52)
for all T1, T2 ∈ R0 with T2 T 1, where n(T1, T2) denotes
the number of DoS attacks in the interval [T1, T2). Indeed, due
to the finite sampling rate, the effective DoS interval ¯Hn is
extended with maximally τ1
m iet time units compared to Hn ,
n ∈ N. Since this extension might also occur at the begin-
ning of an interval [T1, T2), the collection of effective DoS
attacks over the interval [T1, T2) is at most prolonged with
(1 + n(T1, T2))τ1
m iet time units. Observe that the latter is not
the case if T1 ∈ k∈N Wk−1 ∪ {0}, i.e.,
|Ξξ(T1, T2)| |Ξ(T 1, T2)| + n(T1, T2)τ1
m iet, (53)
for all T1 ∈ k∈N Wk−1 ∪ {0} and all T2 ∈ RT 1 . By
means of Definition 1 and Definition 2 for the specific values of
τD and T , we find that according to (53)
|Ξξ(T1, T2)| ς ∗+ T2 − T1
T∗
, (54)
where ς∗ := ς + ντ1
m iet and T∗ := τD T /(τD + τ1
m ietT )for all
T1 ∈ k∈N Wk−1 ∪ {0}and all T2 ∈ RT 1 .
In summary, in this second step of the proof, we defined ef-
fective DoS sequences, which led to the intervals Zk and Wk ,
k ∈ N, representing the stable and (possibly) unstable mode of
the system, respectively. Furthermore, we showed how this ef-
fective DoS is related to the original DoS sequence. This relation
will be important in the stability and performance analysis.
Step III: Time-trajectory bounds on Lyapunov/storage func-
tion. As already mentioned, the collection of time instants at
which either m = 0or m = 1can not directly be related to T .
However, we can deduce the following implications regarding a
trajectory ξ with ξ(0, 0) ∈ X0 and the stable and unstable mode
descriptions
(t, j) ∈ (Wk × N) ∩dom ξ ⇒ m(t, j) = 0,
(t, j) ∈ (Zk × N) ∩dom ξ ⇒ (m(t, j) = 0or m(t, j) = 1).
Based on these implications, (41), (46) and (47), we have that
for all (t, j) ∈ (Wk × N) ∩dom ξ, k ∈ N ∪ {−1}
U (ξ(t, j)) e −ω1 (t−ζk −vk ) U (ξ(ζk + vk , j))
+ θ2
* t
(ζk +vk )
e−ω1 (t−s) |w(s)|2ds (55)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

DOLK et al.: EVENT-TRIGGERED CONTROL SYSTEMS UNDER DENIAL-OF-SERVICE ATTACKS 103
and for all (t, j) ∈ (Zk × N) ∩dom ξ, k ∈ N
U (ξ(t, j)) e ω2 (t−ζm ) U (ξ(ζk , j))
+ θ2
* t
ζk
eω2 (t−s) |w(s)|2ds. (56)
In essence, the right-hand sides of (55) and (56) reflect bounds
on the Lyapunov/storage function U over (hybrid) time for the
stable and unstable modes, respectively. In order to asses the
performance of a system HT ∈ H(ν, τD , ς , T ), we require an
upper-bound that holds for all (t, j) ∈dom ξ. For this reason,
consider the following statement.
Lemma 4: For all (t, j) ∈dom ξ, it holds that
U (ξ(t, j)) Υ(0, t)U (ξ(0, 0)) + θ2
* t
0
Υ(s, t)|w(s)|2ds
(57)
with Υ(s, t) := e−ω1 |¯Θξ (s,t)| eω2 |Ξξ (s,t)| .
Proof of Lemma 4: We will prove Lemma 4 by induction.
First, we need to prove that (57) holds for all (t, j) ∈ [0, ζ0) ×
N ∩ dom ξ. To do so, observe that for all (t, j) ∈ W−1 × N ∩
dom ξ it holds that |¯Θξ(0, t)| = tand |Ξξ(0, t)| = 0. By sub-
stituting the latter in (57), we can conclude that for all (t, j) ∈
W−1 × N ∩dom ξ, the inequality given in (57) coincides with
(55). As such, (57) holds for all (t, j) ∈ W−1 × N ∩dom ξ
and thus for all (t, j) ∈ [0, ζ0) × N ∩dom ξ. Now assume (57)
holds for all (t, j) ∈ [0, ζp) × N ∩dom ξ, where p ∈ N. By
means of this hypothesis and the inequality in (56), we find that
for all (t, j) ∈ (Zp × N) ∩dom ξ,
U (ξ(t, j)) e ω2 (t−ζp ) Υ(0, ζp)U (ξ(0, 0))
+ θ2eω2 (t−ζp )
* ζp
0
Υ(s, ζp)|w(s)|2ds
+ θ2
* t
ζp
eω2 (t−s) |w(s)|2ds. (58)
Since for all t ∈ Zp and all s ∈ [0, t],|¯Θξ(s, ζp)| =
|¯Θξ(s, t)| and t − ζp + |Ξξ(s, ζp)| = |Ξξ(s, t)|, we have that
eω2 (t−ζp ) Υ(s, ζp) = Υ(s, t) for all t ∈ Zp and all s ∈ [0, t].
Substitution of the latter in (58) yields that for all (t, j) ∈
(Zp × N) ∩dom ξ,
U (ξ(t, j)) Υ(0, t)U (ξ(0, 0)) + θ2
* ζp
0
Υ(s, t)|w(s)|2ds
+ θ2
* t
ζp
eω2 (t−s) |w(s)|2ds. (59)
Note that for all t ∈ Zp and s ∈ [ζp, t], t − s = |Ξξ(s, t)|and
in accordance with (51), |¯Θξ(s, t)| = 0and thus eω2 (t−s) =
Υ(s, t) for all t ∈ Zp and s ∈ [ζp, t]. By combining the latter
with (59), we can see that (57) holds for all (t, j) ∈ ([0, ζp +
vp) × N) ∩dom ξ, p ∈ N.
Now we consider the interval Wp. Using (55), we have that
for all (t, j) ∈ (Wp × N) ∩dom ξ,
U (ξ(t, j)) e −ω1 (t−ζp −vp ) Υ(0, ζp + vp)U (ξ(0, 0))
+ θ2e−ω1 (t−ζp −vp )
* ζp +vp
0
Υ(s, ζp + vp)|w(s)|2ds
+ θ2
* t
ζp +vp
e−ω1 (t−s) |w(s)|2ds. (60)
Since t − ζp − vp + |¯Θξ(s, ζp + vp)| = |¯Θξ(s, t)| and
|Ξξ(s, ζp + vp)| = |Ξξ(s, t)|for all t ∈ Wp and all s ∈ [0, t],
we obtain
e−ω1 (t−ζp ) Υ(s, ζp) = Υ(s, t) (61)
for all t ∈ Wp and all s ∈ [0, t]. Substitution of (61) in (60)
yields that for all (t, j) ∈ (Wp × N) ∩dom ξ,
U (ξ(t, j)) Υ(0, t)U (ξ(0, 0)) + θp
* ζp
0
Υ(s, t)|w(s)|2ds
+ θp
t*
ζp
e−ω1 (t−s) |w(s)|2ds. (62)
Combining (61) with the fact that for all t ∈ Wp and s ∈
[ζp + vp, t], t − s = |¯Θξ(s, t)| and in accordance with (50),
|Ξξ(s, t)| = 0, we can see that e−ω1 (t−s) = Υ(s, t) for all
t ∈ Wp and s ∈ [ζp + vp, t]. By means of the latter, we can
conclude that (57) coincides with (62) and thus (57) holds for
all (t, j) ∈ ([0, ζp+1) × N) ∩dom ξ, which concludes the proof
of Lemma 4.
Step IV: Stability and performance analysis. In the last step
of the proof, we show that under (ν, τD , ς , T )-DoS sequences
with τD and T satisfying (31), the system HT is UGES, and
has a finite inducedL ∞ -gain. By means of (54) and the fact that
|¯Θξ(T1, T2)| = T2 − T1 − |Ξξ(T1, T2)|, we obtain that
Υ(T 1, T2) κe −β∗(T 2 −T1 ) , (63)
for all T2 ∈ R0 and all T1 ∈ k∈N Wk−1 ∪ {0}∩ [0, T2],
where κ := eς∗(ω1 +ω2 ) and where β∗ := ω1 − (ω1 + ω2)/T ∗.
Important to note is that condition (31) assures that β∗ > 0.
The inequality given in (63) does not only hold for
T1 ∈ k∈N Wk−1 ∪ {0}∩ [0, T2]. In fact, the inequality
holds for all T1, T2 ∈ R0 with T1 T 2 due to the fol-
lowing. Let 0 T 1 T 2 be arbitrary and consider T ∗
1 =
sup ˜T T 1 | ˜T ∈ k∈N Wk ∪ {0} . Since |Θ(T∗
1 , T1)| =
0, we can write Υ(T ∗
1 , T2) = Υ(T1, T2)eω2 (T 1 −T ∗
1 ) for all
T1, T2 ∈ R0 with T1 T 2. Hence, we have that Υ(T 1, T2)
Υ(T ∗
1 , T2). Due to (63) and the facts that β∗ > 0 and
T ∗
1 ∈ k∈N Wk ∪ {0}∩ [0, T2], we have thatΥ(T ∗
1 , T2)
κe−β∗(T 2 −T ∗
1 ) κe −β∗(T 2 −T1 ) . for all T1, T2 ∈ R0 with T1
T2. Hence, (63) holds for all T1, T2 ∈ R0 with T1 T 2.
1) Stability analysis for the case w = 0. By combining (57)
and (63) for the case w = 0, we find that for all (t, j) ∈
dom ξ
U (ξ(t, j)) κe −β∗t U (ξ(0, 0)).
and for all (t, j) ∈ (Zk × N) ∩dom ξ, k ∈ N
U (ξ(t, j)) e ω2 (t−ζm ) U (ξ(ζk , j))
+ θ2
* t
ζk
eω2 (t−s) |w(s)|2ds. (56)
In essence, the right-hand sides of (55) and (56) reflect bounds
on the Lyapunov/storage function U over (hybrid) time for the
stable and unstable modes, respectively. In order to asses the
performance of a system HT ∈ H(ν, τD , ς , T ), we require an
upper-bound that holds for all (t, j) ∈dom ξ. For this reason,
consider the following statement.
Lemma 4: For all (t, j) ∈dom ξ, it holds that
U (ξ(t, j)) Υ(0, t)U (ξ(0, 0)) + θ2
* t
0
Υ(s, t)|w(s)|2ds
(57)
with Υ(s, t) := e−ω1 |¯Θξ (s,t)| eω2 |Ξξ (s,t)| .
Proof of Lemma 4: We will prove Lemma 4 by induction.
First, we need to prove that (57) holds for all (t, j) ∈ [0, ζ0) ×
N ∩ dom ξ. To do so, observe that for all (t, j) ∈ W−1 × N ∩
dom ξ it holds that |¯Θξ(0, t)| = tand |Ξξ(0, t)| = 0. By sub-
stituting the latter in (57), we can conclude that for all (t, j) ∈
W−1 × N ∩dom ξ, the inequality given in (57) coincides with
(55). As such, (57) holds for all (t, j) ∈ W−1 × N ∩dom ξ
and thus for all (t, j) ∈ [0, ζ0) × N ∩dom ξ. Now assume (57)
holds for all (t, j) ∈ [0, ζp) × N ∩dom ξ, where p ∈ N. By
means of this hypothesis and the inequality in (56), we find that
for all (t, j) ∈ (Zp × N) ∩dom ξ,
U (ξ(t, j)) e ω2 (t−ζp ) Υ(0, ζp)U (ξ(0, 0))
+ θ2eω2 (t−ζp )
* ζp
0
Υ(s, ζp)|w(s)|2ds
+ θ2
* t
ζp
eω2 (t−s) |w(s)|2ds. (58)
Since for all t ∈ Zp and all s ∈ [0, t],|¯Θξ(s, ζp)| =
|¯Θξ(s, t)| and t − ζp + |Ξξ(s, ζp)| = |Ξξ(s, t)|, we have that
eω2 (t−ζp ) Υ(s, ζp) = Υ(s, t) for all t ∈ Zp and all s ∈ [0, t].
Substitution of the latter in (58) yields that for all (t, j) ∈
(Zp × N) ∩dom ξ,
U (ξ(t, j)) Υ(0, t)U (ξ(0, 0)) + θ2
* ζp
0
Υ(s, t)|w(s)|2ds
+ θ2
* t
ζp
eω2 (t−s) |w(s)|2ds. (59)
Note that for all t ∈ Zp and s ∈ [ζp, t], t − s = |Ξξ(s, t)|and
in accordance with (51), |¯Θξ(s, t)| = 0and thus eω2 (t−s) =
Υ(s, t) for all t ∈ Zp and s ∈ [ζp, t]. By combining the latter
with (59), we can see that (57) holds for all (t, j) ∈ ([0, ζp +
vp) × N) ∩dom ξ, p ∈ N.
Now we consider the interval Wp. Using (55), we have that
for all (t, j) ∈ (Wp × N) ∩dom ξ,
U (ξ(t, j)) e −ω1 (t−ζp −vp ) Υ(0, ζp + vp)U (ξ(0, 0))
+ θ2e−ω1 (t−ζp −vp )
* ζp +vp
0
Υ(s, ζp + vp)|w(s)|2ds
+ θ2
* t
ζp +vp
e−ω1 (t−s) |w(s)|2ds. (60)
Since t − ζp − vp + |¯Θξ(s, ζp + vp)| = |¯Θξ(s, t)| and
|Ξξ(s, ζp + vp)| = |Ξξ(s, t)|for all t ∈ Wp and all s ∈ [0, t],
we obtain
e−ω1 (t−ζp ) Υ(s, ζp) = Υ(s, t) (61)
for all t ∈ Wp and all s ∈ [0, t]. Substitution of (61) in (60)
yields that for all (t, j) ∈ (Wp × N) ∩dom ξ,
U (ξ(t, j)) Υ(0, t)U (ξ(0, 0)) + θp
* ζp
0
Υ(s, t)|w(s)|2ds
+ θp
t*
ζp
e−ω1 (t−s) |w(s)|2ds. (62)
Combining (61) with the fact that for all t ∈ Wp and s ∈
[ζp + vp, t], t − s = |¯Θξ(s, t)| and in accordance with (50),
|Ξξ(s, t)| = 0, we can see that e−ω1 (t−s) = Υ(s, t) for all
t ∈ Wp and s ∈ [ζp + vp, t]. By means of the latter, we can
conclude that (57) coincides with (62) and thus (57) holds for
all (t, j) ∈ ([0, ζp+1) × N) ∩dom ξ, which concludes the proof
of Lemma 4.
Step IV: Stability and performance analysis. In the last step
of the proof, we show that under (ν, τD , ς , T )-DoS sequences
with τD and T satisfying (31), the system HT is UGES, and
has a finite inducedL ∞ -gain. By means of (54) and the fact that
|¯Θξ(T1, T2)| = T2 − T1 − |Ξξ(T1, T2)|, we obtain that
Υ(T 1, T2) κe −β∗(T 2 −T1 ) , (63)
for all T2 ∈ R0 and all T1 ∈ k∈N Wk−1 ∪ {0}∩ [0, T2],
where κ := eς∗(ω1 +ω2 ) and where β∗ := ω1 − (ω1 + ω2)/T ∗.
Important to note is that condition (31) assures that β∗ > 0.
The inequality given in (63) does not only hold for
T1 ∈ k∈N Wk−1 ∪ {0}∩ [0, T2]. In fact, the inequality
holds for all T1, T2 ∈ R0 with T1 T 2 due to the fol-
lowing. Let 0 T 1 T 2 be arbitrary and consider T ∗
1 =
sup ˜T T 1 | ˜T ∈ k∈N Wk ∪ {0} . Since |Θ(T∗
1 , T1)| =
0, we can write Υ(T ∗
1 , T2) = Υ(T1, T2)eω2 (T 1 −T ∗
1 ) for all
T1, T2 ∈ R0 with T1 T 2. Hence, we have that Υ(T 1, T2)
Υ(T ∗
1 , T2). Due to (63) and the facts that β∗ > 0 and
T ∗
1 ∈ k∈N Wk ∪ {0}∩ [0, T2], we have thatΥ(T ∗
1 , T2)
κe−β∗(T 2 −T ∗
1 ) κe −β∗(T 2 −T1 ) . for all T1, T2 ∈ R0 with T1
T2. Hence, (63) holds for all T1, T2 ∈ R0 with T1 T 2.
1) Stability analysis for the case w = 0. By combining (57)
and (63) for the case w = 0, we find that for all (t, j) ∈
dom ξ
U (ξ(t, j)) κe −β∗t U (ξ(0, 0)).

104 IEEE TRANSACTIONS ON CONTROL OF NETWORK SYSTEMS, VOL. 4, NO. 1, MARCH 2017
Using (23), (25), (40) and the fact that η(0, 0) = 0, we
obtain
|ξ(t, j)|A
+
κ max (¯cV , ˜cW )
cU
e−(β∗/2)t |ξ(0, 0)|A ,
where ˜cW := γφm iet¯c2
W . Given the fact that due to
(31), β∗ > 0, we can conclude that HT is UGES under
(ν, τD , ς , T )-DoS sequences.
2) Performance analysis for the case w = 0in terms of in-
duced L ∞ -gain. Substitution of (63) in (57) yields
U (ξ(t, j)) κU (ξ(0, 0)) + κθ2
* t
0
e−β∗(t−s) dsw 2
L ∞ .
The facts that U (ξ(t, j)) V (x(t, j)) c z |z(t, j)|2 and
U (ξ(0, 0)) max (¯cV , ˜cW ) |ξ(0, 0)|2
A , we now obtain that for
all (t, j) ∈dom ξ
z L ∞
, κ
cz
max (¯cV , ˜cW )|ξ(0, 0)|A + θ
, κ
cz β∗w L ∞ .
Hence, (22) is satisfied with β(r) = κ
cz max (¯cV , ˜cW )r and
ϑ = θ κ
cz β∗ for p = ∞ which completes the proof.
REFERENCES
[1] V. S. Dolk, P. Tesi, C. D. Persis, and W. P. M. H. Heemels, “Output-based
event-triggered control systems under denial-of-service attacks,” in Proc.
54th IEEE Conf. Dec. Control, Dec. 2015, pp. 4824–4829.
[2] H. Sandberg, S. Amin, and K. Johansson, “Cyberphysical security in
networked control systems: An introduction to the issue,” IEEE Control
Syst. Mag., vol. 35, no. 1, pp. 20–23, Feb. 2015.
[3] F. Pasqualetti, F. Dorfler, and F. Bullo, “Attack detection and identification
in cyber-physical systems,” IEEE Trans. Autom. Control, vol. 58, no. 11,
pp. 2715–2729, Nov. 2013.
[4] W. Xu, K. Ma, W. Trappe, and Y. Zhang, “Jamming sensor networks:
Attack and defense strategies,” IEEE Netw., vol. 20, no. 3, pp. 41–47,
May 2006.
[5] C. De Persis and P. Tesi, “On resilient control of nonlinear systems under
denial-of-service,” in Proc. 53rd IEEE Conf. Dec. Control, Dec. 2014,
pp. 5254–5259.
[6] C. De Persis and P. Tesi, “Input-to-state stabilizing control under denial-
of-service,” IEEE Trans. Autom. Control, vol. 60, no. 11, pp. 2930–2944,
2015.
[7] H. S. Foroush and S. Mart´ınez, “On triggering control of single-input
linear systems under pulse-width modulated DoS jamming attacks,” SIAM
J. Control Optimiz., 2013, submitted, Revised 2016.
[8] B. DeBruhl and P. Tague, “Digital filter design for jamming mitigation
in 802.15.4 communication,” in Proc. 20th Int. Conf. Comput. Commun.
Netw., Jul. 2011, pp. 1–6.
[9] D. Borgers and W. Heemels, “Event-separation properties of event-
triggered control systems,” IEEE Trans. Autom. Control, vol. 59, no. 10,
pp. 2644–2656, Oct. 2014.
[10] M. Donkers and W. Heemels, “Output-based event-triggered control with
guaranteed L ∞ -gain and improved and decentralized event-triggering,”
IEEE Trans. Autom. Control, vol. 57, no. 6, pp. 1362–1376, Jun. 2012.
[11] J. Hespanha and A. Morse, “Stability of switched systems with aver-
age dwell-time,” in Proc. 38th IEEE Conf. Dec. Control, vol. 3, 1999,
pp. 2655–2660.
[12] V. S. Dolk, D. P. Borgers, and W. P. M. H. Heemels, “Dynamic event-
triggered control: Tradeoffs between transmission intervals and perfor-
mance,” in Proc. 53rd IEEE Conf. Dec. Control, Dec. 2014, pp. 2764–
2769.
[13] V. S. Dolk, D. P. Borgers, and W. P. M. H. Heemels, “Output-based and
decentralized dynamic event-triggered control with guaranteed L p-gain
performance and zeno-freeness,” IEEE Trans. Autom. Control, vol. 62, no.
1, pp. 34–49, Jan. 2017.
[14] D. Borgers and W. Heemels, “Stability analysis of large-scale networked
control systems with local networks: A hybrid small-gain approach,” in
Proc. Hybrid Syst.: Comput. Control, Berlin, Germany, Apr. 2014.
[15] K. ˚Astr¨om and B. Bernhardsson, “Comparison of periodic and event based
sampling for first-order stochastic systems,” vol. 11, 1999, pp. 301–306.
[16] K.-E. ˚Arz´en, “A simple event-based PID controller,” in Proc. 14th IFAC
World Congr., Beijing, China, Jan. 1999.
[17] T. Henningsson, E. Johannesson, and A. Cervin, “Sporadic event-
based control of first-order linear stochastic systems,” Automatica,
vol. 44, no. 11, pp. 2890–2895, 2008. [Online]. Available: http://www.
sciencedirect.com/science/article/pii/S0005109808002550.
[18] P. Tabuada, “Event-triggered real-time scheduling of stabilizing control
tasks,” IEEE Trans. Autom. Control, vol. 52, no. 9, pp. 1680–1685,
Sep. 2007.
[19] W. Heemels, K. Johansson, and P. Tabuada, “An introduction to event-
triggered and self-triggered control,” in Proc. 51th IEEE Conf. Dec. Con-
trol, Dec. 2012, pp. 3270–3285.
[20] A. Girard, “Dynamic triggering mechanisms for event-triggered control,”
IEEE Trans. Autom. Control, vol. 60, no. 7, pp. 1992–1997, Jul. 2015.
[21] R. Postoyan, P. Tabuada, D. Neˇsi´c, and A. Anta, “Event-triggered and
self-triggered stabilization of networked control systems,” in Proc. 50th
IEEE Conf. Dec. Control Eur. Control Conf., 2011.
[22] R. Postoyan, A. Anta, D. Ne ˇsi´c, and P. Tabuada, “A unifying Lyapunov-
based framework for the event-triggered control of nonlinear systems,” in
Proc. 50th IEEE Conf. Dec. Control Eur. Control Conf., 2011.
[23] X. Wang and M. D. Lemmon, “Event design in event-triggered feedback
control systems,” in Proc. 47th IEEE Conf. Dec. Control, Dec. 2008,
pp. 2105–2110.
[24] R. Goebel, R. Sanfelice, and A. Teel, Hybrid Dynamical Systems: Model-
ing, Stability, and Robustness. Princeton University Press, 2012.
[25] D. Carnevale, A. Teel, and D. Neˇsi´c, “A Lyapunov proof of an improved
maximum allowable transfer interval for networked control systems,”
IEEE Trans. Autom. Control, vol. 52, no. 5, pp. 892–897, May 2007.
[26] W. Heemels, A. Teel, N. van de Wouw, and D. Neˇsi´c, “Networked control
systems with communication constraints: Tradeoffs between transmis-
sion intervals, delays and performance,” IEEE Trans. Autom. Control,
pp. 1781–1796, 2010.
[27] J. Ploeg, N. van de Wouw, and H. Nijmeijer, “Lp string stability of cas-
caded systems: Application to vehicle platooning,” IEEE Trans. Control
Syst. Technol., vol. 22, no. 2, pp. 786–793, Mar. 2014.
V. S. Dolk received the M.Sc. degree (Hons.) in me-
chanical engineering from the Eindhoven University
of Technology (TU/e), Eindhoven, the Netherlands,
in 2013 where he is currently pursuing the Ph.D.
degree.
His research interests include hybrid dynamical
systems, networked control systems, intelligent trans-
port systems, and event-triggered control.
P. Tesi received the Laurea degree and the Ph.D. de-
grees in computer and control engineering from the
University of Florence, Florence, Italy, in 2005 and
2010, respectively.
He was a Visiting Scholar at the University of
California, Santa Barbara, CA, USA. Thereafter, he
held a postdoctoral position at the University of
Genoa, Genoa, Italy. He also worked in the automa-
tion industry on research and development of net-
worked supervisory control and data-acquisition sys-
tems. He is currently an Assistant Professor at the
Faculty of Mathematics and Natural Sciences, University of Groningen, the
Netherlands. Since 2014, he has been an Associate Editor of the IEEE Control
Systems Society Conference Editorial Board. His main research interests in-
clude adaptive control, hybrid systems, networked control and adaptive optics.
Using (23), (25), (40) and the fact that η(0, 0) = 0, we
obtain
|ξ(t, j)|A
+
κ max (¯cV , ˜cW )
cU
e−(β∗/2)t |ξ(0, 0)|A ,
where ˜cW := γφm iet¯c2
W . Given the fact that due to
(31), β∗ > 0, we can conclude that HT is UGES under
(ν, τD , ς , T )-DoS sequences.
2) Performance analysis for the case w = 0in terms of in-
duced L ∞ -gain. Substitution of (63) in (57) yields
U (ξ(t, j)) κU (ξ(0, 0)) + κθ2
* t
0
e−β∗(t−s) dsw 2
L ∞ .
The facts that U (ξ(t, j)) V (x(t, j)) c z |z(t, j)|2 and
U (ξ(0, 0)) max (¯cV , ˜cW ) |ξ(0, 0)|2
A , we now obtain that for
all (t, j) ∈dom ξ
z L ∞
, κ
cz
max (¯cV , ˜cW )|ξ(0, 0)|A + θ
, κ
cz β∗w L ∞ .
Hence, (22) is satisfied with β(r) = κ
cz max (¯cV , ˜cW )r and
ϑ = θ κ
cz β∗ for p = ∞ which completes the proof.
REFERENCES
[1] V. S. Dolk, P. Tesi, C. D. Persis, and W. P. M. H. Heemels, “Output-based
event-triggered control systems under denial-of-service attacks,” in Proc.
54th IEEE Conf. Dec. Control, Dec. 2015, pp. 4824–4829.
[2] H. Sandberg, S. Amin, and K. Johansson, “Cyberphysical security in
networked control systems: An introduction to the issue,” IEEE Control
Syst. Mag., vol. 35, no. 1, pp. 20–23, Feb. 2015.
[3] F. Pasqualetti, F. Dorfler, and F. Bullo, “Attack detection and identification
in cyber-physical systems,” IEEE Trans. Autom. Control, vol. 58, no. 11,
pp. 2715–2729, Nov. 2013.
[4] W. Xu, K. Ma, W. Trappe, and Y. Zhang, “Jamming sensor networks:
Attack and defense strategies,” IEEE Netw., vol. 20, no. 3, pp. 41–47,
May 2006.
[5] C. De Persis and P. Tesi, “On resilient control of nonlinear systems under
denial-of-service,” in Proc. 53rd IEEE Conf. Dec. Control, Dec. 2014,
pp. 5254–5259.
[6] C. De Persis and P. Tesi, “Input-to-state stabilizing control under denial-
of-service,” IEEE Trans. Autom. Control, vol. 60, no. 11, pp. 2930–2944,
2015.
[7] H. S. Foroush and S. Mart´ınez, “On triggering control of single-input
linear systems under pulse-width modulated DoS jamming attacks,” SIAM
J. Control Optimiz., 2013, submitted, Revised 2016.
[8] B. DeBruhl and P. Tague, “Digital filter design for jamming mitigation
in 802.15.4 communication,” in Proc. 20th Int. Conf. Comput. Commun.
Netw., Jul. 2011, pp. 1–6.
[9] D. Borgers and W. Heemels, “Event-separation properties of event-
triggered control systems,” IEEE Trans. Autom. Control, vol. 59, no. 10,
pp. 2644–2656, Oct. 2014.
[10] M. Donkers and W. Heemels, “Output-based event-triggered control with
guaranteed L ∞ -gain and improved and decentralized event-triggering,”
IEEE Trans. Autom. Control, vol. 57, no. 6, pp. 1362–1376, Jun. 2012.
[11] J. Hespanha and A. Morse, “Stability of switched systems with aver-
age dwell-time,” in Proc. 38th IEEE Conf. Dec. Control, vol. 3, 1999,
pp. 2655–2660.
[12] V. S. Dolk, D. P. Borgers, and W. P. M. H. Heemels, “Dynamic event-
triggered control: Tradeoffs between transmission intervals and perfor-
mance,” in Proc. 53rd IEEE Conf. Dec. Control, Dec. 2014, pp. 2764–
2769.
[13] V. S. Dolk, D. P. Borgers, and W. P. M. H. Heemels, “Output-based and
decentralized dynamic event-triggered control with guaranteed L p-gain
performance and zeno-freeness,” IEEE Trans. Autom. Control, vol. 62, no.
1, pp. 34–49, Jan. 2017.
[14] D. Borgers and W. Heemels, “Stability analysis of large-scale networked
control systems with local networks: A hybrid small-gain approach,” in
Proc. Hybrid Syst.: Comput. Control, Berlin, Germany, Apr. 2014.
[15] K. ˚Astr¨om and B. Bernhardsson, “Comparison of periodic and event based
sampling for first-order stochastic systems,” vol. 11, 1999, pp. 301–306.
[16] K.-E. ˚Arz´en, “A simple event-based PID controller,” in Proc. 14th IFAC
World Congr., Beijing, China, Jan. 1999.
[17] T. Henningsson, E. Johannesson, and A. Cervin, “Sporadic event-
based control of first-order linear stochastic systems,” Automatica,
vol. 44, no. 11, pp. 2890–2895, 2008. [Online]. Available: http://www.
sciencedirect.com/science/article/pii/S0005109808002550.
[18] P. Tabuada, “Event-triggered real-time scheduling of stabilizing control
tasks,” IEEE Trans. Autom. Control, vol. 52, no. 9, pp. 1680–1685,
Sep. 2007.
[19] W. Heemels, K. Johansson, and P. Tabuada, “An introduction to event-
triggered and self-triggered control,” in Proc. 51th IEEE Conf. Dec. Con-
trol, Dec. 2012, pp. 3270–3285.
[20] A. Girard, “Dynamic triggering mechanisms for event-triggered control,”
IEEE Trans. Autom. Control, vol. 60, no. 7, pp. 1992–1997, Jul. 2015.
[21] R. Postoyan, P. Tabuada, D. Neˇsi´c, and A. Anta, “Event-triggered and
self-triggered stabilization of networked control systems,” in Proc. 50th
IEEE Conf. Dec. Control Eur. Control Conf., 2011.
[22] R. Postoyan, A. Anta, D. Ne ˇsi´c, and P. Tabuada, “A unifying Lyapunov-
based framework for the event-triggered control of nonlinear systems,” in
Proc. 50th IEEE Conf. Dec. Control Eur. Control Conf., 2011.
[23] X. Wang and M. D. Lemmon, “Event design in event-triggered feedback
control systems,” in Proc. 47th IEEE Conf. Dec. Control, Dec. 2008,
pp. 2105–2110.
[24] R. Goebel, R. Sanfelice, and A. Teel, Hybrid Dynamical Systems: Model-
ing, Stability, and Robustness. Princeton University Press, 2012.
[25] D. Carnevale, A. Teel, and D. Neˇsi´c, “A Lyapunov proof of an improved
maximum allowable transfer interval for networked control systems,”
IEEE Trans. Autom. Control, vol. 52, no. 5, pp. 892–897, May 2007.
[26] W. Heemels, A. Teel, N. van de Wouw, and D. Neˇsi´c, “Networked control
systems with communication constraints: Tradeoffs between transmis-
sion intervals, delays and performance,” IEEE Trans. Autom. Control,
pp. 1781–1796, 2010.
[27] J. Ploeg, N. van de Wouw, and H. Nijmeijer, “Lp string stability of cas-
caded systems: Application to vehicle platooning,” IEEE Trans. Control
Syst. Technol., vol. 22, no. 2, pp. 786–793, Mar. 2014.
V. S. Dolk received the M.Sc. degree (Hons.) in me-
chanical engineering from the Eindhoven University
of Technology (TU/e), Eindhoven, the Netherlands,
in 2013 where he is currently pursuing the Ph.D.
degree.
His research interests include hybrid dynamical
systems, networked control systems, intelligent trans-
port systems, and event-triggered control.
P. Tesi received the Laurea degree and the Ph.D. de-
grees in computer and control engineering from the
University of Florence, Florence, Italy, in 2005 and
2010, respectively.
He was a Visiting Scholar at the University of
California, Santa Barbara, CA, USA. Thereafter, he
held a postdoctoral position at the University of
Genoa, Genoa, Italy. He also worked in the automa-
tion industry on research and development of net-
worked supervisory control and data-acquisition sys-
tems. He is currently an Assistant Professor at the
Faculty of Mathematics and Natural Sciences, University of Groningen, the
Netherlands. Since 2014, he has been an Associate Editor of the IEEE Control
Systems Society Conference Editorial Board. His main research interests in-
clude adaptive control, hybrid systems, networked control and adaptive optics.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.