CQUniversity COIT20262 Assignment 1: Network Security Analysis Report
VerifiedAdded on 2022/12/22
|9
|2226
|91
Homework Assignment
AI Summary
This document presents a comprehensive solution for COIT20262 Assignment 1, focusing on advanced network security concepts. The assignment delves into packet capture and analysis, exploring potential attack scenarios and mitigation strategies. It covers cryptography, including key distribution methods and digital signatures, evaluating their strengths and weaknesses in securing network communications. Furthermore, the solution provides an in-depth overview of Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks, detailing their characteristics, attack entities, and mitigation techniques, specifically addressing ping flooding attacks. The document includes detailed explanations, and references to provide a robust understanding of the topics covered. This assignment is designed to provide a comprehensive understanding of network security principles and practices.
COIT20262 Assignment 1 Submission Term 1, 2019
COIT20262 - Advanced Network Security, Term 1, 2019
Assignment 1 Submission
Due date: 5pm Friday 26 April 2019 (Week 6) ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 9
COIT20262 - Advanced Network Security, Term 1, 2019
Assignment 1 Submission
Due date: 5pm Friday 26 April 2019 (Week 6) ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COIT20262 Assignment 1 Submission Term 1, 2019
Question 1. Packet Capture and Analysis
Part (e)
As per the assumptions the attacker to create a copy of the netcad program, which can be
named netcad2, would modify the source code of netcad. The implementation would however
create a risk for the source code as the tool would no longer be able to determine the
messages in the network. In addition to this, the data transfers taking palce in the network
would not be identified. The RSA encryptions techniques can be utilized for the decryption of
the data flowing through the network.
Part (f)
In situation where a modification attack takes place on the UDP and the change in unit code
from COIT20262 to COIT20263, there would not be any notification for the server residing
at node 3. Hence the server would be unaware of any of the attack in the networking node.
The cookie stealing attack would be used for obtaining an access to the server by the hacker. .
The malicious SQL codes would be then run on the server which would modify the database.
Part (g)
The servers would not be aware of the attack performed and any type of modifications made
on the network. The replay attack generally occurs in the TCP exchange on the severs. The
attacker performs interception attacks on the sever with the help of masquerade occurring cue
to the retransition process and replay attacks performed on the network server. The risk of the
attack can be however resolved with tagging each of the frames sent and received through the
network from the users with frame ID.
Advanced Network Security Page 2 of 9
Question 1. Packet Capture and Analysis
Part (e)
As per the assumptions the attacker to create a copy of the netcad program, which can be
named netcad2, would modify the source code of netcad. The implementation would however
create a risk for the source code as the tool would no longer be able to determine the
messages in the network. In addition to this, the data transfers taking palce in the network
would not be identified. The RSA encryptions techniques can be utilized for the decryption of
the data flowing through the network.
Part (f)
In situation where a modification attack takes place on the UDP and the change in unit code
from COIT20262 to COIT20263, there would not be any notification for the server residing
at node 3. Hence the server would be unaware of any of the attack in the networking node.
The cookie stealing attack would be used for obtaining an access to the server by the hacker. .
The malicious SQL codes would be then run on the server which would modify the database.
Part (g)
The servers would not be aware of the attack performed and any type of modifications made
on the network. The replay attack generally occurs in the TCP exchange on the severs. The
attacker performs interception attacks on the sever with the help of masquerade occurring cue
to the retransition process and replay attacks performed on the network server. The risk of the
attack can be however resolved with tagging each of the frames sent and received through the
network from the users with frame ID.
Advanced Network Security Page 2 of 9

COIT20262 Assignment 1 Submission Term 1, 2019
Question 2. Cryptography
Part (c)
For identifying the methods to be used for the distribution of the public keys throughout the
networks, the Moodle forum and the email attachment are subjected to attack. The keys are
distributed among the users in the network with help of mails in the network. With the
Moodle forum the public key distributions would be done on the forum and the public keys
can be downloaded easily from the forum on Moodle. The user would however need a key
for downloading the public key from the forum. The authentication process is used here for
the security of the system so the messages transfer in the between the users can be kept
discreet. However the privacy can be comprised the by the users who are sharing the private
key with the users who would be receiving the messages. However, compromising the
authentication functions in the network would lead to denial of services and forgery.
However, the authentication facilities are aptly integrated in the mail services but absent in
the Moodle. Hence, message attacks can easily be performed in the Moodle, which would be
affecting the security in the system and the key confirmation attacks which would create
message leaks within the network.
Part (d)
For the provided scenario the digital signatures are used for the distribution of the
public keys in the network via the Moodel website. The signature is secured process and in
comparison to the normal authentication provides better security constraints for the
encryption, decryption and authentication procedures in the network. Hence, for the private
keys are to be encrypted securely in the network and posted on the Moodle forum. The
encryption technique would be providing an efficient confidentiality to the keys so that they
are not easily accessible by the other members not having access to the decryption process in
the network. The receiver is also required to generate an acknowledgement of descripting the
Advanced Network Security Page 3 of 9
Question 2. Cryptography
Part (c)
For identifying the methods to be used for the distribution of the public keys throughout the
networks, the Moodle forum and the email attachment are subjected to attack. The keys are
distributed among the users in the network with help of mails in the network. With the
Moodle forum the public key distributions would be done on the forum and the public keys
can be downloaded easily from the forum on Moodle. The user would however need a key
for downloading the public key from the forum. The authentication process is used here for
the security of the system so the messages transfer in the between the users can be kept
discreet. However the privacy can be comprised the by the users who are sharing the private
key with the users who would be receiving the messages. However, compromising the
authentication functions in the network would lead to denial of services and forgery.
However, the authentication facilities are aptly integrated in the mail services but absent in
the Moodle. Hence, message attacks can easily be performed in the Moodle, which would be
affecting the security in the system and the key confirmation attacks which would create
message leaks within the network.
Part (d)
For the provided scenario the digital signatures are used for the distribution of the
public keys in the network via the Moodel website. The signature is secured process and in
comparison to the normal authentication provides better security constraints for the
encryption, decryption and authentication procedures in the network. Hence, for the private
keys are to be encrypted securely in the network and posted on the Moodle forum. The
encryption technique would be providing an efficient confidentiality to the keys so that they
are not easily accessible by the other members not having access to the decryption process in
the network. The receiver is also required to generate an acknowledgement of descripting the
Advanced Network Security Page 3 of 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COIT20262 Assignment 1 Submission Term 1, 2019
key so that network would be able to track the number of decryption made in the Moodle.
This would help the network in keeping the system secure with help of this tracking process.
The denial of service from the server end would occur in case there is an unauthenticated
access to the network and digital signature is used for achieving the security. In a fully
functional security system, a pattern is to follow which is dependent on the signed message.
Part (e)
Digital signature is an efficient form of security mechanism that helps in the security of the
network with an increase efficiency than that of the authentication procedures taking place in
the system. The reliability of the digital signature is more than that of the encryption process
as the digital signature is a combination of the encryption technique along with that of the
authentication process. Another huge benefit of the digital signature is that the method would
be helpful in decryption as they would be only be possible with proper authentication and
decryption key. The signatures would also maintain the confidentiality and authenticity of the
files that are flowing through the network. More number of attacks can also be stopped with
the help of the digital signature technique used in the system. The Denial of service and the
man in the middle attacks would be successfully stopped in the system. However, the major
drawback of the digital signature is that they would do not have a self-sufficient security
feature that would be preventing them from being stolen easily. The owner of the key would
also lack in preservation of the rights over the authentication of the digital signature
developed by them.
Question 3. Denial of Service Attack Research
Overview of DDoS Attacks
DoS Attack: The Denial of service attack is a type of network vulnerability that would be
hampering the execution process of the networking system. The attacks would make the
services from the server inaccessible to the clients, which would be creating some serious
Advanced Network Security Page 4 of 9
key so that network would be able to track the number of decryption made in the Moodle.
This would help the network in keeping the system secure with help of this tracking process.
The denial of service from the server end would occur in case there is an unauthenticated
access to the network and digital signature is used for achieving the security. In a fully
functional security system, a pattern is to follow which is dependent on the signed message.
Part (e)
Digital signature is an efficient form of security mechanism that helps in the security of the
network with an increase efficiency than that of the authentication procedures taking place in
the system. The reliability of the digital signature is more than that of the encryption process
as the digital signature is a combination of the encryption technique along with that of the
authentication process. Another huge benefit of the digital signature is that the method would
be helpful in decryption as they would be only be possible with proper authentication and
decryption key. The signatures would also maintain the confidentiality and authenticity of the
files that are flowing through the network. More number of attacks can also be stopped with
the help of the digital signature technique used in the system. The Denial of service and the
man in the middle attacks would be successfully stopped in the system. However, the major
drawback of the digital signature is that they would do not have a self-sufficient security
feature that would be preventing them from being stolen easily. The owner of the key would
also lack in preservation of the rights over the authentication of the digital signature
developed by them.
Question 3. Denial of Service Attack Research
Overview of DDoS Attacks
DoS Attack: The Denial of service attack is a type of network vulnerability that would be
hampering the execution process of the networking system. The attacks would make the
services from the server inaccessible to the clients, which would be creating some serious
Advanced Network Security Page 4 of 9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COIT20262 Assignment 1 Submission Term 1, 2019
problems in the network, which would hamper the security of the network. The DoS attack
would also create problem regarding the communication within the network. The attacker
sends a huge number of data packets to the network that would flood the network
communication medium with unwanted data in the network interfaces. This hampers the
performances and the efficiencies in the network and stop the network in return stops the
services that the network provides it to the clients in the network. It can be stated that the
DoS attack has the ability to impact entire online user base. Thus, the DoS attack turns to be
one of the major attacks that has the capability to conduct cyber scandals. However, it is
observed that a DoS attacks often stays for weeks and sometimes for months. This makes the
system destructive and effects the performance of the organization. These can in impact the
working in different ways has the ability to cause revenue loss, and will lead to huge damage.
DDoS Attack: denial-of-service (DoS) attack used for making the machine unavailable
towards there users. This includes activities that suspends the working of the host server by
gaining control over the internet. A distributed denial-of-service (DDoS) is where the source
of attack is more than one, and aims at attacking the unique IP addresses. It is analogous to a
group of people crowding the entry door or gate to a shop or business, and not letting
legitimate parties enter into the shop or business, disrupting normal operations. In a typical
connection, the user sends a message asking the server to authenticate it. After the server
returns towards the system, the user needs proper authentication approval so that they can
gain access over the device. The user recognizes this appreciation and then allowed towards
the server. In a denial of service attack, the user sends several authentication requests to the
server, filling it up. Once the system identifies an attack, it is observed that the system tries to
stop the attackers. After the connection is stopped by, the attacker tries to sends a new batch
of forged requests. The process begins again tying to attack the system until they get the
control over the system.
Advanced Network Security Page 5 of 9
problems in the network, which would hamper the security of the network. The DoS attack
would also create problem regarding the communication within the network. The attacker
sends a huge number of data packets to the network that would flood the network
communication medium with unwanted data in the network interfaces. This hampers the
performances and the efficiencies in the network and stop the network in return stops the
services that the network provides it to the clients in the network. It can be stated that the
DoS attack has the ability to impact entire online user base. Thus, the DoS attack turns to be
one of the major attacks that has the capability to conduct cyber scandals. However, it is
observed that a DoS attacks often stays for weeks and sometimes for months. This makes the
system destructive and effects the performance of the organization. These can in impact the
working in different ways has the ability to cause revenue loss, and will lead to huge damage.
DDoS Attack: denial-of-service (DoS) attack used for making the machine unavailable
towards there users. This includes activities that suspends the working of the host server by
gaining control over the internet. A distributed denial-of-service (DDoS) is where the source
of attack is more than one, and aims at attacking the unique IP addresses. It is analogous to a
group of people crowding the entry door or gate to a shop or business, and not letting
legitimate parties enter into the shop or business, disrupting normal operations. In a typical
connection, the user sends a message asking the server to authenticate it. After the server
returns towards the system, the user needs proper authentication approval so that they can
gain access over the device. The user recognizes this appreciation and then allowed towards
the server. In a denial of service attack, the user sends several authentication requests to the
server, filling it up. Once the system identifies an attack, it is observed that the system tries to
stop the attackers. After the connection is stopped by, the attacker tries to sends a new batch
of forged requests. The process begins again tying to attack the system until they get the
control over the system.
Advanced Network Security Page 5 of 9

COIT20262 Assignment 1 Submission Term 1, 2019
Difference between the DoS and DDoS attacks: during a DoS attack, a committer uses
single Internet connection for exploiting the vulnerability. After this, the attacker attacks the
system and flood with the fake requests for exhausting the server resources. On the other
hand, distributed denial of service (DDoS) attacks are launched from several connected
devices that are distributed over the Internet. Unlike single-source, DoS attacks, DDoS
attacks aims at targeting the network infrastructure in order to saturate the system with high
volume of attacks. In addition to this DDoS attacks also vary in the manner of their
execution. Moreover, it can be stated that the DoS performs the attacks by using homebrewed
scripts (e.g., Low Orbit Ion Canon). DDoS attacks are also launched from botnets that uses
new clusters of devices infected with viruses so that they can be used for the purpose of
attacking the devices.
Advanced Network Security Page 6 of 9
Difference between the DoS and DDoS attacks: during a DoS attack, a committer uses
single Internet connection for exploiting the vulnerability. After this, the attacker attacks the
system and flood with the fake requests for exhausting the server resources. On the other
hand, distributed denial of service (DDoS) attacks are launched from several connected
devices that are distributed over the Internet. Unlike single-source, DoS attacks, DDoS
attacks aims at targeting the network infrastructure in order to saturate the system with high
volume of attacks. In addition to this DDoS attacks also vary in the manner of their
execution. Moreover, it can be stated that the DoS performs the attacks by using homebrewed
scripts (e.g., Low Orbit Ion Canon). DDoS attacks are also launched from botnets that uses
new clusters of devices infected with viruses so that they can be used for the purpose of
attacking the devices.
Advanced Network Security Page 6 of 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
COIT20262 Assignment 1 Submission Term 1, 2019
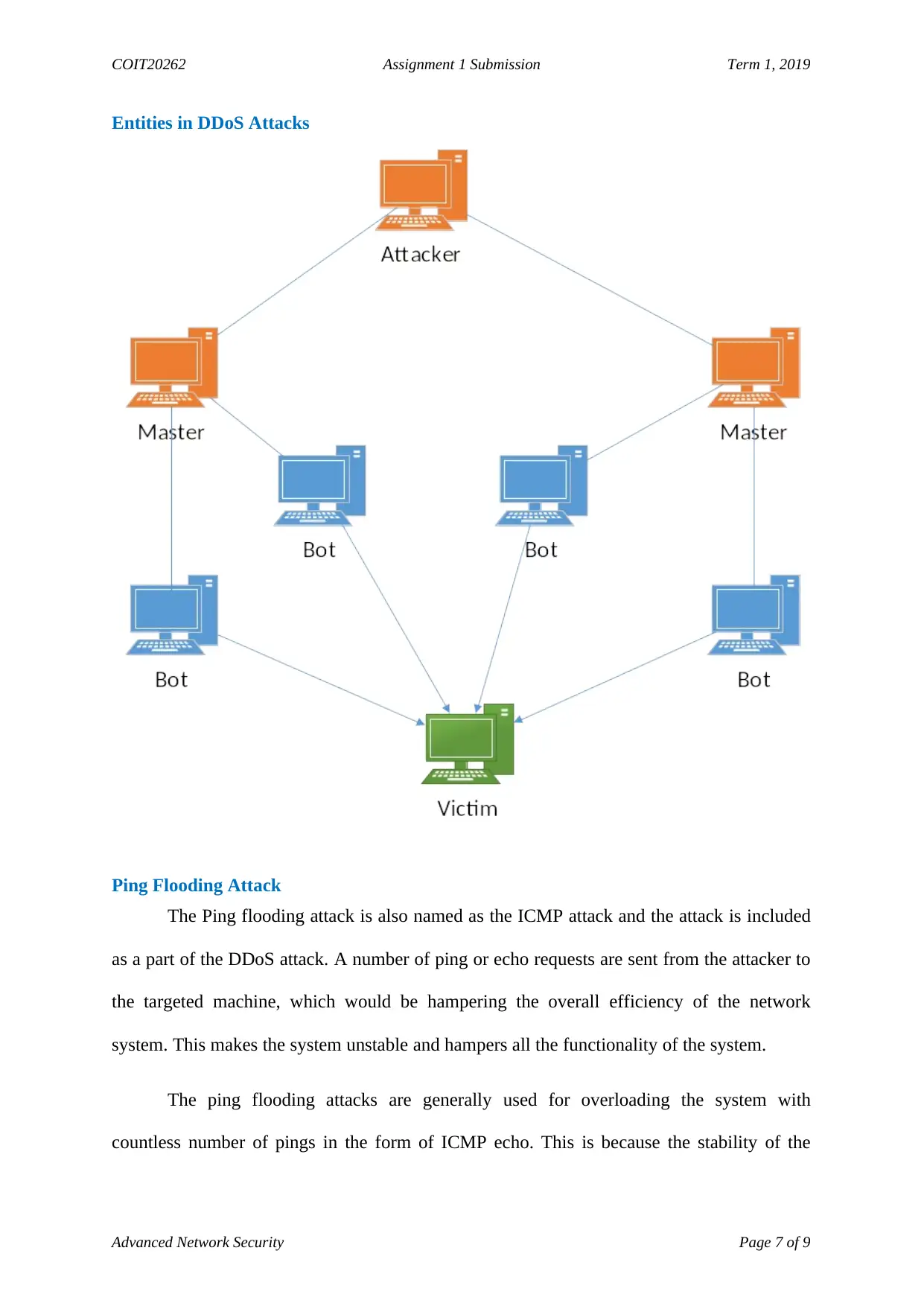
Entities in DDoS Attacks
Ping Flooding Attack
The Ping flooding attack is also named as the ICMP attack and the attack is included
as a part of the DDoS attack. A number of ping or echo requests are sent from the attacker to
the targeted machine, which would be hampering the overall efficiency of the network
system. This makes the system unstable and hampers all the functionality of the system.
The ping flooding attacks are generally used for overloading the system with
countless number of pings in the form of ICMP echo. This is because the stability of the
Advanced Network Security Page 7 of 9
Entities in DDoS Attacks
Ping Flooding Attack
The Ping flooding attack is also named as the ICMP attack and the attack is included
as a part of the DDoS attack. A number of ping or echo requests are sent from the attacker to
the targeted machine, which would be hampering the overall efficiency of the network
system. This makes the system unstable and hampers all the functionality of the system.
The ping flooding attacks are generally used for overloading the system with
countless number of pings in the form of ICMP echo. This is because the stability of the
Advanced Network Security Page 7 of 9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COIT20262 Assignment 1 Submission Term 1, 2019
networking system is lost and the reduces the security mechanism for the system which
would lower the efficiency of security and make the system vulnerable in return. An
important role is being played by the IP address, as information about the IP addresses would
be very important for the attacker to attack the system and send a large number of pings to the
address. The attacker has a particular sequence in which the attack on the system is to be
performed so that they are able to execute the attack properly and possess a greater
bandwidth than that of the victim.
Mitigating Ping Flooding Attack
The recommended software for mitigating the risks involving the attacks in the
network is CloudFare. In addition to the software, additional firewall installations are also
required in the network for prevention of the attack. This would be helpful for reducing the
number of pings received by the system and unidentified IP would not be entertained.
Advanced Network Security Page 8 of 9
networking system is lost and the reduces the security mechanism for the system which
would lower the efficiency of security and make the system vulnerable in return. An
important role is being played by the IP address, as information about the IP addresses would
be very important for the attacker to attack the system and send a large number of pings to the
address. The attacker has a particular sequence in which the attack on the system is to be
performed so that they are able to execute the attack properly and possess a greater
bandwidth than that of the victim.
Mitigating Ping Flooding Attack
The recommended software for mitigating the risks involving the attacks in the
network is CloudFare. In addition to the software, additional firewall installations are also
required in the network for prevention of the attack. This would be helpful for reducing the
number of pings received by the system and unidentified IP would not be entertained.
Advanced Network Security Page 8 of 9

COIT20262 Assignment 1 Submission Term 1, 2019
Bibliography:
Jaber, A. N., Zolkipli, M. F., Majid, M. A., & Anwar, S. (2017). Methods for Preventing
Distributed Denial of Service Attacks in Cloud Computing. Advanced Science Letters, 23(6),
5282-5285.
Luo, S., Wu, J., Li, J., & Pei, B. (2015, August). A defense mechanism for distributed denial
of service attack in software-defined networks. In 2015 Ninth International Conference on
Frontier of Computer Science and Technology (pp. 325-329). IEEE.
Meti, N., Narayan, D. G., & Baligar, V. P. (2017, September). Detection of distributed denial
of service attacks using machine learning algorithms in software defined networks. In 2017
International Conference on Advances in Computing, Communications and Informatics
(ICACCI) (pp. 1366-1371). IEEE.
Zhang, X., Yang, S., & Liu, Y. (2017). Integrated digital signature scheme research for the
hospital electronic medical record system. China Medical Equipment, 14(2), 97-99.
Advanced Network Security Page 9 of 9
Bibliography:
Jaber, A. N., Zolkipli, M. F., Majid, M. A., & Anwar, S. (2017). Methods for Preventing
Distributed Denial of Service Attacks in Cloud Computing. Advanced Science Letters, 23(6),
5282-5285.
Luo, S., Wu, J., Li, J., & Pei, B. (2015, August). A defense mechanism for distributed denial
of service attack in software-defined networks. In 2015 Ninth International Conference on
Frontier of Computer Science and Technology (pp. 325-329). IEEE.
Meti, N., Narayan, D. G., & Baligar, V. P. (2017, September). Detection of distributed denial
of service attacks using machine learning algorithms in software defined networks. In 2017
International Conference on Advances in Computing, Communications and Informatics
(ICACCI) (pp. 1366-1371). IEEE.
Zhang, X., Yang, S., & Liu, Y. (2017). Integrated digital signature scheme research for the
hospital electronic medical record system. China Medical Equipment, 14(2), 97-99.
Advanced Network Security Page 9 of 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





