CPIS 606 Assignment 4 (B): IT Asset Inventory, Router Audit, and CIA
VerifiedAdded on 2022/09/21
|7
|712
|26
Homework Assignment
AI Summary
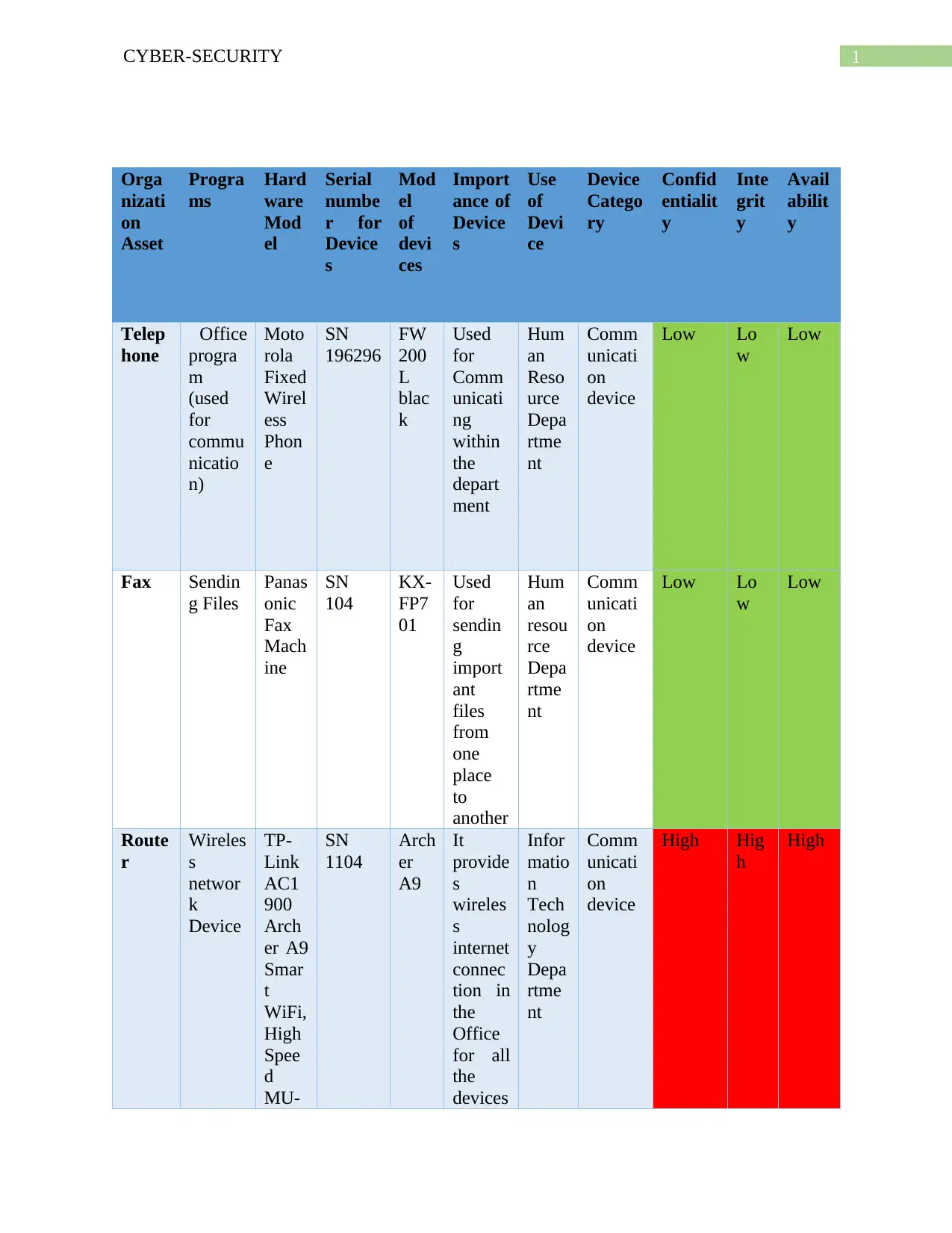
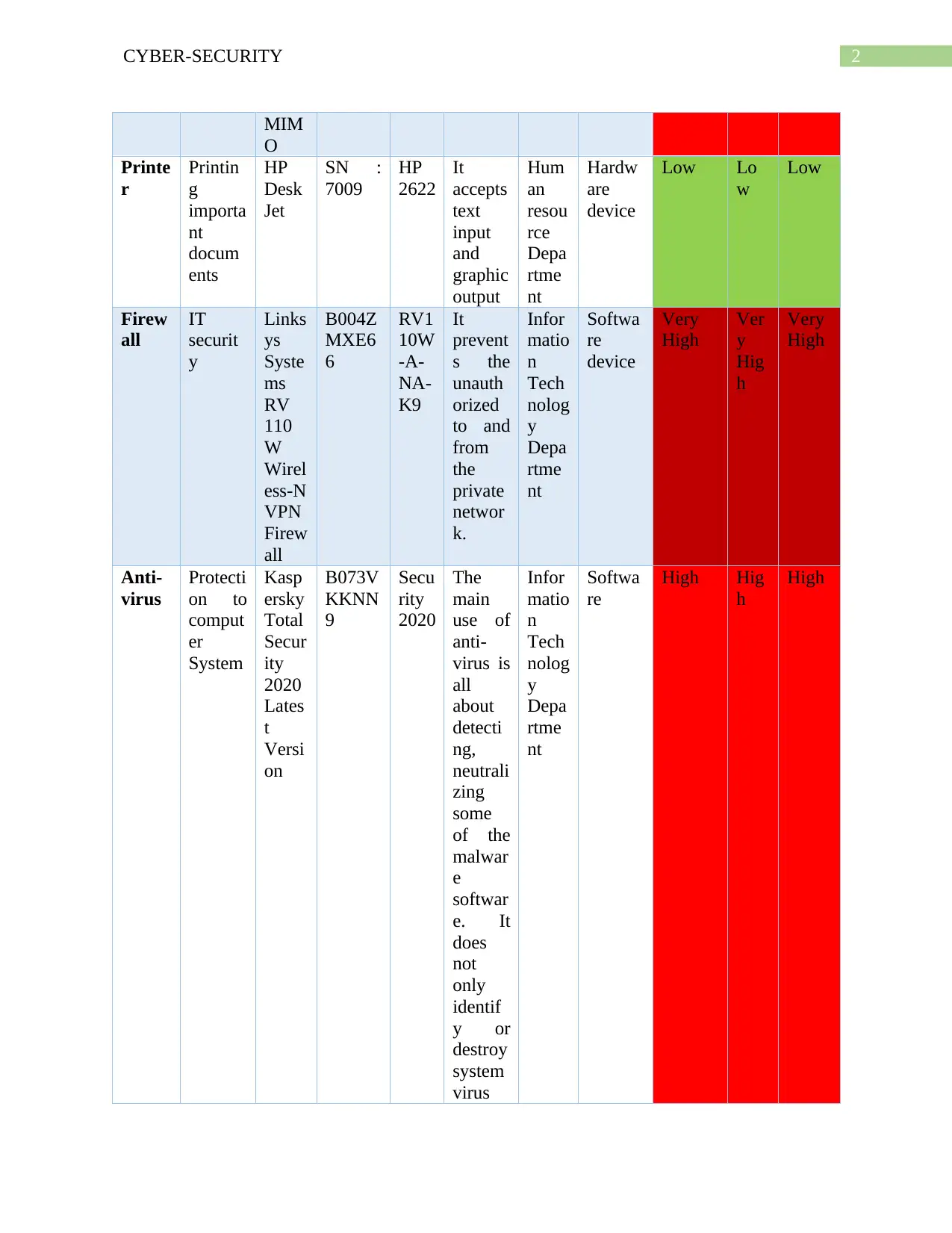
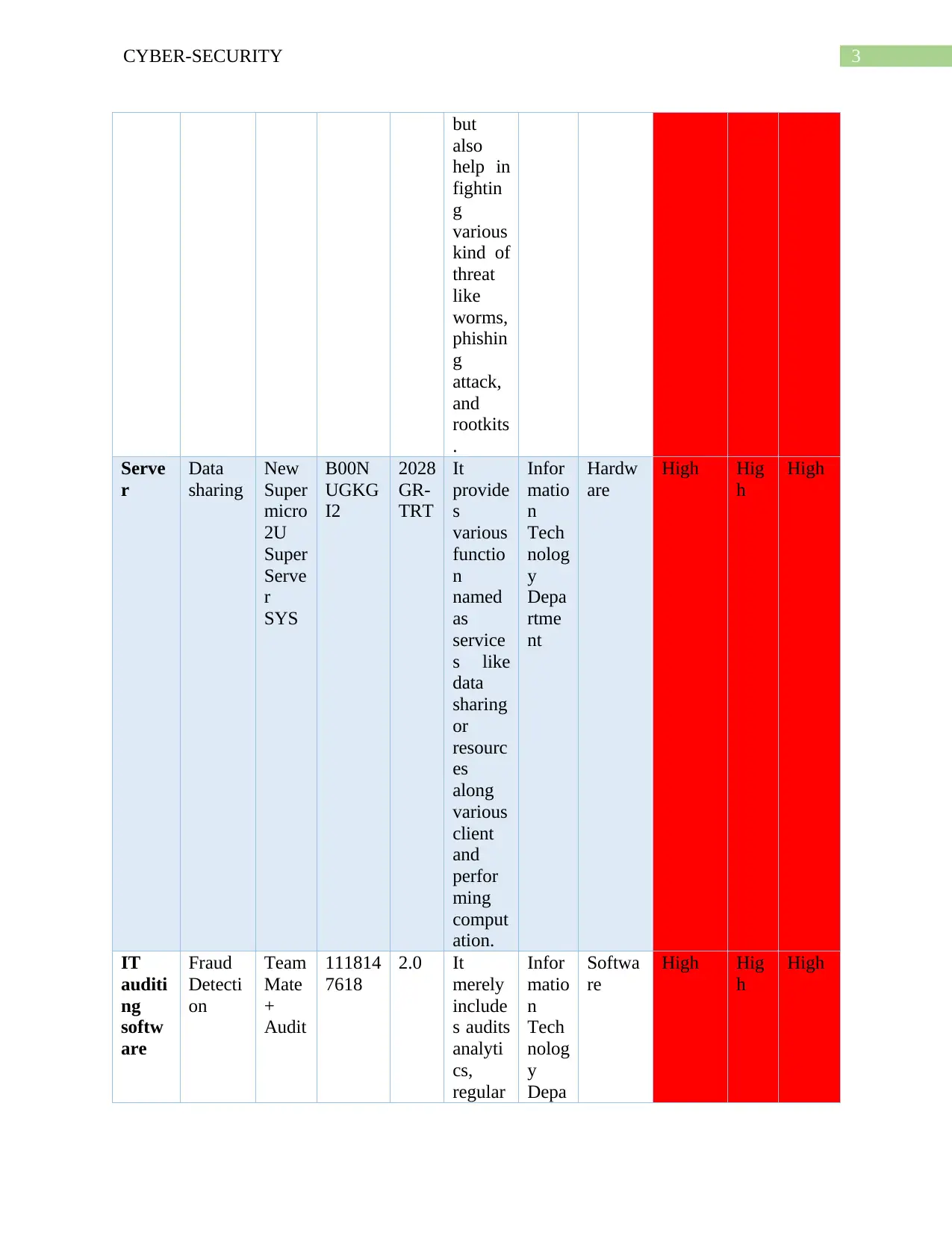
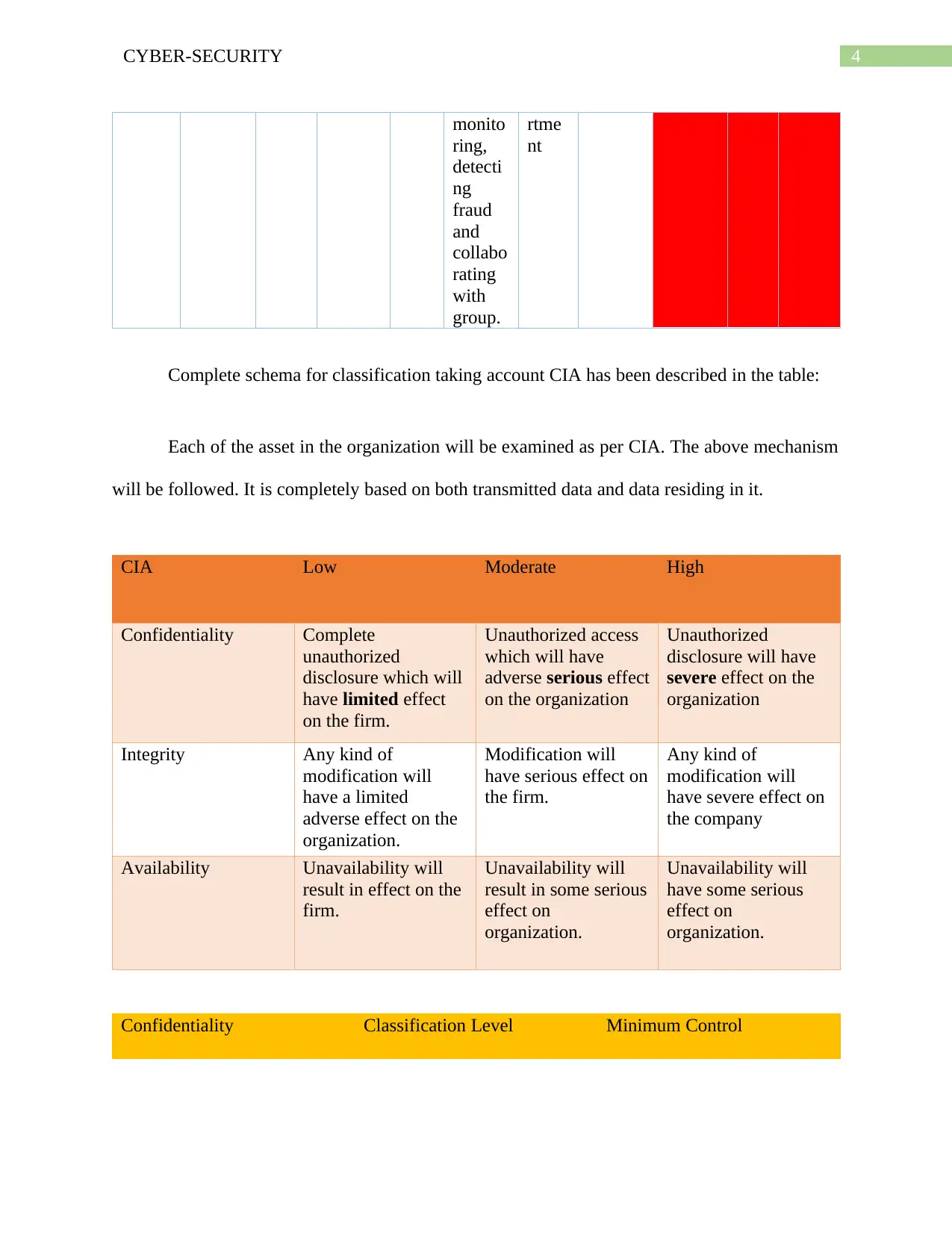
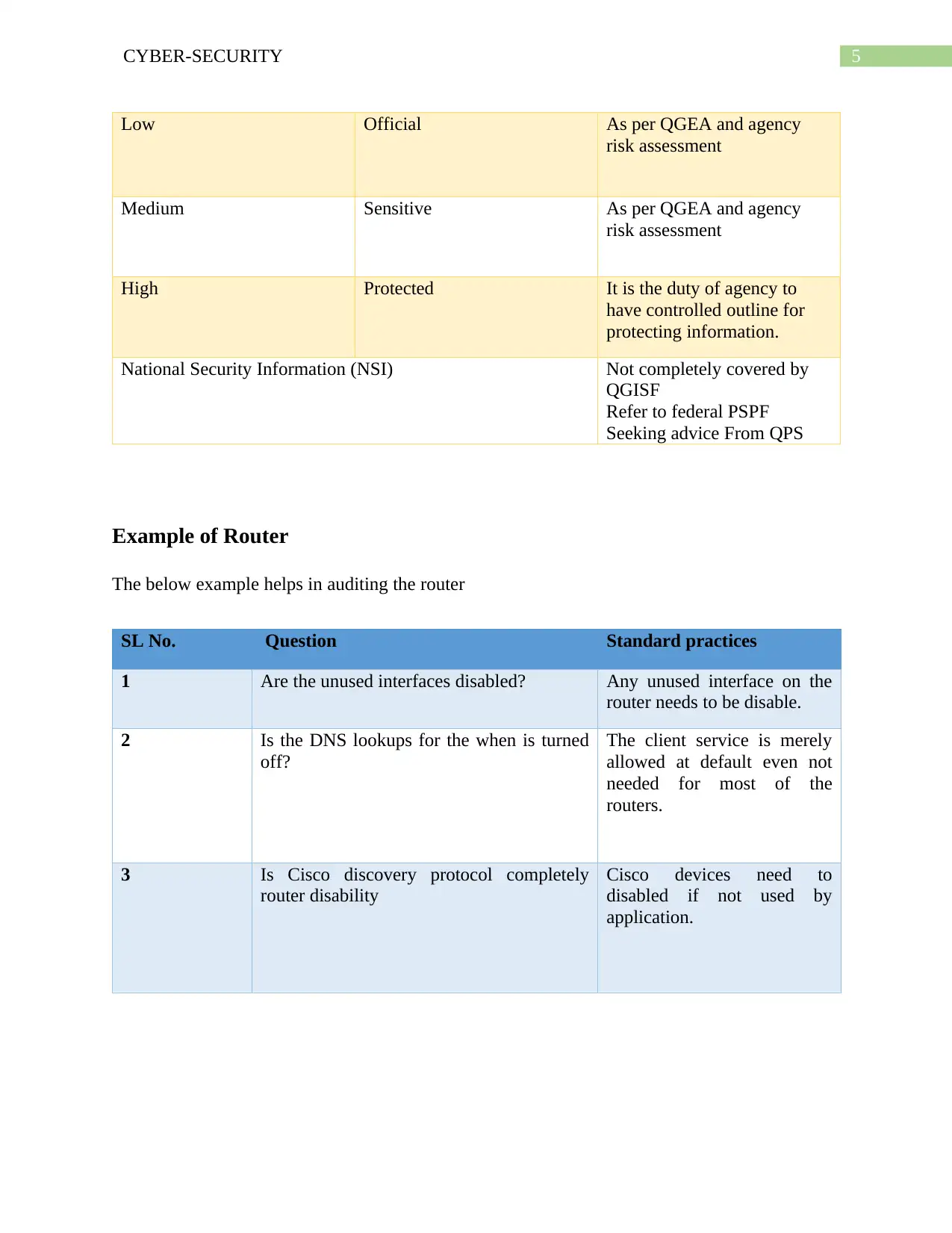
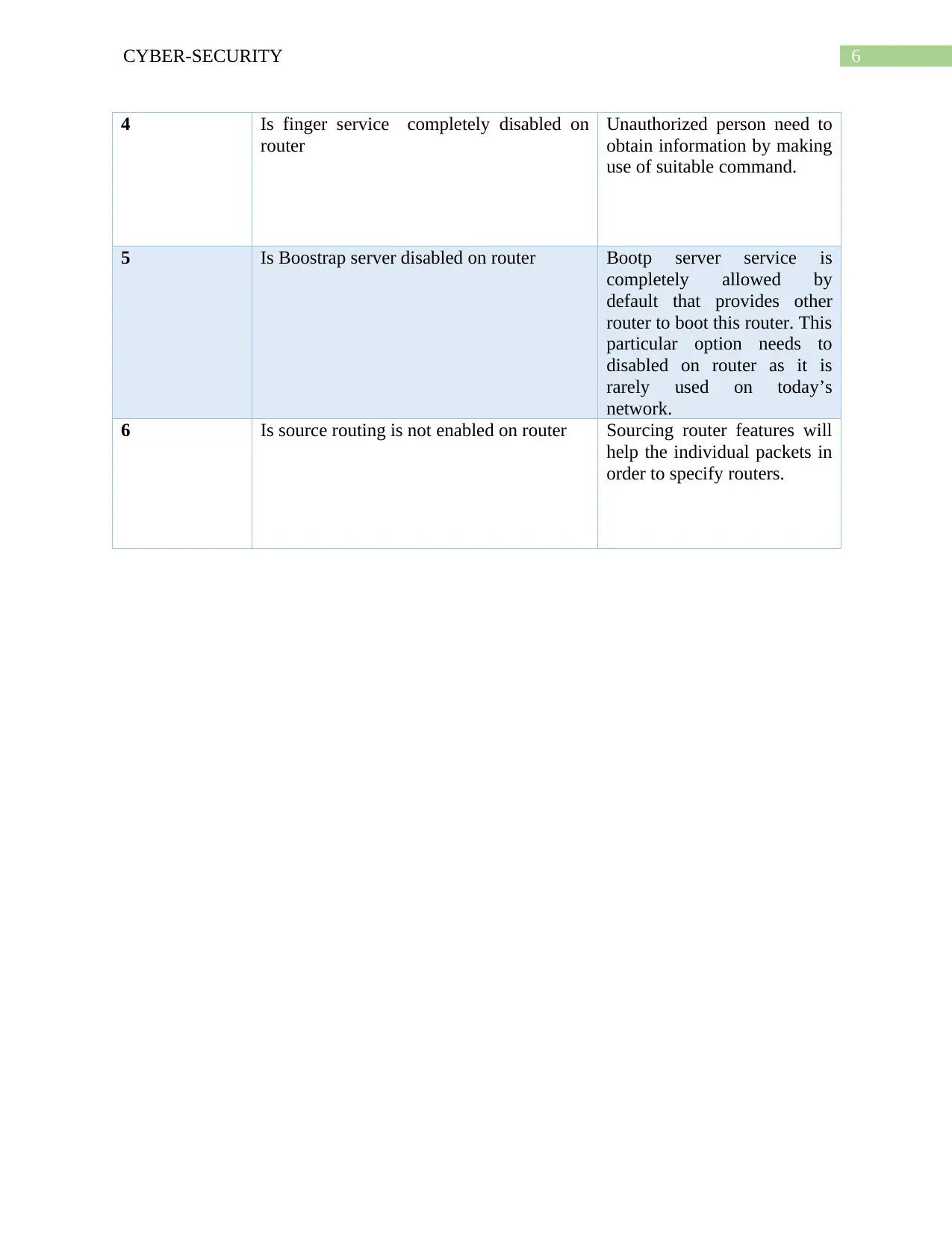
This document presents a comprehensive solution to a CPIS 606 assignment focused on IT auditing, specifically addressing the creation of an IT asset inventory and the auditing of network devices, with a particular emphasis on routers. The assignment requires the identification and categorization of IT assets, including hardware, software, and telecommunication devices, alongside a classification schema based on the CIA triad (Confidentiality, Integrity, and Availability). The solution provides detailed asset inventories, classification tables, and examples of router auditing, including questions to assess security practices like disabling unused interfaces, securing DNS lookups, and disabling unnecessary services. The document also includes the author's notes, which provide insights into the importance of maintaining a current asset inventory for effective cybersecurity incident response and maintaining trust with partners and stakeholders. The solution also includes a complete schema for classification taking account CIA has been described in the table.
1 out of 7




![[object Object]](/_next/static/media/star-bottom.7253800d.svg)