Deakin University SIT284: Corporate Security Management Report
VerifiedAdded on 2022/10/11
|10
|2173
|15
Report
AI Summary
This report provides a comprehensive analysis of the LockerGoga ransomware attack on Altran Technologies, examining the threats, vulnerabilities, and exploits involved. It delves into the legal and ethical issues surrounding data breaches, analyzing the consequences of such incidents, including potential data loss, reputational damage, and financial implications. The report identifies lessons learned from the attack, emphasizing the importance of business domain knowledge and a well-planned workflow. It concludes with recommendations for strengthening security, such as implementing cryptographic algorithms and robust firewalls. The analysis covers aspects of security management, aiming to provide insights into the attack and ways to mitigate its impact.

Running head: Report On Corporate Security Management
REPORT
ON
CORPORATE SECURITY MANAGEMENT
Name of the Students
Name of the University
Author note:
REPORT
ON
CORPORATE SECURITY MANAGEMENT
Name of the Students
Name of the University
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT Security Management
Introduction:
The fundamental objective of this report is to deliver a detail analysis on the current
data breach incidents. Followed by which it will discuss the aspects of security management
in the corporate world. Considering the mentioned aspects this paper will consist a detail
elaboration related to the threats and vulnerability present in the mentioned case scenario.
Here in this report the case of LockerGoga has been taken which is a ransom ware attack.
Followed by analysing the vulnerabilities and the threats it will also consist a detail
explanation related the identification of the ethical considerations as well as the legal issues.
Since, data breach is one of the most popular topic in cyber security which holds a significant
impact on data security it is highly essential to analyse the consequences of this attack in
order to determine the impact of the selected data breach. Followed by the above aspects this
paper will also consist of a detail elaboration related to the aspects which needs to be
addressed in order to avoid the possibilities of data breach. Lastly, it will conclude by
suggesting the mitigation approaches which holds the capability to effectively mitigate the
identified limitations.
Threats, Vulnerabilities and Exploits analysis:
In this paper the scenario of the Altran Technologies has been nominated in order to
discuss about the threats, vulnerabilities as well as for exploit analysis. After a thorough
investigation it has been observed that Altran Technologies is basically a global innovation as
well as engineering consulting company which is located in France. Hence, this organization
consist of international branches. Targeting the broadness of the organizational structure the
attacker has attacked the IT network server of this company in 24th of January, 2019 which
has significantly affected the work flow in the European countries. The announcement of this
attack been made by the organizational authorities on 28th of January 2019. While the attacker
has attacked the IT network of the mentioned company the organization has forced to stop the
Introduction:
The fundamental objective of this report is to deliver a detail analysis on the current
data breach incidents. Followed by which it will discuss the aspects of security management
in the corporate world. Considering the mentioned aspects this paper will consist a detail
elaboration related to the threats and vulnerability present in the mentioned case scenario.
Here in this report the case of LockerGoga has been taken which is a ransom ware attack.
Followed by analysing the vulnerabilities and the threats it will also consist a detail
explanation related the identification of the ethical considerations as well as the legal issues.
Since, data breach is one of the most popular topic in cyber security which holds a significant
impact on data security it is highly essential to analyse the consequences of this attack in
order to determine the impact of the selected data breach. Followed by the above aspects this
paper will also consist of a detail elaboration related to the aspects which needs to be
addressed in order to avoid the possibilities of data breach. Lastly, it will conclude by
suggesting the mitigation approaches which holds the capability to effectively mitigate the
identified limitations.
Threats, Vulnerabilities and Exploits analysis:
In this paper the scenario of the Altran Technologies has been nominated in order to
discuss about the threats, vulnerabilities as well as for exploit analysis. After a thorough
investigation it has been observed that Altran Technologies is basically a global innovation as
well as engineering consulting company which is located in France. Hence, this organization
consist of international branches. Targeting the broadness of the organizational structure the
attacker has attacked the IT network server of this company in 24th of January, 2019 which
has significantly affected the work flow in the European countries. The announcement of this
attack been made by the organizational authorities on 28th of January 2019. While the attacker
has attacked the IT network of the mentioned company the organization has forced to stop the

2IT Security Management
network server in order to protect the customer data. Followed by this incident in a press
release the organisational authorities has mentioned that since, they has stopped the IT
network server the attacker failed to extract any data from the server, as they has mentioned
that after a forensic investigation there is no evidence of data loss.
Threats-
Followed by the above mentioned scenario several threats has been accounted which
are mentioned below:
One of the most significant threats present in this case is the attacker has attacked the
mentioned organizations by clicking the unknown links which, hence this is considered as
one of the significant threat to protect the organizational server to avoid clicking the unknown
links. In this case scenario it has been noticed that the attacker has the intention to spread
over the path in order to encrypt all the files of the organizations network server with the
purpose to disable the organizations authority to access their required data.
The attacker has send the IOCs:
Hash code –
The file names –
The email which is associated with it –
network server in order to protect the customer data. Followed by this incident in a press
release the organisational authorities has mentioned that since, they has stopped the IT
network server the attacker failed to extract any data from the server, as they has mentioned
that after a forensic investigation there is no evidence of data loss.
Threats-
Followed by the above mentioned scenario several threats has been accounted which
are mentioned below:
One of the most significant threats present in this case is the attacker has attacked the
mentioned organizations by clicking the unknown links which, hence this is considered as
one of the significant threat to protect the organizational server to avoid clicking the unknown
links. In this case scenario it has been noticed that the attacker has the intention to spread
over the path in order to encrypt all the files of the organizations network server with the
purpose to disable the organizations authority to access their required data.
The attacker has send the IOCs:
Hash code –
The file names –
The email which is associated with it –
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
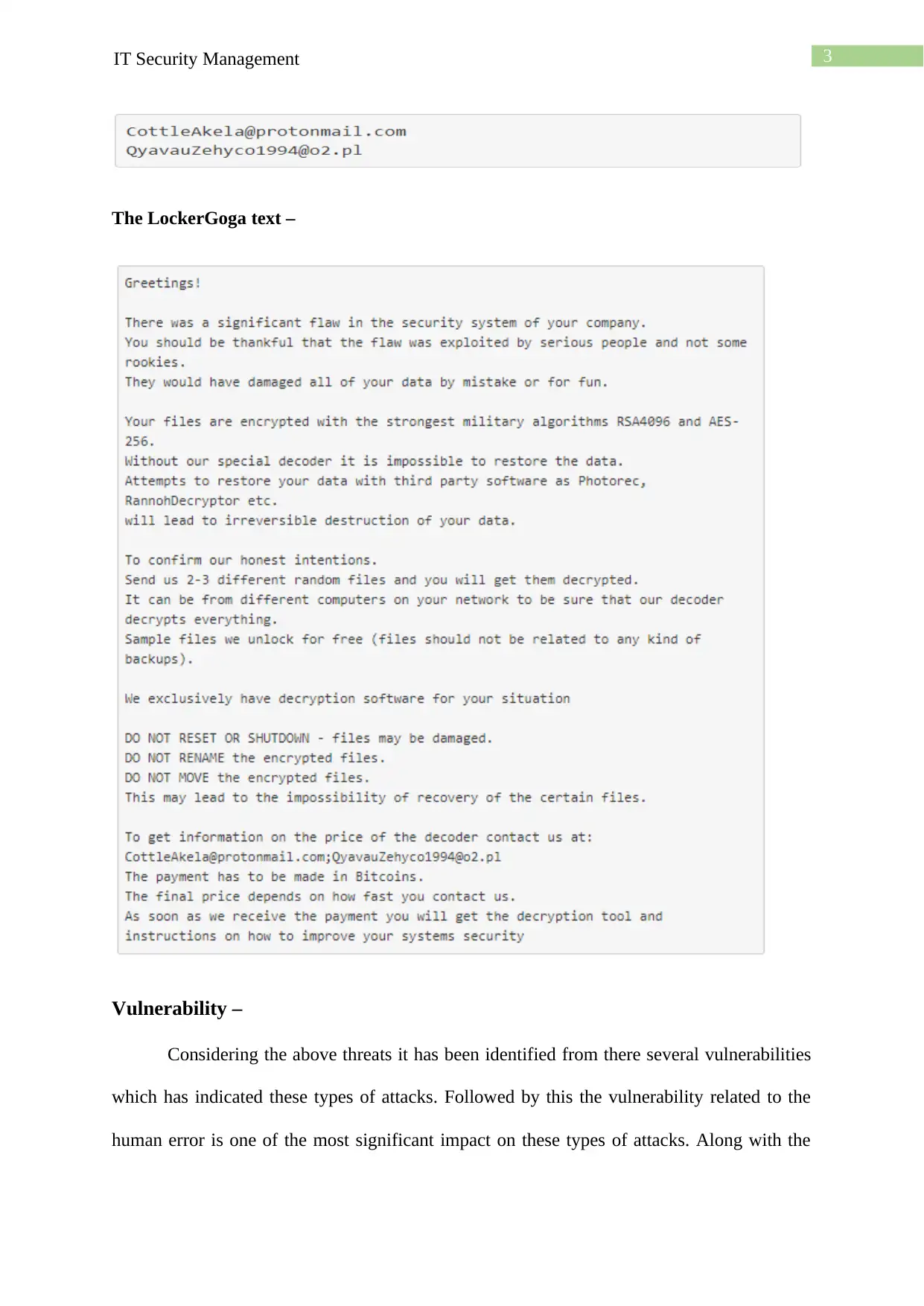
3IT Security Management
The LockerGoga text –
Vulnerability –
Considering the above threats it has been identified from there several vulnerabilities
which has indicated these types of attacks. Followed by this the vulnerability related to the
human error is one of the most significant impact on these types of attacks. Along with the
The LockerGoga text –
Vulnerability –
Considering the above threats it has been identified from there several vulnerabilities
which has indicated these types of attacks. Followed by this the vulnerability related to the
human error is one of the most significant impact on these types of attacks. Along with the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT Security Management
human errors the vulnerability related to the less effective protection to the IT servers invokes
these types of attacks.
Exploit Analysis-
Followed by eh threats present in the mentioned case scenario it has been observed
that utilizing harmful links the attacker invokes the employs of the organization to use that
link by which they can corrupt the organizational files. Along with that the hackers sends
significant numbers of requests to the server of the organization in order to corrupt the IT
network of the organization which will help them to encrypt the organization information.
Thus, after thorough investigation it can be stated that in this case the LockerGoga hacker
intended to spread their affect through the IT network of the organization.
Legal and Ethical issues analysis:
There are various kinds of the legal and also ethical issues related to the data bridge. It
is required so that no harm can occur during the use of the data bridge. When there is any
kind of the violation of any kind of issues in Data Bridge, then it can be considered as the
unethical. In the scientific research of the data bridge it is not mandatory that there is second
or third party is involved should be violated. Ethical matters must be concerned of the
authority of the company because many times they consider the obtained result or the
different kinds of the analysis tool. It is not done ethically as long as the no person except the
personnel related to that knows regarding this matter. The legal and also the ethical issues can
be extended to all the aspects of the activities of the employee. They can implement the most
popular moral standards and also the rules which are legal in nature. They can conduct the
interaction during the conduction of the research but also in the area of the commerce. It is
very important to know that the ethics are not the same. An act may be meaningful but may
be unethical or immoral in nature. There are different numbers of reasons the reason of
human errors the vulnerability related to the less effective protection to the IT servers invokes
these types of attacks.
Exploit Analysis-
Followed by eh threats present in the mentioned case scenario it has been observed
that utilizing harmful links the attacker invokes the employs of the organization to use that
link by which they can corrupt the organizational files. Along with that the hackers sends
significant numbers of requests to the server of the organization in order to corrupt the IT
network of the organization which will help them to encrypt the organization information.
Thus, after thorough investigation it can be stated that in this case the LockerGoga hacker
intended to spread their affect through the IT network of the organization.
Legal and Ethical issues analysis:
There are various kinds of the legal and also ethical issues related to the data bridge. It
is required so that no harm can occur during the use of the data bridge. When there is any
kind of the violation of any kind of issues in Data Bridge, then it can be considered as the
unethical. In the scientific research of the data bridge it is not mandatory that there is second
or third party is involved should be violated. Ethical matters must be concerned of the
authority of the company because many times they consider the obtained result or the
different kinds of the analysis tool. It is not done ethically as long as the no person except the
personnel related to that knows regarding this matter. The legal and also the ethical issues can
be extended to all the aspects of the activities of the employee. They can implement the most
popular moral standards and also the rules which are legal in nature. They can conduct the
interaction during the conduction of the research but also in the area of the commerce. It is
very important to know that the ethics are not the same. An act may be meaningful but may
be unethical or immoral in nature. There are different numbers of reasons the reason of

5IT Security Management
implementing these ethics in Data Bridge. Protection of the fabrication of the data bridge is
the support of the knowledge, truth and avoidance of the errors. The data bridge research
involves in the co-operation and co-ordination among the many other researchers. Many
standards in the research includes the copyright, policies related to the patenting, policies
related to the sharing of the data, and also the rules related to the confidential manner. Some
ethical helps for guarantees that the data bridge researchers can be very responsible to
become the public. Some federal policies of the data bridge is misconducted. It also
differentiates for the interest. The protections of the data bridge and also the necessary for
making the researchers that can funded by the public money. The different of the research
also helps for building the different kinds of the community support. Many of the standards
related to the ethics for promoting the data bridge a variety of the other moral issues. A
researcher of the data bridge can significantly affect the total society and also the matters.
Consequences of the data breach analysis:
Followed by the above case study it has been noticed that however the organization
has saved themselves from losing their data there is also a significant impact of these types of
data breach towards the organizational services. After a thorough investigation on this topic
has provided the knowledge that due to lockerGoga attack there was a high possibilities for
the organization to lose their data as the hacker has already started to spread the attack. Thus,
it can be stated that one of the major consequences of these sort of data breach may led to the
data loss for the organization. Along with that it holds significant impact towards the
reputation of the organization to its customers as due to these types of attacks the
organization will lose the information of the customers due to which the customer can get
into a huge trouble. Along with that there is also a significant impact towards the association
of the employs with the mentioned organization as due to these attacks the organization will
lost its employ data which may affect their association. Along with the consequences related
implementing these ethics in Data Bridge. Protection of the fabrication of the data bridge is
the support of the knowledge, truth and avoidance of the errors. The data bridge research
involves in the co-operation and co-ordination among the many other researchers. Many
standards in the research includes the copyright, policies related to the patenting, policies
related to the sharing of the data, and also the rules related to the confidential manner. Some
ethical helps for guarantees that the data bridge researchers can be very responsible to
become the public. Some federal policies of the data bridge is misconducted. It also
differentiates for the interest. The protections of the data bridge and also the necessary for
making the researchers that can funded by the public money. The different of the research
also helps for building the different kinds of the community support. Many of the standards
related to the ethics for promoting the data bridge a variety of the other moral issues. A
researcher of the data bridge can significantly affect the total society and also the matters.
Consequences of the data breach analysis:
Followed by the above case study it has been noticed that however the organization
has saved themselves from losing their data there is also a significant impact of these types of
data breach towards the organizational services. After a thorough investigation on this topic
has provided the knowledge that due to lockerGoga attack there was a high possibilities for
the organization to lose their data as the hacker has already started to spread the attack. Thus,
it can be stated that one of the major consequences of these sort of data breach may led to the
data loss for the organization. Along with that it holds significant impact towards the
reputation of the organization to its customers as due to these types of attacks the
organization will lose the information of the customers due to which the customer can get
into a huge trouble. Along with that there is also a significant impact towards the association
of the employs with the mentioned organization as due to these attacks the organization will
lost its employ data which may affect their association. Along with the consequences related
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT Security Management
to the data loss, there is a significant risk present related to the network server corruption. As
it has been observed from the mentioned case study that there the attacker has initially
attacked the IT server of the organization followed by which the organization may lose their
server permanently. Thus, it can be stated that due to the LockerGoga attack the
organizational services can be disrupted which holds the significant impact on the
organizational profit. Along with the mentioned risk it has been also mentioned that the
organization may have huge data loss as the data related to the financial data by which the
hacker can extract the have all the access related all the money transactions due to which
there is a significant possibilities of the money loss. Followed by the above mentioned risk
there is a huge possibilities of the risk related to the intellectual property as due to these
attacks the intellectual properties can get into a high risk. Apart from the above risk there is a
significant impact related to the reputation of the organization as if there is any chance of
getting hacked by the hacker the customers as well as the employs of the organization will
have a bad impression towards the organization.
Thus, after the above analysis it can be stated that while considering the aspects of
these types of attacks there is a huge risk related to the organizational damage. However, the
mentioned organization has effectively protected themselves from the attack by forcefully
stopping the IT network server which has disconnected the effect of the mentioned attack.
to the data loss, there is a significant risk present related to the network server corruption. As
it has been observed from the mentioned case study that there the attacker has initially
attacked the IT server of the organization followed by which the organization may lose their
server permanently. Thus, it can be stated that due to the LockerGoga attack the
organizational services can be disrupted which holds the significant impact on the
organizational profit. Along with the mentioned risk it has been also mentioned that the
organization may have huge data loss as the data related to the financial data by which the
hacker can extract the have all the access related all the money transactions due to which
there is a significant possibilities of the money loss. Followed by the above mentioned risk
there is a huge possibilities of the risk related to the intellectual property as due to these
attacks the intellectual properties can get into a high risk. Apart from the above risk there is a
significant impact related to the reputation of the organization as if there is any chance of
getting hacked by the hacker the customers as well as the employs of the organization will
have a bad impression towards the organization.
Thus, after the above analysis it can be stated that while considering the aspects of
these types of attacks there is a huge risk related to the organizational damage. However, the
mentioned organization has effectively protected themselves from the attack by forcefully
stopping the IT network server which has disconnected the effect of the mentioned attack.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT Security Management
Lessons Learned:
In the data bridge and also the attacks occurred in the company learns that the
business domain knowledge is very important. The company should not spent
too many times to improve the technical knowledge. Without knowing the
business properly the probability of the model that could integrate the
company as it can serve the purpose. Most common model is to improve this
kind of the accuracy is to the implementation of the grid search.
The employees should have to understand the workflow of the organization
that is focuses on the details of the work. Data in the real life is very
complicated and it has the very intelligent mind-set for the successful
implementation of the data bridge and also the data science. The company can
perform the exploratory of the data analysis for some time but it may reach to
the any of the insights. The company can provide the continuous training to
the different kinds of the data bridge for the improvement of the data bridge.
The company can perform the arduous data cleaning process. The data could
be in the fact that cannot be clean enough for fedding the different kinds of the
model. The company can only understand that they did not have the good
work flow and also the employees are praying for the best.
Lessons Learned:
In the data bridge and also the attacks occurred in the company learns that the
business domain knowledge is very important. The company should not spent
too many times to improve the technical knowledge. Without knowing the
business properly the probability of the model that could integrate the
company as it can serve the purpose. Most common model is to improve this
kind of the accuracy is to the implementation of the grid search.
The employees should have to understand the workflow of the organization
that is focuses on the details of the work. Data in the real life is very
complicated and it has the very intelligent mind-set for the successful
implementation of the data bridge and also the data science. The company can
perform the exploratory of the data analysis for some time but it may reach to
the any of the insights. The company can provide the continuous training to
the different kinds of the data bridge for the improvement of the data bridge.
The company can perform the arduous data cleaning process. The data could
be in the fact that cannot be clean enough for fedding the different kinds of the
model. The company can only understand that they did not have the good
work flow and also the employees are praying for the best.

8IT Security Management
A well planned work flow gives the view of the company with the entire the
prototyping system of the data bridge. This kind of the experiment is the entire
part of the workflow that can add the logic of the testing of the hypothesis of
the software and also the process of the building of the model. General
problems related to the problems related to the data bridge for getting the
training of the data bridge applications and also starts building the models.
The models can be very much complicated in the real life problems in terms of
the frames that can implement the logics and also development for testing of
the assumption.
Recommendation:
The company should protect the data by implementing the cryptographic
algorithms for protecting the data.
The company should implement a strong firewall so that they can protect their data
as well as the data bridge.
A well planned work flow gives the view of the company with the entire the
prototyping system of the data bridge. This kind of the experiment is the entire
part of the workflow that can add the logic of the testing of the hypothesis of
the software and also the process of the building of the model. General
problems related to the problems related to the data bridge for getting the
training of the data bridge applications and also starts building the models.
The models can be very much complicated in the real life problems in terms of
the frames that can implement the logics and also development for testing of
the assumption.
Recommendation:
The company should protect the data by implementing the cryptographic
algorithms for protecting the data.
The company should implement a strong firewall so that they can protect their data
as well as the data bridge.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT Security Management
Bibliography:
Cyware. (2019). Altran Technologies hit by LockerGoga ransomware attack | Cyware
Hacker News. [online] Available at: https://cyware.com/news/altran-technologies-hit-by-
lockergoga-ransomware-attack-e1f90570 [Accessed 4 Aug. 2019].
Herbert, S., 2019. Why IIoT should make businesses rethink security. Network
Security, 2019(7), pp.9-11.
Janakiraman, R., Lim, J.H. and Rishika, R., 2018. The effect of a data breach announcement
on customer behavior: Evidence from a multichannel retailer. Journal of Marketing, 82(2),
pp.85-105.
SECHEL, S., 2019. A Comparative Assessment of Obfuscated Ransomware Detection
Methods. Informatica Economica, 23(2).
Bibliography:
Cyware. (2019). Altran Technologies hit by LockerGoga ransomware attack | Cyware
Hacker News. [online] Available at: https://cyware.com/news/altran-technologies-hit-by-
lockergoga-ransomware-attack-e1f90570 [Accessed 4 Aug. 2019].
Herbert, S., 2019. Why IIoT should make businesses rethink security. Network
Security, 2019(7), pp.9-11.
Janakiraman, R., Lim, J.H. and Rishika, R., 2018. The effect of a data breach announcement
on customer behavior: Evidence from a multichannel retailer. Journal of Marketing, 82(2),
pp.85-105.
SECHEL, S., 2019. A Comparative Assessment of Obfuscated Ransomware Detection
Methods. Informatica Economica, 23(2).
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





