University of West London: Ethics Application - COVID-19 & SMEs
VerifiedAdded on 2022/12/30
|11
|1873
|33
Homework Assignment
AI Summary
This document presents a student's ethics application for a research project investigating the impact of COVID-19 on small and medium-sized enterprises (SMEs) in the United Kingdom. The application includes a detailed project description, outlining the research questions, aims, and methodology, which is based on secondary data collection from published sources. The student addresses ethical considerations, including data privacy, confidentiality, and informed consent, as well as data management and storage. The application covers aspects of informed consent, confidentiality, and data security, including the use of anonymized data, secure password-protected computer files, and the destruction of sensitive materials after a specified period. The student confirms adherence to the Data Protection Act 1998 and outlines plans for data storage and disposal. The project aims to determine the positive immediate responses for SMEs to recover from COVID-19 in the UK, to identify major challenges faced by SMEs in the UK during COVID-19, and to analyze threats and risks posed by the market external environment. The student acknowledges the need for ethical approval and has received guidance on ethical research practices. The document also includes the student's name, student number, email address, project title, supervisor's name, and date of submission.

Secondary Data collection Only
You are required to complete an ethics application BEFORE
you
embark on the data collection exercise of the research project
Please complete all the following sections:
- Section A: Ethics Form
- Section B: Data management and storage form
You are required to complete an ethics application BEFORE
you
embark on the data collection exercise of the research project
Please complete all the following sections:
- Section A: Ethics Form
- Section B: Data management and storage form
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESEARCH ETHICS AND INTEGRITY
RISK ASSESSMENT FORM
Section A: FORM A
For all Undergraduate/Postgraduate Dissertations and Research
Projects
Please fill in this form, then SAVE IT AS A PDF and submit as instructed by your supervisor
with your project proposal
Your name: (first) ……………………… (last) ………………………
Student number: …………… Your email address: …………
PROJECT DESCRIPTON
Please answer the following questions:
1. Do you intend to involve human participants in the conduct of your research?
If no, please skip questions 2 & 3.
☐ Yes ☐No
2. Does your research involve vulnerable adults or under-18s?
☐ Yes ☐No
3. Could your research potentially expose you, anyone assisting you, or
participants to emotional harm?
☐ Yes ☐No
4. Will your research involve travelling to geo-politically unstable regions/countries
(e.g. areas affected by war, civil unrest, natural disasters, or listed as
unadvisable to travel by the UK government?
☐ Yes ☐No
5. Will your research involve access to security-sensitive material? If yes, you must
include a data management statement.
☐ Yes ☐No
RISK ASSESSMENT FORM
Section A: FORM A
For all Undergraduate/Postgraduate Dissertations and Research
Projects
Please fill in this form, then SAVE IT AS A PDF and submit as instructed by your supervisor
with your project proposal
Your name: (first) ……………………… (last) ………………………
Student number: …………… Your email address: …………
PROJECT DESCRIPTON
Please answer the following questions:
1. Do you intend to involve human participants in the conduct of your research?
If no, please skip questions 2 & 3.
☐ Yes ☐No
2. Does your research involve vulnerable adults or under-18s?
☐ Yes ☐No
3. Could your research potentially expose you, anyone assisting you, or
participants to emotional harm?
☐ Yes ☐No
4. Will your research involve travelling to geo-politically unstable regions/countries
(e.g. areas affected by war, civil unrest, natural disasters, or listed as
unadvisable to travel by the UK government?
☐ Yes ☐No
5. Will your research involve access to security-sensitive material? If yes, you must
include a data management statement.
☐ Yes ☐No

This proposal must be completed with the assistance of your supervisor. You
can change the size of the boxes (below) by typing or deleting as necessary.
It is very important to convey with clarity:
• Your research questions/the problem/the theme or topic you are investigating
(what you are proposing to do and to find out or to create)
• The methodology or technical approach (for projects comprising in whole or in
part the creation of an artefact) you will adopt – methods, number of
participants, who the participants (if any) will be, survey instruments used
technology and equipment employed etc.; and what questions you are
planning to ask your respondents (if applicable); how you will deal with
technical challenges.
3 | P a g e
can change the size of the boxes (below) by typing or deleting as necessary.
It is very important to convey with clarity:
• Your research questions/the problem/the theme or topic you are investigating
(what you are proposing to do and to find out or to create)
• The methodology or technical approach (for projects comprising in whole or in
part the creation of an artefact) you will adopt – methods, number of
participants, who the participants (if any) will be, survey instruments used
technology and equipment employed etc.; and what questions you are
planning to ask your respondents (if applicable); how you will deal with
technical challenges.
3 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
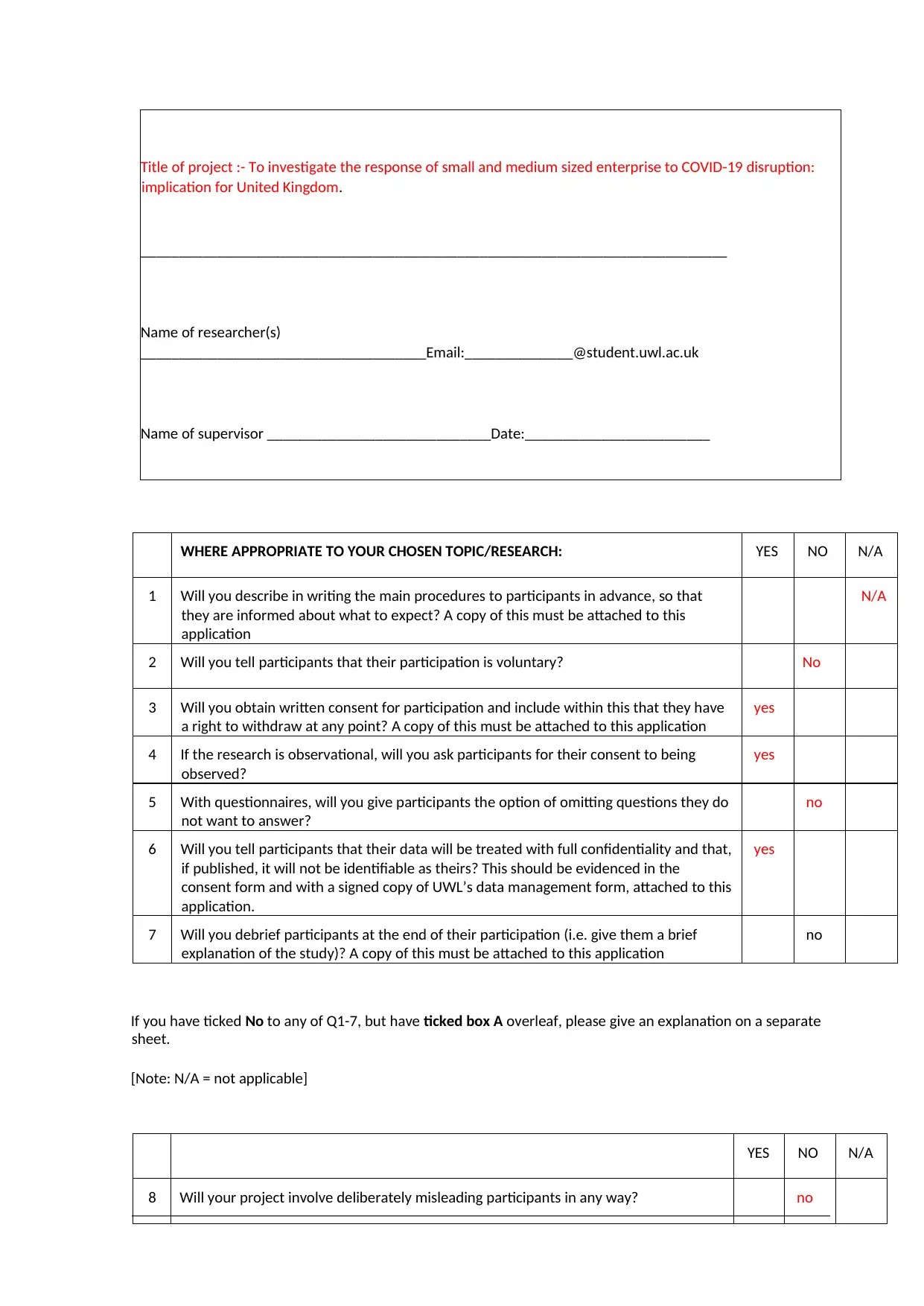
Title of project :- To investigate the response of small and medium sized enterprise to COVID-19 disruption:
implication for United Kingdom.
____________________________________________________________________________
Name of researcher(s)
_____________________________________Email:______________@student.uwl.ac.uk
Name of supervisor _____________________________Date:________________________
WHERE APPROPRIATE TO YOUR CHOSEN TOPIC/RESEARCH: YES NO N/A
1 Will you describe in writing the main procedures to participants in advance, so that
they are informed about what to expect? A copy of this must be attached to this
application
N/A
2 Will you tell participants that their participation is voluntary? No
3 Will you obtain written consent for participation and include within this that they have
a right to withdraw at any point? A copy of this must be attached to this application
yes
4 If the research is observational, will you ask participants for their consent to being
observed?
yes
5 With questionnaires, will you give participants the option of omitting questions they do
not want to answer?
no
6 Will you tell participants that their data will be treated with full confidentiality and that,
if published, it will not be identifiable as theirs? This should be evidenced in the
consent form and with a signed copy of UWL’s data management form, attached to this
application.
yes
7 Will you debrief participants at the end of their participation (i.e. give them a brief
explanation of the study)? A copy of this must be attached to this application
no
If you have ticked No to any of Q1-7, but have ticked box A overleaf, please give an explanation on a separate
sheet.
[Note: N/A = not applicable]
YES NO N/A
8 Will your project involve deliberately misleading participants in any way? no
implication for United Kingdom.
____________________________________________________________________________
Name of researcher(s)
_____________________________________Email:______________@student.uwl.ac.uk
Name of supervisor _____________________________Date:________________________
WHERE APPROPRIATE TO YOUR CHOSEN TOPIC/RESEARCH: YES NO N/A
1 Will you describe in writing the main procedures to participants in advance, so that
they are informed about what to expect? A copy of this must be attached to this
application
N/A
2 Will you tell participants that their participation is voluntary? No
3 Will you obtain written consent for participation and include within this that they have
a right to withdraw at any point? A copy of this must be attached to this application
yes
4 If the research is observational, will you ask participants for their consent to being
observed?
yes
5 With questionnaires, will you give participants the option of omitting questions they do
not want to answer?
no
6 Will you tell participants that their data will be treated with full confidentiality and that,
if published, it will not be identifiable as theirs? This should be evidenced in the
consent form and with a signed copy of UWL’s data management form, attached to this
application.
yes
7 Will you debrief participants at the end of their participation (i.e. give them a brief
explanation of the study)? A copy of this must be attached to this application
no
If you have ticked No to any of Q1-7, but have ticked box A overleaf, please give an explanation on a separate
sheet.
[Note: N/A = not applicable]
YES NO N/A
8 Will your project involve deliberately misleading participants in any way? no
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
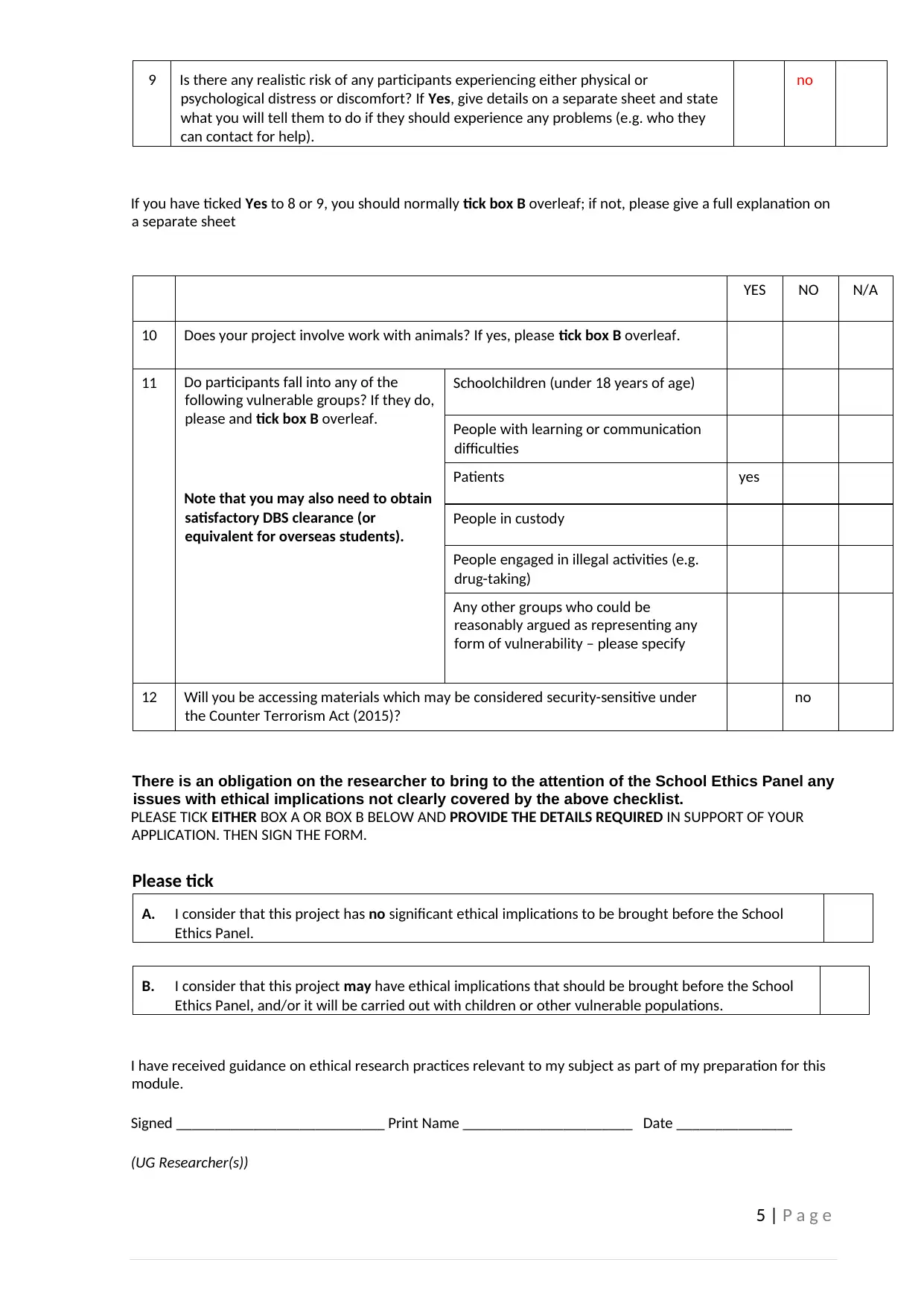
9 Is there any realistic risk of any participants experiencing either physical or
psychological distress or discomfort? If Yes, give details on a separate sheet and state
what you will tell them to do if they should experience any problems (e.g. who they
can contact for help).
no
If you have ticked Yes to 8 or 9, you should normally tick box B overleaf; if not, please give a full explanation on
a separate sheet
YES NO N/A
10 Does your project involve work with animals? If yes, please tick box B overleaf.
11 Do participants fall into any of the
following vulnerable groups? If they do,
please and tick box B overleaf.
Note that you may also need to obtain
satisfactory DBS clearance (or
equivalent for overseas students).
Schoolchildren (under 18 years of age)
People with learning or communication
difficulties
Patients yes
People in custody
People engaged in illegal activities (e.g.
drug-taking)
Any other groups who could be
reasonably argued as representing any
form of vulnerability – please specify
12 Will you be accessing materials which may be considered security-sensitive under
the Counter Terrorism Act (2015)?
no
There is an obligation on the researcher to bring to the attention of the School Ethics Panel any
issues with ethical implications not clearly covered by the above checklist.
PLEASE TICK EITHER BOX A OR BOX B BELOW AND PROVIDE THE DETAILS REQUIRED IN SUPPORT OF YOUR
APPLICATION. THEN SIGN THE FORM.
Please tick
A. I consider that this project has no significant ethical implications to be brought before the School
Ethics Panel.
B. I consider that this project may have ethical implications that should be brought before the School
Ethics Panel, and/or it will be carried out with children or other vulnerable populations.
I have received guidance on ethical research practices relevant to my subject as part of my preparation for this
module.
Signed ___________________________ Print Name ______________________ Date _______________
(UG Researcher(s))
5 | P a g e
psychological distress or discomfort? If Yes, give details on a separate sheet and state
what you will tell them to do if they should experience any problems (e.g. who they
can contact for help).
no
If you have ticked Yes to 8 or 9, you should normally tick box B overleaf; if not, please give a full explanation on
a separate sheet
YES NO N/A
10 Does your project involve work with animals? If yes, please tick box B overleaf.
11 Do participants fall into any of the
following vulnerable groups? If they do,
please and tick box B overleaf.
Note that you may also need to obtain
satisfactory DBS clearance (or
equivalent for overseas students).
Schoolchildren (under 18 years of age)
People with learning or communication
difficulties
Patients yes
People in custody
People engaged in illegal activities (e.g.
drug-taking)
Any other groups who could be
reasonably argued as representing any
form of vulnerability – please specify
12 Will you be accessing materials which may be considered security-sensitive under
the Counter Terrorism Act (2015)?
no
There is an obligation on the researcher to bring to the attention of the School Ethics Panel any
issues with ethical implications not clearly covered by the above checklist.
PLEASE TICK EITHER BOX A OR BOX B BELOW AND PROVIDE THE DETAILS REQUIRED IN SUPPORT OF YOUR
APPLICATION. THEN SIGN THE FORM.
Please tick
A. I consider that this project has no significant ethical implications to be brought before the School
Ethics Panel.
B. I consider that this project may have ethical implications that should be brought before the School
Ethics Panel, and/or it will be carried out with children or other vulnerable populations.
I have received guidance on ethical research practices relevant to my subject as part of my preparation for this
module.
Signed ___________________________ Print Name ______________________ Date _______________
(UG Researcher(s))
5 | P a g e

Signed ___________________________ Print Name ______________________ Date _______________
(Supervisor)
(Supervisor)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

PART 2
SPECIFICATIONS OF PROJECT
Please answer the following question:
1. Do you intend to use only secondary data in the conduct of your research?
☐ Yes ☐No
Introduction to the research
Background to research topic area (with references where applicable). 200 words approx.
Include Aims and Hypothesis, Research Question(s) of the
dissertation/project.
Aim- To investigate the response of small and medium sized enterprises to COVID-19
disruption: implications for United Kingdom (UK).
Objective-
To determine the positive immediate responses for SMEs in order to recover from
COVID-19 in UK.
To identify the major challenges face by SMEs in UK during COVID-19
To analyze threats, risks which posed by market external environment.
Research Questions-
What are positive immediate responses for SMEs in order to recover from COVID-19 in
UK?
What are different major challenges face by SMEs in UK during COVID-19?
How can analyse the threats, risks which posed by market external environment?
Method
Outline all methodological issues - e.g. Design, participants, questionnaires, tests,
method
of data collection. Who are you working with? How? What Measures? What
interventions/manipulations? What controls? If your research entails exclusively the
consultation of published documents, books, articles or other work in the public domain
please state this under the heading
‘materials’.
It can be explained type of study that are
conducted by scholar in order to complete the
research. It is divided into two segments
namely quantitative and qualitative.
Qualitative research has been taken by
Research
design
Qualitative research
7 | P a g e
SPECIFICATIONS OF PROJECT
Please answer the following question:
1. Do you intend to use only secondary data in the conduct of your research?
☐ Yes ☐No
Introduction to the research
Background to research topic area (with references where applicable). 200 words approx.
Include Aims and Hypothesis, Research Question(s) of the
dissertation/project.
Aim- To investigate the response of small and medium sized enterprises to COVID-19
disruption: implications for United Kingdom (UK).
Objective-
To determine the positive immediate responses for SMEs in order to recover from
COVID-19 in UK.
To identify the major challenges face by SMEs in UK during COVID-19
To analyze threats, risks which posed by market external environment.
Research Questions-
What are positive immediate responses for SMEs in order to recover from COVID-19 in
UK?
What are different major challenges face by SMEs in UK during COVID-19?
How can analyse the threats, risks which posed by market external environment?
Method
Outline all methodological issues - e.g. Design, participants, questionnaires, tests,
method
of data collection. Who are you working with? How? What Measures? What
interventions/manipulations? What controls? If your research entails exclusively the
consultation of published documents, books, articles or other work in the public domain
please state this under the heading
‘materials’.
It can be explained type of study that are
conducted by scholar in order to complete the
research. It is divided into two segments
namely quantitative and qualitative.
Qualitative research has been taken by
Research
design
Qualitative research
7 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

researcher in order to understand impact of
COVID-19 on Small sectors and again it is
specified which again supported by research
type taken.
Participants (where
applicable)
no
Materials (to include locations and
resources)
Articles, books and journals
Analysis
CLEARLY describe the method of analysis you are going to use. Is it qualitative
or
quantitative
?
Secondary data is taken from publish sources such as Books, journals etc. and hence decrease
time of searching as well as cost of person who is researching. Scholar has taken secondary data
for the study as after pandemic most of the colleges focuses on it and COVID restriction again
create challenges. It also decreases cost as well as time of participant
COVID-19 on Small sectors and again it is
specified which again supported by research
type taken.
Participants (where
applicable)
no
Materials (to include locations and
resources)
Articles, books and journals
Analysis
CLEARLY describe the method of analysis you are going to use. Is it qualitative
or
quantitative
?
Secondary data is taken from publish sources such as Books, journals etc. and hence decrease
time of searching as well as cost of person who is researching. Scholar has taken secondary data
for the study as after pandemic most of the colleges focuses on it and COVID restriction again
create challenges. It also decreases cost as well as time of participant

Section B: RESEARCH ETHICS AND INTEGRITY
DATA MANAGEMENT AND STORAGE STATEMENT
All applicants should familiarise themselves with the Data Protection Act 1998, and adhere
to its principles in all aspects of their research:
Applicable as data protect act 1998, Collection of digital objects acquired and generated
during the process of research
Research data covers a broad range of types of information (see examples below), and
digital data can be structured and stored in a variety of file formats.
EXAMPLES OF RESEARCH DATA
Some examples of research data:
Documents (text, Word), spreadsheets
Laboratory notebooks, field notebooks, diaries
Questionnaires, -transcripts, codebooks
Audiotapes, videotapes
Photographs, films
Test responses
Slides, artefacts, specimens, samples
Collection of digital objects acquired and generated during the process of research
Database contents (video, audio, text, images)
9 | P a g e
DATA MANAGEMENT AND STORAGE STATEMENT
All applicants should familiarise themselves with the Data Protection Act 1998, and adhere
to its principles in all aspects of their research:
Applicable as data protect act 1998, Collection of digital objects acquired and generated
during the process of research
Research data covers a broad range of types of information (see examples below), and
digital data can be structured and stored in a variety of file formats.
EXAMPLES OF RESEARCH DATA
Some examples of research data:
Documents (text, Word), spreadsheets
Laboratory notebooks, field notebooks, diaries
Questionnaires, -transcripts, codebooks
Audiotapes, videotapes
Photographs, films
Test responses
Slides, artefacts, specimens, samples
Collection of digital objects acquired and generated during the process of research
Database contents (video, audio, text, images)
9 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Models, algorithms, scripts
Contents of an application (input, output, logfiles for analysis software, simulation software,
schemas)
Methodologies and workflows
Standard operating procedures and protocols
As a student or member of staff undertaking a research project, I understand that I am
responsible for the following:
• The security and confidentiality of all data collected
• Mitigating all risks to anonymity, privacy and confidentiality posed by all kinds of
personal information storage, processing, including computer and paper files, e-mail
records, audio and video files, and any information that directly identifies an
individual. It is recommended that data be anonymised at the point of collection.
I will ensure that:
• Data and codes and all identifying information will be kept in separate locked filing
cabinets/files and working files will contain no identifying information, and will only
be accessed by one or two persons
• All audiotapes will be transcribed using codes or pseudonyms for identification of
individuals and destroyed upon completion of the research project
• Access to computer files will be available by password only
• Research data will be stored for up to 5 years after the end of the project, after
which they should be disposed of safely.
Name:
Application ID:
Project title:
Contents of an application (input, output, logfiles for analysis software, simulation software,
schemas)
Methodologies and workflows
Standard operating procedures and protocols
As a student or member of staff undertaking a research project, I understand that I am
responsible for the following:
• The security and confidentiality of all data collected
• Mitigating all risks to anonymity, privacy and confidentiality posed by all kinds of
personal information storage, processing, including computer and paper files, e-mail
records, audio and video files, and any information that directly identifies an
individual. It is recommended that data be anonymised at the point of collection.
I will ensure that:
• Data and codes and all identifying information will be kept in separate locked filing
cabinets/files and working files will contain no identifying information, and will only
be accessed by one or two persons
• All audiotapes will be transcribed using codes or pseudonyms for identification of
individuals and destroyed upon completion of the research project
• Access to computer files will be available by password only
• Research data will be stored for up to 5 years after the end of the project, after
which they should be disposed of safely.
Name:
Application ID:
Project title:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11 | P a g e
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





